Professional Documents
Culture Documents
IMPLEMENTATION
IMPLEMENTATION
Uploaded by
softroniicsCopyright:
Available Formats
You might also like
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeFrom EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeRating: 4 out of 5 stars4/5 (5825)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreFrom EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreRating: 4 out of 5 stars4/5 (1093)
- Never Split the Difference: Negotiating As If Your Life Depended On ItFrom EverandNever Split the Difference: Negotiating As If Your Life Depended On ItRating: 4.5 out of 5 stars4.5/5 (852)
- Grit: The Power of Passion and PerseveranceFrom EverandGrit: The Power of Passion and PerseveranceRating: 4 out of 5 stars4/5 (590)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceFrom EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceRating: 4 out of 5 stars4/5 (903)
- Shoe Dog: A Memoir by the Creator of NikeFrom EverandShoe Dog: A Memoir by the Creator of NikeRating: 4.5 out of 5 stars4.5/5 (541)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersFrom EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersRating: 4.5 out of 5 stars4.5/5 (349)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureFrom EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureRating: 4.5 out of 5 stars4.5/5 (474)
- Her Body and Other Parties: StoriesFrom EverandHer Body and Other Parties: StoriesRating: 4 out of 5 stars4/5 (823)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)From EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Rating: 4.5 out of 5 stars4.5/5 (122)
- The Emperor of All Maladies: A Biography of CancerFrom EverandThe Emperor of All Maladies: A Biography of CancerRating: 4.5 out of 5 stars4.5/5 (271)
- The Little Book of Hygge: Danish Secrets to Happy LivingFrom EverandThe Little Book of Hygge: Danish Secrets to Happy LivingRating: 3.5 out of 5 stars3.5/5 (403)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyFrom EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyRating: 3.5 out of 5 stars3.5/5 (2259)
- The Yellow House: A Memoir (2019 National Book Award Winner)From EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Rating: 4 out of 5 stars4/5 (98)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaFrom EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaRating: 4.5 out of 5 stars4.5/5 (266)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryFrom EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryRating: 3.5 out of 5 stars3.5/5 (231)
- Team of Rivals: The Political Genius of Abraham LincolnFrom EverandTeam of Rivals: The Political Genius of Abraham LincolnRating: 4.5 out of 5 stars4.5/5 (234)
- On Fire: The (Burning) Case for a Green New DealFrom EverandOn Fire: The (Burning) Case for a Green New DealRating: 4 out of 5 stars4/5 (74)
- The Unwinding: An Inner History of the New AmericaFrom EverandThe Unwinding: An Inner History of the New AmericaRating: 4 out of 5 stars4/5 (45)
- Ultrasonic Based Smart Blind Stick For Visually Impaired PersonsDocument3 pagesUltrasonic Based Smart Blind Stick For Visually Impaired PersonssoftroniicsNo ratings yet
- Alumni PortalDocument31 pagesAlumni Portalsoftroniics100% (1)
- #Define LED GPIO.B2 //pin 5Document6 pages#Define LED GPIO.B2 //pin 5softroniicsNo ratings yet
- Special Sensors TitlesDocument1 pageSpecial Sensors TitlessoftroniicsNo ratings yet
- Algorithms: Algorithm 1: Bipartite Graph ConstructionDocument2 pagesAlgorithms: Algorithm 1: Bipartite Graph ConstructionsoftroniicsNo ratings yet
- ZapdroidDocument21 pagesZapdroidsoftroniicsNo ratings yet
- Clock Network Synthesis: Prof. Shiyan Hu Shiyan@mtu - Edu Office: EREC 731Document22 pagesClock Network Synthesis: Prof. Shiyan Hu Shiyan@mtu - Edu Office: EREC 731softroniicsNo ratings yet
- Stock Maintenance SystemDocument3 pagesStock Maintenance SystemsoftroniicsNo ratings yet
- Graphical Password Reinforced Staunchful Nb-Iot For Waste Collection ProcessDocument12 pagesGraphical Password Reinforced Staunchful Nb-Iot For Waste Collection ProcesssoftroniicsNo ratings yet
- Beacon Based Secured DetectionDocument14 pagesBeacon Based Secured DetectionsoftroniicsNo ratings yet
- Bealib: A Beacon Enabled Smart Library SystemDocument1 pageBealib: A Beacon Enabled Smart Library SystemsoftroniicsNo ratings yet
- Face Recognised Attendance AbstractDocument6 pagesFace Recognised Attendance AbstractsoftroniicsNo ratings yet
- Online Phone Billing SystemDocument78 pagesOnline Phone Billing SystemsoftroniicsNo ratings yet
- Matlab Based Project TopicsDocument2 pagesMatlab Based Project TopicssoftroniicsNo ratings yet
- Node Creation Cluster Head ConstructionDocument1 pageNode Creation Cluster Head ConstructionsoftroniicsNo ratings yet
- BLDC ControlDocument1 pageBLDC ControlsoftroniicsNo ratings yet
- An Approach To Color Transformation For Image Encryption and Data HidingDocument5 pagesAn Approach To Color Transformation For Image Encryption and Data HidingsoftroniicsNo ratings yet
- An Encrypted Medical Image Retrieval Algorithm Based On DWT-DCT Frequency DomainDocument1 pageAn Encrypted Medical Image Retrieval Algorithm Based On DWT-DCT Frequency DomainsoftroniicsNo ratings yet
- MATLAB Projects List From SoftroniicsDocument11 pagesMATLAB Projects List From SoftroniicssoftroniicsNo ratings yet
- BSC Diploma Mini Project TopicsDocument3 pagesBSC Diploma Mini Project TopicssoftroniicsNo ratings yet
IMPLEMENTATION
IMPLEMENTATION
Uploaded by
softroniicsCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
IMPLEMENTATION
IMPLEMENTATION
Uploaded by
softroniicsCopyright:
Available Formats
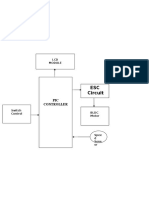
IMPLEMENTATION
MODULES:
Cloud Service Provider
Data Owner Module
ID-based ring signature
Efficiency Analysis
MODULES DESCRIPTION:
Cloud Service Provider
In the first module, we develop the System model of Cloud with the Users.
In this module, we develop Cloud Service Provider module. This is an entity
that provides a data storage service in public cloud.
The S-CSP provides the data outsourcing service and stores data on behalf
of the users.
In this paper, we assume that S-CSP is always online and has abundant
storage capacity and computation power.
And also it approves the group.
Data Owners Module
A data owner is an entity that wants to outsource data storage to the S-CSP
and access the data later.
The Data owner uploads the file in the cloud.
ID-based ring signature
The energy data owner (say, Bob) first setups a ring by choosing a group of
users. This phase only needs the public identity information of ring
members, such as residential addresses, and Bob does not need the
collaboration (or the consent) from any ring members.
Bob uploads his personal data of electronic usage, together with a ring
signature and the identity information of all ring members.
By verifying the ring signature, one can be assured that the data is indeed
given out by a valid resident (from the ring members) while cannot figure
out who the resident is. Hence the anonymity of the data provider is ensured
together with data authenticity. Meanwhile, the verification is efficient
which does not involve any certificate verification.
Efficiency Analysis:
ID-based ring signature seems to be an optimal trade-off among efficiency,
data authenticity and anonymity, and provides a sound solution on data
sharing with a large number of participants.
The size of public parameters is a constant, which only consists of some
security parameters, two integers and some hash functions. The secret key is
very short. It is only an integer. Assume we use 1,024-bit RSA security
level, the secret key is just 1,024 bits.
You might also like
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeFrom EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeRating: 4 out of 5 stars4/5 (5825)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreFrom EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreRating: 4 out of 5 stars4/5 (1093)
- Never Split the Difference: Negotiating As If Your Life Depended On ItFrom EverandNever Split the Difference: Negotiating As If Your Life Depended On ItRating: 4.5 out of 5 stars4.5/5 (852)
- Grit: The Power of Passion and PerseveranceFrom EverandGrit: The Power of Passion and PerseveranceRating: 4 out of 5 stars4/5 (590)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceFrom EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceRating: 4 out of 5 stars4/5 (903)
- Shoe Dog: A Memoir by the Creator of NikeFrom EverandShoe Dog: A Memoir by the Creator of NikeRating: 4.5 out of 5 stars4.5/5 (541)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersFrom EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersRating: 4.5 out of 5 stars4.5/5 (349)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureFrom EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureRating: 4.5 out of 5 stars4.5/5 (474)
- Her Body and Other Parties: StoriesFrom EverandHer Body and Other Parties: StoriesRating: 4 out of 5 stars4/5 (823)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)From EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Rating: 4.5 out of 5 stars4.5/5 (122)
- The Emperor of All Maladies: A Biography of CancerFrom EverandThe Emperor of All Maladies: A Biography of CancerRating: 4.5 out of 5 stars4.5/5 (271)
- The Little Book of Hygge: Danish Secrets to Happy LivingFrom EverandThe Little Book of Hygge: Danish Secrets to Happy LivingRating: 3.5 out of 5 stars3.5/5 (403)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyFrom EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyRating: 3.5 out of 5 stars3.5/5 (2259)
- The Yellow House: A Memoir (2019 National Book Award Winner)From EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Rating: 4 out of 5 stars4/5 (98)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaFrom EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaRating: 4.5 out of 5 stars4.5/5 (266)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryFrom EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryRating: 3.5 out of 5 stars3.5/5 (231)
- Team of Rivals: The Political Genius of Abraham LincolnFrom EverandTeam of Rivals: The Political Genius of Abraham LincolnRating: 4.5 out of 5 stars4.5/5 (234)
- On Fire: The (Burning) Case for a Green New DealFrom EverandOn Fire: The (Burning) Case for a Green New DealRating: 4 out of 5 stars4/5 (74)
- The Unwinding: An Inner History of the New AmericaFrom EverandThe Unwinding: An Inner History of the New AmericaRating: 4 out of 5 stars4/5 (45)
- Ultrasonic Based Smart Blind Stick For Visually Impaired PersonsDocument3 pagesUltrasonic Based Smart Blind Stick For Visually Impaired PersonssoftroniicsNo ratings yet
- Alumni PortalDocument31 pagesAlumni Portalsoftroniics100% (1)
- #Define LED GPIO.B2 //pin 5Document6 pages#Define LED GPIO.B2 //pin 5softroniicsNo ratings yet
- Special Sensors TitlesDocument1 pageSpecial Sensors TitlessoftroniicsNo ratings yet
- Algorithms: Algorithm 1: Bipartite Graph ConstructionDocument2 pagesAlgorithms: Algorithm 1: Bipartite Graph ConstructionsoftroniicsNo ratings yet
- ZapdroidDocument21 pagesZapdroidsoftroniicsNo ratings yet
- Clock Network Synthesis: Prof. Shiyan Hu Shiyan@mtu - Edu Office: EREC 731Document22 pagesClock Network Synthesis: Prof. Shiyan Hu Shiyan@mtu - Edu Office: EREC 731softroniicsNo ratings yet
- Stock Maintenance SystemDocument3 pagesStock Maintenance SystemsoftroniicsNo ratings yet
- Graphical Password Reinforced Staunchful Nb-Iot For Waste Collection ProcessDocument12 pagesGraphical Password Reinforced Staunchful Nb-Iot For Waste Collection ProcesssoftroniicsNo ratings yet
- Beacon Based Secured DetectionDocument14 pagesBeacon Based Secured DetectionsoftroniicsNo ratings yet
- Bealib: A Beacon Enabled Smart Library SystemDocument1 pageBealib: A Beacon Enabled Smart Library SystemsoftroniicsNo ratings yet
- Face Recognised Attendance AbstractDocument6 pagesFace Recognised Attendance AbstractsoftroniicsNo ratings yet
- Online Phone Billing SystemDocument78 pagesOnline Phone Billing SystemsoftroniicsNo ratings yet
- Matlab Based Project TopicsDocument2 pagesMatlab Based Project TopicssoftroniicsNo ratings yet
- Node Creation Cluster Head ConstructionDocument1 pageNode Creation Cluster Head ConstructionsoftroniicsNo ratings yet
- BLDC ControlDocument1 pageBLDC ControlsoftroniicsNo ratings yet
- An Approach To Color Transformation For Image Encryption and Data HidingDocument5 pagesAn Approach To Color Transformation For Image Encryption and Data HidingsoftroniicsNo ratings yet
- An Encrypted Medical Image Retrieval Algorithm Based On DWT-DCT Frequency DomainDocument1 pageAn Encrypted Medical Image Retrieval Algorithm Based On DWT-DCT Frequency DomainsoftroniicsNo ratings yet
- MATLAB Projects List From SoftroniicsDocument11 pagesMATLAB Projects List From SoftroniicssoftroniicsNo ratings yet
- BSC Diploma Mini Project TopicsDocument3 pagesBSC Diploma Mini Project TopicssoftroniicsNo ratings yet