Professional Documents
Culture Documents
Vulnerability Assessment Sample Report
Vulnerability Assessment Sample Report
Uploaded by
santoshs2002848Copyright:
Available Formats
You might also like
- Compliors Sample IT Policy For PCI DSS 1 PDFDocument87 pagesCompliors Sample IT Policy For PCI DSS 1 PDFsantoshs2002848No ratings yet
- List of ISO27001 Templates Iso27001templates PDFDocument3 pagesList of ISO27001 Templates Iso27001templates PDFsantoshs2002848No ratings yet
- Advanced Web Attacks and Exploitation: Offensive SecurityDocument9 pagesAdvanced Web Attacks and Exploitation: Offensive SecurityMinh Tan100% (1)
- A Specimen of Network Security Scan ReportDocument68 pagesA Specimen of Network Security Scan ReportM. Saad JumaniNo ratings yet
- Rapport D'analyse de Vulnérabilité: Website Vulnerability Scanner Report (Light)Document4 pagesRapport D'analyse de Vulnérabilité: Website Vulnerability Scanner Report (Light)Amira JilaliNo ratings yet
- Website Vulnerability Scanner Report (Light)Document5 pagesWebsite Vulnerability Scanner Report (Light)Roberto SihombingNo ratings yet
- Evasion Techniques and Breaching Defenses: Offensive SecurityDocument11 pagesEvasion Techniques and Breaching Defenses: Offensive SecurityAkbar AnggamaulanaNo ratings yet
- PentestTools WebsiteScanner ReportDocument7 pagesPentestTools WebsiteScanner ReportMario Sernaque RumicheNo ratings yet
- Comprehensive Report: Acunetix Threat Level 3Document23 pagesComprehensive Report: Acunetix Threat Level 3bugtestNo ratings yet
- Evasion Techniques and Breaching Defenses: Offensive SecurityDocument11 pagesEvasion Techniques and Breaching Defenses: Offensive SecuritySohel AhmedNo ratings yet
- Detailed Scan Report: Identified Confirmed CriticalDocument103 pagesDetailed Scan Report: Identified Confirmed CriticalViktor CherenapovNo ratings yet
- Affected Items HTTP Plen inDocument26 pagesAffected Items HTTP Plen inAnjura BegumNo ratings yet
- Scan Report PDFDocument6 pagesScan Report PDFJulian MartinezNo ratings yet
- Quick Report: Acunetix Security AuditDocument25 pagesQuick Report: Acunetix Security AuditCristian RamirezNo ratings yet
- Website Vulnerability Scanner Report (Light)Document4 pagesWebsite Vulnerability Scanner Report (Light)MasBaNo ratings yet
- ReportDocument10 pagesReportmanjeetyadav19No ratings yet
- NSE 4 7.0 Sample Questions - Attempt Review2Document10 pagesNSE 4 7.0 Sample Questions - Attempt Review2Subgerencia TecnogiaNo ratings yet
- Opevas Sample ReportDocument60 pagesOpevas Sample ReportjuanNo ratings yet
- SystemCheckReport 09102020 0138Document1 pageSystemCheckReport 09102020 0138nabilNo ratings yet
- PentestTools WebsiteScanner ReportDocument8 pagesPentestTools WebsiteScanner ReportRolando FrancoNo ratings yet
- Security Sample VAPT ReportDocument28 pagesSecurity Sample VAPT ReportRavi GiriNo ratings yet
- Scan Report CRMDocument17 pagesScan Report CRMWeb SploitNo ratings yet
- Web Application Audit Report: Demo AccountDocument12 pagesWeb Application Audit Report: Demo AccountSamuel KonanNo ratings yet
- Advisory2017 09 - CDS 57676Document5 pagesAdvisory2017 09 - CDS 57676Massimo MorelliNo ratings yet
- Website Vulnerability Scanner Sample Report OptimizedDocument11 pagesWebsite Vulnerability Scanner Sample Report OptimizedPauloNo ratings yet
- Tomcat Vulnerability Sample ReportDocument11 pagesTomcat Vulnerability Sample ReportandreirosuNo ratings yet
- CiscoDocument92 pagesCiscoari sirwanNo ratings yet
- Astra Security Sample VAPT ReportDocument28 pagesAstra Security Sample VAPT Reporthanuman1999No ratings yet
- Executive: Acunetix Security AuditDocument3 pagesExecutive: Acunetix Security AuditIbrahim qashtaNo ratings yet
- Comprehensive Report: Acunetix Threat Level 3Document37 pagesComprehensive Report: Acunetix Threat Level 3Yudha Trias RusmanaNo ratings yet
- ReportDocument7 pagesReportAznimar ZainuddinNo ratings yet
- Usenixsec 05Document36 pagesUsenixsec 05mohamedsamirnassar1993No ratings yet
- Final Del Formulario: PHP PHP 5.2.3Document2 pagesFinal Del Formulario: PHP PHP 5.2.3NewtoniXNo ratings yet
- ResultDocument83 pagesResultMaryamNo ratings yet
- Assessment Report: (076271c3)Document87 pagesAssessment Report: (076271c3)Marco SciortinoNo ratings yet
- Vulnerabiliades - DiccionarioDocument142 pagesVulnerabiliades - DiccionarioJohan MorilloNo ratings yet
- Phase2 Security ReportDocument64 pagesPhase2 Security ReportAnonymous r3xb805ENo ratings yet
- (Divi Report) Daptatech RepDocument5 pages(Divi Report) Daptatech RepcarlosNo ratings yet
- Developer ExampleDocument87 pagesDeveloper ExamplehardironNo ratings yet
- ZAP Scanning Report: Site: Https://webapps - Bps.go - IdDocument4 pagesZAP Scanning Report: Site: Https://webapps - Bps.go - Idyoga_wpNo ratings yet
- System Check ResultsDocument1 pageSystem Check ResultsSergio Raúl Ponce GonzalesNo ratings yet
- Tech Talks 52 Good To The Last Drop Writing Robust Flask and Django AppsDocument49 pagesTech Talks 52 Good To The Last Drop Writing Robust Flask and Django Appsumayrh@gmail.comNo ratings yet
- Cargill Web Application Scanning ReportDocument27 pagesCargill Web Application Scanning ReportHari KingNo ratings yet
- Website Vulnscan Sample ReportDocument8 pagesWebsite Vulnscan Sample ReportBalaji RajaramanNo ratings yet
- PhpinfoDocument2 pagesPhpinfomistryjaysheel3No ratings yet
- Astra Security - Sample Report For VAPTDocument30 pagesAstra Security - Sample Report For VAPTIndian OpinionNo ratings yet
- AllDocument48 pagesAlldont4getNo ratings yet
- Developer Report: Acunetix Website Audit 23 December, 2021Document7 pagesDeveloper Report: Acunetix Website Audit 23 December, 2021BAGAS TRI RAMADANA -No ratings yet
- Hunting Beacons: Bartosz JerzmanDocument52 pagesHunting Beacons: Bartosz Jerzmanvha KyNo ratings yet
- Website Vulnerability Scanner Report (Light)Document6 pagesWebsite Vulnerability Scanner Report (Light)alex681219No ratings yet
- VPN Troubleshooting For CheckpointDocument24 pagesVPN Troubleshooting For CheckpointSachin Saini100% (1)
- Johannes B. Ullrich, Ph.D. SANS Technology Institute: GHOST Glibc Gethostbyname Vulnerability CVE-2015-0235Document17 pagesJohannes B. Ullrich, Ph.D. SANS Technology Institute: GHOST Glibc Gethostbyname Vulnerability CVE-2015-0235Saul RamosNo ratings yet
- Vulnerabilities EhipDocument11 pagesVulnerabilities EhipSeanNo ratings yet
- Penetration Testing With Kali Linux (PWK)Document6 pagesPenetration Testing With Kali Linux (PWK)DF QWERTNo ratings yet
- 5 Common Web Application VulnerabilitiesDocument4 pages5 Common Web Application VulnerabilitiesAnonymous Fhs3ufkCNo ratings yet
- Networkvulnerability Scan Sample ReportDocument4 pagesNetworkvulnerability Scan Sample ReportVenâncio GuedesNo ratings yet
- Having Fun With ComDocument65 pagesHaving Fun With ComLeonardoNo ratings yet
- Developer Report PDFDocument65 pagesDeveloper Report PDFAnonymous JyKPfbZBQNo ratings yet
- Active DirectoryDocument10 pagesActive DirectoryKindraNo ratings yet
- Web Application Defender's Cookbook: Battling Hackers and Protecting UsersFrom EverandWeb Application Defender's Cookbook: Battling Hackers and Protecting UsersNo ratings yet
- Innocent Code: A Security Wake-Up Call for Web ProgrammersFrom EverandInnocent Code: A Security Wake-Up Call for Web ProgrammersRating: 3.5 out of 5 stars3.5/5 (3)
- Identity Management: Origination of Concept of I & AM ProductsDocument18 pagesIdentity Management: Origination of Concept of I & AM Productssantoshs2002848100% (1)
- Splunk - Custom Search QueriesDocument3 pagesSplunk - Custom Search Queriessantoshs2002848No ratings yet
- Information Security Information Security: Cyberark Administrator'S Operations ManualDocument37 pagesInformation Security Information Security: Cyberark Administrator'S Operations Manualsantoshs2002848No ratings yet
- ISO 9001-2015 Quality Management System Manual D1.2Document36 pagesISO 9001-2015 Quality Management System Manual D1.2santoshs2002848100% (1)
- Introducing Cyberark: Security For The Heart of The EnterpriseDocument9 pagesIntroducing Cyberark: Security For The Heart of The Enterprisesantoshs2002848No ratings yet
- What Is Identity??Document4 pagesWhat Is Identity??santoshs2002848No ratings yet
- Stages of Malware AnalysisDocument6 pagesStages of Malware Analysissantoshs2002848No ratings yet
- WHITEPAPER - Layer 2 Ethernet Bridge DesignDocument4 pagesWHITEPAPER - Layer 2 Ethernet Bridge Designsantoshs2002848No ratings yet
- Q1) What Are The Primary Functions of Cyberark?Document8 pagesQ1) What Are The Primary Functions of Cyberark?santoshs2002848No ratings yet
- Consultant Bill Format: Template#: c4127 Title: Consultant Bill Format Category: Download This Template in Excel FormatDocument2 pagesConsultant Bill Format: Template#: c4127 Title: Consultant Bill Format Category: Download This Template in Excel Formatsantoshs2002848No ratings yet
- 8.2 IdentityIQ Work ItemsDocument6 pages8.2 IdentityIQ Work Itemssantoshs2002848No ratings yet
- Section A (Answer ONE Question From This Section)Document5 pagesSection A (Answer ONE Question From This Section)santoshs2002848No ratings yet
- Bury CCG Information Governance Incident Reporting Policy V4.0Document15 pagesBury CCG Information Governance Incident Reporting Policy V4.0santoshs2002848No ratings yet
- HCL Anti-Bribery Policy ExternalDocument16 pagesHCL Anti-Bribery Policy Externalsantoshs2002848No ratings yet
- Enterprise Risk Management Sample PolicyDocument4 pagesEnterprise Risk Management Sample Policysantoshs2002848No ratings yet
- ESM Upgrade To 72 PDFDocument46 pagesESM Upgrade To 72 PDFsantoshs2002848No ratings yet
- ESM Upgrade To 72 PDFDocument46 pagesESM Upgrade To 72 PDFsantoshs2002848No ratings yet
- Data Connector Blog 3.0 PDFDocument11 pagesData Connector Blog 3.0 PDFsantoshs2002848No ratings yet
- Example Pci Dss v3 It Security Policy Pcidss ComplianceDocument24 pagesExample Pci Dss v3 It Security Policy Pcidss Compliancesantoshs2002848No ratings yet
- Ipam 1600 PDocument148 pagesIpam 1600 Psagar323No ratings yet
- D-Link AirPlus G DI-524Document95 pagesD-Link AirPlus G DI-524SurviversNo ratings yet
- Merged CNDocument257 pagesMerged CNYuvaraj TankalaNo ratings yet
- ComputerNetwork C5-1 enDocument84 pagesComputerNetwork C5-1 enNguyên VĩnhNo ratings yet
- MITSUBISHI - Manual - PLC - Iq-R - SLMP Connect C# MrJ4BDocument232 pagesMITSUBISHI - Manual - PLC - Iq-R - SLMP Connect C# MrJ4Bca bienNo ratings yet
- InnGate 3 Command Line Interface Reference r1.01Document26 pagesInnGate 3 Command Line Interface Reference r1.01Davi Sadaseeven SaminadenNo ratings yet
- Network Vulnerability Scan With Openvas Report (Light)Document2 pagesNetwork Vulnerability Scan With Openvas Report (Light)alfan666No ratings yet
- Whisp Aps MibDocument92 pagesWhisp Aps MibSamuel JesusNo ratings yet
- Guide To Firewalls and Network Security: Chapter 7 SolutionsDocument3 pagesGuide To Firewalls and Network Security: Chapter 7 SolutionsMohlomphegi Bennet AphaneNo ratings yet
- HTTP Tunnel 1Document6 pagesHTTP Tunnel 1Adailton CruzNo ratings yet
- DS-K1T331 Series Face Recognition Terminal - Datasheet - V1.0.1 - 20200406Document3 pagesDS-K1T331 Series Face Recognition Terminal - Datasheet - V1.0.1 - 20200406CRISTHIAN CAMILO QUINTIN CRUZNo ratings yet
- ALOHADocument18 pagesALOHAMayank JunejaNo ratings yet
- BGP FlowSpecDocument68 pagesBGP FlowSpeckholis_smktelkomNo ratings yet
- Computer Networks MCQ Interview Questions With Answer Set-8 - InfoTechSiteDocument3 pagesComputer Networks MCQ Interview Questions With Answer Set-8 - InfoTechSitelovelyosmile2530% (1)
- 400-051 CciecollabDocument18 pages400-051 CciecollabRose WhiteNo ratings yet
- 30 Netkit Lab BGP Transit AsDocument171 pages30 Netkit Lab BGP Transit AspierpaoloNo ratings yet
- CoursDocument227 pagesCoursSORO YALAMOUSSANo ratings yet
- Iskratel Innbox G67 Datasheet EN PDFDocument2 pagesIskratel Innbox G67 Datasheet EN PDFJose JoseNo ratings yet
- IDS, Firewall & HoneypotDocument11 pagesIDS, Firewall & Honeypotanon_100036097100% (4)
- Sim7020 Series: Simcom Nb-Iot ModuleDocument3 pagesSim7020 Series: Simcom Nb-Iot ModuleAlejandro DemitiNo ratings yet
- SARA-R5 ATCommands (UBX-19047455)Document489 pagesSARA-R5 ATCommands (UBX-19047455)aerNo ratings yet
- Captive Portal Config Using FreeRadious and CoovachilliDocument9 pagesCaptive Portal Config Using FreeRadious and Coovachillirubin nitsuhNo ratings yet
- Wireshark: Presented By: Hiral Chhaya, Anvita PriyamDocument24 pagesWireshark: Presented By: Hiral Chhaya, Anvita PriyamNaponee Nap-shot EvansNo ratings yet
- Pethe, R.M., Burnase, S.R. (2011) Technical Era Language of The Networking - EIGRPDocument5 pagesPethe, R.M., Burnase, S.R. (2011) Technical Era Language of The Networking - EIGRPLee HeaverNo ratings yet
- 2 Twinks With Cum in Face - RedTubeDocument638 pages2 Twinks With Cum in Face - RedTubeMoises Gomes da luzNo ratings yet
- Module 5 MCQDocument32 pagesModule 5 MCQGaurav PandeyNo ratings yet
- Juniper AP-24 DeploymentDocument43 pagesJuniper AP-24 Deploymentcatawiki.businessNo ratings yet
- Css 4th Quarter Week 3Document6 pagesCss 4th Quarter Week 3Hera AsuncionNo ratings yet
- Advance Cyber Security AssignmentDocument2 pagesAdvance Cyber Security AssignmentVenkat Sai Krishna TummisettyNo ratings yet
- Configuring Spanning Tree Protocol (STP) and Advanced STP FeaturesDocument84 pagesConfiguring Spanning Tree Protocol (STP) and Advanced STP FeaturesSergio Antonio Villarreal MarinNo ratings yet
Vulnerability Assessment Sample Report
Vulnerability Assessment Sample Report
Uploaded by
santoshs2002848Original Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Vulnerability Assessment Sample Report
Vulnerability Assessment Sample Report
Uploaded by
santoshs2002848Copyright:
Available Formats
Vulnerability Assessment Report
Demo Account
176.28.50.165
http://tes thtml5.vulnweb.com/#/popular
Confidential
Scan Date: 2017-01-17
Scope
Vulnerability As s es s ment for IP Addres s 176.28.50.165.
Limitations
1. The entire tes t was carried out with no prior knowledge of the s ys tems and applications .
2. All tes t were carried out without any known credentials to s ys tems and applications .
3. Indus Guard does not carry out any DoS attacks or to run any exploits which can affect s ys tems availability.
Confidentiality
This document contains s ens itive and/or confidential information, do not dis tribute, email, fax or trans fer via any
electronic mechanis m without proper authorization. Information contained with in this document s hould be handled with
appropriate caution. While reas onable attempts have been made to confirm the accuracy of the data contained herein,
Indus Guard, as s umes no liability for the completenes s , us e of, or conclus ions drawn from s uch data.
Disclaimer
This , or any other, Security Audit cannot and does not guarantee s ecurity. Indus Guard makes no warranty or claim of any
kind, whats oever, about the accuracy or us efulnes s of any information provided herein. By us ing this information you
agree that Indus Guard s hall be held harmles s in any event. Indus Guard makes this information available s olely under its
Terms of Service Agreement publis hed at s oc.indus guard.com.
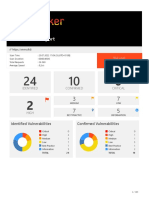
Executive Summary
Total number of vulnerabilities identified for 176.28.50.165 is 209
Page 2 of 120
Scan Date: 2017-01-17
Vulnerability v/s Severity Pie Chart Vulnerability v/s Open Status Pie Chart
Vulnerability v/s Severity Bar Chart Vulnerability Summary
Severity Total
Critical 4
High 23
Medium 86
Low 14
Info 82
Page 3 of 120
Scan Date: 2017-01-17
Vulnerability Details
Title Total
OpenSSH < 7.0 Multiple Vulnerabilities 1
PHP 5.3.x < 5.3.15 Multiple Vulnerabilities 1
PHP Uns upported Vers ion Detection 1
Uns upported Unix Operating Sys tem 1
CGI Generic SQL Injection 1
CGI Generic SQL Injection (2nd pas s ) 1
CGI Generic SQL Injection (blind) 1
CGI Generic SQL Injection (blind, time bas ed) 1
nginx < 1.4.4 / 1.5.7 ngx_pars e_http Security 1
Bypas s
OpenSSH < 6.9 Multiple Vulnerabilities 1
PHP 5 < 5.2.7 Multiple Vulnerabilities 1
PHP 5.3.x < 5.3.13 CGI Query String Code 1
Execution
PHP 5.3.x < 5.3.14 Multiple Vulnerabilities 1
PHP 5.3.x < 5.3.26 Multiple Vulnerabilities 1
PHP 5.3.x < 5.3.27 Multiple Vulnerabilities 1
PHP 5.3.x < 5.3.29 Multiple Vulnerabilities 1
PHP 5.x < 5.2 Multiple Vulnerabilities 1
PHP 5.x < 5.2.2 Information Dis clos ure 1
PHP < 4.4.7 / 5.2.2 Multiple Vulnerabilities 1
PHP < 5.2.1 Multiple Vulnerabilities 1
PHP < 5.2.11 Multiple Vulnerabilities 1
PHP < 5.2.6 Multiple Vulnerabilities 1
PHP < 5.2.8 Multiple Vulnerabilities 1
PHP < 5.3.11 Multiple Vulnerabilities 1
PHP < 5.3.12 / 5.4.2 CGI Query String Code 1
Execution
PHP < 5.3.9 Multiple Vulnerabilities 1
ProFTPD < 1.3.3g / 1.3.4 Res pons e Pool Us e- 1
After-Free Code Execution
CGI Generic Cookie Injection Scripting 1
CGI Generic Cros s -Site Reques t Forgery 1
Detection (potential)
CGI Generic Cros s -Site Scripting 1
(comprehens ive tes t)
CGI Generic Cros s -Site Scripting (extended 1
patterns )
CGI Generic Cros s -Site Scripting (quick tes t) 1
CGI Generic HTML Injections (quick tes t) 1
CGI Generic Local File Inclus ion 1
nginx < 1.6.2 / 1.7.5 SSL Ses s ion Reus e 1
OpenSSH < 5.7 Multiple Vulnerabilities 1
Page 4 of 120
Scan Date: 2017-01-17
OpenSSH < 5.9 Multiple DoS 1
OpenSSH < 6.6 Multiple Vulnerabilities 1
OpenSSH >= 2.3.0 AllowTcpForwarding Port 1
Bouncing
OpenSSH LoginGraceTime / MaxStartups DoS 1
OpenSSH S/KEY Authentication Account 1
Enumeration
OpenSSL 'ChangeCipherSpec' MiTM 5
Vulnerability
OPIE w/ OpenSSH Account Enumeration 1
PHP 5.3.x < 5.3.21 cURL X.509 Certificate 1
Domain Name Matching MiTM Weaknes s
PHP 5.3.x < 5.3.22 Multiple Vulnerabilities 1
PHP 5.3.x < 5.3.23 Information Dis clos ure 1
PHP 5.3.x < 5.3.28 Multiple OpenSSL 1
Vulnerabilities
PHP < 5.2.10 Multiple Vulnerabilities 1
PHP < 5.2.12 Multiple Vulnerabilities 1
PHP < 5.2.3 Multiple Vulnerabilities 1
PHP < 5.2.4 Multiple Vulnerabilities 1
PHP < 5.2.5 Multiple Vulnerabilities 1
PHP < 5.2.9 Multiple Vulnerabilities 1
PHP < 5.3.2 / 5.2.13 Multiple Vulnerabilities 1
PHP Foreign Function Interface Arbitrary DLL 1
Loading s afe_mode Res triction Bypas s
PHP ip2long Function String Validation 1
Weaknes s
PHP PHP_RSHUTDOWN_FUNCTION Security 1
Bypas s
PHP Symlink Function Race Condition 1
open_bas edir Bypas s
SSL Anonymous Cipher Suites Supported 1
SSL Certificate Cannot Be Trus ted 5
SSL Certificate Expiry 5
SSL Certificate with Wrong Hos tname 5
SSL DROWN Attack Vulnerability (Decrypting 2
RSA with Obs olete and Weakened eNcryption)
SSL Medium Strength Cipher Suites 5
Supported
SSL Self-Signed Certificate 5
SSL Vers ion 2 (v2) Protocol Detection 3
SSL Weak Cipher Suites Supported 4
SSL/TLS Diffie-Hellman Modulus <= 1024 Bits 1
(LogJam)
SSL/TLS EXPORT_RSA <= 512-bit Cipher 4
Suites Supported (FREAK)
SSL/TLS Protocol Initialization Vector 5
Implementation Information Dis clos ure
Vulnerability
Page 5 of 120
Scan Date: 2017-01-17
SSLv3 Padding Oracle On Downgraded 3
Legacy Encryption Vulnerability (POODLE)
Web Application SQL Backend Identification 1
Web Application Vulnerable to Clickjacking 1
Web Server info.php / phpinfo.php Detection 1
CGI Generic Injectable Parameter 1
FTP Supports Clear Text Authentication 1
PHP mb_s end_mail() Function Parameter 1
Security Bypas s
POP3 Cleartext Logins Permitted 1
Portable OpenSSH s s h-keys ign s s h-rand- 1
helper Utility File Des criptor Leak Local
Information Dis clos ure
SMTP Service Cleartext Login Permitted 1
SSH Server CBC Mode Ciphers Enabled 1
SSH Weak MAC Algorithms Enabled 1
SSL RC4 Cipher Suites Supported 5
Web Server Us es Plain Text Authentication 1
Forms
Brows able Web Directories 1
CGI Generic Tes ts HTTP Errors 1
CGI Generic Tes ts Load Es timation (all tes ts ) 1
CGI Generic Tes ts Timeout 1
Common Platform Enumeration (CPE) 1
Device Type 1
DNS Server Detection 2
DNS Server Fingerprinting 1
DNS Server hos tname.bind Map Hos tname 1
Dis clos ure
DNS Server Vers ion Detection 1
External URLs 1
FTP Server Detection 1
HTTP Methods Allowed (per directory) 3
HTTP Server Type and Vers ion 3
HTTP X-Content-Security-Policy Res pons e 1
Header Us age
HTTP X-Frame-Options Res pons e Header 1
Us age
HyperText Trans fer Protocol (HTTP) 3
Information
IMAP Service Banner Retrieval 2
IMAP Service STARTTLS Command Support 1
OpenSSL Detection 5
Patch Report 1
PHP Vers ion 1
POP Server Detection 2
POP3 Service STLS Command Support 1
Service Detection: 3 ASCII Digit Code 1
Page 6 of 120
Scan Date: 2017-01-17
Res pons es
SMTP Authentication Methods 2
SMTP Server Detection 2
SSH Algorithms and Languages Supported 1
SSH Protocol Vers ions Supported 1
SSH Server Type and Vers ion Information 1
SSL / TLS Vers ions Supported 5
SSL Certificate commonName Mis match 5
SSL Certificate Information 5
SSL Cipher Block Chaining Cipher Suites 5
Supported
SSL Cipher Suites Supported 5
SSL Perfect Forward Secrecy Cipher Suites 1
Supported
SSL Ses s ion Res ume Supported 3
TCP/IP Times tamps Supported 1
Web Application Potentially Sens itive CGI 1
Parameter Detection
Web mirroring 1
Web Server Allows Pas s word Auto- 1
Completion
Web Server Directory Enumeration 1
Web Server Harves ted Email Addres s es 1
Web Site Client Acces s Policy File Detection 1
Web Site Cros s -Domain Policy File Detection 1
Open Services
www (tcp/8880)
www (tcp/8443)
pop3 (tcp/995)
imap (tcp/993)
smtp (tcp/465)
imap (tcp/143)
pop3 (tcp/110)
Page 7 of 120
Scan Date: 2017-01-17
pop3pw (tcp/106)
www (tcp/80)
dns (udp/53)
dns (tcp/53)
smtp (tcp/25)
ssh (tcp/22)
ftp (tcp/21)
Vulnerabilities
Alert ID: 84650 Found on: 2017-01-17 Severity: Critical
PHP Unsupported Version Detection (tcp/80)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 10.0
Cvss Score: 10.0
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C
PCI Compliance: Fail
Description:
According to its vers ion, the ins tallation of PHP on the remote hos t is no longer s upported. As a res ult, it is likely to
contain s ecurity vulnerabilities .
Solution:
Upgrade to a vers ion of PHP that is currently s upported.
Result:
Source : X-Powered-By: PHP/5.3.10-1~lucid+2uwsgi2 Installed version : 5.3.10-1~lucid+2uwsgi2 End of support
date : 2014/08/14 Announcem ent : http://php.net/archive/2014.php#id2014-08-14-1 Supported versions : 7.1.x /
7.0.x / 5.6.x
References:
https ://wiki.php.net/rfc/releas eproces s
Alert ID: 84663 Found on: 2017-01-17 Severity: Critical
PHP 5.3.x < 5.3.15 Multiple Vulnerabilities (tcp/80)
Open Status: NEW First Found: 2017-01-17
Page 8 of 120
Scan Date: 2017-01-17
CVE ID: CVE-2012-2688,CVE-2012-3365
Cvss Base: 10.0
Cvss Score: 10.0
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C
PCI Compliance: Fail
Description:
According to its banner, the vers ion of PHP ins talled on the remote hos t is 5.3.x earlier than 5.3.15, and is , therefore,
potentially affected by the following vulnerabilities :
- An uns pecified overflow vulnerability exis ts in the function '_php_s tream_s candir' in the file 'main/s treams /s treams .c'.
(CVE-2012-2688)
- An uns pecified error exis ts that can allow the 'open_bas edir' cons traint to be bypas s ed.
(CVE-2012-3365)
Solution:
Upgrade to PHP vers ion 5.3.15 or later.
Result:
Version source : X-Powered-By: PHP/5.3.10-1~lucid+2uwsgi2 Installed version : 5.3.10-1~lucid+2uwsgi2 Fixed
version : 5.3.15
References:
http://www.php.net/ChangeLog-5.php#5.3.15
Alert ID: 84687 Found on: 2017-01-17 Severity: Critical
OpenSSH < 7.0 Multiple Vulnerabilities (tcp/22)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 10.0
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C
Description:
According to its banner, the vers ion of OpenSSH running on the remote hos t is prior to 7.0. It is , therefore, affected by the
following vulnerabilities :
- A flaw exis ts in the kbdint_next_device() function in file auth2-chall.c that allows the circumvention of MaxAuthTries
during keyboard-interactive authentication.
An attacker can exploit this is s ue to force the s ame authentication method to be tried thous ands of times in a s ingle
pas s by us ing a crafted keyboard-interactive 'devices ' s tring, thus allowing a brute-force attack or caus ing a denial of
s ervice. (CVE-2015-5600)
- A s ecurity bypas s vulnerability exis ts in s s hd related to PAM s upport. An authenticated, remote attacker can exploit this
to impact the pre-authentication proces s , allowing the pos s ible execution of arbitrary code. Note that this is s ue only
affects Portable OpenSSH.
(OSVDB 126030)
- A flaw exis ts in s s hd due to s etting ins ecure world-writable permis s ions for TTYs . A local attacker can exploit this , by
injecting crafted terminal es cape s equences , to execute commands for logged-in us ers .
(OSVDB 126031)
- A us e-after-free error exis ts in s s hd related to PAM s upport. A remote attacker can exploit this to impact the pre-
authentication proces s , allowing the pos s ible execution of arbitrary code. Note that this is s ue only affects Portable
OpenSSH. (OSVDB 126033)
Solution:
Upgrade to OpenSSH 7.0 or later.
Page 9 of 120
Scan Date: 2017-01-17
Result:
Version source : SSH-2.0-O penSSH_5.3p1 Debian-3ubuntu7.1 Installed version : 5.3p1 Fixed version : 7.0
References:
http://www.opens s h.com/txt/releas e-7.0
Alert ID: 84704 Found on: 2017-01-17 Severity: Critical
Unsupported Unix Operating System (tcp/0)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 10.0
Cvss Score: 10.0
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C
PCI Compliance: Fail
Description:
According to its vers ion, the remote Unix operating s ys tem is obs olete and no longer maintained by its vendor or
provider.
Lack of s upport implies that no new s ecurity patches will be releas ed for it.
Solution:
Upgrade to a newer vers ion.
Result:
Ubuntu 10.04 support ended on 2013-05-09 (Desktop) / 2015-04-30 (Server).Upgrade to Ubuntu 16.04.For m ore
inform ation, see : https://wiki.ubuntu.com /Releases
Alert ID: 84606 Found on: 2017-01-17 Severity: High
CGI Generic SQL Injection (2nd pass) (tcp/80)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 7.5
Cvss Score: 7.5
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P
PCI Compliance: Fail
Description:
By providing s pecially crafted parameters to CGIs , Indus Guard was able to get an error from the underlying databas e.
This error s ugges ts that the CGI is affected by a SQL injection vulnerability.
An attacker may exploit this flaw to bypas s authentication, read confidential data, modify the remote databas e, or even
take control of the remote operating s ys tem.
Solution:
Modify the relevant CGIs s o that they properly es cape arguments .
Result:
During testing for cookie m anipulation vulnerabilities, SQ L errors were noticed, suggesting that the scripts /
param eters listed below m ay also be vulnerable to SQ L Injection (SQ Li).-------- request --------GET /listproducts.php?
cat=<script>docum ent.cookie="testbodp=9194;"</script> HTTP/1.1Host: rs202995.rs.hosteurope.deAccept-
C harset: iso-8859-1,utf-8;q=0.9,*;q=0.1Accept-Language: enC onnection: Keep-AliveUser-Agent: Mozilla/4.0
(com patible; MSIE 8.0; Windows NT 5.1; Trident/4.0)Pragm a: no-cacheAccept: im age/gif, im age/x-xbitm ap,
im age/jpeg, im age/pjpeg, im age/png, */*-------------------------------- output --------<! -- InstanceBeginEditable
nam e="content_rgn" --><div id="content">Error: You have an error in your SQ L syntax; check the m anual that
corresponds to your MySQ L server version for the right syntax to use near
'=<script>docum ent.cookie="testbodp=9194;"</script>' at line 1Warning: m ysql_fetch_array() expects
Page 10 of 120
Scan Date: 2017-01-17
param eter 1 to be resource, b [...]</div>-------------------------------- request --------GET /listproducts.php?
artist=<script>docum ent.cookie="testbodp=9194;"</script> HTTP/1.1Host: rs202995.rs.hosteurope.deAccept-
C harset: iso-8859-1,utf-8;q=0.9,*;q=0.1Accept-Language: enC onnection: Keep-AliveUser-Agent: Mozilla/4.0
(com patible; MSIE 8.0; Windows NT 5.1; Trident/4.0)Pragm a: no-cacheAccept: im age/gif, im age/x-xbitm ap,
im age/jpeg, im age/pjpeg, im age/png, */*-------------------------------- output --------<! -- InstanceBeginEditable
nam e="content_rgn" --><div id="content">Error: You have an error in your SQ L syntax; check the m anual that
corresponds to your MySQ L server version for the right syntax to use near
'=<script>docum ent.cookie="testbodp=9194;"</script>' at line 1Warning: m ysql_fetch_array() expects
param eter 1 to be resource, b [...]</div>-------------------------------- request --------GET /listproducts.php?
cat=<script>docum ent.cookie="testbodp=9194;"</script>& artist=1 HTTP/1.1Host:
rs202995.rs.hosteurope.deAccept-C harset: iso-8859-1,utf-8;q=0.9,*;q=0.1Accept-Language: enC onnection: Keep-
AliveUser-Agent: Mozilla/4.0 (com patible; MSIE 8.0; Windows NT 5.1; Trident/4.0)Pragm a: no-cacheAccept:
im age/gif, im age/x-xbitm ap, im age/jpeg, im age/pjpeg, im age/png, */*-------------------------------- output --------<! --
InstanceBeginEditable nam e="content_rgn" --><div id="content">Error: You have an error in your SQ L syntax;
check the m anual that corresponds to your MySQ L server version for the right syntax to use near
'=<script>docum ent.cookie="testbodp=9194;"</script>' at line 1Warning: m ysql_fetch_array() expects
param eter 1 to be resource, b [...]</div>------------------------During testing for arbitrary com m and execution (tim e
based) vulnerabilities, SQ L errors were noticed, suggesting that the scripts / param eters listed below m ay also be
vulnerable to SQ L Injection (SQ Li).-------- request --------GET /listproducts.php?
artist=1& cat=1% 20;% 20x% 20% 7C % 7C % 20sleep% 203% 20% 26 HTTP/1.1Host:
rs202995.rs.hosteurope.deAccept-C harset: iso-8859-1,utf-8;q=0.9,*;q=0.1Accept-Language: enC onnection: Keep-
AliveUser-Agent: Mozilla/4.0 (com patible; MSIE 8.0; Windows NT 5.1; Trident/4.0)Pragm a: no-cacheAccept:
im age/gif, im age/x-xbitm ap, im age/jpeg, im age/pjpeg, im age/png, */*-------------------------------- output --------<! --
InstanceBeginEditable nam e="content_rgn" --><div id="content">Error: You have an error in your SQ L syntax;
check the m anual that corresponds to your MySQ L server version for the right syntax to use near 'x || sleep 3 & '
at line 1Warning: m ysql_fetch_array() expects param eter 1 to be resource, b [...]</div>------------------------During
testing for blind SQ L injection (tim e based) vulnerabilities, SQ L errors were not
References:
http://en.wikipedia.org/wiki/SQL_injection
http://www.s ecuriteam.com/s ecurityreviews /5DP0N1P76E.html
http://www.s ecuritydocs .com/library/2651
http://projects .webapps ec.org/SQL-Injection
Alert ID: 84609 Found on: 2017-01-17 Severity: High
CGI Generic SQL Injection (blind) (tcp/80)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 7.5
Cvss Score: 7.5
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P
PCI Compliance: Fail
Description:
By s ending s pecially crafted parameters to one or more CGI s cripts hos ted on the remote web s erver, Indus Guard was
able to get a very different res pons e, which s ugges ts that it may have been able to modify the behavior of the application
and directly acces s the underlying databas e.
An attacker may be able to exploit this is s ue to bypas s authentication, read confidential data, modify the remote
databas e, or even take control of the remote operating s ys tem.
Note that this s cript is experimental and may be prone to fals e pos itives .
Solution:
Modify the affected CGI s cripts s o that they properly es cape arguments .
Page 11 of 120
Scan Date: 2017-01-17
Result:
Using the GET HTTP m ethod, IndusGuard found that :+ The following resources m ay be vulnerable to blind SQ L
injection :+ The 'artist' param eter of the /artists.php C GI :/artists.php?artist=1+and+1=0-------- output --------<! --
InstanceBeginEditable nam e="content_rgn" --><div id="content"><h2 id='pageNam e'>artist:
r4w8173</h2><div class='story'><p><p>Lorem ipsum dolor sit am et, consectetuer adipiscing elit. Donec m o
[...] Sed aliquam sem ut arcu. Phasellus sollicitudin. Vestibulum co [...]-------- vs --------<! -- InstanceBeginEditable
nam e="content_rgn" --><div id="content"></div><! -- InstanceEndEditable -->------------------------+ The 'cat'
param eter of the /listproducts.php C GI :/listproducts.php?artist=1& cat=1+and+1=0-------- output --------<! --
InstanceBeginEditable nam e="content_rgn" --><div id="content"><h2 id='pageNam e'>Posters</h2><div
class='story'><a href='product.php?pic=1'><h3>The shore</h3></a><p><a href='showim age.php?
file=./pictures/1.jpg' target='_blank'><im g style='cursor:pointer' border='0' align='left' src='showim age.php?
file=./pictures/1.jpg& size=160' width='160' he [...]Sed aliquam sem ut arcu.</p><p>painted by: <a
href='artists.php?ar [...]Sed aliquam sem ut arcu.</p><p>painted by: <a href='artists.php?ar [...]-------- vs --------<! --
InstanceBeginEditable nam e="content_rgn" --><div id="content"></div><! -- InstanceEndEditable --><! --end
content -->------------------------/listproducts.php?artist=1& cat=1+and+1=0 {2}-------- output --------<! --
InstanceBeginEditable nam e="content_rgn" --><div id="content"><h2 id='pageNam e'>Posters</h2><div
class='story'><a href='product.php?pic=1'><h3>The shore</h3></a><p><a href='showim age.php?
file=./pictures/1.jpg' target='_blank'><im g style='cursor:pointer' border='0' align='left' src='showim age.php?
file=./pictures/1.jpg& size=160' width='160' he [...]Sed aliquam sem ut arcu.</p><p>painted by: <a
href='artists.php?ar [...]Sed aliquam sem ut arcu.</p><p>painted by: <a href='artists.php?ar [...]-------- vs --------<! --
InstanceBeginEditable nam e="content_rgn" --><div id="content"></div><! -- InstanceEndEditable --><! --end
content -->------------------------+ The 'pic' param eter of the /product.php C GI :/product.php?pic=1+and+1=0-------- output
--------<! -- InstanceBeginEditable nam e="content_rgn" --><div id="content"><h2 id='pageNam e'>The
shore</h2><div class='story'><p><a href='showim age.php?file=./pictures/1.jpg' target='_blank'><im g
style='cursor:pointer' border='0' align='center' src='showim age.php?file=./pictures/1.jpg& size=160' width='160'
height='100'></a><h3>Short description</h3><p>Lo [...]Sed aliquam sem ut arcu.</p><h3>Long
description</h3><p><p>This picture is an 53 cm x 12 cm m asterpiece.-------- vs --------<! -- InstanceBeginEditable
nam e="content_rgn" --><div id="content"></div><! -- InstanceEndEditable --><! --end content -->------------------------
C licking directly on these URLs should exhibit the issue :(you will probably need to read the HTML
source)http://rs202995.rs.hosteurope.de/artists.php?
artist=1+and+1=0http://rs202995.rs.hosteurope.de/listproducts.php?
artist=1& cat=1+and+1=0http://rs202995.rs.hosteurope.de/product.php?pic=1+and+1=0
References:
http://www.s ecuriteam.com/s ecurityreviews /5DP0N1P76E.html
http://www.s ecuritydocs .com/library/2651
http://projects .webapps ec.org/SQL-Injection
Alert ID: 84610 Found on: 2017-01-17 Severity: High
CGI Generic SQL Injection (blind, time based) (tcp/80)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 7.5
Cvss Score: 7.5
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P
PCI Compliance: Fail
Description:
By s ending s pecially crafted parameters to one or more CGI s cripts hos ted on the remote web s erver, Indus Guard was
able to get a s lower res pons e, which s ugges ts that it may have been able to modify the behavior of the application and
directly acces s the underlying databas e.
An attacker may be able to exploit this is s ue to bypas s authentication, read confidential data, modify the remote
databas e, or even take control of the remote operating s ys tem.
Note that this s cript is experimental and may be prone to fals e pos itives .
Page 12 of 120
Scan Date: 2017-01-17
Note that this s cript is experimental and may be prone to fals e pos itives .
Solution:
Modify the affected CGI s cripts s o that they properly es cape arguments .
Result:
Using the GET HTTP m ethod, IndusGuard found that :+ The following resources m ay be vulnerable to blind SQ L
injection (tim e based) :+ The 'artist' param eter of the /artists.php C GI :/artists.php?
artist=1% 20AND% 20SLEEP(21)=0-------- output --------<! DO C TYPE HTML PUBLIC "-//W3C //DTD HTML 4.01
Transitional//EN""http://www.w3.org/TR/htm l4/loose.dtd"><htm l><! -- InstanceBegin
tem plate="/Tem plates/m ain_dynam ic_tem plat [...]<head><m eta http-equiv="C ontent-Type" content="text/htm l;
charset=iso-8859-2"><! -- InstanceBeginEditable nam e="docum ent_title_rgn" --><title>artists</title><! --
InstanceEndEditable --><link rel="stylesheet" href="style.css" type="text/css">[...]------------------------+ The 'cat'
param eter of the /listproducts.php C GI :/listproducts.php?artist=1& cat=1% 20AND% 20SLEEP(3)=0-------- output -------
-------------------------+ The 'pic' param eter of the /product.php C GI :/product.php?pic=1% 20AND% 20SLEEP(21)=0--------
output --------<! DO C TYPE HTML PUBLIC "-//W3C //DTD HTML 4.01
Transitional//EN""http://www.w3.org/TR/htm l4/loose.dtd"><htm l><! -- InstanceBegin
tem plate="/Tem plates/m ain_dynam ic_tem plat [...]<head><m eta http-equiv="C ontent-Type" content="text/htm l;
charset=iso-8859-2"><! -- InstanceBeginEditable nam e="docum ent_title_rgn" --><title>picture details</title><! --
InstanceEndEditable --><link rel="stylesheet" href="style.css" type="text/css">[...]------------------------C licking directly
on these URLs should exhibit the issue :(you will probably need to read the HTML
source)http://rs202995.rs.hosteurope.de/artists.php?
artist=1% 20AND% 20SLEEP(21)=0http://rs202995.rs.hosteurope.de/product.php?pic=1% 20AND% 20SLEEP(21)=0
References:
http://www.s ecuriteam.com/s ecurityreviews /5DP0N1P76E.html
http://www.s ecuritydocs .com/library/2651
http://projects .webapps ec.org/SQL-Injection
Alert ID: 84612 Found on: 2017-01-17 Severity: High
CGI Generic SQL Injection (tcp/80)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 7.5
Cvss Score: 7.5
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P
PCI Compliance: Fail
Description:
By providing s pecially crafted parameters to CGIs , Indus Guard was able to get an error from the underlying databas e.
This error s ugges ts that the CGI is affected by a SQL injection vulnerability.
An attacker may exploit this flaw to bypas s authentication, read confidential data, modify the remote databas e, or even
take control of the remote operating s ys tem.
Solution:
Modify the relevant CGIs s o that they properly es cape arguments .
Result:
Using the GET HTTP m ethod, IndusGuard found that :+ The following resources m ay be vulnerable to SQ L
injection :+ The 'cat' param eter of the /listproducts.php C GI :/listproducts.php?cat=convert(varchar,0x7b5d)--------
output --------<! -- InstanceBeginEditable nam e="content_rgn" --><div id="content">Error: You have an error in
your SQ L syntax; check the m anual that corresponds to your MySQ L server version for the right syntax to use
near 'varchar,0x7b5d)' at line 1Warning: m ysql_fetch_array() expects param eter 1 to be resource, b [...]</div>-----
-------------------+ The 'artist' param eter of the /listproducts.php C GI :/listproducts.php?artist=convert(varchar,0x7b5d)---
----- output --------<! -- InstanceBeginEditable nam e="content_rgn" --><div id="content">Error: You have an error in
your SQ L syntax; check the m anual that corresponds to your MySQ L server version for the right syntax to use
near 'varchar,0x7b5d)' at line 1Warning: m ysql_fetch_array() expects param eter 1 to be resource, b [...]</div>-----
Page 13 of 120
Scan Date: 2017-01-17
-------------------+ The 'cat' param eter of the /listproducts.php C GI :/listproducts.php?
cat=convert(varchar,0x7b5d)& artist=1-------- output --------<! -- InstanceBeginEditable nam e="content_rgn" --><div
id="content">Error: You have an error in your SQ L syntax; check the m anual that corresponds to your MySQ L
server version for the right syntax to use near 'varchar,0x7b5d)' at line 1Warning: m ysql_fetch_array() expects
param eter 1 to be resource, b [...]</div>------------------------C licking directly on these URLs should exhibit the issue
:(you will probably need to read the HTML source)http://rs202995.rs.hosteurope.de/listproducts.php?
cat=convert(varchar,0x7b5d)
References:
http://en.wikipedia.org/wiki/SQL_injection
http://www.s ecuriteam.com/s ecurityreviews /5DP0N1P76E.html
http://www.s ecuritydocs .com/library/2651
http://projects .webapps ec.org/SQL-Injection
http://www.owas p.org/index.php/Guide_to_SQL_Injection
Alert ID: 84630 Found on: 2017-01-17 Severity: High
PHP < 5.2.8 Multiple Vulnerabilities (tcp/80)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2008-5814,CVE-2008-5844
Cvss Base: 7.5
Cvss Score: 7.5
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P
PCI Compliance: Fail
Description:
According to its banner, the vers ion of PHP ins talled on the remote hos t is earlier than 5.2.8. As s uch, it is potentially
affected by the following vulnerabilities :
- PHP fails to properly s anitize error mes s ages of arbitrary HTML or s cript code, would code allow for cros s -s ite s cripting
attacks if PHP's 'dis play_errors ' s etting is enabled. (CVE-2008-5814)
- Vers ion 5.2.7 introduced a regres s ion with regard to 'magic_quotes ' functionality due to an incorrect fix to the filter
extens ion. As a res ult, the 'magic_quotes _gpc' s etting remains off even if it is s et to on. (CVE-2008-5844)
Solution:
Upgrade to PHP vers ion 5.2.8 or later.
Result:
Version source : http://rs202995.rs.hosteurope.de/secured/phpinfo.php Installed version : 5.1.6 Fixed version :
5.2.8
References:
http://bugs .php.net/42718
http://www.php.net/releas es /5_2_8.php
Alert ID: 84634 Found on: 2017-01-17 Severity: High
PHP < 5.3.9 Multiple Vulnerabilities (tcp/80)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2011-3379,CVE-2011-
4566,CVE-2011-4885,CVE-2012
Page 14 of 120
Scan Date: 2017-01-17
Cvss Base: 7.5
Cvss Score: 7.5
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P
PCI Compliance: Fail
Description:
According to its banner, the vers ion of PHP ins talled on the remote hos t is older than 5.3.9. As s uch, it may be affected by
the following s ecurity is s ues :
- The 'is _a()' function in PHP 5.3.7 and 5.3.8 triggers a call to '__autoload()'. (CVE-2011-3379)
- It is pos s ible to create a denial of s ervice condition by s ending multiple, s pecially crafted reques ts containing
parameter values that caus e has h collis ions when computing the has h values for s torage in a has h table. (CVE-2011-
4885)
- An integer overflow exis ts in the exif_proces s _IFD_TAG function in exif.c that can allow a remote attacker to read
arbitrary memory locations or caus e a denial of s ervice condition. This vulnerability only affects PHP 5.4.0beta2 on 32-bit
platforms . (CVE-2011-4566)
- Calls to libxs lt are not res tricted via xs ltSetSecurityPrefs (), which could allow an attacker to create or overwrite files ,
res ulting in arbitrary code execution. (CVE-2012-0057)
- An error exis ts in the function 'tidy_diagnos e' that can allow an attacker to caus e the application to dereference a null
pointer. This caus es the application to cras h. (CVE-2012-0781)
- The 'PDORow' implementation contains an error that can caus e application cras hes when interacting with the s es s ion
feature. (CVE-2012-0788)
- An error exis ts in the timezone handling s uch that repeated calls to the function 's trtotime' can allow a denial of s ervice
attack via memory cons umption.
(CVE-2012-0789)
Solution:
Upgrade to PHP vers ion 5.3.9 or later.
Result:
Version source : http://rs202995.rs.hosteurope.de/secured/phpinfo.php Installed version : 5.1.6 Fixed version :
5.3.9
References:
http://xhe.myxwiki.org/xwiki/bin/view/XSLT/Application_PHP5
http://www.php.net/archive/2012.php#id2012-01-11-1
http://archives .neohaps is .com/archives /bugtraq/2012-01/0092.html
https ://bugs .php.net/bug.php?id=55475
https ://bugs .php.net/bug.php?id=55776
https ://bugs .php.net/bug.php?id=53502
http://www.php.net/ChangeLog-5.php#5.3.9
Alert ID: 84636 Found on: 2017-01-17 Severity: High
PHP < 5.3.12 / 5.4.2 CGI Query String Code Execution (tcp/80)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2012-1823
Page 15 of 120
Scan Date: 2017-01-17
Cvss Base: 8.3
Cvss Score: 8.3
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:C/I:P/A:P
PCI Compliance: Fail
Description:
According to its banner, the vers ion of PHP ins talled on the remote hos t is earlier than 5.3.12 / 5.4.2, and as s uch is
potentially affected by a remote code execution and information dis clos ure vulnerability.
An error in the file 's api/cgi/cgi_main.c' can allow a remote attacker to obtain PHP s ource code from the web s erver or to
potentially execute arbitrary code. In vulnerable configurations , PHP treats certain query s tring parameters as command
line arguments including s witches s uch as '-s ', '-d', and '-c'.
Note that this vulnerability is exploitable only when PHP is us ed in CGI-bas ed configurations . Apache with 'mod_php' is not
an exploitable configuration.
Solution:
Upgrade to PHP vers ion 5.3.12 / 5.4.2 or later. A 'mod_rewrite' workaround is available as well.
Result:
Version source : X-Powered-By: PHP/5.3.10-1~lucid+2uwsgi2 Installed version : 5.3.10-1~lucid+2uwsgi2 Fixed
version : 5.3.12 / 5.4.2
References:
http://eindbazen.net/2012/05/php-cgi-advis ory-cve-2012-1823/
https ://bugs .php.net/bug.php?id=61910
http://www.php.net/archive/2012.php#id2012-05-03-1
http://www.php.net/ChangeLog-5.php#5.3.12
http://www.php.net/ChangeLog-5.php#5.4.2
Alert ID: 84638 Found on: 2017-01-17 Severity: High
PHP 5.x < 5.2.2 Information Disclosure (tcp/80)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2007-1649
Cvss Base: 7.8
Cvss Score: 7.8
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:C/I:N/A:N
PCI Compliance: Fail
Description:
According to its banner, the vers ion of PHP 5.x ins talled on the remote hos t is older than 5.2.2. An attacker may read
s ome heap memory by proces s ing 'S:' s erialized data.
Solution:
Upgrade to PHP vers ion 5.2.2 or later.
Result:
Version source : http://rs202995.rs.hosteurope.de/secured/phpinfo.php Installed version : 5.1.6 Fixed version :
5.2.2
References:
http://www.php.net/releas es /5_2_2.php
Page 16 of 120
Scan Date: 2017-01-17
Alert ID: 84639 Found on: 2017-01-17 Severity: High
PHP 5.3.x < 5.3.27 Multiple Vulnerabilities (tcp/80)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2013-4113
Cvss Base: 9.3
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C
Description:
According to its banner, the vers ion of PHP 5.3.x ins talled on the remote hos t is prior to 5.3.27. It is , therefore, potentially
affected by the following vulnerabilities :
- A buffer overflow error exis ts in the function '_pdo_pgs ql_error'. (Bug #64949)
- A heap corruption error exis ts in numerous functions in the file 'ext/xml/xml.c'. (CVE-2013-4113 / Bug #65236)
Note that this check does not attempt to exploit thes e vulnerabilities , but ins tead, relies only on PHP's s elf-reported
vers ion number.
Solution:
Apply the vendor patch or upgrade to PHP vers ion 5.3.27 or later.
Result:
Version source : X-Powered-By: PHP/5.3.10-1~lucid+2uwsgi2 Installed version : 5.3.10-1~lucid+2uwsgi2 Fixed
version : 5.3.27
References:
http://bugs .php.net/64949
http://bugs .php.net/65236
http://www.php.net/ChangeLog-5.php#5.3.27
Alert ID: 84641 Found on: 2017-01-17 Severity: High
PHP 5.3.x < 5.3.14 Multiple Vulnerabilities (tcp/80)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2012-2143,CVE-2012-
2386,CVE-2012-3450
Cvss Base: 8.5
Cvss Score: 8.5
Cvss Vector: CVSS2#AV:N/AC:M/Au:S/C:C/I:C/A:C
PCI Compliance: Fail
Description:
According to its banner, the vers ion of PHP ins talled on the remote hos t is 5.3.x earlier than 5.3.14, and as s uch is
potentially affected the following vulnerabilities :
- An integer overflow error exis ts in the function 'phar_pars e_tarfile' in the file 'ext/phar/tar.c'. This error can lead to a
heap-bas ed buffer overflow when handling a malicious ly crafted TAR file. Arbitrary code execution is pos s ible due to this
error. (CVE-2012-2386)
- A weaknes s exis ts in the 'crypt' function related to the DES implementation that can allow brute force attacks . (CVE-
2012-2143)
- Several des ign errors involving the incorrect pars ing of PHP PDO prepared s tatements could lead to dis clos ure of
s ens itive information or denial of s ervice. (CVE-2012-3450)
Page 17 of 120
Scan Date: 2017-01-17
Solution:
Upgrade to PHP vers ion 5.3.14 or later.
Result:
Version source : X-Powered-By: PHP/5.3.10-1~lucid+2uwsgi2 Installed version : 5.3.10-1~lucid+2uwsgi2 Fixed
version : 5.3.14
References:
http://www.nes s us .org/u?6adf7abc
https ://bugs .php.net/bug.php?id=61755
http://www.php.net/ChangeLog-5.php#5.3.14
http://www.nes s us .org/u?99140286
Alert ID: 84642 Found on: 2017-01-17 Severity: High
PHP < 5.2.6 Multiple Vulnerabilities (tcp/80)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2007-4850,CVE-2007-
6039,CVE-2008-0599,CVE-2008
Cvss Base: 7.5
Cvss Score: 7.5
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P
PCI Compliance: Fail
Description:
According to its banner, the vers ion of PHP ins talled on the remote hos t is older than 5.2.6. Such vers ions may be
affected by the following is s ues :
- A s tack buffer overflow in Fas tCGI SAPI.
- An integer overflow in printf().
- An s ecurity is s ue aris ing from improper calculation of the length of PATH_TRANSLATED in cgi_main.c.
- A s afe_mode bypas s in cURL.
- Incomplete handling of multibyte chars ins ide es capes hellcmd().
- Is s ues in the bundled PCRE fixed by vers ion 7.6.
Solution:
Upgrade to PHP vers ion 5.2.6 or later.
Result:
Version source : http://rs202995.rs.hosteurope.de/secured/phpinfo.php Installed version : 5.1.6 Fixed version :
5.2.6
References:
http://archives .neohaps is .com/archives /bugtraq/2008-03/0321.html
http://archives .neohaps is .com/archives /fulldis clos ure/2008-05/0103.html
http://archives .neohaps is .com/archives /fulldis clos ure/2008-05/0107.html
http://www.php.net/releas es /5_2_6.php
Page 18 of 120
Scan Date: 2017-01-17
Alert ID: 84645 Found on: 2017-01-17 Severity: High
PHP < 5.3.11 Multiple Vulnerabilities (tcp/80)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2011-1398,CVE-2012-
0831,CVE-2012-1172
Cvss Base: 7.5
Cvss Score: 7.5
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P
PCI Compliance: Fail
Description:
According to its banner, the vers ion of PHP ins talled on the remote hos t is earlier than 5.3.11, and as s uch is potentially
affected by multiple vulnerabilities :
- During the import of environment variables , temporary changes to the 'magic_quotes _gpc' directive are not handled
properly. This can lower the difficulty for SQL injection attacks . (CVE-2012-0831)
- The '$_FILES' variable can be corrupted becaus e the names of uploaded files are not properly validated.
(CVE-2012-1172)
- The 'open_bas edir' directive is not properly handled by the functions 'readline_write_his tory' and
'readline_read_his tory'.
- The 'header()' function does not detect multi-line headers with a CR. (Bug #60227 / CVE-2011-1398)
Solution:
Upgrade to PHP vers ion 5.3.11 or later.
Result:
Version source : X-Powered-By: PHP/5.3.10-1~lucid+2uwsgi2 Installed version : 5.3.10-1~lucid+2uwsgi2 Fixed
version : 5.3.11
References:
http://www.nes s us .org/u?e81d4026
https ://bugs .php.net/bug.php?id=61043
https ://bugs .php.net/bug.php?id=54374
https ://bugs .php.net/bug.php?id=60227
http://marc.info/?l=os s -s ecurity&m=134626481806571&w=2
http://www.php.net/archive/2012.php#id2012-04-26-1
http://www.php.net/ChangeLog-5.php#5.3.11
Alert ID: 84646 Found on: 2017-01-17 Severity: High
PHP < 4.4.7 / 5.2.2 Multiple Vulnerabilities (tcp/80)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2007-0455,CVE-2007-
0911,CVE-2007-1001,CVE-2007
Cvss Base: 7.5
Cvss Score: 7.5
Page 19 of 120
Scan Date: 2017-01-17
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P
PCI Compliance: Fail
Description:
According to its banner, the vers ion of PHP ins talled on the remote hos t is older than 4.4.7 / 5.2.2. Such vers ions may be
affected by s everal is s ues , including buffer overflows in the GD library.
Solution:
Upgrade to PHP 4.4.7 / 5.2.2 or later.
Result:
Version source : http://rs202995.rs.hosteurope.de/secured/phpinfo.php, Installed version : 5.1.6 Fixed version :
4.4.7 / 5.2.2
References:
http://www.php.net/releas es /4_4_7.php
http://www.php.net/releas es /5_2_2.php
Alert ID: 84649 Found on: 2017-01-17 Severity: High
PHP 5.3.x < 5.3.26 Multiple Vulnerabilities (tcp/80)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2013-2110
Cvss Base: 7.5
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P
Description:
According to its banner, the vers ion of PHP 5.3.x ins talled on the remote hos t is prior to 5.3.26. It is , therefore, potentially
affected by the following vulnerabilities :
- An error exis ts in the function 'php_quot_print_encode' in the file 'ext/s tandard/quot_print.c' that could allow a heap-
bas ed buffer overflow when attempting to pars e certain s trings (Bug #64879)
- An integer overflow error exis ts related to the value of 'JEWISH_SDN_MAX' in the file 'ext/calendar/jewis h.c' that could
allow denial of s ervice attacks . (Bug #64895)
Note that this check does not attempt to exploit thes e vulnerabilities , but ins tead, relies only on PHP's s elf-reported
vers ion number.
Solution:
Apply the vendor patch or upgrade to PHP vers ion 5.3.26 or later.
Result:
Version source : X-Powered-By: PHP/5.3.10-1~lucid+2uwsgi2 Installed version : 5.3.10-1~lucid+2uwsgi2 Fixed
version : 5.3.26
References:
http://www.Indus Guard.org/u?60cbc5f0
http://www.Indus Guard.org/u?8456482e
http://www.php.net/ChangeLog-5.php#5.3.26
Alert ID: 84652 Found on: 2017-01-17 Severity: High
PHP 5 < 5.2.7 Multiple Vulnerabilities (tcp/80)
Page 20 of 120
Scan Date: 2017-01-17
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2008-2371,CVE-2008-
2665,CVE-2008-2666,CVE-2008
Cvss Base: 7.5
Cvss Score: 7.5
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P
PCI Compliance: Fail
Description:
According to its banner, the vers ion of PHP ins talled on the remote hos t is older than 5.2.7. Such vers ions may be
affected by s everal s ecurity is s ues :
- File truncation can occur when calling 'dba_replace()' with an invalid argument.
- There is a buffer overflow in the bundled PCRE library fixed by 7.8. (CVE-2008-2371)
- A buffer overflow in the 'imageloadfont()' function in 'ext/gd/gd.c' can be triggered when a s pecially crafted font is given.
(CVE-2008-3658)
- There is a buffer overflow in PHP's internal function 'memns tr()', which is expos ed to us ers pace as 'explode()'. (CVE-
2008-3659)
- When us ed as a Fas tCGI module, PHP s egfaults when opening a file whos e name contains two dots (eg, 'file..php'). (CVE-
2008-3660)
- Multiple directory travers al vulnerabilities in functions s uch as 'pos ix_acces s ()', 'chdir()', 'ftok()' may allow a remote
attacker to bypas s 's afe_mode' res trictions . (CVE-2008-2665 and CVE-2008-2666).
- A buffer overflow may be triggered when proces s ing long mes s age headers in 'php_imap.c' due to us e of an obs olete
API call. (CVE-2008-2829)
- A heap-bas ed buffer overflow may be triggered via a call to 'mb_check_encoding()', part of the 'mbs tring' extens ion.
(CVE-2008-5557)
- Mis s ing initialization of 'BG(page_uid)' and 'BG(page_gid)' when PHP is us ed as an Apache module may allow for
bypas s ing s ecurity res triction due to SAPI 'php_getuid()' overloading. (CVE-2008-5624)
- Incorrect 'php_value' order for Apache configuration may allow bypas s ing PHP's 's afe_mode' s etting.
(CVE-2008-5625)
- The ZipArchive:extractTo() method in the ZipArchive extens ion fails to filter directory travers al s equences from file
names . (CVE-2008-5658)
Solution:
Upgrade to PHP vers ion 5.2.8 or later.
Note that 5.2.7 was been removed from dis tribution becaus e of a regres s ion in that vers ion that res ults in the
'magic_quotes _gpc' s etting remaining off even if it was s et to on.
Result:
Version source : http://rs202995.rs.hosteurope.de/secured/phpinfo.php Installed version : 5.1.6 Fixed version :
5.2.7
References:
http://s ecurityreas on.com/achievement_s ecurityalert/57
http://s ecurityreas on.com/achievement_s ecurityalert/58
http://s ecurityreas on.com/achievement_s ecurityalert/59
http://www.s ektioneins .de/advis ories /SE-2008-06.txt
Page 21 of 120
Scan Date: 2017-01-17
http://archives .neohaps is .com/archives /fulldis clos ure/2008-06/0238.html
http://archives .neohaps is .com/archives /fulldis clos ure/2008-06/0239.html
http://www.openwall.com/lis ts /os s -s ecurity/2008/08/08/2
http://www.openwall.com/lis ts /os s -s ecurity/2008/08/13/8
http://archives .neohaps is .com/archives /fulldis clos ure/2008-11/0433.html
http://archives .neohaps is .com/archives /fulldis clos ure/2008-12/0089.html
http://bugs .php.net/bug.php?id=42862
http://bugs .php.net/bug.php?id=45151
http://bugs .php.net/bug.php?id=45722
http://www.php.net/releas es /5_2_7.php
http://www.php.net/ChangeLog-5.php#5.2.7
Alert ID: 84654 Found on: 2017-01-17 Severity: High
PHP < 5.2.11 Multiple Vulnerabilities (tcp/80)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2009-3291,CVE-2009-
3292,CVE-2009-3293,CVE-2009
Cvss Base: 7.5
Cvss Score: 7.5
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P
PCI Compliance: Fail
Description:
According to its banner, the vers ion of PHP ins talled on the remote hos t is older than 5.2.11. Such vers ions may be
affected by s everal s ecurity is s ues :
- An uns pecified error occurs in certificate validation ins ide 'php_opens s l_apply_verification_policy'.
- An uns pecified input validation vulnerability affects the color index in 'imagecolortrans parent()'.
- An uns pecified input validation vulnerability affects exif proces s ing.
- Calling 'popen()' with an invalid mode can caus e a cras h under Windows . (Bug #44683)
- An integer overflow in 'xml_utf8_decode()' can make it eas ier to bypas s cros s -s ite s cripting and SQL injection
protection mechanis ms us ing a s pecially crafted s tring with a long UTF-8 encoding. (Bug #49687)
- 'proc_open()' can bypas s 's afe_mode_protected_env_vars '.
(Bug #49026)
Solution:
Upgrade to PHP vers ion 5.2.11 or later.
Result:
Version source : http://rs202995.rs.hosteurope.de/secured/phpinfo.php Installed version : 5.1.6 Fixed version :
5.2.11
Page 22 of 120
Scan Date: 2017-01-17
References:
http://www.php.net/ChangeLog-5.php#5.2.11
http://www.php.net/releas es /5_2_11.php
http://news .php.net/php.internals /45597
http://www.php.net/ChangeLog-5.php#5.2.11
Alert ID: 84655 Found on: 2017-01-17 Severity: High
PHP 5.3.x < 5.3.29 Multiple Vulnerabilities (tcp/80)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2013-6712,CVE-2014-
0207,CVE-2014-0237,CVE-2014
Cvss Base: 7.5
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P
Description:
According to its banner, the vers ion of PHP ins talled on the remote hos t is 5.3.x prior to 5.3.29. It is , therefore, affected by
the following vulnerabilities :
- A heap-bas ed buffer overflow error exis ts in the file 'ext/date/lib/pars e_is o_intervals .c' related to handling DateInterval
objects that allows denial of s ervice attacks . (CVE-2013-6712)
- A boundary checking error exis ts related to the Fileinfo extens ion, Compos ite Document Format (CDF) handling, and the
function 'cdf_read_s hort_s ector'. (CVE-2014-0207)
- A flaw exis ts with the 'cdf_unpack_s ummary_info()' function within 's rc/cdf.c' where multiple file_printf calls occur when
handling s pecially crafted CDF files .
This could allow a context dependent attacker to cras h the web application us ing PHP. (CVE-2014-0237)
- A flaw exis ts with the 'cdf_read_property_info()' function within 's rc/cdf.c' where an infinite loop occurs when handling
s pecially crafted CDF files . This could allow a context dependent attacker to cras h the web application us ing PHP. (CVE-
2014-0238)
- A type-confus ion error exis ts related to the Standard PHP Library (SPL) extens ion and the function 'uns erialize'. (CVE-
2014-3515)
- An error exis ts related to configuration s cripts and temporary file handling that could allow ins ecure file us age. (CVE-
2014-3981)
- A heap-bas ed buffer overflow error exis ts related to the function 'dns _get_record' that could allow execution of
arbitrary code. (CVE-2014-4049)
- An out-of-bounds read exis ts in printf. (Bug #67249)
Note that Indus Guard has not attempted to exploit thes e is s ues , but has ins tead relied only on the application's s elf-
reported vers ion number.
Additionally, note that vers ion 5.3.29 marks the end of s upport for the PHP 5.3.x branch.
Solution:
Upgrade to PHP vers ion 5.3.29 or later.
Result:
Version source : X-Powered-By: PHP/5.3.10-1~lucid+2uwsgi2 Installed version : 5.3.10-1~lucid+2uwsgi2 Fixed
version : 5.3.29
Page 23 of 120
Scan Date: 2017-01-17
References:
http://php.net/archive/2014.php#id2014-08-14-1
http://www.php.net/ChangeLog-5.php#5.3.29
Alert ID: 84658 Found on: 2017-01-17 Severity: High
PHP 5.x < 5.2 Multiple Vulnerabilities (tcp/80)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2006-1015,CVE-2006-
1549,CVE-2006-2660,CVE-2006
Cvss Base: 7.5
Cvss Score: 7.5
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P
PCI Compliance: Fail
Description:
According to its banner, the vers ion of PHP 5.x ins talled on the remote hos t is older than 5.2. Such vers ions may be
affected by s everal buffer overflows .
To exploit thes e is s ues , an attacker would need the ability to upload an arbitrary PHP s cript on the remote s erver or to
manipulate s everal variables proces s ed by s ome PHP functions s uch as 'htmlentities ().'
Solution:
Upgrade to PHP vers ion 5.2.0 or later.
Result:
Version source : http://rs202995.rs.hosteurope.de/secured/phpinfo.php Installed version : 5.1.6 Fixed version : 5.2
References:
http://www.hardened-php.net/advis ory_092006.133.html
http://www.php.net/releas es /5_2_0.php
Alert ID: 84659 Found on: 2017-01-17 Severity: High
PHP 5.3.x < 5.3.13 CGI Query String Code Execution (tcp/80)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2012-2311,CVE-2012-
2335,CVE-2012-2336
Cvss Base: 8.3
Cvss Score: 8.3
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:C/I:P/A:P
PCI Compliance: Fail
Description:
According to its banner, the vers ion of PHP ins talled on the remote hos t is 5.3.x earlier than 5.3.13 and, as s uch, is
potentially affected by a remote code execution and information dis clos ure vulnerability.
The fix for CVE-2012-1823 does not completely correct the CGI query vulnerability. Dis clos ure of PHP s ource code and
code execution via query parameters are s till pos s ible.
Note that this vulnerability is exploitable only when PHP is us ed in CGI-bas ed configurations . Apache with 'mod_php' is not
an exploitable configuration.
Solution:
Page 24 of 120
Scan Date: 2017-01-17
Upgrade to PHP vers ion 5.3.13 or later. A 'mod_rewrite' workaround is available as well.
Result:
Version source : X-Powered-By: PHP/5.3.10-1~lucid+2uwsgi2 Installed version : 5.3.10-1~lucid+2uwsgi2 Fixed
version : 5.3.13
References:
http://eindbazen.net/2012/05/php-cgi-advis ory-cve-2012-1823/
https ://bugs .php.net/bug.php?id=61910
http://www.php.net/archive/2012.php#id2012-05-08-1
http://www.php.net/ChangeLog-5.php#5.3.13
Alert ID: 84661 Found on: 2017-01-17 Severity: High
PHP < 5.2.1 Multiple Vulnerabilities (tcp/80)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2006-6383,CVE-2007-
0905,CVE-2007-0906,CVE-2007
Cvss Base: 7.5
Cvss Score: 7.5
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P
PCI Compliance: Fail
Description:
According to its banner, the vers ion of PHP ins talled on the remote hos t is older than 5.2.1. Such vers ions may be
affected by s everal is s ues , including buffer overflows , format s tring vulnerabilities , arbitrary code execution,
's afe_mode' and 'open_bas edir' bypas s es , and clobbering of s uper-globals .
Solution:
Upgrade to PHP vers ion 5.2.1 or later.
Result:
Version source : http://rs202995.rs.hosteurope.de/secured/phpinfo.php Installed version : 5.1.6 Fixed version :
5.2.1
References:
http://www.php.net/releas es /5_2_1.php
Alert ID: 84670 Found on: 2017-01-17 Severity: High
nginx < 1.4.4 / 1.5.7 ngx_parse_http Security Bypass (tcp/80)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 7.5
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P
Description:
According to the s elf-reported vers ion in the Server res pons e header, the ins talled vers ion of nginx is greater than 0.8.41
but prior to 1.4.4 / 1.5.7. It is , therefore, affected by a s ecurity bypas s vulnerability in 'ngx_http_pars e.c' when a file with a
s pace at the end of the URI is reques ted.
Solution:
Either apply the patch manually or upgrade to nginx 1.4.4 / 1.5.7 or later.
Result:
Page 25 of 120
Scan Date: 2017-01-17
Version source : nginx/1.4.1 Installed version : 1.4.1 Fixed version : 1.4.4 / 1.5.7
References:
http://nginx.org/en/s ecurity_advis ories .html
http://mailman.nginx.org/pipermail/nginx-announce/2013/000125.html
http://nginx.org/en/CHANGES-1.4
http://nginx.org/en/CHANGES
Alert ID: 84692 Found on: 2017-01-17 Severity: High
OpenSSH < 6.9 Multiple Vulnerabilities (tcp/22)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 8.5
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:C
Description:
According to its banner, the vers ion of OpenSSH running on the remote hos t is prior to 6.9. It is , therefore, affected by the
following vulnerabilities :
- A flaw exis ts within the x11_open_helper() function in the 'channels .c' file that allows connections to be permitted after
'ForwardX11Timeout' has expired. A remote attacker can exploit this to bypas s timeout checks and XSECURITY
res trictions . (CVE-2015-5352)
- Various is s ues were addres s ed by fixing the weaknes s in agent locking by increas ing the failure delay, s toring the
s alted has h of the pas s word, and us ing a timing-s afe comparis on function.
- An out-of-bounds read error exis ts when handling incorrect pattern lengths . A remote attacker can exploit this to caus e
a denial of s ervice or dis clos e s ens itive information in the memory.
- An out-of-bounds read error exis ts when pars ing the 'Es capeChar' configuration option.
Solution:
Upgrade to OpenSSH 6.9 or later.
Result:
Version source : SSH-2.0-O penSSH_5.3p1 Debian-3ubuntu7.1 Installed version : 5.3p1 Fixed version : 6.9
References:
http://www.opens s h.com/txt/releas e-6.9
http://www.Indus Guard.org/u?725c4682
Alert ID: 84699 Found on: 2017-01-17 Severity: High
ProFTPD < 1.3.3g / 1.3.4 Response Pool Use-After-Free Code Execution (tcp/21)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2011-4130
Cvss Base: 9.0
Cvss Score: 9.0
Cvss Vector: CVSS2#AV:N/AC:L/Au:S/C:C/I:C/A:C
PCI Compliance: Fail
Description:
Page 26 of 120
Scan Date: 2017-01-17
The remote hos t is us ing ProFTPD, a free FTP s erver for Unix and Linux.
According to its banner, the vers ion of ProFTPD ins talled on the remote hos t is earlier than 1.3.3g or 1.3.4. As s uch, it is
potentially affected by a code execution vulnerability due to how the s erver manages the res pons e pool that is us ed to
s end res pons es from the s erver to the client. A remote, authenticated attacker could could leverage this is s ue to
execute arbitrary code on the remote hos t, s ubject to the privileges of the us er running the affected application.
Note that Indus Guard did not actually tes t for the flaw but ins tead has relied on the vers ion in ProFTPD's banner.
Solution:
Upgrade to ProFTPD vers ion 1.3.3g / 1.3.4 or later.
Result:
Version source : 220 ProFTPD 1.3.3e Server (ProFTPD) [176.28.50.165] Installed version : 1.3.3e Fixed version :
1.3.3g / 1.3.4
References:
http://www.zerodayinitiative.com/advis ories /ZDI-11-328/
http://archives .neohaps is .com/archives /fulldis clos ure/2011-11/0175.html
http://bugs .proftpd.org/s how_bug.cgi?id=3711
http://www.proftpd.org/docs /NEWS-1.3.3g
http://www.proftpd.org/docs /NEWS-1.3.4
Alert ID: 84504 Found on: 2017-01-17 Severity: Medium
SSL Certificate with Wrong Hostname (tcp/995)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 5.0
Cvss Score: 5.0
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:N/I:P/A:N
PCI Compliance: Fail
Description:
The commonName (CN) of the SSL certificate pres ented on this s ervice is for a different machine.
Solution:
Purchas e or generate a proper certificate for this s ervice.
Result:
The identity known by IndusGuard is : rs202995.rs.hosteurope.deThe C om m on Nam e in the certificate is :
Parallels Panel
Alert ID: 84507 Found on: 2017-01-17 Severity: Medium
SSLv3 Padding Oracle On Downgraded Legacy Encryption Vulnerability (POODLE) (tcp/995)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2014-3566
Cvss Base: 4.3
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N
Description:
The remote hos t is affected by a man-in-the-middle (MitM) information dis clos ure vulnerability known as POODLE. The
vulnerability is due to the way SSL 3.0 handles padding bytes when decrypting mes s ages encrypted us ing block ciphers
Page 27 of 120
Scan Date: 2017-01-17
in cipher block chaining (CBC) mode. A MitM attacker can decrypt a s elected byte of a cipher text in as few as 256 tries if
they are able to force a victim application to repeatedly s end the s ame data over newly created SSL 3.0 connections .
As long as a client and s ervice both s upport SSLv3, a connection can be 'rolled back' to SSLv3, even if TLSv1 or newer is
s upported by the client and s ervice.
The TLS Fallback SCSV extens ion prevents 'vers ion rollback' attacks without impacting legacy clients ; however, it can
only protect connections when the client and s ervice s upport the extens ion. Sites that cannot dis able SSLv3 immediately
s hould enable this extens ion.
This is a vulnerability in the SSLv3 s pecification, not in a particular SSL implementation. Dis abling SSLv3 is the only way to
completely mitigate the vulnerability.
Solution:
Dis able SSLv3.
Services that mus t s upport SSLv3 s hould enable the TLS Fallback SCSV extens ion until SSLv3 can be dis abled.
Result:
IndusGuard determ ined that the rem ote server supports SSLv3 with at least one C BC cipher suite, indicating that
this server is vulnerable.It appears that TLSv1 or newer is supported on the server. However, the Fallback SC SV
m echanism is not supported, allowing connections to be "rolled back" to SSLv3.
References:
https ://www.imperialviolet.org/2014/10/14/poodle.html
https ://www.opens s l.org/~bodo/s s l-poodle.pdf
https ://tools .ietf.org/html/draft-ietf-tls -downgrade-s cs v-00
Alert ID: 84508 Found on: 2017-01-17 Severity: Medium
SSL Medium Strength Cipher Suites Supported (tcp/995)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 4.3
Cvss Score: 4.3
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N
PCI Compliance: Fail
Description:
The remote hos t s upports the us e of SSL ciphers that offer medium s trength encryption, which we currently regard as
thos e with key lengths at leas t 56 bits and les s than 112 bits .
Note: This is cons iderably eas ier to exploit if the attacker is on the s ame phys ical network.
Solution:
Reconfigure the affected application if pos s ible to avoid us e of medium s trength ciphers .
Result:
Here is the list of m edium strength SSL ciphers supported by the rem ote server : Medium Strength C iphers (> 64-
bit and < 112-bit key) SSLv2 DES-C BC 3-MD5 Kx=RSA Au=RSA Enc=3DES-C BC (168) Mac=MD5 TLSv1 DES-C BC 3-
SHA Kx=RSA Au=RSA Enc=3DES-C BC (168) Mac=SHA1 The fields above are : {O penSSL ciphernam e} Kx={key
exchange} Au={authentication} Enc={sym m etric encryption m ethod} Mac={m essage authentication code}
{export flag}
Alert ID: 84509 Found on: 2017-01-17 Severity: Medium
SSL DROWN Attack Vulnerability (Decrypting RSA with Obsolete and Weakened eNcryption) (tcp/995)
Page 28 of 120
Scan Date: 2017-01-17
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2016-0800
Cvss Base: 4.0
Cvss Vector: CVSS2#AV:N/AC:H/Au:N/C:P/I:P/A:N
Description:
The remote hos t s upports SSLv2 and therefore may be affected by a vulnerability that allows a cros s -protocol
Bleichenbacher padding oracle attack known as DROWN (Decrypting RSA with Obs olete and Weakened eNcryption). This
vulnerability exis ts due to a flaw in the Secure Sockets Layer Vers ion 2 (SSLv2) implementation, and it allows captured
TLS traffic to be decrypted. A man-in-the-middle attacker can exploit this to decrypt the TLS connection by utilizing
previous ly captured traffic and weak cryptography along with a s eries of s pecially crafted connections to an SSLv2
s erver that us es the s ame private key.
Solution:
Dis able SSLv2 and export grade cryptography cipher s uites . Ens ure that private keys are not us ed anywhere with s erver
s oftware that s upports SSLv2 connections .
Result:
The rem ote host is affected by SSL DRO WN and supports the followingvulnerable cipher suites : Low Strength
C iphers (<= 64-bit key) SSLv2 DES-C BC -MD5 Kx=RSA Au=RSA Enc=DES-C BC (56) Mac=MD5 EXP-RC 2-C BC -MD5
Kx=RSA(512) Au=RSA Enc=RC 2-C BC (40) Mac=MD5 export EXP-RC 4-MD5 Kx=RSA(512) Au=RSA Enc=RC 4(40)
Mac=MD5 export High Strength C iphers (>= 112-bit key) SSLv2 RC 4-MD5 Kx=RSA Au=RSA Enc=RC 4(128)
Mac=MD5 The fields above are : {O penSSL ciphernam e} Kx={key exchange} Au={authentication}
Enc={sym m etric encryption m ethod} Mac={m essage authentication code} {export flag}
References:
https ://drownattack.com/
https ://drownattack.com/drown-attack-paper.pdf
Alert ID: 84511 Found on: 2017-01-17 Severity: Medium
SSL Weak Cipher Suites Supported (tcp/995)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 4.3
Cvss Score: 4.3
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N
PCI Compliance: Fail
Description:
The remote hos t s upports the us e of SSL ciphers that offer either weak encryption or no encryption at all.
Note: This is cons iderably eas ier to exploit if the attacker is on the s ame phys ical network.
Solution:
Reconfigure the affected application if pos s ible to avoid us e of weak ciphers .
Result:
Here is the list of weak SSL ciphers supported by the rem ote server : Low Strength C iphers (<= 64-bit key) SSLv2
DES-C BC -MD5 Kx=RSA Au=RSA Enc=DES-C BC (56) Mac=MD5 EXP-RC 2-C BC -MD5 Kx=RSA(512) Au=RSA Enc=RC 2-
C BC (40) Mac=MD5 export EXP-RC 4-MD5 Kx=RSA(512) Au=RSA Enc=RC 4(40) Mac=MD5 export TLSv1 EXP-DES-
C BC -SHA Kx=RSA(512) Au=RSA Enc=DES-C BC (40) Mac=SHA1 export EXP-RC 2-C BC -MD5 Kx=RSA(512) Au=RSA
Enc=RC 2-C BC (40) Mac=MD5 export EXP-RC 4-MD5 Kx=RSA(512) Au=RSA Enc=RC 4(40) Mac=MD5 export DES-
C BC -SHA Kx=RSA Au=RSA Enc=DES-C BC (56) Mac=SHA1 The fields above are : {O penSSL ciphernam e} Kx={key
exchange} Au={authentication} Enc={sym m etric encryption m ethod} Mac={m essage authentication code}
{export flag}
References:
http://www.opens s l.org/docs /apps /ciphers .html
Page 29 of 120
Scan Date: 2017-01-17
Alert ID: 84512 Found on: 2017-01-17 Severity: Medium
SSL Version 2 (v2) Protocol Detection (tcp/995)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2005-2969
Cvss Base: 5.0
Cvss Score: 5.0
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N
PCI Compliance: Fail
Description:
The remote s ervice accepts connections encrypted us ing SSL 2.0, which reportedly s uffers from s everal cryptographic
flaws and has been deprecated for s everal years . An attacker may be able to exploit thes e is s ues to conduct man-in-
the-middle attacks or decrypt communications between the affected s ervice and clients .
Solution:
Cons ult the application's documentation to dis able SSL 2.0 and us e SSL 3.0, TLS 1.0, or higher ins tead.
Result:
- SSLv2 is enabled and the server supports at least one cipher.- SSLv3 is enabled and the server supports at least
one cipher.
References:
http://www.s chneier.com/paper-s s l.pdf
http://s upport.micros oft.com/kb/187498
http://www.linux4beginners .info/node/dis able-s s lv2
Alert ID: 84513 Found on: 2017-01-17 Severity: Medium
SSL/TLS EXPORT_RSA <= 512-bit Cipher Suites Supported (FREAK) (tcp/995)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 5.0
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:N/I:P/A:N
Description:
The remote hos t s upports EXPORT_RSA cipher s uites with keys les s than or equal to 512 bits . An attacker can factor a
512-bit RSA modulus in a s hort amount of time.
A man-in-the middle attacker may be able to downgrade the s es s ion to us e EXPORT_RSA cipher s uites (e.g. CVE-2015-
0204). Thus , it is recommended to remove s upport for weak cipher s uites .
Solution:
Reconfigure the s ervice to remove s upport for EXPORT_RSA cipher s uites .
Result:
EXPO RT_RSA cipher suites supported by the rem ote server : Low Strength C iphers (<= 64-bit key) TLSv1 EXP-DES-
C BC -SHA Kx=RSA(512) Au=RSA Enc=DES-C BC (40) Mac=SHA1 export EXP-RC 2-C BC -MD5 Kx=RSA(512) Au=RSA
Enc=RC 2-C BC (40) Mac=MD5 export EXP-RC 4-MD5 Kx=RSA(512) Au=RSA Enc=RC 4(40) Mac=MD5 export The
fields above are : {O penSSL ciphernam e} Kx={key exchange} Au={authentication} Enc={sym m etric
encryption m ethod} Mac={m essage authentication code} {export flag}
References:
https ://www.s macktls .com/#freak
Page 30 of 120
Scan Date: 2017-01-17
https ://www.opens s l.org/news /s ecadv_20150108.txt
http://www.Indus Guard.org/u?b78da2c4
Alert ID: 84515 Found on: 2017-01-17 Severity: Medium
OpenSSL 'ChangeCipherSpec' MiTM Vulnerability (tcp/995)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2014-0224
Cvss Base: 5.8
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:P/I:P/A:N
Description:
The OpenSSL s ervice on the remote hos t is vulnerable to a man-in-the-middle (MiTM) attack, bas ed on its res pons e to
two cons ecutive 'ChangeCipherSpec' mes s ages during the incorrect phas e of an SSL/TLS hands hake.
This flaw could allow a MiTM attacker to decrypt or forge SSL mes s ages by telling the s ervice to begin encrypted
communications before key material has been exchanged, which caus es predictable keys to be us ed to s ecure future
traffic.
Solution:
OpenSSL 0.9.8 SSL/TLS us ers (client and/or s erver) s hould upgrade to 0.9.8za. OpenSSL 1.0.0 SSL/TLS us ers (client and/or
s erver) s hould upgrade to 1.0.0m. OpenSSL 1.0.1 SSL/TLS us ers (client and/or s erver) s hould upgrade to 1.0.1h.
Result:
The rem ote service accepted an SSL C hangeC ipherSpec m essage at an incorrect point in the handshake
leading to weak keys being used, and then attem pted to decrypt an SSL record using those weak keys.This
check detects unpatched O penSSL 1.0.1, 1.0.0, and 0.9.8 services. O nly 1.0.1 has been shown to be exploitable;
however, O penSSL 1.0.0 and 0.9.8 have received sim ilar patches and users of these versions have been
advised to upgrade as a precaution.
References:
http://www.Indus Guard.org/u?d5709faa
https ://www.imperialviolet.org/2014/06/05/earlyccs .html
https ://www.opens s l.org/news /s ecadv_20140605.txt
Alert ID: 84516 Found on: 2017-01-17 Severity: Medium
SSL/TLS Protocol Initialization Vector Implementation Information Disclosure Vulnerability (tcp/995)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2011-3389
Cvss Base: 4.3
Cvss Score: 4.3
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N
PCI Compliance: Fail
Description:
A vulnerability exis ts in SSL 3.0 and TLS 1.0 that could allow information dis clos ure if an attacker intercepts encrypted
traffic s erved from an affected s ys tem.
TLS 1.1, TLS 1.2, and all cipher s uites that do not us e CBC mode are not affected.
This s cript tries to es tablis h an SSL/TLS remote connection us ing an affected SSL vers ion and cipher s uite, and then
Page 31 of 120
Scan Date: 2017-01-17
s olicits return data.
If returned application data is not fragmented with an empty or one-byte record, it is likely vulnerable.
OpenSSL us es empty fragments as a countermeas ure unles s the 'SSL_OP_DONT_INSERT_EMPTY_FRAGMENTS' option is
s pecified when OpenSSL is initialized.
Micros oft implemented one-byte fragments as a countermeas ure, and the s etting can be controlled via the regis try key
HKEY_LOCAL_MACHINE\Sys tem\CurrentControlSet\Control\SecurityProviders \SCHANNEL\SendExtraRecord.
Therefore, if multiple applications us e the s ame SSL/TLS implementation, s ome may be vulnerable while others may not,
depending on whether or not a countermeas ure has been enabled.
Note that this s cript detects the vulnerability in the SSLv3/TLSv1 protocol implemented in the s erver. It does not detect
the BEAST attack where it exploits the vulnerability at HTTPS client-s ide (i.e., Internet brows er). The detection at s erver-
s ide does not neces s arily mean your s erver is vulnerable to the BEAST attack becaus e the attack exploits the
vulnerability at client-s ide, and both SSL/TLS clients and s ervers can independently employ the s plit record
countermeas ure.
Solution:
Configure SSL/TLS s ervers to only us e TLS 1.1 or TLS 1.2 if s upported.
Configure SSL/TLS s ervers to only s upport cipher s uites that do not us e block ciphers . Apply patches if available.
Note that additional configuration may be required after the ins tallation of the MS12-006 s ecurity update in order to
enable the s plit-record countermeas ure. See http://s upport.micros oft.com/kb/2643584 for details .
Result:
Negotiated cipher suite: AES256-SHA|TLSv1|Kx=RSA|Au=RSA|Enc=AES-C BC (256)|Mac=SHA1
References:
http://www.opens s l.org/~bodo/tls -cbc.txt
http://vnhacker.blogs pot.com/2011/09/beas t.html
http://technet.micros oft.com/en-us /s ecurity/bulletin/ms 12-006
http://s upport.micros oft.com/kb/2643584
http://blogs .ms dn.com/b/kaus hal/archive/2012/01/21/fixing-the-beas t.as px
Alert ID: 84519 Found on: 2017-01-17 Severity: Medium
SSL Certificate Cannot Be Trusted (tcp/995)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 6.4
Cvss Score: 6.4
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:N
PCI Compliance: Fail
Description:
The s erver's X.509 certificate does not have a s ignature from a known public certificate authority. This s ituation can
occur in three different ways , each of which res ults in a break in the chain below which certificates cannot be trus ted.
Firs t, the top of the certificate chain s ent by the s erver might not be des cended from a known public certificate authority.
This can occur either when the top of the chain is an unrecognized, s elf-s igned certificate, or when intermediate
certificates are mis s ing that would connect the top of the certificate chain to a known public certificate authority.
Second, the certificate chain may contain a certificate that is not valid at the time of the s can. This can occur either when
the s can occurs before one of the certificate's 'notBefore' dates , or after one of the certificate's 'notAfter' dates .
Page 32 of 120
Scan Date: 2017-01-17
Third, the certificate chain may contain a s ignature that either didn't match the certificate's information, or was not
pos s ible to verify. Bad s ignatures can be fixed by getting the certificate with the bad s ignature to be re-s igned by its
is s uer. Signatures that could not be verified are the res ult of the certificate's is s uer us ing a s igning algorithm that
Indus Guard either does not s upport or does not recognize.
If the remote hos t is a public hos t in production, any break in the chain nullifies the us e of SSL as anyone could es tablis h
a man in the middle attack agains t the remote hos t.
Solution:
Purchas e or generate a proper certificate for this s ervice.
Result:
The following certificate was part of the certificate chainsent by the rem ote host, but it has expired :|-Subject :
C =US/ST=Virginia/L=Herndon/O =Parallels/O U=Parallels Panel/C N=Parallels Panel/E=info@ parallels.com |-Not
After : Nov 09 10:32:06 2013 GMTThe following certificate was at the top of the certificatechain sent by the rem ote
host, but it is signed by an unknowncertificate authority :|-Subject :
C =US/ST=Virginia/L=Herndon/O =Parallels/O U=Parallels Panel/C N=Parallels Panel/E=info@ parallels.com |-Issuer :
C =US/ST=Virginia/L=Herndon/O =Parallels/O U=Parallels Panel/C N=Parallels Panel/E=info@ parallels.com
Alert ID: 84520 Found on: 2017-01-17 Severity: Medium
SSL Self-Signed Certificate (tcp/995)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 6.4
Cvss Score: 6.4
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:N
PCI Compliance: Fail
Description:
The X.509 certificate chain for this s ervice is not s igned by a recognized certificate authority. If the remote hos t is a
public hos t in production, this nullifies the us e of SSL as anyone could es tablis h a man in the middle attack agains t the
remote hos t.
Note that this check does not check for certificate chains that end in a certificate that is not s elf-s igned, but is s igned by
an unrecognized certificate authority.
Solution:
Purchas e or generate a proper certificate for this s ervice.
Result:
The following certificate was found at the top of the certificatechain sent by the rem ote host, but is self-signed and
was notfound in the list of known certificate authorities :|-Subject :
C =US/ST=Virginia/L=Herndon/O =Parallels/O U=Parallels Panel/C N=Parallels Panel/E=info@ parallels.com
Alert ID: 84522 Found on: 2017-01-17 Severity: Medium
SSL Certificate Expiry (tcp/995)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 5.0
Cvss Score: 5.0
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:N/I:P/A:N
PCI Compliance: Fail
Description:
This s cript checks expiry dates of certificates as s ociated with SSL- enabled s ervices on the target and reports whether
any have already expired.
Solution:
Page 33 of 120
Scan Date: 2017-01-17
Purchas e or generate a new SSL certificate to replace the exis ting one.
Result:
The SSL certificate has already expired : Subject : C =US, ST=Virginia, L=Herndon, O =Parallels, O U=Parallels
Panel, C N=Parallels Panel, em ailAddress=info@ parallels.com Issuer : C =US, ST=Virginia, L=Herndon,
O =Parallels, O U=Parallels Panel, C N=Parallels Panel, em ailAddress=info@ parallels.com Not valid before : Nov 9
10:32:06 2012 GMT Not valid after : Nov 9 10:32:06 2013 GMT
Alert ID: 84525 Found on: 2017-01-17 Severity: Medium
SSL Certificate with Wrong Hostname (tcp/993)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 5.0
Cvss Score: 5.0
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:N/I:P/A:N
PCI Compliance: Fail
Description:
The commonName (CN) of the SSL certificate pres ented on this s ervice is for a different machine.
Solution:
Purchas e or generate a proper certificate for this s ervice.
Result:
The identity known by IndusGuard is : rs202995.rs.hosteurope.deThe C om m on Nam e in the certificate is :
Parallels Panel
Alert ID: 84528 Found on: 2017-01-17 Severity: Medium
SSLv3 Padding Oracle On Downgraded Legacy Encryption Vulnerability (POODLE) (tcp/993)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2014-3566
Cvss Base: 4.3
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N
Description:
The remote hos t is affected by a man-in-the-middle (MitM) information dis clos ure vulnerability known as POODLE. The
vulnerability is due to the way SSL 3.0 handles padding bytes when decrypting mes s ages encrypted us ing block ciphers
in cipher block chaining (CBC) mode. A MitM attacker can decrypt a s elected byte of a cipher text in as few as 256 tries if
they are able to force a victim application to repeatedly s end the s ame data over newly created SSL 3.0 connections .
As long as a client and s ervice both s upport SSLv3, a connection can be 'rolled back' to SSLv3, even if TLSv1 or newer is
s upported by the client and s ervice.
The TLS Fallback SCSV extens ion prevents 'vers ion rollback' attacks without impacting legacy clients ; however, it can
only protect connections when the client and s ervice s upport the extens ion. Sites that cannot dis able SSLv3 immediately
s hould enable this extens ion.
This is a vulnerability in the SSLv3 s pecification, not in a particular SSL implementation. Dis abling SSLv3 is the only way to
completely mitigate the vulnerability.
Solution:
Dis able SSLv3.
Services that mus t s upport SSLv3 s hould enable the TLS Fallback SCSV extens ion until SSLv3 can be dis abled.
Result:
Page 34 of 120
Scan Date: 2017-01-17
IndusGuard determ ined that the rem ote server supports SSLv3 with at least one C BC cipher suite, indicating that
this server is vulnerable.It appears that TLSv1 or newer is supported on the server. However, the Fallback SC SV
m echanism is not supported, allowing connections to be "rolled back" to SSLv3.
References:
https ://www.imperialviolet.org/2014/10/14/poodle.html
https ://www.opens s l.org/~bodo/s s l-poodle.pdf
https ://tools .ietf.org/html/draft-ietf-tls -downgrade-s cs v-00
Alert ID: 84529 Found on: 2017-01-17 Severity: Medium
SSL Medium Strength Cipher Suites Supported (tcp/993)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 4.3
Cvss Score: 4.3
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N
PCI Compliance: Fail
Description:
The remote hos t s upports the us e of SSL ciphers that offer medium s trength encryption, which we currently regard as
thos e with key lengths at leas t 56 bits and les s than 112 bits .
Note: This is cons iderably eas ier to exploit if the attacker is on the s ame phys ical network.
Solution:
Reconfigure the affected application if pos s ible to avoid us e of medium s trength ciphers .
Result:
Here is the list of m edium strength SSL ciphers supported by the rem ote server : Medium Strength C iphers (> 64-
bit and < 112-bit key) SSLv2 DES-C BC 3-MD5 Kx=RSA Au=RSA Enc=3DES-C BC (168) Mac=MD5 TLSv1 DES-C BC 3-
SHA Kx=RSA Au=RSA Enc=3DES-C BC (168) Mac=SHA1 The fields above are : {O penSSL ciphernam e} Kx={key
exchange} Au={authentication} Enc={sym m etric encryption m ethod} Mac={m essage authentication code}
{export flag}
Alert ID: 84530 Found on: 2017-01-17 Severity: Medium
SSL DROWN Attack Vulnerability (Decrypting RSA with Obsolete and Weakened eNcryption) (tcp/993)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2016-0800
Cvss Base: 4.0
Cvss Vector: CVSS2#AV:N/AC:H/Au:N/C:P/I:P/A:N
Description:
The remote hos t s upports SSLv2 and therefore may be affected by a vulnerability that allows a cros s -protocol
Bleichenbacher padding oracle attack known as DROWN (Decrypting RSA with Obs olete and Weakened eNcryption). This
vulnerability exis ts due to a flaw in the Secure Sockets Layer Vers ion 2 (SSLv2) implementation, and it allows captured
TLS traffic to be decrypted. A man-in-the-middle attacker can exploit this to decrypt the TLS connection by utilizing
previous ly captured traffic and weak cryptography along with a s eries of s pecially crafted connections to an SSLv2
s erver that us es the s ame private key.
Solution:
Dis able SSLv2 and export grade cryptography cipher s uites . Ens ure that private keys are not us ed anywhere with s erver
s oftware that s upports SSLv2 connections .
Result:
Page 35 of 120
Scan Date: 2017-01-17
The rem ote host is affected by SSL DRO WN and supports the followingvulnerable cipher suites : Low Strength
C iphers (<= 64-bit key) SSLv2 DES-C BC -MD5 Kx=RSA Au=RSA Enc=DES-C BC (56) Mac=MD5 EXP-RC 2-C BC -MD5
Kx=RSA(512) Au=RSA Enc=RC 2-C BC (40) Mac=MD5 export EXP-RC 4-MD5 Kx=RSA(512) Au=RSA Enc=RC 4(40)
Mac=MD5 export High Strength C iphers (>= 112-bit key) SSLv2 RC 4-MD5 Kx=RSA Au=RSA Enc=RC 4(128)
Mac=MD5 The fields above are : {O penSSL ciphernam e} Kx={key exchange} Au={authentication}
Enc={sym m etric encryption m ethod} Mac={m essage authentication code} {export flag}
References:
https ://drownattack.com/
https ://drownattack.com/drown-attack-paper.pdf
Alert ID: 84532 Found on: 2017-01-17 Severity: Medium
SSL Weak Cipher Suites Supported (tcp/993)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 4.3
Cvss Score: 4.3
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N
PCI Compliance: Fail
Description:
The remote hos t s upports the us e of SSL ciphers that offer either weak encryption or no encryption at all.
Note: This is cons iderably eas ier to exploit if the attacker is on the s ame phys ical network.
Solution:
Reconfigure the affected application if pos s ible to avoid us e of weak ciphers .
Result:
Here is the list of weak SSL ciphers supported by the rem ote server : Low Strength C iphers (<= 64-bit key) SSLv2
DES-C BC -MD5 Kx=RSA Au=RSA Enc=DES-C BC (56) Mac=MD5 EXP-RC 2-C BC -MD5 Kx=RSA(512) Au=RSA Enc=RC 2-
C BC (40) Mac=MD5 export EXP-RC 4-MD5 Kx=RSA(512) Au=RSA Enc=RC 4(40) Mac=MD5 export TLSv1 EXP-DES-
C BC -SHA Kx=RSA(512) Au=RSA Enc=DES-C BC (40) Mac=SHA1 export EXP-RC 2-C BC -MD5 Kx=RSA(512) Au=RSA
Enc=RC 2-C BC (40) Mac=MD5 export EXP-RC 4-MD5 Kx=RSA(512) Au=RSA Enc=RC 4(40) Mac=MD5 export DES-
C BC -SHA Kx=RSA Au=RSA Enc=DES-C BC (56) Mac=SHA1 The fields above are : {O penSSL ciphernam e} Kx={key
exchange} Au={authentication} Enc={sym m etric encryption m ethod} Mac={m essage authentication code}
{export flag}
References:
http://www.opens s l.org/docs /apps /ciphers .html
Alert ID: 84533 Found on: 2017-01-17 Severity: Medium
SSL Version 2 (v2) Protocol Detection (tcp/993)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2005-2969
Cvss Base: 5.0
Cvss Score: 5.0
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N
PCI Compliance: Fail
Description:
The remote s ervice accepts connections encrypted us ing SSL 2.0, which reportedly s uffers from s everal cryptographic
flaws and has been deprecated for s everal years . An attacker may be able to exploit thes e is s ues to conduct man-in-
the-middle attacks or decrypt communications between the affected s ervice and clients .
Page 36 of 120
Scan Date: 2017-01-17
Solution:
Cons ult the application's documentation to dis able SSL 2.0 and us e SSL 3.0, TLS 1.0, or higher ins tead.
Result:
- SSLv2 is enabled and the server supports at least one cipher.- SSLv3 is enabled and the server supports at least
one cipher.
References:
http://www.s chneier.com/paper-s s l.pdf
http://s upport.micros oft.com/kb/187498
http://www.linux4beginners .info/node/dis able-s s lv2
Alert ID: 84534 Found on: 2017-01-17 Severity: Medium
SSL/TLS EXPORT_RSA <= 512-bit Cipher Suites Supported (FREAK) (tcp/993)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 5.0
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:N/I:P/A:N
Description:
The remote hos t s upports EXPORT_RSA cipher s uites with keys les s than or equal to 512 bits . An attacker can factor a
512-bit RSA modulus in a s hort amount of time.
A man-in-the middle attacker may be able to downgrade the s es s ion to us e EXPORT_RSA cipher s uites (e.g. CVE-2015-
0204). Thus , it is recommended to remove s upport for weak cipher s uites .
Solution:
Reconfigure the s ervice to remove s upport for EXPORT_RSA cipher s uites .
Result:
EXPO RT_RSA cipher suites supported by the rem ote server : Low Strength C iphers (<= 64-bit key) TLSv1 EXP-DES-
C BC -SHA Kx=RSA(512) Au=RSA Enc=DES-C BC (40) Mac=SHA1 export EXP-RC 2-C BC -MD5 Kx=RSA(512) Au=RSA
Enc=RC 2-C BC (40) Mac=MD5 export EXP-RC 4-MD5 Kx=RSA(512) Au=RSA Enc=RC 4(40) Mac=MD5 export The
fields above are : {O penSSL ciphernam e} Kx={key exchange} Au={authentication} Enc={sym m etric
encryption m ethod} Mac={m essage authentication code} {export flag}
References:
https ://www.s macktls .com/#freak
https ://www.opens s l.org/news /s ecadv_20150108.txt
http://www.Indus Guard.org/u?b78da2c4
Alert ID: 84536 Found on: 2017-01-17 Severity: Medium
OpenSSL 'ChangeCipherSpec' MiTM Vulnerability (tcp/993)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2014-0224
Cvss Base: 5.8
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:P/I:P/A:N
Description:
The OpenSSL s ervice on the remote hos t is vulnerable to a man-in-the-middle (MiTM) attack, bas ed on its res pons e to
two cons ecutive 'ChangeCipherSpec' mes s ages during the incorrect phas e of an SSL/TLS hands hake.
Page 37 of 120
Scan Date: 2017-01-17
This flaw could allow a MiTM attacker to decrypt or forge SSL mes s ages by telling the s ervice to begin encrypted
communications before key material has been exchanged, which caus es predictable keys to be us ed to s ecure future
traffic.
Solution:
OpenSSL 0.9.8 SSL/TLS us ers (client and/or s erver) s hould upgrade to 0.9.8za. OpenSSL 1.0.0 SSL/TLS us ers (client and/or
s erver) s hould upgrade to 1.0.0m. OpenSSL 1.0.1 SSL/TLS us ers (client and/or s erver) s hould upgrade to 1.0.1h.
Result:
The rem ote service accepted an SSL C hangeC ipherSpec m essage at an incorrect point in the handshake
leading to weak keys being used, and then attem pted to decrypt an SSL record using those weak keys.This
check detects unpatched O penSSL 1.0.1, 1.0.0, and 0.9.8 services. O nly 1.0.1 has been shown to be exploitable;
however, O penSSL 1.0.0 and 0.9.8 have received sim ilar patches and users of these versions have been
advised to upgrade as a precaution.
References:
http://www.Indus Guard.org/u?d5709faa
https ://www.imperialviolet.org/2014/06/05/earlyccs .html
https ://www.opens s l.org/news /s ecadv_20140605.txt
Alert ID: 84537 Found on: 2017-01-17 Severity: Medium
SSL/TLS Protocol Initialization Vector Implementation Information Disclosure Vulnerability (tcp/993)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2011-3389
Cvss Base: 4.3
Cvss Score: 4.3
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N
PCI Compliance: Fail
Description:
A vulnerability exis ts in SSL 3.0 and TLS 1.0 that could allow information dis clos ure if an attacker intercepts encrypted
traffic s erved from an affected s ys tem.
TLS 1.1, TLS 1.2, and all cipher s uites that do not us e CBC mode are not affected.
This s cript tries to es tablis h an SSL/TLS remote connection us ing an affected SSL vers ion and cipher s uite, and then
s olicits return data.
If returned application data is not fragmented with an empty or one-byte record, it is likely vulnerable.
OpenSSL us es empty fragments as a countermeas ure unles s the 'SSL_OP_DONT_INSERT_EMPTY_FRAGMENTS' option is
s pecified when OpenSSL is initialized.
Micros oft implemented one-byte fragments as a countermeas ure, and the s etting can be controlled via the regis try key
HKEY_LOCAL_MACHINE\Sys tem\CurrentControlSet\Control\SecurityProviders \SCHANNEL\SendExtraRecord.
Therefore, if multiple applications us e the s ame SSL/TLS implementation, s ome may be vulnerable while others may not,
depending on whether or not a countermeas ure has been enabled.
Note that this s cript detects the vulnerability in the SSLv3/TLSv1 protocol implemented in the s erver. It does not detect
the BEAST attack where it exploits the vulnerability at HTTPS client-s ide (i.e., Internet brows er). The detection at s erver-
s ide does not neces s arily mean your s erver is vulnerable to the BEAST attack becaus e the attack exploits the
vulnerability at client-s ide, and both SSL/TLS clients and s ervers can independently employ the s plit record
countermeas ure.
Solution:
Page 38 of 120
Scan Date: 2017-01-17
Configure SSL/TLS s ervers to only us e TLS 1.1 or TLS 1.2 if s upported.
Configure SSL/TLS s ervers to only s upport cipher s uites that do not us e block ciphers . Apply patches if available.
Note that additional configuration may be required after the ins tallation of the MS12-006 s ecurity update in order to
enable the s plit-record countermeas ure. See http://s upport.micros oft.com/kb/2643584 for details .
Result:
Negotiated cipher suite: AES256-SHA|TLSv1|Kx=RSA|Au=RSA|Enc=AES-C BC (256)|Mac=SHA1
References:
http://www.opens s l.org/~bodo/tls -cbc.txt
http://vnhacker.blogs pot.com/2011/09/beas t.html
http://technet.micros oft.com/en-us /s ecurity/bulletin/ms 12-006
http://s upport.micros oft.com/kb/2643584
http://blogs .ms dn.com/b/kaus hal/archive/2012/01/21/fixing-the-beas t.as px
Alert ID: 84540 Found on: 2017-01-17 Severity: Medium
SSL Certificate Cannot Be Trusted (tcp/993)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 6.4
Cvss Score: 6.4
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:N
PCI Compliance: Fail
Description:
The s erver's X.509 certificate does not have a s ignature from a known public certificate authority. This s ituation can
occur in three different ways , each of which res ults in a break in the chain below which certificates cannot be trus ted.
Firs t, the top of the certificate chain s ent by the s erver might not be des cended from a known public certificate authority.
This can occur either when the top of the chain is an unrecognized, s elf-s igned certificate, or when intermediate
certificates are mis s ing that would connect the top of the certificate chain to a known public certificate authority.
Second, the certificate chain may contain a certificate that is not valid at the time of the s can. This can occur either when
the s can occurs before one of the certificate's 'notBefore' dates , or after one of the certificate's 'notAfter' dates .
Third, the certificate chain may contain a s ignature that either didn't match the certificate's information, or was not
pos s ible to verify. Bad s ignatures can be fixed by getting the certificate with the bad s ignature to be re-s igned by its
is s uer. Signatures that could not be verified are the res ult of the certificate's is s uer us ing a s igning algorithm that
Indus Guard either does not s upport or does not recognize.
If the remote hos t is a public hos t in production, any break in the chain nullifies the us e of SSL as anyone could es tablis h
a man in the middle attack agains t the remote hos t.
Solution:
Purchas e or generate a proper certificate for this s ervice.
Result:
The following certificate was part of the certificate chainsent by the rem ote host, but it has expired :|-Subject :
C =US/ST=Virginia/L=Herndon/O =Parallels/O U=Parallels Panel/C N=Parallels Panel/E=info@ parallels.com |-Not
After : Nov 09 10:32:06 2013 GMTThe following certificate was at the top of the certificatechain sent by the rem ote
host, but it is signed by an unknowncertificate authority :|-Subject :
C =US/ST=Virginia/L=Herndon/O =Parallels/O U=Parallels Panel/C N=Parallels Panel/E=info@ parallels.com |-Issuer :
C =US/ST=Virginia/L=Herndon/O =Parallels/O U=Parallels Panel/C N=Parallels Panel/E=info@ parallels.com
Page 39 of 120
Scan Date: 2017-01-17
Alert ID: 84541 Found on: 2017-01-17 Severity: Medium
SSL Self-Signed Certificate (tcp/993)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 6.4
Cvss Score: 6.4
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:N
PCI Compliance: Fail
Description:
The X.509 certificate chain for this s ervice is not s igned by a recognized certificate authority. If the remote hos t is a
public hos t in production, this nullifies the us e of SSL as anyone could es tablis h a man in the middle attack agains t the
remote hos t.
Note that this check does not check for certificate chains that end in a certificate that is not s elf-s igned, but is s igned by
an unrecognized certificate authority.
Solution:
Purchas e or generate a proper certificate for this s ervice.
Result:
The following certificate was found at the top of the certificatechain sent by the rem ote host, but is self-signed and
was notfound in the list of known certificate authorities :|-Subject :
C =US/ST=Virginia/L=Herndon/O =Parallels/O U=Parallels Panel/C N=Parallels Panel/E=info@ parallels.com
Alert ID: 84543 Found on: 2017-01-17 Severity: Medium
SSL Certificate Expiry (tcp/993)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 5.0
Cvss Score: 5.0
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:N/I:P/A:N
PCI Compliance: Fail
Description:
This s cript checks expiry dates of certificates as s ociated with SSL- enabled s ervices on the target and reports whether
any have already expired.
Solution:
Purchas e or generate a new SSL certificate to replace the exis ting one.
Result:
The SSL certificate has already expired : Subject : C =US, ST=Virginia, L=Herndon, O =Parallels, O U=Parallels
Panel, C N=Parallels Panel, em ailAddress=info@ parallels.com Issuer : C =US, ST=Virginia, L=Herndon,
O =Parallels, O U=Parallels Panel, C N=Parallels Panel, em ailAddress=info@ parallels.com Not valid before : Nov 9
10:32:06 2012 GMT Not valid after : Nov 9 10:32:06 2013 GMT
Alert ID: 84546 Found on: 2017-01-17 Severity: Medium
SSL Certificate with Wrong Hostname (tcp/465)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 5.0
Cvss Score: 5.0
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:N/I:P/A:N
PCI Compliance: Fail
Page 40 of 120
Scan Date: 2017-01-17
Description:
The commonName (CN) of the SSL certificate pres ented on this s ervice is for a different machine.
Solution:
Purchas e or generate a proper certificate for this s ervice.
Result:
The identity known by IndusGuard is : rs202995.rs.hosteurope.deThe C om m on Nam e in the certificate is :
Parallels Panel
Alert ID: 84547 Found on: 2017-01-17 Severity: Medium
SSL/TLS Diffie-Hellman Modulus <= 1024 Bits (LogJam) (tcp/465)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 4.0
Cvss Vector: CVSS2#AV:N/AC:H/Au:N/C:P/I:P/A:N
Description:
The remote hos t allows SSL/TLS connections with one or more Diffie-Hellman moduli les s than or equal to 1024 bits .
Through cryptanalys is , a third party may be able to find the s hared s ecret in a s hort amount of time (depending on
modulus s ize and attacker res ources ). This may allow the attacker to recover the plain text or potentially violate the
integrity of connections .
Solution:
Reconfigure the s ervice to us e a unique Diffie-Hellman moduli of 2048 bits or greater.
Result:
Vulnerable connection com binations : SSL/TLS version : TLSv1.0 C ipher suite :
TLS1_C K_DHE_RSA_WITH_AES_256_C BC _SHA Diffie-Hellm an MO DP size (bits) : 1024 Logjam attack difficulty : Hard
(would require nation-state resources) SSL/TLS version : TLSv1.0 C ipher suite :
TLS1_C K_DHE_RSA_WITH_3DES_EDE_C BC _SHA Diffie-Hellm an MO DP size (bits) : 1024 Logjam attack difficulty :
Hard (would require nation-state resources) SSL/TLS version : TLSv1.0 C ipher suite :
TLS1_C K_DHE_RSA_WITH_AES_128_C BC _SHA Diffie-Hellm an MO DP size (bits) : 1024 Logjam attack difficulty : Hard
(would require nation-state resources) SSL/TLS version : SSLv3 C ipher suite :
TLS1_C K_DHE_RSA_WITH_AES_256_C BC _SHA Diffie-Hellm an MO DP size (bits) : 1024 Logjam attack difficulty : Hard
(would require nation-state resources) SSL/TLS version : SSLv3 C ipher suite :
TLS1_C K_DHE_RSA_WITH_3DES_EDE_C BC _SHA Diffie-Hellm an MO DP size (bits) : 1024 Logjam attack difficulty :
Hard (would require nation-state resources) SSL/TLS version : SSLv3 C ipher suite :
TLS1_C K_DHE_RSA_WITH_AES_128_C BC _SHA Diffie-Hellm an MO DP size (bits) : 1024 Logjam attack difficulty : Hard
(would require nation-state resources)
References:
http://weakdh.org/
Alert ID: 84550 Found on: 2017-01-17 Severity: Medium
SSLv3 Padding Oracle On Downgraded Legacy Encryption Vulnerability (POODLE) (tcp/465)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2014-3566
Cvss Base: 4.3
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N
Description:
The remote hos t is affected by a man-in-the-middle (MitM) information dis clos ure vulnerability known as POODLE. The
vulnerability is due to the way SSL 3.0 handles padding bytes when decrypting mes s ages encrypted us ing block ciphers
in cipher block chaining (CBC) mode. A MitM attacker can decrypt a s elected byte of a cipher text in as few as 256 tries if
Page 41 of 120
Scan Date: 2017-01-17
they are able to force a victim application to repeatedly s end the s ame data over newly created SSL 3.0 connections .
As long as a client and s ervice both s upport SSLv3, a connection can be 'rolled back' to SSLv3, even if TLSv1 or newer is
s upported by the client and s ervice.
The TLS Fallback SCSV extens ion prevents 'vers ion rollback' attacks without impacting legacy clients ; however, it can
only protect connections when the client and s ervice s upport the extens ion. Sites that cannot dis able SSLv3 immediately
s hould enable this extens ion.
This is a vulnerability in the SSLv3 s pecification, not in a particular SSL implementation. Dis abling SSLv3 is the only way to
completely mitigate the vulnerability.
Solution:
Dis able SSLv3.
Services that mus t s upport SSLv3 s hould enable the TLS Fallback SCSV extens ion until SSLv3 can be dis abled.
Result:
IndusGuard determ ined that the rem ote server supports SSLv3 with at least one C BC cipher suite, indicating that
this server is vulnerable.It appears that TLSv1 or newer is supported on the server. However, the Fallback SC SV
m echanism is not supported, allowing connections to be "rolled back" to SSLv3.
References:
https ://www.imperialviolet.org/2014/10/14/poodle.html
https ://www.opens s l.org/~bodo/s s l-poodle.pdf
https ://tools .ietf.org/html/draft-ietf-tls -downgrade-s cs v-00
Alert ID: 84551 Found on: 2017-01-17 Severity: Medium
SSL Medium Strength Cipher Suites Supported (tcp/465)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 4.3
Cvss Score: 4.3
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N
PCI Compliance: Fail
Description:
The remote hos t s upports the us e of SSL ciphers that offer medium s trength encryption, which we currently regard as
thos e with key lengths at leas t 56 bits and les s than 112 bits .
Note: This is cons iderably eas ier to exploit if the attacker is on the s ame phys ical network.
Solution:
Reconfigure the affected application if pos s ible to avoid us e of medium s trength ciphers .
Result:
Here is the list of m edium strength SSL ciphers supported by the rem ote server : Medium Strength C iphers (> 64-
bit and < 112-bit key) TLSv1 EDH-RSA-DES-C BC 3-SHA Kx=DH Au=RSA Enc=3DES-C BC (168) Mac=SHA1 ADH-DES-
C BC 3-SHA Kx=DH Au=None Enc=3DES-C BC (168) Mac=SHA1 DES-C BC 3-SHA Kx=RSA Au=RSA Enc=3DES-
C BC (168) Mac=SHA1 The fields above are : {O penSSL ciphernam e} Kx={key exchange} Au={authentication}
Enc={sym m etric encryption m ethod} Mac={m essage authentication code} {export flag}
Alert ID: 84553 Found on: 2017-01-17 Severity: Medium
SSL Version 2 (v2) Protocol Detection (tcp/465)
Open Status: NEW First Found: 2017-01-17
Page 42 of 120
Scan Date: 2017-01-17
CVE ID: CVE-2005-2969
Cvss Base: 5.0
Cvss Score: 5.0
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N
PCI Compliance: Fail
Description:
The remote s ervice accepts connections encrypted us ing SSL 2.0, which reportedly s uffers from s everal cryptographic
flaws and has been deprecated for s everal years . An attacker may be able to exploit thes e is s ues to conduct man-in-
the-middle attacks or decrypt communications between the affected s ervice and clients .
Solution:
Cons ult the application's documentation to dis able SSL 2.0 and us e SSL 3.0, TLS 1.0, or higher ins tead.
Result:
- SSLv3 is enabled and the server supports at least one cipher.
References:
http://www.s chneier.com/paper-s s l.pdf
http://s upport.micros oft.com/kb/187498
http://www.linux4beginners .info/node/dis able-s s lv2
Alert ID: 84555 Found on: 2017-01-17 Severity: Medium
SSL Anonymous Cipher Suites Supported (tcp/465)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2007-1858
Cvss Base: 4.3
Cvss Score: 4.3
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N
PCI Compliance: Fail
Description:
The remote hos t s upports the us e of anonymous SSL ciphers . While this enables an adminis trator to s et up a s ervice
that encrypts traffic without having to generate and configure SSL certificates , it offers no way to verify the remote hos t's
identity and renders the s ervice vulnerable to a man-in-the-middle attack.
Note: This is cons iderably eas ier to exploit if the attacker is on the s ame phys ical network.
Solution:
Reconfigure the affected application if pos s ible to avoid us e of weak ciphers .
Result:
Here is the list of SSL anonym ous ciphers supported by the rem ote server : Medium Strength C iphers (> 64-bit
and < 112-bit key) TLSv1 ADH-DES-C BC 3-SHA Kx=DH Au=None Enc=3DES-C BC (168) Mac=SHA1 High Strength
C iphers (>= 112-bit key) TLSv1 ADH-AES128-SHA Kx=DH Au=None Enc=AES-C BC (128) Mac=SHA1 ADH-AES256-
SHA Kx=DH Au=None Enc=AES-C BC (256) Mac=SHA1 ADH-RC 4-MD5 Kx=DH Au=None Enc=RC 4(128) Mac=MD5
The fields above are : {O penSSL ciphernam e} Kx={key exchange} Au={authentication} Enc={sym m etric
encryption m ethod} Mac={m essage authentication code} {export flag}
References:
http://www.opens s l.org/docs /apps /ciphers .html
Alert ID: 84557 Found on: 2017-01-17 Severity: Medium
Page 43 of 120
Scan Date: 2017-01-17
OpenSSL 'ChangeCipherSpec' MiTM Vulnerability (tcp/465)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2014-0224
Cvss Base: 5.8
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:P/I:P/A:N
Description:
The OpenSSL s ervice on the remote hos t is vulnerable to a man-in-the-middle (MiTM) attack, bas ed on its res pons e to
two cons ecutive 'ChangeCipherSpec' mes s ages during the incorrect phas e of an SSL/TLS hands hake.
This flaw could allow a MiTM attacker to decrypt or forge SSL mes s ages by telling the s ervice to begin encrypted
communications before key material has been exchanged, which caus es predictable keys to be us ed to s ecure future
traffic.
Solution:
OpenSSL 0.9.8 SSL/TLS us ers (client and/or s erver) s hould upgrade to 0.9.8za. OpenSSL 1.0.0 SSL/TLS us ers (client and/or
s erver) s hould upgrade to 1.0.0m. OpenSSL 1.0.1 SSL/TLS us ers (client and/or s erver) s hould upgrade to 1.0.1h.
Result:
The rem ote service accepted an SSL C hangeC ipherSpec m essage at an incorrect point in the handshake
leading to weak keys being used, and then attem pted to decrypt an SSL record using those weak keys.This
check detects unpatched O penSSL 1.0.1, 1.0.0, and 0.9.8 services. O nly 1.0.1 has been shown to be exploitable;
however, O penSSL 1.0.0 and 0.9.8 have received sim ilar patches and users of these versions have been
advised to upgrade as a precaution.
References:
http://www.Indus Guard.org/u?d5709faa
https ://www.imperialviolet.org/2014/06/05/earlyccs .html
https ://www.opens s l.org/news /s ecadv_20140605.txt
Alert ID: 84558 Found on: 2017-01-17 Severity: Medium
SSL/TLS Protocol Initialization Vector Implementation Information Disclosure Vulnerability (tcp/465)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2011-3389
Cvss Base: 4.3
Cvss Score: 4.3
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N
PCI Compliance: Fail
Description:
A vulnerability exis ts in SSL 3.0 and TLS 1.0 that could allow information dis clos ure if an attacker intercepts encrypted
traffic s erved from an affected s ys tem.
TLS 1.1, TLS 1.2, and all cipher s uites that do not us e CBC mode are not affected.
This s cript tries to es tablis h an SSL/TLS remote connection us ing an affected SSL vers ion and cipher s uite, and then
s olicits return data.
If returned application data is not fragmented with an empty or one-byte record, it is likely vulnerable.
OpenSSL us es empty fragments as a countermeas ure unles s the 'SSL_OP_DONT_INSERT_EMPTY_FRAGMENTS' option is
s pecified when OpenSSL is initialized.
Micros oft implemented one-byte fragments as a countermeas ure, and the s etting can be controlled via the regis try key
HKEY_LOCAL_MACHINE\Sys tem\CurrentControlSet\Control\SecurityProviders \SCHANNEL\SendExtraRecord.
Page 44 of 120
Scan Date: 2017-01-17
Therefore, if multiple applications us e the s ame SSL/TLS implementation, s ome may be vulnerable while others may not,
depending on whether or not a countermeas ure has been enabled.
Note that this s cript detects the vulnerability in the SSLv3/TLSv1 protocol implemented in the s erver. It does not detect
the BEAST attack where it exploits the vulnerability at HTTPS client-s ide (i.e., Internet brows er). The detection at s erver-
s ide does not neces s arily mean your s erver is vulnerable to the BEAST attack becaus e the attack exploits the
vulnerability at client-s ide, and both SSL/TLS clients and s ervers can independently employ the s plit record
countermeas ure.
Solution:
Configure SSL/TLS s ervers to only us e TLS 1.1 or TLS 1.2 if s upported.
Configure SSL/TLS s ervers to only s upport cipher s uites that do not us e block ciphers . Apply patches if available.
Note that additional configuration may be required after the ins tallation of the MS12-006 s ecurity update in order to
enable the s plit-record countermeas ure. See http://s upport.micros oft.com/kb/2643584 for details .
Result:
Negotiated cipher suite: AES256-SHA|TLSv1|Kx=RSA|Au=RSA|Enc=AES-C BC (256)|Mac=SHA1
References:
http://www.opens s l.org/~bodo/tls -cbc.txt
http://vnhacker.blogs pot.com/2011/09/beas t.html
http://technet.micros oft.com/en-us /s ecurity/bulletin/ms 12-006
http://s upport.micros oft.com/kb/2643584
http://blogs .ms dn.com/b/kaus hal/archive/2012/01/21/fixing-the-beas t.as px
Alert ID: 84561 Found on: 2017-01-17 Severity: Medium
SSL Certificate Cannot Be Trusted (tcp/465)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 6.4
Cvss Score: 6.4
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:N
PCI Compliance: Fail
Description:
The s erver's X.509 certificate does not have a s ignature from a known public certificate authority. This s ituation can
occur in three different ways , each of which res ults in a break in the chain below which certificates cannot be trus ted.
Firs t, the top of the certificate chain s ent by the s erver might not be des cended from a known public certificate authority.
This can occur either when the top of the chain is an unrecognized, s elf-s igned certificate, or when intermediate
certificates are mis s ing that would connect the top of the certificate chain to a known public certificate authority.
Second, the certificate chain may contain a certificate that is not valid at the time of the s can. This can occur either when
the s can occurs before one of the certificate's 'notBefore' dates , or after one of the certificate's 'notAfter' dates .
Third, the certificate chain may contain a s ignature that either didn't match the certificate's information, or was not
pos s ible to verify. Bad s ignatures can be fixed by getting the certificate with the bad s ignature to be re-s igned by its
is s uer. Signatures that could not be verified are the res ult of the certificate's is s uer us ing a s igning algorithm that
Indus Guard either does not s upport or does not recognize.
If the remote hos t is a public hos t in production, any break in the chain nullifies the us e of SSL as anyone could es tablis h
a man in the middle attack agains t the remote hos t.
Page 45 of 120
Scan Date: 2017-01-17
Solution:
Purchas e or generate a proper certificate for this s ervice.
Result:
The following certificate was part of the certificate chainsent by the rem ote host, but it has expired :|-Subject :
C =US/ST=Virginia/L=Herndon/O =Parallels/O U=Parallels Panel/C N=Parallels Panel/E=info@ parallels.com |-Not
After : Nov 09 10:32:06 2013 GMTThe following certificate was at the top of the certificatechain sent by the rem ote
host, but it is signed by an unknowncertificate authority :|-Subject :
C =US/ST=Virginia/L=Herndon/O =Parallels/O U=Parallels Panel/C N=Parallels Panel/E=info@ parallels.com |-Issuer :
C =US/ST=Virginia/L=Herndon/O =Parallels/O U=Parallels Panel/C N=Parallels Panel/E=info@ parallels.com
Alert ID: 84562 Found on: 2017-01-17 Severity: Medium
SSL Self-Signed Certificate (tcp/465)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 6.4
Cvss Score: 6.4
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:N
PCI Compliance: Fail
Description:
The X.509 certificate chain for this s ervice is not s igned by a recognized certificate authority. If the remote hos t is a
public hos t in production, this nullifies the us e of SSL as anyone could es tablis h a man in the middle attack agains t the
remote hos t.
Note that this check does not check for certificate chains that end in a certificate that is not s elf-s igned, but is s igned by
an unrecognized certificate authority.
Solution:
Purchas e or generate a proper certificate for this s ervice.
Result:
The following certificate was found at the top of the certificatechain sent by the rem ote host, but is self-signed and
was notfound in the list of known certificate authorities :|-Subject :
C =US/ST=Virginia/L=Herndon/O =Parallels/O U=Parallels Panel/C N=Parallels Panel/E=info@ parallels.com
Alert ID: 84564 Found on: 2017-01-17 Severity: Medium
SSL Certificate Expiry (tcp/465)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 5.0
Cvss Score: 5.0
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:N/I:P/A:N
PCI Compliance: Fail
Description:
This s cript checks expiry dates of certificates as s ociated with SSL- enabled s ervices on the target and reports whether
any have already expired.
Solution:
Purchas e or generate a new SSL certificate to replace the exis ting one.
Result:
The SSL certificate has already expired : Subject : C =US, ST=Virginia, L=Herndon, O =Parallels, O U=Parallels
Panel, C N=Parallels Panel, em ailAddress=info@ parallels.com Issuer : C =US, ST=Virginia, L=Herndon,
O =Parallels, O U=Parallels Panel, C N=Parallels Panel, em ailAddress=info@ parallels.com Not valid before : Nov 9
10:32:06 2012 GMT Not valid after : Nov 9 10:32:06 2013 GMT
Page 46 of 120
Scan Date: 2017-01-17
Alert ID: 84568 Found on: 2017-01-17 Severity: Medium
SSL Certificate with Wrong Hostname (tcp/143)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 5.0
Cvss Score: 5.0
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:N/I:P/A:N
PCI Compliance: Fail
Description:
The commonName (CN) of the SSL certificate pres ented on this s ervice is for a different machine.
Solution:
Purchas e or generate a proper certificate for this s ervice.
Result:
The identity known by IndusGuard is : rs202995.rs.hosteurope.deThe C om m on Nam e in the certificate is :
Parallels Panel
Alert ID: 84570 Found on: 2017-01-17 Severity: Medium
SSL Medium Strength Cipher Suites Supported (tcp/143)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 4.3
Cvss Score: 4.3
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N
PCI Compliance: Fail
Description:
The remote hos t s upports the us e of SSL ciphers that offer medium s trength encryption, which we currently regard as
thos e with key lengths at leas t 56 bits and les s than 112 bits .
Note: This is cons iderably eas ier to exploit if the attacker is on the s ame phys ical network.
Solution:
Reconfigure the affected application if pos s ible to avoid us e of medium s trength ciphers .
Result:
Here is the list of m edium strength SSL ciphers supported by the rem ote server : Medium Strength C iphers (> 64-
bit and < 112-bit key) TLSv1 DES-C BC 3-SHA Kx=RSA Au=RSA Enc=3DES-C BC (168) Mac=SHA1 The fields above
are : {O penSSL ciphernam e} Kx={key exchange} Au={authentication} Enc={sym m etric encryption m ethod}
Mac={m essage authentication code} {export flag}
Alert ID: 84572 Found on: 2017-01-17 Severity: Medium
SSL Weak Cipher Suites Supported (tcp/143)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 4.3
Cvss Score: 4.3
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N
PCI Compliance: Fail
Description:
The remote hos t s upports the us e of SSL ciphers that offer either weak encryption or no encryption at all.
Page 47 of 120
Scan Date: 2017-01-17
Note: This is cons iderably eas ier to exploit if the attacker is on the s ame phys ical network.
Solution:
Reconfigure the affected application if pos s ible to avoid us e of weak ciphers .
Result:
Here is the list of weak SSL ciphers supported by the rem ote server : Low Strength C iphers (<= 64-bit key) TLSv1
EXP-DES-C BC -SHA Kx=RSA(512) Au=RSA Enc=DES-C BC (40) Mac=SHA1 export EXP-RC 2-C BC -MD5 Kx=RSA(512)
Au=RSA Enc=RC 2-C BC (40) Mac=MD5 export EXP-RC 4-MD5 Kx=RSA(512) Au=RSA Enc=RC 4(40) Mac=MD5 export
DES-C BC -SHA Kx=RSA Au=RSA Enc=DES-C BC (56) Mac=SHA1 The fields above are : {O penSSL ciphernam e}
Kx={key exchange} Au={authentication} Enc={sym m etric encryption m ethod} Mac={m essage authentication
code} {export flag}
References:
http://www.opens s l.org/docs /apps /ciphers .html
Alert ID: 84573 Found on: 2017-01-17 Severity: Medium
SSL/TLS EXPORT_RSA <= 512-bit Cipher Suites Supported (FREAK) (tcp/143)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 5.0
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:N/I:P/A:N
Description:
The remote hos t s upports EXPORT_RSA cipher s uites with keys les s than or equal to 512 bits . An attacker can factor a
512-bit RSA modulus in a s hort amount of time.
A man-in-the middle attacker may be able to downgrade the s es s ion to us e EXPORT_RSA cipher s uites (e.g. CVE-2015-
0204). Thus , it is recommended to remove s upport for weak cipher s uites .
Solution:
Reconfigure the s ervice to remove s upport for EXPORT_RSA cipher s uites .
Result:
EXPO RT_RSA cipher suites supported by the rem ote server : Low Strength C iphers (<= 64-bit key) TLSv1 EXP-DES-
C BC -SHA Kx=RSA(512) Au=RSA Enc=DES-C BC (40) Mac=SHA1 export EXP-RC 2-C BC -MD5 Kx=RSA(512) Au=RSA
Enc=RC 2-C BC (40) Mac=MD5 export EXP-RC 4-MD5 Kx=RSA(512) Au=RSA Enc=RC 4(40) Mac=MD5 export The
fields above are : {O penSSL ciphernam e} Kx={key exchange} Au={authentication} Enc={sym m etric
encryption m ethod} Mac={m essage authentication code} {export flag}
References:
https ://www.s macktls .com/#freak
https ://www.opens s l.org/news /s ecadv_20150108.txt
http://www.Indus Guard.org/u?b78da2c4
Alert ID: 84575 Found on: 2017-01-17 Severity: Medium
OpenSSL 'ChangeCipherSpec' MiTM Vulnerability (tcp/143)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2014-0224
Cvss Base: 5.8
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:P/I:P/A:N
Description:
Page 48 of 120
Scan Date: 2017-01-17
The OpenSSL s ervice on the remote hos t is vulnerable to a man-in-the-middle (MiTM) attack, bas ed on its res pons e to
two cons ecutive 'ChangeCipherSpec' mes s ages during the incorrect phas e of an SSL/TLS hands hake.
This flaw could allow a MiTM attacker to decrypt or forge SSL mes s ages by telling the s ervice to begin encrypted
communications before key material has been exchanged, which caus es predictable keys to be us ed to s ecure future
traffic.
Solution:
OpenSSL 0.9.8 SSL/TLS us ers (client and/or s erver) s hould upgrade to 0.9.8za. OpenSSL 1.0.0 SSL/TLS us ers (client and/or
s erver) s hould upgrade to 1.0.0m. OpenSSL 1.0.1 SSL/TLS us ers (client and/or s erver) s hould upgrade to 1.0.1h.
Result:
The rem ote service accepted an SSL C hangeC ipherSpec m essage at an incorrect point in the handshake
leading to weak keys being used, and then attem pted to decrypt an SSL record using those weak keys.This
check detects unpatched O penSSL 1.0.1, 1.0.0, and 0.9.8 services. O nly 1.0.1 has been shown to be exploitable;
however, O penSSL 1.0.0 and 0.9.8 have received sim ilar patches and users of these versions have been
advised to upgrade as a precaution.
References:
http://www.Indus Guard.org/u?d5709faa
https ://www.imperialviolet.org/2014/06/05/earlyccs .html
https ://www.opens s l.org/news /s ecadv_20140605.txt
Alert ID: 84576 Found on: 2017-01-17 Severity: Medium
SSL/TLS Protocol Initialization Vector Implementation Information Disclosure Vulnerability (tcp/143)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2011-3389
Cvss Base: 4.3
Cvss Score: 4.3
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N
PCI Compliance: Fail
Description:
A vulnerability exis ts in SSL 3.0 and TLS 1.0 that could allow information dis clos ure if an attacker intercepts encrypted
traffic s erved from an affected s ys tem.
TLS 1.1, TLS 1.2, and all cipher s uites that do not us e CBC mode are not affected.
This s cript tries to es tablis h an SSL/TLS remote connection us ing an affected SSL vers ion and cipher s uite, and then
s olicits return data.
If returned application data is not fragmented with an empty or one-byte record, it is likely vulnerable.
OpenSSL us es empty fragments as a countermeas ure unles s the 'SSL_OP_DONT_INSERT_EMPTY_FRAGMENTS' option is
s pecified when OpenSSL is initialized.
Micros oft implemented one-byte fragments as a countermeas ure, and the s etting can be controlled via the regis try key
HKEY_LOCAL_MACHINE\Sys tem\CurrentControlSet\Control\SecurityProviders \SCHANNEL\SendExtraRecord.
Therefore, if multiple applications us e the s ame SSL/TLS implementation, s ome may be vulnerable while others may not,
depending on whether or not a countermeas ure has been enabled.
Note that this s cript detects the vulnerability in the SSLv3/TLSv1 protocol implemented in the s erver. It does not detect
the BEAST attack where it exploits the vulnerability at HTTPS client-s ide (i.e., Internet brows er). The detection at s erver-
s ide does not neces s arily mean your s erver is vulnerable to the BEAST attack becaus e the attack exploits the
vulnerability at client-s ide, and both SSL/TLS clients and s ervers can independently employ the s plit record
Page 49 of 120
Scan Date: 2017-01-17
countermeas ure.
Solution:
Configure SSL/TLS s ervers to only us e TLS 1.1 or TLS 1.2 if s upported.
Configure SSL/TLS s ervers to only s upport cipher s uites that do not us e block ciphers . Apply patches if available.
Note that additional configuration may be required after the ins tallation of the MS12-006 s ecurity update in order to
enable the s plit-record countermeas ure. See http://s upport.micros oft.com/kb/2643584 for details .
Result:
Negotiated cipher suite: AES256-SHA|TLSv1|Kx=RSA|Au=RSA|Enc=AES-C BC (256)|Mac=SHA1
References:
http://www.opens s l.org/~bodo/tls -cbc.txt
http://vnhacker.blogs pot.com/2011/09/beas t.html
http://technet.micros oft.com/en-us /s ecurity/bulletin/ms 12-006
http://s upport.micros oft.com/kb/2643584
http://blogs .ms dn.com/b/kaus hal/archive/2012/01/21/fixing-the-beas t.as px
Alert ID: 84579 Found on: 2017-01-17 Severity: Medium
SSL Certificate Cannot Be Trusted (tcp/143)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 6.4
Cvss Score: 6.4
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:N
PCI Compliance: Fail
Description:
The s erver's X.509 certificate does not have a s ignature from a known public certificate authority. This s ituation can
occur in three different ways , each of which res ults in a break in the chain below which certificates cannot be trus ted.
Firs t, the top of the certificate chain s ent by the s erver might not be des cended from a known public certificate authority.
This can occur either when the top of the chain is an unrecognized, s elf-s igned certificate, or when intermediate
certificates are mis s ing that would connect the top of the certificate chain to a known public certificate authority.
Second, the certificate chain may contain a certificate that is not valid at the time of the s can. This can occur either when
the s can occurs before one of the certificate's 'notBefore' dates , or after one of the certificate's 'notAfter' dates .
Third, the certificate chain may contain a s ignature that either didn't match the certificate's information, or was not
pos s ible to verify. Bad s ignatures can be fixed by getting the certificate with the bad s ignature to be re-s igned by its
is s uer. Signatures that could not be verified are the res ult of the certificate's is s uer us ing a s igning algorithm that
Indus Guard either does not s upport or does not recognize.
If the remote hos t is a public hos t in production, any break in the chain nullifies the us e of SSL as anyone could es tablis h
a man in the middle attack agains t the remote hos t.
Solution:
Purchas e or generate a proper certificate for this s ervice.
Result:
The following certificate was part of the certificate chainsent by the rem ote host, but it has expired :|-Subject :
C =US/ST=Virginia/L=Herndon/O =Parallels/O U=Parallels Panel/C N=Parallels Panel/E=info@ parallels.com |-Not
After : Nov 09 10:32:06 2013 GMTThe following certificate was at the top of the certificatechain sent by the rem ote
host, but it is signed by an unknowncertificate authority :|-Subject :
Page 50 of 120
Scan Date: 2017-01-17
C =US/ST=Virginia/L=Herndon/O =Parallels/O U=Parallels Panel/C N=Parallels Panel/E=info@ parallels.com |-Issuer :
C =US/ST=Virginia/L=Herndon/O =Parallels/O U=Parallels Panel/C N=Parallels Panel/E=info@ parallels.com
Alert ID: 84580 Found on: 2017-01-17 Severity: Medium
SSL Self-Signed Certificate (tcp/143)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 6.4
Cvss Score: 6.4
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:N
PCI Compliance: Fail
Description:
The X.509 certificate chain for this s ervice is not s igned by a recognized certificate authority. If the remote hos t is a
public hos t in production, this nullifies the us e of SSL as anyone could es tablis h a man in the middle attack agains t the
remote hos t.
Note that this check does not check for certificate chains that end in a certificate that is not s elf-s igned, but is s igned by
an unrecognized certificate authority.
Solution:
Purchas e or generate a proper certificate for this s ervice.
Result:
The following certificate was found at the top of the certificatechain sent by the rem ote host, but is self-signed and
was notfound in the list of known certificate authorities :|-Subject :
C =US/ST=Virginia/L=Herndon/O =Parallels/O U=Parallels Panel/C N=Parallels Panel/E=info@ parallels.com
Alert ID: 84582 Found on: 2017-01-17 Severity: Medium
SSL Certificate Expiry (tcp/143)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 5.0
Cvss Score: 5.0
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:N/I:P/A:N
PCI Compliance: Fail
Description:
This s cript checks expiry dates of certificates as s ociated with SSL- enabled s ervices on the target and reports whether
any have already expired.
Solution:
Purchas e or generate a new SSL certificate to replace the exis ting one.
Result:
The SSL certificate has already expired : Subject : C =US, ST=Virginia, L=Herndon, O =Parallels, O U=Parallels
Panel, C N=Parallels Panel, em ailAddress=info@ parallels.com Issuer : C =US, ST=Virginia, L=Herndon,
O =Parallels, O U=Parallels Panel, C N=Parallels Panel, em ailAddress=info@ parallels.com Not valid before : Nov 9
10:32:06 2012 GMT Not valid after : Nov 9 10:32:06 2013 GMT
Alert ID: 84586 Found on: 2017-01-17 Severity: Medium
SSL Certificate with Wrong Hostname (tcp/110)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 5.0
Cvss Score: 5.0
Page 51 of 120
Scan Date: 2017-01-17
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:N/I:P/A:N
PCI Compliance: Fail
Description:
The commonName (CN) of the SSL certificate pres ented on this s ervice is for a different machine.
Solution:
Purchas e or generate a proper certificate for this s ervice.
Result:
The identity known by IndusGuard is : rs202995.rs.hosteurope.deThe C om m on Nam e in the certificate is :
Parallels Panel
Alert ID: 84588 Found on: 2017-01-17 Severity: Medium
SSL Medium Strength Cipher Suites Supported (tcp/110)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 4.3
Cvss Score: 4.3
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N
PCI Compliance: Fail
Description:
The remote hos t s upports the us e of SSL ciphers that offer medium s trength encryption, which we currently regard as
thos e with key lengths at leas t 56 bits and les s than 112 bits .
Note: This is cons iderably eas ier to exploit if the attacker is on the s ame phys ical network.
Solution:
Reconfigure the affected application if pos s ible to avoid us e of medium s trength ciphers .
Result:
Here is the list of m edium strength SSL ciphers supported by the rem ote server : Medium Strength C iphers (> 64-
bit and < 112-bit key) TLSv1 DES-C BC 3-SHA Kx=RSA Au=RSA Enc=3DES-C BC (168) Mac=SHA1 The fields above
are : {O penSSL ciphernam e} Kx={key exchange} Au={authentication} Enc={sym m etric encryption m ethod}
Mac={m essage authentication code} {export flag}
Alert ID: 84590 Found on: 2017-01-17 Severity: Medium
SSL Weak Cipher Suites Supported (tcp/110)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 4.3
Cvss Score: 4.3
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N
PCI Compliance: Fail
Description:
The remote hos t s upports the us e of SSL ciphers that offer either weak encryption or no encryption at all.
Note: This is cons iderably eas ier to exploit if the attacker is on the s ame phys ical network.
Solution:
Reconfigure the affected application if pos s ible to avoid us e of weak ciphers .
Result:
Here is the list of weak SSL ciphers supported by the rem ote server : Low Strength C iphers (<= 64-bit key) TLSv1
EXP-DES-C BC -SHA Kx=RSA(512) Au=RSA Enc=DES-C BC (40) Mac=SHA1 export EXP-RC 2-C BC -MD5 Kx=RSA(512)
Page 52 of 120
Scan Date: 2017-01-17
Au=RSA Enc=RC 2-C BC (40) Mac=MD5 export EXP-RC 4-MD5 Kx=RSA(512) Au=RSA Enc=RC 4(40) Mac=MD5 export
DES-C BC -SHA Kx=RSA Au=RSA Enc=DES-C BC (56) Mac=SHA1 The fields above are : {O penSSL ciphernam e}
Kx={key exchange} Au={authentication} Enc={sym m etric encryption m ethod} Mac={m essage authentication
code} {export flag}
References:
http://www.opens s l.org/docs /apps /ciphers .html
Alert ID: 84591 Found on: 2017-01-17 Severity: Medium
SSL/TLS EXPORT_RSA <= 512-bit Cipher Suites Supported (FREAK) (tcp/110)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 5.0
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:N/I:P/A:N
Description:
The remote hos t s upports EXPORT_RSA cipher s uites with keys les s than or equal to 512 bits . An attacker can factor a
512-bit RSA modulus in a s hort amount of time.
A man-in-the middle attacker may be able to downgrade the s es s ion to us e EXPORT_RSA cipher s uites (e.g. CVE-2015-
0204). Thus , it is recommended to remove s upport for weak cipher s uites .
Solution:
Reconfigure the s ervice to remove s upport for EXPORT_RSA cipher s uites .
Result:
EXPO RT_RSA cipher suites supported by the rem ote server : Low Strength C iphers (<= 64-bit key) TLSv1 EXP-DES-
C BC -SHA Kx=RSA(512) Au=RSA Enc=DES-C BC (40) Mac=SHA1 export EXP-RC 2-C BC -MD5 Kx=RSA(512) Au=RSA
Enc=RC 2-C BC (40) Mac=MD5 export EXP-RC 4-MD5 Kx=RSA(512) Au=RSA Enc=RC 4(40) Mac=MD5 export The
fields above are : {O penSSL ciphernam e} Kx={key exchange} Au={authentication} Enc={sym m etric
encryption m ethod} Mac={m essage authentication code} {export flag}
References:
https ://www.s macktls .com/#freak
https ://www.opens s l.org/news /s ecadv_20150108.txt
http://www.Indus Guard.org/u?b78da2c4
Alert ID: 84593 Found on: 2017-01-17 Severity: Medium
OpenSSL 'ChangeCipherSpec' MiTM Vulnerability (tcp/110)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2014-0224
Cvss Base: 5.8
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:P/I:P/A:N
Description:
The OpenSSL s ervice on the remote hos t is vulnerable to a man-in-the-middle (MiTM) attack, bas ed on its res pons e to
two cons ecutive 'ChangeCipherSpec' mes s ages during the incorrect phas e of an SSL/TLS hands hake.
This flaw could allow a MiTM attacker to decrypt or forge SSL mes s ages by telling the s ervice to begin encrypted
communications before key material has been exchanged, which caus es predictable keys to be us ed to s ecure future
traffic.
Solution:
Page 53 of 120
Scan Date: 2017-01-17
OpenSSL 0.9.8 SSL/TLS us ers (client and/or s erver) s hould upgrade to 0.9.8za. OpenSSL 1.0.0 SSL/TLS us ers (client and/or
s erver) s hould upgrade to 1.0.0m. OpenSSL 1.0.1 SSL/TLS us ers (client and/or s erver) s hould upgrade to 1.0.1h.
Result:
The rem ote service accepted an SSL C hangeC ipherSpec m essage at an incorrect point in the handshake
leading to weak keys being used, and then attem pted to decrypt an SSL record using those weak keys.This
check detects unpatched O penSSL 1.0.1, 1.0.0, and 0.9.8 services. O nly 1.0.1 has been shown to be exploitable;
however, O penSSL 1.0.0 and 0.9.8 have received sim ilar patches and users of these versions have been
advised to upgrade as a precaution.
References:
http://www.Indus Guard.org/u?d5709faa
https ://www.imperialviolet.org/2014/06/05/earlyccs .html
https ://www.opens s l.org/news /s ecadv_20140605.txt
Alert ID: 84594 Found on: 2017-01-17 Severity: Medium
SSL/TLS Protocol Initialization Vector Implementation Information Disclosure Vulnerability (tcp/110)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2011-3389
Cvss Base: 4.3
Cvss Score: 4.3
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N
PCI Compliance: Fail
Description:
A vulnerability exis ts in SSL 3.0 and TLS 1.0 that could allow information dis clos ure if an attacker intercepts encrypted
traffic s erved from an affected s ys tem.
TLS 1.1, TLS 1.2, and all cipher s uites that do not us e CBC mode are not affected.
This s cript tries to es tablis h an SSL/TLS remote connection us ing an affected SSL vers ion and cipher s uite, and then
s olicits return data.
If returned application data is not fragmented with an empty or one-byte record, it is likely vulnerable.
OpenSSL us es empty fragments as a countermeas ure unles s the 'SSL_OP_DONT_INSERT_EMPTY_FRAGMENTS' option is
s pecified when OpenSSL is initialized.
Micros oft implemented one-byte fragments as a countermeas ure, and the s etting can be controlled via the regis try key
HKEY_LOCAL_MACHINE\Sys tem\CurrentControlSet\Control\SecurityProviders \SCHANNEL\SendExtraRecord.
Therefore, if multiple applications us e the s ame SSL/TLS implementation, s ome may be vulnerable while others may not,
depending on whether or not a countermeas ure has been enabled.
Note that this s cript detects the vulnerability in the SSLv3/TLSv1 protocol implemented in the s erver. It does not detect
the BEAST attack where it exploits the vulnerability at HTTPS client-s ide (i.e., Internet brows er). The detection at s erver-
s ide does not neces s arily mean your s erver is vulnerable to the BEAST attack becaus e the attack exploits the
vulnerability at client-s ide, and both SSL/TLS clients and s ervers can independently employ the s plit record
countermeas ure.
Solution:
Configure SSL/TLS s ervers to only us e TLS 1.1 or TLS 1.2 if s upported.
Configure SSL/TLS s ervers to only s upport cipher s uites that do not us e block ciphers . Apply patches if available.
Note that additional configuration may be required after the ins tallation of the MS12-006 s ecurity update in order to
enable the s plit-record countermeas ure. See http://s upport.micros oft.com/kb/2643584 for details .
Page 54 of 120
Scan Date: 2017-01-17
Result:
Negotiated cipher suite: AES256-SHA|TLSv1|Kx=RSA|Au=RSA|Enc=AES-C BC (256)|Mac=SHA1
References:
http://www.opens s l.org/~bodo/tls -cbc.txt
http://vnhacker.blogs pot.com/2011/09/beas t.html
http://technet.micros oft.com/en-us /s ecurity/bulletin/ms 12-006
http://s upport.micros oft.com/kb/2643584
http://blogs .ms dn.com/b/kaus hal/archive/2012/01/21/fixing-the-beas t.as px
Alert ID: 84597 Found on: 2017-01-17 Severity: Medium
SSL Certificate Cannot Be Trusted (tcp/110)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 6.4
Cvss Score: 6.4
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:N
PCI Compliance: Fail
Description:
The s erver's X.509 certificate does not have a s ignature from a known public certificate authority. This s ituation can
occur in three different ways , each of which res ults in a break in the chain below which certificates cannot be trus ted.
Firs t, the top of the certificate chain s ent by the s erver might not be des cended from a known public certificate authority.
This can occur either when the top of the chain is an unrecognized, s elf-s igned certificate, or when intermediate
certificates are mis s ing that would connect the top of the certificate chain to a known public certificate authority.
Second, the certificate chain may contain a certificate that is not valid at the time of the s can. This can occur either when
the s can occurs before one of the certificate's 'notBefore' dates , or after one of the certificate's 'notAfter' dates .
Third, the certificate chain may contain a s ignature that either didn't match the certificate's information, or was not
pos s ible to verify. Bad s ignatures can be fixed by getting the certificate with the bad s ignature to be re-s igned by its
is s uer. Signatures that could not be verified are the res ult of the certificate's is s uer us ing a s igning algorithm that
Indus Guard either does not s upport or does not recognize.
If the remote hos t is a public hos t in production, any break in the chain nullifies the us e of SSL as anyone could es tablis h
a man in the middle attack agains t the remote hos t.
Solution:
Purchas e or generate a proper certificate for this s ervice.
Result:
The following certificate was part of the certificate chainsent by the rem ote host, but it has expired :|-Subject :
C =US/ST=Virginia/L=Herndon/O =Parallels/O U=Parallels Panel/C N=Parallels Panel/E=info@ parallels.com |-Not
After : Nov 09 10:32:06 2013 GMTThe following certificate was at the top of the certificatechain sent by the rem ote
host, but it is signed by an unknowncertificate authority :|-Subject :
C =US/ST=Virginia/L=Herndon/O =Parallels/O U=Parallels Panel/C N=Parallels Panel/E=info@ parallels.com |-Issuer :
C =US/ST=Virginia/L=Herndon/O =Parallels/O U=Parallels Panel/C N=Parallels Panel/E=info@ parallels.com
Alert ID: 84598 Found on: 2017-01-17 Severity: Medium
SSL Self-Signed Certificate (tcp/110)
Open Status: NEW First Found: 2017-01-17
Page 55 of 120
Scan Date: 2017-01-17
Cvss Base: 6.4
Cvss Score: 6.4
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:N
PCI Compliance: Fail
Description:
The X.509 certificate chain for this s ervice is not s igned by a recognized certificate authority. If the remote hos t is a
public hos t in production, this nullifies the us e of SSL as anyone could es tablis h a man in the middle attack agains t the
remote hos t.
Note that this check does not check for certificate chains that end in a certificate that is not s elf-s igned, but is s igned by
an unrecognized certificate authority.
Solution:
Purchas e or generate a proper certificate for this s ervice.
Result:
The following certificate was found at the top of the certificatechain sent by the rem ote host, but is self-signed and
was notfound in the list of known certificate authorities :|-Subject :
C =US/ST=Virginia/L=Herndon/O =Parallels/O U=Parallels Panel/C N=Parallels Panel/E=info@ parallels.com
Alert ID: 84600 Found on: 2017-01-17 Severity: Medium
SSL Certificate Expiry (tcp/110)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 5.0
Cvss Score: 5.0
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:N/I:P/A:N
PCI Compliance: Fail
Description:
This s cript checks expiry dates of certificates as s ociated with SSL- enabled s ervices on the target and reports whether
any have already expired.
Solution:
Purchas e or generate a new SSL certificate to replace the exis ting one.
Result:
The SSL certificate has already expired : Subject : C =US, ST=Virginia, L=Herndon, O =Parallels, O U=Parallels
Panel, C N=Parallels Panel, em ailAddress=info@ parallels.com Issuer : C =US, ST=Virginia, L=Herndon,
O =Parallels, O U=Parallels Panel, C N=Parallels Panel, em ailAddress=info@ parallels.com Not valid before : Nov 9
10:32:06 2012 GMT Not valid after : Nov 9 10:32:06 2013 GMT
Alert ID: 84605 Found on: 2017-01-17 Severity: Medium
Web Application SQL Backend Identification (tcp/80)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 5.0
Cvss Score: 5.0
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N
PCI Compliance: Fail
Description:
At leas t one web application hos ted on the remote web s erver is built on a SQL backend that Indus Guard was able to
identify by looking at error mes s ages .
Page 56 of 120
Scan Date: 2017-01-17
Leaking this kind of information may help an attacker fine-tune attacks agains t the application and its backend.
Solution:
Filter out error mes s ages .
Result:
The web application appears to be based on MySQ LThis inform ation was leaked by these URLs
:http://rs202995.rs.hosteurope.de/
References:
http://projects .webapps ec.org/Fingerprinting
Alert ID: 84611 Found on: 2017-01-17 Severity: Medium
CGI Generic Local File Inclusion (tcp/80)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 5.0
Cvss Score: 5.0
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N
PCI Compliance: Fail
Description:
The remote web s erver hos ts CGI s cripts that fail to adequately s anitize reques t s trings . By leveraging this is s ue, an
attacker may be able to include a local file and dis clos e its content.
Solution:
Res trict acces s to the vulnerable application. Contact the vendor for a patch or upgrade.
Result:
Using the GET HTTP m ethod, IndusGuard found that :+ The following resources m ay be vulnerable to local file
inclusion :+ The 'file' param eter of the /showim age.php C GI :/showim age.php?file=showim age.php-------- output --
------<?php// header("C ontent-Length: 1" /*. filesize($nam e)*/);if( isset($_GET["file"]) & & ! isset($_GET["size"]) ){--------
----------------C licking directly on these URLs should exhibit the issue :(you will probably need to read the HTML
source)http://rs202995.rs.hosteurope.de/showim age.php?file=showim age.php
References:
http://en.wikipedia.org/wiki/Remote_File_Inclus ion
Alert ID: 84613 Found on: 2017-01-17 Severity: Medium
CGI Generic Cross-Site Request Forgery Detection (potential) (tcp/80)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 6.4
Cvss Score: 6.4
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:N
PCI Compliance: Fail
Description:
The s pider found HTML forms on the remote web s erver. Some CGI s cripts do not appear to be protected by random
tokens , a common anti-cros s -s ite reques t forgery (CSRF) protection. The web application might be vulnerable to CSRF
attacks .
Note that :
- Indus Guard did not exploit the flaw,
- Indus Guard cannot identify s ens itive actions -- for example, on an online bank, cons ulting an account is les s s ens itive
than trans fering money.
Page 57 of 120
Scan Date: 2017-01-17
You will have to audit the s ource of the CGI s cripts and check if they are actually affected.
Solution:
Res trict acces s to the vulnerable application. Contact the vendor for a patch or upgrade.
Result:
The following C GIs are not protected by a random token
:/AJAX/index.php/.php/showxm l.php/showxm l.php/showxm l.php/showxm l.php/showxm l.php/.php/AJAX/index.php/
.php/showxm l.php/showxm l.php/showxm l.php/.php/.php/AJAX/index.php/.php/.php/.php/showxm l.php/.php/AJAX/i
ndex.php/showxm l.php/showxm l.php/showxm l.php/showxm l.php/showxm l.php/showxm l.php/.php/AJAX/index.ph
p/showxm l.php/showxm l.php/showxm l.php/showxm l.php/.php/.php/AJAX/index.php/showxm l.php/showxm l.php/s
howxm l.php/.php/showxm l.php/.php/AJAX/index.php/showxm l.php/showxm l.php/.php/showxm l.php/showxm l.ph
p/.php/AJAX/index.php/.php/showxm l.php/showxm l.php/.php/.php/AJAX/index.php/.php/showxm l.php/.php/showx
m l.php/.php/AJAX/index.php/.php/.php/showxm l.php/showxm l.php/.php/AJAX/index.php/.php/.php/.php/.php/AJAX/
index.php/showxm l.php/showxm l.php/showxm l.php/showxm l.php/showxm l.php/.php/AJAX/index.php/.php/showx
m l.php/.php/.php/AJAX/index.php/.php/.php/showxm l.php/.php/AJAX/index.php/showxm l.php/showxm l.php/showx
m l.php/showxm l.php/.php/AJAX/index.php/showxm l.php/showxm l.php/.php/.php/AJAX/index.php/showxm l.php/.p
hp/showxm l.php/.php/AJAX/index.php/showxm l.php/showxm l.php/.php/AJAX/index.php/.php/.php/cart.php/hpp/pa
ram s.php/secured/newuser.php/AJAX/.php/artists.php/listproducts.php/search.php/AJAX/index.php/.php/userinfo.p
hp/hpp//product.php/AJAX/index.php/showxm l.php/.php/AJAX/index.php/.php/showxm l.php/.php/AJAX/index.php/s
howxm l.php/.php/.php/AJAX/index.php/showxm l.php/showxm l.php/showxm l.php/.php/AJAX/index.php/.php/.php/.
php/AJAX/index.php/.php/showxm l.php/showxm l.php/.php/AJAX/index.php/.php/showxm l.php/showxm l.php/show
xm l.php/.php/AJAX/index.php/showxm l.php/.php/.php/.php/AJAX/index.php/showxm l.php/.php/showxm l.php/show
xm l.php/.php/AJAX/index.php/showxm l.php/showxm l.php/.php/showxm l.php/.php/AJAX/index.php/showxm l.php/s
howxm l.php/showxm l.php/.php/.php/AJAX/index.php/.php/showxm l.php/showxm l.php/showxm l.php/showxm l.ph
p/.php/AJAX/index.php/showxm l.php/.php/.php/showxm l.php/.php/AJAX/index.php/showxm l.php/.php/showxm l.ph
p/.php/.php/AJAX/index.php/showxm l.php/.php/showxm l.php/showxm l.php/showxm l.php/.php/AJAX/index.php/sh
owxm l.php/showxm l.php/.php/.php/.php/AJAX/index.php/.php/.php/showxm l.php/.php/.php/AJAX/index.php/.php/.
php/showxm l.php/showxm l.php/showxm l.php/.php/AJAX/index.php/.php/showxm l.php/.php/.php/.php/AJAX/index.
php/.php/showxm l.php/.php/showxm l.php/showxm l.php/.php/AJAX/index.php/.php/showxm l.php/showxm l.php/.p
hp/showxm l.php/.php
References:
http://en.wikipedia.org/wiki/Cros s -s ite_reques t_forgery
Alert ID: 84614 Found on: 2017-01-17 Severity: Medium
CGI Generic Cross-Site Scripting (extended patterns) (tcp/80)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 4.3
Cvss Score: 4.3
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:N/I:P/A:N
PCI Compliance: Fail
Description:
The remote web s erver hos ts one or more CGI s cripts that fail to adequately s anitize reques t s trings with malicious
JavaScript. By leveraging this is s ue, an attacker may be able to caus e arbitrary HTML and s cript code to be executed in a
us er's brows er within the s ecurity context of the affected s ite. Thes e XSS vulnerabilities are likely to be 'non-pers is tent'
or 'reflected'.
Solution:
Res trict acces s to the vulnerable application. Contact the vendor for a patch or upgrade.
Result:
Using the GET HTTP m ethod, IndusGuard found that :+ The following resources m ay be vulnerable to cross-site
scripting (extended patterns) :+ The 'pp' param eter of the /hpp/ C GI :/hpp/?pp=504% 20onerror="alert(504);--------
output --------<a href="?pp=12">check</a><br/><a href="param s.php?
p=valid& pp=504+onerror% 3D% 22alert% 28504% 29% 3B">link1</a><br/><a href="param s.php?
Page 58 of 120
Scan Date: 2017-01-17
p=valid& pp=504 onerror="alert(504);">link2</a><br/><form action="param s.php?p=valid& pp=504
onerror="alert(504);"><input type=subm it nam e=aaaa/></form ><br/><hr><a
href='http://blog.m indedsecurity.com /2009/05/client-side-http-p [...]------------------------C licking directly on these URLs
should exhibit the issue :(you will probably need to read the HTML source)http://rs202995.rs.hosteurope.de/hpp/?
pp=504% 20onerror="alert(504);
References:
http://en.wikipedia.org/wiki/Cros s _s ite_s cripting#Non-pers is tent
http://www.nes s us .org/u?9717ad85
http://projects .webapps ec.org/Cros s -Site+Scripting
Alert ID: 84615 Found on: 2017-01-17 Severity: Medium
CGI Generic Cross-Site Scripting (comprehensive test) (tcp/80)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 4.3
Cvss Score: 4.3
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:N/I:P/A:N
PCI Compliance: Fail
Description:
The remote web s erver hos ts CGI s cripts that fail to adequately s anitize reques t s trings of malicious JavaScript. By
leveraging this is s ue, an attacker may be able to caus e arbitrary HTML and s cript code to be executed in a us er's
brows er within the s ecurity context of the affected s ite. Thes e XSS are likely to be 'non-pers is tent' or 'reflected'.
Solution:
Res trict acces s to the vulnerable application. Contact the vendor for a patch or upgrade.
Result:
Using the GET HTTP m ethod, IndusGuard found that :+ The following resources m ay be vulnerable to cross-site
scripting (com prehensive test) :+ The 'pp' param eter of the /hpp/ C GI :/hpp/?
pp=<<<<<<<<<<foo"bar'204>>>>>-------- output --------<a href="?pp=12">check</a><br/><a
href="param s.php?
p=valid& pp=% 3C % 3C % 3C % 3C % 3C % 3C % 3C % 3C % 3C % 3C foo% 22bar% 27204% 3E% 3E% 3E% 3E% 3E">link1
</a><br/><a href="param s.php?p=valid& pp=<<<<<<<<<<foo"bar'204>>>>>">link2</a><br/><form
action="param s.php?p=valid& pp=<<<<<<<<<<foo"bar'204>>>>>"><input type=subm it
nam e=aaaa/></form ><br/><hr><a href='http://blog.m indedsecurity.com /2009/05/client-side-http-p [...]---------------
---------+ The 'file' param eter of the /showim age.php C GI :/showim age.php?
file=<<<<<<<<<<foo"bar'204>>>>>-------- output --------Warning: fopen(): Unable to access
<<<<<<<<<<foo"bar'204>>>>> in /hj/var/www/showim age.php on line 7Warning:
fopen(<<<<<<<<<<foo"bar'204>>>>>): failed to open stream : [...]------------------------+ The 'cat' param eter of the
/listproducts.php C GI :/listproducts.php?cat=<<<<<<<<<<foo"bar'204>>>>>-------- output --------<! --
InstanceBeginEditable nam e="content_rgn" --><div id="content">Error: You have an error in your SQ L syntax;
check the m anual that corresponds to your MySQ L server version for the right syntax to use near
'=<<<<<<<<<<foo"bar'204>>>>>' at line 1Warning: m ysql_fetch_array() expects param eter 1 to be resource,
b [...]</div>------------------------+ The 'artist' param eter of the /listproducts.php C GI :/listproducts.php?
artist=<<<<<<<<<<foo"bar'204>>>>>-------- output --------<! -- InstanceBeginEditable nam e="content_rgn" --
><div id="content">Error: You have an error in your SQ L syntax; check the m anual that corresponds to your
MySQ L server version for the right syntax to use near '=<<<<<<<<<<foo"bar'204>>>>>' at line 1Warning:
m ysql_fetch_array() expects param eter 1 to be resource, b [...]</div>------------------------+ The 'cat' param eter of the
/listproducts.php C GI :/listproducts.php?cat=<<<<<<<<<<foo"bar'204>>>>>& artist=1-------- output --------<! --
InstanceBeginEditable nam e="content_rgn" --><div id="content">Error: You have an error in your SQ L syntax;
check the m anual that corresponds to your MySQ L server version for the right syntax to use near
'=<<<<<<<<<<foo"bar'204>>>>>' at line 1Warning: m ysql_fetch_array() expects param eter 1 to be resource,
b [...]</div>------------------------+ The 'pp' param eter of the /hpp/param s.php C GI :/hpp/param s.php?
pp=<<<<<<<<<<foo"bar'204>>>>>-------- output --------<<<<<<<<<<foo"bar'204>>>>>------------------------+ The 'p'
param eter of the /hpp/param s.php C GI :/hpp/param s.php?p=<<<<<<<<<<foo"bar'204>>>>>-------- output --------
Page 59 of 120
Scan Date: 2017-01-17
<<<<<<<<<<foo"bar'204>>>>>------------------------+ The 'pp' param eter of the /hpp/param s.php C GI
:/hpp/param s.php?pp=<<<<<<<<<<foo"bar'204>>>>>& p=valid& aaaa/=-------- output --------valid<<
References:
http://en.wikipedia.org/wiki/Cros s _s ite_s cripting#Non-pers is tent
http://www.nes s us .org/u?9717ad85
http://projects .webapps ec.org/Cros s -Site+Scripting
Alert ID: 84616 Found on: 2017-01-17 Severity: Medium
CGI Generic Cookie Injection Scripting (tcp/80)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 4.3
Cvss Score: 4.3
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:N/I:P/A:N
PCI Compliance: Fail
Description:
The remote web s erver hos ts at leas t one CGI s cript that fails to adequately s anitize reques t s trings with malicious
JavaScript.
By leveraging this is s ue, an attacker may be able to inject arbitrary cookies . Depending on the s tructure of the web
application, it may be pos s ible to launch a 's es s ion fixation' attack us ing this mechanis m.
Pleas e note that :
- Indus Guard did not check if the s es s ion fixation attack is feas ible.
- This is not the only vector of s es s ion fixation.
Solution:
Res trict acces s to the vulnerable application. Contact the vendor for a patch or upgrade.
Result:
Using the GET HTTP m ethod, IndusGuard found that :+ The following resources m ay be vulnerable to cookie
m anipulation :+ The 'pp' param eter of the /hpp/ C GI :/hpp/?
pp=<script>docum ent.cookie="testbodp=9194;"</script>-------- output --------<a href="?
pp=12">check</a><br/><a href="param s.php?
p=valid& pp=% 3C script% 3Edocum ent.cookie% 3D% 22testbodp% 3D9194% 3B% 22% 3C % 2Fscript% 3E">link1</
a><br/><a href="param s.php?
p=valid& pp=<script>docum ent.cookie="testbodp=9194;"</script>">link2</a><br/><form
action="param s.php?p=valid& pp=<script>docum ent.cookie="testbodp=9194;"</script>"><input type=subm it
nam e=aaaa/></form ><br/><hr><a href='http://blog.m indedsecurity.com /2009/05/client-side-http-p [...]---------------
---------+ The 'cat' param eter of the /listproducts.php C GI :/listproducts.php?
cat=<script>docum ent.cookie="testbodp=9194;"</script>-------- output --------<! -- InstanceBeginEditable
nam e="content_rgn" --><div id="content">Error: You have an error in your SQ L syntax; check the m anual that
corresponds to your MySQ L server version for the right syntax to use near
'=<script>docum ent.cookie="testbodp=9194;"</script>' at line 1Warning: m ysql_fetch_array() expects
param eter 1 to be resource, b [...]</div>------------------------+ The 'artist' param eter of the /listproducts.php C GI
:/listproducts.php?artist=<script>docum ent.cookie="testbodp=9194;"</script>-------- output --------<! --
InstanceBeginEditable nam e="content_rgn" --><div id="content">Error: You have an error in your SQ L syntax;
check the m anual that corresponds to your MySQ L server version for the right syntax to use near
'=<script>docum ent.cookie="testbodp=9194;"</script>' at line 1Warning: m ysql_fetch_array() expects
param eter 1 to be resource, b [...]</div>------------------------+ The 'cat' param eter of the /listproducts.php C GI
:/listproducts.php?cat=<script>docum ent.cookie="testbodp=9194;"</script>& artist=1-------- output --------<! --
InstanceBeginEditable nam e="content_rgn" --><div id="content">Error: You have an error in your SQ L syntax;
Page 60 of 120
Scan Date: 2017-01-17
check the m anual that corresponds to your MySQ L server version for the right syntax to use near
'=<script>docum ent.cookie="testbodp=9194;"</script>' at line 1Warning: m ysql_fetch_array() expects
param eter 1 to be resource, b [...]</div>------------------------+ The 'pp' param eter of the /hpp/param s.php C GI
:/hpp/param s.php?pp=<script>docum ent.cookie="testbodp=9194;"</script>-------- output --------
<script>docum ent.cookie="testbodp=9194;"</script>------------------------+ The 'p' param eter of the /hpp/param s.php
C GI :/hpp/param s.php?p=<script>docum ent.cookie="testbodp=9194;"</script>-------- output --------
<script>docum ent.cookie="testbodp=9194;"</script>------------------------+ The 'pp' param eter of the
/hpp/param s.php C GI :/hpp/param s.php?
pp=<script>docum ent.cookie="testbodp=9194;"</script>& p=valid& aaaa/=-------- output --------
valid<script>docum ent.cookie="testbodp=9194;"</script>------------------------+ The 'p' param eter of the
/hpp/param s.php C GI :/hpp/param s.php?
pp=12& p=<script>docum ent.cookie="testbodp=9194;"</script>& aaaa/=-------- output --------
<script>docum ent.cookie="testbodp=9194;"</script>12------------------------
References:
http://en.wikipedia.org/wiki/Ses s ion_fixation
http://www.owas p.org/index.php/Ses s ion_Fixation
http://www.acros .s i/papers /s es s ion_fixation.pdf
http://projects .webapps ec.org/Ses s ion-Fixation
Alert ID: 84617 Found on: 2017-01-17 Severity: Medium
CGI Generic Cross-Site Scripting (quick test) (tcp/80)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 4.3
Cvss Score: 4.3
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:N/I:P/A:N
PCI Compliance: Fail
Description:
The remote web s erver hos ts CGI s cripts that fail to adequately s anitize reques t s trings with malicious JavaScript. By
leveraging this is s ue, an attacker may be able to caus e arbitrary HTML and s cript code to be executed in a us er's
brows er within the s ecurity context of the affected s ite.
Thes e XSS are likely to be 'non pers is tent' or 'reflected'.
Solution:
Res trict acces s to the vulnerable application. Contact the vendor for a patch or upgrade.
Result:
Using the GET HTTP m ethod, IndusGuard found that :+ The following resources m ay be vulnerable to cross-site
scripting (quick test) :+ The 'pp' param eter of the /hpp/ C GI :/hpp/?pp=<IMG% 20SRC ="javascript:alert(104);">------
-- output --------<a href="?pp=12">check</a><br/><a href="param s.php?
p=valid& pp=% 3C IMG+SRC % 3D% 22javascript% 3Aalert% 28104% 29% 3B% 22% 3E">link1</a><br/><a
href="param s.php?p=valid& pp=<IMG SRC ="javascript:alert(104);">">link2</a><br/><form
action="param s.php?p=valid& pp=<IMG SRC ="javascript:alert(104);">"><input type=subm it
nam e=aaaa/></form ><br/><hr><a href='http://blog.m indedsecurity.com /2009/05/client-side-http-p [...]---------------
---------+ The 'cat' param eter of the /listproducts.php C GI :/listproducts.php?
cat=<IMG% 20SRC ="javascript:alert(104);">-------- output --------<! -- InstanceBeginEditable nam e="content_rgn" --
><div id="content">Error: You have an error in your SQ L syntax; check the m anual that corresponds to your
MySQ L server version for the right syntax to use near '=<IMG SRC ="javascript:alert(104);">' at line 1Warning:
m ysql_fetch_array() expects param eter 1 to be resource, b [...]</div>------------------------+ The 'artist' param eter of the
/listproducts.php C GI :/listproducts.php?artist=<IMG% 20SRC ="javascript:alert(104);">-------- output --------<! --
InstanceBeginEditable nam e="content_rgn" --><div id="content">Error: You have an error in your SQ L syntax;
check the m anual that corresponds to your MySQ L server version for the right syntax to use near '=<IMG
SRC ="javascript:alert(104);">' at line 1Warning: m ysql_fetch_array() expects param eter 1 to be resource, b
[...]</div>------------------------+ The 'cat' param eter of the /listproducts.php C GI :/listproducts.php?
Page 61 of 120
Scan Date: 2017-01-17
cat=<IMG% 20SRC ="javascript:alert(104);">& artist=1-------- output --------<! -- InstanceBeginEditable
nam e="content_rgn" --><div id="content">Error: You have an error in your SQ L syntax; check the m anual that
corresponds to your MySQ L server version for the right syntax to use near '=<IMG SRC ="javascript:alert(104);">'
at line 1Warning: m ysql_fetch_array() expects param eter 1 to be resource, b [...]</div>------------------------+ The 'pp'
param eter of the /hpp/param s.php C GI :/hpp/param s.php?pp=<IMG% 20SRC ="javascript:alert(104);">--------
output --------<IMG SRC ="javascript:alert(104);">------------------------+ The 'p' param eter of the /hpp/param s.php C GI
:/hpp/param s.php?p=<IMG% 20SRC ="javascript:alert(104);">-------- output --------<IMG
SRC ="javascript:alert(104);">------------------------+ The 'pp' param eter of the /hpp/param s.php C GI :/hpp/param s.php?
pp=<IMG% 20SRC ="javascript:alert(104);">& p=valid& aaaa/=-------- output --------valid<IMG
SRC ="javascript:alert(104);">------------------------+ The 'p' param eter of the /hpp/param s.php C GI :/hpp/param s.php?
pp=12& p=<IMG% 20SRC ="javascript:alert(104);">& aaaa/=-------- output --------<IMG
SRC ="javascript:alert(104);">12------------------------C licking directly on these URLs should exhibit the issue :(you will
probably need to read the HTML source)http://rs202995.rs.hosteurope.de/hpp/?
pp=<IMG% 20SRC ="javascript:alert(104);">
References:
http://en.wikipedia.org/wiki/Cros s _s ite_s cripting#Non-pers is tent
http://www.nes s us .org/u?9717ad85
http://projects .webapps ec.org/Cros s -Site+Scripting
Alert ID: 84618 Found on: 2017-01-17 Severity: Medium
Web Application Vulnerable to Clickjacking (tcp/80)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 4.3
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:N/I:P/A:N
Description:
The remote web s erver does not s et an X-Frame-Options res pons e header in all content res pons es .
X-Frame-Options has been propos ed by Micros oft as a way to mitigate clickjacking attacks and is currently s upported by
all major brows er vendors .
Solution:
Return the X-Frame-Options HTTP header with the page's res pons e.
This prevents the page's content from being rendered by another s ite when us ing the frame or iframe HTML tags .
Result:
The following pages do not use a clickjacking m itigation response header and contain a clickable event : -
http://rs202995.rs.hosteurope.de/ - http://rs202995.rs.hosteurope.de/AJAX/ -
http://rs202995.rs.hosteurope.de/AJAX/index.php - http://rs202995.rs.hosteurope.de/AJAX/index.php/.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/ -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/.php?id=/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/.php?id=/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/GET -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/PO ST -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/infotitle -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/showxm l.php -
Page 62 of 120
Scan Date: 2017-01-17
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/showxm l.php/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/showxm l.php/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/styles.css -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/showxm l.php/.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/showxm l.php/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/showxm l.php/.php?id=/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/showxm l.php/.php?id=/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/showxm l.php/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/showxm l.php/showxm l.php/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/showxm l.php/showxm l.php/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/ -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/ -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/.php?id=/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/.php?id=/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/GET -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/PO ST -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/infotitle -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/showxm l.php/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/showxm l.php/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/styles.css -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php?id=/ -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php?id=/.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php?id=/.php/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php?id=/.php/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php?id=/.php?id= - http://rs
References:
http://en.wikipedia.org/wiki/Clickjacking
http://www.Indus Guard.org/u?1bced8d9
https ://www.owas p.org/index.php/Clickjacking_Defens e_Cheat_Sheet
Alert ID: 84626 Found on: 2017-01-17 Severity: Medium
nginx < 1.6.2 / 1.7.5 SSL Session Reuse (tcp/80)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 4.0
Cvss Vector: CVSS2#AV:N/AC:H/Au:N/C:P/I:P/A:N
Description:
According to the s elf-reported vers ion in the s erver res pons e header, the vers ion of nginx ins talled on the remote hos t is
0.5.6 or higher, 1.6.x prior to 1.6.2, or 1.7.x prior to 1.7.5. It is , therefore, affected by an SSL s es s ion or TLS s es s ion ticket
key handling error. A flaw exis ts in the file 'event/ngx_event_opens s l.c' that could allow a remote attacker to obtain
s ens itive information or to take control of a s es s ion.
Note that this is s ue only affects s ervers having multiple 's erver{}' configurations s haring the s ame values for
's s l_s es s ion_cache' or 's s l_s es s ion_ticket_key'.
Solution:
Upgrade to nginx 1.6.2 / 1.7.5 or later.
Page 63 of 120
Scan Date: 2017-01-17
Result:
Version source : nginx/1.4.1 Installed version : 1.4.1 Fixed version : 1.6.2 / 1.7.5
References:
http://bh.ht.vc/vhos t_confus ion.pdf
http://nginx.org/en/s ecurity_advis ories .html
http://mailman.nginx.org/pipermail/nginx-announce/2014/000146.html
http://mailman.nginx.org/pipermail/nginx-announce/2014/000145.html
http://mailman.nginx.org/pipermail/nginx-announce/2014/000147.html
http://nginx.org/en/CHANGES
http://nginx.org/en/CHANGES-1.6
Alert ID: 84628 Found on: 2017-01-17 Severity: Medium
CGI Generic HTML Injections (quick test) (tcp/80)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 4.3
Cvss Score: 4.3
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:N/I:P/A:N
PCI Compliance: Fail
Description:
The remote web s erver hos ts CGI s cripts that fail to adequately s anitize reques t s trings with malicious JavaScript. By
leveraging this is s ue, an attacker may be able to caus e arbitrary HTML to be executed in a us er's brows er within the
s ecurity context of the affected s ite.
The remote web s erver may be vulnerable to IFRAME injections or cros s -s ite s cripting attacks :
- IFRAME injections allow 'virtual defacement' that might s care or anger gullible us ers . Such injections are s ometimes
implemented for 'phis hing' attacks .
- XSS are extens ively tes ted by four other s cripts .
- Some applications (e.g. web forums ) authorize a s ubs et of HTML without any ill effect. In this cas e, ignore this warning.
Solution:
Either res trict acces s to the vulnerable application or contact the vendor for an update.
Result:
Using the GET HTTP m ethod, IndusGuard found that :+ The following resources m ay be vulnerable to HTML
injection :+ The 'pp' param eter of the /hpp/ C GI :/hpp/?pp=<"qbvxty% 0A>-------- output --------<a href="?
pp=12">check</a><br/><a href="param s.php?p=valid& pp=% 3C % 22qbvxty% 0A% 3E">link1</a><br/><a
href="param s.php?p=valid& pp=<"qbvxty>">link2</a><br/><form action="param s.php?
p=valid& pp=<"qbvxty>"><input type=subm it nam e=aaaa/></form ><br/>------------------------+ The 'p' param eter of
the /hpp/param s.php C GI :/hpp/param s.php?p=<"qbvxty% 0A>-------- output --------<"qbvxty>------------------------+ The
'pp' param eter of the /hpp/param s.php C GI :/hpp/param s.php?pp=<"qbvxty% 0A>-------- output --------<"qbvxty>------
------------------+ The 'p' param eter of the /hpp/param s.php C GI :/hpp/param s.php?p=<"qbvxty% 0A>& pp=12--------
output --------<"qbvxty>12------------------------+ The 'pp' param eter of the /hpp/param s.php C GI :/hpp/param s.php?
p=valid& pp=<"qbvxty% 0A>-------- output --------valid<"qbvxty>------------------------+ The 'artist' param eter of the
/listproducts.php C GI :/listproducts.php?artist=<"qbvxty% 0A>-------- output --------<! -- InstanceBeginEditable
nam e="content_rgn" --><div id="content">Error: You have an error in your SQ L syntax; check the m anual that
corresponds to your MySQ L server version for the right syntax to use near '=<"qbvxty>' at line 1Warning:
Page 64 of 120
Scan Date: 2017-01-17
m ysql_fetch_array() expects param eter 1 to be resource, b [...]------------------------+ The 'cat' param eter of the
/listproducts.php C GI :/listproducts.php?cat=<"qbvxty% 0A>-------- output --------<! -- InstanceBeginEditable
nam e="content_rgn" --><div id="content">Error: You have an error in your SQ L syntax; check the m anual that
corresponds to your MySQ L server version for the right syntax to use near '=<"qbvxty>' at line 1Warning:
m ysql_fetch_array() expects param eter 1 to be resource, b [...]------------------------/listproducts.php?
artist=1& cat=<"qbvxty% 0A>-------- output --------<! -- InstanceBeginEditable nam e="content_rgn" --><div
id="content">Error: You have an error in your SQ L syntax; check the m anual that corresponds to your MySQ L
server version for the right syntax to use near '=<"qbvxty>' at line 1Warning: m ysql_fetch_array() expects
param eter 1 to be resource, b [...]------------------------C licking directly on these URLs should exhibit the issue :(you will
probably need to read the HTML source)http://rs202995.rs.hosteurope.de/hpp/?
pp=<"qbvxty% 0A>http://rs202995.rs.hosteurope.de/hpp/param s.php?
p=<"qbvxty% 0A>http://rs202995.rs.hosteurope.de/hpp/param s.php?
pp=<"qbvxty% 0A>http://rs202995.rs.hosteurope.de/hpp/param s.php?
p=<"qbvxty% 0A>& pp=12http://rs202995.rs.hosteurope.de/hpp/param s.php?
p=valid& pp=<"qbvxty% 0A>http://rs202995.rs.hosteurope.de/listproducts.php?
artist=<"qbvxty% 0A>http://rs202995.rs.hosteurope.de/listproducts.php?
cat=<"qbvxty% 0A>http://rs202995.rs.hosteurope.de/listproducts.php?artist=1& cat=<"qbvxty% 0A>
References:
http://www.nes s us .org/u?f8fdd645
Alert ID: 84631 Found on: 2017-01-17 Severity: Medium
PHP < 5.2.5 Multiple Vulnerabilities (tcp/80)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2007-3996,CVE-2007-
4782,CVE-2007-4783,CVE-2007
Cvss Base: 4.4
Cvss Score: 4.4
Cvss Vector: CVSS2#AV:L/AC:M/Au:N/C:P/I:P/A:P
PCI Compliance: Fail
Description:
According to its banner, the vers ion of PHP ins talled on the remote hos t is older than 5.2.5. Such vers ions may be
affected by various is s ues , including but not limited to s everal buffer overflows .
Solution:
Upgrade to PHP vers ion 5.2.5 or later.
Result:
Version source : http://rs202995.rs.hosteurope.de/secured/phpinfo.php Installed version : 5.1.6 Fixed version :
5.2.5
References:
http://www.php.net/releas es /5_2_5.php
Alert ID: 84632 Found on: 2017-01-17 Severity: Medium
PHP Foreign Function Interface Arbitrary DLL Loading safe_mode Restriction Bypass (tcp/80)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2007-4528
Cvss Base: 4.3
Cvss Score: 4.3
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:N/I:P/A:N
PCI Compliance: Fail
Page 65 of 120
Scan Date: 2017-01-17
Description:
According to its banner, the vers ion of PHP ins talled on the remote hos t is affected by a s ecurity bypas s vulnerability. The
Foreign Function Interface (ffi) extens ion does not follow s afe_mode res trictions , which allows context-dependent
attackers to execute arbitrary code by loading an arbitrary DLL and calling a function.
Solution:
There is no known s olution at this time.
Result:
Version source : X-Powered-By: PHP/5.3.10-1~lucid+2uwsgi2 Installed version : 5.3.10-1~lucid+2uwsgi2
References:
http://pecl.php.net/package-info.php?package=ffi
Alert ID: 84633 Found on: 2017-01-17 Severity: Medium
PHP ip2long Function String Validation Weakness (tcp/80)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2006-4023
Cvss Base: 5.0
Cvss Score: 5.0
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N
PCI Compliance: Fail
Description:
According to its banner, the 'ip2long()' function in the vers ion of PHP ins talled on the remote hos t may incorrectly validate
an arbitrary s tring and return a valid network IP addres s .
Solution:
There is no known s olution at this time.
Result:
Version source : X-Powered-By: PHP/5.3.10-1~lucid+2uwsgi2 Installed version : 5.3.10-1~lucid+2uwsgi2
References:
http://retrogod.altervis ta.org/php_ip2long.htm
http://www.s ecurityfocus .com/archive/1/441529/100/100/threaded
Alert ID: 84635 Found on: 2017-01-17 Severity: Medium
PHP 5.3.x < 5.3.28 Multiple OpenSSL Vulnerabilities (tcp/80)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2013-4073,CVE-2013-6420
Cvss Base: 6.8
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:P/I:P/A:P
Description:
According to its banner, the vers ion of PHP ins talled on the remote hos t is 5.3.x prior to 5.3.28. It is , therefore, potentially
affected by the following vulnerabilities :
- A flaw exis ts in the PHP OpenSSL extens ion's hos tname identity check when handling certificates that contain
hos tnames with NULL bytes . An attacker could potentially exploit this flaw to conduct man-in-the-middle attacks to s poof
SSL s ervers . Note that to exploit this is s ue, an attacker would need to obtain a carefully-crafted certificate s igned by an
authority that the client trus ts . (CVE-2013-4073)
Page 66 of 120
Scan Date: 2017-01-17
- A memory corruption flaw exis ts in the way the opens s l_x509_pars e() function of the PHP OpenSSL extens ion pars ed
X.509 certificates . A remote attacker could us e this flaw to provide a malicious , s elf-s igned certificate or a certificate
s igned by a trus ted authority to a PHP application us ing the aforementioned function. This could caus e the application to
cras h or pos s ibly allow the attacker to execute arbitrary code with the privileges of the us er running the PHP interpreter.
(CVE-2013-6420)
Note that this check does not attempt to exploit thes e vulnerabilities , but ins tead relies only on PHP's s elf-reported
vers ion number.
Solution:
Upgrade to PHP vers ion 5.3.28 or later.
Result:
Version source : X-Powered-By: PHP/5.3.10-1~lucid+2uwsgi2 Installed version : 5.3.10-1~lucid+2uwsgi2 Fixed
version : 5.3.28
References:
http://s eclis ts .org/fulldis clos ure/2013/Dec/96
https ://bugzilla.redhat.com/s how_bug.cgi?id=1036830
http://www.Indus Guard.org/u?b6ec9ef9
http://www.php.net/ChangeLog-5.php#5.3.28
Alert ID: 84637 Found on: 2017-01-17 Severity: Medium
PHP 5.3.x < 5.3.21 cURL X.509 Certificate Domain Name Matching MiTM Weakness (tcp/80)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 4.3
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:N/I:P/A:N
Description:
According to its banner, the vers ion of PHP 5.3.x ins talled on the remote hos t is prior to 5.3.21. It is , therefore, potentially
affected by a weaknes s in the cURL extens ion that can allow SSL s poofing and man-in-the-middle attacks .
When attempting to validate a certificate, the cURL library (libcurl) fails to verify that a s erver hos tname matches a
domain name in an X.509 certificate's 'Subject Common Name' (CN) or 'SubjectAltName'.
Note that this check does not attempt to verify whether the PHP ins tall has been built with the cURL extention, but ins tead
relies only on PHP's s elf-reported vers ion number.
Solution:
Upgrade to PHP vers ion 5.3.21 or later.
Result:
Version source : X-Powered-By: PHP/5.3.10-1~lucid+2uwsgi2 Installed version : 5.3.10-1~lucid+2uwsgi2 Fixed
version : 5.3.21
References:
http://www.php.net/ChangeLog-5.php#5.3.21
https ://bugs .php.net/bug.php?id=63352
https ://bugs .php.net/bug.php?id=63795
Alert ID: 84640 Found on: 2017-01-17 Severity: Medium
Page 67 of 120
Scan Date: 2017-01-17
PHP < 5.2.10 Multiple Vulnerabilities (tcp/80)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2009-2687
Cvss Base: 5.1
Cvss Score: 5.1
Cvss Vector: CVSS2#AV:N/AC:H/Au:N/C:P/I:P/A:P
PCI Compliance: Fail
Description:
According to its banner, the vers ion of PHP ins talled on the remote hos t is older than 5.2.10. Such vers ions are reportedly
affected by multiple vulnerabilities :
- Sufficient checks are not performed on fields res erved for offs ets in function 'exif_read_data()'. Succes s ful exploitation
of this is s ue could res ult in a denial of s ervice condition. (bug 48378)
- Provided 's afe_mode_exec_dir' is not s et (not s et by default), it may be pos s ible to bypas s 's afe_mode' res trictions by
preceding a backs las h in functions s uch as 'exec()', 's ys tem()', 's hell_exec()', 'pas s thru()' and 'popen()' on a s ys tem
running PHP on Windows . (bug 45997)
Solution:
Upgrade to PHP vers ion 5.2.10 or later.
Result:
Version source : http://rs202995.rs.hosteurope.de/secured/phpinfo.php Installed version : 5.1.6 Fixed version :
5.2.10
References:
http://bugs .php.net/bug.php?id=45997
http://bugs .php.net/bug.php?id=48378
http://www.php.net/releas es /5_2_10.php
http://www.php.net/ChangeLog-5.php#5.2.10
Alert ID: 84643 Found on: 2017-01-17 Severity: Medium
PHP < 5.3.2 / 5.2.13 Multiple Vulnerabilities (tcp/80)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2010-1128,CVE-2010-
1129,CVE-2010-1130
Cvss Base: 6.4
Cvss Score: 6.4
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:N
PCI Compliance: Fail
Description:
According to its banner, the vers ion of PHP ins talled on the remote hos t is older than 5.3.2 / 5.2.13. Such vers ions may be
affected by s everal s ecurity is s ues :
- Directory paths not ending with '/' may not be correctly validated ins ide 'tempnam()' in 's afe_mode' configuration.
- It may be pos s ible to bypas s the 'open_bas edir'/ 's afe_mode' configuration res trictions due to an error in s es s ion
extens ions .
- An uns pecified vulnerability affects the LCG entropy.
Solution:
Page 68 of 120
Scan Date: 2017-01-17
Upgrade to PHP vers ion 5.3.2 / 5.2.13 or later.
Result:
Version source : http://rs202995.rs.hosteurope.de/secured/phpinfo.php Installed version : 5.1.6 Fixed version :
5.3.2 / 5.2.13
References:
http://s ecurityreas on.com/achievement_s ecurityalert/82
http://s ecurityreas on.com/s ecurityalert/7008
http://archives .neohaps is .com/archives /fulldis clos ure/2010-02/0209.html
http://www.php.net/releas es /5_3_2.php
http://www.php.net/ChangeLog-5.php#5.3.2
http://www.php.net/releas es /5_2_13.php
http://www.php.net/ChangeLog-5.php#5.2.13
Alert ID: 84644 Found on: 2017-01-17 Severity: Medium
PHP 5.3.x < 5.3.23 Information Disclosure (tcp/80)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2013-1824
Cvss Base: 4.3
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N
Description:
According to its banner, the vers ion of PHP 5.3.x ins talled on the remote hos t is prior to 5.3.23. It is , therefore, potentially
affected by an information dis clos ure vulnerability.
The fix for CVE-2013-1643 was incomplete and an error s till exis ts in the files 'ext/s oap/php_xml.c' and
'ext/libxml/libxml.c' related to handling external entities . This error could caus e PHP to pars e remote XML documents
defined by an attacker and could allow acces s to arbitrary files .
Note that this check does not attempt to exploit the vulnerability, but ins tead, relies only on PHP's s elf-reported vers ion
number.
Solution:
Upgrade to PHP vers ion 5.3.23 or later.
Result:
Version source : X-Powered-By: PHP/5.3.10-1~lucid+2uwsgi2 Installed version : 5.3.10-1~lucid+2uwsgi2 Fixed
version : 5.3.23
References:
http://www.Indus Guard.org/u?7c770707
http://www.php.net/ChangeLog-5.php#5.3.23
Alert ID: 84647 Found on: 2017-01-17 Severity: Medium
PHP < 5.2.4 Multiple Vulnerabilities (tcp/80)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2007-1413,CVE-2007-
Page 69 of 120
Scan Date: 2017-01-17
2872,CVE-2007-3294,CVE-2007
Cvss Base: 6.8
Cvss Score: 6.8
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:P/I:P/A:P
PCI Compliance: Fail
Description:
According to its banner, the vers ion of PHP ins talled on the remote hos t is older than 5.2.4. Such vers ions may be
affected by various is s ues , including but not limited to s everal overflows .
Solution:
Upgrade to PHP vers ion 5.2.4 or later.
Result:
Version source : http://rs202995.rs.hosteurope.de/secured/phpinfo.php Installed version : 5.1.6 Fixed version :
5.2.4
References:
http://www.php.net/releas es /5_2_4.php
Alert ID: 84648 Found on: 2017-01-17 Severity: Medium
PHP PHP_RSHUTDOWN_FUNCTION Security Bypass (tcp/80)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2012-1171
Cvss Base: 5.0
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N
Description:
According to its banner, the vers ion of PHP 5.x ins talled on the remote hos t is 5.x prior to 5.3.11 or 5.4.x prior to 5.4.1 and
thus , is potentially affected by a s ecurity bypas s vulnerability.
An error exis ts related to the function 'PHP_RSHUTDOWN_FUNCTION' in the libxml extens ion and the 's tream_clos e'
method that could allow a remote attacker to bypas s 'open_bas edir' protections and obtain s ens itive information.
Note that this check has not attempted to exploit this is s ue, but has ins tead relied only on PHP's s elf-reported vers ion
number.
Solution:
Upgrade to PHP vers ion 5.3.11 / 5.4.1 or later.
Result:
Version source : X-Powered-By: PHP/5.3.10-1~lucid+2uwsgi2 Installed version : 5.3.10-1~lucid+2uwsgi2 Fixed
version : 5.3.11 / 5.4.1
References:
http://www.Indus Guard.org/u?bcc428c2
https ://bugs .php.net/bug.php?id=61367
Alert ID: 84651 Found on: 2017-01-17 Severity: Medium
PHP Symlink Function Race Condition open_basedir Bypass (tcp/80)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2006-5178
Cvss Base: 6.2
Cvss Score: 6.2
Page 70 of 120
Scan Date: 2017-01-17
Cvss Vector: CVSS2#AV:L/AC:H/Au:N/C:C/I:C/A:C
PCI Compliance: Fail
Description:
According to its banner, the vers ion of PHP ins talled on the remote hos t is affected by a s ecurity bypas s vulnerability. A
race condition exis ts in the s ymlink function that allows local us ers to bypas s the open_bas edir res triction by us ing a
combination of s ymlink, mkdir, and unlink functions .
Solution:
There is no known s olution at this time.
Result:
Version source : X-Powered-By: PHP/5.3.10-1~lucid+2uwsgi2 Installed version : 5.3.10-1~lucid+2uwsgi2
References:
http://www.s ecurityfocus .com/archive/1/447649/100/0/threaded
Alert ID: 84653 Found on: 2017-01-17 Severity: Medium
PHP < 5.2.9 Multiple Vulnerabilities (tcp/80)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2008-5498,CVE-2009-
1271,CVE-2009-1272
Cvss Base: 5.0
Cvss Score: 5.0
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:N/I:N/A:P
PCI Compliance: Fail
Description:
According to its banner, the vers ion of PHP ins talled on the remote hos t is older than 5.2.9. Such vers ions may be
affected by s everal s ecurity is s ues :
- Background color is not correctly validated with a non true color image in function 'imagerotate()'. (CVE-2008-5498)
- A denial of s ervice condition can be triggered by trying to extract zip files that contain files with relative paths in file or
directory names .
- Function 'explode()' is affected by an uns pecified vulnerability.
- It may be pos s ible to trigger a s egfault by pas s ing a s pecially crafted s tring to function 'js on_decode()'.
- Function 'xml_error_s tring()' is affected by a flaw which res ults in mes s ages being off by one.
Solution:
Upgrade to PHP vers ion 5.2.9 or later.
Result:
Version source : http://rs202995.rs.hosteurope.de/secured/phpinfo.php Installed version : 5.1.6 Fixed version :
5.2.9
References:
http://news .php.net/php.internals /42762
http://www.php.net/releas es /5_2_9.php
http://www.php.net/ChangeLog-5.php#5.2.9
Page 71 of 120
Scan Date: 2017-01-17
Alert ID: 84656 Found on: 2017-01-17 Severity: Medium
PHP < 5.2.12 Multiple Vulnerabilities (tcp/80)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2009-3557,CVE-2009-
3558,CVE-2009-4017,CVE-2009
Cvss Base: 6.8
Cvss Score: 6.8
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:P/I:P/A:P
PCI Compliance: Fail
Description:
According to its banner, the vers ion of PHP ins talled on the remote hos t is older than 5.2.12. Such vers ions may be
affected by s everal s ecurity is s ues :
- It is pos s ible to bypas s the 's afe_mode' configuration s etting us ing 'tempnam()'. (CVE-2009-3557)
- It is pos s ible to bypas s the 'open_bas edir' configuration s etting us ing 'pos ix_mkfifo()'. (CVE-2009-3558)
- Provided file uploading is enabled (it is by default), an attacker can upload files us ing a POST reques t with
'multipart/form-data' content even if the target s cript does n't actually s upport file uploads per s e. B y s upplying a large
number (15,000+) of files , he may be able to caus e the web s erver to s top res ponding while it proces s es the file lis t.
(CVE-2009-4017)
- Mis s ing protection for '$_SESSION' from interrupt corruption and improved 's es s ion.s ave_path' check.
(CVE-2009-4143)
- Ins ufficient input s tring validation in the 'htmls pecialchars ()' function. (CVE-2009-4142)
Solution:
Upgrade to PHP vers ion 5.2.12 or later.
Result:
Version source : http://rs202995.rs.hosteurope.de/secured/phpinfo.php Installed version : 5.1.6 Fixed version :
5.2.12
References:
http://www.nes s us .org/u?57f2d08f
http://www.php.net/releas es /5_2_12.php
http://www.php.net/ChangeLog-5.php#5.2.12
Alert ID: 84660 Found on: 2017-01-17 Severity: Medium
PHP 5.3.x < 5.3.22 Multiple Vulnerabilities (tcp/80)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2013-1635,CVE-2013-1643
Cvss Base: 4.3
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:N/I:P/A:N
Description:
According to its banner, the vers ion of PHP 5.3.x ins talled on the remote hos t is prior to 5.3.22. It is , therefore, potentially
affected by the following vulnerabilities :
- An error exis ts in the file 'ext/s oap/s oap.c' related to the 's oap.ws dl_cache_dir' configuration directive and writing
cache files that could allow remote 'ws dl' files to be written to arbitrary locations . (CVE-2013-1635)
Page 72 of 120
Scan Date: 2017-01-17
- An error exis ts in the file 'ext/s oap/php_xml.c' related to pars ing SOAP 'ws dl' files and external entities that could caus e
PHP to pars e remote XML documents defined by an attacker. This could allow acces s to arbitrary files . (CVE-2013-1643)
Note that this check does not attempt to exploit the vulnerabilities but, ins tead relies only on PHP's s elf-reported vers ion
number.
Solution:
Upgrade to PHP vers ion 5.3.22 or later.
Result:
Version source : X-Powered-By: PHP/5.3.10-1~lucid+2uwsgi2 Installed version : 5.3.10-1~lucid+2uwsgi2 Fixed
version : 5.3.22
References:
http://www.Indus Guard.org/u?2dcf53bd
http://www.Indus Guard.org/u?889595b1
http://www.php.net/ChangeLog-5.php#5.3.22
Alert ID: 84662 Found on: 2017-01-17 Severity: Medium
PHP < 5.2.3 Multiple Vulnerabilities (tcp/80)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2007-1900,CVE-2007-
2756,CVE-2007-2872,CVE-2007
Cvss Base: 6.8
Cvss Score: 6.8
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:P/I:P/A:P
PCI Compliance: Fail
Description:
According to its banner, the vers ion of PHP ins talled on the remote hos t is older than 5.2.3. Such vers ions may be
affected by s everal is s ues , including an integer overflow, 's afe_mode' and 'open_bas edir' bypas s , and a denial of s ervice
vulnerability.
Solution:
Upgrade to PHP vers ion 5.2.3 or later.
Result:
Version source : http://rs202995.rs.hosteurope.de/secured/phpinfo.php Installed version : 5.1.6 Fixed version :
5.2.3
References:
http://www.php.net/releas es /5_2_3.php
Alert ID: 84665 Found on: 2017-01-17 Severity: Medium
Web Server info.php / phpinfo.php Detection (tcp/80)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 5.0
Cvss Score: 5.0
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N
PCI Compliance: Fail
Description:
Page 73 of 120
Scan Date: 2017-01-17
Many PHP ins tallation tutorials ins truct the us er to create a PHP file that calls the PHP function 'phpinfo()' for debugging
purpos es . Various PHP applications may als o include s uch a file. By acces s ing s uch a file, a remote attacker can
dis cover a large amount of information about the remote web s erver, including :
- The us ername of the us er who ins talled php and if they are a SUDO us er.
- The IP addres s of the hos t.
- The vers ion of the operating s ys tem.
- The web s erver vers ion.
- The root directory of the web s erver.
- Configuration information about the remote PHP ins tallation.
Solution:
Remove the affected file(s ).
Result:
IndusGuard discovered the following URL that calls phpinfo() : -
http://rs202995.rs.hosteurope.de/secured/phpinfo.php
Alert ID: 84688 Found on: 2017-01-17 Severity: Medium
OpenSSH LoginGraceTime / MaxStartups DoS (tcp/22)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 5.0
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:N/I:N/A:P
Description:
According to its banner, a vers ion of OpenSSH earlier than vers ion 6.2 is lis tening on this port. The default configuration
of OpenSSH ins talls before 6.2 could allow a remote attacker to bypas s the LoginGraceTime and MaxStartups thres holds
by periodically making a large number of new TCP connections and thereby prevent legitimate us ers from gaining
acces s to the s ervice.
Note that this check has not tried to exploit the is s ue or detect whether the remote s ervice us es a vulnerable
configuration. Ins tead, it has s imply checked the vers ion of OpenSSH running on the remote hos t.
Solution:
Upgrade to OpenSSH 6.2 and review the as s ociated s erver configuration s ettings .
Result:
Version source : SSH-2.0-O penSSH_5.3p1 Debian-3ubuntu7.1 Installed version : 5.3p1 Fixed version : 6.2
References:
http://www.openwall.com/lis ts /os s -s ecurity/2013/02/06/5
http://opens s h.org/txt/releas e-6.2
http://tools .cis co.com/s ecurity/center/viewAlert.x?alertId=28883
Alert ID: 84690 Found on: 2017-01-17 Severity: Medium
OpenSSH < 5.9 Multiple DoS (tcp/22)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2010-4755,CVE-2011-5000
Cvss Base: 4.0
Page 74 of 120
Scan Date: 2017-01-17
Cvss Base: 4.0
Cvss Score: 4.0
Cvss Vector: CVSS2#AV:N/AC:L/Au:S/C:N/I:N/A:P
PCI Compliance: Fail
Description:
According to its banner, the vers ion of OpenSSH running on the remote hos t is prior to vers ion 5.9. Such vers ions are
affected by multiple denial of s ervice vulnerabilities :
- A denial of s ervice vulnerability exis ts in the gs s -s erv.c 's s h_gs s api_pars e_ename' function. A remote attacker may be
able to trigger this vulnerability if gs s api-with-mic is enabled to create a denial of s ervice condition via a large value in a
certain length field.
(CVE-2011-5000)
- On FreeBSD, NetBSD, OpenBSD, and other products , a remote, authenticated attacker could exploit the remote_glob()
and proces s _put() functions to caus e a denial of s ervice (CPU and memory cons umption).
(CVE-2010-4755)
Solution:
Upgrade to OpenSSH 5.9 or later.
Result:
Version source : SSH-2.0-O penSSH_5.3p1 Debian-3ubuntu7.1 Installed version : 5.3p1 Fixed version : 5.9
References:
http://cxs ecurity.com/res earch/89
http://s ite.pi3.com.pl/adv/s s h_1.txt
Alert ID: 84693 Found on: 2017-01-17 Severity: Medium
OpenSSH >= 2.3.0 AllowTcpForwarding Port Bouncing (tcp/22)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2004-1653
Cvss Base: 6.4
Cvss Score: 6.4
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:N
PCI Compliance: Fail
Description:
According to its banner, the remote hos t is running OpenSSH, vers ion 2.3.0 or later. Such vers ions of OpenSSH allow
forwarding TCP connections . If the OpenSSH s erver is configured to allow anonymous connections (e.g. AnonCVS),
remote, unauthenticated us ers could us e the hos t as a proxy.
Solution:
Dis allow anonymous us ers , s et AllowTcpForwarding to 'no', or us e the Match directive to res trict anonymous us ers .
Result:
Version source : ssh-2.0-openssh_5.3p1 debian-3ubuntu7.1 Installed version : 5.3p1
References:
http://marc.info/?l=bugtraq&m=109413637313484&w=2
http://www.nes s us .org/u?2c86d008
Alert ID: 84694 Found on: 2017-01-17 Severity: Medium
OpenSSH S/KEY Authentication Account Enumeration (tcp/22)
Page 75 of 120
Scan Date: 2017-01-17
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2007-2243
Cvss Base: 5.0
Cvss Score: 5.0
Cvss Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N
PCI Compliance: Fail
Description:
When OpenSSH has S/KEY authentication enabled, it is pos s ible to determine remotely if an account configured for S/KEY
authentication exis ts .
Note that Indus Guard has not tried to exploit the is s ue, but rather only checked if OpenSSH is running on the remote hos t.
As a res ult, it will not detect if the remote hos t has implemented a workaround.
Solution:
A patch currently does not exis t for this is s ue. As a workaround, either s et 'ChallengeRes pons eAuthentication' in the
OpenSSH config to 'no' or us e a vers ion of OpenSSH without S/KEY s upport compiled in.
Result:
Version source : SSH-2.0-O penSSH_5.3p1 Debian-3ubuntu7.1 Installed version : 5.3p1
References:
http://www.nes s us .org/u?87921f08
Alert ID: 84695 Found on: 2017-01-17 Severity: Medium
OPIE w/ OpenSSH Account Enumeration (tcp/22)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2007-2768
Cvss Base: 4.3
Cvss Score: 4.3
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N
PCI Compliance: Fail
Description:
When us ing OPIE for PAM and OpenSSH, it is pos s ible for remote attackers to determine the exis tence of certain us er
acounts .
Note that Indus Guard has not tried to exploit the is s ue, but rather only checked if OpenSSH is running on the remote hos t.
As a res ult, it does not detect if the remote hos t actually has OPIE for PAM ins talled.
Solution:
A patch currently does not exis t for this is s ue. As a workaround, ens ure that OPIE for PAM is not ins talled.
Result:
Version source : SSH-2.0-O penSSH_5.3p1 Debian-3ubuntu7.1 Installed version : 5.3p1
References:
http://archives .neohaps is .com/archives /fulldis clos ure/2007-04/0635.html
Alert ID: 84696 Found on: 2017-01-17 Severity: Medium
OpenSSH < 6.6 Multiple Vulnerabilities (tcp/22)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 6.8
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:P/I:P/A:P
Page 76 of 120
Scan Date: 2017-01-17
Description:
According to its banner, the vers ion of OpenSSH running on the remote hos t is prior to vers ion 6.6. It is , therefore,
affected by the following vulnerabilities :
- An error exis ts related to the function 'has h_buffer' in the file 's chnorr.c' that could allow denial of s ervice attacks . Note
that the J-PAKE protocol mus t be enabled at compile time via the 'CFLAGS' variable '-DJPAKE' in the file 'Makefile.inc' in
order for the OpenSSL ins tallation to be vulnerable. This is not enabled by default. Further note that only vers ions 5.3
through 6.5.x are affected by this is s ue. (CVE-2014-1692)
- An error exis ts related to the 'AcceptEnv' configuration s etting in 's s hd_config' and wildcards . An attacker can bypas s
environment res trictions by us ing a s pecially crafted reques t. (CVE-2014-2532)
Solution:
Upgrade to OpenSSH 6.6 or later.
Result:
Version source : SSH-2.0-O penSSH_5.3p1 Debian-3ubuntu7.1 Installed version : 5.3p1 Fixed version : 6.6
References:
http://www.opens s h.com/txt/releas e-6.6
http://www.gos s amer-threads .com/lis ts /opens s h/dev/57663#57663
Alert ID: 84697 Found on: 2017-01-17 Severity: Medium
OpenSSH < 5.7 Multiple Vulnerabilities (tcp/22)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2010-4478,CVE-2012-0814
Cvss Base: 6.8
Cvss Score: 6.8
Cvss Vector: CVSS2#AV:N/AC:M/Au:N/C:P/I:P/A:P
PCI Compliance: Fail
Description:
According to its banner, the vers ion of OpenSSH running on the remote hos t is earlier than 5.7. Vers ions before 5.7 may
be affected by the following vulnerabilities :
- A s ecurity bypas s vulnerability becaus e OpenSSH does not properly validate the public parameters in the J-PAKE
protocol. This could allow an attacker to authenticate without the s hared s ecret. Note that this is s ue is only exploitable
when OpenSSH is built with J-PAKE s upport, which is currently experimental and dis abled by default, and that Indus Guard
has not checked whether J-PAKE s upport is indeed enabled. (CVE-2010-4478)
- The auth_pars e_options function in auth-options .c in s s hd provides debug mes s ages containing authorized_keys
command options , which allows remote, authenticated us ers to obtain potentially s ens itive information by reading thes e
mes s ages . (CVE-2012-0814)
Solution:
Upgrade to OpenSSH 5.7 or later.
Result:
Version source : SSH-2.0-O penSSH_5.3p1 Debian-3ubuntu7.1 Installed version : 5.3p1 Fixed version : 5.7
References:
http://s eb.dbzteam.org/crypto/jpake-s es s ion-key-retrieval.pdf
http://www.openbs d.org/cgi-bin/cvs web/s rc/us r.bin/s s h/jpake.c#rev1.5
http://www.nes s us .org/u?3f1722f0
Page 77 of 120
Scan Date: 2017-01-17
Alert ID: 84506 Found on: 2017-01-17 Severity: Low
SSL RC4 Cipher Suites Supported (tcp/995)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2013-2566
Cvss Base: 2.6
Cvss Vector: CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:N
Description:
The remote hos t s upports the us e of RC4 in one or more cipher s uites . The RC4 cipher is flawed in its generation of a
ps eudo-random s tream of bytes s o that a wide variety of s mall bias es are introduced into the s tream, decreas ing its
randomnes s .
If plaintext is repeatedly encrypted (e.g. HTTP cookies ), and an attacker is able to obtain many (i.e. tens of millions )
ciphertexts , the attacker may be able to derive the plaintext.
Solution:
Reconfigure the affected application, if pos s ible, to avoid us e of RC4 ciphers .
Result:
List of RC 4 cipher suites supported by the rem ote server : Low Strength C iphers (<= 64-bit key) SSLv2 EXP-RC 4-
MD5 Kx=RSA(512) Au=RSA Enc=RC 4(40) Mac=MD5 export TLSv1 EXP-RC 4-MD5 Kx=RSA(512) Au=RSA
Enc=RC 4(40) Mac=MD5 export High Strength C iphers (>= 112-bit key) SSLv2 RC 4-MD5 Kx=RSA Au=RSA
Enc=RC 4(128) Mac=MD5 TLSv1 RC 4-MD5 Kx=RSA Au=RSA Enc=RC 4(128) Mac=MD5 RC 4-SHA Kx=RSA Au=RSA
Enc=RC 4(128) Mac=SHA1 The fields above are : {O penSSL ciphernam e} Kx={key exchange}
Au={authentication} Enc={sym m etric encryption m ethod} Mac={m essage authentication code} {export flag}
References:
http://www.Indus Guard.org/u?217a3666
http://cr.yp.to/talks /2013.03.12/s lides .pdf
http://www.is g.rhul.ac.uk/tls /
Alert ID: 84527 Found on: 2017-01-17 Severity: Low
SSL RC4 Cipher Suites Supported (tcp/993)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2013-2566
Cvss Base: 2.6
Cvss Vector: CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:N
Description:
The remote hos t s upports the us e of RC4 in one or more cipher s uites . The RC4 cipher is flawed in its generation of a
ps eudo-random s tream of bytes s o that a wide variety of s mall bias es are introduced into the s tream, decreas ing its
randomnes s .
If plaintext is repeatedly encrypted (e.g. HTTP cookies ), and an attacker is able to obtain many (i.e. tens of millions )
ciphertexts , the attacker may be able to derive the plaintext.
Solution:
Reconfigure the affected application, if pos s ible, to avoid us e of RC4 ciphers .
Result:
List of RC 4 cipher suites supported by the rem ote server : Low Strength C iphers (<= 64-bit key) SSLv2 EXP-RC 4-
MD5 Kx=RSA(512) Au=RSA Enc=RC 4(40) Mac=MD5 export TLSv1 EXP-RC 4-MD5 Kx=RSA(512) Au=RSA
Page 78 of 120
Scan Date: 2017-01-17
Enc=RC 4(40) Mac=MD5 export High Strength C iphers (>= 112-bit key) SSLv2 RC 4-MD5 Kx=RSA Au=RSA
Enc=RC 4(128) Mac=MD5 TLSv1 RC 4-MD5 Kx=RSA Au=RSA Enc=RC 4(128) Mac=MD5 RC 4-SHA Kx=RSA Au=RSA
Enc=RC 4(128) Mac=SHA1 The fields above are : {O penSSL ciphernam e} Kx={key exchange}
Au={authentication} Enc={sym m etric encryption m ethod} Mac={m essage authentication code} {export flag}
References:
http://www.Indus Guard.org/u?217a3666
http://cr.yp.to/talks /2013.03.12/s lides .pdf
http://www.is g.rhul.ac.uk/tls /
Alert ID: 84549 Found on: 2017-01-17 Severity: Low
SSL RC4 Cipher Suites Supported (tcp/465)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2013-2566
Cvss Base: 2.6
Cvss Vector: CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:N
Description:
The remote hos t s upports the us e of RC4 in one or more cipher s uites . The RC4 cipher is flawed in its generation of a
ps eudo-random s tream of bytes s o that a wide variety of s mall bias es are introduced into the s tream, decreas ing its
randomnes s .
If plaintext is repeatedly encrypted (e.g. HTTP cookies ), and an attacker is able to obtain many (i.e. tens of millions )
ciphertexts , the attacker may be able to derive the plaintext.
Solution:
Reconfigure the affected application, if pos s ible, to avoid us e of RC4 ciphers .
Result:
List of RC 4 cipher suites supported by the rem ote server : High Strength C iphers (>= 112-bit key) TLSv1 ADH-RC 4-
MD5 Kx=DH Au=None Enc=RC 4(128) Mac=MD5 RC 4-MD5 Kx=RSA Au=RSA Enc=RC 4(128) Mac=MD5 RC 4-SHA
Kx=RSA Au=RSA Enc=RC 4(128) Mac=SHA1 The fields above are : {O penSSL ciphernam e} Kx={key exchange}
Au={authentication} Enc={sym m etric encryption m ethod} Mac={m essage authentication code} {export flag}
References:
http://www.Indus Guard.org/u?217a3666
http://cr.yp.to/talks /2013.03.12/s lides .pdf
http://www.is g.rhul.ac.uk/tls /
Alert ID: 84569 Found on: 2017-01-17 Severity: Low
SSL RC4 Cipher Suites Supported (tcp/143)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2013-2566
Cvss Base: 2.6
Cvss Vector: CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:N
Description:
The remote hos t s upports the us e of RC4 in one or more cipher s uites . The RC4 cipher is flawed in its generation of a
ps eudo-random s tream of bytes s o that a wide variety of s mall bias es are introduced into the s tream, decreas ing its
randomnes s .
Page 79 of 120
Scan Date: 2017-01-17
If plaintext is repeatedly encrypted (e.g. HTTP cookies ), and an attacker is able to obtain many (i.e. tens of millions )
ciphertexts , the attacker may be able to derive the plaintext.
Solution:
Reconfigure the affected application, if pos s ible, to avoid us e of RC4 ciphers .
Result:
List of RC 4 cipher suites supported by the rem ote server : Low Strength C iphers (<= 64-bit key) TLSv1 EXP-RC 4-
MD5 Kx=RSA(512) Au=RSA Enc=RC 4(40) Mac=MD5 export High Strength C iphers (>= 112-bit key) TLSv1 RC 4-MD5
Kx=RSA Au=RSA Enc=RC 4(128) Mac=MD5 RC 4-SHA Kx=RSA Au=RSA Enc=RC 4(128) Mac=SHA1 The fields above
are : {O penSSL ciphernam e} Kx={key exchange} Au={authentication} Enc={sym m etric encryption m ethod}
Mac={m essage authentication code} {export flag}
References:
http://www.Indus Guard.org/u?217a3666
http://cr.yp.to/talks /2013.03.12/s lides .pdf
http://www.is g.rhul.ac.uk/tls /
Alert ID: 84587 Found on: 2017-01-17 Severity: Low
SSL RC4 Cipher Suites Supported (tcp/110)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2013-2566
Cvss Base: 2.6
Cvss Vector: CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:N
Description:
The remote hos t s upports the us e of RC4 in one or more cipher s uites . The RC4 cipher is flawed in its generation of a
ps eudo-random s tream of bytes s o that a wide variety of s mall bias es are introduced into the s tream, decreas ing its
randomnes s .
If plaintext is repeatedly encrypted (e.g. HTTP cookies ), and an attacker is able to obtain many (i.e. tens of millions )
ciphertexts , the attacker may be able to derive the plaintext.
Solution:
Reconfigure the affected application, if pos s ible, to avoid us e of RC4 ciphers .
Result:
List of RC 4 cipher suites supported by the rem ote server : Low Strength C iphers (<= 64-bit key) TLSv1 EXP-RC 4-
MD5 Kx=RSA(512) Au=RSA Enc=RC 4(40) Mac=MD5 export High Strength C iphers (>= 112-bit key) TLSv1 RC 4-MD5
Kx=RSA Au=RSA Enc=RC 4(128) Mac=MD5 RC 4-SHA Kx=RSA Au=RSA Enc=RC 4(128) Mac=SHA1 The fields above
are : {O penSSL ciphernam e} Kx={key exchange} Au={authentication} Enc={sym m etric encryption m ethod}
Mac={m essage authentication code} {export flag}
References:
http://www.Indus Guard.org/u?217a3666
http://cr.yp.to/talks /2013.03.12/s lides .pdf
http://www.is g.rhul.ac.uk/tls /
Alert ID: 84604 Found on: 2017-01-17 Severity: Low
POP3 Cleartext Logins Permitted (tcp/110)
Page 80 of 120
Scan Date: 2017-01-17
Open Status: NEW First Found: 2017-01-17
Cvss Base: 2.6
Cvss Score: 2.6
Cvss Vector: CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:N
PCI Compliance: Pas s
Description:
The remote hos t is running a POP3 daemon that allows cleartext logins over unencrypted connections . An attacker can
uncover us er names and pas s words by s niffing traffic to the POP3 daemon if a les s s ecure authentication mechanis m
(eg, USER command, AUTH PLAIN, AUTH LOGIN) is us ed.
Solution:
Contact your vendor for a fix or encrypt traffic with SSL / TLS us ing s tunnel.
Result:
The following cleartext m ethods are supported :SASL LO GIN C RAM-MD5 PLAINUSER
References:
http://tools .ietf.org/html/rfc2222
http://tools .ietf.org/html/rfc2595
Alert ID: 84621 Found on: 2017-01-17 Severity: Low
Web Server Uses Plain Text Authentication Forms (tcp/80)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 2.6
Cvss Score: 2.6
Cvss Vector: CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:N
PCI Compliance: Pas s
Description:
The remote web s erver contains s everal HTML form fields containing an input of type 'pas s word' which trans mit their
information to a remote web s erver in cleartext.
An attacker eaves dropping the traffic between web brows er and s erver may obtain logins and pas s words of valid us ers .
Solution:
Make s ure that every s ens itive form trans mits content over HTTPS.
Result:
Page : /login.phpDestination Page: /userinfo.phpPage : /signup.phpDestination Page: /secured/newuser.php
Alert ID: 84657 Found on: 2017-01-17 Severity: Low
PHP mb_send_mail() Function Parameter Security Bypass (tcp/80)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2006-1014
Cvss Base: 3.2
Cvss Score: 3.2
Cvss Vector: CVSS2#AV:L/AC:L/Au:S/C:P/I:P/A:N
PCI Compliance: Pas s
Description:
According to its banner, the vers ion of PHP ins talled on the remote hos t is affected by a flaw that allows an attacker to
gain unauthorized privileges . When us ed with s endmail and when accepting remote input for the additional_parameters
Page 81 of 120
Scan Date: 2017-01-17
argument to the mb_s end_mail function, it is pos s ible for context-dependent attackers to read and create arbitrary files .
Solution:
There is no known s olution at this time.
Result:
Version source : X-Powered-By: PHP/5.3.10-1~lucid+2uwsgi2 Installed version : 5.3.10-1~lucid+2uwsgi2
References:
http://www.s ecurityfocus .com/archive/1/426342/100/0/threaded
Alert ID: 84667 Found on: 2017-01-17 Severity: Low
CGI Generic Injectable Parameter (tcp/80)
Open Status: NEW First Found: 2017-01-17
Description:
Indus Guard was able to to inject innocuous s trings into CGI parameters and read them back in the HTTP res pons e.
The affected parameters are candidates for extended injection tes ts like cros s -s ite s cripting attacks .
This is not a weaknes s per s e, the main purpos e of this tes t is to s peed up other s cripts . The res ults may be us eful for a
human pen-tes ter.
Solution:
n/a
Result:
Using the GET HTTP m ethod, IndusGuard found that :+ The following resources m ay be vulnerable to injectable
param eter :+ The 'pp' param eter of the /hpp/ C GI :/hpp/?pp=% 00zjfvtt-------- output --------<a href="?
pp=12">check</a><br/><a href="param s.php?p=valid& pp=% 00zjfvtt">link1</a><br/><a href="param s.php?
p=valid& pp=.zjfvtt">link2</a><br/><form action="param s.php?p=valid& pp=.zjfvtt"><input type=subm it
nam e=aaaa/></form ><br/><hr><a href='http://blog.m indedsecurity.com /2009/05/client-side-http-p [...]---------------
---------+ The 'file' param eter of the /showim age.php C GI :/showim age.php?file=zjfvtt-------- output --------Warning:
fopen(): Unable to access zjfvtt in /hj/var/www/showim age.php on line 7Warning: fopen(zjfvtt): failed to open
stream : No such file or dir [...]------------------------+ The 'cat' param eter of the /listproducts.php C GI :/listproducts.php?
cat=zjfvtt-------- output --------<! -- InstanceBeginEditable nam e="content_rgn" --><div id="content">Error: Unknown
colum n 'zjfvtt' in 'where clause'Warning: m ysql_fetch_array() expects param eter 1 to be resource, b [...]</div>------
------------------+ The 'artist' param eter of the /listproducts.php C GI :/listproducts.php?artist=zjfvtt-------- output --------<! --
InstanceBeginEditable nam e="content_rgn" --><div id="content">Error: Unknown colum n 'zjfvtt' in 'where
clause'Warning: m ysql_fetch_array() expects param eter 1 to be resource, b [...]</div>------------------------+ The 'cat'
param eter of the /listproducts.php C GI :/listproducts.php?cat=zjfvtt& artist=1-------- output --------<! --
InstanceBeginEditable nam e="content_rgn" --><div id="content">Error: Unknown colum n 'zjfvtt' in 'where
clause'Warning: m ysql_fetch_array() expects param eter 1 to be resource, b [...]</div>------------------------+ The 'pp'
param eter of the /hpp/param s.php C GI :/hpp/param s.php?pp=% 00zjfvtt-------- output --------.zjfvtt------------------------+ The
'p' param eter of the /hpp/param s.php C GI :/hpp/param s.php?p=% 00zjfvtt-------- output --------.zjfvtt------------------------+
The 'pp' param eter of the /hpp/param s.php C GI :/hpp/param s.php?pp=% 00zjfvtt& p=valid& aaaa/=-------- output ----
----valid.zjfvtt------------------------+ The 'p' param eter of the /hpp/param s.php C GI :/hpp/param s.php?
pp=12& p=% 00zjfvtt& aaaa/=-------- output --------.zjfvtt12------------------------C licking directly on these URLs should exhibit
the issue :(you will probably need to read the HTML source)http://rs202995.rs.hosteurope.de/hpp/?
pp=% 00zjfvtthttp://rs202995.rs.hosteurope.de/showim age.php?
file=zjfvtthttp://rs202995.rs.hosteurope.de/listproducts.php?
cat=zjfvtthttp://rs202995.rs.hosteurope.de/listproducts.php?
artist=zjfvtthttp://rs202995.rs.hosteurope.de/listproducts.php?
cat=zjfvtt& artist=1http://rs202995.rs.hosteurope.de/hpp/param s.php?
pp=% 00zjfvtthttp://rs202995.rs.hosteurope.de/hpp/param s.php?
p=% 00zjfvtthttp://rs202995.rs.hosteurope.de/hpp/param s.php?
pp=% 00zjfvtt& p=valid& aaaa/=http://rs202995.rs.hosteurope.de/hpp/param s.php?pp=12& p=% 00zjfvtt& aaaa/=
Page 82 of 120
Scan Date: 2017-01-17
Alert ID: 84680 Found on: 2017-01-17 Severity: Low
SMTP Service Cleartext Login Permitted (tcp/25)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 2.6
Cvss Score: 2.6
Cvss Vector: CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:N
PCI Compliance: Pas s
Description:
The remote hos t is running an SMTP s erver that advertis es that it allows cleartext logins over unencrypted connections .
An attacker may be able to uncover us er names and pas s words by s niffing traffic to the s erver if a les s s ecure
authentication mechanis m (i.e. LOGIN or PLAIN) is us ed.
Solution:
Configure the s ervice to s upport les s s ecure authentication mechanis ms only over an encrypted channel.
Result:
The SMTP server advertises the following SASL m ethods over anunencrypted channel : All supported m ethods :
PLAIN, LO GIN, DIGEST-MD5, C RAM-MD5 C leartext m ethods : PLAIN, LO GIN
References:
http://tools .ietf.org/html/rfc4422
http://tools .ietf.org/html/rfc4954
Alert ID: 84684 Found on: 2017-01-17 Severity: Low
SSH Weak MAC Algorithms Enabled (tcp/22)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 2.6
Cvss Vector: CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:N
Description:
The SSH s erver is configured to allow either MD5 or 96-bit MAC algorithms , both of which are cons idered weak.
Note that this check only checks for the options of the SSH s erver and does not check for vulnerable s oftware vers ions .
Solution:
Contact the vendor or cons ult product documentation to dis able MD5 and 96-bit MAC algorithms .
Result:
The following client-to-server Message Authentication C ode (MAC ) algorithm sare supported : hm ac-m d5 hm ac-
m d5-96 hm ac-sha1-96The following server-to-client Message Authentication C ode (MAC ) algorithm sare
supported : hm ac-m d5 hm ac-m d5-96 hm ac-sha1-96
Alert ID: 84685 Found on: 2017-01-17 Severity: Low
SSH Server CBC Mode Ciphers Enabled (tcp/22)
Open Status: NEW First Found: 2017-01-17
CVE ID: CVE-2008-5161
Cvss Base: 2.6
Cvss Vector: CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:N
Description:
Page 83 of 120
Scan Date: 2017-01-17
The SSH s erver is configured to s upport Cipher Block Chaining (CBC) encryption. This may allow an attacker to recover
the plaintext mes s age from the ciphertext.
Note that this check only checks for the options of the SSH s erver and does not check for vulnerable s oftware vers ions .
Solution:
Contact the vendor or cons ult product documentation to dis able CBC mode cipher encryption, and enable CTR or GCM
cipher mode encryption.
Result:
The following client-to-server C ipher Block C haining (C BC ) algorithm sare supported : 3des-cbc aes128-cbc
aes192-cbc aes256-cbc blowfish-cbc cast128-cbc rijndael-cbc@ lysator.liu.seThe following server-to-client C ipher
Block C haining (C BC ) algorithm sare supported : 3des-cbc aes128-cbc aes192-cbc aes256-cbc blowfish-cbc
cast128-cbc rijndael-cbc@ lysator.liu.se
Alert ID: 84689 Found on: 2017-01-17 Severity: Low
Portable OpenSSH ssh-keysign ssh-rand-helper Utility File Descriptor Leak Local Information Disclosure
(tcp/22)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 2.1
Cvss Score: 2.1
Cvss Vector: CVSS2#AV:L/AC:L/Au:N/C:P/I:N/A:N
PCI Compliance: Pas s
Description:
According to its banner, the vers ion of OpenSSH running on the remote hos t is earlier than 5.8p2. Such vers ions may be
affected by a local information dis clos ure vulnerability that could allow the contents of the hos t's private key to be
acces s ible by locally tracing the execution of the s s h-keys ign utility. Having the hos t's private key may allow the
impers onation of the hos t.
Note that ins tallations are only vulnerable if s s h-rand-helper was enabled during the build proces s , which is not the cas e
for *BSD, OS X, Cygwin and Linux.
Solution:
Upgrade to Portable OpenSSH 5.8p2 or later.
Result:
Version source : SSH-2.0-O penSSH_5.3p1 Debian-3ubuntu7.1 Installed version : 5.3p1 Fixed version : 5.8p2
References:
http://www.opens s h.com/txt/portable-keys ign-rand-helper.adv
http://www.opens s h.com/txt/releas e-5.8p2
Alert ID: 84700 Found on: 2017-01-17 Severity: Low
FTP Supports Clear Text Authentication (tcp/21)
Open Status: NEW First Found: 2017-01-17
Cvss Base: 2.6
Cvss Score: 2.6
Cvss Vector: CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:N
PCI Compliance: Pas s
Description:
The remote FTP s erver allows the us er's name and pas s word to be trans mitted in clear text, which could be intercepted
by a network s niffer or a man-in-the-middle attack.
Page 84 of 120
Scan Date: 2017-01-17
Solution:
Switch to SFTP (part of the SSH s uite) or FTPS (FTP over SSL/TLS). In the latter cas e, configure the s erver s o that control
connections are encrypted.
Result:
This FTP server does not support 'AUTH TLS'.
Alert ID: 84498 Found on: 2017-01-17 Severity: Info
HyperText Transfer Protocol (HTTP) Information (tcp/8880)
Open Status: NEW First Found: 2017-01-17
Description:
This tes t gives s ome information about the remote HTTP protocol - the vers ion us ed, whether HTTP Keep-Alive and HTTP
pipelining are enabled, etc...
This tes t is informational only and does not denote any s ecurity problem.
Solution:
n/a
Result:
Protocol version : HTTP/1.1SSL : noKeep-Alive : noO ptions allowed : O PTIO NS, GET, HEAD, PO STHeaders :
C onnection: close Expires: Thu, 16 Feb 2017 10:40:40 GMT C ache-C ontrol: m ax-age=2592000 C ontent-Type:
text/htm l C ontent-Length: 345 Date: Tue, 17 Jan 2017 10:40:40 GMT Server: sw-cp-server
Alert ID: 84499 Found on: 2017-01-17 Severity: Info
HTTP Methods Allowed (per directory) (tcp/8880)
Open Status: NEW First Found: 2017-01-17
Description:
By calling the OPTIONS method, it is pos s ible to determine which HTTP methods are allowed on each directory.
As this lis t may be incomplete, the check als o tes ts - if 'Thorough tes ts ' are enabled or 'Enable web applications tes ts ' is
s et to 'yes ' in the s can policy - various known HTTP methods on each directory and cons iders them as uns upported if it
receives a res pons e code of 400, 403, 405, or 501.
Note that the check output is only informational and does not neces s arily indicate the pres ence of any s ecurity
vulnerabilities .
Solution:
n/a
Result:
Based on the response to an O PTIO NS request : - HTTP m ethods GET HEAD PO ST O PTIO NS are allowed on :
/Based on tests of each m ethod : - HTTP m ethods C O PY DELETE GET HEAD LO C K MKC O L MO VE O PTIO NS PO ST
PRO PFIND PRO PPATC H PUT UNLO C K are allowed on : /
Alert ID: 84500 Found on: 2017-01-17 Severity: Info
HTTP Server Type and Version (tcp/8880)
Open Status: NEW First Found: 2017-01-17
Description:
Page 85 of 120
Scan Date: 2017-01-17
This check attempts to determine the type and the vers ion of the remote web s erver.
Solution:
n/a
Result:
The rem ote web server type is :sw-cp-server
Alert ID: 84501 Found on: 2017-01-17 Severity: Info
HyperText Transfer Protocol (HTTP) Information (tcp/8443)
Open Status: NEW First Found: 2017-01-17
Description:
This tes t gives s ome information about the remote HTTP protocol - the vers ion us ed, whether HTTP Keep-Alive and HTTP
pipelining are enabled, etc...
This tes t is informational only and does not denote any s ecurity problem.
Solution:
n/a
Result:
Protocol version : HTTP/1.1SSL : noKeep-Alive : noO ptions allowed : O PTIO NS, GET, HEAD, PO STHeaders :
C onnection: close Expires: Thu, 16 Feb 2017 10:40:39 GMT C ache-C ontrol: m ax-age=2592000 C ontent-Type:
text/htm l C ontent-Length: 345 Date: Tue, 17 Jan 2017 10:40:39 GMT Server: sw-cp-server
Alert ID: 84502 Found on: 2017-01-17 Severity: Info
HTTP Methods Allowed (per directory) (tcp/8443)
Open Status: NEW First Found: 2017-01-17
Description:
By calling the OPTIONS method, it is pos s ible to determine which HTTP methods are allowed on each directory.
As this lis t may be incomplete, the check als o tes ts - if 'Thorough tes ts ' are enabled or 'Enable web applications tes ts ' is
s et to 'yes ' in the s can policy - various known HTTP methods on each directory and cons iders them as uns upported if it
receives a res pons e code of 400, 403, 405, or 501.
Note that the check output is only informational and does not neces s arily indicate the pres ence of any s ecurity
vulnerabilities .
Solution:
n/a
Result:
Based on the response to an O PTIO NS request : - HTTP m ethods GET HEAD PO ST O PTIO NS are allowed on :
/Based on tests of each m ethod : - HTTP m ethods C O PY DELETE GET HEAD LO C K MKC O L MO VE O PTIO NS PO ST
PRO PFIND PRO PPATC H PUT UNLO C K are allowed on : /
Alert ID: 84503 Found on: 2017-01-17 Severity: Info
HTTP Server Type and Version (tcp/8443)
Open Status: NEW First Found: 2017-01-17
Description:
Page 86 of 120
Scan Date: 2017-01-17
This check attempts to determine the type and the vers ion of the remote web s erver.
Solution:
n/a
Result:
The rem ote web server type is :sw-cp-server
Alert ID: 84505 Found on: 2017-01-17 Severity: Info
SSL Session Resume Supported (tcp/995)
Open Status: NEW First Found: 2017-01-17
Description:
This s cript detects whether a hos t allows res uming SSL s es s ions by performing a full SSL hands hake to receive a
s es s ion ID, and then reconnecting with the previous ly us ed s es s ion ID. If the s erver accepts the s es s ion ID in the
s econd connection, the s erver maintains a cache of s es s ions that can be res umed.
Solution:
n/a
Result:
This port supports resum ing SSLv3 sessions.
Alert ID: 84510 Found on: 2017-01-17 Severity: Info
SSL Cipher Block Chaining Cipher Suites Supported (tcp/995)
Open Status: NEW First Found: 2017-01-17
Description:
The remote hos t s upports the us e of SSL ciphers that operate in Cipher Block Chaining (CBC) mode. Thes e cipher s uites
offer additional s ecurity over Electronic Codebook (ECB) mode, but have the potential to leak information if us ed
improperly.
Solution:
n/a
Result:
Here is the list of SSL C BC ciphers supported by the rem ote server : Low Strength C iphers (<= 64-bit key) SSLv2
DES-C BC -MD5 Kx=RSA Au=RSA Enc=DES-C BC (56) Mac=MD5 EXP-RC 2-C BC -MD5 Kx=RSA(512) Au=RSA Enc=RC 2-
C BC (40) Mac=MD5 export TLSv1 EXP-DES-C BC -SHA Kx=RSA(512) Au=RSA Enc=DES-C BC (40) Mac=SHA1 export
EXP-RC 2-C BC -MD5 Kx=RSA(512) Au=RSA Enc=RC 2-C BC (40) Mac=MD5 export DES-C BC -SHA Kx=RSA Au=RSA
Enc=DES-C BC (56) Mac=SHA1 Medium Strength C iphers (> 64-bit and < 112-bit key) SSLv2 DES-C BC 3-MD5
Kx=RSA Au=RSA Enc=3DES-C BC (168) Mac=MD5 TLSv1 DES-C BC 3-SHA Kx=RSA Au=RSA Enc=3DES-C BC (168)
Mac=SHA1 High Strength C iphers (>= 112-bit key) SSLv2 RC 2-C BC -MD5 Kx=RSA Au=RSA Enc=RC 2-C BC (128)
Mac=MD5 TLSv1 AES128-SHA Kx=RSA Au=RSA Enc=AES-C BC (128) Mac=SHA1 AES256-SHA Kx=RSA Au=RSA
Enc=AES-C BC (256) Mac=SHA1 The fields above are : {O penSSL ciphernam e} Kx={key exchange}
Au={authentication} Enc={sym m etric encryption m ethod} Mac={m essage authentication code} {export flag}
References:
http://www.opens s l.org/docs /apps /ciphers .html
http://www.Indus Guard.org/u?cc4a822a
http://www.opens s l.org/~bodo/tls -cbc.txt
Page 87 of 120
Scan Date: 2017-01-17
Alert ID: 84514 Found on: 2017-01-17 Severity: Info
SSL Cipher Suites Supported (tcp/995)
Open Status: NEW First Found: 2017-01-17
Description:
This s cript detects which SSL ciphers are s upported by the remote s ervice for encrypting communications .
Solution:
n/a
Result:
Here is the list of SSL ciphers supported by the rem ote server :Each group is reported per SSL Version.SSL
Version : TLSv1 Low Strength C iphers (<= 64-bit key) EXP-DES-C BC -SHA Kx=RSA(512) Au=RSA Enc=DES-C BC (40)
Mac=SHA1 export EXP-RC 2-C BC -MD5 Kx=RSA(512) Au=RSA Enc=RC 2-C BC (40) Mac=MD5 export EXP-RC 4-MD5
Kx=RSA(512) Au=RSA Enc=RC 4(40) Mac=MD5 export DES-C BC -SHA Kx=RSA Au=RSA Enc=DES-C BC (56)
Mac=SHA1 Medium Strength C iphers (> 64-bit and < 112-bit key) DES-C BC 3-SHA Kx=RSA Au=RSA Enc=3DES-
C BC (168) Mac=SHA1 High Strength C iphers (>= 112-bit key) AES128-SHA Kx=RSA Au=RSA Enc=AES-C BC (128)
Mac=SHA1 AES256-SHA Kx=RSA Au=RSA Enc=AES-C BC (256) Mac=SHA1 RC 4-MD5 Kx=RSA Au=RSA
Enc=RC 4(128) Mac=MD5 RC 4-SHA Kx=RSA Au=RSA Enc=RC 4(128) Mac=SHA1 SSL Version : SSLv3 Low Strength
C iphers (<= 64-bit key) EXP-DES-C BC -SHA Kx=RSA(512) Au=RSA Enc=DES-C BC (40) Mac=SHA1 export EXP-RC 2-
C BC -MD5 Kx=RSA(512) Au=RSA Enc=RC 2-C BC (40) Mac=MD5 export EXP-RC 4-MD5 Kx=RSA(512) Au=RSA
Enc=RC 4(40) Mac=MD5 export DES-C BC -SHA Kx=RSA Au=RSA Enc=DES-C BC (56) Mac=SHA1 Medium Strength
C iphers (> 64-bit and < 112-bit key) DES-C BC 3-SHA Kx=RSA Au=RSA Enc=3DES-C BC (168) Mac=SHA1 High
Strength C iphers (>= 112-bit key) AES128-SHA Kx=RSA Au=RSA Enc=AES-C BC (128) Mac=SHA1 AES256-SHA
Kx=RSA Au=RSA Enc=AES-C BC (256) Mac=SHA1 RC 4-MD5 Kx=RSA Au=RSA Enc=RC 4(128) Mac=MD5 RC 4-SHA
Kx=RSA Au=RSA Enc=RC 4(128) Mac=SHA1 SSL Version : SSLv2 Low Strength C iphers (<= 64-bit key) DES-C BC -
MD5 Kx=RSA Au=RSA Enc=DES-C BC (56) Mac=MD5 EXP-RC 2-C BC -MD5 Kx=RSA(512) Au=RSA Enc=RC 2-C BC (40)
Mac=MD5 export EXP-RC 4-MD5 Kx=RSA(512) Au=RSA Enc=RC 4(40) Mac=MD5 export Medium Strength C iphers
(> 64-bit and < 112-bit key) DES-C BC 3-MD5 Kx=RSA Au=RSA Enc=3DES-C BC (168) Mac=MD5 High Strength
C iphers (>= 112-bit key) RC 2-C BC -MD5 Kx=RSA Au=RSA Enc=RC 2-C BC (128) Mac=MD5 RC 4-MD5 Kx=RSA Au=RSA
Enc=RC 4(128) Mac=MD5 The fields above are : {O penSSL ciphernam e} Kx={key exchange}
Au={authentication} Enc={sym m etric encryption m ethod} Mac={m essage authentication code} {export flag}
References:
http://www.opens s l.org/docs /apps /ciphers .html
Alert ID: 84517 Found on: 2017-01-17 Severity: Info
SSL Certificate commonName Mismatch (tcp/995)
Open Status: NEW First Found: 2017-01-17
Description:
This s ervice pres ents an SSL certificate for which the 'commonName' (CN) does not match the hos t name on which the
s ervice lis tens .
Solution:
If the machine has s everal names , make s ure that us ers connect to the s ervice through the DNS hos t name that
matches the common name in the certificate.
Result:
The host nam e known by IndusGuard is : rs202995.rs.hosteurope.deThe C om m on Nam e in the certificate is :
parallels panel
Alert ID: 84518 Found on: 2017-01-17 Severity: Info
OpenSSL Detection (tcp/995)
Page 88 of 120
Scan Date: 2017-01-17
Open Status: NEW First Found: 2017-01-17
Description:
Bas ed on its behavior, it s eems that the remote s ervice is us ing the OpenSSL library to encrypt traffic.
Note that this check can only detect OpenSSL implementations that have enabled s upport for TLS extens ions (RFC 4366).
Solution:
n/a
References:
http://www.opens s l.org
Alert ID: 84521 Found on: 2017-01-17 Severity: Info
SSL Certificate Information (tcp/995)
Open Status: NEW First Found: 2017-01-17
Description:
This check connects to every SSL-related port and attempts to extract and dump the X.509 certificate.
Solution:
n/a
Result:
Subject Nam e: C ountry: USState/Province: VirginiaLocality: HerndonO rganization: ParallelsO rganization Unit:
Parallels PanelC om m on Nam e: Parallels PanelEm ail Address: info@ parallels.com Issuer Nam e: C ountry:
USState/Province: VirginiaLocality: HerndonO rganization: ParallelsO rganization Unit: Parallels PanelC om m on
Nam e: Parallels PanelEm ail Address: info@ parallels.com Serial Num ber: 50 9C DB A6 Version: 1Signature
Algorithm : SHA-1 With RSA EncryptionNot Valid Before: Nov 09 10:32:06 2012 GMTNot Valid After: Nov 09
10:32:06 2013 GMTPublic Key Info: Algorithm : RSA EncryptionKey Length: 2048 bitsPublic Key: 00 DA 42 9A E5 33
70 B0 DB DD C A 0D C 5 54 08 D3 6C D9 31 79 C E 65 D1 F5 11 3A 1F 5B 9E 0C 53 14 B1 19 13 6F 4E 5C BA 6C 98 EE
2B ED 60 55 E2 48 2E EA 16 9C 70 C 8 E6 94 42 DC 02 71 BA 59 3D DC 7B B3 F6 D7 0C E2 C F F5 53 47 8E 2F D3
AD 2B 68 1D 9D 03 95 5E B8 0C 3D 7C D2 EB B5 A3 35 A1 2D 58 ED 42 22 29 20 78 DE 1D 91 70 63 55 B7 0F B8
31 40 EB 43 F8 8B 03 B2 1D C 9 4C BE 61 2D 3E 5E D4 B9 09 06 88 47 C 9 1B 5B 9E 26 80 12 55 20 E5 D8 7E 66 44
AC C 2 F6 6E C 9 F5 B4 B6 2A 14 B7 8A 3F D1 3D 5C 3F 7E 25 3A 48 18 E1 13 FB 9D 7E C 1 E6 4D 12 1E 03 73 6C C 9
61 B0 48 89 AD AD 4A 4F 08 26 45 44 28 4E A7 B5 2B 15 E5 9A E2 D6 B7 5D 50 9E 0B F9 7E 0A 84 E1 62 6E E3 3F
EA C 0 C F D8 FF B9 3D 5E 0E 2C 74 C 5 D0 3E F3 16 E2 F1 E6 F5 D6 57 7F D4 92 F4 0F 8B 2E 2A 7B A0 B0 8C E5 10
37 Exponent: 01 00 01 Signature Length: 256 bytes / 2048 bitsSignature: 00 22 9C F8 E3 1E 45 98 6C 25 E7 37 19
12 B5 B6 F0 2C 86 E0 E0 31 FB C B 36 46 D0 7E D9 F1 F1 7B 1E 6E 82 D4 EC FD E9 9A 73 4A A1 8F 68 37 58 34 A1
B1 9F 2C A3 C 3 2A 40 D9 9C C 2 48 E4 1F AA C D 5A A5 87 06 EF 5A 24 36 09 68 82 44 AD 39 52 FC 70 5C DE DF
09 29 2C E3 B5 17 1A 61 B7 95 0E A7 21 1F F2 4B EB F6 A9 4C 3F BC A6 7F DF 59 BA FF 3C D1 B6 11 FA B7 C 2 5A
51 7C 6C 07 38 22 9D 34 04 C B 2C 74 52 BB 81 37 FE 70 97 49 31 7A 90 33 85 86 3C BD 0D 9C 68 BD 8F A1 A7
74 C E 3F F1 93 62 19 0A 32 E6 EB C 4 77 AB 55 DF 16 5D 86 D9 0C 7A AE D3 A8 9E 56 92 C F 94 D1 70 F4 06 BD
33 11 35 49 A4 76 74 0C 11 9C 52 3D 2F 01 9C 6E AC 64 B0 2F 92 A6 B2 45 C 9 AA 30 9A 56 38 EB 52 54 11 03 0A
44 86 06 BB 53 6B 1B 11 F5 40 B0 E4 C 8 AC DD 39 92 C E 84 D2 AB D4 A8 F3 8A 3E 86 44 BD E9 3E Fingerprints :
SHA-256 Fingerprint: A0 82 92 DA 52 55 74 E1 6B 13 7D D0 B6 C 0 81 40 30 C F 3D BA A7 21 32 45 5D C 3 85 DF A7
F2 D9 88 SHA-1 Fingerprint: E5 6C 82 EE 62 05 DD 93 BF 17 E9 38 35 6E 70 BA A1 71 91 67 MD5 Fingerprint: 88 C 1
7E 0F 7E 06 68 98 95 31 38 85 AE 81 43 2B
Alert ID: 84523 Found on: 2017-01-17 Severity: Info
SSL / TLS Versions Supported (tcp/995)
Open Status: NEW First Found: 2017-01-17
Description:
Page 89 of 120
Scan Date: 2017-01-17
This s cript detects which SSL and TLS vers ions are s upported by the remote s ervice for encrypting communications .
Solution:
n/a
Result:
This port supports SSLv2/SSLv3/TLSv1.0.
Alert ID: 84524 Found on: 2017-01-17 Severity: Info
POP Server Detection (tcp/995)
Open Status: NEW First Found: 2017-01-17
Description:
The remote hos t is running a s erver that unders tands the Pos t Office Protocol (POP), us ed by email clients to retrieve
mes s ages from a s erver, pos s ibly acros s a network link.
Solution:
Dis able this s ervice if you do not us e it.
Result:
Rem ote PO P server banner :+O K Hello there. <17503.1484647941@ localhost.localdom ain>
References:
http://en.wikipedia.org/wiki/Pos t_Office_Protocol
Alert ID: 84526 Found on: 2017-01-17 Severity: Info
SSL Session Resume Supported (tcp/993)
Open Status: NEW First Found: 2017-01-17
Description:
This s cript detects whether a hos t allows res uming SSL s es s ions by performing a full SSL hands hake to receive a
s es s ion ID, and then reconnecting with the previous ly us ed s es s ion ID. If the s erver accepts the s es s ion ID in the
s econd connection, the s erver maintains a cache of s es s ions that can be res umed.
Solution:
n/a
Result:
This port supports resum ing SSLv3 sessions.
Alert ID: 84531 Found on: 2017-01-17 Severity: Info
SSL Cipher Block Chaining Cipher Suites Supported (tcp/993)
Open Status: NEW First Found: 2017-01-17
Description:
The remote hos t s upports the us e of SSL ciphers that operate in Cipher Block Chaining (CBC) mode. Thes e cipher s uites
offer additional s ecurity over Electronic Codebook (ECB) mode, but have the potential to leak information if us ed
improperly.
Solution:
n/a
Result:
Page 90 of 120
Scan Date: 2017-01-17
Here is the list of SSL C BC ciphers supported by the rem ote server : Low Strength C iphers (<= 64-bit key) SSLv2
DES-C BC -MD5 Kx=RSA Au=RSA Enc=DES-C BC (56) Mac=MD5 EXP-RC 2-C BC -MD5 Kx=RSA(512) Au=RSA Enc=RC 2-
C BC (40) Mac=MD5 export TLSv1 EXP-DES-C BC -SHA Kx=RSA(512) Au=RSA Enc=DES-C BC (40) Mac=SHA1 export
EXP-RC 2-C BC -MD5 Kx=RSA(512) Au=RSA Enc=RC 2-C BC (40) Mac=MD5 export DES-C BC -SHA Kx=RSA Au=RSA
Enc=DES-C BC (56) Mac=SHA1 Medium Strength C iphers (> 64-bit and < 112-bit key) SSLv2 DES-C BC 3-MD5
Kx=RSA Au=RSA Enc=3DES-C BC (168) Mac=MD5 TLSv1 DES-C BC 3-SHA Kx=RSA Au=RSA Enc=3DES-C BC (168)
Mac=SHA1 High Strength C iphers (>= 112-bit key) SSLv2 RC 2-C BC -MD5 Kx=RSA Au=RSA Enc=RC 2-C BC (128)
Mac=MD5 TLSv1 AES128-SHA Kx=RSA Au=RSA Enc=AES-C BC (128) Mac=SHA1 AES256-SHA Kx=RSA Au=RSA
Enc=AES-C BC (256) Mac=SHA1 The fields above are : {O penSSL ciphernam e} Kx={key exchange}
Au={authentication} Enc={sym m etric encryption m ethod} Mac={m essage authentication code} {export flag}
References:
http://www.opens s l.org/docs /apps /ciphers .html
http://www.Indus Guard.org/u?cc4a822a
http://www.opens s l.org/~bodo/tls -cbc.txt
Alert ID: 84535 Found on: 2017-01-17 Severity: Info
SSL Cipher Suites Supported (tcp/993)
Open Status: NEW First Found: 2017-01-17
Description:
This s cript detects which SSL ciphers are s upported by the remote s ervice for encrypting communications .
Solution:
n/a
Result:
Here is the list of SSL ciphers supported by the rem ote server :Each group is reported per SSL Version.SSL
Version : TLSv1 Low Strength C iphers (<= 64-bit key) EXP-DES-C BC -SHA Kx=RSA(512) Au=RSA Enc=DES-C BC (40)
Mac=SHA1 export EXP-RC 2-C BC -MD5 Kx=RSA(512) Au=RSA Enc=RC 2-C BC (40) Mac=MD5 export EXP-RC 4-MD5
Kx=RSA(512) Au=RSA Enc=RC 4(40) Mac=MD5 export DES-C BC -SHA Kx=RSA Au=RSA Enc=DES-C BC (56)
Mac=SHA1 Medium Strength C iphers (> 64-bit and < 112-bit key) DES-C BC 3-SHA Kx=RSA Au=RSA Enc=3DES-
C BC (168) Mac=SHA1 High Strength C iphers (>= 112-bit key) AES128-SHA Kx=RSA Au=RSA Enc=AES-C BC (128)
Mac=SHA1 AES256-SHA Kx=RSA Au=RSA Enc=AES-C BC (256) Mac=SHA1 RC 4-MD5 Kx=RSA Au=RSA
Enc=RC 4(128) Mac=MD5 RC 4-SHA Kx=RSA Au=RSA Enc=RC 4(128) Mac=SHA1 SSL Version : SSLv3 Low Strength
C iphers (<= 64-bit key) EXP-DES-C BC -SHA Kx=RSA(512) Au=RSA Enc=DES-C BC (40) Mac=SHA1 export EXP-RC 2-
C BC -MD5 Kx=RSA(512) Au=RSA Enc=RC 2-C BC (40) Mac=MD5 export EXP-RC 4-MD5 Kx=RSA(512) Au=RSA
Enc=RC 4(40) Mac=MD5 export DES-C BC -SHA Kx=RSA Au=RSA Enc=DES-C BC (56) Mac=SHA1 Medium Strength
C iphers (> 64-bit and < 112-bit key) DES-C BC 3-SHA Kx=RSA Au=RSA Enc=3DES-C BC (168) Mac=SHA1 High
Strength C iphers (>= 112-bit key) AES128-SHA Kx=RSA Au=RSA Enc=AES-C BC (128) Mac=SHA1 AES256-SHA
Kx=RSA Au=RSA Enc=AES-C BC (256) Mac=SHA1 RC 4-MD5 Kx=RSA Au=RSA Enc=RC 4(128) Mac=MD5 RC 4-SHA
Kx=RSA Au=RSA Enc=RC 4(128) Mac=SHA1 SSL Version : SSLv2 Low Strength C iphers (<= 64-bit key) DES-C BC -
MD5 Kx=RSA Au=RSA Enc=DES-C BC (56) Mac=MD5 EXP-RC 2-C BC -MD5 Kx=RSA(512) Au=RSA Enc=RC 2-C BC (40)
Mac=MD5 export EXP-RC 4-MD5 Kx=RSA(512) Au=RSA Enc=RC 4(40) Mac=MD5 export Medium Strength C iphers
(> 64-bit and < 112-bit key) DES-C BC 3-MD5 Kx=RSA Au=RSA Enc=3DES-C BC (168) Mac=MD5 High Strength
C iphers (>= 112-bit key) RC 2-C BC -MD5 Kx=RSA Au=RSA Enc=RC 2-C BC (128) Mac=MD5 RC 4-MD5 Kx=RSA Au=RSA
Enc=RC 4(128) Mac=MD5 The fields above are : {O penSSL ciphernam e} Kx={key exchange}
Au={authentication} Enc={sym m etric encryption m ethod} Mac={m essage authentication code} {export flag}
References:
http://www.opens s l.org/docs /apps /ciphers .html
Alert ID: 84538 Found on: 2017-01-17 Severity: Info
Page 91 of 120
Scan Date: 2017-01-17
SSL Certificate commonName Mismatch (tcp/993)
Open Status: NEW First Found: 2017-01-17
Description:
This s ervice pres ents an SSL certificate for which the 'commonName' (CN) does not match the hos t name on which the
s ervice lis tens .
Solution:
If the machine has s everal names , make s ure that us ers connect to the s ervice through the DNS hos t name that
matches the common name in the certificate.
Result:
The host nam e known by IndusGuard is : rs202995.rs.hosteurope.deThe C om m on Nam e in the certificate is :
parallels panel
Alert ID: 84539 Found on: 2017-01-17 Severity: Info
OpenSSL Detection (tcp/993)
Open Status: NEW First Found: 2017-01-17
Description:
Bas ed on its behavior, it s eems that the remote s ervice is us ing the OpenSSL library to encrypt traffic.
Note that this check can only detect OpenSSL implementations that have enabled s upport for TLS extens ions (RFC 4366).
Solution:
n/a
References:
http://www.opens s l.org
Alert ID: 84542 Found on: 2017-01-17 Severity: Info
SSL Certificate Information (tcp/993)
Open Status: NEW First Found: 2017-01-17
Description:
This check connects to every SSL-related port and attempts to extract and dump the X.509 certificate.
Solution:
n/a
Result:
Subject Nam e: C ountry: USState/Province: VirginiaLocality: HerndonO rganization: ParallelsO rganization Unit:
Parallels PanelC om m on Nam e: Parallels PanelEm ail Address: info@ parallels.com Issuer Nam e: C ountry:
USState/Province: VirginiaLocality: HerndonO rganization: ParallelsO rganization Unit: Parallels PanelC om m on
Nam e: Parallels PanelEm ail Address: info@ parallels.com Serial Num ber: 50 9C DB A6 Version: 1Signature
Algorithm : SHA-1 With RSA EncryptionNot Valid Before: Nov 09 10:32:06 2012 GMTNot Valid After: Nov 09
10:32:06 2013 GMTPublic Key Info: Algorithm : RSA EncryptionKey Length: 2048 bitsPublic Key: 00 DA 42 9A E5 33
70 B0 DB DD C A 0D C 5 54 08 D3 6C D9 31 79 C E 65 D1 F5 11 3A 1F 5B 9E 0C 53 14 B1 19 13 6F 4E 5C BA 6C 98 EE
2B ED 60 55 E2 48 2E EA 16 9C 70 C 8 E6 94 42 DC 02 71 BA 59 3D DC 7B B3 F6 D7 0C E2 C F F5 53 47 8E 2F D3
AD 2B 68 1D 9D 03 95 5E B8 0C 3D 7C D2 EB B5 A3 35 A1 2D 58 ED 42 22 29 20 78 DE 1D 91 70 63 55 B7 0F B8
31 40 EB 43 F8 8B 03 B2 1D C 9 4C BE 61 2D 3E 5E D4 B9 09 06 88 47 C 9 1B 5B 9E 26 80 12 55 20 E5 D8 7E 66 44
AC C 2 F6 6E C 9 F5 B4 B6 2A 14 B7 8A 3F D1 3D 5C 3F 7E 25 3A 48 18 E1 13 FB 9D 7E C 1 E6 4D 12 1E 03 73 6C C 9
61 B0 48 89 AD AD 4A 4F 08 26 45 44 28 4E A7 B5 2B 15 E5 9A E2 D6 B7 5D 50 9E 0B F9 7E 0A 84 E1 62 6E E3 3F
EA C 0 C F D8 FF B9 3D 5E 0E 2C 74 C 5 D0 3E F3 16 E2 F1 E6 F5 D6 57 7F D4 92 F4 0F 8B 2E 2A 7B A0 B0 8C E5 10
Page 92 of 120
Scan Date: 2017-01-17
37 Exponent: 01 00 01 Signature Length: 256 bytes / 2048 bitsSignature: 00 22 9C F8 E3 1E 45 98 6C 25 E7 37 19
12 B5 B6 F0 2C 86 E0 E0 31 FB C B 36 46 D0 7E D9 F1 F1 7B 1E 6E 82 D4 EC FD E9 9A 73 4A A1 8F 68 37 58 34 A1
B1 9F 2C A3 C 3 2A 40 D9 9C C 2 48 E4 1F AA C D 5A A5 87 06 EF 5A 24 36 09 68 82 44 AD 39 52 FC 70 5C DE DF
09 29 2C E3 B5 17 1A 61 B7 95 0E A7 21 1F F2 4B EB F6 A9 4C 3F BC A6 7F DF 59 BA FF 3C D1 B6 11 FA B7 C 2 5A
51 7C 6C 07 38 22 9D 34 04 C B 2C 74 52 BB 81 37 FE 70 97 49 31 7A 90 33 85 86 3C BD 0D 9C 68 BD 8F A1 A7
74 C E 3F F1 93 62 19 0A 32 E6 EB C 4 77 AB 55 DF 16 5D 86 D9 0C 7A AE D3 A8 9E 56 92 C F 94 D1 70 F4 06 BD
33 11 35 49 A4 76 74 0C 11 9C 52 3D 2F 01 9C 6E AC 64 B0 2F 92 A6 B2 45 C 9 AA 30 9A 56 38 EB 52 54 11 03 0A
44 86 06 BB 53 6B 1B 11 F5 40 B0 E4 C 8 AC DD 39 92 C E 84 D2 AB D4 A8 F3 8A 3E 86 44 BD E9 3E Fingerprints :
SHA-256 Fingerprint: A0 82 92 DA 52 55 74 E1 6B 13 7D D0 B6 C 0 81 40 30 C F 3D BA A7 21 32 45 5D C 3 85 DF A7
F2 D9 88 SHA-1 Fingerprint: E5 6C 82 EE 62 05 DD 93 BF 17 E9 38 35 6E 70 BA A1 71 91 67 MD5 Fingerprint: 88 C 1
7E 0F 7E 06 68 98 95 31 38 85 AE 81 43 2B
Alert ID: 84544 Found on: 2017-01-17 Severity: Info
SSL / TLS Versions Supported (tcp/993)
Open Status: NEW First Found: 2017-01-17
Description:
This s cript detects which SSL and TLS vers ions are s upported by the remote s ervice for encrypting communications .
Solution:
n/a
Result:
This port supports SSLv2/SSLv3/TLSv1.0.
Alert ID: 84545 Found on: 2017-01-17 Severity: Info
IMAP Service Banner Retrieval (tcp/993)
Open Status: NEW First Found: 2017-01-17
Description:
An IMAP (Internet Mes s age Acces s Protocol) s erver is ins talled and running on the remote hos t.
Solution:
n/a
Result:
The rem ote im ap server banner is :* O K [C APABILITY IMAP4rev1 UIDPLUS C HILDREN NAMESPAC E
THREAD=O RDEREDSUBJEC T THREAD=REFERENC ES SO RT Q UO TA AUTH=C RAM-MD5 AUTH=PLAIN IDLE AC L
AC L2=UNIO N]
Alert ID: 84548 Found on: 2017-01-17 Severity: Info
SSL Session Resume Supported (tcp/465)
Open Status: NEW First Found: 2017-01-17
Description:
This s cript detects whether a hos t allows res uming SSL s es s ions by performing a full SSL hands hake to receive a
s es s ion ID, and then reconnecting with the previous ly us ed s es s ion ID. If the s erver accepts the s es s ion ID in the
s econd connection, the s erver maintains a cache of s es s ions that can be res umed.
Solution:
n/a
Result:
Page 93 of 120
Scan Date: 2017-01-17
This port supports resum ing SSLv3 sessions.
Alert ID: 84552 Found on: 2017-01-17 Severity: Info
SSL Cipher Block Chaining Cipher Suites Supported (tcp/465)
Open Status: NEW First Found: 2017-01-17
Description:
The remote hos t s upports the us e of SSL ciphers that operate in Cipher Block Chaining (CBC) mode. Thes e cipher s uites
offer additional s ecurity over Electronic Codebook (ECB) mode, but have the potential to leak information if us ed
improperly.
Solution:
n/a
Result:
Here is the list of SSL C BC ciphers supported by the rem ote server : Medium Strength C iphers (> 64-bit and <
112-bit key) TLSv1 EDH-RSA-DES-C BC 3-SHA Kx=DH Au=RSA Enc=3DES-C BC (168) Mac=SHA1 ADH-DES-C BC 3-SHA
Kx=DH Au=None Enc=3DES-C BC (168) Mac=SHA1 DES-C BC 3-SHA Kx=RSA Au=RSA Enc=3DES-C BC (168)
Mac=SHA1 High Strength C iphers (>= 112-bit key) TLSv1 DHE-RSA-AES128-SHA Kx=DH Au=RSA Enc=AES-
C BC (128) Mac=SHA1 DHE-RSA-AES256-SHA Kx=DH Au=RSA Enc=AES-C BC (256) Mac=SHA1 ADH-AES128-SHA
Kx=DH Au=None Enc=AES-C BC (128) Mac=SHA1 ADH-AES256-SHA Kx=DH Au=None Enc=AES-C BC (256)
Mac=SHA1 AES128-SHA Kx=RSA Au=RSA Enc=AES-C BC (128) Mac=SHA1 AES256-SHA Kx=RSA Au=RSA Enc=AES-
C BC (256) Mac=SHA1 The fields above are : {O penSSL ciphernam e} Kx={key exchange} Au={authentication}
Enc={sym m etric encryption m ethod} Mac={m essage authentication code} {export flag}
References:
http://www.opens s l.org/docs /apps /ciphers .html
http://www.Indus Guard.org/u?cc4a822a
http://www.opens s l.org/~bodo/tls -cbc.txt
Alert ID: 84554 Found on: 2017-01-17 Severity: Info
SSL Perfect Forward Secrecy Cipher Suites Supported (tcp/465)
Open Status: NEW First Found: 2017-01-17
Description:
The remote hos t s upports the us e of SSL ciphers that offer Perfect Forward Secrecy (PFS) encryption. Thes e cipher
s uites ens ure that recorded SSL traffic cannot be broken at a future date if the s erver's private key is compromis ed.
Solution:
n/a
Result:
Here is the list of SSL PFS ciphers supported by the rem ote server : Medium Strength C iphers (> 64-bit and < 112-
bit key) TLSv1 EDH-RSA-DES-C BC 3-SHA Kx=DH Au=RSA Enc=3DES-C BC (168) Mac=SHA1 High Strength C iphers
(>= 112-bit key) TLSv1 DHE-RSA-AES128-SHA Kx=DH Au=RSA Enc=AES-C BC (128) Mac=SHA1 DHE-RSA-AES256-
SHA Kx=DH Au=RSA Enc=AES-C BC (256) Mac=SHA1 The fields above are : {O penSSL ciphernam e} Kx={key
exchange} Au={authentication} Enc={sym m etric encryption m ethod} Mac={m essage authentication code}
{export flag}
References:
http://www.opens s l.org/docs /apps /ciphers .html
http://en.wikipedia.org/wiki/Diffie-Hellman_key_exchange
Page 94 of 120
Scan Date: 2017-01-17
http://en.wikipedia.org/wiki/Perfect_forward_s ecrecy
Alert ID: 84556 Found on: 2017-01-17 Severity: Info
SSL Cipher Suites Supported (tcp/465)
Open Status: NEW First Found: 2017-01-17
Description:
This s cript detects which SSL ciphers are s upported by the remote s ervice for encrypting communications .
Solution:
n/a
Result:
Here is the list of SSL ciphers supported by the rem ote server :Each group is reported per SSL Version.SSL
Version : TLSv1 Medium Strength C iphers (> 64-bit and < 112-bit key) EDH-RSA-DES-C BC 3-SHA Kx=DH Au=RSA
Enc=3DES-C BC (168) Mac=SHA1 ADH-DES-C BC 3-SHA Kx=DH Au=None Enc=3DES-C BC (168) Mac=SHA1 DES-
C BC 3-SHA Kx=RSA Au=RSA Enc=3DES-C BC (168) Mac=SHA1 High Strength C iphers (>= 112-bit key) DHE-RSA-
AES128-SHA Kx=DH Au=RSA Enc=AES-C BC (128) Mac=SHA1 DHE-RSA-AES256-SHA Kx=DH Au=RSA Enc=AES-
C BC (256) Mac=SHA1 ADH-AES128-SHA Kx=DH Au=None Enc=AES-C BC (128) Mac=SHA1 ADH-AES256-SHA Kx=DH
Au=None Enc=AES-C BC (256) Mac=SHA1 ADH-RC 4-MD5 Kx=DH Au=None Enc=RC 4(128) Mac=MD5 AES128-SHA
Kx=RSA Au=RSA Enc=AES-C BC (128) Mac=SHA1 AES256-SHA Kx=RSA Au=RSA Enc=AES-C BC (256) Mac=SHA1
RC 4-MD5 Kx=RSA Au=RSA Enc=RC 4(128) Mac=MD5 RC 4-SHA Kx=RSA Au=RSA Enc=RC 4(128) Mac=SHA1 SSL
Version : SSLv3 Medium Strength C iphers (> 64-bit and < 112-bit key) EDH-RSA-DES-C BC 3-SHA Kx=DH Au=RSA
Enc=3DES-C BC (168) Mac=SHA1 ADH-DES-C BC 3-SHA Kx=DH Au=None Enc=3DES-C BC (168) Mac=SHA1 DES-
C BC 3-SHA Kx=RSA Au=RSA Enc=3DES-C BC (168) Mac=SHA1 High Strength C iphers (>= 112-bit key) DHE-RSA-
AES128-SHA Kx=DH Au=RSA Enc=AES-C BC (128) Mac=SHA1 DHE-RSA-AES256-SHA Kx=DH Au=RSA Enc=AES-
C BC (256) Mac=SHA1 ADH-AES128-SHA Kx=DH Au=None Enc=AES-C BC (128) Mac=SHA1 ADH-AES256-SHA Kx=DH
Au=None Enc=AES-C BC (256) Mac=SHA1 ADH-RC 4-MD5 Kx=DH Au=None Enc=RC 4(128) Mac=MD5 AES128-SHA
Kx=RSA Au=RSA Enc=AES-C BC (128) Mac=SHA1 AES256-SHA Kx=RSA Au=RSA Enc=AES-C BC (256) Mac=SHA1
RC 4-MD5 Kx=RSA Au=RSA Enc=RC 4(128) Mac=MD5 RC 4-SHA Kx=RSA Au=RSA Enc=RC 4(128) Mac=SHA1 The
fields above are : {O penSSL ciphernam e} Kx={key exchange} Au={authentication} Enc={sym m etric
encryption m ethod} Mac={m essage authentication code} {export flag}
References:
http://www.opens s l.org/docs /apps /ciphers .html
Alert ID: 84559 Found on: 2017-01-17 Severity: Info
SSL Certificate commonName Mismatch (tcp/465)
Open Status: NEW First Found: 2017-01-17
Description:
This s ervice pres ents an SSL certificate for which the 'commonName' (CN) does not match the hos t name on which the
s ervice lis tens .
Solution:
If the machine has s everal names , make s ure that us ers connect to the s ervice through the DNS hos t name that
matches the common name in the certificate.
Result:
The host nam e known by IndusGuard is : rs202995.rs.hosteurope.deThe C om m on Nam e in the certificate is :
parallels panel
Page 95 of 120
Scan Date: 2017-01-17
Alert ID: 84560 Found on: 2017-01-17 Severity: Info
OpenSSL Detection (tcp/465)
Open Status: NEW First Found: 2017-01-17
Description:
Bas ed on its behavior, it s eems that the remote s ervice is us ing the OpenSSL library to encrypt traffic.
Note that this check can only detect OpenSSL implementations that have enabled s upport for TLS extens ions (RFC 4366).
Solution:
n/a
References:
http://www.opens s l.org
Alert ID: 84563 Found on: 2017-01-17 Severity: Info
SSL Certificate Information (tcp/465)
Open Status: NEW First Found: 2017-01-17
Description:
This check connects to every SSL-related port and attempts to extract and dump the X.509 certificate.
Solution:
n/a
Result:
Subject Nam e: C ountry: USState/Province: VirginiaLocality: HerndonO rganization: ParallelsO rganization Unit:
Parallels PanelC om m on Nam e: Parallels PanelEm ail Address: info@ parallels.com Issuer Nam e: C ountry:
USState/Province: VirginiaLocality: HerndonO rganization: ParallelsO rganization Unit: Parallels PanelC om m on
Nam e: Parallels PanelEm ail Address: info@ parallels.com Serial Num ber: 50 9C DB A6 Version: 1Signature
Algorithm : SHA-1 With RSA EncryptionNot Valid Before: Nov 09 10:32:06 2012 GMTNot Valid After: Nov 09
10:32:06 2013 GMTPublic Key Info: Algorithm : RSA EncryptionKey Length: 2048 bitsPublic Key: 00 DA 42 9A E5 33
70 B0 DB DD C A 0D C 5 54 08 D3 6C D9 31 79 C E 65 D1 F5 11 3A 1F 5B 9E 0C 53 14 B1 19 13 6F 4E 5C BA 6C 98 EE
2B ED 60 55 E2 48 2E EA 16 9C 70 C 8 E6 94 42 DC 02 71 BA 59 3D DC 7B B3 F6 D7 0C E2 C F F5 53 47 8E 2F D3
AD 2B 68 1D 9D 03 95 5E B8 0C 3D 7C D2 EB B5 A3 35 A1 2D 58 ED 42 22 29 20 78 DE 1D 91 70 63 55 B7 0F B8
31 40 EB 43 F8 8B 03 B2 1D C 9 4C BE 61 2D 3E 5E D4 B9 09 06 88 47 C 9 1B 5B 9E 26 80 12 55 20 E5 D8 7E 66 44
AC C 2 F6 6E C 9 F5 B4 B6 2A 14 B7 8A 3F D1 3D 5C 3F 7E 25 3A 48 18 E1 13 FB 9D 7E C 1 E6 4D 12 1E 03 73 6C C 9
61 B0 48 89 AD AD 4A 4F 08 26 45 44 28 4E A7 B5 2B 15 E5 9A E2 D6 B7 5D 50 9E 0B F9 7E 0A 84 E1 62 6E E3 3F
EA C 0 C F D8 FF B9 3D 5E 0E 2C 74 C 5 D0 3E F3 16 E2 F1 E6 F5 D6 57 7F D4 92 F4 0F 8B 2E 2A 7B A0 B0 8C E5 10
37 Exponent: 01 00 01 Signature Length: 256 bytes / 2048 bitsSignature: 00 22 9C F8 E3 1E 45 98 6C 25 E7 37 19
12 B5 B6 F0 2C 86 E0 E0 31 FB C B 36 46 D0 7E D9 F1 F1 7B 1E 6E 82 D4 EC FD E9 9A 73 4A A1 8F 68 37 58 34 A1
B1 9F 2C A3 C 3 2A 40 D9 9C C 2 48 E4 1F AA C D 5A A5 87 06 EF 5A 24 36 09 68 82 44 AD 39 52 FC 70 5C DE DF
09 29 2C E3 B5 17 1A 61 B7 95 0E A7 21 1F F2 4B EB F6 A9 4C 3F BC A6 7F DF 59 BA FF 3C D1 B6 11 FA B7 C 2 5A
51 7C 6C 07 38 22 9D 34 04 C B 2C 74 52 BB 81 37 FE 70 97 49 31 7A 90 33 85 86 3C BD 0D 9C 68 BD 8F A1 A7
74 C E 3F F1 93 62 19 0A 32 E6 EB C 4 77 AB 55 DF 16 5D 86 D9 0C 7A AE D3 A8 9E 56 92 C F 94 D1 70 F4 06 BD
33 11 35 49 A4 76 74 0C 11 9C 52 3D 2F 01 9C 6E AC 64 B0 2F 92 A6 B2 45 C 9 AA 30 9A 56 38 EB 52 54 11 03 0A
44 86 06 BB 53 6B 1B 11 F5 40 B0 E4 C 8 AC DD 39 92 C E 84 D2 AB D4 A8 F3 8A 3E 86 44 BD E9 3E Fingerprints :
SHA-256 Fingerprint: A0 82 92 DA 52 55 74 E1 6B 13 7D D0 B6 C 0 81 40 30 C F 3D BA A7 21 32 45 5D C 3 85 DF A7
F2 D9 88 SHA-1 Fingerprint: E5 6C 82 EE 62 05 DD 93 BF 17 E9 38 35 6E 70 BA A1 71 91 67 MD5 Fingerprint: 88 C 1
7E 0F 7E 06 68 98 95 31 38 85 AE 81 43 2B
Alert ID: 84565 Found on: 2017-01-17 Severity: Info
SSL / TLS Versions Supported (tcp/465)
Page 96 of 120
Scan Date: 2017-01-17
Open Status: NEW First Found: 2017-01-17
Description:
This s cript detects which SSL and TLS vers ions are s upported by the remote s ervice for encrypting communications .
Solution:
n/a
Result:
This port supports SSLv3/TLSv1.0.
Alert ID: 84566 Found on: 2017-01-17 Severity: Info
SMTP Authentication Methods (tcp/465)
Open Status: NEW First Found: 2017-01-17
Description:
The remote SMTP s erver advertis es that it s upports authentication.
Solution:
Review the lis t of methods and whether they're available over an encrypted channel.
Result:
The following authentication m ethods are advertised by the SMTPserver with encryption : C RAM-MD5 DIGEST-MD5
LO GIN PLAIN
References:
http://tools .ietf.org/html/rfc4422
http://tools .ietf.org/html/rfc4954
Alert ID: 84567 Found on: 2017-01-17 Severity: Info
SMTP Server Detection (tcp/465)
Open Status: NEW First Found: 2017-01-17
Description:
The remote hos t is running a mail (SMTP) s erver on this port.
Since SMTP s ervers are the targets of s pammers , it is recommended you dis able it if you do not us e it.
Solution:
Dis able this s ervice if you do not us e it, or filter incoming traffic to this port.
Result:
Rem ote SMTP server banner :220 rs202995.rs.hosteurope.de ESMTP Postfix (Ubuntu)
Alert ID: 84571 Found on: 2017-01-17 Severity: Info
SSL Cipher Block Chaining Cipher Suites Supported (tcp/143)
Open Status: NEW First Found: 2017-01-17
Description:
The remote hos t s upports the us e of SSL ciphers that operate in Cipher Block Chaining (CBC) mode. Thes e cipher s uites
offer additional s ecurity over Electronic Codebook (ECB) mode, but have the potential to leak information if us ed
Page 97 of 120
Scan Date: 2017-01-17
improperly.
Solution:
n/a
Result:
Here is the list of SSL C BC ciphers supported by the rem ote server : Low Strength C iphers (<= 64-bit key) TLSv1
EXP-DES-C BC -SHA Kx=RSA(512) Au=RSA Enc=DES-C BC (40) Mac=SHA1 export EXP-RC 2-C BC -MD5 Kx=RSA(512)
Au=RSA Enc=RC 2-C BC (40) Mac=MD5 export DES-C BC -SHA Kx=RSA Au=RSA Enc=DES-C BC (56) Mac=SHA1
Medium Strength C iphers (> 64-bit and < 112-bit key) TLSv1 DES-C BC 3-SHA Kx=RSA Au=RSA Enc=3DES-
C BC (168) Mac=SHA1 High Strength C iphers (>= 112-bit key) TLSv1 AES128-SHA Kx=RSA Au=RSA Enc=AES-
C BC (128) Mac=SHA1 AES256-SHA Kx=RSA Au=RSA Enc=AES-C BC (256) Mac=SHA1 The fields above are :
{O penSSL ciphernam e} Kx={key exchange} Au={authentication} Enc={sym m etric encryption m ethod}
Mac={m essage authentication code} {export flag}
References:
http://www.opens s l.org/docs /apps /ciphers .html
http://www.Indus Guard.org/u?cc4a822a
http://www.opens s l.org/~bodo/tls -cbc.txt
Alert ID: 84574 Found on: 2017-01-17 Severity: Info
SSL Cipher Suites Supported (tcp/143)
Open Status: NEW First Found: 2017-01-17
Description:
This s cript detects which SSL ciphers are s upported by the remote s ervice for encrypting communications .
Solution:
n/a
Result:
Here is the list of SSL ciphers supported by the rem ote server :Each group is reported per SSL Version.SSL
Version : TLSv1 Low Strength C iphers (<= 64-bit key) EXP-DES-C BC -SHA Kx=RSA(512) Au=RSA Enc=DES-C BC (40)
Mac=SHA1 export EXP-RC 2-C BC -MD5 Kx=RSA(512) Au=RSA Enc=RC 2-C BC (40) Mac=MD5 export EXP-RC 4-MD5
Kx=RSA(512) Au=RSA Enc=RC 4(40) Mac=MD5 export DES-C BC -SHA Kx=RSA Au=RSA Enc=DES-C BC (56)
Mac=SHA1 Medium Strength C iphers (> 64-bit and < 112-bit key) DES-C BC 3-SHA Kx=RSA Au=RSA Enc=3DES-
C BC (168) Mac=SHA1 High Strength C iphers (>= 112-bit key) AES128-SHA Kx=RSA Au=RSA Enc=AES-C BC (128)
Mac=SHA1 AES256-SHA Kx=RSA Au=RSA Enc=AES-C BC (256) Mac=SHA1 RC 4-MD5 Kx=RSA Au=RSA
Enc=RC 4(128) Mac=MD5 RC 4-SHA Kx=RSA Au=RSA Enc=RC 4(128) Mac=SHA1 The fields above are : {O penSSL
ciphernam e} Kx={key exchange} Au={authentication} Enc={sym m etric encryption m ethod} Mac={m essage
authentication code} {export flag}
References:
http://www.opens s l.org/docs /apps /ciphers .html
Alert ID: 84577 Found on: 2017-01-17 Severity: Info
SSL Certificate commonName Mismatch (tcp/143)
Open Status: NEW First Found: 2017-01-17
Description:
This s ervice pres ents an SSL certificate for which the 'commonName' (CN) does not match the hos t name on which the
s ervice lis tens .
Page 98 of 120
Scan Date: 2017-01-17
Solution:
If the machine has s everal names , make s ure that us ers connect to the s ervice through the DNS hos t name that
matches the common name in the certificate.
Result:
The host nam e known by IndusGuard is : rs202995.rs.hosteurope.deThe C om m on Nam e in the certificate is :
parallels panel
Alert ID: 84578 Found on: 2017-01-17 Severity: Info
OpenSSL Detection (tcp/143)
Open Status: NEW First Found: 2017-01-17
Description:
Bas ed on its behavior, it s eems that the remote s ervice is us ing the OpenSSL library to encrypt traffic.
Note that this check can only detect OpenSSL implementations that have enabled s upport for TLS extens ions (RFC 4366).
Solution:
n/a
References:
http://www.opens s l.org
Alert ID: 84581 Found on: 2017-01-17 Severity: Info
SSL Certificate Information (tcp/143)
Open Status: NEW First Found: 2017-01-17
Description:
This check connects to every SSL-related port and attempts to extract and dump the X.509 certificate.
Solution:
n/a
Result:
Subject Nam e: C ountry: USState/Province: VirginiaLocality: HerndonO rganization: ParallelsO rganization Unit:
Parallels PanelC om m on Nam e: Parallels PanelEm ail Address: info@ parallels.com Issuer Nam e: C ountry:
USState/Province: VirginiaLocality: HerndonO rganization: ParallelsO rganization Unit: Parallels PanelC om m on
Nam e: Parallels PanelEm ail Address: info@ parallels.com Serial Num ber: 50 9C DB A6 Version: 1Signature
Algorithm : SHA-1 With RSA EncryptionNot Valid Before: Nov 09 10:32:06 2012 GMTNot Valid After: Nov 09
10:32:06 2013 GMTPublic Key Info: Algorithm : RSA EncryptionKey Length: 2048 bitsPublic Key: 00 DA 42 9A E5 33
70 B0 DB DD C A 0D C 5 54 08 D3 6C D9 31 79 C E 65 D1 F5 11 3A 1F 5B 9E 0C 53 14 B1 19 13 6F 4E 5C BA 6C 98 EE
2B ED 60 55 E2 48 2E EA 16 9C 70 C 8 E6 94 42 DC 02 71 BA 59 3D DC 7B B3 F6 D7 0C E2 C F F5 53 47 8E 2F D3
AD 2B 68 1D 9D 03 95 5E B8 0C 3D 7C D2 EB B5 A3 35 A1 2D 58 ED 42 22 29 20 78 DE 1D 91 70 63 55 B7 0F B8
31 40 EB 43 F8 8B 03 B2 1D C 9 4C BE 61 2D 3E 5E D4 B9 09 06 88 47 C 9 1B 5B 9E 26 80 12 55 20 E5 D8 7E 66 44
AC C 2 F6 6E C 9 F5 B4 B6 2A 14 B7 8A 3F D1 3D 5C 3F 7E 25 3A 48 18 E1 13 FB 9D 7E C 1 E6 4D 12 1E 03 73 6C C 9
61 B0 48 89 AD AD 4A 4F 08 26 45 44 28 4E A7 B5 2B 15 E5 9A E2 D6 B7 5D 50 9E 0B F9 7E 0A 84 E1 62 6E E3 3F
EA C 0 C F D8 FF B9 3D 5E 0E 2C 74 C 5 D0 3E F3 16 E2 F1 E6 F5 D6 57 7F D4 92 F4 0F 8B 2E 2A 7B A0 B0 8C E5 10
37 Exponent: 01 00 01 Signature Length: 256 bytes / 2048 bitsSignature: 00 22 9C F8 E3 1E 45 98 6C 25 E7 37 19
12 B5 B6 F0 2C 86 E0 E0 31 FB C B 36 46 D0 7E D9 F1 F1 7B 1E 6E 82 D4 EC FD E9 9A 73 4A A1 8F 68 37 58 34 A1
B1 9F 2C A3 C 3 2A 40 D9 9C C 2 48 E4 1F AA C D 5A A5 87 06 EF 5A 24 36 09 68 82 44 AD 39 52 FC 70 5C DE DF
09 29 2C E3 B5 17 1A 61 B7 95 0E A7 21 1F F2 4B EB F6 A9 4C 3F BC A6 7F DF 59 BA FF 3C D1 B6 11 FA B7 C 2 5A
51 7C 6C 07 38 22 9D 34 04 C B 2C 74 52 BB 81 37 FE 70 97 49 31 7A 90 33 85 86 3C BD 0D 9C 68 BD 8F A1 A7
74 C E 3F F1 93 62 19 0A 32 E6 EB C 4 77 AB 55 DF 16 5D 86 D9 0C 7A AE D3 A8 9E 56 92 C F 94 D1 70 F4 06 BD
33 11 35 49 A4 76 74 0C 11 9C 52 3D 2F 01 9C 6E AC 64 B0 2F 92 A6 B2 45 C 9 AA 30 9A 56 38 EB 52 54 11 03 0A
44 86 06 BB 53 6B 1B 11 F5 40 B0 E4 C 8 AC DD 39 92 C E 84 D2 AB D4 A8 F3 8A 3E 86 44 BD E9 3E Fingerprints :
Page 99 of 120
Scan Date: 2017-01-17
SHA-256 Fingerprint: A0 82 92 DA 52 55 74 E1 6B 13 7D D0 B6 C 0 81 40 30 C F 3D BA A7 21 32 45 5D C 3 85 DF A7
F2 D9 88 SHA-1 Fingerprint: E5 6C 82 EE 62 05 DD 93 BF 17 E9 38 35 6E 70 BA A1 71 91 67 MD5 Fingerprint: 88 C 1
7E 0F 7E 06 68 98 95 31 38 85 AE 81 43 2B
Alert ID: 84583 Found on: 2017-01-17 Severity: Info
SSL / TLS Versions Supported (tcp/143)
Open Status: NEW First Found: 2017-01-17
Description:
This s cript detects which SSL and TLS vers ions are s upported by the remote s ervice for encrypting communications .
Solution:
n/a
Result:
This port supports TLSv1.0.
Alert ID: 84584 Found on: 2017-01-17 Severity: Info
IMAP Service STARTTLS Command Support (tcp/143)
Open Status: NEW First Found: 2017-01-17
Description:
The remote IMAP s ervice s upports the us e of the 'STARTTLS' command to s witch from a plaintext to an encrypted
communications channel.
Solution:
n/a
Result:
Here is the IMAP server's SSL certificate that IndusGuard was able tocollect after sending a 'STARTTLS' com m and
:------------------------------ snip ------------------------------Subject Nam e: C ountry: USState/Province: VirginiaLocality:
HerndonO rganization: ParallelsO rganization Unit: Parallels PanelC om m on Nam e: Parallels PanelEm ail Address:
info@ parallels.com Issuer Nam e: C ountry: USState/Province: VirginiaLocality: HerndonO rganization:
ParallelsO rganization Unit: Parallels PanelC om m on Nam e: Parallels PanelEm ail Address:
info@ parallels.com Serial Num ber: 50 9C DB A6 Version: 1Signature Algorithm : SHA-1 With RSA EncryptionNot
Valid Before: Nov 09 10:32:06 2012 GMTNot Valid After: Nov 09 10:32:06 2013 GMTPublic Key Info: Algorithm :
RSA EncryptionKey Length: 2048 bitsPublic Key: 00 DA 42 9A E5 33 70 B0 DB DD C A 0D C 5 54 08 D3 6C D9 31 79
C E 65 D1 F5 11 3A 1F 5B 9E 0C 53 14 B1 19 13 6F 4E 5C BA 6C 98 EE 2B ED 60 55 E2 48 2E EA 16 9C 70 C 8 E6 94
42 DC 02 71 BA 59 3D DC 7B B3 F6 D7 0C E2 C F F5 53 47 8E 2F D3 AD 2B 68 1D 9D 03 95 5E B8 0C 3D 7C D2 EB
B5 A3 35 A1 2D 58 ED 42 22 29 20 78 DE 1D 91 70 63 55 B7 0F B8 31 40 EB 43 F8 8B 03 B2 1D C 9 4C BE 61 2D 3E
5E D4 B9 09 06 88 47 C 9 1B 5B 9E 26 80 12 55 20 E5 D8 7E 66 44 AC C 2 F6 6E C 9 F5 B4 B6 2A 14 B7 8A 3F D1 3D
5C 3F 7E 25 3A 48 18 E1 13 FB 9D 7E C 1 E6 4D 12 1E 03 73 6C C 9 61 B0 48 89 AD AD 4A 4F 08 26 45 44 28 4E A7
B5 2B 15 E5 9A E2 D6 B7 5D 50 9E 0B F9 7E 0A 84 E1 62 6E E3 3F EA C 0 C F D8 FF B9 3D 5E 0E 2C 74 C 5 D0 3E F3
16 E2 F1 E6 F5 D6 57 7F D4 92 F4 0F 8B 2E 2A 7B A0 B0 8C E5 10 37 Exponent: 01 00 01 Signature Length: 256
bytes / 2048 bitsSignature: 00 22 9C F8 E3 1E 45 98 6C 25 E7 37 19 12 B5 B6 F0 2C 86 E0 E0 31 FB C B 36 46 D0
7E D9 F1 F1 7B 1E 6E 82 D4 EC FD E9 9A 73 4A A1 8F 68 37 58 34 A1 B1 9F 2C A3 C 3 2A 40 D9 9C C 2 48 E4 1F AA
C D 5A A5 87 06 EF 5A 24 36 09 68 82 44 AD 39 52 FC 70 5C DE DF 09 29 2C E3 B5 17 1A 61 B7 95 0E A7 21 1F F2
4B EB F6 A9 4C 3F BC A6 7F DF 59 BA FF 3C D1 B6 11 FA B7 C 2 5A 51 7C 6C 07 38 22 9D 34 04 C B 2C 74 52 BB
81 37 FE 70 97 49 31 7A 90 33 85 86 3C BD 0D 9C 68 BD 8F A1 A7 74 C E 3F F1 93 62 19 0A 32 E6 EB C 4 77 AB 55
DF 16 5D 86 D9 0C 7A AE D3 A8 9E 56 92 C F 94 D1 70 F4 06 BD 33 11 35 49 A4 76 74 0C 11 9C 52 3D 2F 01 9C
6E AC 64 B0 2F 92 A6 B2 45 C 9 AA 30 9A 56 38 EB 52 54 11 03 0A 44 86 06 BB 53 6B 1B 11 F5 40 B0 E4 C 8 AC DD
39 92 C E 84 D2 AB D4 A8 F3 8A 3E 86 44 BD E9 3E ------------------------------ snip ------------------------------
References:
http://en.wikipedia.org/wiki/STARTTLS
Page 100 of 120
Scan Date: 2017-01-17
http://tools .ietf.org/html/rfc2595
Alert ID: 84585 Found on: 2017-01-17 Severity: Info
IMAP Service Banner Retrieval (tcp/143)
Open Status: NEW First Found: 2017-01-17
Description:
An IMAP (Internet Mes s age Acces s Protocol) s erver is ins talled and running on the remote hos t.
Solution:
n/a
Result:
The rem ote im ap server banner is :* O K [C APABILITY IMAP4rev1 UIDPLUS C HILDREN NAMESPAC E
THREAD=O RDEREDSUBJEC T THREAD=REFERENC ES SO RT Q UO TA AUTH=C RAM-MD5 AUTH=PLAIN IDLE AC L
AC L2=UNIO N STARTTLS]
Alert ID: 84589 Found on: 2017-01-17 Severity: Info
SSL Cipher Block Chaining Cipher Suites Supported (tcp/110)
Open Status: NEW First Found: 2017-01-17
Description:
The remote hos t s upports the us e of SSL ciphers that operate in Cipher Block Chaining (CBC) mode. Thes e cipher s uites
offer additional s ecurity over Electronic Codebook (ECB) mode, but have the potential to leak information if us ed
improperly.
Solution:
n/a
Result:
Here is the list of SSL C BC ciphers supported by the rem ote server : Low Strength C iphers (<= 64-bit key) TLSv1
EXP-DES-C BC -SHA Kx=RSA(512) Au=RSA Enc=DES-C BC (40) Mac=SHA1 export EXP-RC 2-C BC -MD5 Kx=RSA(512)
Au=RSA Enc=RC 2-C BC (40) Mac=MD5 export DES-C BC -SHA Kx=RSA Au=RSA Enc=DES-C BC (56) Mac=SHA1
Medium Strength C iphers (> 64-bit and < 112-bit key) TLSv1 DES-C BC 3-SHA Kx=RSA Au=RSA Enc=3DES-
C BC (168) Mac=SHA1 High Strength C iphers (>= 112-bit key) TLSv1 AES128-SHA Kx=RSA Au=RSA Enc=AES-
C BC (128) Mac=SHA1 AES256-SHA Kx=RSA Au=RSA Enc=AES-C BC (256) Mac=SHA1 The fields above are :
{O penSSL ciphernam e} Kx={key exchange} Au={authentication} Enc={sym m etric encryption m ethod}
Mac={m essage authentication code} {export flag}
References:
http://www.opens s l.org/docs /apps /ciphers .html
http://www.Indus Guard.org/u?cc4a822a
http://www.opens s l.org/~bodo/tls -cbc.txt
Alert ID: 84592 Found on: 2017-01-17 Severity: Info
SSL Cipher Suites Supported (tcp/110)
Open Status: NEW First Found: 2017-01-17
Description:
Page 101 of 120
Scan Date: 2017-01-17
This s cript detects which SSL ciphers are s upported by the remote s ervice for encrypting communications .
Solution:
n/a
Result:
Here is the list of SSL ciphers supported by the rem ote server :Each group is reported per SSL Version.SSL
Version : TLSv1 Low Strength C iphers (<= 64-bit key) EXP-DES-C BC -SHA Kx=RSA(512) Au=RSA Enc=DES-C BC (40)
Mac=SHA1 export EXP-RC 2-C BC -MD5 Kx=RSA(512) Au=RSA Enc=RC 2-C BC (40) Mac=MD5 export EXP-RC 4-MD5
Kx=RSA(512) Au=RSA Enc=RC 4(40) Mac=MD5 export DES-C BC -SHA Kx=RSA Au=RSA Enc=DES-C BC (56)
Mac=SHA1 Medium Strength C iphers (> 64-bit and < 112-bit key) DES-C BC 3-SHA Kx=RSA Au=RSA Enc=3DES-
C BC (168) Mac=SHA1 High Strength C iphers (>= 112-bit key) AES128-SHA Kx=RSA Au=RSA Enc=AES-C BC (128)
Mac=SHA1 AES256-SHA Kx=RSA Au=RSA Enc=AES-C BC (256) Mac=SHA1 RC 4-MD5 Kx=RSA Au=RSA
Enc=RC 4(128) Mac=MD5 RC 4-SHA Kx=RSA Au=RSA Enc=RC 4(128) Mac=SHA1 The fields above are : {O penSSL
ciphernam e} Kx={key exchange} Au={authentication} Enc={sym m etric encryption m ethod} Mac={m essage
authentication code} {export flag}
References:
http://www.opens s l.org/docs /apps /ciphers .html
Alert ID: 84595 Found on: 2017-01-17 Severity: Info
SSL Certificate commonName Mismatch (tcp/110)
Open Status: NEW First Found: 2017-01-17
Description:
This s ervice pres ents an SSL certificate for which the 'commonName' (CN) does not match the hos t name on which the
s ervice lis tens .
Solution:
If the machine has s everal names , make s ure that us ers connect to the s ervice through the DNS hos t name that
matches the common name in the certificate.
Result:
The host nam e known by IndusGuard is : rs202995.rs.hosteurope.deThe C om m on Nam e in the certificate is :
parallels panel
Alert ID: 84596 Found on: 2017-01-17 Severity: Info
OpenSSL Detection (tcp/110)
Open Status: NEW First Found: 2017-01-17
Description:
Bas ed on its behavior, it s eems that the remote s ervice is us ing the OpenSSL library to encrypt traffic.
Note that this check can only detect OpenSSL implementations that have enabled s upport for TLS extens ions (RFC 4366).
Solution:
n/a
References:
http://www.opens s l.org
Alert ID: 84599 Found on: 2017-01-17 Severity: Info
SSL Certificate Information (tcp/110)
Page 102 of 120
Scan Date: 2017-01-17
Open Status: NEW First Found: 2017-01-17
Description:
This check connects to every SSL-related port and attempts to extract and dump the X.509 certificate.
Solution:
n/a
Result:
Subject Nam e: C ountry: USState/Province: VirginiaLocality: HerndonO rganization: ParallelsO rganization Unit:
Parallels PanelC om m on Nam e: Parallels PanelEm ail Address: info@ parallels.com Issuer Nam e: C ountry:
USState/Province: VirginiaLocality: HerndonO rganization: ParallelsO rganization Unit: Parallels PanelC om m on
Nam e: Parallels PanelEm ail Address: info@ parallels.com Serial Num ber: 50 9C DB A6 Version: 1Signature
Algorithm : SHA-1 With RSA EncryptionNot Valid Before: Nov 09 10:32:06 2012 GMTNot Valid After: Nov 09
10:32:06 2013 GMTPublic Key Info: Algorithm : RSA EncryptionKey Length: 2048 bitsPublic Key: 00 DA 42 9A E5 33
70 B0 DB DD C A 0D C 5 54 08 D3 6C D9 31 79 C E 65 D1 F5 11 3A 1F 5B 9E 0C 53 14 B1 19 13 6F 4E 5C BA 6C 98 EE
2B ED 60 55 E2 48 2E EA 16 9C 70 C 8 E6 94 42 DC 02 71 BA 59 3D DC 7B B3 F6 D7 0C E2 C F F5 53 47 8E 2F D3
AD 2B 68 1D 9D 03 95 5E B8 0C 3D 7C D2 EB B5 A3 35 A1 2D 58 ED 42 22 29 20 78 DE 1D 91 70 63 55 B7 0F B8
31 40 EB 43 F8 8B 03 B2 1D C 9 4C BE 61 2D 3E 5E D4 B9 09 06 88 47 C 9 1B 5B 9E 26 80 12 55 20 E5 D8 7E 66 44
AC C 2 F6 6E C 9 F5 B4 B6 2A 14 B7 8A 3F D1 3D 5C 3F 7E 25 3A 48 18 E1 13 FB 9D 7E C 1 E6 4D 12 1E 03 73 6C C 9
61 B0 48 89 AD AD 4A 4F 08 26 45 44 28 4E A7 B5 2B 15 E5 9A E2 D6 B7 5D 50 9E 0B F9 7E 0A 84 E1 62 6E E3 3F
EA C 0 C F D8 FF B9 3D 5E 0E 2C 74 C 5 D0 3E F3 16 E2 F1 E6 F5 D6 57 7F D4 92 F4 0F 8B 2E 2A 7B A0 B0 8C E5 10
37 Exponent: 01 00 01 Signature Length: 256 bytes / 2048 bitsSignature: 00 22 9C F8 E3 1E 45 98 6C 25 E7 37 19
12 B5 B6 F0 2C 86 E0 E0 31 FB C B 36 46 D0 7E D9 F1 F1 7B 1E 6E 82 D4 EC FD E9 9A 73 4A A1 8F 68 37 58 34 A1
B1 9F 2C A3 C 3 2A 40 D9 9C C 2 48 E4 1F AA C D 5A A5 87 06 EF 5A 24 36 09 68 82 44 AD 39 52 FC 70 5C DE DF
09 29 2C E3 B5 17 1A 61 B7 95 0E A7 21 1F F2 4B EB F6 A9 4C 3F BC A6 7F DF 59 BA FF 3C D1 B6 11 FA B7 C 2 5A
51 7C 6C 07 38 22 9D 34 04 C B 2C 74 52 BB 81 37 FE 70 97 49 31 7A 90 33 85 86 3C BD 0D 9C 68 BD 8F A1 A7
74 C E 3F F1 93 62 19 0A 32 E6 EB C 4 77 AB 55 DF 16 5D 86 D9 0C 7A AE D3 A8 9E 56 92 C F 94 D1 70 F4 06 BD
33 11 35 49 A4 76 74 0C 11 9C 52 3D 2F 01 9C 6E AC 64 B0 2F 92 A6 B2 45 C 9 AA 30 9A 56 38 EB 52 54 11 03 0A
44 86 06 BB 53 6B 1B 11 F5 40 B0 E4 C 8 AC DD 39 92 C E 84 D2 AB D4 A8 F3 8A 3E 86 44 BD E9 3E Fingerprints :
SHA-256 Fingerprint: A0 82 92 DA 52 55 74 E1 6B 13 7D D0 B6 C 0 81 40 30 C F 3D BA A7 21 32 45 5D C 3 85 DF A7
F2 D9 88 SHA-1 Fingerprint: E5 6C 82 EE 62 05 DD 93 BF 17 E9 38 35 6E 70 BA A1 71 91 67 MD5 Fingerprint: 88 C 1
7E 0F 7E 06 68 98 95 31 38 85 AE 81 43 2B
Alert ID: 84601 Found on: 2017-01-17 Severity: Info
SSL / TLS Versions Supported (tcp/110)
Open Status: NEW First Found: 2017-01-17
Description:
This s cript detects which SSL and TLS vers ions are s upported by the remote s ervice for encrypting communications .
Solution:
n/a
Result:
This port supports TLSv1.0.
Alert ID: 84602 Found on: 2017-01-17 Severity: Info
POP3 Service STLS Command Support (tcp/110)
Open Status: NEW First Found: 2017-01-17
Description:
The remote POP3 s ervice s upports the us e of the 'STLS' command to s witch from a plaintext to an encrypted
communications channel.
Page 103 of 120
Scan Date: 2017-01-17
Solution:
n/a
Result:
Here is the PO P3 server's SSL certificate that IndusGuard was able tocollect after sending a 'STLS' com m and :-------
----------------------- snip ------------------------------Subject Nam e: C ountry: USState/Province: VirginiaLocality:
HerndonO rganization: ParallelsO rganization Unit: Parallels PanelC om m on Nam e: Parallels PanelEm ail Address:
info@ parallels.com Issuer Nam e: C ountry: USState/Province: VirginiaLocality: HerndonO rganization:
ParallelsO rganization Unit: Parallels PanelC om m on Nam e: Parallels PanelEm ail Address:
info@ parallels.com Serial Num ber: 50 9C DB A6 Version: 1Signature Algorithm : SHA-1 With RSA EncryptionNot
Valid Before: Nov 09 10:32:06 2012 GMTNot Valid After: Nov 09 10:32:06 2013 GMTPublic Key Info: Algorithm :
RSA EncryptionKey Length: 2048 bitsPublic Key: 00 DA 42 9A E5 33 70 B0 DB DD C A 0D C 5 54 08 D3 6C D9 31 79
C E 65 D1 F5 11 3A 1F 5B 9E 0C 53 14 B1 19 13 6F 4E 5C BA 6C 98 EE 2B ED 60 55 E2 48 2E EA 16 9C 70 C 8 E6 94
42 DC 02 71 BA 59 3D DC 7B B3 F6 D7 0C E2 C F F5 53 47 8E 2F D3 AD 2B 68 1D 9D 03 95 5E B8 0C 3D 7C D2 EB
B5 A3 35 A1 2D 58 ED 42 22 29 20 78 DE 1D 91 70 63 55 B7 0F B8 31 40 EB 43 F8 8B 03 B2 1D C 9 4C BE 61 2D 3E
5E D4 B9 09 06 88 47 C 9 1B 5B 9E 26 80 12 55 20 E5 D8 7E 66 44 AC C 2 F6 6E C 9 F5 B4 B6 2A 14 B7 8A 3F D1 3D
5C 3F 7E 25 3A 48 18 E1 13 FB 9D 7E C 1 E6 4D 12 1E 03 73 6C C 9 61 B0 48 89 AD AD 4A 4F 08 26 45 44 28 4E A7
B5 2B 15 E5 9A E2 D6 B7 5D 50 9E 0B F9 7E 0A 84 E1 62 6E E3 3F EA C 0 C F D8 FF B9 3D 5E 0E 2C 74 C 5 D0 3E F3
16 E2 F1 E6 F5 D6 57 7F D4 92 F4 0F 8B 2E 2A 7B A0 B0 8C E5 10 37 Exponent: 01 00 01 Signature Length: 256
bytes / 2048 bitsSignature: 00 22 9C F8 E3 1E 45 98 6C 25 E7 37 19 12 B5 B6 F0 2C 86 E0 E0 31 FB C B 36 46 D0
7E D9 F1 F1 7B 1E 6E 82 D4 EC FD E9 9A 73 4A A1 8F 68 37 58 34 A1 B1 9F 2C A3 C 3 2A 40 D9 9C C 2 48 E4 1F AA
C D 5A A5 87 06 EF 5A 24 36 09 68 82 44 AD 39 52 FC 70 5C DE DF 09 29 2C E3 B5 17 1A 61 B7 95 0E A7 21 1F F2
4B EB F6 A9 4C 3F BC A6 7F DF 59 BA FF 3C D1 B6 11 FA B7 C 2 5A 51 7C 6C 07 38 22 9D 34 04 C B 2C 74 52 BB
81 37 FE 70 97 49 31 7A 90 33 85 86 3C BD 0D 9C 68 BD 8F A1 A7 74 C E 3F F1 93 62 19 0A 32 E6 EB C 4 77 AB 55
DF 16 5D 86 D9 0C 7A AE D3 A8 9E 56 92 C F 94 D1 70 F4 06 BD 33 11 35 49 A4 76 74 0C 11 9C 52 3D 2F 01 9C
6E AC 64 B0 2F 92 A6 B2 45 C 9 AA 30 9A 56 38 EB 52 54 11 03 0A 44 86 06 BB 53 6B 1B 11 F5 40 B0 E4 C 8 AC DD
39 92 C E 84 D2 AB D4 A8 F3 8A 3E 86 44 BD E9 3E ------------------------------ snip ------------------------------
References:
http://en.wikipedia.org/wiki/STARTTLS
http://tools .ietf.org/html/rfc2595
Alert ID: 84603 Found on: 2017-01-17 Severity: Info
POP Server Detection (tcp/110)
Open Status: NEW First Found: 2017-01-17
Description:
The remote hos t is running a s erver that unders tands the Pos t Office Protocol (POP), us ed by email clients to retrieve
mes s ages from a s erver, pos s ibly acros s a network link.
Solution:
Dis able this s ervice if you do not us e it.
Result:
Rem ote PO P server banner :+O K Hello there. <17499.1484647941@ localhost.localdom ain>
References:
http://en.wikipedia.org/wiki/Pos t_Office_Protocol
Alert ID: 84607 Found on: 2017-01-17 Severity: Info
CGI Generic Tests HTTP Errors (tcp/80)
Open Status: NEW First Found: 2017-01-17
Page 104 of 120
Scan Date: 2017-01-17
Description:
Indus Guard ran into trouble while running its generic CGI tes ts agains t the remote web s erver (for example, connection
refus ed, timeout, etc). When this happens , Indus Guard aborts the current tes t and s witches to the next CGI s cript on the
s ame port or to another web s erver. Thus , particular plugin or tes t s ignature may be incomplete.
Solution:
Res can with a longer network timeout or les s parallelis m for example, by changing the following options in the s can
policy :
- Network -> Network Receive Timeout (check_read_timeout)
- Options -> Number of hos ts in parallel (max_hos ts )
- Options -> Number of checks in parallel (max_checks )
Result:
IndusGuard encountered : - 1 error involving blind SQ L injection (tim e based) checks : . reading the status line:
errno=1 (operation tim ed out)
Alert ID: 84608 Found on: 2017-01-17 Severity: Info
CGI Generic Tests Timeout (tcp/80)
Open Status: NEW First Found: 2017-01-17
Description:
Some generic CGI tes ts ran out of time during the s can. The res ults may be incomplete.
Solution:
Run your run s can again with a longer timeout or les s ambitious options :
- Combinations of arguments values = 'all combinations ' is much s lower than 'two pairs ' or 's ingle'.
- Stop at firs t flaw = 'per port' is quicker.
- In 's ome pairs ' or 's ome combinations ' mode, try reducing web_app_tes ts .tes ted_values _for_each_parameter in
Indus Guardd.conf
Result:
The following tests tim ed out without finding any flaw :- XSS (on HTTP headers)- SQ L injection (on param eters
nam es)- SSI injection (on HTTP headers)- SQ L injection (on HTTP headers)The following tests were interrupted
and did not report all possible flaws :- blind SQ L injection- SQ L injection
Alert ID: 84619 Found on: 2017-01-17 Severity: Info
External URLs (tcp/80)
Open Status: NEW First Found: 2017-01-17
Description:
Indus Guard gathered HREF links to external s ites by crawling the remote web s erver.
Solution:
n/a
Result:
4 external URLs were gathered on this web server : URL... - Seen
on...http://blog.m indedsecurity.com /2009/05/client-side-http-param eter-pollution.htm l -
/hpp/http://www.acunetix.com - /http://www.acunetix.com / - /http://www.eclectasy.com /Fractal-Explorer/index.htm l -
/
Page 105 of 120
Scan Date: 2017-01-17
Alert ID: 84620 Found on: 2017-01-17 Severity: Info
HTTP X-Content-Security-Policy Response Header Usage (tcp/80)
Open Status: NEW First Found: 2017-01-17
Description:
The remote web s erver s ets an X-Content-Security-Policy (CSP) res pons e header in s ome res pons es .
CSP has been propos ed as a way to mitigate cros s -s ite s cripting and clickjacking attacks .
Solution:
n/a
Result:
The following pages do not set a C ontent-Security-Policy response header or set a perm issive policy: -
http://rs202995.rs.hosteurope.de/ - http://rs202995.rs.hosteurope.de/AJAX/ -
http://rs202995.rs.hosteurope.de/AJAX/index.php - http://rs202995.rs.hosteurope.de/AJAX/index.php/.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/ -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/.php?id=/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/.php?id=/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/GET -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/PO ST -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/infotitle -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/showxm l.php/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/showxm l.php/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/styles.css -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/showxm l.php/.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/showxm l.php/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/showxm l.php/.php?id=/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/showxm l.php/.php?id=/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/showxm l.php/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/showxm l.php/showxm l.php/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/showxm l.php/showxm l.php/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/ -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/ -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/.php?id=/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/.php?id=/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/GET -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/PO ST -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/infotitle -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/showxm l.php/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/showxm l.php/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/styles.css -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php?id= -
Page 106 of 120
Scan Date: 2017-01-17
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php?id=/ -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php?id=/.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php?id=/.php/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php?id=/.php/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php?id=/.php?id= - http://rs2029
References:
https ://wiki.mozilla.org/Security/CSP/Specification
https ://developer.mozilla.org/en/Introducing_Content_Security_Policy
http://people.mozilla.com/~bs terne/content-s ecurity-policy/
Alert ID: 84622 Found on: 2017-01-17 Severity: Info
Web Server Harvested Email Addresses (tcp/80)
Open Status: NEW First Found: 2017-01-17
Description:
Indus Guard harves ted HREF mailto: links and extracted email addres s es by crawling the remote web s erver.
Solution:
n/a
Result:
The following em ail address has been gathered :- 'wvs@ acunetix.com ', referenced from : /listproducts.php?
cat=1 /product.php?pic=3 /search.php /artists.php /categories.php /index.php /product.php?pic=7
/Tem plates/m ain_dynam ic_tem plate.dwt.php /artists.php?artist=3 /listproducts.php?artist=2 /listproducts.php?
artist=3 /listproducts.php?cat=2 /listproducts.php?cat=4 /product.php?pic=2 /artists.php?artist=1 /product.php?
pic=6 /disclaim er.php /artists.php?artist=2 / /signup.php /product.php?pic=4 /listproducts.php?cat=3
/listproducts.php?artist=1 /product.php?pic=5 /product.php?pic=1 /cart.php /login.php /guestbook.php
Alert ID: 84623 Found on: 2017-01-17 Severity: Info
Web Server Allows Password Auto-Completion (tcp/80)
Open Status: NEW First Found: 2017-01-17
Description:
The remote web s erver contains at leas t HTML form field containing an input of type 'pas s word' where 'autocomplete' is
not s et to 'off'.
While this does not repres ent a ris k to this web s erver per s e, it does mean that us ers who us e the affected forms may
have their credentials s aved in their brows ers , which could in turn lead to a los s of confidentiality if any of them us e a
s hared hos t or their machine is compromis ed at s ome point.
Solution:
Add the attribute 'autocomplete=off' to thes e fields to prevent brows ers from caching credentials .
Result:
Page : /login.phpDestination Page: /userinfo.phpPage : /signup.phpDestination Page: /secured/newuser.php
Alert ID: 84624 Found on: 2017-01-17 Severity: Info
HTTP X-Frame-Options Response Header Usage (tcp/80)
Open Status: NEW First Found: 2017-01-17
Page 107 of 120
Scan Date: 2017-01-17
Description:
The remote web s erver s ets an X-Frame-Options res pons e header in s ome res pons es .
X-Frame-Options has been propos ed by Micros oft as a way to mitigate clickjacking attacks and has als o been
implemented in Chrome and Safari.
Solution:
n/a
Result:
The following pages do not set a X-Fram e-O ptions response header or set a perm issive policy: -
http://rs202995.rs.hosteurope.de/ - http://rs202995.rs.hosteurope.de/AJAX/ -
http://rs202995.rs.hosteurope.de/AJAX/index.php - http://rs202995.rs.hosteurope.de/AJAX/index.php/.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/ -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/.php?id=/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/.php?id=/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/GET -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/PO ST -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/infotitle -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/showxm l.php/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/showxm l.php/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/.php?id=/styles.css -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/showxm l.php/.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/showxm l.php/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/showxm l.php/.php?id=/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/showxm l.php/.php?id=/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/showxm l.php/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/showxm l.php/showxm l.php/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php/showxm l.php/showxm l.php/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/ -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/ -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/.php?id=/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/.php?id=/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/GET -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/PO ST -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/infotitle -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/showxm l.php/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/showxm l.php/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php/styles.css -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php?id=/ -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php?id=/.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php?id=/.php/.php?id= -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php?id=/.php/showxm l.php -
http://rs202995.rs.hosteurope.de/AJAX/index.php/.php/.php?id=/.php?id=/.php?id= - http://rs202995.rs.ho
References:
Page 108 of 120
Scan Date: 2017-01-17
http://en.wikipedia.org/wiki/Clickjacking
http://blogs .s ans .org/apps ecs treetfighter/2009/10/15/adoption-of-x-frame-options -header/
Alert ID: 84625 Found on: 2017-01-17 Severity: Info
Web Application Potentially Sensitive CGI Parameter Detection (tcp/80)
Open Status: NEW First Found: 2017-01-17
Description:
According to their names , s ome CGI parameters may control s ens itive data (e.g., ID, privileges , commands , prices ,
credit card data, etc.). In the cours e of us ing an application, thes e variables may dis clos e s ens itive data or be prone to
tampering that could res ult in privilege es calation. Thes e parameters s hould be examined to determine what type of data
is controlled and if it pos es a s ecurity ris k.
** This check only reports information that may be us eful for auditors
** or pen-tes ters , not a real flaw.
Solution:
Ens ure s ens itive data is not dis clos ed by CGI parameters . In addition, do not us e CGI parameters to control acces s to
res ources or privileges .
Result:
Potentially sensitive param eters for C GI
/AJAX/index.php/.php/showxm l.php/showxm l.php/showxm l.php/showxm l.php/showxm l.php/.php :id : Potential
horizontal or vertical privilege escalationPotentially sensitive param eters for C GI
/AJAX/index.php/.php/showxm l.php/showxm l.php/showxm l.php/.php/.php :id : Potential horizontal or vertical
privilege escalationPotentially sensitive param eters for C GI /AJAX/index.php/.php/.php/.php/showxm l.php/.php :id
: Potential horizontal or vertical privilege escalationPotentially sensitive param eters for C GI
/AJAX/index.php/showxm l.php/showxm l.php/showxm l.php/showxm l.php/showxm l.php/showxm l.php/.php :id :
Potential horizontal or vertical privilege escalationPotentially sensitive param eters for C GI
/AJAX/index.php/showxm l.php/showxm l.php/showxm l.php/showxm l.php/.php/.php :id : Potential horizontal or
vertical privilege escalationPotentially sensitive param eters for C GI
/AJAX/index.php/showxm l.php/showxm l.php/showxm l.php/.php/showxm l.php/.php :id : Potential horizontal or
vertical privilege escalationPotentially sensitive param eters for C GI
/AJAX/index.php/showxm l.php/showxm l.php/.php/showxm l.php/showxm l.php/.php :id : Potential horizontal or
vertical privilege escalationPotentially sensitive param eters for C GI
/AJAX/index.php/.php/showxm l.php/showxm l.php/.php/.php :id : Potential horizontal or vertical privilege
escalationPotentially sensitive param eters for C GI /AJAX/index.php/.php/showxm l.php/.php/showxm l.php/.php :id
: Potential horizontal or vertical privilege escalationPotentially sensitive param eters for C GI
/AJAX/index.php/.php/.php/showxm l.php/showxm l.php/.php :id : Potential horizontal or vertical privilege
escalationPotentially sensitive param eters for C GI /AJAX/index.php/.php/.php/.php/.php :id : Potential horizontal or
vertical privilege escalationPotentially sensitive param eters for C GI
/AJAX/index.php/showxm l.php/showxm l.php/showxm l.php/showxm l.php/showxm l.php/.php :id : Potential
horizontal or vertical privilege escalationPotentially sensitive param eters for C GI
/AJAX/index.php/.php/showxm l.php/.php/.php :id : Potential horizontal or vertical privilege escalationPotentially
sensitive param eters for C GI /AJAX/index.php/.php/.php/showxm l.php/.php :id : Potential horizontal or vertical
privilege escalationPotentially sensitive param eters for C GI
/AJAX/index.php/showxm l.php/showxm l.php/showxm l.php/showxm l.php/.php :id : Potential horizontal or vertical
privilege escalationPotentially sensitive param eters for C GI
/AJAX/index.php/showxm l.php/showxm l.php/.php/.php :id : Potential horizontal or vertical privilege
escalationPotentially sensitive param eters for C GI /AJAX/index.php/showxm l.php/.php/showxm l.php/.php :id :
Potential horizontal or vertical privilege escalationPotentially sensitive param eters for C GI
/AJAX/index.php/showxm l.php/showxm l.php/.php :id : Potential horizontal or vertical privilege
escalationPotentially sensitive param eters for C GI /AJAX/index.php/.php/.php :id : Potential horizontal or vertical
privilege escalationPotentially sensitive param eters for C GI /cart.php :price : Manipulating this could allow for
price m odificationPotentially sensitive param eters for C GI /AJAX/.php :id : Potential horizontal or vertical privilege
escalationPotentially sensitive param eters for C GI /AJAX/index.php/.php :id : Potential horizontal or vertical
Page 109 of 120
Scan Date: 2017-01-17
privilege escalationPotentially sensitive param eters for C GI /userinfo.php :pass : Possibly a clear or hashed
password, vulnerable to sniffing or dictionary attackPotentially sensitive param eters for C GI
/AJAX/index.php/showxm l.php/.php :id : Potential horizontal or vertical privilege escalationPotentially sensitive
param eters for C GI /AJAX/index.php/.php/showxm l.php/.php :id : Potential horizontal or vertical privilege
escalationPotentially sensitive param eters for C GI /AJAX/index.php/showxm l.php/.php/.php :id : Potential
horizontal or vertical privilege escalationPotentially sensitive param eters for C GI
/AJAX/index.php/showxm l.php/showxm l.php
Alert ID: 84627 Found on: 2017-01-17 Severity: Info
CGI Generic Tests Load Estimation (all tests) (tcp/80)
Open Status: NEW First Found: 2017-01-17
Description:
This s cript computes the maximum number of reques ts that would be done by the generic web tes ts , depending on
mis cellaneous options . It does not perform any tes t by its elf.
The res ults can be us ed to es timate the duration of thes e tes ts , or the complexity of additional manual tes ts .
Note that the s cript does not try to compute this duration bas ed on external factors s uch as the network and web
s ervers loads .
Solution:
n/a
Result:
Here are the estim ated num ber of requests in m iscellaneous m odesfor one m ethod only (GET or PO ST) :[Single /
Som e Pairs / All Pairs / Som e C om binations / All C om binations]on site request forgery : S=6 SP=6 AP=6 SC =6
AC =6 SQ L injection : S=1824 SP=3672 AP=3672 SC =32640 AC =32640 unseen param eters : S=2660 SP=5355
AP=5355 SC =47600 AC =47600 local file inclusion : S=76 SP=153 AP=153 SC =1360 AC =1360 web code
injection : S=76 SP=153 AP=153 SC =1360 AC =1360 cookie m anipulation : S=12 SP=16 AP=16 SC =16 AC =16
XML injection : S=76 SP=153 AP=153 SC =1360 AC =1360 form at string : S=152 SP=306 AP=306 SC =2720
AC =2720 script injection : S=6 SP=6 AP=6 SC =6 AC =6 cross-site scripting (com prehensive test): S=304 SP=612
AP=612 SC =5440 AC =5440 injectable param eter : S=152 SP=306 AP=306 SC =2720 AC =2720 cross-site
scripting (extended patterns) : S=36 SP=36 AP=36 SC =36 AC =36 directory traversal (write access) : S=152
SP=306 AP=306 SC =2720 AC =2720 SSI injection : S=228 SP=459 AP=459 SC =4080 AC =4080 header injection
: S=12 SP=12 AP=12 SC =12 AC =12 directory traversal : S=1900 SP=3825 AP=3825 SC =34000 AC =34000 HTML
injection : S=30 SP=30 AP=30 SC =30 AC =30 cross-site scripting (quick test) : S=66 SP=88 AP=88 SC =88 AC =88
arbitrary com m and execution (tim e based) : S=456 SP=918 AP=918 SC =8160 AC =8160 SQ L injection (2nd
order) : S=76 SP=153 AP=153 SC =1360 AC =1360 persistent XSS : S=304 SP=612 AP=612 SC =5440 AC =5440
directory traversal (extended test) : S=3876 SP=7803 AP=7803 SC =69360 AC =69360 arbitrary com m and
execution : S=1216 SP=2448 AP=2448 SC =21760 AC =21760 blind SQ L injection (4 requests) : S=304 SP=612
AP=612 SC =5440 AC =5440 HTTP response splitting : S=54 SP=54 AP=54 SC =54 AC =54 blind SQ L injection :
S=912 SP=1836 AP=1836 SC =16320 AC =16320 All tests : S=14966 SP=29930 AP=29930 SC =264088
AC =264088 Here are the estim ated num ber of requests in m iscellaneous m odesfor both m ethods (GET and
PO ST) :[Single / Som e Pairs / All Pairs / Som e C om binations / All C om binations]on site request forgery : S=12
SP=12 AP=12 SC =12 AC =12 SQ L injection : S=3648 SP=7344 AP=7344 SC =65280 AC =65280 unseen
param eters : S=5320 SP=10710 AP=10710 SC =95200 AC =95200 local file inclusion : S=152 SP=306 AP=306
SC =2720 AC =2720 web code injection : S=152 SP=306 AP=306 SC =2720 AC =2720 cookie m anipulation :
S=24 SP=32 AP=32 SC =32 AC =32 XML injection : S=152 SP=306 AP=306 SC =2720 AC =2720 form at string
Alert ID: 84629 Found on: 2017-01-17 Severity: Info
Web Site Client Access Policy File Detection (tcp/80)
Open Status: NEW First Found: 2017-01-17
Description:
Page 110 of 120
Scan Date: 2017-01-17
The remote web s erver contains a client acces s policy file. This is a s imple XML file us ed by Micros oft Silverlight to allow
acces s to s ervices that res ide outs ide the exact web domain from which a Silverlight control originated.
Solution:
Review the contents of the policy file carefully. Improper policies , es pecially an unres tricted one with jus t '*', could allow
for cros s - s ite reques t forgery or other attacks agains t the web s erver.
Result:
IndusGuard was able to obtain a client access policy file from therem ote host at the following URL :
http://rs202995.rs.hosteurope.de/clientaccesspolicy.xm l
References:
http://www.Indus Guard.org/u?85a62f76
Alert ID: 84664 Found on: 2017-01-17 Severity: Info
PHP Version (tcp/80)
Open Status: NEW First Found: 2017-01-17
Description:
This check attempts to determine the vers ion of PHP available on the remote web s erver.
Solution:
n/a
Result:
IndusGuard was able to identify the following PHP version inform ation : Version : 5.1.6 Source :
http://rs202995.rs.hosteurope.de/secured/phpinfo.php Version : 5.3.10-1~lucid+2uwsgi2 Source : X-Powered-By:
PHP/5.3.10-1~lucid+2uwsgi2
Alert ID: 84666 Found on: 2017-01-17 Severity: Info
Browsable Web Directories (tcp/80)
Open Status: NEW First Found: 2017-01-17
Description:
Mis cellaneous Indus Guard checks identified directories on this web s erver that are brows able.
Solution:
Make s ure that brows able directories do not leak confidential informative or give acces s to s ens itive res ources . And us e
acces s res trictions or dis able directory indexing for any that do.
Result:
The following directories are browsable
:http://rs202995.rs.hosteurope.de/C VS/http://rs202995.rs.hosteurope.de/Tem plates/http://rs202995.rs.hosteurope.
de/adm in/http://rs202995.rs.hosteurope.de/im ages/
References:
http://projects .webapps ec.org/Directory-Indexing
Alert ID: 84668 Found on: 2017-01-17 Severity: Info
Web Site Cross-Domain Policy File Detection (tcp/80)
Open Status: NEW First Found: 2017-01-17
Page 111 of 120
Scan Date: 2017-01-17
Description:
The remote web s erver contains a cros s -domain policy file. This is a s imple XML file us ed by Adobe's Flas h Player to
allow acces s to data that res ides outs ide the exact web domain from which a Flas h movie file originated.
Solution:
Review the contents of the policy file carefully. Improper policies , es pecially an unres tricted one with jus t '*', could allow
for cros s - s ite reques t forgery and cros s -s ite s cripting attacks agains t the web s erver.
Result:
IndusGuard was able to obtain a cross-dom ain policy file from the rem otehost using the following URL :
http://rs202995.rs.hosteurope.de/crossdom ain.xm l
References:
http://www.adobe.com/devnet/flas hplayer/articles /cros s _domain_policy.html
http://www.adobe.com/go/tn_14213
http://www.nes s us .org/u?74a6a9a5
http://www.nes s us .org/u?50ee6db2
Alert ID: 84669 Found on: 2017-01-17 Severity: Info
HyperText Transfer Protocol (HTTP) Information (tcp/80)
Open Status: NEW First Found: 2017-01-17
Description:
This tes t gives s ome information about the remote HTTP protocol - the vers ion us ed, whether HTTP Keep-Alive and HTTP
pipelining are enabled, etc...
This tes t is informational only and does not denote any s ecurity problem.
Solution:
n/a
Result:
Protocol version : HTTP/1.1SSL : noKeep-Alive : noO ptions allowed : (Not im plem ented)Headers : Server:
nginx/1.4.1 Date: Tue, 17 Jan 2017 10:40:38 GMT C ontent-Type: text/htm l Transfer-Encoding: chunked
C onnection: keep-alive X-Powered-By: PHP/5.3.10-1~lucid+2uwsgi2
Alert ID: 84671 Found on: 2017-01-17 Severity: Info
HTTP Methods Allowed (per directory) (tcp/80)
Open Status: NEW First Found: 2017-01-17
Description:
By calling the OPTIONS method, it is pos s ible to determine which HTTP methods are allowed on each directory.
As this lis t may be incomplete, the check als o tes ts - if 'Thorough tes ts ' are enabled or 'Enable web applications tes ts ' is
s et to 'yes ' in the s can policy - various known HTTP methods on each directory and cons iders them as uns upported if it
receives a res pons e code of 400, 403, 405, or 501.
Note that the check output is only informational and does not neces s arily indicate the pres ence of any s ecurity
vulnerabilities .
Solution:
n/a
Page 112 of 120
Scan Date: 2017-01-17
Result:
Based on tests of each m ethod : - HTTP m ethods AC L BC O PY BDELETE BMO VE BPRO PFIND BPRO PPATC H C HEC KIN
C HEC KO UT C O PY DEBUG DELETE GET HEAD INDEX LABEL LO C K MERGE MKAC TIVITY MKC O L MKWO RKSPAC E MO VE
NO TIFY O PTIO NS O RDERPATC H PATC H PO LL PO ST PRO PFIND PRO PPATC H PUT REPO RT RPC _IN_DATA
RPC _O UT_DATA SEARC H SUBSC RIBE UNC HEC KO UT UNLO C K UNSUBSC RIBE UPDATE are allowed on : /cgi-bin -
HTTP m ethods GET HEAD PO ST are allowed on : / /AJAX /AJAX/index.php /AJAX/index.php/.php
/AJAX/index.php/.php/.php /AJAX/index.php/.php/.php/.php /AJAX/index.php/.php/.php/showxm l.php
/AJAX/index.php/.php/.php/showxm l.php/showxm l.php /AJAX/index.php/.php/showxm l.php
/AJAX/index.php/.php/showxm l.php/.php /AJAX/index.php/.php/showxm l.php/.php/showxm l.php
/AJAX/index.php/.php/showxm l.php/showxm l.php /AJAX/index.php/.php/showxm l.php/showxm l.php/.php
/AJAX/index.php/.php/showxm l.php/showxm l.php/showxm l.php
/AJAX/index.php/.php/showxm l.php/showxm l.php/showxm l.php/showxm l.php /AJAX/index.php/showxm l.php
/AJAX/index.php/showxm l.php/.php /C VS /Tem plates /adm in /im ages /secured - Invalid/unknown HTTP m ethods
are allowed on : /cgi-bin
Alert ID: 84672 Found on: 2017-01-17 Severity: Info
HTTP Server Type and Version (tcp/80)
Open Status: NEW First Found: 2017-01-17
Description:
This check attempts to determine the type and the vers ion of the remote web s erver.
Solution:
n/a
Result:
The rem ote web server type is :nginx/1.4.1
Alert ID: 84673 Found on: 2017-01-17 Severity: Info
Web mirroring (tcp/80)
Open Status: NEW First Found: 2017-01-17
Description:
This s cript makes a mirror of the remote web s ite(s ) and extracts the lis t of CGIs that are us ed by the remote hos t.
It is s ugges ted that you change the number of pages to mirror in the 'Options ' s ection of the client.
Solution:
n/a
Result:
Webm irror perform ed 2000 queries in 425s (4.0705 queries per second)The following C GIs have been
discovered :+ C GI : /search.php Methods : PO ST Argum ent : goButton Value: go Argum ent : searchFor Argum ent :
test Value: query+ C GI : /listproducts.php Methods : GET Argum ent : artist Value: 3 Argum ent : cat Value: 4+ C GI :
/artists.php Methods : GET Argum ent : artist Value: 3+ C GI : /com m ent.php Methods : GET,PO ST Argum ent : Subm it
Value: Subm it Argum ent : aid Value: 3 Argum ent : com m ent Argum ent : nam e Value: <your nam e here>
Argum ent : phpaction Value: echo $_PO ST[com m ent]; Argum ent : pid Value: 6+ C GI : /guestbook.php Methods :
PO ST Argum ent : nam e Value: anonym ous user Argum ent : subm it Value: add m essage Argum ent : text+ C GI :
/AJAX/index.php/.php Methods : GET Argum ent : id Value: /.php?id=/.php?id=/showxm l.php/.php?
id=/PO ST/showxm l.php+ C GI : /userinfo.php Methods : PO ST Argum ent : pass Argum ent : unam e+ C GI : /hpp/
Methods : GET Argum ent : pp Value: 12+ C GI : /product.php Methods : GET Argum ent : pic Value: 6+ C GI :
/showim age.php Methods : GET Argum ent : file Value: ./pictures/6.jpg+ C GI : /AJAX/index.php/showxm l.php/.php
Methods : GET Argum ent : id Value: /showxm l.php/showxm l.php/showxm l.php/showxm l.php/showxm l.php+ C GI :
/AJAX/.php Methods : GET Argum ent : id+ C GI : /secured/newuser.php Methods : PO ST Argum ent : signup Value:
signup Argum ent : uaddress Argum ent : ucc Argum ent : uem ail Argum ent : upass Argum ent : upass2 Argum ent :
Page 113 of 120
Scan Date: 2017-01-17
uphone Argum ent : urnam e Argum ent : uunam e+ C GI : /hpp/param s.php Methods : GET Argum ent : aaaa/
Argum ent : p Value: valid Argum ent : pp Value: 12+ C GI : /cart.php Methods : PO ST Argum ent : addcart Value: 6
Argum ent : price Value: 10000+ C GI : /AJAX/index.php/.php/.php Methods : GET Argum ent : id Value:
/showxm l.php/showxm l.php/showxm l.php/showxm l.php/showxm l.php+ C GI :
/AJAX/index.php/showxm l.php/showxm l.php/.php Methods : GET Argum ent : id Value:
/showxm l.php/showxm l.php/showxm l.php/showxm l.php+ C GI : /AJAX/index.php/.php/showxm l.php/.php Methods
: GET Argum ent : id Value: /showxm l.php/showxm l.php/showxm l.php/showxm l.php+ C GI :
/AJAX/index.php/showxm l.php/.php/.php Methods : GET Argum ent : id Value:
/showxm l.php/showxm l.php/showxm l.php+ C GI : /AJAX/index.php/showxm l.php/showxm l.php/showxm l.php/.php
Methods : GET Argum ent : id Value: /showxm l.php/showxm l.php/showxm l.php+ C GI :
/AJAX/index.php/.php/.php/.php Methods : GET Argum ent : id Value: /showxm l.php/showxm l.php/showxm l.php+
C GI : /AJAX/index.php/.php/showxm l.php/showxm l.php/.php Methods : GET Argum ent : id Value:
/showxm l.php/showxm l.php/showxm l.php+ C GI : /AJAX/index.php/showxm l.php/.php/showxm l.php/.php Methods
: GET Argum ent : id Value: /showxm l.php/showxm l.php+ C GI :
/AJAX/index.php/showxm l.php/showxm l.php/.php/.php Methods : GET Argum ent : id Value:
/showxm l.php/showxm l.php+ C GI : /AJAX/index.php/showxm l.php/showxm l.php/showxm l.php/showxm l.php/.php
Methods : GET Argum ent : id Value: /showxm l.php/showxm l.php+ C GI :
/AJAX/index.php/.php/.php/showxm l.php/.php Methods : GET Argum ent : id Value: /showxm l.php/showxm l.php+
C GI : /AJAX/index.php/.php/showxm l.php/.php/.php Methods : GET Argum ent : id Value:
/showxm l.php/showxm l.php+ C GI : /AJAX/index.php/.php/showxm l.php/showxm l.php/showxm l.php/.php Methods
: GET Argum ent : id Value: /showxm l.php/showxm l.php+ C GI : /AJAX/index.php/showxm l.php/.php/.php/.php
Methods : GET Argum ent : id Value: /showxm l.php+ C GI :
/AJAX/index.php/showxm l.php/.php/showxm l.php/showxm l.php/.php Methods : GET Argum ent : id Value:
/showxm l.php+ C GI : /AJAX/index.php/showxm l.php/showxm l.php/.php/showxm l.php/.php Methods : GET
Argum ent : id Value: /showxm l.php+ C GI : /AJAX/index.php/showxm l.php/showxm l.php/showxm l.php/.php/.php
Methods : GET Argum ent : id Value: /showxm l.php+ C GI :
/AJAX/index.php/showxm l.php/showxm l.php/showxm l.php/showxm l.php/showxm l
Alert ID: 84674 Found on: 2017-01-17 Severity: Info
Web Server Directory Enumeration (tcp/80)
Open Status: NEW First Found: 2017-01-17
Description:
This check attempts to determine the pres ence of various common directories on the remote web s erver. By s ending a
reques t for a directory, the web s erver res pons e code indicates if it is a valid directory or not.
Solution:
n/a
Result:
The following directories were discovered:/adm in, /cgi-bin, /secured, /C VS, /Tem plates, /im agesWhile this is not,
in and of itself, a bug, you should m anually inspect these directories to ensure that they are in com pliance with
com panysecurity standards
References:
http://projects .webapps ec.org/Predictable-Res ource-Location
Alert ID: 84675 Found on: 2017-01-17 Severity: Info
DNS Server Fingerprinting (udp/53)
Open Status: NEW First Found: 2017-01-17
Description:
This s cript attempts to identify the remote DNS s erver type and vers ion by s ending various invalid reques ts to the
remote DNS s erver and analyzing the error codes returned.
Page 114 of 120
Scan Date: 2017-01-17
Solution:
n/a
Result:
IndusGuard was not able to reliably identify the rem ote DNS server type.It m ight be : ISC BIND 9.4.2-P2-W2The
fingerprint differs from these known signatures on 2 points.If you know the type and version of the rem ote DNS
server, please sendthe following signature to dns-signatures@ IndusGuard.org :
4q:5:5:1q:1:1q:t:t:t:5:0AAX:5:5:5Z0:5:5:4q:4q:4q:5:5:5:0AAXD:
References:
http://cr.yp.to/s urveys /dns 1.html
Alert ID: 84676 Found on: 2017-01-17 Severity: Info
DNS Server hostname.bind Map Hostname Disclosure (udp/53)
Open Status: NEW First Found: 2017-01-17
Description:
It is pos s ible to learn the remote hos t name by querying the remote DNS s erver for 'hos tname.bind' in the CHAOS
domain.
Solution:
It may be pos s ible to dis able this feature. Cons ult the vendor's documentation for more information.
Result:
The rem ote host nam e is :rs202995
Alert ID: 84677 Found on: 2017-01-17 Severity: Info
DNS Server Detection (udp/53)
Open Status: NEW First Found: 2017-01-17
Description:
The remote s ervice is a Domain Name Sys tem (DNS) s erver, which provides a mapping between hos tnames and IP
addres s es .
Solution:
Dis able this s ervice if it is not needed or res trict acces s to internal hos ts only if the s ervice is available externally.
References:
http://en.wikipedia.org/wiki/Domain_Name_Sys tem
Alert ID: 84678 Found on: 2017-01-17 Severity: Info
DNS Server Version Detection (tcp/53)
Open Status: NEW First Found: 2017-01-17
Description:
Indus Guard was able to obtain vers ion information by s ending a s pecial TXT record query to the remote hos t.
Note that this vers ion is not neces s arily accurate and could even be forged, as s ome DNS s ervers s end the information
bas ed on a configuration file.
Solution:
Page 115 of 120
Scan Date: 2017-01-17
n/a
Result:
DNS server answer for "version.bind" (over TC P) : none
Alert ID: 84679 Found on: 2017-01-17 Severity: Info
DNS Server Detection (tcp/53)
Open Status: NEW First Found: 2017-01-17
Description:
The remote s ervice is a Domain Name Sys tem (DNS) s erver, which provides a mapping between hos tnames and IP
addres s es .
Solution:
Dis able this s ervice if it is not needed or res trict acces s to internal hos ts only if the s ervice is available externally.
References:
http://en.wikipedia.org/wiki/Domain_Name_Sys tem
Alert ID: 84681 Found on: 2017-01-17 Severity: Info
SMTP Authentication Methods (tcp/25)
Open Status: NEW First Found: 2017-01-17
Description:
The remote SMTP s erver advertis es that it s upports authentication.
Solution:
Review the lis t of methods and whether they're available over an encrypted channel.
Result:
The following authentication m ethods are advertised by the SMTPserver without encryption : C RAM-MD5 DIGEST-
MD5 LO GIN PLAIN
References:
http://tools .ietf.org/html/rfc4422
http://tools .ietf.org/html/rfc4954
Alert ID: 84682 Found on: 2017-01-17 Severity: Info
SMTP Server Detection (tcp/25)
Open Status: NEW First Found: 2017-01-17
Description:
The remote hos t is running a mail (SMTP) s erver on this port.
Since SMTP s ervers are the targets of s pammers , it is recommended you dis able it if you do not us e it.
Solution:
Dis able this s ervice if you do not us e it, or filter incoming traffic to this port.
Result:
Rem ote SMTP server banner :220 ************************************************
Page 116 of 120
Scan Date: 2017-01-17
Alert ID: 84683 Found on: 2017-01-17 Severity: Info
Service Detection: 3 ASCII Digit Code Responses (tcp/25)
Open Status: NEW First Found: 2017-01-17
Description:
This check is a complement of find_s ervice1.nas l. It attempts to identify s ervices that return 3 ASCII digits codes (ie: FTP,
SMTP, NNTP, ...)
Solution:
n/a
Result:
A SMTP server is running on this port
Alert ID: 84686 Found on: 2017-01-17 Severity: Info
SSH Algorithms and Languages Supported (tcp/22)
Open Status: NEW First Found: 2017-01-17
Description:
This s cript detects which algorithms and languages are s upported by the remote s ervice for encrypting
communications .
Solution:
n/a
Result:
IndusGuard negotiated the following encryption algorithm with the server : aes128-cbcThe server supports the
following options for kex_algorithm s : diffie-hellm an-group-exchange-sha1 diffie-hellm an-group-exchange-
sha256 diffie-hellm an-group1-sha1 diffie-hellm an-group14-sha1The server supports the following options for
server_host_key_algorithm s : ssh-dss ssh-rsaThe server supports the following options for
encryption_algorithm s_client_to_server : 3des-cbc aes128-cbc aes128-ctr aes192-cbc aes192-ctr aes256-cbc
aes256-ctr arcfour arcfour128 arcfour256 blowfish-cbc cast128-cbc rijndael-cbc@ lysator.liu.seThe server supports
the following options for encryption_algorithm s_server_to_client : 3des-cbc aes128-cbc aes128-ctr aes192-cbc
aes192-ctr aes256-cbc aes256-ctr arcfour arcfour128 arcfour256 blowfish-cbc cast128-cbc rijndael-
cbc@ lysator.liu.seThe server supports the following options for m ac_algorithm s_client_to_server : hm ac-m d5
hm ac-m d5-96 hm ac-ripem d160 hm ac-ripem d160@ openssh.com hm ac-sha1 hm ac-sha1-96 um ac-
64@ openssh.com The server supports the following options for m ac_algorithm s_server_to_client : hm ac-m d5
hm ac-m d5-96 hm ac-ripem d160 hm ac-ripem d160@ openssh.com hm ac-sha1 hm ac-sha1-96 um ac-
64@ openssh.com The server supports the following options for com pression_algorithm s_client_to_server : none
zlib@ openssh.com The server supports the following options for com pression_algorithm s_server_to_client : none
zlib@ openssh.com
Alert ID: 84691 Found on: 2017-01-17 Severity: Info
SSH Protocol Versions Supported (tcp/22)
Open Status: NEW First Found: 2017-01-17
Description:
This check determines the vers ions of the SSH protocol s upported by the remote SSH daemon.
Solution:
n/a
Page 117 of 120
Scan Date: 2017-01-17
Result:
The rem ote SSH daem on supports the following versions of theSSH protocol : - 1.99 - 2.0SSHv2 host key
fingerprint : a1:7d:bd:2c:5d:9f:02:26:da:52:91:c0:2d:20:2f:3c
Alert ID: 84698 Found on: 2017-01-17 Severity: Info
SSH Server Type and Version Information (tcp/22)
Open Status: NEW First Found: 2017-01-17
Description:
It is pos s ible to obtain information about the remote SSH s erver by s ending an empty authentication reques t.
Solution:
n/a
Result:
SSH version : SSH-2.0-O penSSH_5.3p1 Debian-3ubuntu7.1SSH supported authentication : publickey,password
Alert ID: 84701 Found on: 2017-01-17 Severity: Info
FTP Server Detection (tcp/21)
Open Status: NEW First Found: 2017-01-17
Description:
It is pos s ible to obtain the banner of the remote FTP s erver by connecting to the remote port.
Solution:
N/A
Result:
The rem ote FTP banner is :220 ProFTPD 1.3.3e Server (ProFTPD) [176.28.50.165]
Alert ID: 84702 Found on: 2017-01-17 Severity: Info
Patch Report (tcp/0)
Open Status: NEW First Found: 2017-01-17
Description:
The remote hos t is mis s ing one or s everal s ecurity patches .
This check lis ts the newes t vers ion of each patch to ins tall to make s ure the remote hos t is up-to-date.
Solution:
Ins tall the patches lis ted below
Result:
. You need to take the following 5 actions :[ O penSSH < 7.4 Multiple Vulnerabilities (96151) ]+ Action to take :
Upgrade to O penSSH version 7.4 or later.+Im pact : Taking this action will resolve 17 different vulnerabilities
(C VEs).[ O penSSL 'C hangeC ipherSpec' MiTM Potential Vulnerability (74326) ]+ Action to take : O penSSL 0.9.8
SSL/TLS users (client and/or server) should upgrade to 0.9.8za. O penSSL 1.0.0 SSL/TLS users (client and/or
server) should upgrade to 1.0.0m . O penSSL 1.0.1 SSL/TLS users (client and/or server) should upgrade to
1.0.1h.+Im pact : Taking this action will resolve 7 different vulnerabilities (C VEs).[ PHP 5.3.x < 5.3.29 Multiple
Vulnerabilities (77285) ]+ Action to take : Upgrade to PHP version 5.3.29 or later.+Im pact : Taking this action will
resolve 131 different vulnerabilities (C VEs).[ ProFTPD FTP C om m and Handling Sym link Arbitrary File O verwrite
(66970) ]+ Action to take : Upgrade to 1.3.4c / 1.3.5rc1 or apply the patch from the vendor.[ nginx < 1.6.2 / 1.7.5
SSL Session Reuse (78386) ]+ Action to take : Upgrade to nginx 1.6.2 / 1.7.5 or later.+Im pact : Taking this action
Page 118 of 120
Scan Date: 2017-01-17
will resolve 3 different vulnerabilities (C VEs).
Alert ID: 84703 Found on: 2017-01-17 Severity: Info
Common Platform Enumeration (CPE) (tcp/0)
Open Status: NEW First Found: 2017-01-17
Description:
By us ing information obtained from a Indus Guard s can, this check reports CPE (Common Platform Enumeration)
matches for various hardware and s oftware products found on a hos t.
Note that if an official CPE is not available for the product, this check computes the bes t pos s ible CPE bas ed on the
information available from the s can.
Solution:
n/a
Result:
The rem ote operating system m atched the following C PE : cpe:/o:canonical:ubuntu_linux:10.04Following
application C PE's m atched on the rem ote system : cpe:/a:openbsd:openssh:5.3 -> O penBSD O penSSH 5.3
cpe:/a:php:php:5.3.10 -> PHP 5.3.10 cpe:/a:igor_sysoev:nginx:1.4.1
References:
http://cpe.mitre.org/
Alert ID: 84705 Found on: 2017-01-17 Severity: Info
Device Type (tcp/0)
Open Status: NEW First Found: 2017-01-17
Description:
Bas ed on the remote operating s ys tem, it is pos s ible to determine what the remote s ys tem type is (eg: a printer, router,
general-purpos e computer, etc).
Solution:
n/a
Result:
Rem ote device type : general-purposeC onfidence level : 95
Alert ID: 84706 Found on: 2017-01-17 Severity: Info
TCP/IP Timestamps Supported (tcp/0)
Open Status: NEW First Found: 2017-01-17
Description:
The remote hos t implements TCP times tamps , as defined by RFC1323. A s ide effect of this feature is that the uptime of
the remote hos t can s ometimes be computed.
Solution:
n/a
References:
http://www.ietf.org/rfc/rfc1323.txt
Page 119 of 120
Scan Date: 2017-01-17
Page 120 of 120
Scan Date: 2017-01-17
You might also like
- Compliors Sample IT Policy For PCI DSS 1 PDFDocument87 pagesCompliors Sample IT Policy For PCI DSS 1 PDFsantoshs2002848No ratings yet
- List of ISO27001 Templates Iso27001templates PDFDocument3 pagesList of ISO27001 Templates Iso27001templates PDFsantoshs2002848No ratings yet
- Advanced Web Attacks and Exploitation: Offensive SecurityDocument9 pagesAdvanced Web Attacks and Exploitation: Offensive SecurityMinh Tan100% (1)
- A Specimen of Network Security Scan ReportDocument68 pagesA Specimen of Network Security Scan ReportM. Saad JumaniNo ratings yet
- Rapport D'analyse de Vulnérabilité: Website Vulnerability Scanner Report (Light)Document4 pagesRapport D'analyse de Vulnérabilité: Website Vulnerability Scanner Report (Light)Amira JilaliNo ratings yet
- Website Vulnerability Scanner Report (Light)Document5 pagesWebsite Vulnerability Scanner Report (Light)Roberto SihombingNo ratings yet
- Evasion Techniques and Breaching Defenses: Offensive SecurityDocument11 pagesEvasion Techniques and Breaching Defenses: Offensive SecurityAkbar AnggamaulanaNo ratings yet
- PentestTools WebsiteScanner ReportDocument7 pagesPentestTools WebsiteScanner ReportMario Sernaque RumicheNo ratings yet
- Comprehensive Report: Acunetix Threat Level 3Document23 pagesComprehensive Report: Acunetix Threat Level 3bugtestNo ratings yet
- Evasion Techniques and Breaching Defenses: Offensive SecurityDocument11 pagesEvasion Techniques and Breaching Defenses: Offensive SecuritySohel AhmedNo ratings yet
- Detailed Scan Report: Identified Confirmed CriticalDocument103 pagesDetailed Scan Report: Identified Confirmed CriticalViktor CherenapovNo ratings yet
- Affected Items HTTP Plen inDocument26 pagesAffected Items HTTP Plen inAnjura BegumNo ratings yet
- Scan Report PDFDocument6 pagesScan Report PDFJulian MartinezNo ratings yet
- Quick Report: Acunetix Security AuditDocument25 pagesQuick Report: Acunetix Security AuditCristian RamirezNo ratings yet
- Website Vulnerability Scanner Report (Light)Document4 pagesWebsite Vulnerability Scanner Report (Light)MasBaNo ratings yet
- ReportDocument10 pagesReportmanjeetyadav19No ratings yet
- NSE 4 7.0 Sample Questions - Attempt Review2Document10 pagesNSE 4 7.0 Sample Questions - Attempt Review2Subgerencia TecnogiaNo ratings yet
- Opevas Sample ReportDocument60 pagesOpevas Sample ReportjuanNo ratings yet
- SystemCheckReport 09102020 0138Document1 pageSystemCheckReport 09102020 0138nabilNo ratings yet
- PentestTools WebsiteScanner ReportDocument8 pagesPentestTools WebsiteScanner ReportRolando FrancoNo ratings yet
- Security Sample VAPT ReportDocument28 pagesSecurity Sample VAPT ReportRavi GiriNo ratings yet
- Scan Report CRMDocument17 pagesScan Report CRMWeb SploitNo ratings yet
- Web Application Audit Report: Demo AccountDocument12 pagesWeb Application Audit Report: Demo AccountSamuel KonanNo ratings yet
- Advisory2017 09 - CDS 57676Document5 pagesAdvisory2017 09 - CDS 57676Massimo MorelliNo ratings yet
- Website Vulnerability Scanner Sample Report OptimizedDocument11 pagesWebsite Vulnerability Scanner Sample Report OptimizedPauloNo ratings yet
- Tomcat Vulnerability Sample ReportDocument11 pagesTomcat Vulnerability Sample ReportandreirosuNo ratings yet
- CiscoDocument92 pagesCiscoari sirwanNo ratings yet
- Astra Security Sample VAPT ReportDocument28 pagesAstra Security Sample VAPT Reporthanuman1999No ratings yet
- Executive: Acunetix Security AuditDocument3 pagesExecutive: Acunetix Security AuditIbrahim qashtaNo ratings yet
- Comprehensive Report: Acunetix Threat Level 3Document37 pagesComprehensive Report: Acunetix Threat Level 3Yudha Trias RusmanaNo ratings yet
- ReportDocument7 pagesReportAznimar ZainuddinNo ratings yet
- Usenixsec 05Document36 pagesUsenixsec 05mohamedsamirnassar1993No ratings yet
- Final Del Formulario: PHP PHP 5.2.3Document2 pagesFinal Del Formulario: PHP PHP 5.2.3NewtoniXNo ratings yet
- ResultDocument83 pagesResultMaryamNo ratings yet
- Assessment Report: (076271c3)Document87 pagesAssessment Report: (076271c3)Marco SciortinoNo ratings yet
- Vulnerabiliades - DiccionarioDocument142 pagesVulnerabiliades - DiccionarioJohan MorilloNo ratings yet
- Phase2 Security ReportDocument64 pagesPhase2 Security ReportAnonymous r3xb805ENo ratings yet
- (Divi Report) Daptatech RepDocument5 pages(Divi Report) Daptatech RepcarlosNo ratings yet
- Developer ExampleDocument87 pagesDeveloper ExamplehardironNo ratings yet
- ZAP Scanning Report: Site: Https://webapps - Bps.go - IdDocument4 pagesZAP Scanning Report: Site: Https://webapps - Bps.go - Idyoga_wpNo ratings yet
- System Check ResultsDocument1 pageSystem Check ResultsSergio Raúl Ponce GonzalesNo ratings yet
- Tech Talks 52 Good To The Last Drop Writing Robust Flask and Django AppsDocument49 pagesTech Talks 52 Good To The Last Drop Writing Robust Flask and Django Appsumayrh@gmail.comNo ratings yet
- Cargill Web Application Scanning ReportDocument27 pagesCargill Web Application Scanning ReportHari KingNo ratings yet
- Website Vulnscan Sample ReportDocument8 pagesWebsite Vulnscan Sample ReportBalaji RajaramanNo ratings yet
- PhpinfoDocument2 pagesPhpinfomistryjaysheel3No ratings yet
- Astra Security - Sample Report For VAPTDocument30 pagesAstra Security - Sample Report For VAPTIndian OpinionNo ratings yet
- AllDocument48 pagesAlldont4getNo ratings yet
- Developer Report: Acunetix Website Audit 23 December, 2021Document7 pagesDeveloper Report: Acunetix Website Audit 23 December, 2021BAGAS TRI RAMADANA -No ratings yet
- Hunting Beacons: Bartosz JerzmanDocument52 pagesHunting Beacons: Bartosz Jerzmanvha KyNo ratings yet
- Website Vulnerability Scanner Report (Light)Document6 pagesWebsite Vulnerability Scanner Report (Light)alex681219No ratings yet
- VPN Troubleshooting For CheckpointDocument24 pagesVPN Troubleshooting For CheckpointSachin Saini100% (1)
- Johannes B. Ullrich, Ph.D. SANS Technology Institute: GHOST Glibc Gethostbyname Vulnerability CVE-2015-0235Document17 pagesJohannes B. Ullrich, Ph.D. SANS Technology Institute: GHOST Glibc Gethostbyname Vulnerability CVE-2015-0235Saul RamosNo ratings yet
- Vulnerabilities EhipDocument11 pagesVulnerabilities EhipSeanNo ratings yet
- Penetration Testing With Kali Linux (PWK)Document6 pagesPenetration Testing With Kali Linux (PWK)DF QWERTNo ratings yet
- 5 Common Web Application VulnerabilitiesDocument4 pages5 Common Web Application VulnerabilitiesAnonymous Fhs3ufkCNo ratings yet
- Networkvulnerability Scan Sample ReportDocument4 pagesNetworkvulnerability Scan Sample ReportVenâncio GuedesNo ratings yet
- Having Fun With ComDocument65 pagesHaving Fun With ComLeonardoNo ratings yet
- Developer Report PDFDocument65 pagesDeveloper Report PDFAnonymous JyKPfbZBQNo ratings yet
- Active DirectoryDocument10 pagesActive DirectoryKindraNo ratings yet
- Web Application Defender's Cookbook: Battling Hackers and Protecting UsersFrom EverandWeb Application Defender's Cookbook: Battling Hackers and Protecting UsersNo ratings yet
- Innocent Code: A Security Wake-Up Call for Web ProgrammersFrom EverandInnocent Code: A Security Wake-Up Call for Web ProgrammersRating: 3.5 out of 5 stars3.5/5 (3)
- Identity Management: Origination of Concept of I & AM ProductsDocument18 pagesIdentity Management: Origination of Concept of I & AM Productssantoshs2002848100% (1)
- Splunk - Custom Search QueriesDocument3 pagesSplunk - Custom Search Queriessantoshs2002848No ratings yet
- Information Security Information Security: Cyberark Administrator'S Operations ManualDocument37 pagesInformation Security Information Security: Cyberark Administrator'S Operations Manualsantoshs2002848No ratings yet
- ISO 9001-2015 Quality Management System Manual D1.2Document36 pagesISO 9001-2015 Quality Management System Manual D1.2santoshs2002848100% (1)
- Introducing Cyberark: Security For The Heart of The EnterpriseDocument9 pagesIntroducing Cyberark: Security For The Heart of The Enterprisesantoshs2002848No ratings yet
- What Is Identity??Document4 pagesWhat Is Identity??santoshs2002848No ratings yet
- Stages of Malware AnalysisDocument6 pagesStages of Malware Analysissantoshs2002848No ratings yet
- WHITEPAPER - Layer 2 Ethernet Bridge DesignDocument4 pagesWHITEPAPER - Layer 2 Ethernet Bridge Designsantoshs2002848No ratings yet
- Q1) What Are The Primary Functions of Cyberark?Document8 pagesQ1) What Are The Primary Functions of Cyberark?santoshs2002848No ratings yet
- Consultant Bill Format: Template#: c4127 Title: Consultant Bill Format Category: Download This Template in Excel FormatDocument2 pagesConsultant Bill Format: Template#: c4127 Title: Consultant Bill Format Category: Download This Template in Excel Formatsantoshs2002848No ratings yet
- 8.2 IdentityIQ Work ItemsDocument6 pages8.2 IdentityIQ Work Itemssantoshs2002848No ratings yet
- Section A (Answer ONE Question From This Section)Document5 pagesSection A (Answer ONE Question From This Section)santoshs2002848No ratings yet
- Bury CCG Information Governance Incident Reporting Policy V4.0Document15 pagesBury CCG Information Governance Incident Reporting Policy V4.0santoshs2002848No ratings yet
- HCL Anti-Bribery Policy ExternalDocument16 pagesHCL Anti-Bribery Policy Externalsantoshs2002848No ratings yet
- Enterprise Risk Management Sample PolicyDocument4 pagesEnterprise Risk Management Sample Policysantoshs2002848No ratings yet
- ESM Upgrade To 72 PDFDocument46 pagesESM Upgrade To 72 PDFsantoshs2002848No ratings yet
- ESM Upgrade To 72 PDFDocument46 pagesESM Upgrade To 72 PDFsantoshs2002848No ratings yet
- Data Connector Blog 3.0 PDFDocument11 pagesData Connector Blog 3.0 PDFsantoshs2002848No ratings yet
- Example Pci Dss v3 It Security Policy Pcidss ComplianceDocument24 pagesExample Pci Dss v3 It Security Policy Pcidss Compliancesantoshs2002848No ratings yet
- Ipam 1600 PDocument148 pagesIpam 1600 Psagar323No ratings yet
- D-Link AirPlus G DI-524Document95 pagesD-Link AirPlus G DI-524SurviversNo ratings yet
- Merged CNDocument257 pagesMerged CNYuvaraj TankalaNo ratings yet
- ComputerNetwork C5-1 enDocument84 pagesComputerNetwork C5-1 enNguyên VĩnhNo ratings yet
- MITSUBISHI - Manual - PLC - Iq-R - SLMP Connect C# MrJ4BDocument232 pagesMITSUBISHI - Manual - PLC - Iq-R - SLMP Connect C# MrJ4Bca bienNo ratings yet
- InnGate 3 Command Line Interface Reference r1.01Document26 pagesInnGate 3 Command Line Interface Reference r1.01Davi Sadaseeven SaminadenNo ratings yet
- Network Vulnerability Scan With Openvas Report (Light)Document2 pagesNetwork Vulnerability Scan With Openvas Report (Light)alfan666No ratings yet
- Whisp Aps MibDocument92 pagesWhisp Aps MibSamuel JesusNo ratings yet
- Guide To Firewalls and Network Security: Chapter 7 SolutionsDocument3 pagesGuide To Firewalls and Network Security: Chapter 7 SolutionsMohlomphegi Bennet AphaneNo ratings yet
- HTTP Tunnel 1Document6 pagesHTTP Tunnel 1Adailton CruzNo ratings yet
- DS-K1T331 Series Face Recognition Terminal - Datasheet - V1.0.1 - 20200406Document3 pagesDS-K1T331 Series Face Recognition Terminal - Datasheet - V1.0.1 - 20200406CRISTHIAN CAMILO QUINTIN CRUZNo ratings yet
- ALOHADocument18 pagesALOHAMayank JunejaNo ratings yet
- BGP FlowSpecDocument68 pagesBGP FlowSpeckholis_smktelkomNo ratings yet
- Computer Networks MCQ Interview Questions With Answer Set-8 - InfoTechSiteDocument3 pagesComputer Networks MCQ Interview Questions With Answer Set-8 - InfoTechSitelovelyosmile2530% (1)
- 400-051 CciecollabDocument18 pages400-051 CciecollabRose WhiteNo ratings yet
- 30 Netkit Lab BGP Transit AsDocument171 pages30 Netkit Lab BGP Transit AspierpaoloNo ratings yet
- CoursDocument227 pagesCoursSORO YALAMOUSSANo ratings yet
- Iskratel Innbox G67 Datasheet EN PDFDocument2 pagesIskratel Innbox G67 Datasheet EN PDFJose JoseNo ratings yet
- IDS, Firewall & HoneypotDocument11 pagesIDS, Firewall & Honeypotanon_100036097100% (4)
- Sim7020 Series: Simcom Nb-Iot ModuleDocument3 pagesSim7020 Series: Simcom Nb-Iot ModuleAlejandro DemitiNo ratings yet
- SARA-R5 ATCommands (UBX-19047455)Document489 pagesSARA-R5 ATCommands (UBX-19047455)aerNo ratings yet
- Captive Portal Config Using FreeRadious and CoovachilliDocument9 pagesCaptive Portal Config Using FreeRadious and Coovachillirubin nitsuhNo ratings yet
- Wireshark: Presented By: Hiral Chhaya, Anvita PriyamDocument24 pagesWireshark: Presented By: Hiral Chhaya, Anvita PriyamNaponee Nap-shot EvansNo ratings yet
- Pethe, R.M., Burnase, S.R. (2011) Technical Era Language of The Networking - EIGRPDocument5 pagesPethe, R.M., Burnase, S.R. (2011) Technical Era Language of The Networking - EIGRPLee HeaverNo ratings yet
- 2 Twinks With Cum in Face - RedTubeDocument638 pages2 Twinks With Cum in Face - RedTubeMoises Gomes da luzNo ratings yet
- Module 5 MCQDocument32 pagesModule 5 MCQGaurav PandeyNo ratings yet
- Juniper AP-24 DeploymentDocument43 pagesJuniper AP-24 Deploymentcatawiki.businessNo ratings yet
- Css 4th Quarter Week 3Document6 pagesCss 4th Quarter Week 3Hera AsuncionNo ratings yet
- Advance Cyber Security AssignmentDocument2 pagesAdvance Cyber Security AssignmentVenkat Sai Krishna TummisettyNo ratings yet
- Configuring Spanning Tree Protocol (STP) and Advanced STP FeaturesDocument84 pagesConfiguring Spanning Tree Protocol (STP) and Advanced STP FeaturesSergio Antonio Villarreal MarinNo ratings yet