Professional Documents
Culture Documents
0 ratings0% found this document useful (0 votes)
42 viewsSchool of Information Systems IS302: Lab Exercise: March 2012
School of Information Systems IS302: Lab Exercise: March 2012
Uploaded by
Dalibor ŽivićThis document provides instructions for a lab exercise on password security and firewall configuration. It describes:
1) Setting up two virtual machines, IST Windows XP and IST Linux, for the exercises.
2) Performing password cracking on Windows and Linux passwords to demonstrate password security issues.
3) Configuring a firewall on IST Linux using UFW and observing intrusion detection using Snort.
Copyright:
© All Rights Reserved
Available Formats
Download as DOC, PDF, TXT or read online from Scribd
You might also like
- 1607806691505tips To Unlock Siemens S7 200 PLC CPUDocument14 pages1607806691505tips To Unlock Siemens S7 200 PLC CPUMohamed lamine AssaslaNo ratings yet
- Database Systems A Practical Approach To Design ImDocument9 pagesDatabase Systems A Practical Approach To Design ImSatheeshRajuKalidhindi0% (1)
- Hack The WorldDocument17 pagesHack The Worldjuli_nazNo ratings yet
- Actas3 19Document7 pagesActas3 19Muhammad HumaidiNo ratings yet
- Cisco PIX Firewalls - FAQsDocument11 pagesCisco PIX Firewalls - FAQsbiddumehtaNo ratings yet
- Installation InstructionsDocument33 pagesInstallation Instructionsdreamboy87No ratings yet
- Lab7 InstructionDocument10 pagesLab7 Instructionzargham.razaNo ratings yet
- What Is Windows Vista?Document7 pagesWhat Is Windows Vista?Maria MocanuNo ratings yet
- Penetrating Windows 8 With Syringe UtiliDocument5 pagesPenetrating Windows 8 With Syringe UtiliAGBADAN Yao EricNo ratings yet
- Using Cadence NC-Verilog or Verilog-XL Simulator: Electronic Design Automation (EDA) Tools at NPUDocument6 pagesUsing Cadence NC-Verilog or Verilog-XL Simulator: Electronic Design Automation (EDA) Tools at NPUApoorva BhattNo ratings yet
- Simple VB Script VirusesDocument24 pagesSimple VB Script VirusesAbdinasir Mohamed AddowNo ratings yet
- 7Document7 pages7Benoit RenaudNo ratings yet
- Pentest LinuxDocument17 pagesPentest LinuxDragueur CharmeurNo ratings yet
- A Seminar: GNIT Girls Institute of TechnologyDocument24 pagesA Seminar: GNIT Girls Institute of Technologygolaaa100% (1)
- GNS3 NotesDocument3 pagesGNS3 NotesBidhan HalderNo ratings yet
- 49 & 99 Powerful Computer Tricks - Top 50+ Computer Hacks and TricksDocument96 pages49 & 99 Powerful Computer Tricks - Top 50+ Computer Hacks and TricksGajab HeisterNo ratings yet
- Start Up and Shut Down A Computer: Inside This ResourceDocument15 pagesStart Up and Shut Down A Computer: Inside This ResourcePriyanka SharmaNo ratings yet
- Hacking - Wep Cracking - Ultimate Guide (Video)Document3 pagesHacking - Wep Cracking - Ultimate Guide (Video)Adnan Sohail100% (1)
- Operating Systems Lab 1Document6 pagesOperating Systems Lab 1medo_ali5050No ratings yet
- Computer Fund Part II Lesson 01Document25 pagesComputer Fund Part II Lesson 01Annabelle Rigat de LeonNo ratings yet
- 19Document72 pages19Mohamed YounisNo ratings yet
- Home Automation Using Arduino Wifi Module Esp8266Document11 pagesHome Automation Using Arduino Wifi Module Esp8266Dr. M. Thillai Rani Asst Prof ECENo ratings yet
- Practica BackdoorDocument6 pagesPractica BackdoorLuis Alberto GpNo ratings yet
- Windows and InternetDocument8 pagesWindows and InternetAlex LeeNo ratings yet
- SMBConfiguration (3) ) )Document4 pagesSMBConfiguration (3) ) )Kurem Rubén MayénNo ratings yet
- 10 Super Cool Notepad TricksDocument11 pages10 Super Cool Notepad TricksJovenil BacatanNo ratings yet
- Lab 4 Worksheet: Deploying ApplicationsDocument17 pagesLab 4 Worksheet: Deploying ApplicationsShivamChadhaNo ratings yet
- Openswan Installation and Configuration TutorialDocument5 pagesOpenswan Installation and Configuration TutorialsaulparadaNo ratings yet
- Task 1:: Run The Vmware Workstation and Click On Create A New Virtual Machine OptionDocument24 pagesTask 1:: Run The Vmware Workstation and Click On Create A New Virtual Machine OptionAkshay Kumar TapariaNo ratings yet
- Lab - Using Wireshark To View Network TrafficDocument10 pagesLab - Using Wireshark To View Network TrafficEdy CrackmasterNo ratings yet
- VaccineDocument23 pagesVaccineshayalaNo ratings yet
- Resetting Passwords BfsDocument3 pagesResetting Passwords BfsjudazNo ratings yet
- Anti Forensics GuideDocument9 pagesAnti Forensics GuideDelin BardhiNo ratings yet
- How To Crack WEP - SpoonfedDocument13 pagesHow To Crack WEP - SpoonfedArimatéia FigueredoNo ratings yet
- Secrets Hidden in Windows XPDocument6 pagesSecrets Hidden in Windows XPMihai ParaschivNo ratings yet
- How To Make Virus With Notepad (Dangerous Scripts)Document8 pagesHow To Make Virus With Notepad (Dangerous Scripts)bambamNo ratings yet
- Installation Guide: Symantec Endpoint Protection Symantec Management AgentDocument7 pagesInstallation Guide: Symantec Endpoint Protection Symantec Management AgentJufri JumanNo ratings yet
- Microsoft Security Compliance Manager (SCM) Release Notes: Version HistoryDocument3 pagesMicrosoft Security Compliance Manager (SCM) Release Notes: Version HistorySalman AslamNo ratings yet
- Installing Using VMDocument12 pagesInstalling Using VMsaz gaxNo ratings yet
- ATL Education Foundation Information Security TrainingDocument35 pagesATL Education Foundation Information Security TrainingATL Education FoundationNo ratings yet
- Lab Setup Instructions SEC560 v04Document15 pagesLab Setup Instructions SEC560 v04Edward StarkNo ratings yet
- Remove Password From A Protected Excel Worksheet - The Most Authoritative Technology BlogDocument8 pagesRemove Password From A Protected Excel Worksheet - The Most Authoritative Technology Bloglaiping_lumNo ratings yet
- Icf 7 Module Second QuarterDocument24 pagesIcf 7 Module Second QuarterKazandra Cassidy Garcia100% (1)
- Windows Run CommandsDocument6 pagesWindows Run Commandsboy2959No ratings yet
- SabayonLinux Extradoc Rev.ADocument3 pagesSabayonLinux Extradoc Rev.AayranayranNo ratings yet
- CSEC630 Lab2 - IDS Revised 20110614Document18 pagesCSEC630 Lab2 - IDS Revised 20110614acg49100% (1)
- Wemos ESP32 Lolin32 Board BOOK ENGLISHDocument22 pagesWemos ESP32 Lolin32 Board BOOK ENGLISHDima KnyaNo ratings yet
- Windows OS Help ExerciseDocument3 pagesWindows OS Help ExercisejesuschrististhemanNo ratings yet
- Openvpn TomatoDocument5 pagesOpenvpn Tomatoarsh275No ratings yet
- Re: What's The Difference Between Safe Mode and Selective StartupDocument11 pagesRe: What's The Difference Between Safe Mode and Selective StartupYogesh2323No ratings yet
- PING Howto PDFDocument42 pagesPING Howto PDFbehessNo ratings yet
- LearningMaterial ICT4 v6 0 Week11Document10 pagesLearningMaterial ICT4 v6 0 Week11MN IHNo ratings yet
- Nokia n900 Pwnphone ManualDocument9 pagesNokia n900 Pwnphone ManualFer ContoNo ratings yet
- How To Bypass PIN and Password Locks in Android?: What Do I Need To Know?Document7 pagesHow To Bypass PIN and Password Locks in Android?: What Do I Need To Know?ahmadkamalNo ratings yet
- Networking: Ipconfig Ping FC CHKDSK Net AccountsDocument27 pagesNetworking: Ipconfig Ping FC CHKDSK Net Accountsshivsharma330No ratings yet
- Esp 32 Universal With Display Board Getting Started 2.4 InchDocument23 pagesEsp 32 Universal With Display Board Getting Started 2.4 Inchben.altenberg44No ratings yet
- Stopping Unneeded Startup Services and Making XP Boot FasterDocument21 pagesStopping Unneeded Startup Services and Making XP Boot Fastershan99960No ratings yet
- Esp8266 V10Document22 pagesEsp8266 V10lalonaderNo ratings yet
- Wireless and Mobile Hacking and Sniffing TechniquesFrom EverandWireless and Mobile Hacking and Sniffing TechniquesNo ratings yet
- Vulnerability Assessment ServicesDocument2 pagesVulnerability Assessment ServicesDalibor Živić0% (1)
- BMW CenovnikDocument4 pagesBMW CenovnikDalibor ŽivićNo ratings yet
- Entrepreneur SmartTips Guide Business Plan Step by Step Guide PDFDocument10 pagesEntrepreneur SmartTips Guide Business Plan Step by Step Guide PDFDalibor Živić100% (1)
- Server Confere Server - Conference - Registrationnce Registration ListDocument11 pagesServer Confere Server - Conference - Registrationnce Registration ListDalibor ŽivićNo ratings yet
- Booklet German Vol1 PDFDocument20 pagesBooklet German Vol1 PDFDalibor Živić100% (2)
- Learning Theory PDFDocument1 pageLearning Theory PDFDalibor ŽivićNo ratings yet
- Ftejerezbrochure PDFDocument28 pagesFtejerezbrochure PDFDalibor Živić100% (1)
- FSTFD Brochure PDFDocument4 pagesFSTFD Brochure PDFDalibor ŽivićNo ratings yet
- 076 - Clear Speech - Student-S Book - Judy B. Gilbert - 2005 3rd Ed - (With Audio) PDFDocument194 pages076 - Clear Speech - Student-S Book - Judy B. Gilbert - 2005 3rd Ed - (With Audio) PDFd-fbuser-180386969100% (3)
- ASSiMil Nemacki Bez Muke-Knjiga PDFDocument212 pagesASSiMil Nemacki Bez Muke-Knjiga PDFMarko Vucic90% (10)
- Environmental Test Chambers: Expert in Environmental Climatic Simulations Technical DataDocument2 pagesEnvironmental Test Chambers: Expert in Environmental Climatic Simulations Technical DatagidoNo ratings yet
- ATLAS Scaffolding Inspection ChecklistDocument2 pagesATLAS Scaffolding Inspection ChecklistCris Suyam100% (1)
- Setting Up 802.1x AuthentiactionDocument4 pagesSetting Up 802.1x AuthentiactionruletriplexNo ratings yet
- PricelistDocument11 pagesPricelistReynaldo V Tanglao Jr.No ratings yet
- CS Chapter 3-1 2016Document58 pagesCS Chapter 3-1 2016idrisabdurazek0123No ratings yet
- Tabela Com Codigos e Caracteristicas de Capacitores de TantaloDocument51 pagesTabela Com Codigos e Caracteristicas de Capacitores de TantaloArialdo FurlaniNo ratings yet
- E1211E1211M-12 Standard Practice For Leak Detection and Location Using Surface-Mounted Acoustic Emission SensorsDocument5 pagesE1211E1211M-12 Standard Practice For Leak Detection and Location Using Surface-Mounted Acoustic Emission SensorsAhmed Shaban KotbNo ratings yet
- Example Code ReviewDocument32 pagesExample Code ReviewGareth PriceNo ratings yet
- Computer Aided Machine DrawingDocument8 pagesComputer Aided Machine DrawingLankipalli HemanthNo ratings yet
- SEHS9538Document17 pagesSEHS9538George ZormpasNo ratings yet
- Manual (EN)Document48 pagesManual (EN)Wael SalemNo ratings yet
- U20 Comil -1629 Owner's Manual (double-sided)Document84 pagesU20 Comil -1629 Owner's Manual (double-sided)syamsbnNo ratings yet
- Materials System SpecificationDocument9 pagesMaterials System Specificationnadeem shaikhNo ratings yet
- Computer Boot-Up Troubleshoot FlowchartDocument21 pagesComputer Boot-Up Troubleshoot FlowchartCheAzahariCheAhmad100% (1)
- tp6113 Kohler GeneratorDocument160 pagestp6113 Kohler GeneratorVivek ThangamaniNo ratings yet
- Real Time Scenario For Abstract Class and Interface: Industry Oriented Java-1Document18 pagesReal Time Scenario For Abstract Class and Interface: Industry Oriented Java-1dev eloperNo ratings yet
- Mysmsshop PricingDocument4 pagesMysmsshop PricingshubamNo ratings yet
- Volume Control DampersDocument20 pagesVolume Control DampersSMBEAUTYNo ratings yet
- P442 CortecDocument6 pagesP442 CortecHari Krishna.MNo ratings yet
- UMTS Network Expansion Solution V2 0Document6 pagesUMTS Network Expansion Solution V2 0Umar PervaizNo ratings yet
- By Indrani Choudhury Date:-03/01/2007Document60 pagesBy Indrani Choudhury Date:-03/01/2007Neeraja KolaNo ratings yet
- On Site Coc l-4Document6 pagesOn Site Coc l-4GemmedaMidakso100% (8)
- Hoja de DatosDocument9 pagesHoja de DatosJhon AlfonsoNo ratings yet
- Global Surface Quality Evaluation Procedure: 26 February, 2008Document19 pagesGlobal Surface Quality Evaluation Procedure: 26 February, 2008Mostafa Abd El AlemNo ratings yet
- Introduction To Cisco RoutersDocument64 pagesIntroduction To Cisco RouterssutharshanlkNo ratings yet
- GP628 Plus 6.5Document8 pagesGP628 Plus 6.5Sheldon JimbauNo ratings yet
- Twain Unit For Delphi Tacquireimage Ver 1.4 (Oct/2000)Document13 pagesTwain Unit For Delphi Tacquireimage Ver 1.4 (Oct/2000)Pedro Rodrigo SantosNo ratings yet
School of Information Systems IS302: Lab Exercise: March 2012
School of Information Systems IS302: Lab Exercise: March 2012
Uploaded by
Dalibor Živić0 ratings0% found this document useful (0 votes)
42 views15 pagesThis document provides instructions for a lab exercise on password security and firewall configuration. It describes:
1) Setting up two virtual machines, IST Windows XP and IST Linux, for the exercises.
2) Performing password cracking on Windows and Linux passwords to demonstrate password security issues.
3) Configuring a firewall on IST Linux using UFW and observing intrusion detection using Snort.
Original Description:
d
Original Title
Lab
Copyright
© © All Rights Reserved
Available Formats
DOC, PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentThis document provides instructions for a lab exercise on password security and firewall configuration. It describes:
1) Setting up two virtual machines, IST Windows XP and IST Linux, for the exercises.
2) Performing password cracking on Windows and Linux passwords to demonstrate password security issues.
3) Configuring a firewall on IST Linux using UFW and observing intrusion detection using Snort.
Copyright:
© All Rights Reserved
Available Formats
Download as DOC, PDF, TXT or read online from Scribd
Download as doc, pdf, or txt
0 ratings0% found this document useful (0 votes)
42 views15 pagesSchool of Information Systems IS302: Lab Exercise: March 2012
School of Information Systems IS302: Lab Exercise: March 2012
Uploaded by
Dalibor ŽivićThis document provides instructions for a lab exercise on password security and firewall configuration. It describes:
1) Setting up two virtual machines, IST Windows XP and IST Linux, for the exercises.
2) Performing password cracking on Windows and Linux passwords to demonstrate password security issues.
3) Configuring a firewall on IST Linux using UFW and observing intrusion detection using Snort.
Copyright:
© All Rights Reserved
Available Formats
Download as DOC, PDF, TXT or read online from Scribd
Download as doc, pdf, or txt
You are on page 1of 15
School of Information Systems
IS302: Lab Exercise
Week 11
Version 3.2
March 2012
SINGAPORE MANAGEMENT UNIVERSITY
SCHOOL OF INFORMATION SYSTEMS
IS302 INFORMATION SECURITY AND TRUST
LABORATORY SETUP ( 10 minutes)
For the following lab exercises, two virtual operating systems, IST Windows XP and IST inux have been
created! "ou will be using these # virtual machines to run the lab tools and applications! These # guest operating
systems are running in a closed networ$ %with different IP addresses& within the same physical machine!
'ourse( IS )*# Information Security and Trust Page #
IST Windows XP IST inux
ab Physical +ost ,achine
Using the Vit!"# O$e"ting S%ste&
-! When the virtual machines first starts up if you see the following prompt, select .I copied it/!
#! "ou will see the following when both virtual machines load successfully!
)! Select IST ab Windows XP by clic$ing on .IST ab Windows XP/ button located at the bottom left
hand corner of the screen! Similarly, select IST ab inux by clic$ing on .IST ab inux/!
0! To use the 1irtual ,achine, simply clic$ within the image screen! To release control bac$ to the host
machine, use Shi't(Ct#(A#t!
'ourse( IS )*# Information Security and Trust Page )
IS302 INFORMATION SECURITY AND TRUST
LA)ORATORY E*ERCISE A
+INDO+S AND LINU* PASS+ORD
1 OBJECTIVE AND LEARNING OUTCOMES
11 OBJECTIVE
The ob2ective of this exercise is to learn about the importance of secure passwords in Windows and inux!
1! LEARNING OUTCOMES
3t the end of the laboratory session, students should be able to(
-! 4un brute force attac$s on Windows and 5nix passwords
#! Implement secure passwords for systems!
! LABORATORY E"ERCISE
!1 #in$%&s P'ss&%($) O*+,(',- (!0 minutes)
-! 'lic$ on the IST Windows XP virtual machine to get focus and clic$ .5ser/ to log in!
#! 6o to Start78'ontrol Panel785ser 3ccounts in the IST Windows XP 1irtual machine!
9xercise -( ist the accounts in the IST Windows XP!
:::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::
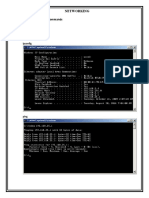
)! ;pen command prompt! 4un the command ipconfig!
9xercise #( What is the IP address of IST Windows XP<
:::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::
'ourse( IS )*# Information Security and Trust Page 0
0! To start brea$ing the IST Windows XP virtual machine=s passwords, we will first boot into the ;phcrac$
boot image that has been preloaded! The following steps will configure the IST Windows XP to boot up
from ;phcrac$ '> image!
a! Select IST ab Windows XP! Press Shift7'trl73lt to release control to the host machine! 'lic$
4emovable >evices78'>?>1>%I>9&! Select .File system/ in the left panel, and then select
@opt@data@vm@ist:winxp:6X@ophcrac$7livecd7-!#!#!iso, %where AX= is your section number& and
clic$ ;pen! This will attached the virtual '>74;, that is preloaded with the ;phcrac$ boot
image! If prompted to select program to open '>74;,, clic$ 'ancel!
b! 6o to Start78 Turn ;ff! 'lic$ 49ST34T to reboot the IST ab Windows XP! %I,P;4T3BT(
>; B;T S99'T T54B ;FF&
C! When the IST ab Windows XP restarts, the ;phcrac$ ive'> image will be loaded! Select the first
option by hitting enter!
'ourse( IS )*# Information Security and Trust Page C
D! The ;phcrac$ image ta$es approximately #7) minutes to load! 3fter the loading image, it will proceed
to crac$ the Windows passwords!
9xercise )( What is the BTPasswd for bob and 3dministrator<
:::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::
E! ;nce you get the password for bob and 3dministrator you can stop ;phcrac$ by clic$ing .Stop/ and
then .9xit/ to end ophcrac$!
F! In the terminal below, type Ente
G! The terminal will prompt for shutdown! Type .n/ and Ente! %I,P;4T3BT( >; B;T T"P9 .y/&
'ourse( IS )*# Information Security and Trust Page D
-*! Press Shift7'trl73lt to return control to the host machine! 'lic$ 1,78 4emovable >evices78
'>?>1>%I>9& and clic$ >isconnect to disable the virtual '>74;,! If prompted to .>isconnect
anyway %and override the loc$&</ clic$ ."es/! This is to allow IST ab Windows XP to reboot bac$ to
Windows XP!
--! 'lic$ on the IST ab Windows XP and enter .reboot/ and hit enter! IST ab Windows XP will now
reboot bac$ to Windows XP!
'ourse( IS )*# Information Security and Trust Page E
!. Linu/ P'ss&%($)J%+n t+e Ri**e( (!0 minutes)
-! 'lic$ on the IST ab inux virtual machine to get focus and login with the following credentials!
5sername( root, Password( passwd
#! In the IST inux virtual machine, clic$ on 'omputer, located at the lower left hand corner! Select
6nome Terminal!
)! In the command shell, enter the command( ifconfig
9xercise 0( What is the IP address of IST ab inux<
:::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::
0! In the command shell, enter the command( cd HSP3'9I 2ohn?run! %Bote( HSP3'9I refers to single white
space!&
C! 4un the following command to get the password hashes and save it in a file .pwdfile/! This is to
combine the password information from the ?etc?passwd and ?etc?shadow files into a single password
file, pwdfile!
'ourse( IS )*# Information Security and Trust Page F
!?unshadow HSP3'9I ?etc?passwd HSP3'9I ?etc?shadow 8 pwdfile
D! 4un John The 4ipper to crac$ the password for user .bob/ using the following command!
!?2ohn HSP3'9IKuserLbob HSP3'9I pwdfile
9xercise C( What is bob=s password<
:::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::
9xercise D( +ow much time does it ta$e to crac$ the password<
:::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::
9xercise E( +ow would you change the password to ma$e it less susceptible to brute7force dictionary attac$<
:::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::
!0 St(%n1 P'ss&%($ Settin1s
-! 'onfigure a strong password for bob that you thin$ will be resilient to dictionary attac$! The following
commands changes the password for user .bob/!
passwd HSP3'9I bob
"ou will be prompted to enter your password twice to confirm the password change for user bob! If the
password you entered is too simple, inux will show a warning message! If you want to $eep the password,
you can ignore the message and proceed to enter your password again to confirm the change!
#! 4un the following command to get the password hashes and save it in a file .pwdfile/!
!?unshadow HSP3'9I ?etc?passwd HSP3'9I ?etc?shadow 8 pwdfile
)! 4un John to ripper to crac$ the password for user .bob/ using the following command!
!?2ohn HSP3'9IKuserLbob HSP3'9I pwdfile
"ou can type Ctrl-C to stop the password crac$ing process!
9xercise G( Is your password crac$ed successfully< If so, how long did it ta$e<
:::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::
79B> ;F 3M 37
'ourse( IS )*# Information Security and Trust Page G
SINGAPORE MANAGEMENT UNIVERSITY
SCHOOL OF INFORMATION SYSTEMS
IS302 INFORMATION SECURITY AND TRUST
LA)ORATORY E*ERCISE )
FIRE+ALL AND INTRUSION DETECTION SYSTEMS
1 OBJECTIVE AND LEARNING OUTCOMES
11 OBJECTIVE
The ob2ective of this exercise is to learn about the functions of firewall and intrusion detection system!
1! LEARNING OUTCOMES
3t the end of the laboratory session, students should be able to(
)! Identify port scan attac$ trace in Snort I>S!
0! 'onfigure firewall using "3ST Firewall ,anager in inux!
! LABORATORY E"ERCISE
!! St'(t Sn%(t IDS %n IST Linu/ (10 minutes)
-! 'lic$ on the IST inux virtual machine to get focus and login with the following credentials if you are
not already logged on!
5sername( root, Password( passwd
-#! In IST inux virtual machine, clic$ on 'omputer, located at the lower left hand corner! Select 6nome
Terminal!
-)! Start the Snort I>S with the following command(
'ourse( IS )*# Information Security and Trust Page -*
snort HSP3'9I Kc HSP3'9I ?etc?snort?snortlab!conf HSP3'9I K3 HSP3'9I fast
Snort is now monitoring the pac$ets sent and received by IST inux! >o not close the terminal! In the next
section we will launch a port scan from IST Windows XP and later examine the alert Snort captures!
!. L'un,+ P%(t S,'n 2(%m IST #in$%&s "P (10 minutes)
Port scans are used by attac$ers to gather information about the services that are running on the targeted
server! This information is important to attac$ers as it will determine the methods used to compromise the
targeted server!
In the following steps, we will launch a port scan from IST Windows XP to find out the listening ports
running on IST inux!
-! 'lic$ on IST Windows XP virtual machine to get focus and clic$ .5ser/ to log in if you have not already
logged in!
-0! 'lic$ in the N&"$ icon, ! Bmap is an open source port scanning tool that is freNuently used
to scan for hosts and services in a networ$!
-C! 9nter the IST ab inux IP address, you noted in 3M 3 9xercise 0! Select .4egular Scan/ in the
Profile field! 'lic$ S,"n to start scanning!
9xercise #( ist the ports and services that are opened on IST inux!
'ourse( IS )*# Information Security and Trust Page --
4eplace this with
the IP noted in
3M 3 9xercise 0
!0 Vie& Sn%(t A3e(ts (10 minutes)
"ou have 2ust launch a port scan in the previous sectionO we will now examine the alert log capture by Snort!
-! 'lic$ on the IST inux image to get focus!
#! Stop the Snort I>S by typing .ctrl7'/ on the terminal!
-D! 1iew the Snort alerts using a inux text editor, 6edit with the following command!
geditHspaceI?var?log?snort?alert
9xercise )( What important information can you get about an attac$ from the alert log<
::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::
9xercise 0( >iscuss how Snort detects the port scan! H+int( http(??www!dslreports!com?faN?-E-I
:::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::
9xercise C( What do you suggest as a counter7measure to port scan attac$s<
!4 En'53e 6i(e&'33 (14 minutes)
In this section, we will enable the firewall on IST inux as a counter7measure to the port scan attac$s! My
default, when the firewall is enabled all ports will be bloc$ed! 3ny incoming traffic will be dropped by the
firewall!
-! ;pen the "aST Firewall ,anager as follows
a! 'lic$ on 'omputer, located at the lower left hand corner!
b! 'lic$ on "aST
c! 'lic$ on Security and 5sers
d! >ouble clic$ on Firewall!
'ourse( IS )*# Information Security and Trust Page -#
-E! 9nable the firewall
-F! 'lic$ on Start Firewall Bow and then clic$ Bext!
'ourse( IS )*# Information Security and Trust Page -)
-G! 'lic$ 3ccept! The firewall is now enabled and will bloc$ all incoming traffic to IST inux!
#*! We shall now verify that the firewall is indeed enabled and dropping all incoming traffic by running the
port scan from IST Windows XP again! 'lic$ on IST Windows XP virtual machine to get focus and start
B,ap to run a regular port scan on IST inux again!
9xercise D( ist the ports and services that are opened on IST inux!
::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::
9xercise E( +as the number of open ports been reduced< Why<
!4 C%n2i1u(e 6i(e&'33 t% A33%& Aut+%(i7e$ T('22i, (14 minutes)
The IST inux virtual machine is running as a web server! +ence, it will need to allow users access to the
port F* %+TTP&! In the following section, we will configure the firewall to allow +TTP access on the IST
inux server!
-! et us first verify that port F* on the IST inux virtual machine is not accessible from IST Windows XP!
'lic$ on the IST Windows XP virtual machine to get focus! In the IST Windows XP, got to Start7
8Internet 9xplorer to open the Internet 9xplorer browser! 6o to the IST inux webpage! %4efer to 3M
3 9xercise 0 for the IST inux IP address!& 9!g! http(??-E#!-D!G#!-0C
#-! 'lic$ on the IST inux virtual machine to get focus! In IST inux, open the "aST Firewall ,anager!
##! 'lic$ on .3llowed Services/ located at the left hand frame
#)! 5nder Service to 3llow, select +TTP Server and clic$ 3dd!
'ourse( IS )*# Information Security and Trust Page -0
#0! 'lic$ Bext and 3ccept to finish the configuration! +TTP port F* is now configured as an allowed
service on the firewall! The firewall will now drop all incoming traffic except for port F* traffic!
9xercise F( 'an you access the IST inux webpage from IST WinXP after configuring the firewall<
. Dis,ussi%n (O*ti%n'3)
-! >esign a secure white list firewall policy for a server %-*!-*!G!-& with the following reNuirements(
3llow potential external clients to access the website hosted on port F* of the server which
provides product and company information!
3llow the administrator to remotely manage the server from the IP address -*!-*!-*!- using
SS+ %port ##&!
Mased on the information above, complete the IP filter table shown below!
Source IP Source Port >estination IP >estination Port 3llow?>eny
3ny 3ny 3llow
3ny 3llow
3ny 3ny 3ny 3ny >eny
#! The company plans to implement an Intrusion >etection System! The networ$ diagram below depicts the
current networ$ design of the company! Mase on the diagram belowO discuss where the intrusion detection
system should be deployed!
79B> 3M M7
'ourse( IS )*# Information Security and Trust Page -C
You might also like
- 1607806691505tips To Unlock Siemens S7 200 PLC CPUDocument14 pages1607806691505tips To Unlock Siemens S7 200 PLC CPUMohamed lamine AssaslaNo ratings yet
- Database Systems A Practical Approach To Design ImDocument9 pagesDatabase Systems A Practical Approach To Design ImSatheeshRajuKalidhindi0% (1)
- Hack The WorldDocument17 pagesHack The Worldjuli_nazNo ratings yet
- Actas3 19Document7 pagesActas3 19Muhammad HumaidiNo ratings yet
- Cisco PIX Firewalls - FAQsDocument11 pagesCisco PIX Firewalls - FAQsbiddumehtaNo ratings yet
- Installation InstructionsDocument33 pagesInstallation Instructionsdreamboy87No ratings yet
- Lab7 InstructionDocument10 pagesLab7 Instructionzargham.razaNo ratings yet
- What Is Windows Vista?Document7 pagesWhat Is Windows Vista?Maria MocanuNo ratings yet
- Penetrating Windows 8 With Syringe UtiliDocument5 pagesPenetrating Windows 8 With Syringe UtiliAGBADAN Yao EricNo ratings yet
- Using Cadence NC-Verilog or Verilog-XL Simulator: Electronic Design Automation (EDA) Tools at NPUDocument6 pagesUsing Cadence NC-Verilog or Verilog-XL Simulator: Electronic Design Automation (EDA) Tools at NPUApoorva BhattNo ratings yet
- Simple VB Script VirusesDocument24 pagesSimple VB Script VirusesAbdinasir Mohamed AddowNo ratings yet
- 7Document7 pages7Benoit RenaudNo ratings yet
- Pentest LinuxDocument17 pagesPentest LinuxDragueur CharmeurNo ratings yet
- A Seminar: GNIT Girls Institute of TechnologyDocument24 pagesA Seminar: GNIT Girls Institute of Technologygolaaa100% (1)
- GNS3 NotesDocument3 pagesGNS3 NotesBidhan HalderNo ratings yet
- 49 & 99 Powerful Computer Tricks - Top 50+ Computer Hacks and TricksDocument96 pages49 & 99 Powerful Computer Tricks - Top 50+ Computer Hacks and TricksGajab HeisterNo ratings yet
- Start Up and Shut Down A Computer: Inside This ResourceDocument15 pagesStart Up and Shut Down A Computer: Inside This ResourcePriyanka SharmaNo ratings yet
- Hacking - Wep Cracking - Ultimate Guide (Video)Document3 pagesHacking - Wep Cracking - Ultimate Guide (Video)Adnan Sohail100% (1)
- Operating Systems Lab 1Document6 pagesOperating Systems Lab 1medo_ali5050No ratings yet
- Computer Fund Part II Lesson 01Document25 pagesComputer Fund Part II Lesson 01Annabelle Rigat de LeonNo ratings yet
- 19Document72 pages19Mohamed YounisNo ratings yet
- Home Automation Using Arduino Wifi Module Esp8266Document11 pagesHome Automation Using Arduino Wifi Module Esp8266Dr. M. Thillai Rani Asst Prof ECENo ratings yet
- Practica BackdoorDocument6 pagesPractica BackdoorLuis Alberto GpNo ratings yet
- Windows and InternetDocument8 pagesWindows and InternetAlex LeeNo ratings yet
- SMBConfiguration (3) ) )Document4 pagesSMBConfiguration (3) ) )Kurem Rubén MayénNo ratings yet
- 10 Super Cool Notepad TricksDocument11 pages10 Super Cool Notepad TricksJovenil BacatanNo ratings yet
- Lab 4 Worksheet: Deploying ApplicationsDocument17 pagesLab 4 Worksheet: Deploying ApplicationsShivamChadhaNo ratings yet
- Openswan Installation and Configuration TutorialDocument5 pagesOpenswan Installation and Configuration TutorialsaulparadaNo ratings yet
- Task 1:: Run The Vmware Workstation and Click On Create A New Virtual Machine OptionDocument24 pagesTask 1:: Run The Vmware Workstation and Click On Create A New Virtual Machine OptionAkshay Kumar TapariaNo ratings yet
- Lab - Using Wireshark To View Network TrafficDocument10 pagesLab - Using Wireshark To View Network TrafficEdy CrackmasterNo ratings yet
- VaccineDocument23 pagesVaccineshayalaNo ratings yet
- Resetting Passwords BfsDocument3 pagesResetting Passwords BfsjudazNo ratings yet
- Anti Forensics GuideDocument9 pagesAnti Forensics GuideDelin BardhiNo ratings yet
- How To Crack WEP - SpoonfedDocument13 pagesHow To Crack WEP - SpoonfedArimatéia FigueredoNo ratings yet
- Secrets Hidden in Windows XPDocument6 pagesSecrets Hidden in Windows XPMihai ParaschivNo ratings yet
- How To Make Virus With Notepad (Dangerous Scripts)Document8 pagesHow To Make Virus With Notepad (Dangerous Scripts)bambamNo ratings yet
- Installation Guide: Symantec Endpoint Protection Symantec Management AgentDocument7 pagesInstallation Guide: Symantec Endpoint Protection Symantec Management AgentJufri JumanNo ratings yet
- Microsoft Security Compliance Manager (SCM) Release Notes: Version HistoryDocument3 pagesMicrosoft Security Compliance Manager (SCM) Release Notes: Version HistorySalman AslamNo ratings yet
- Installing Using VMDocument12 pagesInstalling Using VMsaz gaxNo ratings yet
- ATL Education Foundation Information Security TrainingDocument35 pagesATL Education Foundation Information Security TrainingATL Education FoundationNo ratings yet
- Lab Setup Instructions SEC560 v04Document15 pagesLab Setup Instructions SEC560 v04Edward StarkNo ratings yet
- Remove Password From A Protected Excel Worksheet - The Most Authoritative Technology BlogDocument8 pagesRemove Password From A Protected Excel Worksheet - The Most Authoritative Technology Bloglaiping_lumNo ratings yet
- Icf 7 Module Second QuarterDocument24 pagesIcf 7 Module Second QuarterKazandra Cassidy Garcia100% (1)
- Windows Run CommandsDocument6 pagesWindows Run Commandsboy2959No ratings yet
- SabayonLinux Extradoc Rev.ADocument3 pagesSabayonLinux Extradoc Rev.AayranayranNo ratings yet
- CSEC630 Lab2 - IDS Revised 20110614Document18 pagesCSEC630 Lab2 - IDS Revised 20110614acg49100% (1)
- Wemos ESP32 Lolin32 Board BOOK ENGLISHDocument22 pagesWemos ESP32 Lolin32 Board BOOK ENGLISHDima KnyaNo ratings yet
- Windows OS Help ExerciseDocument3 pagesWindows OS Help ExercisejesuschrististhemanNo ratings yet
- Openvpn TomatoDocument5 pagesOpenvpn Tomatoarsh275No ratings yet
- Re: What's The Difference Between Safe Mode and Selective StartupDocument11 pagesRe: What's The Difference Between Safe Mode and Selective StartupYogesh2323No ratings yet
- PING Howto PDFDocument42 pagesPING Howto PDFbehessNo ratings yet
- LearningMaterial ICT4 v6 0 Week11Document10 pagesLearningMaterial ICT4 v6 0 Week11MN IHNo ratings yet
- Nokia n900 Pwnphone ManualDocument9 pagesNokia n900 Pwnphone ManualFer ContoNo ratings yet
- How To Bypass PIN and Password Locks in Android?: What Do I Need To Know?Document7 pagesHow To Bypass PIN and Password Locks in Android?: What Do I Need To Know?ahmadkamalNo ratings yet
- Networking: Ipconfig Ping FC CHKDSK Net AccountsDocument27 pagesNetworking: Ipconfig Ping FC CHKDSK Net Accountsshivsharma330No ratings yet
- Esp 32 Universal With Display Board Getting Started 2.4 InchDocument23 pagesEsp 32 Universal With Display Board Getting Started 2.4 Inchben.altenberg44No ratings yet
- Stopping Unneeded Startup Services and Making XP Boot FasterDocument21 pagesStopping Unneeded Startup Services and Making XP Boot Fastershan99960No ratings yet
- Esp8266 V10Document22 pagesEsp8266 V10lalonaderNo ratings yet
- Wireless and Mobile Hacking and Sniffing TechniquesFrom EverandWireless and Mobile Hacking and Sniffing TechniquesNo ratings yet
- Vulnerability Assessment ServicesDocument2 pagesVulnerability Assessment ServicesDalibor Živić0% (1)
- BMW CenovnikDocument4 pagesBMW CenovnikDalibor ŽivićNo ratings yet
- Entrepreneur SmartTips Guide Business Plan Step by Step Guide PDFDocument10 pagesEntrepreneur SmartTips Guide Business Plan Step by Step Guide PDFDalibor Živić100% (1)
- Server Confere Server - Conference - Registrationnce Registration ListDocument11 pagesServer Confere Server - Conference - Registrationnce Registration ListDalibor ŽivićNo ratings yet
- Booklet German Vol1 PDFDocument20 pagesBooklet German Vol1 PDFDalibor Živić100% (2)
- Learning Theory PDFDocument1 pageLearning Theory PDFDalibor ŽivićNo ratings yet
- Ftejerezbrochure PDFDocument28 pagesFtejerezbrochure PDFDalibor Živić100% (1)
- FSTFD Brochure PDFDocument4 pagesFSTFD Brochure PDFDalibor ŽivićNo ratings yet
- 076 - Clear Speech - Student-S Book - Judy B. Gilbert - 2005 3rd Ed - (With Audio) PDFDocument194 pages076 - Clear Speech - Student-S Book - Judy B. Gilbert - 2005 3rd Ed - (With Audio) PDFd-fbuser-180386969100% (3)
- ASSiMil Nemacki Bez Muke-Knjiga PDFDocument212 pagesASSiMil Nemacki Bez Muke-Knjiga PDFMarko Vucic90% (10)
- Environmental Test Chambers: Expert in Environmental Climatic Simulations Technical DataDocument2 pagesEnvironmental Test Chambers: Expert in Environmental Climatic Simulations Technical DatagidoNo ratings yet
- ATLAS Scaffolding Inspection ChecklistDocument2 pagesATLAS Scaffolding Inspection ChecklistCris Suyam100% (1)
- Setting Up 802.1x AuthentiactionDocument4 pagesSetting Up 802.1x AuthentiactionruletriplexNo ratings yet
- PricelistDocument11 pagesPricelistReynaldo V Tanglao Jr.No ratings yet
- CS Chapter 3-1 2016Document58 pagesCS Chapter 3-1 2016idrisabdurazek0123No ratings yet
- Tabela Com Codigos e Caracteristicas de Capacitores de TantaloDocument51 pagesTabela Com Codigos e Caracteristicas de Capacitores de TantaloArialdo FurlaniNo ratings yet
- E1211E1211M-12 Standard Practice For Leak Detection and Location Using Surface-Mounted Acoustic Emission SensorsDocument5 pagesE1211E1211M-12 Standard Practice For Leak Detection and Location Using Surface-Mounted Acoustic Emission SensorsAhmed Shaban KotbNo ratings yet
- Example Code ReviewDocument32 pagesExample Code ReviewGareth PriceNo ratings yet
- Computer Aided Machine DrawingDocument8 pagesComputer Aided Machine DrawingLankipalli HemanthNo ratings yet
- SEHS9538Document17 pagesSEHS9538George ZormpasNo ratings yet
- Manual (EN)Document48 pagesManual (EN)Wael SalemNo ratings yet
- U20 Comil -1629 Owner's Manual (double-sided)Document84 pagesU20 Comil -1629 Owner's Manual (double-sided)syamsbnNo ratings yet
- Materials System SpecificationDocument9 pagesMaterials System Specificationnadeem shaikhNo ratings yet
- Computer Boot-Up Troubleshoot FlowchartDocument21 pagesComputer Boot-Up Troubleshoot FlowchartCheAzahariCheAhmad100% (1)
- tp6113 Kohler GeneratorDocument160 pagestp6113 Kohler GeneratorVivek ThangamaniNo ratings yet
- Real Time Scenario For Abstract Class and Interface: Industry Oriented Java-1Document18 pagesReal Time Scenario For Abstract Class and Interface: Industry Oriented Java-1dev eloperNo ratings yet
- Mysmsshop PricingDocument4 pagesMysmsshop PricingshubamNo ratings yet
- Volume Control DampersDocument20 pagesVolume Control DampersSMBEAUTYNo ratings yet
- P442 CortecDocument6 pagesP442 CortecHari Krishna.MNo ratings yet
- UMTS Network Expansion Solution V2 0Document6 pagesUMTS Network Expansion Solution V2 0Umar PervaizNo ratings yet
- By Indrani Choudhury Date:-03/01/2007Document60 pagesBy Indrani Choudhury Date:-03/01/2007Neeraja KolaNo ratings yet
- On Site Coc l-4Document6 pagesOn Site Coc l-4GemmedaMidakso100% (8)
- Hoja de DatosDocument9 pagesHoja de DatosJhon AlfonsoNo ratings yet
- Global Surface Quality Evaluation Procedure: 26 February, 2008Document19 pagesGlobal Surface Quality Evaluation Procedure: 26 February, 2008Mostafa Abd El AlemNo ratings yet
- Introduction To Cisco RoutersDocument64 pagesIntroduction To Cisco RouterssutharshanlkNo ratings yet
- GP628 Plus 6.5Document8 pagesGP628 Plus 6.5Sheldon JimbauNo ratings yet
- Twain Unit For Delphi Tacquireimage Ver 1.4 (Oct/2000)Document13 pagesTwain Unit For Delphi Tacquireimage Ver 1.4 (Oct/2000)Pedro Rodrigo SantosNo ratings yet