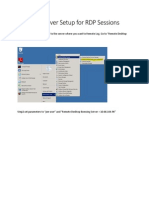
Professional Documents
Culture Documents
Kerboros
Kerboros
Uploaded by
Gurdev SinghOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Kerboros
Kerboros
Uploaded by
Gurdev SinghCopyright:
Available Formats
What is Kerberos?
Kerberos is a network authentication protocol created by MIT, and uses symmetric-key cryptography[18] to authenticate users to network services, which means passwords are never actually sent over the network. Consequently, when users authenticate to network services using Kerberos, unauthorized users attempting to gather passwords by monitoring network traffic are effectively thwarted. Advantages of Kerberos Most conventional network services use password-based authentication schemes. Such schemes require a user to authenticate to a given network server by supplying their username and password. Unfortunately, the transmission of authentication information for many services is unencrypted. For such a scheme to be secure, the network has to be inaccessible to outsiders, and all computers and users on the network must be trusted and trustworthy. Even if this is the case, a network that is connected to the Internet can no longer be assumed to be secure. Any attacker who gains access to the network can use a simple packet analyzer, also known as a packet sniffer, to intercept usernames and passwords, compromising user accounts and the integrity of the entire security infrastructure. The primary design goal of Kerberos is to eliminate the transmission of unencrypted passwords across the network. If used properly, Kerberos effectively eliminates the threat that packet sniffers would otherwise pose on a network. How Kerberos Works Kerberos differs from username/password authentication methods. Instead of authenticating each user to each network service, Kerberos uses symmetric encryption and a trusted third party (a KDC), to authenticate users to a suite of network services. When a user authenticates to the KDC, the KDC sends a ticket specific to that session back to the user's machine, and any Kerberosaware services look for the ticket on the user's machine rather than requiring the user to authenticate using a password. When a user on a Kerberos-aware network logs in to their workstation, their principal is sent to the KDC as part of a request for a TGT from the Authentication Server. This request can be sent by the log-in program so that it is transparent to the user, or can be sent by the kinit program after the
user logs in. The KDC then checks for the principal in its database. If the principal is found, the KDC creates a TGT, which is encrypted using the user's key and returned to that user. The login or kinit program on the client then decrypts the TGT using the user's key, which it computes from the user's password. The user's key is used only on the client machine and is not transmitted over the network. The TGT is set to expire after a certain period of time (usually ten to twentyfour hours) and is stored in the client machine's credentials cache. An expiration time is set so that a compromised TGT is of use to an attacker for only a short period of time. After the TGT has been issued, the user does not have to re-enter their password until the TGT expires or until they log out and log in again. Whenever the user needs access to a network service, the client software uses the TGT to request a new ticket for that specific service from the TGS. The service ticket is then used to authenticate the user to that service transparently. Note
Kerberos depends on the following network services to function correctly.
Approximate clock synchronization between the machines on the network. A clock synchronization program should be set up for the network, such as ntpd. Domain Name Service (DNS). You should ensure that the DNS entries and hosts on the network are all properly configured. Kerberos and PAM Kerberos-aware services do not currently make use of Pluggable Authentication Modules (PAM) these services bypass PAM completely. However, applications that use PAM can make use of Kerberos for authentication if the pam_krb5 module (provided in the pam_krb5 package) is installed. The pam_krb5 package contains sample configuration files that allow services such as login and gdm to authenticate users as well as obtain
initial credentials using their passwords. If access to network servers is always performed using Kerberos-aware services or services that use GSSAPI, such as IMAP, the network can be considered reasonably safe. Kerberos Terminology Kerberos has its own terminology to define various aspects of the service. Before learning how Kerberos works, it is important to learn the following terms. authentication server (AS) A server that issues tickets for a desired service which are in turn given to users for access to the service. The AS responds to requests from clients who do not have or do not send credentials with a request. It is usually used to gain access to the ticket-granting server (TGS) service by issuing a ticketgranting ticket (TGT). The AS usually runs on the same host as the key distribution center (KDC).
ciphertext Encrypted data.
client An entity on the network (a user, a host, or an application) that can receive a ticket from Kerberos.
credentials A temporary set of electronic credentials that verify the identity of a client for a particular service. Also called a ticket. key distribution center (KDC) A service that issues Kerberos tickets, and which usually run on the same host as the ticket-granting server (TGS). ticket A temporary set of electronic credentials that verify the identity of a client for a particular service. Also called credentials.
ticket-granting server (TGS) A server that issues tickets for a desired service which are in turn given to users for access to the service. The TGS usually runs on the same host as the KDC. ticket-granting ticket (TGT) A special ticket that allows the client to obtain additional tickets without applying for them from the KDC. realm A network that uses Kerberos, composed of one or more servers called KDCs and a potentially large number of clients.
You might also like
- VAN-DE-VIJVER-2002-Freschwater Diatoms From Ile de La Possesion PDFDocument209 pagesVAN-DE-VIJVER-2002-Freschwater Diatoms From Ile de La Possesion PDFKARINA DELGADONo ratings yet
- 2000 MSB Magazine WinterDocument40 pages2000 MSB Magazine Wintertmm53No ratings yet
- 9 Kerberos AuthenticationDocument3 pages9 Kerberos AuthenticationNeetishNo ratings yet
- Experiment No. - : W Hat Is Kerberos?Document7 pagesExperiment No. - : W Hat Is Kerberos?PoonamNo ratings yet
- KerberosDocument12 pagesKerberosAthithya RNo ratings yet
- 4G ReportDocument34 pages4G Reportraveesh91No ratings yet
- Kerberos NotesDocument7 pagesKerberos Notesskhanshaikh3No ratings yet
- Crypto Unit 5 ...Document9 pagesCrypto Unit 5 ...Roshan PradhanNo ratings yet
- Kerberos ExplainedDocument6 pagesKerberos ExplainedDavid GuluaNo ratings yet
- Research Paper On KerberosDocument4 pagesResearch Paper On Kerberosafeedvnlb100% (1)
- A Simple Authentication DialogueDocument2 pagesA Simple Authentication DialogueRandomNo ratings yet
- Us 14 Duckwall Abusing Microsoft Kerberos Sorry You Guys Don't Get It WPDocument9 pagesUs 14 Duckwall Abusing Microsoft Kerberos Sorry You Guys Don't Get It WPjmanteauNo ratings yet
- Course Code: CSE 606 Course Title: Cryptography & Information SecurityDocument6 pagesCourse Code: CSE 606 Course Title: Cryptography & Information SecurityNazmul HaqueNo ratings yet
- What Is Kerberos?: The Internet Is An Insecure Place. Many of The Protocols Used in The Internet Do Not ProvideDocument4 pagesWhat Is Kerberos?: The Internet Is An Insecure Place. Many of The Protocols Used in The Internet Do Not ProvideShweta BaliyanNo ratings yet
- VVFGC Cns Unit2 (Final)Document13 pagesVVFGC Cns Unit2 (Final)ArthiNo ratings yet
- Kerberos: by R.Venkatesh Ap/CseDocument37 pagesKerberos: by R.Venkatesh Ap/CseGunasekaran PNo ratings yet
- Unit 5Document34 pagesUnit 5sriramganesh8107No ratings yet
- INS - Assignment 2 (TCS2223033)Document6 pagesINS - Assignment 2 (TCS2223033)Kavinesh 123No ratings yet
- Kerberos X.509 Directory Authentication Service Part2-1Document22 pagesKerberos X.509 Directory Authentication Service Part2-1singh246018No ratings yet
- Introduction:: UNIT-4Document25 pagesIntroduction:: UNIT-4shiva guntiNo ratings yet
- Kerberos 1Document13 pagesKerberos 1Aravind SaiNo ratings yet
- Active Directory Security FundamentalsDocument11 pagesActive Directory Security FundamentalsBanji EwinNo ratings yet
- Kerberos AuthenticationDocument2 pagesKerberos Authenticationsethii_ankushNo ratings yet
- Kerberos PDFDocument2 pagesKerberos PDFGokulNo ratings yet
- Ijcnc 050205Document12 pagesIjcnc 050205AIRCC - IJCNCNo ratings yet
- Kerberos ArchitectureDocument11 pagesKerberos ArchitectureShashwat ShriparvNo ratings yet
- MODULEDocument74 pagesMODULEritikagupta.3kNo ratings yet
- 22 KerberosDocument22 pages22 KerberosSpoorthy HUNo ratings yet
- KERBEROSDocument9 pagesKERBEROSPoonam ChauhanNo ratings yet
- CNS Unit IV PDFDocument80 pagesCNS Unit IV PDFKartheeNo ratings yet
- NTLM Kerberos and Public Key Cryptography (1) 55-1Document27 pagesNTLM Kerberos and Public Key Cryptography (1) 55-1ozer longNo ratings yet
- 3-Red Teaming Active DirectoryDocument286 pages3-Red Teaming Active Directoryfutdh9404No ratings yet
- How Kerberos Authentication WorksDocument1 pageHow Kerberos Authentication Workssatheesh786No ratings yet
- Seatwork IASDocument1 pageSeatwork IASRheny BondocNo ratings yet
- Cryptography: Computer Science and EngineeringDocument33 pagesCryptography: Computer Science and Engineeringkundankeshari2537No ratings yet
- KerberosDocument3 pagesKerberosSrisomanadh MedicherlaNo ratings yet
- The KerberosDocument6 pagesThe Kerberosanon_785506245No ratings yet
- CS - Kerberos & Other Authentication ProtocolsDocument3 pagesCS - Kerberos & Other Authentication Protocolskhushiyadav88400No ratings yet
- Network Security GlossaryDocument6 pagesNetwork Security GlossaryAnkur VermaNo ratings yet
- Kerberos Seminar ReportDocument29 pagesKerberos Seminar ReportNaveen Krishnan100% (2)
- 4.2 Understand Kerberos Authentication and Domain SecurityDocument22 pages4.2 Understand Kerberos Authentication and Domain SecurityChitra TamilchelvanNo ratings yet
- Ijcet: International Journal of Computer Engineering & Technology (Ijcet)Document8 pagesIjcet: International Journal of Computer Engineering & Technology (Ijcet)IAEME PublicationNo ratings yet
- Kerberos AbstractDocument2 pagesKerberos Abstractsneha1991mishraNo ratings yet
- The Vulnerability of PasswordsDocument2 pagesThe Vulnerability of PasswordsKiran DevireddyNo ratings yet
- Information System Security AABFS-Jordan: Supervisor:Dr. Lo'ai Ali TawalbehDocument18 pagesInformation System Security AABFS-Jordan: Supervisor:Dr. Lo'ai Ali TawalbehRoyNo ratings yet
- The Kerberos Authentication System Was Developed at TheDocument23 pagesThe Kerberos Authentication System Was Developed at TheNageshNo ratings yet
- The Kerberos ProtocolDocument18 pagesThe Kerberos ProtocolJohn Wilson100% (1)
- ch4 Bu CnsDocument80 pagesch4 Bu CnsSudhanshu PandeyNo ratings yet
- Kerberos Protocol: An Overview: Carlo Baliello Alessandro Basso Cinzia Di GiustoDocument10 pagesKerberos Protocol: An Overview: Carlo Baliello Alessandro Basso Cinzia Di Giustoscet 315No ratings yet
- (CNS) Unit-2Document45 pages(CNS) Unit-2RudrNo ratings yet
- 12-User Identification and Authentication (Cont.)Document35 pages12-User Identification and Authentication (Cont.)Абзал КалдыбековNo ratings yet
- Benefits of Kerberos: Delegated AuthenticationDocument2 pagesBenefits of Kerberos: Delegated AuthenticationNURRUL ISMAILNo ratings yet
- Report On KerberosDocument28 pagesReport On KerberosShobhit JainNo ratings yet
- GlossaryDocument12 pagesGlossarydeserki20No ratings yet
- Kerberos and NTLM AuthenticationDocument4 pagesKerberos and NTLM AuthenticationAbhijeet KumarNo ratings yet
- Combined Efficient WSN Key Protocol For Internet of ThingsDocument20 pagesCombined Efficient WSN Key Protocol For Internet of ThingsK Asif RiadNo ratings yet
- Unit 4 - Information Security - WWW - Rgpvnotes.inDocument11 pagesUnit 4 - Information Security - WWW - Rgpvnotes.inshesh6200No ratings yet
- Practical-10 AIM: Study of Kerberos System.: An Introduction To KerberosDocument7 pagesPractical-10 AIM: Study of Kerberos System.: An Introduction To KerberosPresha ThakkarNo ratings yet
- Kerberoasting PDF 1632400601Document43 pagesKerberoasting PDF 1632400601marcus_fabioNo ratings yet
- Kerberos: Strengths and WeaknessesDocument2 pagesKerberos: Strengths and WeaknessesDerek CoxNo ratings yet
- Securing .NET Web Services with SSL: How to Protect “Data in Transit” between Client and Remote ServerFrom EverandSecuring .NET Web Services with SSL: How to Protect “Data in Transit” between Client and Remote ServerNo ratings yet
- Azure Security - AZ 500Document2 pagesAzure Security - AZ 500Gurdev SinghNo ratings yet
- 10.13.3.gurgaon OfficeDocument2 pages10.13.3.gurgaon OfficeGurdev SinghNo ratings yet
- RDP Remote DesktopDocument4 pagesRDP Remote DesktopGurdev SinghNo ratings yet
- Samba4 Configuration: (Root@dc1 ) # CD /optDocument9 pagesSamba4 Configuration: (Root@dc1 ) # CD /optGurdev SinghNo ratings yet
- SIGVERIFDocument5 pagesSIGVERIFKamal Deo PrasadNo ratings yet
- Real Estate Development 5Th Edition Principles and Process Full ChapterDocument22 pagesReal Estate Development 5Th Edition Principles and Process Full Chaptermary.jauregui841100% (54)
- Product Specification 803QDocument4 pagesProduct Specification 803QAlexandre SpNo ratings yet
- Knjiga 07Document578 pagesKnjiga 07laridzomicNo ratings yet
- Estate TaxDocument48 pagesEstate TaxBhosx Kim100% (1)
- Akropong Prosperity Statement A4Document2 pagesAkropong Prosperity Statement A4Transforming communities UgandaNo ratings yet
- Application of Epidemiology in CHNDocument72 pagesApplication of Epidemiology in CHNAnon Nimos100% (1)
- Insight in Psychiatry by Ivana MarkovDocument345 pagesInsight in Psychiatry by Ivana MarkovmalextomasNo ratings yet
- UNIT 2 Nutritional Requirement and Dietary Guidelines of NepalDocument13 pagesUNIT 2 Nutritional Requirement and Dietary Guidelines of NepalSwaichchha BasnetNo ratings yet
- Ibn - Arabi in The Eyes of The Great MujaddidDocument3 pagesIbn - Arabi in The Eyes of The Great Mujaddidapi-3699057No ratings yet
- Study Guide in The Sunnah of Womens Salah Power PointDocument35 pagesStudy Guide in The Sunnah of Womens Salah Power PointCrimson JacksonNo ratings yet
- Genuino Vs NLRCDocument2 pagesGenuino Vs NLRCJessy Francis100% (1)
- Dum 1111Document2 pagesDum 1111tkNo ratings yet
- Horngrens Accounting Global Edition 10th Edition Nobles Solutions ManualDocument35 pagesHorngrens Accounting Global Edition 10th Edition Nobles Solutions Manualserenadinhmzi100% (28)
- Bai Tap Tieng Anh Lop 8 Unit 12 Life On Other PlanetsDocument6 pagesBai Tap Tieng Anh Lop 8 Unit 12 Life On Other PlanetsThủy TrầnNo ratings yet
- Wonders First Grade Spelling Words Unit #'S 4-6Document1 pageWonders First Grade Spelling Words Unit #'S 4-6api-291341296No ratings yet
- Diversity Managment Unit5-1Document1 pageDiversity Managment Unit5-1Chirayu SinghNo ratings yet
- Comparison of WALA Ridge and Dental Arch Dimension PDFDocument7 pagesComparison of WALA Ridge and Dental Arch Dimension PDFJoshua StalinNo ratings yet
- Benedict Joseph Labre LitanyDocument3 pagesBenedict Joseph Labre Litanydonmage100% (2)
- İngilizcede Regular (Düzenli) Ve İrregular (Düzensiz) Kelimeler Zafer Hoca PDFDocument6 pagesİngilizcede Regular (Düzenli) Ve İrregular (Düzensiz) Kelimeler Zafer Hoca PDFZafer Hoca YdsNo ratings yet
- Smart Tab Android Users GuideDocument288 pagesSmart Tab Android Users Guidegautham2850% (2)
- QM ZG528 - L1Document26 pagesQM ZG528 - L1RamPrasathNo ratings yet
- QuarterlyBo 12081800 01739053 31122019 PDFDocument1 pageQuarterlyBo 12081800 01739053 31122019 PDFSangamesh Sangu0% (1)
- Operating Segments Comprehensive ProblemDocument2 pagesOperating Segments Comprehensive ProblemJazehl Joy ValdezNo ratings yet
- ODMP Hydrology and Water Resources Inception ReportDocument68 pagesODMP Hydrology and Water Resources Inception ReportAse JohannessenNo ratings yet
- 31 Samss 009Document8 pages31 Samss 009BHAVEESHNo ratings yet
- Trade and Other ReceivablesDocument21 pagesTrade and Other ReceivablesNoella Marie BaronNo ratings yet
- Kriteria Penilaian JuriDocument8 pagesKriteria Penilaian JuriMuhamad AmirulNo ratings yet
- Méndez Et Al., 2015Document12 pagesMéndez Et Al., 2015Martin MarchiNo ratings yet