Professional Documents
Culture Documents
Trusteer Mobile Risk Engine
Trusteer Mobile Risk Engine
Uploaded by
August Majer IIICopyright:
Available Formats
You might also like
- 176 Security Issues Internal Security by MR Satveer Singh 2024 03Document12 pages176 Security Issues Internal Security by MR Satveer Singh 2024 03Sanjeev KumarNo ratings yet
- ThreatMetrix Cybercrime Defender PlatformDocument3 pagesThreatMetrix Cybercrime Defender PlatformJoshua McAfeeNo ratings yet
- 5 Facts You Should Know About Mobile Security - ZimperiumDocument7 pages5 Facts You Should Know About Mobile Security - ZimperiumGratouillasNo ratings yet
- Factelligence MiddlewareDocument362 pagesFactelligence MiddlewareEduin ZuloagaNo ratings yet
- Mobile Threats and AttacksDocument25 pagesMobile Threats and AttacksOstilio SystemsNo ratings yet
- Malware: Iii. Motives To Create Mobile MalwareDocument10 pagesMalware: Iii. Motives To Create Mobile MalwareNida NawazNo ratings yet
- Unit 3 SE PDFDocument78 pagesUnit 3 SE PDFSwetha DNo ratings yet
- 12063690Document70 pages12063690saba janelidzeNo ratings yet
- Artificial Intelligence AI Security: Preventative Measures 1)Document5 pagesArtificial Intelligence AI Security: Preventative Measures 1)Ajin PaulNo ratings yet
- CYBER SECURITY (R18A0521) - Pages-5Document6 pagesCYBER SECURITY (R18A0521) - Pages-573035537rishubrother95827594No ratings yet
- PSP Assignment1Document25 pagesPSP Assignment1B BasitNo ratings yet
- Awaz MDocument11 pagesAwaz Mawaz mustafaNo ratings yet
- Mobile Banking: Vikas - (Course Title)Document5 pagesMobile Banking: Vikas - (Course Title)VikasNo ratings yet
- TWP - Nguyen Duc Hieu - Pham Trung HieuDocument21 pagesTWP - Nguyen Duc Hieu - Pham Trung HieuPham HieuNo ratings yet
- SOVA Android TrojanDocument2 pagesSOVA Android TrojanShovan GhoshNo ratings yet
- Mobile Device Security Important?Document5 pagesMobile Device Security Important?Abhishek PatelNo ratings yet
- Review On Mobile Threats andDocument9 pagesReview On Mobile Threats andijdpsNo ratings yet
- MobilesecurityintroDocument35 pagesMobilesecurityintronarsingthakur100% (1)
- CERT-In NCSAM Book - 20231002 - 182603 - 0000Document17 pagesCERT-In NCSAM Book - 20231002 - 182603 - 0000winkrish8805No ratings yet
- IT Assignment - Shreya Tripathi (MBA - 2nd Sem)Document30 pagesIT Assignment - Shreya Tripathi (MBA - 2nd Sem)Shreya TripathiNo ratings yet
- Mobile Devices and WirelessDocument21 pagesMobile Devices and WirelessabdulhafithNo ratings yet
- 3 MobilesecurityintroDocument35 pages3 Mobilesecurityintroradislamy-1No ratings yet
- ReportDocument4 pagesReportendurthiabhilashNo ratings yet
- 2 Factor Authentication PDFDocument18 pages2 Factor Authentication PDFHuzaifaNo ratings yet
- M A P T: Obile Pplication Enetration EstingDocument12 pagesM A P T: Obile Pplication Enetration EstingTemel tüzemenNo ratings yet
- Android SecurityDocument32 pagesAndroid SecurityPeerukkan Nazrin Beham Assistant ProfessorNo ratings yet
- Current Scenario in Cyber SecurityDocument256 pagesCurrent Scenario in Cyber SecurityPankaj Singh100% (1)
- Cyb 413 NoteDocument35 pagesCyb 413 NoteAdedolamu AyandeleNo ratings yet
- IP SECURITY Anshika NewDocument15 pagesIP SECURITY Anshika Newdiwansingh29081999No ratings yet
- Materi Chpt.5 E-Commerce Security and Payment SystemsDocument37 pagesMateri Chpt.5 E-Commerce Security and Payment Systemsdonny antaraNo ratings yet
- MITB - Online Banking NightmareDocument2 pagesMITB - Online Banking NightmareAhmed SalehNo ratings yet
- Mobile SecurityDocument4 pagesMobile Securityinfonetayur_78448935No ratings yet
- Learning Material For Unit 4Document19 pagesLearning Material For Unit 4shikha22bcom24No ratings yet
- Smartphone Security GuidelinesDocument15 pagesSmartphone Security GuidelinesManjiri AmitNo ratings yet
- Unit 3Document89 pagesUnit 3nellutlaramyaNo ratings yet
- Data 1Document6 pagesData 1Gaurav RaneNo ratings yet
- Security, Legal and Ethical IssuesDocument21 pagesSecurity, Legal and Ethical IssuesThe PaletteNo ratings yet
- Security TechGuide Mobile 1011 v2Document21 pagesSecurity TechGuide Mobile 1011 v2Victor ChuNo ratings yet
- The Thriving Malware Industry: Cybercrime Made EasyDocument12 pagesThe Thriving Malware Industry: Cybercrime Made EasyJayesh NowbuthNo ratings yet
- Cyber Law ShortsDocument3 pagesCyber Law ShortsJyoti BhutiaNo ratings yet
- Preventing Spoofing Attacks in Mobile Banking Based On User Input Pattern - Based AuthenticationDocument5 pagesPreventing Spoofing Attacks in Mobile Banking Based On User Input Pattern - Based AuthenticationInternational Organization of Scientific Research (IOSR)No ratings yet
- Understanding The Risks of Mobile AppsDocument7 pagesUnderstanding The Risks of Mobile AppsblussierttNo ratings yet
- UG III FC NotesDocument24 pagesUG III FC Notesnencybatham122No ratings yet
- Privacy Unit1Document6 pagesPrivacy Unit1SwetankNo ratings yet
- 10 11648 J WCMC 20130101 15Document9 pages10 11648 J WCMC 20130101 15tolufakanleNo ratings yet
- Module 1Document16 pagesModule 1Shubham SarkarNo ratings yet
- E Business AnswersDocument20 pagesE Business AnswersNIKHIL ARORANo ratings yet
- DocumentDocument14 pagesDocumentMlondi DlaminiNo ratings yet
- The Thriving Malware Industry: Cybercrime Made EasyDocument12 pagesThe Thriving Malware Industry: Cybercrime Made EasyCao Minh TríNo ratings yet
- Rishi Tiwari - E Com. AssignDocument3 pagesRishi Tiwari - E Com. AssignRishiNo ratings yet
- Security Testing ArticlesDocument7 pagesSecurity Testing ArticlesVara PrasadNo ratings yet
- 20bce0610 VL2022230103815 Pe003Document32 pages20bce0610 VL2022230103815 Pe003DILITH DINESHNo ratings yet
- Information Assurance and CybersecurityDocument18 pagesInformation Assurance and Cybersecurityzahra zahidNo ratings yet
- 0 - Security and Control in Information System 12-13Document26 pages0 - Security and Control in Information System 12-13Amneet KaurNo ratings yet
- Emergence of Risk-Based Authentication in Online Financial Services: You Can'T Hide Your Lyin' IpsDocument11 pagesEmergence of Risk-Based Authentication in Online Financial Services: You Can'T Hide Your Lyin' IpsforoldpcNo ratings yet
- A Secure Web Authentication ProtocolDocument18 pagesA Secure Web Authentication ProtocolLavanyaNo ratings yet
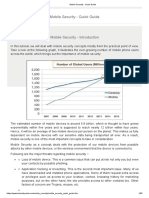
- Mobile Security - Quick GuideDocument63 pagesMobile Security - Quick GuideVenkatNo ratings yet
- Information Security in Mobile Application: Research Paper OnDocument21 pagesInformation Security in Mobile Application: Research Paper Onyogesh_8488No ratings yet
- Unit 3Document81 pagesUnit 3gbuzzz31No ratings yet
- Mobile SecurityDocument10 pagesMobile SecurityBirender SinghNo ratings yet
- Shoulder WorkoutDocument13 pagesShoulder WorkoutAugust Majer IIINo ratings yet
- Nash Equilibrium: IllustrationsDocument45 pagesNash Equilibrium: IllustrationsAugust Majer IIINo ratings yet
- Relationship Marketing and Brand Involvement of Professionals Through Web-Enhanced Brand Communities: The Case of ColoplastDocument13 pagesRelationship Marketing and Brand Involvement of Professionals Through Web-Enhanced Brand Communities: The Case of ColoplastAugust Majer IIINo ratings yet
- Italian Verbs PDFDocument1 pageItalian Verbs PDFAugust Majer IIINo ratings yet
- Connecting To Linux Using PuttyDocument9 pagesConnecting To Linux Using Puttydilip4682794No ratings yet
- VBScript in A NutshellDocument46 pagesVBScript in A NutshellROHITCHOURASIYANo ratings yet
- Adv7340 7341 PDFDocument108 pagesAdv7340 7341 PDFTheotech EletronNo ratings yet
- Executive Information System (EIS)Document26 pagesExecutive Information System (EIS)lakshaynarayan92% (12)
- Quick Report: Acunetix Security AuditDocument4 pagesQuick Report: Acunetix Security Auditgandariangmbojo2023No ratings yet
- Moodle PresentationDocument22 pagesMoodle Presentationsvinod sNo ratings yet
- Module 2 - Basic Comp Op and File MGTDocument45 pagesModule 2 - Basic Comp Op and File MGT77丨S A W ًNo ratings yet
- Win 2k8 Installing Casino and Admin 2.20.XxDocument4 pagesWin 2k8 Installing Casino and Admin 2.20.Xxfofi07No ratings yet
- ICF 9 1st SummativeDocument2 pagesICF 9 1st Summativeallan tomasNo ratings yet
- ZP Power-Pack Whitepaper3Document16 pagesZP Power-Pack Whitepaper3Juan David BoteroNo ratings yet
- Lovish'sDocument37 pagesLovish'sParas TalujaNo ratings yet
- What Are The Differences Between Windows and LinuxDocument8 pagesWhat Are The Differences Between Windows and LinuxGeorge MurphyNo ratings yet
- JennyDocument16 pagesJennyMyrna PanesNo ratings yet
- Dmxsoft SushiDocument1 pageDmxsoft SushiRichter SiegfriedNo ratings yet
- Exchange 2010 Mailbox Server Role Requirements Calculator: Blue VariablesDocument9 pagesExchange 2010 Mailbox Server Role Requirements Calculator: Blue VariableswaitslipknotbleedNo ratings yet
- Exam Az 800 Administering Windows Server Hybrid Core Infrastructure Skills MeasuredDocument5 pagesExam Az 800 Administering Windows Server Hybrid Core Infrastructure Skills MeasuredMike DanielNo ratings yet
- Linda Pagan: 8514 Solitude Hill LN Richmond, TX 77407 (713) 384-8476 Lindarpagan@gmail - Co MDocument2 pagesLinda Pagan: 8514 Solitude Hill LN Richmond, TX 77407 (713) 384-8476 Lindarpagan@gmail - Co Mapi-355399601No ratings yet
- Software - Components & CharacteristicsDocument2 pagesSoftware - Components & CharacteristicsvsrajeshvsNo ratings yet
- Installation Guide SaltinourHair 19Document9 pagesInstallation Guide SaltinourHair 19VivienLamNo ratings yet
- Vijeo Quick Start Tutorial V720Document114 pagesVijeo Quick Start Tutorial V720ssgfreemailNo ratings yet
- Adobe Photoshop - Create Smart Objects PDFDocument3 pagesAdobe Photoshop - Create Smart Objects PDFmukasuraNo ratings yet
- Kickas Proxy WebsitesDocument7 pagesKickas Proxy Websiteskichu123No ratings yet
- Name: Dhanraj B. Ranvirkar Topic: Basics of GitDocument7 pagesName: Dhanraj B. Ranvirkar Topic: Basics of GitRitik bhadoriaNo ratings yet
- ZK 6.5.0 Installation GuideDocument115 pagesZK 6.5.0 Installation Guideachile123No ratings yet
- Components of Forcepoint DLP Management ServerDocument8 pagesComponents of Forcepoint DLP Management ServerAnandapriya MohantaNo ratings yet
- In Social Media MarketingDocument2 pagesIn Social Media MarketingNOR FAQIHAH NADHRAHNo ratings yet
- FortifyDocument100 pagesFortifyfernando PalloNo ratings yet
- Project On - Web Devlopment and PythonDocument26 pagesProject On - Web Devlopment and PythonRishaw KumarNo ratings yet
- ABAP Program To Delete A File From The Application Server - Code Gallery - SCN WikiDocument4 pagesABAP Program To Delete A File From The Application Server - Code Gallery - SCN Wikisdv varshneyNo ratings yet
Trusteer Mobile Risk Engine
Trusteer Mobile Risk Engine
Uploaded by
August Majer IIIOriginal Description:
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Trusteer Mobile Risk Engine
Trusteer Mobile Risk Engine
Uploaded by
August Majer IIICopyright:
Available Formats
With the welcome growth in mobile banking, financial institutions must manage the increased
risk associated with the mobile channel. FFIEC guidance requirements for layered security,
continuous risk assessment and complex device fingerprinting naturally extend to the mobile
channel. Organizations looking to mitigate mobile fraud risk should address complex cross
channel attacks and the unique challenges associated with the mobile channel.
The Mobile Channel is a Hot Target for Cybercriminals
Mobile device adoption will ultimately surpass personal computers in both units and online banking usage
Mobile banking apps are designed with limited security controls and are unaware of device risk
Immature mobile fraud detection systems increase the likelihood of a successful attack
Expanding mobile banking and payment capabilities make the mobile channel an increasingly attractive target
With a growing number of targets and limited fraud detection and prevention capabilities, the mobile channel is
becoming an attractive target for cybercriminals.
Account Takeover via Mobile Devices Defeats Device ID Solutions
Cybercriminals steal credentials from the victims PC via malware or phishing attacks to commit account takeover
using the mobile device browser. This method represents a major challenge for device ID systems, as many
mobile devices have the same fingerprint. For example, most iPhones look alike (same OS, browser, fonts, etc.).
A comprehensive risk assessment that incorporates device ID, device risk factors and detailed account compromise
history is required to detect account takeover.
Rogue Applications and Mobile Malware Steal Banking Credentials
Cybercriminals leverage security vulnerabilities and social engineering to infect mobile devices with
malware. Fake gaming or security mobile applications embedded with malware are offered through
application stores and marketplaces. Mobile devices are also infected by accessing websites
with exploit code that targets mobile browser vulnerabilities (i.e., drive-by-downloads).
Mobile/PC Combo Attacks Circumvent SMS
One-Time Password Authentication
Cybercriminals can easily infect a victims mobile device to overcome
SMS one-time password (OTP) authentication. After a users PC is infected with
malware, the user is presented with a message to download security software to
their mobile device. This software intercepts SMS messages and allows the criminal
to obtain the victims OTP. These malware variants leverage both the online and
mobile channels to execute the attack.
MOBILE RISK MANAGEMENT
Trusteer
Mobile Risk Engine
Trusteer Mobile Risk Engine
Conclusive Mobile Fraud Risk Detection Based on Device and Account Risk
Factors Across Channels
Assesses Mobile Fraud Risk in Real-Time
Trusteer Mobile Risk Engine (MRE) protects the mobile channel by performing a mobile risk
assessment based on device and account risk factors. It enables organizations to mitigate risk
by producing accurate and conclusive recommendations to allow, restrict or deny user access.
Organizations can use these recommendations to apply stepped-up authentication or extended
transaction review for truly high-risk users, sessions and transactions.
Trusteer Mobile Risk Engine
Capabilities
Detects vulnerable and compromised
devices
Captures persistent device ID, geolocation and detailed device risk factors
Correlates device and account risk factors
across online and mobile channels
Detects High-Risk Devices Based on Multiple Data Sources
MRE generates accurate security recommendations based on multiple device risk factors. To
accommodate deployment or integration restrictions, MRE can consume risk data from the
included Trusteer Mobile SDK and Trusteer Mobile App (i.e., on-device components) or from the
customers web app via an API. MRE maintains a global fraudster device database that is shared
across organizations.
Conclusively stops account takeover
attacks from mobile devices using stolen
credentials
Correlates Online and Mobile Banking Risk Data for Conclusive Mobile Risk Detection
Web-based service
To address complex attacks across online and mobile channels, MRE can incorporate account risk
factors including malware infections and phishing incidents. This extended data set is collected by
Trusteers client-based (Trusteer Rapport) and clientless (Trusteer Pinpoint Malware Detection) fraud
prevention solutions. The risk data is used to accurately detect account takeover attempts from
mobile devices using compromised credentials from other channels.
Trusteer Mobile Risk Engine
Components
Trusteer Mobile SDK
Trusteer Mobile App
Custom Data API
Trusteer Mobile Risk Engine Data
Risk Sources
Meets FFIEC Guidance for Continuous Risk Assessment
The FFIEC guidance requires financial institutions to implement continuous risk assessment
and implement multiple security layers to detect fraudulent transactions. MRE detects high-risk
activity by assessing the risk of every mobile device, mobile login and mobile transaction. The
risk-based recommended actions can range from authenticating the user to preventing access to
the account.
Trusteer Pinpoint Malware Detection
Trusteer Pinpoint Account Takeover
(ATO) Detection
Trusteer Rapport
Ensures a Secure and Hassle-Free Mobile
Banking Experience
Device
By relying on multiple risk factors across multiple
Vulnerabilities
channels, MRE can accurately track the full attack
lifecycle. It uses a set of mobile risk detection
rules that map current attack patterns and
are updated based on Trusteers global
intelligence. Only truly high-risk users
and transactions are flagged for review
or stepped-up authentication
Persistent
in order to minimize the
Device ID
burden to the customer.
Phishing
Incidents
Trusteer
Mobile Risk Engine
Malware
Infections
Global Fraudster Device Database
Global
Intelligence
!
Trusteer Mobile Risk Engine correlates device risk factors
and account compromise history to automatically tag
fraudsters devices across all protected organizations.
Account
Access/ Trx
Trusteer Mobile SDK
Embedded Security Library for Android and iOS Native Mobile Banking Apps
Detects High-Risk Access from Compromised or Vulnerable Devices
Trusteer Mobile SDK Risk Factors
Trusteer Mobile SDK is invoked when the mobile application is launched to collect various device
risk factors. These include: geolocation, device time, IP address, missing OS security patches, rooted/
jailbroken device status, risky system configuration settings, malware infections, use of unsecured
Wi-Fi connection and more. Risk data is provided to the mobile banking app and can be used to
restrict functionality based on device risk level. For example, limiting specific application functions
(adding a payee or transferring money) on a jailbroken device. The risk data can also be sent to the
Trusteer Mobile Risk Engine where it is correlated with additional device and account risk factors
(such as malware infections and phishing incidents) to flag high risk access and transactions.
Persistent Device ID
Generates a Persistent Mobile Device ID for Unique Device Identification
User ID
Trusteer Mobile SDK creates a persistent mobile device ID allowing the organization to uniquely
identify any device using the native mobile banking app. The persistent device ID is associated with
the users account and uniquely identifies the device, even after the phone is re-imaged. This ensures
new devices are identified, login attempts from known devices are unchallenged, and potential
fraudster devices are flagged.
SIM Data
Trusteer Mobile App
Secure Mobile Browser for Online Banking
Secures Mobile Web Access to Online Banking
Trusteer Mobile App includes a secure mobile browser. End users use the mobile browser to safely
access the online banking website and financial institutions can mandate that their online banking
websites are only accessed via the Trusteer Mobile App. Whenever a protected website is accessed,
a complete security posture assessment is performed on the device. Trusteer Mobile App collects
mobile device risk factors and a persistent mobile device ID and sends these to the online banking
website and Trusteer Mobile Risk Engine where they are used for mobile risk assessment.
Alerts the User of Device Security Risks
Trusteer Mobile App users can view their device security status via a dedicated dashboard.
Indications of malware infection, unsecure Wi-Fi connections and other security risks are
identified. The user can resolve these risks by following step-by-step remediation guidance
provided by the app.
Protects the User from Fake Banking Websites
Trusteer Mobile App protects against pharming attacks. By validating both
the IP address and the SSL certificate when a protected website
is accessed, both session hijacking (Man-in-the-Middle)
and redirection attacks are prevented.
Jailbreak/Rooted Device
Malware Infection
OS Patching
Wi-Fi Security
Rogue Apps
Application ID
Geolocation
And more
Trusteer Cybercrime Prevention Architecture
Trusteer Cybercrime Intelligence
Global threat intelligence and fraudster database
Trusteer Pinpoint
Cybercrime Intelligence
Layer 2:
Clientless Fraud
Prevention
Trusteer Pinpoint
Account Takeover (ATO)
Detection
Malware
Detection
Trusteer Mobile
Risk Engine
er
Custom
e
Prot
c tio
Account Takeover (ATO) Detection
Correlation of multiple fraud risk indicators for
conclusive account takeover and mobile risk
detection
Malware Detection
Clientless detection of Man-in-the-Browser
malware infected endpoints
Trusteer Mobile Risk Engine
Detects mobile and cross-channel fraud risk via
web-based services and the included mobile
client components
Trusteer Apex
Zero-day exploits and data exfiltration prevention
for employees endpoints
Em
plo
Trusteer Apex
ye e
Prote
c
Trusteer Rapport Trusteer Mobile
tion
Cu
r Pr
stome
o te
c tio
Layer 1:
Endpoint Security
Trusteer Rapport
Prevention and remediation of malware and
phishing threats on PCs and Macs
Trusteer Mobile
Embedded security library for native mobile apps,
dedicated secure mobile browser, out-of-band
authentication
Trusteer is the Global Leader in Financial Fraud Prevention
Boston-based Trusteer is the leading provider of endpoint cybercrime prevention solutions that protect
MOBILE
RISK
MANAGEMENT
organizations against financial losses and data breaches. Hundreds of organizations and millions of end
users rely on Trusteer to protect managed and unmanaged endpoints against exploitation and compromise
by online threats that are invisible to legacy security solutions. Global organizations such as HSBC, Santander,
SunTrust and Fifth Third are among Trusteers customers.
Trusteer Inc.
545 Boylston Street, 5th Floor
Boston, MA 02116
T: +1 (866) 496-6139
T: +1 (617) 606-7755
info@trusteer.com
trusteer.com
You might also like
- 176 Security Issues Internal Security by MR Satveer Singh 2024 03Document12 pages176 Security Issues Internal Security by MR Satveer Singh 2024 03Sanjeev KumarNo ratings yet
- ThreatMetrix Cybercrime Defender PlatformDocument3 pagesThreatMetrix Cybercrime Defender PlatformJoshua McAfeeNo ratings yet
- 5 Facts You Should Know About Mobile Security - ZimperiumDocument7 pages5 Facts You Should Know About Mobile Security - ZimperiumGratouillasNo ratings yet
- Factelligence MiddlewareDocument362 pagesFactelligence MiddlewareEduin ZuloagaNo ratings yet
- Mobile Threats and AttacksDocument25 pagesMobile Threats and AttacksOstilio SystemsNo ratings yet
- Malware: Iii. Motives To Create Mobile MalwareDocument10 pagesMalware: Iii. Motives To Create Mobile MalwareNida NawazNo ratings yet
- Unit 3 SE PDFDocument78 pagesUnit 3 SE PDFSwetha DNo ratings yet
- 12063690Document70 pages12063690saba janelidzeNo ratings yet
- Artificial Intelligence AI Security: Preventative Measures 1)Document5 pagesArtificial Intelligence AI Security: Preventative Measures 1)Ajin PaulNo ratings yet
- CYBER SECURITY (R18A0521) - Pages-5Document6 pagesCYBER SECURITY (R18A0521) - Pages-573035537rishubrother95827594No ratings yet
- PSP Assignment1Document25 pagesPSP Assignment1B BasitNo ratings yet
- Awaz MDocument11 pagesAwaz Mawaz mustafaNo ratings yet
- Mobile Banking: Vikas - (Course Title)Document5 pagesMobile Banking: Vikas - (Course Title)VikasNo ratings yet
- TWP - Nguyen Duc Hieu - Pham Trung HieuDocument21 pagesTWP - Nguyen Duc Hieu - Pham Trung HieuPham HieuNo ratings yet
- SOVA Android TrojanDocument2 pagesSOVA Android TrojanShovan GhoshNo ratings yet
- Mobile Device Security Important?Document5 pagesMobile Device Security Important?Abhishek PatelNo ratings yet
- Review On Mobile Threats andDocument9 pagesReview On Mobile Threats andijdpsNo ratings yet
- MobilesecurityintroDocument35 pagesMobilesecurityintronarsingthakur100% (1)
- CERT-In NCSAM Book - 20231002 - 182603 - 0000Document17 pagesCERT-In NCSAM Book - 20231002 - 182603 - 0000winkrish8805No ratings yet
- IT Assignment - Shreya Tripathi (MBA - 2nd Sem)Document30 pagesIT Assignment - Shreya Tripathi (MBA - 2nd Sem)Shreya TripathiNo ratings yet
- Mobile Devices and WirelessDocument21 pagesMobile Devices and WirelessabdulhafithNo ratings yet
- 3 MobilesecurityintroDocument35 pages3 Mobilesecurityintroradislamy-1No ratings yet
- ReportDocument4 pagesReportendurthiabhilashNo ratings yet
- 2 Factor Authentication PDFDocument18 pages2 Factor Authentication PDFHuzaifaNo ratings yet
- M A P T: Obile Pplication Enetration EstingDocument12 pagesM A P T: Obile Pplication Enetration EstingTemel tüzemenNo ratings yet
- Android SecurityDocument32 pagesAndroid SecurityPeerukkan Nazrin Beham Assistant ProfessorNo ratings yet
- Current Scenario in Cyber SecurityDocument256 pagesCurrent Scenario in Cyber SecurityPankaj Singh100% (1)
- Cyb 413 NoteDocument35 pagesCyb 413 NoteAdedolamu AyandeleNo ratings yet
- IP SECURITY Anshika NewDocument15 pagesIP SECURITY Anshika Newdiwansingh29081999No ratings yet
- Materi Chpt.5 E-Commerce Security and Payment SystemsDocument37 pagesMateri Chpt.5 E-Commerce Security and Payment Systemsdonny antaraNo ratings yet
- MITB - Online Banking NightmareDocument2 pagesMITB - Online Banking NightmareAhmed SalehNo ratings yet
- Mobile SecurityDocument4 pagesMobile Securityinfonetayur_78448935No ratings yet
- Learning Material For Unit 4Document19 pagesLearning Material For Unit 4shikha22bcom24No ratings yet
- Smartphone Security GuidelinesDocument15 pagesSmartphone Security GuidelinesManjiri AmitNo ratings yet
- Unit 3Document89 pagesUnit 3nellutlaramyaNo ratings yet
- Data 1Document6 pagesData 1Gaurav RaneNo ratings yet
- Security, Legal and Ethical IssuesDocument21 pagesSecurity, Legal and Ethical IssuesThe PaletteNo ratings yet
- Security TechGuide Mobile 1011 v2Document21 pagesSecurity TechGuide Mobile 1011 v2Victor ChuNo ratings yet
- The Thriving Malware Industry: Cybercrime Made EasyDocument12 pagesThe Thriving Malware Industry: Cybercrime Made EasyJayesh NowbuthNo ratings yet
- Cyber Law ShortsDocument3 pagesCyber Law ShortsJyoti BhutiaNo ratings yet
- Preventing Spoofing Attacks in Mobile Banking Based On User Input Pattern - Based AuthenticationDocument5 pagesPreventing Spoofing Attacks in Mobile Banking Based On User Input Pattern - Based AuthenticationInternational Organization of Scientific Research (IOSR)No ratings yet
- Understanding The Risks of Mobile AppsDocument7 pagesUnderstanding The Risks of Mobile AppsblussierttNo ratings yet
- UG III FC NotesDocument24 pagesUG III FC Notesnencybatham122No ratings yet
- Privacy Unit1Document6 pagesPrivacy Unit1SwetankNo ratings yet
- 10 11648 J WCMC 20130101 15Document9 pages10 11648 J WCMC 20130101 15tolufakanleNo ratings yet
- Module 1Document16 pagesModule 1Shubham SarkarNo ratings yet
- E Business AnswersDocument20 pagesE Business AnswersNIKHIL ARORANo ratings yet
- DocumentDocument14 pagesDocumentMlondi DlaminiNo ratings yet
- The Thriving Malware Industry: Cybercrime Made EasyDocument12 pagesThe Thriving Malware Industry: Cybercrime Made EasyCao Minh TríNo ratings yet
- Rishi Tiwari - E Com. AssignDocument3 pagesRishi Tiwari - E Com. AssignRishiNo ratings yet
- Security Testing ArticlesDocument7 pagesSecurity Testing ArticlesVara PrasadNo ratings yet
- 20bce0610 VL2022230103815 Pe003Document32 pages20bce0610 VL2022230103815 Pe003DILITH DINESHNo ratings yet
- Information Assurance and CybersecurityDocument18 pagesInformation Assurance and Cybersecurityzahra zahidNo ratings yet
- 0 - Security and Control in Information System 12-13Document26 pages0 - Security and Control in Information System 12-13Amneet KaurNo ratings yet
- Emergence of Risk-Based Authentication in Online Financial Services: You Can'T Hide Your Lyin' IpsDocument11 pagesEmergence of Risk-Based Authentication in Online Financial Services: You Can'T Hide Your Lyin' IpsforoldpcNo ratings yet
- A Secure Web Authentication ProtocolDocument18 pagesA Secure Web Authentication ProtocolLavanyaNo ratings yet
- Mobile Security - Quick GuideDocument63 pagesMobile Security - Quick GuideVenkatNo ratings yet
- Information Security in Mobile Application: Research Paper OnDocument21 pagesInformation Security in Mobile Application: Research Paper Onyogesh_8488No ratings yet
- Unit 3Document81 pagesUnit 3gbuzzz31No ratings yet
- Mobile SecurityDocument10 pagesMobile SecurityBirender SinghNo ratings yet
- Shoulder WorkoutDocument13 pagesShoulder WorkoutAugust Majer IIINo ratings yet
- Nash Equilibrium: IllustrationsDocument45 pagesNash Equilibrium: IllustrationsAugust Majer IIINo ratings yet
- Relationship Marketing and Brand Involvement of Professionals Through Web-Enhanced Brand Communities: The Case of ColoplastDocument13 pagesRelationship Marketing and Brand Involvement of Professionals Through Web-Enhanced Brand Communities: The Case of ColoplastAugust Majer IIINo ratings yet
- Italian Verbs PDFDocument1 pageItalian Verbs PDFAugust Majer IIINo ratings yet
- Connecting To Linux Using PuttyDocument9 pagesConnecting To Linux Using Puttydilip4682794No ratings yet
- VBScript in A NutshellDocument46 pagesVBScript in A NutshellROHITCHOURASIYANo ratings yet
- Adv7340 7341 PDFDocument108 pagesAdv7340 7341 PDFTheotech EletronNo ratings yet
- Executive Information System (EIS)Document26 pagesExecutive Information System (EIS)lakshaynarayan92% (12)
- Quick Report: Acunetix Security AuditDocument4 pagesQuick Report: Acunetix Security Auditgandariangmbojo2023No ratings yet
- Moodle PresentationDocument22 pagesMoodle Presentationsvinod sNo ratings yet
- Module 2 - Basic Comp Op and File MGTDocument45 pagesModule 2 - Basic Comp Op and File MGT77丨S A W ًNo ratings yet
- Win 2k8 Installing Casino and Admin 2.20.XxDocument4 pagesWin 2k8 Installing Casino and Admin 2.20.Xxfofi07No ratings yet
- ICF 9 1st SummativeDocument2 pagesICF 9 1st Summativeallan tomasNo ratings yet
- ZP Power-Pack Whitepaper3Document16 pagesZP Power-Pack Whitepaper3Juan David BoteroNo ratings yet
- Lovish'sDocument37 pagesLovish'sParas TalujaNo ratings yet
- What Are The Differences Between Windows and LinuxDocument8 pagesWhat Are The Differences Between Windows and LinuxGeorge MurphyNo ratings yet
- JennyDocument16 pagesJennyMyrna PanesNo ratings yet
- Dmxsoft SushiDocument1 pageDmxsoft SushiRichter SiegfriedNo ratings yet
- Exchange 2010 Mailbox Server Role Requirements Calculator: Blue VariablesDocument9 pagesExchange 2010 Mailbox Server Role Requirements Calculator: Blue VariableswaitslipknotbleedNo ratings yet
- Exam Az 800 Administering Windows Server Hybrid Core Infrastructure Skills MeasuredDocument5 pagesExam Az 800 Administering Windows Server Hybrid Core Infrastructure Skills MeasuredMike DanielNo ratings yet
- Linda Pagan: 8514 Solitude Hill LN Richmond, TX 77407 (713) 384-8476 Lindarpagan@gmail - Co MDocument2 pagesLinda Pagan: 8514 Solitude Hill LN Richmond, TX 77407 (713) 384-8476 Lindarpagan@gmail - Co Mapi-355399601No ratings yet
- Software - Components & CharacteristicsDocument2 pagesSoftware - Components & CharacteristicsvsrajeshvsNo ratings yet
- Installation Guide SaltinourHair 19Document9 pagesInstallation Guide SaltinourHair 19VivienLamNo ratings yet
- Vijeo Quick Start Tutorial V720Document114 pagesVijeo Quick Start Tutorial V720ssgfreemailNo ratings yet
- Adobe Photoshop - Create Smart Objects PDFDocument3 pagesAdobe Photoshop - Create Smart Objects PDFmukasuraNo ratings yet
- Kickas Proxy WebsitesDocument7 pagesKickas Proxy Websiteskichu123No ratings yet
- Name: Dhanraj B. Ranvirkar Topic: Basics of GitDocument7 pagesName: Dhanraj B. Ranvirkar Topic: Basics of GitRitik bhadoriaNo ratings yet
- ZK 6.5.0 Installation GuideDocument115 pagesZK 6.5.0 Installation Guideachile123No ratings yet
- Components of Forcepoint DLP Management ServerDocument8 pagesComponents of Forcepoint DLP Management ServerAnandapriya MohantaNo ratings yet
- In Social Media MarketingDocument2 pagesIn Social Media MarketingNOR FAQIHAH NADHRAHNo ratings yet
- FortifyDocument100 pagesFortifyfernando PalloNo ratings yet
- Project On - Web Devlopment and PythonDocument26 pagesProject On - Web Devlopment and PythonRishaw KumarNo ratings yet
- ABAP Program To Delete A File From The Application Server - Code Gallery - SCN WikiDocument4 pagesABAP Program To Delete A File From The Application Server - Code Gallery - SCN Wikisdv varshneyNo ratings yet