Professional Documents
Culture Documents
4g - A New Era in Wireless
4g - A New Era in Wireless
Uploaded by
NelsonRodriguezCopyright:
Available Formats
You might also like
- Sample Report - A Hackers ReconnaissanceDocument14 pagesSample Report - A Hackers ReconnaissanceSailja Sasibindu MalleboinaNo ratings yet
- Principles of Information Seccurity Chapter 4Document8 pagesPrinciples of Information Seccurity Chapter 4Keahi Wong78% (9)
- Broken Access ControlDocument3 pagesBroken Access ControlGlady GladsonNo ratings yet
- 4G-A New Era in Wireless Telecommunication: Piyush Gupta, Priyadarshan PatilDocument8 pages4G-A New Era in Wireless Telecommunication: Piyush Gupta, Priyadarshan PatilVipul PuriNo ratings yet
- 5G Mobile TechnologiesDocument8 pages5G Mobile Technologiesசெல்வம் கருணாநிதிNo ratings yet
- Wireless Mobile Communication - A Study of 4G Technology: S. B. AkintoyeDocument11 pagesWireless Mobile Communication - A Study of 4G Technology: S. B. AkintoyeSorin DobreNo ratings yet
- Multiple Access Techniques in 4G: Amritpal Kaur and DeepaliDocument3 pagesMultiple Access Techniques in 4G: Amritpal Kaur and DeepalipreetvibeNo ratings yet
- 4g Mobile CommunicationsDocument19 pages4g Mobile CommunicationsSmart PassiNo ratings yet
- 4g Wireless Technology (1) Electronics Seminar TopicsDocument10 pages4g Wireless Technology (1) Electronics Seminar TopicsfinitehourabyssNo ratings yet
- 4G TechnologyDocument26 pages4G TechnologytheshlagNo ratings yet
- Issues in Mobility Management in 4G Networks: AbstractDocument16 pagesIssues in Mobility Management in 4G Networks: AbstractHan JeeNo ratings yet
- 4g Technology Seminar Report PDFDocument12 pages4g Technology Seminar Report PDFPriyanshu Kumar100% (6)
- 4g ComparisonDocument5 pages4g ComparisonAnita Paudel ThapaNo ratings yet
- 4G Mobile Networks Technology Beyond 2.5 and 3G - (Abstract)Document16 pages4G Mobile Networks Technology Beyond 2.5 and 3G - (Abstract)DeepakNath100% (1)
- Wireless Communications: Seminor Topic OnDocument9 pagesWireless Communications: Seminor Topic OnPraveen KumarNo ratings yet
- "4G Technology": A Seminar Report OnDocument16 pages"4G Technology": A Seminar Report OnRohit SoniNo ratings yet
- 4g Communications Rajendar BitsDocument16 pages4g Communications Rajendar BitssaddamhussainmdNo ratings yet
- Bimbo SeminarDocument19 pagesBimbo Seminargolden abidemNo ratings yet
- Features in Future: 4G Visions From A Technical Perspective: Jun-Zhao Sun, Jaakko Sauvola, and Douglas HowieDocument5 pagesFeatures in Future: 4G Visions From A Technical Perspective: Jun-Zhao Sun, Jaakko Sauvola, and Douglas HowieGowthami SandeshNo ratings yet
- ACN Assign - Jyotimoi - I079 PDFDocument12 pagesACN Assign - Jyotimoi - I079 PDFJyotimoiHazarikaNo ratings yet
- Inside Cintents - Seminarfinal (USHA)Document14 pagesInside Cintents - Seminarfinal (USHA)Amit majhiNo ratings yet
- 4G CommunicationsDocument9 pages4G CommunicationsPravin AndhaleNo ratings yet
- 4G Wireless Technology: A Brief Review: April 2013Document10 pages4G Wireless Technology: A Brief Review: April 2013DineshNo ratings yet
- Preparation of Your Project Report (5G Standards)Document6 pagesPreparation of Your Project Report (5G Standards)AneelaMalikNo ratings yet
- 4G Technology: Team: Commwarrior Leela VatiDocument9 pages4G Technology: Team: Commwarrior Leela VatimalonanNo ratings yet
- 4G Wireless Technology: A Brief Review: April 2013Document10 pages4G Wireless Technology: A Brief Review: April 2013MATHEUS REYNALDINo ratings yet
- 4g Mobile Communication System A Seminar Report (1) Computer Science Seminar TopicsDocument7 pages4g Mobile Communication System A Seminar Report (1) Computer Science Seminar TopicsfinitehourabyssNo ratings yet
- 4G and Its Future Impact: Indian Scenario: Butchi Babu Muvva, Rajkumar Maipaksana, and M. Narasimha ReddyDocument3 pages4G and Its Future Impact: Indian Scenario: Butchi Babu Muvva, Rajkumar Maipaksana, and M. Narasimha ReddyKartik NairNo ratings yet
- 4g Mobile CommunicationsDocument8 pages4g Mobile CommunicationsSrinivas MadhiraNo ratings yet
- 4g Mobile CommunicationDocument10 pages4g Mobile CommunicationGirish SahareNo ratings yet
- A Review of 4G Wireless Technology Innovation and Its Impact On The WorldDocument8 pagesA Review of 4G Wireless Technology Innovation and Its Impact On The WorldLutfullahNo ratings yet
- Index: Sr. No. TopicDocument18 pagesIndex: Sr. No. TopicDinesh ChahalNo ratings yet
- Wireless Evolution With 4G Technologies: Prof. D. U. Adokar, Priti J. RajputDocument11 pagesWireless Evolution With 4G Technologies: Prof. D. U. Adokar, Priti J. RajputNebiye SolomonNo ratings yet
- 5G Network Architecture Seminar ReportDocument25 pages5G Network Architecture Seminar ReportNkanu OkpaNo ratings yet
- 4G Technology: Department of Computer Engineering, D.Y.P.I.E.TDocument28 pages4G Technology: Department of Computer Engineering, D.Y.P.I.E.Tdinu8086No ratings yet
- 4g - Mobile CommunicationDocument11 pages4g - Mobile CommunicationsrinivascbitNo ratings yet
- Security Enhancement in MANET With 4GDocument4 pagesSecurity Enhancement in MANET With 4GSilverline HartNo ratings yet
- Seminar Report On 5 Pen PC TechnologyDocument23 pagesSeminar Report On 5 Pen PC TechnologyBiswajit Mohanty0% (2)
- 2G-5G Networks: Evolution of Technologies, Standards, and DeploymentDocument14 pages2G-5G Networks: Evolution of Technologies, Standards, and DeploymentRathore Yuvraj SinghNo ratings yet
- An Ultimate Mobile Solution: Tejeswini.M.V 5 Sem, EEE Shridevi Institute of Engg & Tech, TumkurDocument8 pagesAn Ultimate Mobile Solution: Tejeswini.M.V 5 Sem, EEE Shridevi Institute of Engg & Tech, TumkurAbhishek BendigeriNo ratings yet
- 4G-Beyond 3G and Wireless Networks: Indira Gandhi National Open University (IGNOU), Delh, IndiaDocument8 pages4G-Beyond 3G and Wireless Networks: Indira Gandhi National Open University (IGNOU), Delh, IndiaChara SukaNo ratings yet
- 4G Mobile Communications - Emerging Technologies: December 2015Document7 pages4G Mobile Communications - Emerging Technologies: December 2015NOORNo ratings yet
- 4g Magic CommunicationDocument3 pages4g Magic CommunicationKashish PariNo ratings yet
- 4G Wireless Systems 1Document27 pages4G Wireless Systems 1Vineeth MathewNo ratings yet
- 4G MOBILE CommunicationsDocument10 pages4G MOBILE CommunicationsAnkit SrivastavaNo ratings yet
- IEEEconference EzhilDocument6 pagesIEEEconference EzhilChahinez HARZALLAHNo ratings yet
- 4G Seminar+PDFDocument4 pages4G Seminar+PDFSibani Sankar PradhanNo ratings yet
- User Demands and Wireless Technologies: Global Mobile AccessDocument44 pagesUser Demands and Wireless Technologies: Global Mobile AccessSihirli HazineNo ratings yet
- 4g Technology AbstractDocument3 pages4g Technology AbstractPurnima KNo ratings yet
- Fifth Generation Seminar ReportDocument25 pagesFifth Generation Seminar ReportNkanu OkpaNo ratings yet
- A Comprehensive Study: 5G Wireless Networks and Emerging TechnologiesDocument6 pagesA Comprehensive Study: 5G Wireless Networks and Emerging TechnologiesafzhussainNo ratings yet
- 4G Technologies: Jishnu.S, Iii-Cse, Hindusthan Institute of TechnologyDocument12 pages4G Technologies: Jishnu.S, Iii-Cse, Hindusthan Institute of TechnologyJishnu NairNo ratings yet
- Research Paper On 3g and 4g Wireless TechnologyDocument4 pagesResearch Paper On 3g and 4g Wireless Technologyfve140vb100% (1)
- Goals of True Broad Band's Wireless Next Wave (4G-5G)Document5 pagesGoals of True Broad Band's Wireless Next Wave (4G-5G)alokcena007No ratings yet
- 4g Wireless TechnologyDocument32 pages4g Wireless Technologysayyadsa313No ratings yet
- 4G Mobile Terminal AchitectureDocument6 pages4G Mobile Terminal AchitectureTaofeek K SalamiNo ratings yet
- IEEEconference EzhilDocument5 pagesIEEEconference Ezhilyounas125No ratings yet
- Seminar On 4G TechnologiesDocument24 pagesSeminar On 4G TechnologiesSelva RajNo ratings yet
- An Insight To 4 Generation Wireless SystemDocument11 pagesAn Insight To 4 Generation Wireless Systemvenkat4uuuNo ratings yet
- The 5G Revolution: How the Next Generation of Wireless Will Change EverythingFrom EverandThe 5G Revolution: How the Next Generation of Wireless Will Change EverythingNo ratings yet
- Introduction To The Microsoft Security Development Lifecycle (SDL) .PPSXDocument30 pagesIntroduction To The Microsoft Security Development Lifecycle (SDL) .PPSXAnonymous 6Rf5ZA2No ratings yet
- Malware Reverse Engineering Part 1 Static AnalysisDocument27 pagesMalware Reverse Engineering Part 1 Static AnalysisBik AshNo ratings yet
- Cri 227 Cybercrime P1 Exam With AnswersDocument5 pagesCri 227 Cybercrime P1 Exam With Answerswhsi poiskw100% (2)
- Cisa Question PDFDocument21 pagesCisa Question PDFVirat Arya0% (1)
- Pa 3400 SeriesDocument7 pagesPa 3400 SeriessonyalmafittNo ratings yet
- 5.2 Digital CurrencyDocument3 pages5.2 Digital CurrencyMUFAZZAL SADHIQUENo ratings yet
- INE Host and Network Penetration Testing Post Exploitation Course FilesDocument111 pagesINE Host and Network Penetration Testing Post Exploitation Course FilesghostttNo ratings yet
- DR Interview QuestionsDocument25 pagesDR Interview QuestionsamryoussefkhalilNo ratings yet
- CNN News Website AnalysisDocument5 pagesCNN News Website AnalysisRaja MubeenNo ratings yet
- Entry Level Security Services Consultant (Cambridge, MA) Job in CAMBRIDGE, MA - IBMDocument4 pagesEntry Level Security Services Consultant (Cambridge, MA) Job in CAMBRIDGE, MA - IBMSumanta SinhatalNo ratings yet
- NIST - SP.1800-26 - Data Integrity PDFDocument523 pagesNIST - SP.1800-26 - Data Integrity PDFioqseNo ratings yet
- Fortigate 400f SeriesDocument10 pagesFortigate 400f SeriesDaniel MontanoNo ratings yet
- TÜV Rheinland RHSC Souvenir ProgramDocument32 pagesTÜV Rheinland RHSC Souvenir ProgramAnonymous WVaekX9No ratings yet
- Group 2 Internal Control in Cis EnvironmentDocument13 pagesGroup 2 Internal Control in Cis EnvironmentKathlaine Mae ObaNo ratings yet
- Norton AntivirusDocument15 pagesNorton AntivirusMaidenn MarasNo ratings yet
- PAM360 Best Practices GuideDocument46 pagesPAM360 Best Practices GuideaforabadNo ratings yet
- FDA Fact Sheet: The FDA's Role in Medical Device CybersecurityDocument1 pageFDA Fact Sheet: The FDA's Role in Medical Device CybersecurityMaryAnn VanValkenburgNo ratings yet
- Ethical Issues of M-CommerceDocument5 pagesEthical Issues of M-CommerceNk NoviaNo ratings yet
- Mse IndividualDocument16 pagesMse Individualaa AaaNo ratings yet
- Implementing AAA Through Freeradius With MySQL On Ubuntu Server 12Document3 pagesImplementing AAA Through Freeradius With MySQL On Ubuntu Server 12Yohanes SatriaNo ratings yet
- Global Future of Energy 4.0 - Artificial Intelligence and Operational Efficiency Event, 20-21 of June 2019, AmsterdamDocument4 pagesGlobal Future of Energy 4.0 - Artificial Intelligence and Operational Efficiency Event, 20-21 of June 2019, AmsterdamNorman JoshiNo ratings yet
- Login VPDDocument2 pagesLogin VPDJukeNo ratings yet
- A+ PracticeDocument83 pagesA+ Practicevil33100% (1)
- L 06 SecurityorganizationDocument36 pagesL 06 SecurityorganizationMita PramihapsariNo ratings yet
- Luna EFT Customer Release Notes - PN007-011454-001 - RevT - M090900EDocument13 pagesLuna EFT Customer Release Notes - PN007-011454-001 - RevT - M090900Efiqur1No ratings yet
- Final Group Project On HackingDocument30 pagesFinal Group Project On HackingPersian PowerNo ratings yet
- Kali Cheat SheetDocument1 pageKali Cheat SheetCristiana HandreaNo ratings yet
4g - A New Era in Wireless
4g - A New Era in Wireless
Uploaded by
NelsonRodriguezOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
4g - A New Era in Wireless
4g - A New Era in Wireless
Uploaded by
NelsonRodriguezCopyright:
Available Formats
4G- A NEW ERA IN WIRELESS
TELECOMMUNICATION
Piyush Gupta, Priyadarshan Patil
Magister Program in Software Engineering
Mlardalen University
School of Innovation, Design and Engineering
Hgskoleplan 1, Vsters, Sweden
{pga09001, ppl09001}@student.mdh.se
ABSTRACT
4G connect anytime, anywhere, anyhow promising
ubiquitous network access at high speed to the end users,
has been a topic of great interest especially for the wireless
telecom industry. 4G seems to be the solution for the
growing user requirements of wireless broadband access
and the limitations of the existing wireless communication
system. The purpose of this paper is to provide an overview
of the different aspects of 4G which includes its features, its
proposed architecture and key technological enablers. It
also elaborates on the roadblocks in its implementations. A
special consideration has been given to the security
concerns of 4G by discussing a security threat analysis
model proposed by International Telecommunication
Union (ITU). By applying this model, a detailed analysis of
threats to 4G and the corresponding measures to counter
them can be performed.
1. INTRODUCTION
Wireless telecommunication history can be
classified into different generations of network. Each
generation has been a giant stride which revolutionized the
field of mobile communication. As discussed in paper [1],
era of telecommunication started with 1G in 1980 where all
the systems where based on analog radio signal technology.
Voice was considered to be the main traffic. Various 1G
standards defined were Advance Mobile Phone System
(AMPS), Nordic Mobile Telephone (NMT), Time Division
Multiple Access (TDMA) and Frequency Division Mutiple
Access (FDMA). In 1990, 1G was replaced by 2G which
provided rich set of services such as high voice quality and
global mobility based on the digital radio signal
technology. Here also voice was considered to be the main
traffic. 2G includes standards such as Global System For
Mobile Communications (GSM), General Packet Radio
System (GPRS). Both 1G and 2G are based on circuit-
switched technology for data communication at low speed.
2G was a huge success.
2G was followed by 2.5G which is an intermitent
between 2G and 3G. It is based on both circuit switched
and packet switched technologies providing high data rate
with low power consumption. It uses the infrastructure of
Global System for Mobile communications (GSM) and
Code division multiple access (CDMA) to provide its
services.
In the present generation, 2.5G is replaced by 3G
which includes standards from 2.5G and also some other
technologies such as WiMAX (Worldwide Interoperability
for Microwave Access). It is totally based on the packet
switching technology providing broad range of high quality
services to the end user to meet the demand of high data
rate and increasing rate of network users. But 3G was
unable to repeat the success story of 2G as it provided only
few new features over 2G.
Before 3G was deployed all over the world, the idea
of technology beyond 3G started evolving. This idea was
beyond the imagination of ordinary mobile user promising
connect anytime, anyhow, anywhere [4]. This ubiquitous
network access will be achieved by seamlessly integrating
the available and new networks using a core IP based
network layer. This vision is called as the 4
th
generation of
communication (4G).
The paper introduces the idea behind 4G
providing a brief overview about its features, architecture
and challenges faced in its implementation. Security being
a primary concern in any implementation; it motivates the
discussion about threat analysis model. Section 2 cites an
example of how an ideal wireless communication network
should provide service to the end user. Motivation behind
4G and its features are covered in Section 3. Proposed
architecture for 4G and key technologies enabling 4G are
discussed in Section 4 and 5 respectively. Section 6 covers
the challenges in the migration to 4G while section 7
elucidates the threat analysis model which can be used as a
base for the future research work in 4G security. Current
developments and future work to be done in 4G are covered
in Section 8. Section 9 briefs up the conclusion of the
paper and Section 10 enlist all the references of the research
papers.
2. AN IDEAL WIRELESS
COMMUNICATION SCENARIO
Paper [2] provides a good example summarizing the
users expectations from the next generation of wireless
network as illustrated below:
Before going on a vacation, people generally buy
travel guide or browse internet to gather information
spending time and money. But what the users wants to
experience is something like this: The user plans for a
vacation with his family. He downloads a mobile tourist
guide application provided by a mobile service provider
(SP) on his personal terminal. Using this application, user
downloads a travel guide package in his language of
choice. The personal terminal also has a route planner
(GPRS enabled) which can interact with the guide
application helping the user in smooth navigation of his
holiday destination. SP also sends information about
various famous tourist spots like museum and can also
book tickets for the museum on users request by
interacting with the museum operators network. Once the
user reaches the museum, he uses the local network of
museum (Wi-Fi) to listen to the streaming guided tour of
the museum explaining the different artifacts.
Thus, the user would have an experience of life
time. Now the question is whether such an ubiquitous
communication network service can be provided to the user
at high quality and low cost.
3. WHY THE LEAP TOWARDS 4G
The vision which considers 4G as an extension to 3G
cellular services is called as the linear 4G vision [2]. But
the extent of 4G capabilities goes beyond the cellular
services. Envisioning 4G as high speed delivery of services
via the most efficient network available from the pool of
wireless networks is called as the concurrent 4G vision [2].
One of the major reasons of 3G being unable to repeat the
success story of 2G was the provision of only few
additional services over 2G. It was not encouraging enough
for the customers to change their equipments. Paper [2]
suggests a user-centric approach for the design of 4G to
avoid mismatch between the users expectations and the
services provided by 4G. Using the discussion in paper [2-
5], features of 4G which cater to the end-users
expectations and the problems of the current generation
networks can be listed as follows:
User friendliness
4G aims at providing myriad of services to the end
users at high speed. The applications developed to avail
these services should be highly user friendly minimizing
the interaction between the application and the user. For
example, integration of speech recognition technology in
the user interfaces would ease the use of the applications
for every layman.
User personalization
High data transfer rates and ubiquitous coverage of 4G
networks would provide users access to large repository of
data and services. Users should have flexibility to filter
these data and services as per his preferences by
configuring the operational mode of their devices, so that
he can preselect the service features he wants to use. For an
example, user in a mall interested in buying clothes should
receive alerts about various discount offers on clothes
rather than about the other accessories.
Terminal and Network heterogeneity
Terminal heterogeneity refers to the different types of
terminals in terms of the size, weight, display features,
power consumption, etc. Network heterogeneity means the
different types of access networks like WiMAX, Wi-Fi
(Wireless Fidelity), UMTS (Universal Mobile
Telecommunications System) and so forth which differ in
their coverage area, data rate, latency and data loss rate.
Each of these terminals and services cater to different user
requirements. In 4G, all these terminals and networks will
provide common services independent of their capabilities.
This is also called as service personalization.
High Performance
Low transfer rates of 3G restrict the users ability to
take advantage of the rich multimedia contents across the
wireless networks. 4G is expected to provide wireless
download speeds of about 1Gbps in local area network
(LAN) and 100 Mbps in wide area network (WAN), about
260 times greater than the 3G wireless networks.
Interoperability
Multiple standards of 3G restrict the users mobility
and interoperation across different networks. 4G targets at
providing a unified global standard which will facilitate
global mobility and service portability. In other words, end
user can subscribe to different services from different
service providers using the same mobile device.
Intelligent Networking
3G is based primarily on cell or base station WAN
design. 4G aims at building hybrid networks utilizing both
the Wireless LAN concept and WAN design. Thus, the
world would have base stations everywhere providing
ubiquitous network coverage to users at high speed. For
example, a user walking on road is browsing internet using
GPRS (General Packet Radio Service-WAN design). The
moment he enters a mall with Wi-Fi (LAN design),
seamless hand-over from GPRS to Wi-Fi would take place
without the users knowledge.
Network Convergence:
Network convergence is the efficient coexistence of
multimedia, voice and data communication within a single
network. [5]
Currently the telecommunication environment is
divided into wireless and fixed line communication. To
avail these different kinds of services, the end user require
different devices such as cellular phones, fixed line phones,
laptops and PDAs. Once the fixed mobile convergence is
in place in 4G, the distinction between these services will
disappear. The current 3G technology is not able to capture
the market share as done by the fixed line services partly
because of its low bit rates of 384kbps and because of the
high costs associated with these services. But with the
emergence of 4G aiming at global integrated IP based
network, the wireless sector will be able to match the fixed
line sectors in terms of both costs and speed. 4G will lead
to convergence in terms of both devices and services. Thus,
handset capabilities, MP3, camera, mobile broadband
services would be made available in a single device.
Service convergence will result from availability of
telecommunication and internet on a single platform. This
would force the fixed line sector to jump in the competitive
wireless market. In response, the wireless operators will
also jump into the fixed line sector. Thus slowly the
boundaries between these markets will disappear. Thus, the
end user will benefit from one business providing variety of
services. He will experience high quality service at
affordable prices. Thus fixed mobile convergence will act
as a catalyst for stimulating markets to come up with new
innovative and cost effective ideas.
Scalability
Scalability in mobile networks is the ability to handle
the increasing numbers of users and services. 4G will use
IPv6 addressing scheme which will support large number
of wireless devices eliminating the need for Network
address translation (NAT). NAT is technique of sharing
limited number of addresses among large number of
devices. The huge expanse of current internet world
signifies the scalability support of IP. Thus, the use of IP as
core network layer will make 4G easily scalable.
Lower power consumption
Battery technology has not been able to keep pace
with the growing telecom industry. 2G devices required
one battery while 3G required two batteries. Battery drain
is a persistent problem of wireless devices. 4G aims at
breaking this directly proportional rule. Shorter
communication links is one of the few solutions proposed
to cater to this requirement.
Low costs
4G is designed to be spectrally efficient with no
requirement to buy costly extra spectrum. It is not
development of a completely new system rather built on the
top of the existing networks. 4G will also support
backward compatibility with 2G and 3G devices. All these
factors will make 4G much cheaper than the current
generation networks.
4. 4G NETWORK ARCHITECTURE
Figure 1 shows the widely accepted 4G network
structure with IP as the core network used for
communication; integrating the 2G, 3G and 4G
technologies using a convergence layer [4].
Figure 1: 4G Network Structure
Figure 2 shows the proposed layered/level
Architecture of 4G network elucidated in [6].
This architecture fulfills the basic requirement of
servicing the standalone and mobile subscribers on an
anytime, anywhere, anyhow basis in dynamic network
conditions. The architecture is based on Internet Protocol
version 6 (IPV6) which operates at the transport layer
enabling seamless communication across various
heterogeneous networks and based on the key factors such
as mobility, Quality of Service (QoS) and efficient resource
management schemes. The functionalities provided by each
layer and module can be described as follows:
Figure 2: Layered 4G architecture
Application
This layer is composed of various third party
applications which provide value added services to its
subscribers.
Network
This layer consists of various sub layers described as
follows:
Services
This layer manages the interaction between
various value-added services and networks.
Mobility Management
This layer provides quality and uniform services
to the mobile/stationary terminal across various
heterogeneous networks. It provides features of low
handover latency and packet loss during the provision
of real-time and non-real time services to the end user
moving across different networks. To achieve this, it
performs tasks such as binding update (updating the
care-off address of the mobile user), location
management, common control signaling (signaling
required to perform wireless network discovery),
address assignment, handover control mechanism and
so forth.
Resource Management
This layer incorporates the functionalities of
allocation, de-allocation and reallocation of the
network resources which are acquired during the
communication sessions within the same or different
network domains. This activity is performed during or
before the communication activity. This layer also
performs the task of congestion control, packet
scheduling and packet classification.
Quality of service (QoS) management
This layer provides best optimal utilization of the
available resources. In scenarios where the network
resources are limited it provides an option to the
applications to choose between high overall
throughput and low end-to-end delay. It provides the
best trade-off mechanisms depending on the
applications preference. It encompasses several
activities such as link utilization control, bandwidth
control and so forth.
Physical
This layer consist of the core IPV6 network of 4G and
other heterogeneous access networks such as GSM (Global
System for Mobile communications), CDMA( Code
Division Multiple Access) and WLAN in their physical
view. This layer is composed of two sub-layers namely:
Convergence layer
This layer provides common control signaling
mechanism across the core and other heterogeneous
networks at the physical level. It also allows different
radio access networks to transparently use the
independent network services such as mobility
management, resource management and QoS
management.
Different RAN
This layer consists of several radio access
networks communicating with each other at the
physical level.
Operation, Administration, Maintenance and
Provisioning
This layer spans across all the layers of the network
architecture and provides the functionalities of network
controlling, network monitoring and fault detection. It also
maintains the repudiation between various services and
resources of several heterogeneous and core networks.
Security
This layer also branches across all the layers of the 4G
network architecture which perform the function of
authentication, authorization, encryption, establishment and
implementation of service policy agreement between the
various vendors.
5. KEY 4G TECHNOLOGIES
This section provides a brief description of the key
technologies which would enable 4G implementation based
on the discussion in [7-11]. They are discussed as follows:
5.1 OFDMA
OFDMA can be used for the downlink transmission
(signal transmission from the base station to mobile
terminal) of the symbols for achieving high spectral
efficiency. It provides high performance on full bandwidth
usage.
It is a channel allocation scheme based on the
orthogonal frequency division multiplexing technique that
splits the data to be transmitted along the orthogonal
narrowband carriers well spaced by frequency. The
technique used for splitting the data is Inverse Fast Fourier
Transform (IIFT) which incorporates the advantage of
transmitting the data at a higher rate. The introduction of a
cyclic prefix (CP) in terms of guard interval consists of
repetition of the last part of the symbol at the beginning of
each symbol transmitted. This avoids interference between
the various symbols and the carriers if the CP interval is
longer than the delay caused by the interferences of the
channel. This improves the robustness of the technology
used for the multipath transmission. The use of narrowband
subcarrier is to get a channel which is constant for each
sub-band (input symbol broken down number of smaller
bands). This avoids synchronization problems at the
receiver side during the symbol transmission through the
channel. In order to get high spectral efficient system,
overlapping between the mutually orthogonal subcarrier is
allowed.
OFDMA is compatible with other technologies such
as Multiple Input Multiple Output and smart antennas.
OFDM not only improves the performance of the physical
layer but also adds to the improvement of the Data Link
Layer. It facilitates the optimization between various layers
of network for usage of radio link from multiple radios.
OFDMA is currently applied on various wireless and
wire line standards such as Wi-Fi, Wireless LAN, Ultra
Wideband (UWB), Wireless PAN, WiMAX, WiBro,
HiperMAN, Wireless MAN, 3GPP UMTS & 3GPP@ LTE
(Long-Term Evolution).
5.2 SCFDMA
It can be used for the uplink transmission of the
symbols. It is a channel allocation scheme used for data
transmission based on single carrier frequency division
multiplexing technique that allows the transmission of the
symbols across a single carrier .The techniques used for
splitting the data is IFFT described in the above section and
Discrete Fourier transform (DFT) which performs the task
of splitting the data across multiple sub-carriers and
transmitting virtually as a single carrier. DFT is performed
prior to IFFT. SCFDMA provides low peak-to-average-
power ratio (PAPR) as compared to OFDMA. In this
scheme, as the data is transmitted along the multiple
subcarriers and if one subcarrier is in problem it is easy to
recover the data from the other subcarriers based on
frequency selection for the channel. But the recovery of
data at the receiver side requires the selection of the data
from the multiple subcarriers and requires more efforts for
removing the error in the data.
5.3 Multiple-Input and Multiple-Output
(MIMO)
This is an antenna technology which uses multiple
channels in radios to provide the functions of both the
transmitter and receiver of data signals sent over the
network as shown in the figure 3 [12]. It provides high
spectral efficiency and link reliability facilitating
significant increase in the data throughput and radio link
usage without additional bandwidth and transmission
power. This high efficiency is due to the availability of an
independent path in a rich scattering environment for each
transmitter and receiver antennas in the radio.
Figure 3: MIMO
The MIMO channels can be used with OFDMA for
transmission and reception of modulated signal over
network to single or multiple users. This is currently used
in WLAN Wi-Fi 802.11n, Mesh Networks (e.g., WMAN
WiMAX 802.16e, RFID, and Digital Home.
5.4 Multi-user MIMO (MU-MIMO)
This is the variant antenna technology that enhances
the communication capabilities of the individual radio
terminal used by radios in the network by introducing
multiple independent radio terminals. This allows
transmission and reception to and from multiple users using
the same band.
5.5 Software Defined Radio (SDR)
SDR is a radio communication system implemented as
software on the personal computer or embedded devices. It
scans the available networks and then reconfigures itself for
the selected network by downloading the software specific
to that network. It is used for implementation of the
multimodal, multi-band, multi-standard user terminals and
base stations which allows accessibility across various
wireless and wireline heterogeneous networks. There are
several advantages of SDR such as flexibility in network
expansion i.e. operator can expands its network
infrastructure by adding few modems to base station
transceiver system. It reduces the cost for development of
multimodal, multiband and multi-standard user equipments.
This will benefit both the end users and the service
providers. The current SDR technology is not capable of
supporting the multiple networks. It should be enhanced to
support multiple networks.
6. CHALLENGES IN 4G
Paper [13] groups challenges faced in the migration to
4G into three different aspects and discusses them in detail
as follows:
Mobile station:
Multimode user terminal
Multimode user terminal is a device working in
different modes supporting a wide variety of 4G
services and wireless networks by reconfiguring
themselves to adapt to different wireless networks.
They encounter several design issues such as
limitations in the device size, cost, power consumption
and backward compatibility to systems. One possible
solution to this is the use of SDR which adapts itself to
the wireless interface of the network. Figure 4 shows
multimode user terminal simultaneously interacting
with the different access networks.
Wireless network discovery
Availing 4G services require the multimode user
terminal to discover and select the preferred wireless
network. Service discovery in 4G will be much more
challenging then 3G because of the heterogeneity of
the networks and their access protocols. SDR
approach has been proposed to counter this challenge.
As shown in the figure 4, SDR will scan for the
available networks and download the software
required to interface with the selected network.
Software can be downloaded from a PC server, smart
card or from over the air (OTA). Slow download
speeds is one of the major problems faced by the SDR
approach.
Wireless network selection
4G will provide the users a choice to select a
wireless network providing optimized performance
and high QoS for a particular place, time and desired
service (communication, multimedia). But what
parameters define high QoS and optimized
performance at particular instant needs to be clearly
defined to make the network selection procedure
efficient and transparent to the end user. Possible
considerations may be available network resources,
network supported service types and cost and user
preference.
Figure 4: Multimode user Terminal
System
Terminal mobility
Terminal mobility is an essential characteristic to
fulfill the Anytime Anywhere promise of 4G. It
allows the mobile users to roam across the geographic
boundaries of wireless networks [13]. Two main
issues in terminal mobility are location and hand off
management. Location management involves tracking
the location of the mobile users and maintaining
information such as the authentication data, QoS
capabilities, and the original and the current cell
location. Handoff management is maintaining the
ongoing communication when the terminal roams.
Handoff can be horizontal or vertical depending on
whether the user moves from one cell to another
within the same wireless systems or across different
wireless systems (WLAN to GSM). Handoff process
faces several challenges like maintaining the QoS and
system performance across different systems, deciding
the correct handoff time, designing the correct handoff
mechanism, packet losses, handover latency and the
increased system load.
Network infrastructure and QoS support
Unlike previous generation networks (2G and
3G), 4G is an integration of IP and non-IP based
system. Prior to 4G, QoS designs were made with a
particular wireless system in mind. But in 4G
networks QoS designs should consider the integration
of different wireless networks to guarantee QoS for
the end-to-end services.
Security
Most of the security schemes and the
encryption/decryption protocols of the current
generation networks were designed only for specific
services. They seem to be very inflexible to be used
across the heterogeneous architecture of 4G which
needs dynamically reconfigurable, adaptive and light-
weight security mechanism.
Fault tolerance
Wireless networks characterize a tree-like
topology. Any failure in one of the levels can affect all
the network elements at the levels below. This
problem can be further aggravated because of the
multiple tree topologies. Adequate research work is
required to devise a strategy for fault tolerance in
wireless networks.
Services
Multiple operators and billing system
In the current era of 2G and 3G networks, each
operator has its own billing scheme based on the call
duration, services used, etc. But in 4G each user can
avail to different services made available by different
operators. This would complicate the billing system
for both the service providers and the end users. This
asks for a unified billing system for all the services of
the 4G network. To cater to these issues several
frameworks are being studied based on the
requirements of scalability, flexibility, accuracy and
usability.
Personal mobility
Unlike terminal mobility, personal mobility
considers the movement of the user. It emphasizes on
provision of personal communication- ensuring
message delivery to the user irrespective of his
location and the terminal he is using and personalized
operating environment- adapting the message display
as per the characteristics of user terminal.
7. 4G SECURITY THREAT ANALYSIS
Amidst the concerns of technology, devices,
architecture for 4G; security has not received much
attention although being an important parameter for its
marketing among the end users. Paper [14] discusses the
security aspect of 4G in detail. A region may be connected
by multiple Radio Access Network (RAN). One of the
governing factors for selecting an appropriate RAN will be
the security features provided by the network.
7.1 Key Objectives for secured N/W
architecture
Availability: network services are available
without any disruptions or interruptions
Interoperability: the security solutions are
generic and not specific to any particular services
or networks
Usability: security services provided should be
easy to use
QoS guarantee: Security services like
cryptographic algorithms should meet the QoS
constraints of voice and multimedia traffic
Cost-effectiveness: The cost of security should
be lower than the cost of the risks
Each stakeholder in the 4G network has its own set of
security requirements. 4G security systems need to be
flexible enough to adapt to these requirements. They should
also comprehend other vulnerabilities which might disrupt
the functioning of the systems.
7.2 Possible threats faced by 4G
As all the network operators and service provide
would share a common core network
infrastructure, compromise of a single operator
will lead to the collapse of the entire network
infrastructure.
Third-parties can masquerade as legitimate users
resulting in theft of service and billing frauds.
Since 4G is a secure IP based solution it will be
vulnerable to all the security threats as the current
Internet world.
On the lines of email-spam, the Spam over
Internet telephony (SPIT), the new spam over
VoIP may become serious will become serious
threats.
Spoofing attacks can lead to misdirected
communication and internet banking related
frauds.
Eavesdropping and interception of private
communications.
Phishing attacks, stealing bank account details
and other secured information.
7.3 Security threat analysis model
X.805 is a standard based on the Bell Labs security
model developed by ITU. This standard provides a
systematic and organized way of performing network
security evaluation and planning. This model has been
proposed by ITU to perform a network security analysis of
the emerging new generation networks.
The network security architecture consists of three
layers, three planes and eight dimensions which help
identify possible threats or attacks on the system.
7.3.1 Security layers
Security layer defines the network
equipments or the facilities which need to be
protected from security threats. The three layers
are mainly:
Infrastructure layer: Consists of the building
blocks of the network like routers, switches,
Ethernet links, etc.
Service layer: Services provided to the end
users like VoIP (Voice over Internet Protocol),
Wi-Fi, etc constitutes this layer.
Application layer: Network-based applications
accessed by the end-users such as web browsing,
email, etc constitute this layer.
7.3.2 Security Planes
The security plane specifies the
different types of network activities that need to
be protected. The three security planes classified
are [15]:
User plane is concerned with information
routing and performs several functions such as
error correction and flow control. User services
such as voice, fax, video, web access, etc can be
categorized under the user plane.
Control plane deals with the short term network
operations such as control of communication
sessions like call setup, call release, etc. It
contains several functions like security(
performing authentication) , QoS, mobility,
charging, etc
Management plane is concerned with the
long-term network operations and includes
functions like fault, configuration,
accounting (pricing and billing),
performance and security (maintaining the
authentication system) management.
7.3.3 Security dimensions
Security dimensions specify the
different threats and the measures to counter
them. The eight security dimensions are:
Access control: Keeps a track on the protection
level against the unauthorized use of network
resources. For example, password, ACL, firewall.
Authentication: checks whether the user of the
network resources has been authenticated. For
example, digital signature and certificates.
Non-repudiation: Prevents denial of occurrence
of an activity on the network. For example,
system logs, digital signatures.
Data confidentiality: ensures that data is made
available only to the authorized user using
encryption mechanism.
Communication security: Ensures the data
flow only between authorized end points.
Data integrity: Counters unauthorized attempts
made to modify the data using anti-virus software
or encryption mechanisms.
Availability: Ensures that the network resources
and services are always available to the
authorized users using network redundancy
techniques.
Privacy: Prevents revelation of any important
information derived from network monitoring
activities performed by other malicious users
using encryption techniques.
7.3.4 Threat Analysis Model
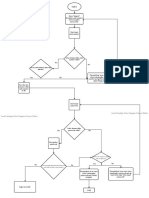
As shown in the Figure 5 [14], we define nine
modules corresponding to the three security layers and
three security planes. The eight security dimensions are
applied to each of the module. Each module has different
security objectives and corresponding security measures to
cater to those objectives. Thus, these architecture help us to
comprehend which network resources and activities are
vulnerable to which threats and what measures can be taken
to counter those threats. It can be applied to any network
technology like wireless, wired, converged networks, etc.
Figure 5: Threat analysis Model
8. WHEN WILL 4G HAPPEN?
Air of uncertainty is looming large over the
development and deployment of 4G networks. Telecom
experts predict 2010-2011 time frame. Vodafone and
Verizon Wireless have developed a common platform for
supporting mobiles in 4G networks using LTE technology
and they are currently in the field trial phase [16]. NTT-
Docomo has managed to achieve a speed of about
100MBPS for the moving terminal and 1 GBPS for the
stationary terminal. They are scheduling to deploy the first
commercial network by 2010 [17]. Spring Nextel is
planning to deploy 4G network mobile services using
WiMAX technology in US [17]. Ericssion will deploy first
commercial 4G network based on LTE to provide mobile
broadband services for the TeliaSonera customers in
Stockholm [18].
9. CONCLUSION
The advent of 4G is sure to revolutionize the field
of telecommunication domain bringing the wireless
experience to a completely new level. It would provide
wealth of features and services making the world a smaller
place to live. Thus, 4G seems to have the capability to
realize the scenario discussed in Section 2. But 4G should
also take lesson from the 3Gs failure to capture the
imagination of the end-users. Technology should not be
developed for technologys sake rather it should target the
end user. Thus, user-centric approach towards 4Gs
development is the key to its success. Common consensus
on the standards and the technologies for 4G needs to be
reached to fasten 4Gs deployment which would be a
gradual process. Lot of research work is required to
investigate the open issues like design for SDR, QoS
parameters and so forth. The threat analysis model
provided by ITU is very apt for the complete analysis and
planning for security of 4G. It can be used as a reference
framework for future research. But still comprehensive
research work is required in the field of network security to
tackle potential security threats because a ubiquitous
secured heterogeneous network will appeal more to the
todays consumers.
10. REFERENCES
[1] J. Ibrahim. 4G Features. Bechtel Telecommunications
and Technical Journal, Volume 1, Number.1, December
2002, Page(s): 11-14.
[2] Frattasi, S.; Fathi, H.; Fitzek, F.H.P.; Katz, M.D.;
Prasad, R. Defining 4G Technology from the Users
Perspective. IEEE Volume 20, Issue 1, Jan.-Feb. 2006,
Page(s):35 41.
[3] Santhi, K.R.; Srivastava, V.K. ; SenthilKumaran,
G.; Butare, A. Goals of True Broad bands Wireless Next
Wave (4G-5G). Vehicular Technology Conference, 2003.
VTC 2003-Fall. 2003 IEEE 58
th
, Volume 4, Oct.2003,
Pages(s): 2317-2321.
[4] A. H. Khan, M. A. Qadeer, J. A. Ansari and S.
Waheed. 4G as a Next Generation Wireless Network.
Future Computer and Communication, 2009. ICFCC 2009.
International Conference, April 2009, Page(s):334 - 338
[5] Jinsung Choi. 4G, Solution for Convergence?.
Microwave Symposium Digest, 2006. IEEE MTT-S
International, June 2006 , Page(s):843 - 846
[6] Kibria, M.R.; Mirchandani, V.; Jamalipour, A.
A Consolidated Architecture for 4G/B3G Networks.
Wireless Communications and Networking Conference,
2005, IEEE Volume 4, March 2005, Page(s):2406 - 2411.
[7] Berardinelli, G.; Ruiz de Temino, L.A.; Frattasi, S.;
Rahman, M.; Mogensen, P. OFDMA vs. SC-FDMA:
performance comparison in local area imt-a scenarios.
IEEE Wireless Communications, Volume 15, Issue 5,
October 2008, Page(s):64-72.
[8] Goldsmith, A.; Jafar, S.A.; Jindal, N.; Vishwanath,
S. Capacity Limits of MIMO Channels. Selected Areas in
Communications, IEEE Journal Volume 21, Issue 5, June
2003, Page (s): 684 - 702.
[9] Adachi, K.; Adachi, F.; Nakagawa, M. A Study on
Channel Capacities of MC-CDMA MIMO and OFDM
MIMO. Communication Systems, 2008. ICCS 2008. 11th
IEEE Singapore International Conference, Nov. 2008,
Page(s):1384 1388.
[10] Xiaodong Wang. OFDM and Its Application to 4G.
Wireless and Optical Communications, 2005. 14th Annual
WOCC 2005. International Conference, April 2005
Page(s):69.
[11] Mitola, J.; III E-Systems, Fairfax, VA.
Software Radios Survey, Critical Evaluation and Future
Directions. Aerospace and Electronic Systems Magazine,
IEEE, Volume 8, Issue 4, April 1993, Page(s):25 36.
[12] Sharony, J. Introduction of Wireless Theory and
Application. IEEE LI, November 2006.
[13] Suk Yu Hui, Kai Hau Yeung. Challenges in the
Migration to 4G Mobile Systems. Communications
Magazine, IEEE Volume 41, Issue 12, Dec. 2003,
Page(s):54 - 59
[14] Yongsuk Park, Taejoon Park. A Survey of Security
Threats on 4G Networks. Globecom Workshops, 2007,
IEEE, Nov. 2007, Page(s):1 - 6.
[15] Kappler C. UMTS Networks and Beyond. John Wiley
& sons ltd, 2009.
[16] Krenik, B. 4G Wireless Technology: When will it
happen? What does it offer?. Solid-State Circuits
Conference, 2008. A-SSCC '08, IEEE Asian, Nov. 2008,
Page(s):141 144.
[17] Integrating 3G and 4G Networks to Enhance the
Mobile Internet Experience.
[14.10.2009] https://4gworld.com/
[18] Ericsson to provide 4G network for TeliaSonera.
[13.10.2009]
http://networking.cbronline.com/news/ericsson_to_provide
_4g_network_for_teliasonera_220109
You might also like
- Sample Report - A Hackers ReconnaissanceDocument14 pagesSample Report - A Hackers ReconnaissanceSailja Sasibindu MalleboinaNo ratings yet
- Principles of Information Seccurity Chapter 4Document8 pagesPrinciples of Information Seccurity Chapter 4Keahi Wong78% (9)
- Broken Access ControlDocument3 pagesBroken Access ControlGlady GladsonNo ratings yet
- 4G-A New Era in Wireless Telecommunication: Piyush Gupta, Priyadarshan PatilDocument8 pages4G-A New Era in Wireless Telecommunication: Piyush Gupta, Priyadarshan PatilVipul PuriNo ratings yet
- 5G Mobile TechnologiesDocument8 pages5G Mobile Technologiesசெல்வம் கருணாநிதிNo ratings yet
- Wireless Mobile Communication - A Study of 4G Technology: S. B. AkintoyeDocument11 pagesWireless Mobile Communication - A Study of 4G Technology: S. B. AkintoyeSorin DobreNo ratings yet
- Multiple Access Techniques in 4G: Amritpal Kaur and DeepaliDocument3 pagesMultiple Access Techniques in 4G: Amritpal Kaur and DeepalipreetvibeNo ratings yet
- 4g Mobile CommunicationsDocument19 pages4g Mobile CommunicationsSmart PassiNo ratings yet
- 4g Wireless Technology (1) Electronics Seminar TopicsDocument10 pages4g Wireless Technology (1) Electronics Seminar TopicsfinitehourabyssNo ratings yet
- 4G TechnologyDocument26 pages4G TechnologytheshlagNo ratings yet
- Issues in Mobility Management in 4G Networks: AbstractDocument16 pagesIssues in Mobility Management in 4G Networks: AbstractHan JeeNo ratings yet
- 4g Technology Seminar Report PDFDocument12 pages4g Technology Seminar Report PDFPriyanshu Kumar100% (6)
- 4g ComparisonDocument5 pages4g ComparisonAnita Paudel ThapaNo ratings yet
- 4G Mobile Networks Technology Beyond 2.5 and 3G - (Abstract)Document16 pages4G Mobile Networks Technology Beyond 2.5 and 3G - (Abstract)DeepakNath100% (1)
- Wireless Communications: Seminor Topic OnDocument9 pagesWireless Communications: Seminor Topic OnPraveen KumarNo ratings yet
- "4G Technology": A Seminar Report OnDocument16 pages"4G Technology": A Seminar Report OnRohit SoniNo ratings yet
- 4g Communications Rajendar BitsDocument16 pages4g Communications Rajendar BitssaddamhussainmdNo ratings yet
- Bimbo SeminarDocument19 pagesBimbo Seminargolden abidemNo ratings yet
- Features in Future: 4G Visions From A Technical Perspective: Jun-Zhao Sun, Jaakko Sauvola, and Douglas HowieDocument5 pagesFeatures in Future: 4G Visions From A Technical Perspective: Jun-Zhao Sun, Jaakko Sauvola, and Douglas HowieGowthami SandeshNo ratings yet
- ACN Assign - Jyotimoi - I079 PDFDocument12 pagesACN Assign - Jyotimoi - I079 PDFJyotimoiHazarikaNo ratings yet
- Inside Cintents - Seminarfinal (USHA)Document14 pagesInside Cintents - Seminarfinal (USHA)Amit majhiNo ratings yet
- 4G CommunicationsDocument9 pages4G CommunicationsPravin AndhaleNo ratings yet
- 4G Wireless Technology: A Brief Review: April 2013Document10 pages4G Wireless Technology: A Brief Review: April 2013DineshNo ratings yet
- Preparation of Your Project Report (5G Standards)Document6 pagesPreparation of Your Project Report (5G Standards)AneelaMalikNo ratings yet
- 4G Technology: Team: Commwarrior Leela VatiDocument9 pages4G Technology: Team: Commwarrior Leela VatimalonanNo ratings yet
- 4G Wireless Technology: A Brief Review: April 2013Document10 pages4G Wireless Technology: A Brief Review: April 2013MATHEUS REYNALDINo ratings yet
- 4g Mobile Communication System A Seminar Report (1) Computer Science Seminar TopicsDocument7 pages4g Mobile Communication System A Seminar Report (1) Computer Science Seminar TopicsfinitehourabyssNo ratings yet
- 4G and Its Future Impact: Indian Scenario: Butchi Babu Muvva, Rajkumar Maipaksana, and M. Narasimha ReddyDocument3 pages4G and Its Future Impact: Indian Scenario: Butchi Babu Muvva, Rajkumar Maipaksana, and M. Narasimha ReddyKartik NairNo ratings yet
- 4g Mobile CommunicationsDocument8 pages4g Mobile CommunicationsSrinivas MadhiraNo ratings yet
- 4g Mobile CommunicationDocument10 pages4g Mobile CommunicationGirish SahareNo ratings yet
- A Review of 4G Wireless Technology Innovation and Its Impact On The WorldDocument8 pagesA Review of 4G Wireless Technology Innovation and Its Impact On The WorldLutfullahNo ratings yet
- Index: Sr. No. TopicDocument18 pagesIndex: Sr. No. TopicDinesh ChahalNo ratings yet
- Wireless Evolution With 4G Technologies: Prof. D. U. Adokar, Priti J. RajputDocument11 pagesWireless Evolution With 4G Technologies: Prof. D. U. Adokar, Priti J. RajputNebiye SolomonNo ratings yet
- 5G Network Architecture Seminar ReportDocument25 pages5G Network Architecture Seminar ReportNkanu OkpaNo ratings yet
- 4G Technology: Department of Computer Engineering, D.Y.P.I.E.TDocument28 pages4G Technology: Department of Computer Engineering, D.Y.P.I.E.Tdinu8086No ratings yet
- 4g - Mobile CommunicationDocument11 pages4g - Mobile CommunicationsrinivascbitNo ratings yet
- Security Enhancement in MANET With 4GDocument4 pagesSecurity Enhancement in MANET With 4GSilverline HartNo ratings yet
- Seminar Report On 5 Pen PC TechnologyDocument23 pagesSeminar Report On 5 Pen PC TechnologyBiswajit Mohanty0% (2)
- 2G-5G Networks: Evolution of Technologies, Standards, and DeploymentDocument14 pages2G-5G Networks: Evolution of Technologies, Standards, and DeploymentRathore Yuvraj SinghNo ratings yet
- An Ultimate Mobile Solution: Tejeswini.M.V 5 Sem, EEE Shridevi Institute of Engg & Tech, TumkurDocument8 pagesAn Ultimate Mobile Solution: Tejeswini.M.V 5 Sem, EEE Shridevi Institute of Engg & Tech, TumkurAbhishek BendigeriNo ratings yet
- 4G-Beyond 3G and Wireless Networks: Indira Gandhi National Open University (IGNOU), Delh, IndiaDocument8 pages4G-Beyond 3G and Wireless Networks: Indira Gandhi National Open University (IGNOU), Delh, IndiaChara SukaNo ratings yet
- 4G Mobile Communications - Emerging Technologies: December 2015Document7 pages4G Mobile Communications - Emerging Technologies: December 2015NOORNo ratings yet
- 4g Magic CommunicationDocument3 pages4g Magic CommunicationKashish PariNo ratings yet
- 4G Wireless Systems 1Document27 pages4G Wireless Systems 1Vineeth MathewNo ratings yet
- 4G MOBILE CommunicationsDocument10 pages4G MOBILE CommunicationsAnkit SrivastavaNo ratings yet
- IEEEconference EzhilDocument6 pagesIEEEconference EzhilChahinez HARZALLAHNo ratings yet
- 4G Seminar+PDFDocument4 pages4G Seminar+PDFSibani Sankar PradhanNo ratings yet
- User Demands and Wireless Technologies: Global Mobile AccessDocument44 pagesUser Demands and Wireless Technologies: Global Mobile AccessSihirli HazineNo ratings yet
- 4g Technology AbstractDocument3 pages4g Technology AbstractPurnima KNo ratings yet
- Fifth Generation Seminar ReportDocument25 pagesFifth Generation Seminar ReportNkanu OkpaNo ratings yet
- A Comprehensive Study: 5G Wireless Networks and Emerging TechnologiesDocument6 pagesA Comprehensive Study: 5G Wireless Networks and Emerging TechnologiesafzhussainNo ratings yet
- 4G Technologies: Jishnu.S, Iii-Cse, Hindusthan Institute of TechnologyDocument12 pages4G Technologies: Jishnu.S, Iii-Cse, Hindusthan Institute of TechnologyJishnu NairNo ratings yet
- Research Paper On 3g and 4g Wireless TechnologyDocument4 pagesResearch Paper On 3g and 4g Wireless Technologyfve140vb100% (1)
- Goals of True Broad Band's Wireless Next Wave (4G-5G)Document5 pagesGoals of True Broad Band's Wireless Next Wave (4G-5G)alokcena007No ratings yet
- 4g Wireless TechnologyDocument32 pages4g Wireless Technologysayyadsa313No ratings yet
- 4G Mobile Terminal AchitectureDocument6 pages4G Mobile Terminal AchitectureTaofeek K SalamiNo ratings yet
- IEEEconference EzhilDocument5 pagesIEEEconference Ezhilyounas125No ratings yet
- Seminar On 4G TechnologiesDocument24 pagesSeminar On 4G TechnologiesSelva RajNo ratings yet
- An Insight To 4 Generation Wireless SystemDocument11 pagesAn Insight To 4 Generation Wireless Systemvenkat4uuuNo ratings yet
- The 5G Revolution: How the Next Generation of Wireless Will Change EverythingFrom EverandThe 5G Revolution: How the Next Generation of Wireless Will Change EverythingNo ratings yet
- Introduction To The Microsoft Security Development Lifecycle (SDL) .PPSXDocument30 pagesIntroduction To The Microsoft Security Development Lifecycle (SDL) .PPSXAnonymous 6Rf5ZA2No ratings yet
- Malware Reverse Engineering Part 1 Static AnalysisDocument27 pagesMalware Reverse Engineering Part 1 Static AnalysisBik AshNo ratings yet
- Cri 227 Cybercrime P1 Exam With AnswersDocument5 pagesCri 227 Cybercrime P1 Exam With Answerswhsi poiskw100% (2)
- Cisa Question PDFDocument21 pagesCisa Question PDFVirat Arya0% (1)
- Pa 3400 SeriesDocument7 pagesPa 3400 SeriessonyalmafittNo ratings yet
- 5.2 Digital CurrencyDocument3 pages5.2 Digital CurrencyMUFAZZAL SADHIQUENo ratings yet
- INE Host and Network Penetration Testing Post Exploitation Course FilesDocument111 pagesINE Host and Network Penetration Testing Post Exploitation Course FilesghostttNo ratings yet
- DR Interview QuestionsDocument25 pagesDR Interview QuestionsamryoussefkhalilNo ratings yet
- CNN News Website AnalysisDocument5 pagesCNN News Website AnalysisRaja MubeenNo ratings yet
- Entry Level Security Services Consultant (Cambridge, MA) Job in CAMBRIDGE, MA - IBMDocument4 pagesEntry Level Security Services Consultant (Cambridge, MA) Job in CAMBRIDGE, MA - IBMSumanta SinhatalNo ratings yet
- NIST - SP.1800-26 - Data Integrity PDFDocument523 pagesNIST - SP.1800-26 - Data Integrity PDFioqseNo ratings yet
- Fortigate 400f SeriesDocument10 pagesFortigate 400f SeriesDaniel MontanoNo ratings yet
- TÜV Rheinland RHSC Souvenir ProgramDocument32 pagesTÜV Rheinland RHSC Souvenir ProgramAnonymous WVaekX9No ratings yet
- Group 2 Internal Control in Cis EnvironmentDocument13 pagesGroup 2 Internal Control in Cis EnvironmentKathlaine Mae ObaNo ratings yet
- Norton AntivirusDocument15 pagesNorton AntivirusMaidenn MarasNo ratings yet
- PAM360 Best Practices GuideDocument46 pagesPAM360 Best Practices GuideaforabadNo ratings yet
- FDA Fact Sheet: The FDA's Role in Medical Device CybersecurityDocument1 pageFDA Fact Sheet: The FDA's Role in Medical Device CybersecurityMaryAnn VanValkenburgNo ratings yet
- Ethical Issues of M-CommerceDocument5 pagesEthical Issues of M-CommerceNk NoviaNo ratings yet
- Mse IndividualDocument16 pagesMse Individualaa AaaNo ratings yet
- Implementing AAA Through Freeradius With MySQL On Ubuntu Server 12Document3 pagesImplementing AAA Through Freeradius With MySQL On Ubuntu Server 12Yohanes SatriaNo ratings yet
- Global Future of Energy 4.0 - Artificial Intelligence and Operational Efficiency Event, 20-21 of June 2019, AmsterdamDocument4 pagesGlobal Future of Energy 4.0 - Artificial Intelligence and Operational Efficiency Event, 20-21 of June 2019, AmsterdamNorman JoshiNo ratings yet
- Login VPDDocument2 pagesLogin VPDJukeNo ratings yet
- A+ PracticeDocument83 pagesA+ Practicevil33100% (1)
- L 06 SecurityorganizationDocument36 pagesL 06 SecurityorganizationMita PramihapsariNo ratings yet
- Luna EFT Customer Release Notes - PN007-011454-001 - RevT - M090900EDocument13 pagesLuna EFT Customer Release Notes - PN007-011454-001 - RevT - M090900Efiqur1No ratings yet
- Final Group Project On HackingDocument30 pagesFinal Group Project On HackingPersian PowerNo ratings yet
- Kali Cheat SheetDocument1 pageKali Cheat SheetCristiana HandreaNo ratings yet