Professional Documents
Culture Documents
Basic Data Compression Concepts: - Lossless - Lossy - Compression Ratio
Basic Data Compression Concepts: - Lossless - Lossy - Compression Ratio
Uploaded by
Harshit LalpuraOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Basic Data Compression Concepts: - Lossless - Lossy - Compression Ratio
Basic Data Compression Concepts: - Lossless - Lossy - Compression Ratio
Uploaded by
Harshit LalpuraCopyright:
Available Formats
1
CSE 521
Algorithms
Spring 2003
Entropy
Arithmetic Coding
CSE 521 - Arithmetic Coding - Spring 2003 2
Basic Data Compression Concepts
Encoder Decoder
compressed original
x y
x
Lossless compression
Also called entropy coding, reversible coding.
Lossy compression
Also called irreversible coding.
Compression ratio =
is number of bits in x.
x x =
x x =
y x
x
decompressed
CSE 521 - Arithmetic Coding - Spring 2003 3
Why Compress
Conserve storage space
Reduce time for transmission
Faster to encode, send, then decode than to send
the original
Progressive transmission
Some compression techniques allow us to send
the most important bits first so we can get a low
resolution version of some data before getting the
high fidelity version
Reduce computation
Use less data to achieve an approximate answer
CSE 521 - Arithmetic Coding - Spring 2003 4
Braille
System to read text by feeling raised dots on
paper (or on electronic displays). Invented in
1820s by Louis Braille, a French blind man.
a b c z
and the with mother
th gh ch
CSE 521 - Arithmetic Coding - Spring 2003 5
Braille Example
Clear text:
Call me Ishmael. Some years ago -- never mind how
long precisely -- having \\ little or no money in my purse,
and nothing particular to interest me on shore, \\ I thought
I would sail about a little and see the watery part of the
world. (238 characters)
Grade 2 Braille in ASCII.
,call me ,i\%mael4 ,``s ye$>$s ago -- n``e m9d h[ l;g
precisely -- hav+ \\ ll or no m``oy 9 my purse1 \& no?+
``picul$>$ 6 9t]e/ me on \%ore1 \\ ,i $?$``$|$ ,i wd sail
ab a ll \& see ! wat]y ``p ( ! \_w4 (203 characters)
Compression ratio = 238/203 = 1.17
CSE 521 - Arithmetic Coding - Spring 2003 6
Lossless Compression
Data is not lost - the original is really needed.
text compression
compression of computer binaries to fit on a floppy
Compression ratio typically no better than 4:1 for
lossless compression on many kinds of files.
Statistical Techniques
Huffman coding
Arithmetic coding
Golomb coding
Dictionary techniques
LZW, LZ77
Sequitur
Burrows-Wheeler Method
Standards - Morse code, Braille, Unix compress, gzip,
zip, bzip, GIF, JBIG, Lossless JPEG
2
CSE 521 - Arithmetic Coding - Spring 2003 7
Why is Data Compression Possible
Most data from nature has redundancy
There is more data than the actual information
contained in the data.
Squeezing out the excess data amounts to
compression.
However, unsqeezing out is necessary to be able
to figure out what the data means.
Information theory is needed to understand
the limits of compression and give clues on
how to compress well.
CSE 521 - Arithmetic Coding - Spring 2003 8
Information Theory
Developed by Shannon in the 1940s and 50s
Attempts to explain the limits of communication
using probability theory.
Example: Suppose English text is being sent
Suppose a t is received. Given English, the next
symbol being a z has very low probability, the
next symbol being a h has much higher probability.
Receiving a z has much more information in it than
receiving a h. We already knew it was more likely
we would receive an h.
CSE 521 - Arithmetic Coding - Spring 2003 9
0
1
2
3
4
5
6
7
0
.0
1
0
.0
8
0
.1
5
0
.2
2
0
.2
9
0
.3
6
0
.4
3
0
.5
0
.5
7
0
.6
4
0
.7
1
0
.7
8
0
.8
5
0
.9
2
0
.9
9
x
y
-l og(x)
First-order Information
Suppose we are given symbols {a
1
, a
2
, ... , a
m
}.
P(a
i
) = probability of symbol a
i
occurring in the
absence of any other information.
P(a
1
) + P(a
2
) + ... + P(a
m
) = 1
inf(a
i
) = -log
2
P(a
i
) bits is the information of a
i
in
bits.
CSE 521 - Arithmetic Coding - Spring 2003 10
Example
{a, b, c} with P(a) = 1/8, P(b) = 1/4, P(c) = 5/8
inf(a) = -log
2
(1/8) = 3
inf(b) = -log
2
(1/4) = 2
inf(c) = -log
2
(5/8) = .678
Receiving an a has more information than
receiving a b or c.
CSE 521 - Arithmetic Coding - Spring 2003 11
First Order Entropy
The first order entropy is defined for a probability
distribution over symbols {a
1
, a
2
, ... , a
m
}.
H is the average number of bits required to code up a
symbol, given all we know is the probability distribution
of the symbols.
H is the Shannon lower bound on the average number of
bits to code a symbol in this source model.
Stronger models of entropy include context. Well talk
about this later.
)) ( ( log ) (
2
1
i
m
i
i
a P a P H
=
=
CSE 521 - Arithmetic Coding - Spring 2003 12
Entropy Examples
{a, b, c} with a 1/8, b 1/4, c 5/8.
H = 1/8 *3 + 1/4 *2 + 5/8* .678 = 1.3 bits/symbol
{a, b, c} with a 1/3, b 1/3, c 1/3. (worst case)
H = -3* (1/3)*log
2
(1/3) = 1.6 bits/symbol
{a, b, c} with a 1, b 0, c 0 (best case)
H = -1*log
2
(1) = 0
Note that the standard coding of 3 symbols
takes 2 bits.
3
CSE 521 - Arithmetic Coding - Spring 2003 13
Entropy Curve
Suppose we have two symbols with probabilities
x and 1-x, respectively.
0
0.2
0.4
0.6
0.8
1
1.2
0
0
.1
0
.2
0
.3
0
.4
0
.5
0
.6
0
.7
0
.8
0
.91
probability of first symbol
e
n
t
r
o
p
y
-(x log x + (1-x)log(1-x))
maximum entropy at .5
CSE 521 - Arithmetic Coding - Spring 2003 14
Reals in Binary
Any real number x in the interval [0,1) can be
represented in binary as .b
1
b
2
... where b
i
is a
bit.
0
1
x
0 1 0 1 ....
binary representation
CSE 521 - Arithmetic Coding - Spring 2003 15
First Conversion
L := 0; R :=1; i := 1
while x > L *
if x < (L+R)/2 then b
i
:= 0 ; R := (L+R)/2;
if x > (L+R)/2 then b
i
:= 1 ; L := (L+R)/2;
i := i + 1
end{while}
b
j
:= 0 for all j > i
* Invariant: x is always in the interval [L,R)
CSE 521 - Arithmetic Coding - Spring 2003 16
Conversion using Scaling
Always scale the interval to unit size, but x must be
changed as part of the scaling.
0
1
x
0 1 0 1 ....
CSE 521 - Arithmetic Coding - Spring 2003 17
Binary Conversion with Scaling
y := x; i := 0
while y > 0 *
i := i + 1;
if y < 1/2 then b
i
:= 0; y := 2y;
if y > 1/2 then b
i
:= 1; y := 2y 1;
end{while}
b
j
:= 0 for all j > i + 1
* Invariant: x = .b
1
b
2
... b
i
+ y/2
i
CSE 521 - Arithmetic Coding - Spring 2003 18
Proof of the Invariant
Initially x = 0 + y/2
0
Assume x =.b
1
b
2
... b
i
+ y/2
i
Case 1. y < 1/2. b
i+1
= 0 and y = 2y
.b
1
b
2
... b
i
b
i+1
+ y/2
i+1
= .b
1
b
2
... b
i
0+ 2y/2
i+1
= .b
1
b
2
... b
i
+ y/2
i
= x
Case 2. y > 1/2. b
i+1
= 1 and y = 2y 1
.b
1
b
2
... b
i
b
i+1
+ y/2
i+1
= .b
1
b
2
... b
i
1+ (2y-1)/2
i+1
= .b
1
b
2
... b
i
+1/2
i+1
+ 2y/2
i+1
-1/2
i+1
= .b
1
b
2
... b
i
+ y/2
i
= x
4
CSE 521 - Arithmetic Coding - Spring 2003 19
Arithmetic Coding
Basic idea in arithmetic coding:
represent each string x of length n by a unique
interval [L,R) in [0,1).
The width r-l of the interval [L,R) represents the
probability of x occurring.
The interval [L,R) can itself be represented by any
number, called a tag, within the half open interval.
The k significant bits of the tag .t
1
t
2
t
3
... is the code of
x. That is, . .t
1
t
2
t
3
...t
k
000... is in the interval [L,R).
CSE 521 - Arithmetic Coding - Spring 2003 20
Example of Arithmetic Coding (1)
a
b
bb
0
1
bba
15/27
19/27
.100011100...
.101101000...
tag = 17/27 = .101000010...
code = 101
1. tag must be in the half open interval.
2. tag can be chosen to be (L+R)/2.
3. code is the significant bits of the tag.
1/3
2/3
CSE 521 - Arithmetic Coding - Spring 2003 21
Some Tags are Better than Others
a
b
ba
0
1
bab
11/27
15/27
.011010000...
.100011100...
1/3
2/3
Using tag = (L+R)/2
tag = 13/27 = .011110110...
code = 0111
Alternative tag = 14/37 = .100001001...
code = 1
CSE 521 - Arithmetic Coding - Spring 2003 22
Example of Codes
P(a) = 1/3, P(b) = 2/3.
a
b
aa
ab
ba
bb
aaa
aab
aba
abb
baa
bab
bba
bbb
0
1
0/27
1/27
3/27
9/27
5/27
11/27
15/27
19/27
27/27
.000010010...
.000000000...
.000111000...
.001011110...
.010101010...
.011010000...
.100011100...
.101101000...
.111111111...
.000001001... 0 aaa
.000100110... 0001 aab
.001001100... 001 aba
.010000101... 01 abb
.010111110... 01011 baa
tag = (L+R)/2 code
.011110111... 0111 bab
.101000010... 101 bba
.110110100... 11 bbb
.95 bits/symbol
.92 entropy lower bound
CSE 521 - Arithmetic Coding - Spring 2003 23
Code Generation from Tag
If binary tag is .t
1
t
2
t
3
... = (L+R)/2 in [L,R) then
we want to choose k to form the code t
1
t
2
...t
k
.
Short code:
choose k to be as small as possible so that
L < .t
1
t
2
...t
k
000... < R.
Guaranteed code:
choose
L < .t
1
t
2
...t
k
b
1
b
2
b
3
... < R for any bits b
1
b
2
b
3
...
for fixed length strings provides a good prefix code.
example: [.000000000..., .000010010...), tag = .000001001...
Short code: 0
Guaranteed code: 000001
(
1 L)) (1/(R log k
2
+ =
CSE 521 - Arithmetic Coding - Spring 2003 24
Guaranteed Code Example
P(a) = 1/3, P(b) = 2/3.
a
b
aa
ab
ba
bb
aaa
aab
aba
abb
baa
bab
bba
bbb
0
1
0/27
1/27
3/27
9/27
5/27
11/27
15/27
19/27
27/27
.000001001... 0 0000 aaa
.000100110... 0001 0001 aab
.001001100... 001 001 aba
.010000101... 01 0100 abb
.010111110... 01011 01011 baa
tag = (L+R)/2
.011110111... 0111 0111 bab
.101000010... 101 101 bba
.110110100... 11 11 bbb
short
code
Prefix
code
5
CSE 521 - Arithmetic Coding - Spring 2003 25
Arithmetic Coding Algorithm
P(a
1
), P(a
2
), , P(a
m
)
C(a
i
) = P(a
1
) + P(a
2
) + + P(a
i-1
)
Encode x
1
x
2
...x
n
Initialize L := 0 and R:= 1;
for i = 1 to n do
W := R - L;
L := L + W * C(x
i
);
R := L + W * P(x
i
);
t := (L+R)/2;
choose code for the tag
CSE 521 - Arithmetic Coding - Spring 2003 26
Arithmetic Coding Example
P(a) = 1/4, P(b) = 1/2, P(c) = 1/4
C(a) = 0, C(b) = 1/4, C(c) = 3/4
abca
symbol W L R
0 1
a 1 0 1/4
b 1/4 1/16 3/16
c 1/8 5/32 6/32
a 1/32 5/32 21/128
tag = (5/32 + 21/128)/2 = 41/256 = .001010010...
L = .001010000...
R = .001010100...
code = 00101
prefix code = 00101001
W := R - L;
L := L + W C(x);
R := L + W P(x)
CSE 521 - Arithmetic Coding - Spring 2003 27
Decoding (1)
Assume the length is known to be 3.
0001 which converts to the tag .0001000...
a
b
0
1
.0001000... output a
CSE 521 - Arithmetic Coding - Spring 2003 28
Decoding (2)
Assume the length is known to be 3.
0001 which converts to the tag .0001000...
a
b
0
1
aa
ab
.0001000... output a
CSE 521 - Arithmetic Coding - Spring 2003 29
Decoding (3)
Assume the length is known to be 3.
0001 which converts to the tag .0001000...
a
b
0
1
aa
ab
aab .0001000... output b
CSE 521 - Arithmetic Coding - Spring 2003 30
Arithmetic Decoding Algorithm
P(a
1
), P(a
2
), , P(a
m
)
C(a
i
) = P(a
1
) + P(a
2
) + + P(a
i-1
)
Decode b
1
b
2
...b
m
, number of symbols is n.
Initialize L := 0 and R := 1;
t := .b
1
b
2
...b
m
000...
for i = 1 to n do
W := R - L;
find j such that L + W * C(a
j
) < t < L + W * (C(a
j
)+P(a
j
))
output a
j
;
L := L + W * C(a
j
);
R := L + W * P(a
j
);
6
CSE 521 - Arithmetic Coding - Spring 2003 31
Decoding Example
P(a) = 1/4, P(b) = 1/2, P(c) = 1/4
C(a) = 0, C(b) = 1/4, C(c) = 3/4
00101
tag = .00101000... = 5/32
W L R output
0 1
1 0 1/4 a
1/4 1/16 3/16 b
1/8 5/32 6/32 c
1/32 5/32 21/128 a
CSE 521 - Arithmetic Coding - Spring 2003 32
Decoding Issues
There are two ways for the decoder to know
when to stop decoding.
1. Transmit the length of the string
2. Transmit a unique end of string symbol
CSE 521 - Arithmetic Coding - Spring 2003 33
More Issues
Avoiding real arithmetic and scaling
Context
Adaptive
Comparison with Huffman coding
CSE 521 - Arithmetic Coding - Spring 2003 34
Scaling
Scaling:
By scaling we can keep L and R in a reasonable
range of values so that W = R L does not
underflow.
The code can be produced progressively, not at
the end.
Complicates decoding some.
CSE 521 - Arithmetic Coding - Spring 2003 35
Scaling Principle
Lower half
If [L,R) is contained in [0,.5) then
L := 2L; R := 2R
output 0, followed by C 1s
C := 0.
Upper half
If [L,R) is contained in [.5,1) then
L := 2L 1, R := 2R - 1
output 1, followed by C 0s
C := 0
Middle Half
If [L,R) is contained in [.25,.75) then
L := 2L .5, R := 2R -.5
C := C + 1.
C keeps track of the
number of bits needed
when we learn which
side of 1/2 the tag must
be in.
CSE 521 - Arithmetic Coding - Spring 2003 36
Example
baa
a
b
0
1
1/3
2/3
L = 1/3 R = 3/3
C = 0
7
CSE 521 - Arithmetic Coding - Spring 2003 37
Example
baa
a
b
0
1
1/3
2/3
Scale middle half
L = 1/3 R = 3/3
L = 3/9 R = 5/9
C = 0
CSE 521 - Arithmetic Coding - Spring 2003 38
Example
baa
a
b
0
1
1/3
2/3
L = 3/9 R = 5/9
L = 3/18 R = 11/18
C = 1
ba
CSE 521 - Arithmetic Coding - Spring 2003 39
Example
baa
a
b
0
1
1/3
2/3
L = 3/18 R = 11/18
L = 9/54 R = 17/54
C = 1
ba
baa
Scale lower half
CSE 521 - Arithmetic Coding - Spring 2003 40
Example
baa 01
a
b
0
1
1/3
2/3
L = 9/54 R = 17/54
L = 18/54 R = 34/54
C = 0
ba
baa
CSE 521 - Arithmetic Coding - Spring 2003 41
Example
baa 011
a
b
0
1
1/3
2/3
L = 9/54 R = 17/54
L = 18/54 R = 34/54
C = 0
ba
baa
.0101
.1000 = tag
.1010
In end L < < R, choose tag to be 1/2
CSE 521 - Arithmetic Coding - Spring 2003 42
Integer Implementation
m bit integers
Represent 0 with 0000 (m times)
Represent 1 with 1111 (m times)
Probabilities represented by frequencies
n
i
is the number of times that symbol a
i
occurs
C
i
= n
1
+ n
2
+ + n
i-1
N = n
1
+ n
2
+ + n
m
L' : L
1
N
C W
L : R
N
C W
L : L'
1 L R : W
1 i
i
=
+ =
(
+ =
+ =
+
Coding the i-th symbol using
integer calculations.
Must use scaling!
8
CSE 521 - Arithmetic Coding - Spring 2003 43
Context
Consider 1 symbol context.
Example: 3 contexts.
prev
next
a b c
a .4 .2 .4
b .1 .8 .1
c .25 .25 .5
CSE 521 - Arithmetic Coding - Spring 2003 44
Example with Scaling
acc
a b c
a .4 .2 .4
b .1 .8 .1
c .25 .25 .5
prev
next
a
Equally Likely model
ac
1/3
1/3
1/3
0 10 1
a model
c model
.4
.2
.4
.25
.25
.5
acc
0
1/3
0
2/3
2/5
2/3
3/10
5/6
17/30
5/6
first half middle half second half
2/3
2/15
Code = 0101
CSE 521 - Arithmetic Coding - Spring 2003 45
Arithmetic Coding with Context
Maintain the probabilities for each context.
For the first symbol use the equal probability
model
For each successive symbol use the model
for the previous symbol.
CSE 521 - Arithmetic Coding - Spring 2003 46
Adaptation
Simple solution Equally Probable Model.
Initially all symbols have frequency 1.
After symbol x is coded, increment its frequency
by 1
Use the new model for coding the next symbol
Example in alphabet a,b,c,d
a a b a a c
a 1 2 3 3 4 5 5
b 1 1 1 2 2 2 2
c 1 1 1 1 1 1 2
d 1 1 1 1 1 1 1
After aabaac is encoded
The probability model is
a 5/10 b 2/10
c 2/10 d 1/10
CSE 521 - Arithmetic Coding - Spring 2003 47
Zero Frequency Problem
How do we weight symbols that have not occurred yet.
Equal weights? Not so good with many symbols
Escape symbol, but what should its weight be?
When a new symbol is encountered send the <esc>, followed
by the symbol in the equally probable model. (Both encoded
arithmetically.)
a a b a a c
a 0 1 2 2 3 4 4
b 0 0 0 1 1 1 1
c 0 0 0 0 0 0 1
d 0 0 0 0 0 0 0
<esc> 1 1 1 1 1 1 1
After aabaac is encoded
The probability model is
a 4/7 b 1/7
c 1/7 d 0
<esc> 1/7
CSE 521 - Arithmetic Coding - Spring 2003 48
PPM
Prediction with Partial Matching
Cleary and Witten (1984)
State of the art arithmetic coder
Arbitrary order context
The context chosen is one that does a good
prediction given the past
Adaptive
Example
Context the does not predict the next symbol a
well. Move to the context he which does.
9
CSE 521 - Arithmetic Coding - Spring 2003 49
Arithmetic vs. Huffman
Both compress very well. For m symbol grouping.
Huffman is within 1/m of entropy.
Arithmetic is within 2/m of entropy.
Context
Huffman needs a tree for every context.
Arithmetic needs a small table of frequencies for every
context.
Adaptation
Huffman has an elaborate adaptive algorithm
Arithmetic has a simple adaptive mechanism.
Bottom Line Arithmetic is more flexible than
Huffman.
CSE 521 - Arithmetic Coding - Spring 2003 50
Applications of Arithmetic Coding
JPEG 2000
Image compression
Wavelet transform
Bit-planes of the transformed image is adaptively
arithmetic coded.
Contexts relate to structure of wavelet coefficients
JBIG
Binary image compression
Context is about 10 nearby pixels already coded.
You might also like
- Arithmetic CodingDocument20 pagesArithmetic CodingperhackerNo ratings yet
- EC 2214: Coding & Data Compression: Vishwakarma Institute of TechnologyDocument35 pagesEC 2214: Coding & Data Compression: Vishwakarma Institute of TechnologyAnuj BodheNo ratings yet
- Image Compression (Chapter 8) : CS474/674 - Prof. BebisDocument128 pagesImage Compression (Chapter 8) : CS474/674 - Prof. Bebissrc0108No ratings yet
- Chapter - 7 ICGDocument27 pagesChapter - 7 ICGsachinkj143143No ratings yet
- Compression For Sending and Storing Information: Text, Audio, Images, VideosDocument28 pagesCompression For Sending and Storing Information: Text, Audio, Images, VideosPradeep RamuNo ratings yet
- Huffman CodingDocument6 pagesHuffman CodingjitensoftNo ratings yet
- Why Needed?: Without Compression, These Applications Would Not Be FeasibleDocument11 pagesWhy Needed?: Without Compression, These Applications Would Not Be Feasiblesmile00972No ratings yet
- Intermediate Code GenerationDocument23 pagesIntermediate Code Generationতানভীর তাঈনNo ratings yet
- Raptor Codes: Amin ShokrollahiDocument1 pageRaptor Codes: Amin ShokrollahiRajesh HarikrishnanNo ratings yet
- Full Adder VHDLDocument52 pagesFull Adder VHDLTushar JainNo ratings yet
- Design Example - A Division-By-Constant Combinational CircuitDocument4 pagesDesign Example - A Division-By-Constant Combinational CircuitPhuc HoangNo ratings yet
- Lab 2Document4 pagesLab 2Risinu WijesingheNo ratings yet
- Slides 08 6 4Document6 pagesSlides 08 6 4mohammed229No ratings yet
- Image Compression (Chapter 8) : CS474/674 - Prof. BebisDocument75 pagesImage Compression (Chapter 8) : CS474/674 - Prof. BebisKoushik SupercalifragilisticNo ratings yet
- 1 - Primitive Data Types (2019) - 2Document50 pages1 - Primitive Data Types (2019) - 2Mathew HethrewNo ratings yet
- Useful PDFDocument16 pagesUseful PDFbharathiNo ratings yet
- Huffman Coding: Vida MovahediDocument24 pagesHuffman Coding: Vida MovahediSushant ChopraNo ratings yet
- CS246 Hw1Document5 pagesCS246 Hw1sudh123456No ratings yet
- Simple Data Types in C: Alan L. Cox Alc@rice - EduDocument41 pagesSimple Data Types in C: Alan L. Cox Alc@rice - EduNiranjana KrishnanNo ratings yet
- TCS 502 AssignmentDocument12 pagesTCS 502 Assignmentapi-381239125% (8)
- CryptoDocument15 pagesCryptoNihar Ranjan PandaNo ratings yet
- Programming in QBasicDocument28 pagesProgramming in QBasicSalisu Murtala100% (2)
- Image CompressionDocument133 pagesImage CompressionDeebika KaliyaperumalNo ratings yet
- The Role of Forward Error Correction in Fiber-Optic SystemDocument42 pagesThe Role of Forward Error Correction in Fiber-Optic System17585No ratings yet
- Rohini 33759187478Document6 pagesRohini 33759187478justinejoyplayboyNo ratings yet
- Lecture 8-PrintDocument24 pagesLecture 8-Printraj singhNo ratings yet
- CSC 2426 ReportDocument3 pagesCSC 2426 ReportnekriachvvNo ratings yet
- Chapter 1: Digital Systems and Binary NumbersDocument24 pagesChapter 1: Digital Systems and Binary Numbers李亞竹No ratings yet
- Lecture 3: Linearity TestingDocument7 pagesLecture 3: Linearity TestingSushmita ChoudharyNo ratings yet
- NYU POLY CS2134 HW 1aDocument5 pagesNYU POLY CS2134 HW 1aMehul PatelNo ratings yet
- Crypto TPDocument13 pagesCrypto TPSk SharmaNo ratings yet
- Cryptography Engineering: CSIC30040 Spring 2023 Lecture 6Document218 pagesCryptography Engineering: CSIC30040 Spring 2023 Lecture 6王皓平No ratings yet
- Lecture 3: Introduction To Lexical Analysis: Front-End Back-EndDocument12 pagesLecture 3: Introduction To Lexical Analysis: Front-End Back-EndAayush KaushalNo ratings yet
- Intermediate Code Generation 1Document56 pagesIntermediate Code Generation 1shashwat2010No ratings yet
- Correctedreport EXP 3Document12 pagesCorrectedreport EXP 3SuneelRuttalaNo ratings yet
- Input Source Encoder Channel Encoder Binary InterfaceDocument29 pagesInput Source Encoder Channel Encoder Binary InterfaceMuhammadwaqasnaseemNo ratings yet
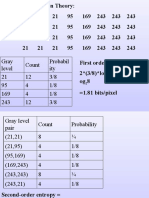
- Gray Level Count Probabil Ity 21 12 3/8 95 4 1/8 169 4 1/8 243 12 3/8Document51 pagesGray Level Count Probabil Ity 21 12 3/8 95 4 1/8 169 4 1/8 243 12 3/8kamnakhannaNo ratings yet
- Tornado Codes and Luby Transform Codes PDFDocument12 pagesTornado Codes and Luby Transform Codes PDFpathmakerpkNo ratings yet
- Cryptography1 MKG v2Document47 pagesCryptography1 MKG v2Sreevalli ChowdaryNo ratings yet
- Source Coding OmpressionDocument34 pagesSource Coding Ompression최규범No ratings yet
- ADA Lec 001-005Document86 pagesADA Lec 001-005Hikmatullah SaqibNo ratings yet
- Concatenated Codes (CH 15)Document21 pagesConcatenated Codes (CH 15)vensri9994563No ratings yet
- Recursion: Breaking Down Problems Into Solvable SubproblemsDocument26 pagesRecursion: Breaking Down Problems Into Solvable Subproblemsalbert_kerrNo ratings yet
- 1 - Coding and DecodingDocument6 pages1 - Coding and DecodingDonika MarkandeNo ratings yet
- Assignment - Digital CommunicationDocument6 pagesAssignment - Digital CommunicationnetsanetNo ratings yet
- Chapter2 - Machine Instructions and ProgramsDocument85 pagesChapter2 - Machine Instructions and ProgramsBala KrishnaNo ratings yet
- 1 Introduction To Linear Block CodesDocument13 pages1 Introduction To Linear Block CodesRini KamilNo ratings yet
- Lemp El Ziv CompressionDocument6 pagesLemp El Ziv CompressionssfofoNo ratings yet
- ECE 368 A Tour by Example of Non-Trivial Circuit Design and VHDL DescriptionDocument23 pagesECE 368 A Tour by Example of Non-Trivial Circuit Design and VHDL DescriptionAnand ChaudharyNo ratings yet
- Compression IIDocument51 pagesCompression IIJagadeesh NaniNo ratings yet
- Set A Answer KeyDocument11 pagesSet A Answer Keymm8805No ratings yet
- Convolutional Codes Turbo Codes LDPC CodesDocument49 pagesConvolutional Codes Turbo Codes LDPC CodesveerutheprinceNo ratings yet
- CHAPTER 03 - Cyclic CodesDocument30 pagesCHAPTER 03 - Cyclic CodessuthasenthilNo ratings yet
- InfThe L2Document15 pagesInfThe L2Harshit LalpuraNo ratings yet
- Huffman CodingDocument6 pagesHuffman CodingjitensoftNo ratings yet
- Holiday Homes SBIDocument4 pagesHoliday Homes SBIHarshit LalpuraNo ratings yet
- 008 - Be Sem7winterexamination 2013 PDFDocument5 pages008 - Be Sem7winterexamination 2013 PDFHarshit LalpuraNo ratings yet
- IT Foundation Practice Assignments - PF V1Document5 pagesIT Foundation Practice Assignments - PF V1Sai Ram RajulapatiNo ratings yet
- SQL-2 SelectDocument24 pagesSQL-2 SelectAbdul RehmanNo ratings yet
- Low Level DesignDocument12 pagesLow Level Designhedimit846No ratings yet
- Dbms 3Document36 pagesDbms 3zatharoxNo ratings yet
- Data Structures and AlgorithmsDocument46 pagesData Structures and AlgorithmsMaria CaneteNo ratings yet
- CH 1Document31 pagesCH 1vijay vidyalayaNo ratings yet
- Exercise UI CRM2006S Part3Document40 pagesExercise UI CRM2006S Part3Venki KasaNo ratings yet
- Automation of Accounting Processes Impact of Artificial IntelligenceDocument7 pagesAutomation of Accounting Processes Impact of Artificial IntelligenceLakesh kumar padhyNo ratings yet
- Map 1Document9 pagesMap 11012361No ratings yet
- LogDocument322 pagesLogDian FadilaNo ratings yet
- CbgapiDocument32 pagesCbgapiPrettypure TacurdaNo ratings yet
- C++20 FeaturesDocument5 pagesC++20 FeaturesFifthtoe BizwareNo ratings yet
- Experiment 12Document13 pagesExperiment 12kapil singhNo ratings yet
- Tutorial4 - Wizard - Multiple Tables and Parameterized Queries - 2022Document55 pagesTutorial4 - Wizard - Multiple Tables and Parameterized Queries - 2022Crentsil KwayieNo ratings yet
- Week 3 - 10Document10 pagesWeek 3 - 10benjaminfranklinczNo ratings yet
- Building An RDMA-Capable Application With IB Verbs: 1 BasicsDocument12 pagesBuilding An RDMA-Capable Application With IB Verbs: 1 BasicsGwisang ChoiNo ratings yet
- Xpath TutorialDocument60 pagesXpath Tutorialashokmvanjare100% (1)
- Assignment 3 Usmans COALDocument4 pagesAssignment 3 Usmans COALAbdullah MuftyNo ratings yet
- Formal Specification of Computing SystemsDocument30 pagesFormal Specification of Computing SystemsChuka OkoyeNo ratings yet
- 25 Deadlock Solutions PDFDocument53 pages25 Deadlock Solutions PDFHari HaranNo ratings yet
- Rajasthan Technical University, Kota: Department of Computer Science EngineeringDocument19 pagesRajasthan Technical University, Kota: Department of Computer Science EngineeringlucasNo ratings yet
- Python Syllabus 2019 PDF DownloadDocument8 pagesPython Syllabus 2019 PDF DownloadMohammed AbraruddinNo ratings yet
- Python Interview QuestionsDocument54 pagesPython Interview Questionsdorian451No ratings yet
- Chapter 5 SQL PDFDocument16 pagesChapter 5 SQL PDFameni souissiNo ratings yet
- 9-6 Working With Java Service WrapperDocument18 pages9-6 Working With Java Service WrapperHarish BandiNo ratings yet
- Front-End Architect Resume Profile - Hire IT PeopleDocument6 pagesFront-End Architect Resume Profile - Hire IT PeoplebheemsinhNo ratings yet
- Applet and BC User PropertyDocument7 pagesApplet and BC User PropertyRishabh GoyalNo ratings yet
- Models en AtpDocument169 pagesModels en AtpSantiago Morillo100% (2)
- Adobe Media Encoder LogDocument14 pagesAdobe Media Encoder LogTermo TecnicoNo ratings yet
- Polyspace Bug Finder Server UgDocument384 pagesPolyspace Bug Finder Server UgLộc HuỳnhNo ratings yet