Professional Documents
Culture Documents
Lab Manual SPCC
Lab Manual SPCC
Uploaded by
enggeng7Copyright:
Available Formats
You might also like
- Architecture of The Pentium MicroprocessorDocument12 pagesArchitecture of The Pentium Microprocessorenggeng7No ratings yet
- Sales Achievement PredictorDocument1 pageSales Achievement PredictorusamainNo ratings yet
- At The End of The Lesson, 80% of The Students Should Be Able To: 1. Find The Sum of The Measures of The Exterior Angles of A PolygonDocument5 pagesAt The End of The Lesson, 80% of The Students Should Be Able To: 1. Find The Sum of The Measures of The Exterior Angles of A PolygonBA RTNo ratings yet
- CD Record - 310618104006Document200 pagesCD Record - 310618104006Ajay BharadwajNo ratings yet
- Vedant 9564 Batch BDocument125 pagesVedant 9564 Batch BKnow UnknownNo ratings yet
- System Software and Compiler Design LaboratoryDocument33 pagesSystem Software and Compiler Design LaboratoryBeing FantasticNo ratings yet
- Lab 4 MCSE - 207 - SuyashDocument25 pagesLab 4 MCSE - 207 - SuyashSuyash VishwakarmaNo ratings yet
- CS2304 System Software UNIT I NOTES PDFDocument9 pagesCS2304 System Software UNIT I NOTES PDFPavankumar PkNo ratings yet
- KCG College of Technology, Chennai-96 Computer Science and EngineeringDocument9 pagesKCG College of Technology, Chennai-96 Computer Science and EngineeringTeja ReddyNo ratings yet
- M.Tech ES ARM LABDocument14 pagesM.Tech ES ARM LABdownloadscribdpdfNo ratings yet
- Lab Manual: Subject Name: Subject Code: Programme Name: B.Tech. CSE Regulation: 2018Document52 pagesLab Manual: Subject Name: Subject Code: Programme Name: B.Tech. CSE Regulation: 2018wogamNo ratings yet
- Cs 9303 System Software Internals: V.P Jaya ChitraDocument88 pagesCs 9303 System Software Internals: V.P Jaya ChitraSagar ChingaliNo ratings yet
- Report MPA On Assembler in C++Document17 pagesReport MPA On Assembler in C++Randhir SinghNo ratings yet
- SS Lab ManualDocument60 pagesSS Lab ManualDennis Ebenezer DhanarajNo ratings yet
- Exp 6Document5 pagesExp 6ettedirishwanthNo ratings yet
- Experiment No1 SPCCDocument8 pagesExperiment No1 SPCCChetan GaikarNo ratings yet
- DAA LabDocument39 pagesDAA LabRemiNo ratings yet
- System Software Lab ManualDocument42 pagesSystem Software Lab ManualSHIVALKAR J85% (20)
- Aim: To Implement First Pass of Two Pass Assembler For IBM 360/370 Objective: Develop A Program To Implement First PassDocument4 pagesAim: To Implement First Pass of Two Pass Assembler For IBM 360/370 Objective: Develop A Program To Implement First Passchinmayee daliNo ratings yet
- Distributed System Lab ManualDocument62 pagesDistributed System Lab ManualIrfaan Khan Qasmi75% (4)
- CS1203 System Software UNIT I Question AnsDocument10 pagesCS1203 System Software UNIT I Question AnskeerthisivaNo ratings yet
- Object Oriented ProgrammingDocument53 pagesObject Oriented ProgrammingAdnan Alam KhanNo ratings yet
- SPOS Lab ManualDocument63 pagesSPOS Lab ManualAaditya Iyer83% (6)
- CS2209 - Oops Lab ManualDocument62 pagesCS2209 - Oops Lab ManualSelva Kanmani100% (1)
- System C Usage TutorialDocument38 pagesSystem C Usage TutorialJeffrey BrownNo ratings yet
- Final - OOPJ Lab ManualDocument36 pagesFinal - OOPJ Lab Manualchavanpraful0525No ratings yet
- Name: Yuvraj Sharma GR No: 21910694 Roll No: 324054 Batch: D3Document5 pagesName: Yuvraj Sharma GR No: 21910694 Roll No: 324054 Batch: D3YUVRAJ SHARMANo ratings yet
- Compiler Lab ManualDocument26 pagesCompiler Lab ManualVenu Pmu50% (2)
- BCSE307P - Compiler Lab ManualDocument48 pagesBCSE307P - Compiler Lab Manualsaisivani.ashok2021No ratings yet
- Distributed System Lab ManualDocument62 pagesDistributed System Lab ManualSachin Pukale100% (1)
- Exp 1Document6 pagesExp 1Aryan TiwariNo ratings yet
- Assembler 2 PassDocument13 pagesAssembler 2 PasssukruthkrishnaNo ratings yet
- HPCDocument7 pagesHPCSmita ShresthaNo ratings yet
- Cs8602 Lab ManualDocument28 pagesCs8602 Lab ManualpriyapNo ratings yet
- Engineering Lab Manuals - CS2308 - System Software LM PDFDocument14 pagesEngineering Lab Manuals - CS2308 - System Software LM PDFAjith SureshNo ratings yet
- StMat Computer SCDocument45 pagesStMat Computer SCSiddhant GangapurwalaNo ratings yet
- Part - A: (Choose Any 5)Document7 pagesPart - A: (Choose Any 5)Sam RNo ratings yet
- LP-1 Lab ManualDocument31 pagesLP-1 Lab ManualGamer studioNo ratings yet
- Expt 7pass1 AssemblerDocument5 pagesExpt 7pass1 AssemblerKaitlyn beckhamNo ratings yet
- SsDocument60 pagesSsponns100% (1)
- Labmanual Compiler DesignDocument65 pagesLabmanual Compiler Designsridharegsp100% (3)
- Lab Syllabus r2008Document15 pagesLab Syllabus r2008prisci_duraiNo ratings yet
- Computer Science ProjectDocument16 pagesComputer Science ProjectOjas TaoriNo ratings yet
- CA Classes-51-55Document5 pagesCA Classes-51-55SrinivasaRaoNo ratings yet
- W.E.F. 11 Dec 2018: Faculty: Prof. Kamal MistryDocument9 pagesW.E.F. 11 Dec 2018: Faculty: Prof. Kamal MistryVedang GupteNo ratings yet
- CD Lab Manual 2024 CtechDocument37 pagesCD Lab Manual 2024 CtechAmar Hain HumNo ratings yet
- Introduction To Algorithms and FlowchartDocument48 pagesIntroduction To Algorithms and FlowchartAbdullah Al-suleimaniNo ratings yet
- M.tech-ECE-Embedded Systems (ES) - SEM1 Course Structure & SyllabiDocument8 pagesM.tech-ECE-Embedded Systems (ES) - SEM1 Course Structure & Syllabisatraj5No ratings yet
- Hardware-Software Co-Partitioning For Distributed Embedded SystemsDocument41 pagesHardware-Software Co-Partitioning For Distributed Embedded SystemsRaghu RamNo ratings yet
- Compiler LabDocument4 pagesCompiler LabNambiRajaNo ratings yet
- SP (Simple Processor) SpecificationDocument4 pagesSP (Simple Processor) SpecificationrisirarocksNo ratings yet
- CS2304 System Software UNIT I NOTESDocument9 pagesCS2304 System Software UNIT I NOTESClashing with DeepakNo ratings yet
- C++ ExercisesDocument83 pagesC++ ExercisesAbdelrahman Elattar50% (2)
- Aviral DT 1.2Document11 pagesAviral DT 1.2Aman Pratap SinghNo ratings yet
- Compiler Design LabDocument15 pagesCompiler Design LabMosaddek Hossain100% (1)
- C Programming for the Pc the Mac and the Arduino Microcontroller SystemFrom EverandC Programming for the Pc the Mac and the Arduino Microcontroller SystemNo ratings yet
- Embedded Software Design and Programming of Multiprocessor System-on-Chip: Simulink and System C Case StudiesFrom EverandEmbedded Software Design and Programming of Multiprocessor System-on-Chip: Simulink and System C Case StudiesNo ratings yet
- Python Advanced Programming: The Guide to Learn Python Programming. Reference with Exercises and Samples About Dynamical Programming, Multithreading, Multiprocessing, Debugging, Testing and MoreFrom EverandPython Advanced Programming: The Guide to Learn Python Programming. Reference with Exercises and Samples About Dynamical Programming, Multithreading, Multiprocessing, Debugging, Testing and MoreNo ratings yet
- Introduction to Python Programming: Do your first steps into programming with pythonFrom EverandIntroduction to Python Programming: Do your first steps into programming with pythonNo ratings yet
- Projects With Microcontrollers And PICCFrom EverandProjects With Microcontrollers And PICCRating: 5 out of 5 stars5/5 (1)
- Subject:-Engineering Mathematics III Class: - SE-IT Subject Code:-ITC 301 Module Number: - 3 Fourier SeriesDocument19 pagesSubject:-Engineering Mathematics III Class: - SE-IT Subject Code:-ITC 301 Module Number: - 3 Fourier Seriesenggeng7No ratings yet
- Sr. Number: Name of Participant: Email ID: Mobile NumberDocument5 pagesSr. Number: Name of Participant: Email ID: Mobile Numberenggeng7No ratings yet
- Mapping 1 PracticalDocument12 pagesMapping 1 Practicalenggeng7No ratings yet
- Sec8 1Document16 pagesSec8 1enggeng7No ratings yet
- Superscalar ArchitectureDocument9 pagesSuperscalar Architectureenggeng7No ratings yet
- Poiuytteewqqasdfghgjlol, MNNCBBVBF Hfghtyu654256758787685634 Efyhf Tughjghdxfx BCGNH GFDGDGFGH GJGHDXGFHGJH FGDGFJHKGHDFG FHGFD FGD GFDH FG SDGJH G JDFGFSHDFHJ FGJ SF FHDF GJDF GHDFH GDocument1 pagePoiuytteewqqasdfghgjlol, MNNCBBVBF Hfghtyu654256758787685634 Efyhf Tughjghdxfx BCGNH GFDGDGFGH GJGHDXGFHGJH FGDGFJHKGHDFG FHGFD FGD GFDH FG SDGJH G JDFGFSHDFHJ FGJ SF FHDF GJDF GHDFH Genggeng7No ratings yet
- Pillai HOC College of Engineering and Technology, RasayaniDocument1 pagePillai HOC College of Engineering and Technology, Rasayanienggeng7No ratings yet
- #Include Void Main (Printf ("Hello SANDEEP/n") )Document1 page#Include Void Main (Printf ("Hello SANDEEP/n") )enggeng7No ratings yet
- Course File Programming and Problem Solving in CDocument10 pagesCourse File Programming and Problem Solving in Cenggeng7No ratings yet
- Te CN Lab ManualDocument58 pagesTe CN Lab Manualenggeng7No ratings yet
- List of Experiments OOPM16Document3 pagesList of Experiments OOPM16enggeng7No ratings yet
- Diagram: Use Case Diagram Page 1Document1 pageDiagram: Use Case Diagram Page 1enggeng7No ratings yet
- Exp 10 DFSDocument4 pagesExp 10 DFSenggeng7No ratings yet
- Vehicle Management SystemDocument3 pagesVehicle Management Systemenggeng7No ratings yet
- Thermo 1 & 2Document4 pagesThermo 1 & 2Oloj YuNo ratings yet
- Tle Grade7n8 Dressmaking Module 3 Week310 PDFDocument10 pagesTle Grade7n8 Dressmaking Module 3 Week310 PDFgilbert datu100% (1)
- Zoning in Processing Facilities 375003 7Document2 pagesZoning in Processing Facilities 375003 7TinnysumardiNo ratings yet
- Nsejs-2023 ST 1Document13 pagesNsejs-2023 ST 1S DNo ratings yet
- Seagate DiscWizard User GuideDocument68 pagesSeagate DiscWizard User GuideTotulRedus RoNo ratings yet
- Kollmorgen B With ServoStar S and CD TB CatalogDocument10 pagesKollmorgen B With ServoStar S and CD TB CatalogElectromateNo ratings yet
- Iot Fundamentals: A Comprehensive Introduction To Iot Theory & ApplicationsDocument97 pagesIot Fundamentals: A Comprehensive Introduction To Iot Theory & ApplicationsMohammed Elyas86% (7)
- Qadm 3Document7 pagesQadm 3Ravi Kiran VithanalaNo ratings yet
- The Umbrella Test PDFDocument2 pagesThe Umbrella Test PDF178317No ratings yet
- Colm Flynn's Debating HandbookDocument57 pagesColm Flynn's Debating HandbookRoland ApareceNo ratings yet
- Homeroom Guidance Learner'S Development Assessment S.Y. 2020-2021Document4 pagesHomeroom Guidance Learner'S Development Assessment S.Y. 2020-2021Marnellie Bautista-ValdezNo ratings yet
- PS3 SolutionsDocument3 pagesPS3 SolutionsYenhao Philip ChenNo ratings yet
- InstructionsDocument2 pagesInstructionsDeepak BoraseNo ratings yet
- 高中高考英语常用单词词性转换及派生Document17 pages高中高考英语常用单词词性转换及派生clarikeiNo ratings yet
- Codeofconduct English 2015Document44 pagesCodeofconduct English 2015Cherry Ann GidaNo ratings yet
- A Detailed Lesson Plan in Science 3Document3 pagesA Detailed Lesson Plan in Science 3Lauren may Villanueva75% (4)
- DS LabDocument46 pagesDS LabKamalStarkNo ratings yet
- Adm Math7 q2 Module1 Revised Final Dec2Document28 pagesAdm Math7 q2 Module1 Revised Final Dec2Random NanaNo ratings yet
- A1 ReviewDocument17 pagesA1 ReviewallenNo ratings yet
- 2018 ICpEP CpE Challenge Mechanics ProgrammingDocument7 pages2018 ICpEP CpE Challenge Mechanics ProgrammingCha FigueroaNo ratings yet
- TIBCO Administrator™: Server Configuration GuideDocument297 pagesTIBCO Administrator™: Server Configuration Guidepankaj somNo ratings yet
- Catastrophe ModelCatastrophe Modelling LingDocument14 pagesCatastrophe ModelCatastrophe Modelling LingneomilanNo ratings yet
- Comp128 ThesisDocument39 pagesComp128 ThesisInfinito SerNo ratings yet
- #142 Two-Stage Ejecting Structure - Technical Tutorial - MISUMIDocument2 pages#142 Two-Stage Ejecting Structure - Technical Tutorial - MISUMIgaliskribdNo ratings yet
- Work Life BalanceDocument10 pagesWork Life BalanceAngelica HalmajanNo ratings yet
- FALLON 1987 Constructivist Coherence Theory of Constitutional InterpretationDocument99 pagesFALLON 1987 Constructivist Coherence Theory of Constitutional InterpretationcarriewydraNo ratings yet
- Osullivan T 09071996 TranscriptDocument2 pagesOsullivan T 09071996 Transcriptapi-380159566No ratings yet
Lab Manual SPCC
Lab Manual SPCC
Uploaded by
enggeng7Original Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Lab Manual SPCC
Lab Manual SPCC
Uploaded by
enggeng7Copyright:
Available Formats
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
Mahatma Education Societys
PILLAI HOC COLLEGE OF ENGINEERING AND TECHNOLOGY, RASAYANI
Lab Manual
System Programming & Compiler
Construction
Program
T.E
Semester
VI
Subject Name
System Programming & Compiler
Construction
Practical In-Charge
Name & Signature
Department of Computer Engineering
I/C HOD
Prof. Sandeep Raskar
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
Mahatma Education Societys
PILLAI HOC COLLEGE OF ENGINEERING AND TECHNOLOGY
ESAY 2014-2015
Department
: Computer Engineering.
Class
: TE
Subject
: System Programming & Compiler Construction
Experiment List
Serial No.
1.
Name of experiment
2.
Study of 360/370 processor with instructions.
Assemblers: 2 pass Assembler.
3.
Macro processor: 2 pass Macro processor.
4.
Lexical analyzer tool : flex
5.
Parser generator tool: Yacc.
6.
Find first() , follow() set of given grammar
7.
Create your library in Linux environment and using it.
8.
Code Generation algorithm.
9.
Code Optimization techniques.
10.
Study ld command in Unix/Linux.
Experiment No. 01
Study of 360/370 processor with instructions
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
Aim: Study of 360/370 processor with instructions.
Theory:
Conclusion:
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
Experiment No. 2
Assemblers: 2 pass Assembler.
Title: Design and implementation of 2 pass assemblers for X86 machine
Theory:
Assembly Language Syntax:
Each line of a program is one of the following:
an instruction
an assembler directive (or pseudo-op)
a comment
Whitespace (between symbols) and case are ignored. Comments (beginning with ;)
are also ignored.
An instruction has the following format:
LABEL OPCODE OPERANDS ; COMMENTS
Example:
ADDR1,R1,R3
ADDR1,R1,#3
LDR6,NUMBER
BRzLOOP
Schemes of translation:
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
I. Two pass translation:
It can handles forward reference easily.
Location counter(LC) processing is done in pass 1 and the symbols defined in the
program are entered into symbol table.
The second pass uses this address information to generate target program.
II. Single pass translation:
Forward reference is handled by back patching.
Data structure of assembler
1
Symbol Table(ST)
1. Mnemonics table or Machine-Operation table (MOT).
2. Pseudo-opcode table (POT)
3. Literal table (LT)
4. Location counter.
Symbol table:
Mnemonic opcode table:
Pseudo-opcode table (POT)
Literal table(LT)
IC:
Address
Opcode fields:
i
Statement class
Department of Computer Engineering
Opcode
Operand
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
i.
code
Operand-2 fields
i. Operand class:
S:symbol
L:literals
ii. code
2-Pass Assembler:
Pass-I
I
Separate symbol, mnemonic and operand fields.
I.
Build the symbol table.
II.
Construct intermediate code.
Pass-II
I
Evaluate fields and generate code.
I.
Process pseudo-opcodes.
Algorithm:
Pass-I
Step1: Initialize all variables:
Loc_cntr=0;
Littab_ptr=0;
Step2: Read line();
Break-words();
Step3: While(opcode!=end)
Read line();
Break-words();
case1: if opcode=start or opcode=small model
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
Loc_cntr=Value in operand field;
Case2: if opcode=lable
Insert_symtab(lable,Loc_cntr);
Case3: if opcode=.data
Code=search_code_MOT(opcode)
Size=search_size_MOT(opcode)
Loc_cntr=Loc_cntr+size;
Generate_ic(DL,code);
Read line();
Break-words();
Insert_symtab(symbol,Loc_cntr);
Case5: else //when opcode is imperative
i
code=search_code_MOT(opcode);
i.
Length=search_size_MOT(opcode);
ii.
Check_operand_literal();
If yes:
Insert_littab(litaral,Loc_cntr)
Littab_ptr++;
If no:
Find operand enry in SYMTAB
Generate IC(IS,code)(S,entry-no);
Loc_cntr=Loc_cntr+size;
Case6:
If opcode=end
i
code=search_code_MOT(opcode);
i.
Length=search_size_MOT(opcode);
Department of Computer Engineering
//statement
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
ii.
Loc_cntr=Loc_cntr+size;
Step4: stop.
Program:
Program for 2 pass Assemblers
#include<stdio.h>
#include<string.h>
#include<conio.h>
void chk_label();
void chk_opcode();
void READ_LINE();
struct optab
{
char
code[10],objcode[10];
}myoptab[3]={
{"LDA","00"},
{"JMP","01"},
{"STA","02"}
};
struct symtab{
char symbol[10];
int addr;
}mysymtab[10];
int startaddr,locctr,symcount=0,length;
char line[20],label[8],opcode[8],operand[8],programname[10];
/*ASSEMBLER PASS 1 */
void PASS1()
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
{
FILE *input,*inter;
input=fopen("input.txt","r");
inter=fopen("inter.txt","w");
printf("LOCATION LABEL\tOPERAND\tOPCODE\n");
printf("_____________________________________");
fgets(line,20,input);
READ_LINE();
if(!strcmp(opcode,"START"))
{
startaddr=atoi(operand);
locctr=startaddr;
strcpy(programname,label);
fprintf(inter,"%s",line);
fgets(line,20,input);
}
else
{
programname[0]='\0';
startaddr=0;
locctr=0;
}
printf("\n %d\t %s\t%s\t %s",locctr,label,opcode,operand);
while(strcmp(line,"END")!=0)
{
READ_LINE();
printf("\n %d\t %s \t%s\t %s",locctr,label,opcode,operand);
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
if(label[0]!='\0')chk_label();
chk_opcode();
fprintf(inter,"%s %s %s\n",label,opcode,operand);
fgets(line,20,input);
}
printf("\n %d\t\t%s",locctr,line);
fprintf(inter,"%s",line);
fclose(inter);
fclose(input);
}
/*Assesmbler pass 2 */
void PASS2()
{
FILE *inter,*output;
char record[30],part[8],value[5];/*Part array was defined as part[6]
previously*/
int currtxtlen=0,foundopcode,foundoperand,chk,operandaddr,recaddr=0;
inter=fopen("inter.txt","r");
output=fopen("output.txt","w");
fgets(line,20,inter);
READ_LINE();
if(!strcmp(opcode,"START")) fgets(line,20,inter);
printf("\n\nCorresponding Object code is..\n");
printf("\nH^ %s ^ %d ^ %d ",programname,startaddr,length);
fprintf(output,"\nH^ %s ^ %d ^ %d ",programname,startaddr,length);
recaddr=startaddr; record[0]='\0';
while(strcmp(line,"END")!=0)
{
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
operandaddr=foundoperand=foundopcode=0;
value[0]=part[0]= '\0';
READ_LINE();
for(chk=0;chk<3;chk++)
{
if(!strcmp(opcode,myoptab[chk].code))
{
foundopcode=1;
strcpy(part,myoptab[chk].objcode);
if(operand[0]!='\0')
{
for(chk=0;chk<symcount;chk++)
if(!strcmp(mysymtab[chk].symbol,operand))
{
itoa(mysymtab[chk].addr,value,10);
strcat(part,value);
foundoperand=1;
}
if(!foundoperand)strcat(part,"err");
}
}
}
if(!foundopcode)
{
if(strcmp(opcode,"BYTE")==0 || strcmp(opcode,"WORD")||
strcmp(opcode,"RESB"))
{
strcat(part,operand);
}
}
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
if((currtxtlen+strlen(part))<=8)
/*This step was having buffer overflow issue since part[6]
was defined previously which i corrected to part[8].
Because of this first two bytes of stack are getting lost*/
{
strcat(record,"^");
strcat(record,part);
currtxtlen+=strlen(part);
}
else
{
printf("\nT^ %d ^%d %s",recaddr,currtxtlen,record);
fprintf(output,"\nT^ %d ^%d %s",recaddr,currtxtlen,record);
recaddr+=currtxtlen;
currtxtlen=strlen(part);
strcpy(record,part);
}
fgets(line,20,inter);
}
printf("\nT^ %d ^%d %s",recaddr,currtxtlen,record);
fprintf(output,"\nT^ %d ^%d %s",recaddr,currtxtlen,record);
printf("\nE^ %d\n",startaddr);
fprintf(output,"\nE^ %d\n",startaddr);
fclose(inter);
fclose(output);
}
void READ_LINE()
{
char buff[8],word1[8],word2[8],word3[8];
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
int i,j=0,count=0;
label[0]=opcode[0]=operand[0]=word1[0]=word2[0]=word3[0]='\0';
for(i=0;line[i]!='\0';i++)
{
if(line[i]!=' ')
buff[j++]=line[i];
else
{
buff[j]='\0';
strcpy(word3,word2);
strcpy(word2,word1);
strcpy(word1,buff);
j=0;
count++;
}
}
buff[j-1]='\0';
strcpy(word3,word2);
strcpy(word2,word1);
strcpy(word1,buff);
switch(count)
{
case 0:strcpy(opcode,word1);
break;
case 1:{strcpy(opcode,word2);strcpy(operand,word1);}
break;
case 2:
{strcpy(label,word3);strcpy(opcode,word2);strcpy(operand,word1);}
break;
}
}
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
void chk_label()
{
int k,dupsym=0;
for(k=0;k<symcount;k++)
if(!strcmp(label,mysymtab[k].symbol))
{
mysymtab[k].addr=-1;
dupsym=1;
break;
}
if(!dupsym)
{
strcpy(mysymtab[symcount].symbol,label);
mysymtab[symcount++].addr=locctr;
}
}
void chk_opcode()
{
int k=0,found=0;
for(k=0;k<3;k++)
if(!strcmp(opcode,myoptab[k].code))
{
locctr+=3;
found=1;
break;
}
if(!found)
{
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
if(!strcmp( opcode,"WORD")) locctr+=3;
else if (!strcmp(opcode,"RESW"))locctr+=(3*atoi(operand));
else if(!strcmp(opcode,"RESB"))locctr+=atoi(operand);
}
}
int main()
{
PASS1();
length=locctr-startaddr;
PASS2();
getch();
Conclusion: Thus we have implemented 2 pass assemblers for X86 machine.
Experiment No.3
Macro processor: 2 pass Macro processor.
Title: Design and Implementation of Macro Processor.
Theory: A macro instruction is a notational convenience for the programmer. It allows
the programmer to write shorthand version of a program (module programming). The
macro processor replaces each macro invocation with the corresponding sequence of
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
statements (expanding). Macro processor recognizes macro definitions, save the macro
definition, recognize macro calls, expand macro calls.
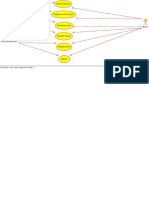
Macro Processor
Source Code
(with macro)
obj
Macro ProcessorExpanded Compiler
Code
or Assembler
Recognize macro definitions
Save the macro definition
Recognize macro calls
Expand macro calls
Examples:
Macro
Start of the definition
Incr
Macro name
Mov ax,10
Sequence to be abbreviated
Add ax,01
Mend
End of definition
Parameterized Macro
macro
&lable incr &arg1, &arg2
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
mov ax,&arg1
&lable add ax, &arg2
sub arg2,1
jnz &lable
Mend
Calll to this macro definition will be:
loop1 incr var1,var2
Conditional Macro
macro
Vary &count, &arg1,&arg2,&arg3
Add ax, &arg1
AIF (&count EQ 1).FINI
Test if &count=1
Add ax,&arg2
AIF (&count EQ 2).FINI
Test if &count=1
Add ax,&arg3
.FINI mend
Label start with (.) and do not appear in the output.
AGO is unconditional branch
AIF is conditional branch
If Call to this macro is:
Vary 3,var1,var2,var3
Expansion will be:
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
Add ax,var1
Add ax,var2
Add ax,var3
If call is:
Vary 2, var1,var2
Expansion will be:
Add ax,var1
Ad ax,var2
Nested Macro
1
Macro calls within macro
Macro
Add1 &arg1
Mov ax,&arg2
Add ax,1
Mend
Macro
Adds &arg1,&arg2
Add1 &arg1
Add1 &arg2
1. Macro Instruction defining macros:
macro
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
define &sub
macro
&sub &y
mov ax,&y
sub ax,01
mend
mend
Recursive Macro
macro
Incr &arg1
Mov ax, &arg1
Add ax,1
AIF (&arg1 EQ 10) .L1
Incr arg1
.L1 mend
Design of simple macro processor
.small model
Macro
ABC &a, &a2
Mov ax, &a1
Add ax,&a2
Mend
.data
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
Var1 db 10
.code
ABC 10,20
end
Expanded code will be:
.small model
.data
Var1 db 10
.code
Mov ax,10
Add ax,20
end
Algorithm
Pass 1:
1 Both counters for MDT and MNT i.e. MDTC and MNTC are initialized
first.
1. Macro process in first pass reads each and every line of source code.
2. If it is macro pseudo opcode, the entire macro definition that follows is
saved in MDT
3. The macro name is entered in MNT.
4. When MEND pseudo opcode is encountered that means all macro definition
have been processed, so transfer control to pass2.
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
Pass 2:
1. Read source code supplied by pass1to see opcode mnemonic of each line is
present in MNT or not.
2. When call is found, the MDTP is set to corresponding macro definition
stored in MDT.
3. The positional vs actual parameter list is prepared. Each line from MDT is
read and positional parameter is replaced by actual parameter.
4. Scanning of input file continues.
5. When MEND pseudo output is countered, MDT terminates expansion of
6. macro.
7. When END pseudo output is encountered, expansion code is transferred to
assembler for further processing.
Program:
#include<stdio.h>
#include<conio.h>
#include<string.h>
#include<stdlib.h>
void main()
{
FILE *f1,*f2,*f3;char mne[20],opnd[20],la[20];clrscr();
f1=fopen("minp2.txt","r");
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
f2=fopen("ntab2.txt","w+");
f3=fopen("dtab2.txt","w+");
fscanf(f1,"%s%s%s",la,mne,opnd);
while(strcmp(mne,"MEND")!=0){if(strcmp(mne,"MACRO")==0){fprintf(f2,"%s\n",la);
fprintf(f3,"%s\t%s\n",la,opnd);
}
elsefprintf(f3,"%s\t%s\n",mne,opnd);
fscanf(f1,"%s%s%s",la,mne,opnd);
}f
printf(f3,"%s",mne);
fclose(f1);
fclose(f2);
fclose(f3);
printf("PASS 1 is successful");
getch();
}
Input file:
minp2.txt
EX1
MACRO &A,&B
LDA
&A
STA
&B
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
minp2.txt
-
MEND
SAMPLE START
1000
EX1
N1,N2
N1
RESW
N2
RESW
END
Output files:
dtab2.txt
EX1
&A,&B
LDA
&A
STA
&B
MEND
ntab2.txt
EX1
Conclusion: Thus we have implemented Macro Processor.
EXPERIMENT NO. 4
Lexical analyzer tool : flex
Title: Design a Lexical Analyzer for a language whose grammar is known.
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
Theory:
Structure of a lex file
The structure of a lex file is intentionally similar to that of a yacc file; files are divided up
into three sections, separated by lines that contain only two percent signs, as follows:
Definition section
%%
Rules section
%%
C code section
The definition section is the place to define macros and to import header files
written in C. It is also possible to write any C code here, which will be copied
verbatim into the generated source file.
The rules section is the most important section; it associates patterns with C
statements. Patterns are simply regular expressions. When the lexer sees some text
in the input matching a given pattern, it executes the associated C code. This is the
basis of how lex operates.
The C code section contains C statements and functions that are copied verbatim
to the generated source file. These statements presumably contain code called by
the rules in the rules section. In large programs it is more convenient to place this
code in a separate file and link it in at compile time.
Program:
/***Program to count the number of characters,words,spaces,end of lines from the
given input line***/
%{
#include <stdio.h>
int charcount=0,wordcnt=0,spacecnt=0,linecnt=0;
%}
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
WORD[^\t\n,\.:]+ /*for word*/
EOL[\n] /* for end of line */
BLANK[ ] /* for word */
%%
/*** The rule section to identify words,space, and lines***/
/* matches word and counts word and characters */
{word}{wordcnt++;charcnt=charcnt+yyleng;} {BLANK} { spacecnt++;}
/*identify end of line and count line */
{EOL}{linecnt++;}
/* ignore all other and count character */
{charcnt++;}
%%
/* called by lex when input is exhausted.Return 1 if you are done or 0 if more processing
is required*/
int yywrap()
{
return 1;
}
/* The C code section*/
int main(int argc,char *argv[])
{
/* if only one argument not passed to the program*/
if(argc!=2)
{
/* output usage format of the program and exit*/
print (Usage:<./a.out><sourcefile>\n);
exit(0);
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
}
yyin=fopen(argv[1],r);/*read input*/
yylex(); /* call lexer */
/* prime counts */
print(total number of characters=%d\ Total Number of word=%d\n Total number of
spaces=%d\n Total Number of lines=%d.
return 0;
}
Conclusion: Thus we have implemented simple parser using yacc and lex.
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
EXPERIMENT NO. 5
Parser generator tool: Yacc.
Title: Design and Implementation of simple Parser using Lex Yacc.
Theory:
Yacc is the Utility which generates the function 'yyparse' which is indeed the Parser. Yacc
describes a context free , LALR(1) grammar and supports both bottom-up and top-down
parsing.The general format for the YACC file is very similar to that of the Lex file.
1. Declarations
2. Grammar Rules
3. Subroutines
Basic Specifications:Names refer to either tokens or nonterminal symbols. Yacc requires
token names to be declared as such. In addition, for reasons discussed in Section 3, it is
often desirable to include the lexical analyzer as part of the specification file; it may be
useful to include other programs as well. Thus, every specification file consists of three
sections: the declarations, (grammar) rules, and programs. The sections are separated by
double percent ``%%'' marks. (The percent ``%'' is generally used in Yacc specifications as
an escape character.)
In other words, a full specification file looks like
declarations
%%
rules
%%
programs
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
The declaration section may be empty. Moreover, if the programs section is omitted, the
second %% mark may be omitted also;
thus, the smallest legal Yacc specification is
%%
Rules
Program:
//IMPLEMENT A NATURL LANGUAGE PARSER USING LEX & YACC
//LEX FILE
%{
/*Recognising parts of speech*/
#include "y.tab.h"
%}
VERB
"is"|"am"|"are"|"were"|"was"|"be"|"being"|"been"|"do"|"does"|"did"|"will"|"has"|"have"|"ha
d"
ADVERB "very"|"simply"|"gently"|"quietly"|"calmly"|"angrily"
PRONOUN "she"|"we"|"they"|"I"|"you"|"he"|"it"
ARTICLE "a"|"an"|"the"
%%
{VERB}
{printf("\nverb");
return(VERB);
}
{ADVERB} {printf("\nadverb");
return(ADVERB);
}
{PRONOUN} {printf("\npronoun");
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
return(PRONOUN);
}
{ARTICLE} {printf("\narticle");
return(ARTICLE);
}
[a-zA-Z]+
{printf("\nnoun");
return(NOUN);
}
%%
//YACC FILE
%{
/*To recognise english sentences*/
#include<stdio.h>
%}
%token NOUN PRONOUN VERB ADVERB ARTICLE
%%
sentence: subject VERB object {printf("\nSentence is valid");}
;
subject: ARTICLE NOUN
| NOUN
| ARTICLE PRONOUN
| PRONOUN
;
object: ARTICLE NOUN
| NOUN
;
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
%%
extern FILE *yyin;
main()
{
do{
yyparse();
}while(!feof(yyin));
}
yyerror(s)
{
fprintf(stderr,"%s\n",s);}
//OUTPUT
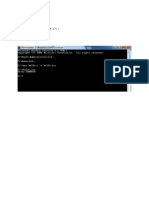
[root@localhost assign3]# lex natural.l
[root@localhost assign3]# yacc -d natural.y
[root@localhost assign3]# gcc lex.yy.c y.tab.c -lfl
[root@localhost assign3]# ./a.out
Ram is a boy
noun
verb
article
noun
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
Sentence is valid
Conclusion: Thus we have implemented simple parser using yacc and lex.
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
Experiment No.6
Find first() , follow() set of given grammar
Title: Find first(),follow() set of given grammer.
Theory:
Automatic techniques for constructing parsers start with computing
some basic functions for symbols in the grammar. These functions are
useful in understanding both recursive descent and bottom-up LR
parsers.
First(a)
First(a) is the set of terminals that begin strings derived from a, which can include epsilon.
1.
2.
3.
4.
First(X) starts with the empty set.
if X is a terminal, First(X) is {X}.
if X -> epsilon is a production, add epsilon to First(X).
if X is a non-terminal and X -> Y1 Y2 ... Yk is a production, add First(Y1) to
First(X).
5. for (i = 1; if Yi can derive epsilon; i++)
add First(Yi+1) to First(X)
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
Follow(A)
Follow(A) for nonterminal A is the set of terminals that can appear immediately to the
right of A in some sentential form S -> aAxB... To compute Follow, apply these rules to all
nonterminals in the grammar:
1. Add $ to Follow(S)
2. if A -> aBb then add First(b) - epsilon to Follow(B)
3. if A -> aB or A -> aBb where epsilon is in First(b), then add Follow(A) to
Follow(B).
Program:
C code to Find First and Follow in a given Grammar
/* C program to find First and Follow in a given Grammar. */
#include<stdio.h>
#include<string.h>
int i,j,l,m,n=0,o,p,nv,z=0,x=0;
char str[10],temp,temp2[10],temp3[20],*ptr;
struct prod
{
char lhs[10],rhs[10][10],ft[10],fol[10];
int n;
}pro[10];
void findter()
{
int k,t;
for(k=0;k<n;k++)
{
if(temp==pro[k].lhs[0])
{
for(t=0;t<pro[k].n;t++)
{
if( pro[k].rhs[t][0]<65 || pro[k].rhs[t][0]>90 )
pro[i].ft[strlen(pro[i].ft)]=pro[k].rhs[t][0];
else if( pro[k].rhs[t][0]>=65 && pro[k].rhs[t][0]<=90 )
{
temp=pro[k].rhs[t][0];
if(temp=='S')
pro[i].ft[strlen(pro[i].ft)]='#';
findter();
}
}
break;
}
}
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
void findfol()
{
int k,t,p1,o1,chk;
char *ptr1;
for(k=0;k<n;k++)
{
chk=0;
for(t=0;t<pro[k].n;t++)
{
ptr1=strchr(pro[k].rhs[t],temp);
if( ptr1 )
{
p1=ptr1-pro[k].rhs[t];
if(pro[k].rhs[t][p1+1]>=65 && pro[k].rhs[t][p1+1]<=90)
{
for(o1=0;o1<n;o1++)
if(pro[o1].lhs[0]==pro[k].rhs[t][p1+1])
{
strcat(pro[i].fol,pro[o1].ft);
chk++;
}
}
else if(pro[k].rhs[t][p1+1]=='\0')
{
temp=pro[k].lhs[0];
if(pro[l].rhs[j][p]==temp)
continue;
if(temp=='S')
strcat(pro[i].fol,"$");
findfol();
chk++;
}
else
{
pro[i].fol[strlen(pro[i].fol)]=pro[k].rhs[t][p1+1];
chk++;
}
}
}
if(chk>0)
break;
}
}
void main()
{
FILE *f;
clrscr();
for(i=0;i<10;i++)
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
pro[i].n=0;
f=fopen("tab5.txt","r");
while(!feof(f))
{
fscanf(f,"%s",pro[n].lhs);
if(n>0)
{
if( strcmp(pro[n].lhs,pro[n-1].lhs) == 0 )
{
pro[n].lhs[0]='\0';
fscanf(f,"%s",pro[n-1].rhs[pro[n-1].n]);
pro[n-1].n++;
continue;
}
}
fscanf(f,"%s",pro[n].rhs[pro[n].n]);
pro[n].n++;
n++;
}
printf("\n\nTHE GRAMMAR IS AS FOLLOWS\n\n");
for(i=0;i<n;i++)
for(j=0;j<pro[i].n;j++)
printf("%s -> %s\n",pro[i].lhs,pro[i].rhs[j]);
pro[0].ft[0]='#';
for(i=0;i<n;i++)
{
for(j=0;j<pro[i].n;j++)
{
if( pro[i].rhs[j][0]<65 || pro[i].rhs[j][0]>90 )
{
pro[i].ft[strlen(pro[i].ft)]=pro[i].rhs[j][0];
}
else if( pro[i].rhs[j][0]>=65 && pro[i].rhs[j][0]<=90 )
{
temp=pro[i].rhs[j][0];
if(temp=='S')
pro[i].ft[strlen(pro[i].ft)]='#';
findter();
}
}
}
printf("\n\nFIRST\n");
for(i=0;i<n;i++)
{
printf("\n%s -> ",pro[i].lhs);
for(j=0;j<strlen(pro[i].ft);j++)
{
for(l=j-1;l>=0;l--)
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
if(pro[i].ft[l]==pro[i].ft[j])
break;
if(l==-1)
printf("%c",pro[i].ft[j]);
}
}
for(i=0;i<n;i++)
temp2[i]=pro[i].lhs[0];
pro[0].fol[0]='$';
for(i=0;i<n;i++)
{
for(l=0;l<n;l++)
{
for(j=0;j<pro[i].n;j++)
{
ptr=strchr(pro[l].rhs[j],temp2[i]);
if( ptr )
{
p=ptr-pro[l].rhs[j];
if(pro[l].rhs[j][p+1]>=65 && pro[l].rhs[j][p+1]<=90)
{
for(o=0;o<n;o++)
if(pro[o].lhs[0]==pro[l].rhs[j][p+1])
strcat(pro[i].fol,pro[o].ft);
}
else if(pro[l].rhs[j][p+1]=='\0')
{
temp=pro[l].lhs[0];
if(pro[l].rhs[j][p]==temp)
continue;
if(temp=='S')
strcat(pro[i].fol,"$");
findfol();
}
else
pro[i].fol[strlen(pro[i].fol)]=pro[l].rhs[j][p+1];
}
}
}
}
printf("\n\nFOLLOW\n");
for(i=0;i<n;i++)
{
printf("\n%s -> ",pro[i].lhs);
for(j=0;j<strlen(pro[i].fol);j++)
{
for(l=j-1;l>=0;l--)
if(pro[i].fol[l]==pro[i].fol[j])
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
break;
if(l==-1)
printf("%c",pro[i].fol[j]);
}
}
getch();
}
Input File For First and Follow Program:
S ABE
Sa
Ap
At
B Aq
Sf
Aw
Conclusion: Thus we have implemented Find First and Follow in a given Grammar
EXPERIMENT NO. 8
Code Generation algorithm.
Title: Study of code genration algorithm.
Theory:
In computing, code generation is the process by which a compiler's code generator
converts some intermediate representation of source code into a form (e.g., machine code)
that can be readily executed by a machine.
Sophisticated compilers typically perform multiple passes over various
intermediate forms. This multi-stage process is used because many algorithms for code
optimization are easier to apply one at a time, or because the input to one optimization
relies on the completed processing performed by another optimization. This organization
also facilitates the creation of a single compiler that can target multiple architectures, as
only the last of the code generation stages (the backend) needs to change from target to
target. (For more information on compiler design, see Compiler.)
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
The input to the code generator typically consists of a parse tree or an abstract
syntax tree. The tree is converted into a linear sequence of instructions, usually in an
intermediate language such as three address code. Further stages of compilation may or
may not be referred to as "code generation", depending on whether they involve a
significant change in the representation of the program. (For example, a peephole
optimization pass would not likely be called "code generation", although a code generator
might incorporate a peephole optimization pass.)
Major tasks in code generation
In addition to the basic conversion from an intermediate representation into a linear
sequence of machine instructions, a typical code generator tries to optimize the generated
code in some way.
Tasks which are typically part of a sophisticated compiler's "code generation" phase
include:
Instruction selection: which instructions to use.
Instruction scheduling: in which order to put those instructions. Scheduling is a
speed optimization that can have a critical effect on pipelined machines.
Register allocation: the allocation of variables to processor registers[1]
Debug data generation if required so the code can be debugged.
Instruction selection is typically carried out by doing a recursive postorder traversal on the
abstract syntax tree, matching particular tree configurations against templates; for
example, the tree W:= ADD(X,MUL(Y,Z)) might be transformed into a linear sequence
of instructions by recursively generating the sequences for t1:= X and t2:=
MUL(Y,Z), and then emitting the instruction ADD W, t1, t2.
In a compiler that uses an intermediate language, there may be two instruction selection
stages one to convert the parse tree into intermediate code, and a second phase much
later to convert the intermediate code into instructions from the instruction set of the target
machine. This second phase does not require a tree traversal; it can be done linearly, and
typically involves a simple replacement of intermediate-language operations with their
corresponding opcodes. However, if the compiler is actually a language translator (for
example, one that converts Eiffel to C), then the second code-generation phase may
involve building a tree from the linear intermediate code.
Role of code generator in a compiler
The final phase in our compiler model is the code generator. It takes as input an
intermediate representation of the source program and produces as output an equivalent
target
program.The requirements traditionally imposed on a code generator are severe. The
output code
must be correct and of high quality, meaning that it should make effective
use of the resources of the target machine. Moreover, the code generator itself should run
efficiently.
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
ISSUES IN THE DESIGN OF CODE GENRATION
Input
three address presentations (quadruples, triples, ...)
Virtual machine presentations (bytecode, stack-machine, ...)
Linear presentation (postfix, ...)
Graphical presentation (syntax trees, DAGs,...)
Target program
-Instruction set architecture (RISC, CISC)
Producing absolute machine-anguage program
Producing relocatable machine-language program
Producing assembly language programs
Instruction Selection
The complexity of mapping IR program into code-sequence for target machine
depends on:
Level of IR (high-level or low-level)
Nature of instruction set (data type support)
Desired quality of generated code (speed and size)
Register Allocation
Selecting the set of variables that will
reside in registers at each point in the
program
Register Assignment
Picking the specific register that a
variable will reside in
Evaluation Order
Selecting the order in which computations are performed
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
Affects the efficiency of the target code
Picking a best order is NP-complete
Some orders require fewer registers than others
Conclusion: Thus we have studied code generation algorithm.
EXPERIMENT NO. 9
Code Optimization techniques.
Title: Implementation of code optimization techniques.
Theory:
PEEPHOLE OPTIMIZATION
A statement-by-statement code-generations strategy often produce target code that
contains redundant instructions and suboptimal constructs .The quality of such target code
can be improved by applying optimizing transformations to the target program. A simple
but effective technique for improving the target code is peephole optimization, a method
for trying to improving the performance of the target program by examining a short
sequence of target instructions (called the peephole) and replacing these instructions by a
shorter or faster sequence, whenever possible. The peephole is a small, moving window on
the target program. The code in the peephole need not contiguous, although some
implementations do require this. We shall give the following examples of program
transformations that are characteristic of peephole optimizations:
Redundant-instructions elimination
Flow-of-control optimizations
Algebraic simplifications
Use of machine idioms
REDUNTANT LOADS AND STORES
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
If we see the instructions sequence
(1) MOV R0,a
(2) (2)MOV a,R0
we can delete instructions (2) because whenever (2) is executed. (1) will ensure that the
value of a is already in register R0.If (2) had a label we could not be sure that (1) was
always executed immediately before (2) and so we could not remove (2).
UNREACHABLE CODE:
Another opportunity for peephole optimizations is the removal of unreachable
instructions. An unlabeled instruction immediately following an unconditional jump may
be removed. This operation can be repeated to eliminate a sequence of instructions. For
example, for debugging purposes, a large program may have within it certain segments
that are executed only if a variable debug is 1.In C, the source code might look like:
#define debug 0
.
If ( debug ) {
Print debugging information
}
In the intermediate representations the if-statement may be translated as:
If debug =1 goto L2
Goto L2
L1: print debugging information
L2:(a)
One obvious peephole optimization is to eliminate jumps over jumps .Thus no matter what
the value of debug, (a) can be replaced by:
If debug 1 goto
Print debugging information
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
L2:(b)
As the argument of the statement of (b) evaluates to a constant true it can be replaced
by
If debug 0 goto L2
Print debugging information
L2: (c)
As the argument of the first statement of (c) evaluates to a constant true, it can be replaced
by goto L2. Then all the statement that print debugging aids are manifestly unreachable
and can be eliminated one at a time.
Conclusion: Thus we have implemented code optimization.
Program
class CO
{
public static void main(String[] args)
{
int i,j,b,k=0;
String op[][]={{"void","main()"," "," "," "," "," "," "},
{"{"," "," "," "," "," "," "," "},
{"pi","=","3.14",",","r","=","5",";"},
{"A","=","pi","*","r","*","r"," "},
{"}"," "," "," "," "," "," "," "}};
String rs[][]=new String[10][10];
String v;char a;
System.out.println("program code is:");
for(i=0;i<5;i++)
{
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
for(j=0;j<8;j++)
{
System.out.print(op[i][j]+" ");
}
System.out.println();
}
for(i=0;i<5;i++)
{
for(j=0;j<8;j++)
{
v=op[i][j];
if(v.compareTo("=")==0)
{
a=op[i][j+1].charAt(0);
if(a>=48 && a<=57)
{
rs[k][0]=op[i][j-1];
rs[k++][1]=op[i][j+1];
}
}
}
}
System.out.println("Identifier\tValue");
for(i=0;i<k;i++)
{
for(j=0;j<2;j++)
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
{
System.out.print(rs[i][j]+"\t");
}
System.out.println();
}
for(i=0;i<5;i++)
{
for(j=0;j<8;j++)
{
for(b=0;b<k;b++)
{
if(rs[b]
[0].compareTo(op[i][j])==0&&op[i][j+1].compareTo("=")!=0)
{
op[i][j]=rs[b][1];
}
}
}
}
System.out.println("program code after code optimization:");
for(i=0;i<5;i++)
{
for(j=0;j<8;j++)
{
System.out.print(op[i][j]+" ");
}
System.out.println();
}
}
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
}
OUTPUT
program code is:
void main()
{
pi = 3.14 , r = 5 ;
A = pi * r * r ;
}
Identifier
Value
pi
3.14
program code after code optimization:
void main()
{
pi = 3.14 , r = 5 ;
A = 3.14 * 5 * 5 ;
}
Conclusion: Thus we have implemented of code optimization techniques.
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
EXPERIMENT NO. 10
Study of ld command in Unix/Linux.
Title: Study of ld command in Unix/Linux.
Theory:
ld combines a number of object and archive files, relocates their data and ties up symbol
references. Usually the last step in compiling a program is to run ld.
ld accepts Linker Command Language files written in a superset of AT&T's Link Editor
Command Language syntax, to provide explicit and total control over the linking process.
This man page does not describe the command language; see the ld entry in "info", or
the manual ld: the GNU linker, for full details on the command language and on other
aspects of the GNU linker.
This version of ld uses the general purpose BFD libraries to operate on object files. This
allows ld to read, combine, and write object files in many different formats---for example,
COFF or "a.out". Different formats may be linked together to produce any available
kind of object file.
Aside from its flexibility, the GNU linker is more helpful than other linkers in providing
diagnostic information. Many linkers abandon execution immediately upon encountering
an error; whenever possible, ld continues executing, allowing you to identify other errors
(or, in some cases, to get an output file in spite of the error).
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
The GNU linker ld is meant to cover a broad range of situations, and to be as compatible as
possible with other linkers. As a result, you have many choices to control its behavior.
OPTIONS
The linker supports a plethora of command-line options, but in actual practice few of them
are used in any particular context. For instance, a frequent use of ld is to link standard
Unix object files on a standard, supported Unix system. On such a system, to link a file
"hello.o":
ld -o <output> /lib/crt0.o hello.o -lc
This tells ld to produce a file called output as the result of linking the file
"/lib/crt0.o" with "hello.o" and the library "libc.a", which will come from
the standard search directories. (See the discussion of the -l option below.)
Some of the command-line options to ld may be specified at any point in the command
line. However, options which refer to files, such as -l or -T, cause the file to be read at the
point at which the option appears in the command line, relative to the object files and other
file options. Repeating non-file options with a different argument will either have no
further effect, or override prior occurrences (those further to the left on the command line)
of that option. Options which may be meaningfully specified more than once are noted in
the descriptions below.
Non-option arguments are object files or archives which are to be linked together. They
may follow, precede, or be mixed in with command-line options, except that an object file
argument may not be placed between an option and its argument.
Usually the linker is invoked with at least one object file, but you can specify other forms
of binary input files using -l, -R, and the script command language. If no binary input files
at all are specified, the linker does not produce any output, and issues the message No
input files.
If the linker can not recognize the format of an object file, it will assume that it is a linker
script. A script specified in this way augments the main linker script used for the link
(either the default linker script or the one specified by using -T). This feature permits the
linker to link against a file which appears to be an object or an archive, but actually merely
defines some symbol values, or uses "INPUT" or "GROUP" to load other objects. Note
that specifying a script in this way merely augments the main linker script; use the -T
option to replace the default linker script entirely.
For options whose names are a single letter, option arguments must either follow the
option letter without intervening whitespace, or be given as separate arguments
immediately following the option that requires them.
For options whose names are multiple letters, either one dash or two can precede the
option name; for example, -trace-symbol and --trace-symbol are equivalent. Note - there
is one exception to this rule. Multiple letter options that start with a lower case 'o' can only
be preceeded by two dashes. This is to reduce confusion with the -o option. So for
example -omagic sets the output file name to magic whereas --omagic sets the NMAGIC
flag on the output.
Arguments to multiple-letter options must either be separated from the option name by an
equals sign, or be given as separate arguments immediately following the option that
requires them. For example, --trace-symbol foo and --trace-symbol=foo are equivalent.
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
Unique abbreviations of the names of multiple-letter options are accepted.
Note - if the linker is being invoked indirectly, via a compiler driver (eg gcc) then all the
linker command line options should be prefixed by -Wl, (or whatever is appropriate for
the particular compiler driver) like this:
gcc -Wl,--startgroup foo.o bar.o -Wl,--endgroup
This is important, because otherwise the compiler driver program may silently drop the
linker options, resulting in a bad link.
Here is a table of the generic command line switches accepted by the GNU linker:
-akeyword
This option is supported for HP/UX compatibility. The keyword argument must be
one of the strings archive, shared, or default. -aarchive is functionally equivalent
to -Bstatic, and the other two keywords are functionally equivalent to -Bdynamic.
This option may be used any number of times.
-Aarchitecture
--architecture=architecture
In the current release of ld, this option is useful only for the Intel 960 family of
architectures. In that ld configuration, the architecture argument identifies the
particular architecture in the 960 family, enabling some safeguards and modifying
the archive-library search path.
Future releases of ld may support similar functionality for other architecture
families.
-b input-format
--format=input-format
ld may be configured to support more than one kind of object file. If your ld is
configured this way, you can use the -b option to specify the binary format for input
object files that follow this option on the command line. Even when ld is configured
to support alternative object formats, you don't usually need to specify this, as ld
should be configured to expect as a default input format the most usual format on
each machine. input-format is a text string, the name of a particular format supported
by the BFD libraries. (You can list the available binary formats with objdump -i.)
You may want to use this option if you are linking files with an unusual binary
format. You can also use -b to switch formats explicitly (when linking object files of
different formats), by including -b input-format before each group of object files in a
particular format.
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
The default format is taken from the environment variable "GNUTARGET".
You can also define the input format from a script, using the command "TARGET";
-c MRI-commandfile
--mri-script=MRI-commandfile
For compatibility with linkers produced by MRI, ld accepts script files written in an
alternate, restricted command language, described in the MRI Compatible Script
Files section of GNU ld documentation. Introduce MRI script files with the option -c;
use the -T option to run linker scripts written in the general-purpose ld scripting
language. If MRI-cmdfile does not exist, ld looks for it in the directories specified by
any -L options.
-d
-dc
-dp
These three options are equivalent; multiple forms are supported for compatibility
with other linkers. They assign space to common symbols even if a relocatable
output file is specified (with -r). The script command
"FORCE_COMMON_ALLOCATION" has the same effect.
-e entry
--entry=entry
Use entry as the explicit symbol for beginning execution of your program, rather
than the default entry point. If there is no symbol named entry, the linker will try to
parse entry as a number, and use that as the entry address (the number will be
interpreted in base 10; you may use a leading 0x for base 16, or a leading 0 for base
8).
-E
--export-dynamic
When creating a dynamically linked executable, add all symbols to the dynamic
symbol table. The dynamic symbol table is the set of symbols which are visible from
dynamic objects at run time.
If you do not use this option, the dynamic symbol table will normally contain only
those symbols which are referenced by some dynamic object mentioned in the link.
If you use "dlopen" to load a dynamic object which needs to refer back to the
symbols defined by the program, rather than some other dynamic object, then you
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
will probably need to use this option when linking the program itself.
You can also use the version script to control what symbols should be added to the
dynamic symbol table if the output format supports it. See the description of
--version-script in @ref{VERSION}.
-EB
Link big-endian objects. This affects the default output format.
-EL
Link little-endian objects. This affects the default output format.
-f
--auxiliary name
When creating an ELF shared object, set the internal DT_AUXILIARY field to the
specified name. This tells the dynamic linker that the symbol table of the shared
object should be used as an auxiliary filter on the symbol table of the shared object
name.
If you later link a program against this filter object, then, when you run the program,
the dynamic linker will see the DT_AUXILIARY field. If the dynamic linker resolves
any symbols from the filter object, it will first check whether there is a definition in
the shared object name. If there is one, it will be used instead of the definition in the
filter object. The shared object name need not exist. Thus the shared object name
may be used to provide an alternative implementation of certain functions, perhaps
for debugging or for machine specific performance.
This option may be specified more than once. The DT_AUXILIARY entries will be
created in the order in which they appear on the command line.
-F name
--filter name
When creating an ELF shared object, set the internal DT_FILTER field to the specified
name. This tells the dynamic linker that the symbol table of the shared object which
is being created should be used as a filter on the symbol table of the shared object
name.
If you later link a program against this filter object, then, when you run the program,
the dynamic linker will see the DT_FILTER field. The dynamic linker will resolve
symbols according to the symbol table of the filter object as usual, but it will
actually link to the definitions found in the shared object name. Thus the filter object
can be used to select a subset of the symbols provided by the object name.
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
Some older linkers used the -F option throughout a compilation toolchain for
specifying object-file format for both input and output object files. The GNU linker
uses other mechanisms for this purpose: the -b, --format, --oformat options, the
"TARGET" command in linker scripts, and the "GNUTARGET" environment
variable. The GNU linker will ignore the -F option when not creating an ELF shared
object.
-fini name
When creating an ELF executable or shared object, call NAME when the executable
or shared object is unloaded, by setting DT_FINI to the address of the function. By
default, the linker uses "_fini" as the function to call.
-g
Ignored. Provided for compatibility with other tools.
-Gvalue
--gpsize=value
Set the maximum size of objects to be optimized using the GP register to size. This is
only meaningful for object file formats such as MIPS ECOFF which supports putting
large and small objects into different sections. This is ignored for other object file
formats.
-hname
-soname=name
When creating an ELF shared object, set the internal DT_SONAME field to the
specified name. When an executable is linked with a shared object which has a
DT_SONAME field, then when the executable is run the dynamic linker will attempt
to load the shared object specified by the DT_SONAME field rather than the using the
file name given to the linker.
-i
Perform an incremental link (same as option -r).
-init name
When creating an ELF executable or shared object, call NAME when the executable
or shared object is loaded, by setting DT_INIT to the address of the function. By
default, the linker uses "_init" as the function to call.
-larchive
--library=archive
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
Add archive file archive to the list of files to link. This option may be used any
number of times. ld will search its path-list for occurrences of "libarchive.a" for
every archive specified.
On systems which support shared libraries, ld may also search for libraries with
extensions other than ".a". Specifically, on ELF and SunOS systems, ld will search
a directory for a library with an extension of ".so" before searching for one with
an extension of ".a". By convention, a ".so" extension indicates a shared library.
The linker will search an archive only once, at the location where it is specified on
the command line. If the archive defines a symbol which was undefined in some
object which appeared before the archive on the command line, the linker will
include the appropriate file(s) from the archive. However, an undefined symbol in an
object appearing later on the command line will not cause the linker to search the
archive again.
See the -( option for a way to force the linker to search archives multiple times.
You may list the same archive multiple times on the command line.
This type of archive searching is standard for Unix linkers. However, if you are
using ld on AIX, note that it is different from the behaviour of the AIX linker.
-Lsearchdir
--library-path=searchdir
Add path searchdir to the list of paths that ld will search for archive libraries and ld
control scripts. You may use this option any number of times. The directories are
searched in the order in which they are specified on the command line. Directories
specified on the command line are searched before the default directories. All -L
options apply to all -l options, regardless of the order in which the options appear.
If searchdir begins with "=", then the "=" will be replaced by the sysroot prefix, a
path specified when the linker is configured.
The default set of paths searched (without being specified with -L) depends on
which emulation mode ld is using, and in some cases also on how it was configured.
The paths can also be specified in a link script with the "SEARCH_DIR" command.
Directories specified this way are searched at the point in which the linker script
appears in the command line.
-memulation
Emulate the emulation linker. You can list the available emulations with the
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
--verbose or -V options.
If the -m option is not used, the emulation is taken from the "LDEMULATION"
environment variable, if that is defined.
Otherwise, the default emulation depends upon how the linker was configured.
-M
--print-map
Print a link map to the standard output. A link map provides information about the
link, including the following:
*
Where object files and symbols are mapped into memory.
*
How common symbols are allocated.
*
All archive members included in the link, with a mention of the symbol
which caused the archive member to be brought in.
-n
--nmagic
Turn off page alignment of sections, and mark the output as "NMAGIC" if possible.
-N
--omagic
Set the text and data sections to be readable and writable. Also, do not page-align the
data segment, and disable linking against shared libraries. If the output format
supports Unix style magic numbers, mark the output as "OMAGIC".
--no-omagic
This option negates most of the effects of the -N option. It sets the text section to be
read-only, and forces the data segment to be page-aligned. Note - this option does
not enable linking against shared libraries. Use -Bdynamic for this.
-o output
--output=output
Use output as the name for the program produced by ld; if this option is not
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
specified, the name a.out is used by default. The script command "OUTPUT" can
also specify the output file name.
-O level
If level is a numeric values greater than zero ld optimizes the output. This might take
significantly longer and therefore probably should only be enabled for the final
binary.
-q
--emit-relocs
Leave relocation sections and contents in fully linked exececutables. Post link
analysis and optimization tools may need this information in order to perform
correct modifications of executables. This results in larger executables.
This option is currently only supported on ELF platforms.
-r
--relocateable
Generate relocatable output---i.e., generate an output file that can in turn serve as
input to ld. This is often called partial linking. As a side effect, in environments that
support standard Unix magic numbers, this option also sets the output file's magic
number to "OMAGIC". If this option is not specified, an absolute file is produced.
When linking C++ programs, this option will not resolve references to constructors;
to do that, use -Ur.
When an input file does not have the same format as the output file, partial linking is
only supported if that input file does not contain any relocations. Different output
formats can have further restrictions; for example some "a.out"-based formats do
not support partial linking with input files in other formats at all.
This option does the same thing as -i.
-R filename
--just-symbols=filename
Read symbol names and their addresses from filename, but do not relocate it or
include it in the output. This allows your output file to refer symbolically to absolute
locations of memory defined in other programs. You may use this option more than
once.
For compatibility with other ELF linkers, if the -R option is followed by a directory
name, rather than a file name, it is treated as the -rpath option.
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
-s
--strip-all
Omit all symbol information from the output file.
-S
--strip-debug
Omit debugger symbol information (but not all symbols) from the output file.
-t
--trace
Print the names of the input files as ld processes them.
-T scriptfile
--script=scriptfile
Use scriptfile as the linker script. This script replaces ld's default linker script (rather
than adding to it), so commandfile must specify everything necessary to describe the
output file. If scriptfile does not exist in the current directory, "ld" looks for it in
the directories specified by any preceding -L options. Multiple -T options
accumulate.
-u symbol
--undefined=symbol
Force symbol to be entered in the output file as an undefined symbol. Doing this
may, for example, trigger linking of additional modules from standard libraries. -u
may be repeated with different option arguments to enter additional undefined
symbols. This option is equivalent to the "EXTERN" linker script command.
-Ur
For anything other than C++ programs, this option is equivalent to -r: it generates
relocatable output---i.e., an output file that can in turn serve as input to ld. When
linking C++ programs, -Ur does resolve references to constructors, unlike -r. It does
not work to use -Ur on files that were themselves linked with -Ur; once the
constructor table has been built, it cannot be added to. Use -Ur only for the last
partial link, and -r for the others.
--unique[=SECTION]
Creates a separate output section for every input section matching SECTION, or if the
optional wildcard SECTION argument is missing, for every orphan input section. An
orphan section is one not specifically mentioned in a linker script. You may use this
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
option multiple times on the command line; It prevents the normal merging of input
sections with the same name, overriding output section assignments in a linker
script.
-v
--version
-V
Display the version number for ld. The -V option also lists the supported emulations.
-x
--discard-all
Delete all local symbols.
-X
--discard-locals
Delete all temporary local symbols. For most targets, this is all local symbols whose
names begin with L.
-y symbol
--trace-symbol=symbol
Print the name of each linked file in which symbol appears. This option may be
given any number of times. On many systems it is necessary to prepend an
underscore.
This option is useful when you have an undefined symbol in your link but don't
know where the reference is coming from.
-Y path
Add path to the default library search path. This option exists for Solaris
compatibility.
-z keyword
The recognized keywords are "initfirst", "interpose", "loadfltr",
"nodefaultlib", "nodelete", "nodlopen", "nodump", "now",
"origin", "combreloc", "nocombreloc" and "nocopyreloc". The
other keywords are ignored for Solaris compatibility. "initfirst" marks the
object to be initialized first at runtime before any other objects. "interpose"
marks the object that its symbol table interposes before all symbols but the primary
executable. "loadfltr" marks the object that its filtees be processed immediately
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
at runtime. "nodefaultlib" marks the object that the search for dependencies of
this object will ignore any default library search paths. "nodelete" marks the
object shouldn't be unloaded at runtime. "nodlopen" marks the object not
available to "dlopen". "nodump" marks the object can not be dumped by
"dldump". "now" marks the object with the non-lazy runtime binding.
"origin" marks the object may contain $ORIGIN. "defs" disallows undefined
symbols. "muldefs" allows multiple definitions. "combreloc" combines
multiple reloc sections and sorts them to make dynamic symbol lookup caching
possible. "nocombreloc" disables multiple reloc sections combining.
"nocopyreloc" disables production of copy relocs.
-( archives -)
--start-group archives --end-group
The archives should be a list of archive files. They may be either explicit file names,
or -l options.
The specified archives are searched repeatedly until no new undefined references are
created. Normally, an archive is searched only once in the order that it is specified
on the command line. If a symbol in that archive is needed to resolve an undefined
symbol referred to by an object in an archive that appears later on the command line,
the linker would not be able to resolve that reference. By grouping the archives, they
all be searched repeatedly until all possible references are resolved.
Using this option has a significant performance cost. It is best to use it only when
there are unavoidable circular references between two or more archives.
--accept-unknown-input-arch
--no-accept-unknown-input-arch
Tells the linker to accept input files whose architecture cannot be recognised. The
assumption is that the user knows what they are doing and deliberately wants to link
in these unknown input files. This was the default behaviour of the linker, before
release 2.14. The default behaviour from release 2.14 onwards is to reject such input
files, and so the --accept-unknown-input-arch option has been added to restore the
old behaviour.
-assert keyword
This option is ignored for SunOS compatibility.
-Bdynamic
-dy
-call_shared
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
Link against dynamic libraries. This is only meaningful on platforms for which
shared libraries are supported. This option is normally the default on such platforms.
The different variants of this option are for compatibility with various systems. You
may use this option multiple times on the command line: it affects library searching
for -l options which follow it.
-Bgroup
Set the "DF_1_GROUP" flag in the "DT_FLAGS_1" entry in the dynamic section.
This causes the runtime linker to handle lookups in this object and its dependencies
to be performed only inside the group. --no-undefined is implied. This option is
only meaningful on ELF platforms which support shared libraries.
-Bstatic
-dn
-non_shared
-static
Do not link against shared libraries. This is only meaningful on platforms for which
shared libraries are supported. The different variants of this option are for
compatibility with various systems. You may use this option multiple times on the
command line: it affects library searching for -l options which follow it.
-Bsymbolic
When creating a shared library, bind references to global symbols to the definition
within the shared library, if any. Normally, it is possible for a program linked against
a shared library to override the definition within the shared library. This option is
only meaningful on ELF platforms which support shared libraries.
--check-sections
--no-check-sections
Asks the linker not to check section addresses after they have been assigned to see if
there any overlaps. Normally the linker will perform this check, and if it finds any
overlaps it will produce suitable error messages. The linker does know about, and
does make allowances for sections in overlays. The default behaviour can be
restored by using the command line switch --check-sections.
--cref
Output a cross reference table. If a linker map file is being generated, the cross
reference table is printed to the map file. Otherwise, it is printed on the standard
output.
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
The format of the table is intentionally simple, so that it may be easily processed by
a script if necessary. The symbols are printed out, sorted by name. For each symbol,
a list of file names is given. If the symbol is defined, the first file listed is the
location of the definition. The remaining files contain references to the symbol.
--no-define-common
This option inhibits the assignment of addresses to common symbols. The script
command "INHIBIT_COMMON_ALLOCATION" has the same effect.
The --no-define-common option allows decoupling the decision to assign addresses
to Common symbols from the choice of the output file type; otherwise a nonRelocatable output type forces assigning addresses to Common symbols. Using
--no-define-common allows Common symbols that are referenced from a shared
library to be assigned addresses only in the main program. This eliminates the
unused duplicate space in the shared library, and also prevents any possible
confusion over resolving to the wrong duplicate when there are many dynamic
modules with specialized search paths for runtime symbol resolution.
--defsym symbol=expression
Create a global symbol in the output file, containing the absolute address given by
expression. You may use this option as many times as necessary to define multiple
symbols in the command line. A limited form of arithmetic is supported for the
expression in this context: you may give a hexadecimal constant or the name of an
existing symbol, or use "+" and "-" to add or subtract hexadecimal constants or
symbols. If you need more elaborate expressions, consider using the linker
command language from a script. Note: there should be no white space between
symbol, the equals sign (``=''), and expression.
--demangle[=style]
--no-demangle
These options control whether to demangle symbol names in error messages and
other output. When the linker is told to demangle, it tries to present symbol names in
a readable fashion: it strips leading underscores if they are used by the object file
format, and converts C++ mangled symbol names into user readable names. Different
compilers have different mangling styles. The optional demangling style argument
can be used to choose an appropriate demangling style for your compiler. The linker
will demangle by default unless the environment variable
COLLECT_NO_DEMANGLE is set. These options may be used to override the default.
--dynamic-linker file
Set the name of the dynamic linker. This is only meaningful when generating
dynamically linked ELF executables. The default dynamic linker is normally correct;
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
don't use this unless you know what you are doing.
--embedded-relocs
This option is only meaningful when linking MIPS embedded PIC code, generated by
the -membedded-pic option to the GNU compiler and assembler. It causes the linker
to create a table which may be used at runtime to relocate any data which was
statically initialized to pointer values. See the code in testsuite/ld-empic for details.
--fatal-warnings
Treat all warnings as errors.
--force-exe-suffix
Make sure that an output file has a .exe suffix.
If a successfully built fully linked output file does not have a ".exe" or ".dll"
suffix, this option forces the linker to copy the output file to one of the same name
with a ".exe" suffix. This option is useful when using unmodified Unix makefiles
on a Microsoft Windows host, since some versions of Windows won't run an image
unless it ends in a ".exe" suffix.
--no-gc-sections
--gc-sections
Enable garbage collection of unused input sections. It is ignored on targets that do
not support this option. This option is not compatible with -r, nor should it be used
with dynamic linking. The default behaviour (of not performing this garbage
collection) can be restored by specifying --no-gc-sections on the command line.
--help
Print a summary of the command-line options on the standard output and exit.
--target-help
Print a summary of all target specific options on the standard output and exit.
-Map mapfile
Print a link map to the file mapfile. See the description of the -M option, above.
--no-keep-memory
ld normally optimizes for speed over memory usage by caching the symbol tables of
input files in memory. This option tells ld to instead optimize for memory usage, by
rereading the symbol tables as necessary. This may be required if ld runs out of
memory space while linking a large executable.
Department of Computer Engineering
SYSTEM PROGRAMMING & COMPILER CONSTRUCTION
--no-undefined
-z defs
Normally when creating a non-symbolic shared library, undefined symbols are
allowed and left to be resolved by the runtime loader. These options disallows such
undefined symbols.
--allow-multiple-definition
-z muldefs
Normally when a symbol is defined multiple times, the linker will report a fatal
error. These options allow multiple definitions and the first definition will be used.
--allow-shlib-undefined
Allow undefined symbols in shared objects even when --no-undefined is set. The net
result will be that undefined symbols in regular objects will still trigger an error, but
undefined symbols in shared objects will be ignored. The implementation of
no_undefined makes the assumption that the runtime linker will choke on undefined
symbols. However there is at least one system (BeOS) where undefined symbols in
shared libraries is normal since the kernel patches them at load time to select which
function is most appropriate for the current architecture. I.E. dynamically select an
appropriate memset function. Apparently it is also normal for HPPA shared libraries
to have undefined symbols.
Conclusion: Thus we have studied ld command in Unix/Linux.
Department of Computer Engineering
You might also like
- Architecture of The Pentium MicroprocessorDocument12 pagesArchitecture of The Pentium Microprocessorenggeng7No ratings yet
- Sales Achievement PredictorDocument1 pageSales Achievement PredictorusamainNo ratings yet
- At The End of The Lesson, 80% of The Students Should Be Able To: 1. Find The Sum of The Measures of The Exterior Angles of A PolygonDocument5 pagesAt The End of The Lesson, 80% of The Students Should Be Able To: 1. Find The Sum of The Measures of The Exterior Angles of A PolygonBA RTNo ratings yet
- CD Record - 310618104006Document200 pagesCD Record - 310618104006Ajay BharadwajNo ratings yet
- Vedant 9564 Batch BDocument125 pagesVedant 9564 Batch BKnow UnknownNo ratings yet
- System Software and Compiler Design LaboratoryDocument33 pagesSystem Software and Compiler Design LaboratoryBeing FantasticNo ratings yet
- Lab 4 MCSE - 207 - SuyashDocument25 pagesLab 4 MCSE - 207 - SuyashSuyash VishwakarmaNo ratings yet
- CS2304 System Software UNIT I NOTES PDFDocument9 pagesCS2304 System Software UNIT I NOTES PDFPavankumar PkNo ratings yet
- KCG College of Technology, Chennai-96 Computer Science and EngineeringDocument9 pagesKCG College of Technology, Chennai-96 Computer Science and EngineeringTeja ReddyNo ratings yet
- M.Tech ES ARM LABDocument14 pagesM.Tech ES ARM LABdownloadscribdpdfNo ratings yet
- Lab Manual: Subject Name: Subject Code: Programme Name: B.Tech. CSE Regulation: 2018Document52 pagesLab Manual: Subject Name: Subject Code: Programme Name: B.Tech. CSE Regulation: 2018wogamNo ratings yet
- Cs 9303 System Software Internals: V.P Jaya ChitraDocument88 pagesCs 9303 System Software Internals: V.P Jaya ChitraSagar ChingaliNo ratings yet
- Report MPA On Assembler in C++Document17 pagesReport MPA On Assembler in C++Randhir SinghNo ratings yet
- SS Lab ManualDocument60 pagesSS Lab ManualDennis Ebenezer DhanarajNo ratings yet
- Exp 6Document5 pagesExp 6ettedirishwanthNo ratings yet
- Experiment No1 SPCCDocument8 pagesExperiment No1 SPCCChetan GaikarNo ratings yet
- DAA LabDocument39 pagesDAA LabRemiNo ratings yet
- System Software Lab ManualDocument42 pagesSystem Software Lab ManualSHIVALKAR J85% (20)
- Aim: To Implement First Pass of Two Pass Assembler For IBM 360/370 Objective: Develop A Program To Implement First PassDocument4 pagesAim: To Implement First Pass of Two Pass Assembler For IBM 360/370 Objective: Develop A Program To Implement First Passchinmayee daliNo ratings yet
- Distributed System Lab ManualDocument62 pagesDistributed System Lab ManualIrfaan Khan Qasmi75% (4)
- CS1203 System Software UNIT I Question AnsDocument10 pagesCS1203 System Software UNIT I Question AnskeerthisivaNo ratings yet
- Object Oriented ProgrammingDocument53 pagesObject Oriented ProgrammingAdnan Alam KhanNo ratings yet
- SPOS Lab ManualDocument63 pagesSPOS Lab ManualAaditya Iyer83% (6)
- CS2209 - Oops Lab ManualDocument62 pagesCS2209 - Oops Lab ManualSelva Kanmani100% (1)
- System C Usage TutorialDocument38 pagesSystem C Usage TutorialJeffrey BrownNo ratings yet
- Final - OOPJ Lab ManualDocument36 pagesFinal - OOPJ Lab Manualchavanpraful0525No ratings yet
- Name: Yuvraj Sharma GR No: 21910694 Roll No: 324054 Batch: D3Document5 pagesName: Yuvraj Sharma GR No: 21910694 Roll No: 324054 Batch: D3YUVRAJ SHARMANo ratings yet
- Compiler Lab ManualDocument26 pagesCompiler Lab ManualVenu Pmu50% (2)
- BCSE307P - Compiler Lab ManualDocument48 pagesBCSE307P - Compiler Lab Manualsaisivani.ashok2021No ratings yet
- Distributed System Lab ManualDocument62 pagesDistributed System Lab ManualSachin Pukale100% (1)
- Exp 1Document6 pagesExp 1Aryan TiwariNo ratings yet
- Assembler 2 PassDocument13 pagesAssembler 2 PasssukruthkrishnaNo ratings yet
- HPCDocument7 pagesHPCSmita ShresthaNo ratings yet
- Cs8602 Lab ManualDocument28 pagesCs8602 Lab ManualpriyapNo ratings yet
- Engineering Lab Manuals - CS2308 - System Software LM PDFDocument14 pagesEngineering Lab Manuals - CS2308 - System Software LM PDFAjith SureshNo ratings yet
- StMat Computer SCDocument45 pagesStMat Computer SCSiddhant GangapurwalaNo ratings yet
- Part - A: (Choose Any 5)Document7 pagesPart - A: (Choose Any 5)Sam RNo ratings yet
- LP-1 Lab ManualDocument31 pagesLP-1 Lab ManualGamer studioNo ratings yet
- Expt 7pass1 AssemblerDocument5 pagesExpt 7pass1 AssemblerKaitlyn beckhamNo ratings yet
- SsDocument60 pagesSsponns100% (1)
- Labmanual Compiler DesignDocument65 pagesLabmanual Compiler Designsridharegsp100% (3)
- Lab Syllabus r2008Document15 pagesLab Syllabus r2008prisci_duraiNo ratings yet
- Computer Science ProjectDocument16 pagesComputer Science ProjectOjas TaoriNo ratings yet
- CA Classes-51-55Document5 pagesCA Classes-51-55SrinivasaRaoNo ratings yet
- W.E.F. 11 Dec 2018: Faculty: Prof. Kamal MistryDocument9 pagesW.E.F. 11 Dec 2018: Faculty: Prof. Kamal MistryVedang GupteNo ratings yet
- CD Lab Manual 2024 CtechDocument37 pagesCD Lab Manual 2024 CtechAmar Hain HumNo ratings yet
- Introduction To Algorithms and FlowchartDocument48 pagesIntroduction To Algorithms and FlowchartAbdullah Al-suleimaniNo ratings yet
- M.tech-ECE-Embedded Systems (ES) - SEM1 Course Structure & SyllabiDocument8 pagesM.tech-ECE-Embedded Systems (ES) - SEM1 Course Structure & Syllabisatraj5No ratings yet
- Hardware-Software Co-Partitioning For Distributed Embedded SystemsDocument41 pagesHardware-Software Co-Partitioning For Distributed Embedded SystemsRaghu RamNo ratings yet
- Compiler LabDocument4 pagesCompiler LabNambiRajaNo ratings yet
- SP (Simple Processor) SpecificationDocument4 pagesSP (Simple Processor) SpecificationrisirarocksNo ratings yet
- CS2304 System Software UNIT I NOTESDocument9 pagesCS2304 System Software UNIT I NOTESClashing with DeepakNo ratings yet
- C++ ExercisesDocument83 pagesC++ ExercisesAbdelrahman Elattar50% (2)
- Aviral DT 1.2Document11 pagesAviral DT 1.2Aman Pratap SinghNo ratings yet
- Compiler Design LabDocument15 pagesCompiler Design LabMosaddek Hossain100% (1)
- C Programming for the Pc the Mac and the Arduino Microcontroller SystemFrom EverandC Programming for the Pc the Mac and the Arduino Microcontroller SystemNo ratings yet
- Embedded Software Design and Programming of Multiprocessor System-on-Chip: Simulink and System C Case StudiesFrom EverandEmbedded Software Design and Programming of Multiprocessor System-on-Chip: Simulink and System C Case StudiesNo ratings yet
- Python Advanced Programming: The Guide to Learn Python Programming. Reference with Exercises and Samples About Dynamical Programming, Multithreading, Multiprocessing, Debugging, Testing and MoreFrom EverandPython Advanced Programming: The Guide to Learn Python Programming. Reference with Exercises and Samples About Dynamical Programming, Multithreading, Multiprocessing, Debugging, Testing and MoreNo ratings yet
- Introduction to Python Programming: Do your first steps into programming with pythonFrom EverandIntroduction to Python Programming: Do your first steps into programming with pythonNo ratings yet
- Projects With Microcontrollers And PICCFrom EverandProjects With Microcontrollers And PICCRating: 5 out of 5 stars5/5 (1)
- Subject:-Engineering Mathematics III Class: - SE-IT Subject Code:-ITC 301 Module Number: - 3 Fourier SeriesDocument19 pagesSubject:-Engineering Mathematics III Class: - SE-IT Subject Code:-ITC 301 Module Number: - 3 Fourier Seriesenggeng7No ratings yet
- Sr. Number: Name of Participant: Email ID: Mobile NumberDocument5 pagesSr. Number: Name of Participant: Email ID: Mobile Numberenggeng7No ratings yet
- Mapping 1 PracticalDocument12 pagesMapping 1 Practicalenggeng7No ratings yet
- Sec8 1Document16 pagesSec8 1enggeng7No ratings yet
- Superscalar ArchitectureDocument9 pagesSuperscalar Architectureenggeng7No ratings yet
- Poiuytteewqqasdfghgjlol, MNNCBBVBF Hfghtyu654256758787685634 Efyhf Tughjghdxfx BCGNH GFDGDGFGH GJGHDXGFHGJH FGDGFJHKGHDFG FHGFD FGD GFDH FG SDGJH G JDFGFSHDFHJ FGJ SF FHDF GJDF GHDFH GDocument1 pagePoiuytteewqqasdfghgjlol, MNNCBBVBF Hfghtyu654256758787685634 Efyhf Tughjghdxfx BCGNH GFDGDGFGH GJGHDXGFHGJH FGDGFJHKGHDFG FHGFD FGD GFDH FG SDGJH G JDFGFSHDFHJ FGJ SF FHDF GJDF GHDFH Genggeng7No ratings yet
- Pillai HOC College of Engineering and Technology, RasayaniDocument1 pagePillai HOC College of Engineering and Technology, Rasayanienggeng7No ratings yet
- #Include Void Main (Printf ("Hello SANDEEP/n") )Document1 page#Include Void Main (Printf ("Hello SANDEEP/n") )enggeng7No ratings yet
- Course File Programming and Problem Solving in CDocument10 pagesCourse File Programming and Problem Solving in Cenggeng7No ratings yet
- Te CN Lab ManualDocument58 pagesTe CN Lab Manualenggeng7No ratings yet
- List of Experiments OOPM16Document3 pagesList of Experiments OOPM16enggeng7No ratings yet
- Diagram: Use Case Diagram Page 1Document1 pageDiagram: Use Case Diagram Page 1enggeng7No ratings yet
- Exp 10 DFSDocument4 pagesExp 10 DFSenggeng7No ratings yet
- Vehicle Management SystemDocument3 pagesVehicle Management Systemenggeng7No ratings yet
- Thermo 1 & 2Document4 pagesThermo 1 & 2Oloj YuNo ratings yet
- Tle Grade7n8 Dressmaking Module 3 Week310 PDFDocument10 pagesTle Grade7n8 Dressmaking Module 3 Week310 PDFgilbert datu100% (1)
- Zoning in Processing Facilities 375003 7Document2 pagesZoning in Processing Facilities 375003 7TinnysumardiNo ratings yet
- Nsejs-2023 ST 1Document13 pagesNsejs-2023 ST 1S DNo ratings yet
- Seagate DiscWizard User GuideDocument68 pagesSeagate DiscWizard User GuideTotulRedus RoNo ratings yet
- Kollmorgen B With ServoStar S and CD TB CatalogDocument10 pagesKollmorgen B With ServoStar S and CD TB CatalogElectromateNo ratings yet
- Iot Fundamentals: A Comprehensive Introduction To Iot Theory & ApplicationsDocument97 pagesIot Fundamentals: A Comprehensive Introduction To Iot Theory & ApplicationsMohammed Elyas86% (7)
- Qadm 3Document7 pagesQadm 3Ravi Kiran VithanalaNo ratings yet
- The Umbrella Test PDFDocument2 pagesThe Umbrella Test PDF178317No ratings yet
- Colm Flynn's Debating HandbookDocument57 pagesColm Flynn's Debating HandbookRoland ApareceNo ratings yet
- Homeroom Guidance Learner'S Development Assessment S.Y. 2020-2021Document4 pagesHomeroom Guidance Learner'S Development Assessment S.Y. 2020-2021Marnellie Bautista-ValdezNo ratings yet
- PS3 SolutionsDocument3 pagesPS3 SolutionsYenhao Philip ChenNo ratings yet
- InstructionsDocument2 pagesInstructionsDeepak BoraseNo ratings yet
- 高中高考英语常用单词词性转换及派生Document17 pages高中高考英语常用单词词性转换及派生clarikeiNo ratings yet
- Codeofconduct English 2015Document44 pagesCodeofconduct English 2015Cherry Ann GidaNo ratings yet
- A Detailed Lesson Plan in Science 3Document3 pagesA Detailed Lesson Plan in Science 3Lauren may Villanueva75% (4)
- DS LabDocument46 pagesDS LabKamalStarkNo ratings yet
- Adm Math7 q2 Module1 Revised Final Dec2Document28 pagesAdm Math7 q2 Module1 Revised Final Dec2Random NanaNo ratings yet
- A1 ReviewDocument17 pagesA1 ReviewallenNo ratings yet
- 2018 ICpEP CpE Challenge Mechanics ProgrammingDocument7 pages2018 ICpEP CpE Challenge Mechanics ProgrammingCha FigueroaNo ratings yet
- TIBCO Administrator™: Server Configuration GuideDocument297 pagesTIBCO Administrator™: Server Configuration Guidepankaj somNo ratings yet
- Catastrophe ModelCatastrophe Modelling LingDocument14 pagesCatastrophe ModelCatastrophe Modelling LingneomilanNo ratings yet
- Comp128 ThesisDocument39 pagesComp128 ThesisInfinito SerNo ratings yet
- #142 Two-Stage Ejecting Structure - Technical Tutorial - MISUMIDocument2 pages#142 Two-Stage Ejecting Structure - Technical Tutorial - MISUMIgaliskribdNo ratings yet
- Work Life BalanceDocument10 pagesWork Life BalanceAngelica HalmajanNo ratings yet
- FALLON 1987 Constructivist Coherence Theory of Constitutional InterpretationDocument99 pagesFALLON 1987 Constructivist Coherence Theory of Constitutional InterpretationcarriewydraNo ratings yet
- Osullivan T 09071996 TranscriptDocument2 pagesOsullivan T 09071996 Transcriptapi-380159566No ratings yet