Professional Documents
Culture Documents
Day 3
Day 3
Uploaded by
api-3067200070 ratings0% found this document useful (0 votes)
22 views2 pagesThe document outlines the schedule for Day 3 of a cybersecurity conference. It includes sessions on enhancing security and privacy in IoT, how IT security affects businesses, computer and network security, malware attacks, cyber response strategies, security challenges and content authoring, and a panel discussion on lessons from 2015 data breaches. Various speakers will discuss threats to security and privacy from IoT, how companies can develop security plans, network security best practices, malware dangers and recovery strategies, how security firms assist with response plans, and reducing security risks. The panel will explore why data breaches continue occurring and how companies can prevent them.
Original Description:
Original Title
day 3
Copyright
© © All Rights Reserved
Available Formats
DOCX, PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentThe document outlines the schedule for Day 3 of a cybersecurity conference. It includes sessions on enhancing security and privacy in IoT, how IT security affects businesses, computer and network security, malware attacks, cyber response strategies, security challenges and content authoring, and a panel discussion on lessons from 2015 data breaches. Various speakers will discuss threats to security and privacy from IoT, how companies can develop security plans, network security best practices, malware dangers and recovery strategies, how security firms assist with response plans, and reducing security risks. The panel will explore why data breaches continue occurring and how companies can prevent them.
Copyright:
© All Rights Reserved
Available Formats
Download as DOCX, PDF, TXT or read online from Scribd
Download as docx, pdf, or txt
0 ratings0% found this document useful (0 votes)
22 views2 pagesDay 3
Day 3
Uploaded by
api-306720007The document outlines the schedule for Day 3 of a cybersecurity conference. It includes sessions on enhancing security and privacy in IoT, how IT security affects businesses, computer and network security, malware attacks, cyber response strategies, security challenges and content authoring, and a panel discussion on lessons from 2015 data breaches. Various speakers will discuss threats to security and privacy from IoT, how companies can develop security plans, network security best practices, malware dangers and recovery strategies, how security firms assist with response plans, and reducing security risks. The panel will explore why data breaches continue occurring and how companies can prevent them.
Copyright:
© All Rights Reserved
Available Formats
Download as DOCX, PDF, TXT or read online from Scribd
Download as docx, pdf, or txt
You are on page 1of 2
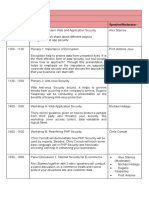
Day 3
13 October 2016, Thursday
Time
Programme
Speaker/Moderator
0900 - 1000
Keynote 3: Enhance Security and Privacy in the Internet
of Things (IoT)
David Caissy
Nowadays, there are numerous arising threats on the
issues of security and privacy in IoT. Through this
presentation, David Caissy will be share about the
threats and concern of security and privacy faced in IoT,
which has plays an fundamental role in protecting
personal data and monitor their flow from things to the
cloud for the industry.
1000 - 1030
Plenary 4: How Does IT Security Affects Everybody
Chris Babel
Tzachi Levy will be giving a presentation on how does IT
security will affects every business and organization.
Company need to have a security plain to ensure the
safety of information assets.
1100 - 1200
Breakout 2A: Computer and Network Security
Kevin Beaver
Kevin Beaver will be discussing what is network security,
how does it protect you your organisation and what
organization will be benefits of network security.
1100 - 1200
Breakout 2B: Malware Attack
Costin Raiu
With the rise of widespread internet access, malware
attack are commonly used to steal sensitive information
and gain access to private computer systems. Through
this session, Costin Raiu will be sharing what are the
dangers that the businesses faced and how to protect
your businesses from such activities and recover from
the attacks.
1100 - 1200
Breakout 2C: Cyber Response Strategies
Cyber Response Strategies are mostly used by IT
security company. Through this session, Andrew Borene
will share about how IT security company works in
helping to develop response strategies to defend and
protect your businesses from being attack.
Andrew Borene
1100 - 1200
Breakout 2D: Security Challenges and Content Authoring
Christopher G. Cwalina
There are list of security challenges that identified in this
industry. Christopher G. Cwalina will be discussing on
how to reduce risks and protect the information that
manages our business as well as content authoring
techniques.
1400 - 1500
Panel Discussion 3: Takeaways from 2015's Data
Breaches
Information security is no longer a mysterious function
and many companies suffered huge loss due the leak of
customers information. Why data breaches keep
occurring? How can your company guard against data
breaches? During the discussion, the speakers will
explore on why were experiencing these roadblocks and
discuss on how to to minimize this impact on your
security program.
David Caissy
(Moderator)
Kevin Beaver
Chris Babel
Christopher G.
Cwalina
You might also like
- Day 2Document2 pagesDay 2api-306720007No ratings yet
- Cyber Security and Cyber ThreatsDocument7 pagesCyber Security and Cyber ThreatsAnonymous CwJeBCAXpNo ratings yet
- Fabellore SOCDocument3 pagesFabellore SOCJoshua RoxasNo ratings yet
- Siblu Khan 1101216058 CSE: Presented byDocument26 pagesSiblu Khan 1101216058 CSE: Presented byPS GameRNo ratings yet
- Siblu Khan 1101216058 CSE: Presented byDocument26 pagesSiblu Khan 1101216058 CSE: Presented byBGIIT COMPUTER EDUCATIONNo ratings yet
- Introduction To Cyber Security Chapter 1Document6 pagesIntroduction To Cyber Security Chapter 1Pinoy Ako EntertainmentNo ratings yet
- Top Security Trends For 2020Document4 pagesTop Security Trends For 2020Dean JosephNo ratings yet
- CH 05Document38 pagesCH 05Febri MonikaNo ratings yet
- Green (2015) Cyber Security An Introduction To Non-Technical ManagersDocument264 pagesGreen (2015) Cyber Security An Introduction To Non-Technical ManagersFinneganNo ratings yet
- The 10 Keystones of Cybersecurity 2020Document15 pagesThe 10 Keystones of Cybersecurity 2020Mohd Khairul Adne Mat HussinNo ratings yet
- Cyber Security Magazine MalaysiaDocument40 pagesCyber Security Magazine Malaysiaendhy_azizNo ratings yet
- Seminar Report by Agung WijayakusumaDocument3 pagesSeminar Report by Agung WijayakusumaJati Purwosunu RoyatNo ratings yet
- Securing Your Digital WorldDocument8 pagesSecuring Your Digital WorldlhbutiyaNo ratings yet
- 8 Steps to Better Security: A Simple Cyber Resilience Guide for BusinessFrom Everand8 Steps to Better Security: A Simple Cyber Resilience Guide for BusinessNo ratings yet
- Vol13 No2Document44 pagesVol13 No2Jainiti PrasadNo ratings yet
- Module - 1 - Dale - Baltazar - Assignment 1Document4 pagesModule - 1 - Dale - Baltazar - Assignment 1dalebaltazarNo ratings yet
- IIA-IsACA 2nd Annual IT Hacking ConferenceDocument20 pagesIIA-IsACA 2nd Annual IT Hacking ConferenceShaharudin BmnNo ratings yet
- Cyber Security 1st PhaseDocument12 pagesCyber Security 1st Phaseitjobsncr2000No ratings yet
- Transcript Cybersecurity Case A IBM Security Helps WimbledonDocument2 pagesTranscript Cybersecurity Case A IBM Security Helps WimbledonAhmed OthmenNo ratings yet
- Block 4 Cyber Security and IT ActDocument77 pagesBlock 4 Cyber Security and IT ActSougata ChattopadhyayNo ratings yet
- 1-An Executive Guide To SecurityDocument17 pages1-An Executive Guide To SecuritybbgarciNo ratings yet
- DIONISIO - Industry 4.0 WebinarDocument2 pagesDIONISIO - Industry 4.0 WebinarMaria Ela DionisioNo ratings yet
- CIS 4340 Windows System Security - FootprintingDocument3 pagesCIS 4340 Windows System Security - FootprintingRussell T FreemanNo ratings yet
- 16-SecurityBasics 70Document70 pages16-SecurityBasics 70Smita R. S.No ratings yet
- Cybe R Secu Rity: Pari Varshney 1222051 BSC (H) BiochemistryDocument7 pagesCybe R Secu Rity: Pari Varshney 1222051 BSC (H) BiochemistryjatinderNo ratings yet
- Information AssuranceDocument11 pagesInformation AssuranceNeil ElegioNo ratings yet
- The Good, The Bad and The Missing: A Narrative Review of Cyber-Security Implications For Australian Small BusinessesDocument20 pagesThe Good, The Bad and The Missing: A Narrative Review of Cyber-Security Implications For Australian Small Businesseschairul rachmanNo ratings yet
- Grp3 CYBER-SECURITYDocument17 pagesGrp3 CYBER-SECURITYJessa BuanNo ratings yet
- Cyber SecurityDocument23 pagesCyber Securitynayemnosor007No ratings yet
- Introduction To Cyber Security Handbook PDFDocument104 pagesIntroduction To Cyber Security Handbook PDFVjay MadhamNo ratings yet
- Cybersecurity for Beginners : Learn the Fundamentals of Cybersecurity in an Easy, Step-by-Step Guide: 1From EverandCybersecurity for Beginners : Learn the Fundamentals of Cybersecurity in an Easy, Step-by-Step Guide: 1No ratings yet
- Comprehensive Guide to Personal Cybersecurity: Personal Cybersecurity Practices for a Safer Digital LifeFrom EverandComprehensive Guide to Personal Cybersecurity: Personal Cybersecurity Practices for a Safer Digital LifeNo ratings yet
- Network Security and Anti HackingDocument8 pagesNetwork Security and Anti Hackingnewlog6303No ratings yet
- Cyber Security NavigatingTrendDocument7 pagesCyber Security NavigatingTrendLasya AnnambhatlaNo ratings yet
- Information Technology Cyber Security vs. Computer SecurityDocument7 pagesInformation Technology Cyber Security vs. Computer SecuritySisterjoonNo ratings yet
- Cyber SecurityDocument23 pagesCyber SecurityChandu SyamNo ratings yet
- Cyber Security MGTDocument13 pagesCyber Security MGTSmart RobitoNo ratings yet
- Day 1Document2 pagesDay 1api-306720007No ratings yet
- Cns Full MaterialDocument233 pagesCns Full MaterialMadhuri BethaNo ratings yet
- CYBERSECURITYby Dipesh JhaDocument21 pagesCYBERSECURITYby Dipesh Jhadipesh104jhaNo ratings yet
- Blog Template - Cyber Security 1Document6 pagesBlog Template - Cyber Security 1ShieldonsystemsNo ratings yet
- 17 Cs 39Document17 pages17 Cs 39Saurabh ChaturvediNo ratings yet
- Introduction To CybersecurityDocument30 pagesIntroduction To Cybersecurityadam iqbalNo ratings yet
- Hakin9 EN 03 2014Document74 pagesHakin9 EN 03 2014xtofsetNo ratings yet
- Data Encryption and Security: Q: Find The Current Security Challenges Faced by Computer Security? AnsDocument2 pagesData Encryption and Security: Q: Find The Current Security Challenges Faced by Computer Security? AnsNF CyborgNo ratings yet
- RISKSDocument5 pagesRISKSCarleen Grace DeleonNo ratings yet
- Why You Need Cyber Security:-The Protection of Data, Networks and Computing Power. The Protection of DataDocument4 pagesWhy You Need Cyber Security:-The Protection of Data, Networks and Computing Power. The Protection of DataSainbu GuptaNo ratings yet
- ProjectDocument6 pagesProjectacharyay72No ratings yet
- Cloud Storage VulnerabilityDocument9 pagesCloud Storage Vulnerabilityapi-357344694No ratings yet
- Cyber Security BacicsDocument53 pagesCyber Security BacicsJoël KangalaNo ratings yet
- Defending Your Budget: How To Show ROI of Cybersecurity InvestmentsDocument7 pagesDefending Your Budget: How To Show ROI of Cybersecurity InvestmentsTanteNo ratings yet
- Cybersecurity For Beginners: Learn How To Defend Against Online ThreatsFrom EverandCybersecurity For Beginners: Learn How To Defend Against Online ThreatsNo ratings yet
- Imc401 Group Assignment Cyber SecurityDocument11 pagesImc401 Group Assignment Cyber SecurityNUR AZLINA MUHAMMADNo ratings yet
- Cyber SecurityDocument31 pagesCyber Securityshivashankarhr06No ratings yet
- PDFDocument29 pagesPDFnay jimenezNo ratings yet
- AssignmentDocument5 pagesAssignmentMinza ANo ratings yet
- IAS301 Midterm Lesson1Document21 pagesIAS301 Midterm Lesson1Lee Andrew CelesteNo ratings yet
- Cyber Security ObjectivesDocument3 pagesCyber Security ObjectivesManishaNo ratings yet