Professional Documents
Culture Documents
0 ratings0% found this document useful (0 votes)
345 viewsPresentation Layer PPT 1 PDF
Presentation Layer PPT 1 PDF
Uploaded by
Sai Krishna SKThe presentation layer performs translation, encryption/decryption, authentication, and compression. Translation converts data between formats like ASCII and EBCDIC. Encryption encodes data using algorithms and keys, while decryption reverses the process. Authentication verifies sender identity using digital signatures that encrypt data in multiple steps. Compression reduces file size using lossless methods that preserve all data or lossy methods that sacrifice some quality.
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
You might also like
- KS3 Presentation - 24 Introduction To NetworksDocument48 pagesKS3 Presentation - 24 Introduction To Networkshunia abbass100% (1)
- Computer Network Principles - Revision Exam PaperDocument18 pagesComputer Network Principles - Revision Exam PaperEse KelvinNo ratings yet
- Java and Multi ThreadingDocument44 pagesJava and Multi ThreadingShraddha Sheth100% (1)
- DC Lab 1 Data RepresentationDocument3 pagesDC Lab 1 Data RepresentationbhavnaNo ratings yet
- CSCU Module 04 Data Encryption PDFDocument23 pagesCSCU Module 04 Data Encryption PDFSandeep Roy100% (1)
- Lesson Plan Wired and Wireless NetworksDocument7 pagesLesson Plan Wired and Wireless NetworksTek CasoneteNo ratings yet
- More Stable and Secure ConnectionDocument3 pagesMore Stable and Secure ConnectionSpidocadoNo ratings yet
- Paper 2 Theory For 9618Document33 pagesPaper 2 Theory For 9618rayan.muzzammil5No ratings yet
- Presentation Layer & Session LayerDocument51 pagesPresentation Layer & Session LayerAnonymous fp8NP80% (1)
- Computer Science Lesson Plan Week 3 - T3-PracticalDocument4 pagesComputer Science Lesson Plan Week 3 - T3-PracticalIshrat JehanNo ratings yet
- Introduction To Computer NetworksDocument6 pagesIntroduction To Computer NetworksMahesh KhatiwadaNo ratings yet
- Peripheral DevicesDocument22 pagesPeripheral DevicesHans Leo LatigayNo ratings yet
- IGCSE ICT - Types of Computer NetworksDocument5 pagesIGCSE ICT - Types of Computer NetworksSudeepa HerathNo ratings yet
- Networking 1Document28 pagesNetworking 1rahul3071No ratings yet
- The Electronic Equivalent of The Document and Fingerprint Pair Is The Message and Digest PairDocument36 pagesThe Electronic Equivalent of The Document and Fingerprint Pair Is The Message and Digest PairRAJ TAPASENo ratings yet
- NC101 Module 5Document8 pagesNC101 Module 5Sarah May Nacion MorescoNo ratings yet
- Critical Thinking Chapter 1 QuestionsDocument11 pagesCritical Thinking Chapter 1 Questionsapi-347017345No ratings yet
- Ethernet Layer 2, Switching and Bridging Logic Lec2Document15 pagesEthernet Layer 2, Switching and Bridging Logic Lec2Hiroyo ChanNo ratings yet
- CCNA Assignment 1Document4 pagesCCNA Assignment 1Sudhindra HnNo ratings yet
- Introduction To Networks: KVS Regional Office Jaipur - Session 2020-21 Page 14 of 19Document3 pagesIntroduction To Networks: KVS Regional Office Jaipur - Session 2020-21 Page 14 of 19adamNo ratings yet
- Ict Rev Igcse 5791 C9.unlockedDocument11 pagesIct Rev Igcse 5791 C9.unlockeddarsan979767% (3)
- Remote Sharing ApplicationDocument25 pagesRemote Sharing Applicationsachin singh100% (1)
- KS3 Revision Notes - 01 Introduction To ComputersDocument15 pagesKS3 Revision Notes - 01 Introduction To ComputersMugerwa CharlesNo ratings yet
- PC Hardware & Networking Syllabus PDFDocument2 pagesPC Hardware & Networking Syllabus PDFHassan MohamedNo ratings yet
- Course Notes - Unit 1 PDFDocument4 pagesCourse Notes - Unit 1 PDFMichael SkyersNo ratings yet
- Class VII-ICT Network & Communication-WK 2Document3 pagesClass VII-ICT Network & Communication-WK 2shayan kashifNo ratings yet
- UNIT 6 Hardware & Software Concepts PDFDocument9 pagesUNIT 6 Hardware & Software Concepts PDFlavanyatumuNo ratings yet
- Computer Network Practical FileDocument31 pagesComputer Network Practical FileAbhishek JainNo ratings yet
- KS3 Ict NotesDocument47 pagesKS3 Ict NotesKayla the Awesome100% (1)
- Effects of Using ICTDocument12 pagesEffects of Using ICTMaaz RashidNo ratings yet
- Classless AddressingDocument9 pagesClassless AddressingBurim PlakolliNo ratings yet
- Teachers HandbookDocument16 pagesTeachers HandbookRoberto PiresNo ratings yet
- Topic 1 - Introduction To C# ProgrammingDocument42 pagesTopic 1 - Introduction To C# ProgrammingKhalid Mehboob100% (1)
- Olevel Computer Science Notes 2210 PDFDocument18 pagesOlevel Computer Science Notes 2210 PDFEmaanNo ratings yet
- Difference Between Baseband and Broadband TransmissionDocument3 pagesDifference Between Baseband and Broadband Transmissionfellix smithNo ratings yet
- GCC Unit 1Document83 pagesGCC Unit 1Bhargava TipirisettyNo ratings yet
- Selected Topics in Computer Science CHDocument24 pagesSelected Topics in Computer Science CHMehari TemesgenNo ratings yet
- High-Level Language & Low-Level Language PDFDocument5 pagesHigh-Level Language & Low-Level Language PDFImran MuhammadNo ratings yet
- Data Structures and Algorithms: Module - 3 Linked ListDocument44 pagesData Structures and Algorithms: Module - 3 Linked Listbhumika.verma00No ratings yet
- Data Communication and Networking Slides Chap 1Document31 pagesData Communication and Networking Slides Chap 1Takarookie67% (3)
- Lecture 8 - TCP IpDocument24 pagesLecture 8 - TCP IpAbdul Rehman100% (1)
- Week 2 - Data Representation - StudDocument25 pagesWeek 2 - Data Representation - Studtipu tipuNo ratings yet
- Algorithms NotesDocument93 pagesAlgorithms NotesPrajakta BagalNo ratings yet
- Information Technology (9626) - A Level Notes Information Technology (9626) - A Level NotesDocument49 pagesInformation Technology (9626) - A Level Notes Information Technology (9626) - A Level NotesKatherine PierceNo ratings yet
- 9626 Learner Guide (For Examination From 2022)Document27 pages9626 Learner Guide (For Examination From 2022)gabkaimviNo ratings yet
- Compu TalentDocument2 pagesCompu TalentNitin Wandre100% (1)
- Balancing Function and FashionDocument41 pagesBalancing Function and FashionFernand Torres LayugNo ratings yet
- Cloud Computing Unit-4Document61 pagesCloud Computing Unit-4Aswini LayaNo ratings yet
- Sample EndDocument120 pagesSample Endairjaffna.lk100% (1)
- Question Bank For Computer ArchitectureDocument23 pagesQuestion Bank For Computer ArchitecturesuryaNo ratings yet
- Module-1 Chapter1Document55 pagesModule-1 Chapter1Disha ShettyNo ratings yet
- Internet SecurityDocument3 pagesInternet Securityannelireino100% (1)
- OSI Model CheatSheet - ATech (Waqas Karim) v1.2 PDFDocument1 pageOSI Model CheatSheet - ATech (Waqas Karim) v1.2 PDFSeptian Rahman HakimNo ratings yet
- CN Stop and Wait ProtocolDocument3 pagesCN Stop and Wait ProtocolPriyadarshini RNo ratings yet
- 1.3.1a Networks and Topologies (LANs)Document25 pages1.3.1a Networks and Topologies (LANs)emona.mockuNo ratings yet
- CN Unit1 8-7-10Document20 pagesCN Unit1 8-7-10nallapatiharika0% (1)
- Module 2 - Lecture 3 - Network Configuration - LAN SetupDocument28 pagesModule 2 - Lecture 3 - Network Configuration - LAN SetupZeeshan BhattiNo ratings yet
- 1.1 AlgorithmsDocument68 pages1.1 AlgorithmsJCNo ratings yet
- Network Management System A Complete Guide - 2020 EditionFrom EverandNetwork Management System A Complete Guide - 2020 EditionRating: 5 out of 5 stars5/5 (1)
- Block Cipher PrincipalDocument4 pagesBlock Cipher PrincipalAnurag PokhriyalNo ratings yet
- CFD Analysis On Hdpe Double Pipe Heat ExchangerDocument8 pagesCFD Analysis On Hdpe Double Pipe Heat ExchangerSai Krishna SKNo ratings yet
- Oracle in Erp: Presenting By: Sai Krishna Jaligama 16K81A03D6Document9 pagesOracle in Erp: Presenting By: Sai Krishna Jaligama 16K81A03D6Sai Krishna SKNo ratings yet
- Take Away Kit PDFDocument2 pagesTake Away Kit PDFSai Krishna SKNo ratings yet
- Slide 1prinicipal Component AnalysisDocument2 pagesSlide 1prinicipal Component AnalysisSai Krishna SKNo ratings yet
- Sae Baja Chassis: Step 1: Step 1: LEARN THE RULES!!!!!Document17 pagesSae Baja Chassis: Step 1: Step 1: LEARN THE RULES!!!!!Sai Krishna SKNo ratings yet
- CFD Analysis of Automotive Ventilated Disc Brake Rotor: Amol V. More, Prof - Sivakumar RDocument5 pagesCFD Analysis of Automotive Ventilated Disc Brake Rotor: Amol V. More, Prof - Sivakumar RSai Krishna SKNo ratings yet
- ExternalDocument17 pagesExternalSai Krishna SKNo ratings yet
- Seminar Presentation: Types of Geo-Thermal Power PlantsDocument7 pagesSeminar Presentation: Types of Geo-Thermal Power PlantsSai Krishna SKNo ratings yet
- Take Away KitDocument2 pagesTake Away KitSai Krishna SKNo ratings yet
- Charan SeminorDocument19 pagesCharan SeminorSai Krishna SKNo ratings yet
- SAEDocument12 pagesSAESai Krishna SKNo ratings yet
- Cad CamDocument50 pagesCad CamSai Krishna SKNo ratings yet
- Baja SAE - 2018 Cost Report SubmissionDocument23 pagesBaja SAE - 2018 Cost Report SubmissionSai Krishna SKNo ratings yet
- Oop in Python Best ResourcesDocument1 pageOop in Python Best ResourcesSamuel ForknerNo ratings yet
- SFD, BMD and Deflection of Beams Question SheetDocument4 pagesSFD, BMD and Deflection of Beams Question SheetSai Krishna SKNo ratings yet
- Simple Stresses and Strains PDFDocument2 pagesSimple Stresses and Strains PDFSai Krishna SK100% (1)
- SOM Sheet 3: Complex Stresses - 2 Minute QuestionsDocument2 pagesSOM Sheet 3: Complex Stresses - 2 Minute QuestionsSai Krishna SKNo ratings yet
- Simple Stresses and Strains PDFDocument2 pagesSimple Stresses and Strains PDFSai Krishna SK100% (1)
- Ansys PDFDocument9 pagesAnsys PDFSai Krishna SKNo ratings yet
- Caesar Cipher ReportDocument5 pagesCaesar Cipher ReportAnonymous troowCm6PRNo ratings yet
- Confidentiality and Privacy ControlsDocument4 pagesConfidentiality and Privacy ControlsAmara Prabasari100% (1)
- Privacy Protection Based Access Control Scheme in Cloud-Based Services - 1crore ProjectsDocument5 pagesPrivacy Protection Based Access Control Scheme in Cloud-Based Services - 1crore ProjectsLalitha PonnamNo ratings yet
- C235 - IT Security and Management: Modern Symmetric CiphersDocument33 pagesC235 - IT Security and Management: Modern Symmetric CiphersSundeel Bin HaleemNo ratings yet
- Basic CryptanalysisDocument363 pagesBasic CryptanalysisToma XtraNo ratings yet
- Cryptography and Number Theory - Presentation - MARSDocument21 pagesCryptography and Number Theory - Presentation - MARSsunil_38No ratings yet
- Cryptodict m3Document15 pagesCryptodict m3Velibor SabanNo ratings yet
- Classical Encryption TechniquesDocument12 pagesClassical Encryption Techniquessushantluitel39No ratings yet
- UNIT-3 Notes CNSDocument19 pagesUNIT-3 Notes CNSramNo ratings yet
- Difference Between Steganography and CryptographyDocument1 pageDifference Between Steganography and CryptographyMohamed AliNo ratings yet
- Public KeyDocument320 pagesPublic Keytayel67% (3)
- A Lightweight Encryption Algorithm IOTDocument10 pagesA Lightweight Encryption Algorithm IOTMohammed F. Albrawy100% (1)
- Class Test 1Document3 pagesClass Test 1Magi100% (1)
- CH 02Document35 pagesCH 02ojaym alojaymNo ratings yet
- Jit QPDocument61 pagesJit QPKumar kumarNo ratings yet
- Cryptanalysis and Types of AttacksDocument3 pagesCryptanalysis and Types of AttacksSourav DebnathNo ratings yet
- Applications For Public-Key CryptosystemsDocument25 pagesApplications For Public-Key CryptosystemsRanjanNo ratings yet
- Instapdf - in Computer System and Application Tybcom Sem 6 MCQ 903Document12 pagesInstapdf - in Computer System and Application Tybcom Sem 6 MCQ 903Alok RanjanNo ratings yet
- Unit6 SecurityDocument78 pagesUnit6 SecuritygloudpsdkNo ratings yet
- KSA T318 MTA FALL 2022 2023 AnswerDocument6 pagesKSA T318 MTA FALL 2022 2023 AnswerMohamed El ShazlyNo ratings yet
- Deniability CipherDocument7 pagesDeniability CipherCasandra EdwardsNo ratings yet
- Real-Time Segregation of Encrypted Data Using EntropyDocument10 pagesReal-Time Segregation of Encrypted Data Using EntropyammuvijuNo ratings yet
- AES11Document51 pagesAES11Karthiga MuruganNo ratings yet
- CYB102 Module 2Document5 pagesCYB102 Module 2Umar FaruqNo ratings yet
- PHD DissertationDocument197 pagesPHD DissertationLennin GalvezNo ratings yet
- Cie2 Set2 CNSDocument2 pagesCie2 Set2 CNSThiru KumaraNo ratings yet
- 01-Introduction To CryptographyDocument107 pages01-Introduction To CryptographyHggNo ratings yet
- Encrypting Data With The Blowfish AlgorithmDocument4 pagesEncrypting Data With The Blowfish AlgorithmramachandraNo ratings yet
- An Analysis of Port Knocking and Single Packet Authorization Sebastien JeanquierDocument76 pagesAn Analysis of Port Knocking and Single Packet Authorization Sebastien JeanquierHenry OseiNo ratings yet
Presentation Layer PPT 1 PDF
Presentation Layer PPT 1 PDF
Uploaded by
Sai Krishna SK0 ratings0% found this document useful (0 votes)
345 views16 pagesThe presentation layer performs translation, encryption/decryption, authentication, and compression. Translation converts data between formats like ASCII and EBCDIC. Encryption encodes data using algorithms and keys, while decryption reverses the process. Authentication verifies sender identity using digital signatures that encrypt data in multiple steps. Compression reduces file size using lossless methods that preserve all data or lossy methods that sacrifice some quality.
Original Description:
Original Title
Presentation Layer ppt 1 pdf
Copyright
© © All Rights Reserved
Available Formats
PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentThe presentation layer performs translation, encryption/decryption, authentication, and compression. Translation converts data between formats like ASCII and EBCDIC. Encryption encodes data using algorithms and keys, while decryption reverses the process. Authentication verifies sender identity using digital signatures that encrypt data in multiple steps. Compression reduces file size using lossless methods that preserve all data or lossy methods that sacrifice some quality.
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
Download as pdf or txt
0 ratings0% found this document useful (0 votes)
345 views16 pagesPresentation Layer PPT 1 PDF
Presentation Layer PPT 1 PDF
Uploaded by
Sai Krishna SKThe presentation layer performs translation, encryption/decryption, authentication, and compression. Translation converts data between formats like ASCII and EBCDIC. Encryption encodes data using algorithms and keys, while decryption reverses the process. Authentication verifies sender identity using digital signatures that encrypt data in multiple steps. Compression reduces file size using lossless methods that preserve all data or lossy methods that sacrifice some quality.
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
Download as pdf or txt
You are on page 1of 16
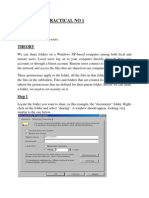
Presentation Layer
Functions of Presentation Layer
1. Translation
2. Encryption/Decryption
3. Authentication
4. Compression
1. Translation
• The internal representation of a piece of information from one machine to other is
called translation
• Translation can be done either directly or indirectly.
• In direct translation method(whether it is simplex, half duplex or full duplex)
ASCII code is translated into EBCDIC code at the receiver.
• In the indirect method, ASCII code is translated to a standard format at the
sender and translated into EBCDIC at the receiver.
• Direct method is not acceptable in most cases.
• Indirect method is recommended by the OSI. The recommended model is called
abstract syntax notation 1.
• This model not only takes care of translation problem but also handles other
formatting problems such as diverse nature of data.
• It uses the concept of object where an object is defined as an information entity with
type and value that can be easily translated from one representation to other.
2. Encryption/Decryption
• Encryption means that the sender transforms the original information to another
form and sends the resulting unintelligible message out over the network.
• Decryption reverses the encryption process in order to transform the message back to
its original form.
• The Sender uses an encryption algorithm and a key to transform the plain text into
a cipher text.
• The Receiver uses a decryption algorithm and a key to transform the cipher text back
to the original plaintext
• Encryption and decryption methods fall into two categories
• Conventional method
• public key method
Conventional methods
• Conventional encryption methods are of two types
• Character level encryption
• Substitutional
• Mono alphabetic substitution
• Poly alphabetic substitution
• transpositional
• Bit level encryption
• Encoding/decoding
• Permutation
• Substitution
• Product
• Exclusive OR
• Rotation
• Data encryption standard
Substitutional Encryption
• It is the simplest level of character level encryption
• Mono alphabetic encryption replaces each character by another
character(some times called as Caesar Cipher)
• It simply adds a number to the ASCII code of the character and
decryption algorithm simply subtracts the same number. Disadvantage is
it can be easily broken by a snooper.
• Poly alphabetic encryption technique is to find the position of the character
in the text and use that value as the key. Each occurrence of the character
can have a different substitute. Even this code can be easily broken by an
experienced snooper
Transpositional encryption
• A more secure method is transpositional encryption.
• Here characters retain their plaintext form but change their positions to
create a cipher text.
• The text is organized into a two dimensional table and the columns are
interchanged according to a key.
• The key defines which columns should be swapped.
• Transpositional encryption is not very secure.
• The character frequencies are preserved and the snooper can find the plain
text through trial and error.
Bit level encryption
• In bit level encryption techniques, data as text, graphics, audio or video are first divided into
blocks of bits, then altered by encoding/decoding, permutation, substitution, exclusive OR,
rotation and so on.
• Encoding/Decoding: A decoder changes an input of n bits into an output of 2n bits. The output
should have only one single 1, located at the position determined by the input.eg: 01 will be
decoded as 0010
• Permutation: it is the fact transposition at bit level. It is done in 3 ways.
• Straight permutation: I/O bits are preserved only the positions are changed.
• Compressed permutation: No. of bits are reduced by dropping the no.of bits.
• Expanded permutation: No. of bits are increased by repeating some bits.
• Substitution: n bits are substituted another n bits using combination of P-boxes(a permutation
unit that can easily be made as a hardware circuit with internal wiring), encoders and decoders.
• Product: The P-boxes and S-boxes can be combined and called a product. A product unit is
made of several stages of P-boxes and S-boxes.
• Exclusive OR: The input and the key are exclusive ORed together to create the output. (xclusive
OR operation on two bits is 0 if the two bits are same and 1 if they are different)
• Rotation: it rotates bits to the right or to the left. The key is the number of bits to be rotated.
Data Encryption Standard(DES)
• One example of bit -level encryption is DES.
• It is designed by IBM and adopted by US Govt. for non military and non
classified use.
• The algorithm encrypts a 64 bit plain text using a 56 bit key.
• The text is put through 19 different and very complex procedures to create
a 64 bit cipher text.
• The first and last two steps are simple, but 2nd and 17th steps are complex.
Public Key methods
• In conventional method decryption is always inverse of encryption, so
anyone who knows encryption algorithm and key can deduce decryption
algorithm. The solution to this is public key encryption.
• In Public key encryption user has the same encryption algorithm and key.
But decryption algorithm and key are kept secret. Only an authorized
person can decrypt it( it is not reverse of encryption alg).
• Even if the intruder knows encryption algorithm and encryption key he will
be still unable to decipher the code.
• The next slide illustrates using how encryption algorithm and public keys
are announced openly and decryption algorithm and key are kept secretly.
Authentication
• Authentication means verifying the identity of a sender.
• Example of such authentication using public key encryption /decryption is
Digital Signature.
• In network transactions when you can’t sign personally we can create
equivalent of an electronic or digital signature by the way you send data.
• One implementation uses the reciprocity of RSA.
• Like how Kp and Ks are reciprocal digital signatures add another level of
encryption and decryption to the process.
Working of Digital Signature
• Customer encrypts plain text(P) using a secret key (Ks-1) and creates first
level of cipher text (C1).
• The first Cipher text is encrypted again using public key (Kp-1) to create
second cipher text (C2).
• C2 is sent through the network and received by the bank.
• Bank uses secret key (Ks-2) to decipher C2 to C1.
• It then uses the public key (Kp-2) to decipher C1 to original plain text.
• Unless the customer sends Ks-1 and Kp-1 bank would not know Ks-2 and
Kp-2. So he cannot say he did not do the transaction
Data Compression
• Data compression reduces no. of bits sent.
• Methods used to compress data are generally divided into two broad
categories 1) lossless 2) lossy
• Lossless compression: Here compressing and decompressing algorithms are
usually the inverse of each other.
• Lossy compression: The decompressed information neednot be an exact
replica of the original information but some thing very close it is called
lossy data compression
Loss less compression techniques
• Run length Encoding: When data contain strings of repeated symbols the strings
can be replaced by a special marker followed by repeated symbol followed by
number of occurrences.
• Statistical compression: This method uses short codes for frequent symbols and
long codes for infrequent symbols. In this way length of total data is reduced
tremendously. Three common encoding systems with this principle are
• Morse Code: uses variable length combinations of mark(dash) and space(dot) to encode
data.
• Huffman coding: Uses variable length codes(strings of 0’s and 1’s) to encode the set of
symbols.
• Limpel-ziv encoding: It looks for repeated strings or words and stores them in variables.
It then replaces the occurrences of that string with a pointer to that variable.
• Relative of reducing compression: Another way of reducing the number of bits is
relative compression or differential encoding. This is useful if we are sending
consecutive frames.
Lossy Compression
• Methods of Lossy compression will lose some of the original data in
progress
• Methods that have been developed using lossy compression techniques are
• Photographic experts group(JPEG)
• Motion picture experts group(MPEG)
You might also like
- KS3 Presentation - 24 Introduction To NetworksDocument48 pagesKS3 Presentation - 24 Introduction To Networkshunia abbass100% (1)
- Computer Network Principles - Revision Exam PaperDocument18 pagesComputer Network Principles - Revision Exam PaperEse KelvinNo ratings yet
- Java and Multi ThreadingDocument44 pagesJava and Multi ThreadingShraddha Sheth100% (1)
- DC Lab 1 Data RepresentationDocument3 pagesDC Lab 1 Data RepresentationbhavnaNo ratings yet
- CSCU Module 04 Data Encryption PDFDocument23 pagesCSCU Module 04 Data Encryption PDFSandeep Roy100% (1)
- Lesson Plan Wired and Wireless NetworksDocument7 pagesLesson Plan Wired and Wireless NetworksTek CasoneteNo ratings yet
- More Stable and Secure ConnectionDocument3 pagesMore Stable and Secure ConnectionSpidocadoNo ratings yet
- Paper 2 Theory For 9618Document33 pagesPaper 2 Theory For 9618rayan.muzzammil5No ratings yet
- Presentation Layer & Session LayerDocument51 pagesPresentation Layer & Session LayerAnonymous fp8NP80% (1)
- Computer Science Lesson Plan Week 3 - T3-PracticalDocument4 pagesComputer Science Lesson Plan Week 3 - T3-PracticalIshrat JehanNo ratings yet
- Introduction To Computer NetworksDocument6 pagesIntroduction To Computer NetworksMahesh KhatiwadaNo ratings yet
- Peripheral DevicesDocument22 pagesPeripheral DevicesHans Leo LatigayNo ratings yet
- IGCSE ICT - Types of Computer NetworksDocument5 pagesIGCSE ICT - Types of Computer NetworksSudeepa HerathNo ratings yet
- Networking 1Document28 pagesNetworking 1rahul3071No ratings yet
- The Electronic Equivalent of The Document and Fingerprint Pair Is The Message and Digest PairDocument36 pagesThe Electronic Equivalent of The Document and Fingerprint Pair Is The Message and Digest PairRAJ TAPASENo ratings yet
- NC101 Module 5Document8 pagesNC101 Module 5Sarah May Nacion MorescoNo ratings yet
- Critical Thinking Chapter 1 QuestionsDocument11 pagesCritical Thinking Chapter 1 Questionsapi-347017345No ratings yet
- Ethernet Layer 2, Switching and Bridging Logic Lec2Document15 pagesEthernet Layer 2, Switching and Bridging Logic Lec2Hiroyo ChanNo ratings yet
- CCNA Assignment 1Document4 pagesCCNA Assignment 1Sudhindra HnNo ratings yet
- Introduction To Networks: KVS Regional Office Jaipur - Session 2020-21 Page 14 of 19Document3 pagesIntroduction To Networks: KVS Regional Office Jaipur - Session 2020-21 Page 14 of 19adamNo ratings yet
- Ict Rev Igcse 5791 C9.unlockedDocument11 pagesIct Rev Igcse 5791 C9.unlockeddarsan979767% (3)
- Remote Sharing ApplicationDocument25 pagesRemote Sharing Applicationsachin singh100% (1)
- KS3 Revision Notes - 01 Introduction To ComputersDocument15 pagesKS3 Revision Notes - 01 Introduction To ComputersMugerwa CharlesNo ratings yet
- PC Hardware & Networking Syllabus PDFDocument2 pagesPC Hardware & Networking Syllabus PDFHassan MohamedNo ratings yet
- Course Notes - Unit 1 PDFDocument4 pagesCourse Notes - Unit 1 PDFMichael SkyersNo ratings yet
- Class VII-ICT Network & Communication-WK 2Document3 pagesClass VII-ICT Network & Communication-WK 2shayan kashifNo ratings yet
- UNIT 6 Hardware & Software Concepts PDFDocument9 pagesUNIT 6 Hardware & Software Concepts PDFlavanyatumuNo ratings yet
- Computer Network Practical FileDocument31 pagesComputer Network Practical FileAbhishek JainNo ratings yet
- KS3 Ict NotesDocument47 pagesKS3 Ict NotesKayla the Awesome100% (1)
- Effects of Using ICTDocument12 pagesEffects of Using ICTMaaz RashidNo ratings yet
- Classless AddressingDocument9 pagesClassless AddressingBurim PlakolliNo ratings yet
- Teachers HandbookDocument16 pagesTeachers HandbookRoberto PiresNo ratings yet
- Topic 1 - Introduction To C# ProgrammingDocument42 pagesTopic 1 - Introduction To C# ProgrammingKhalid Mehboob100% (1)
- Olevel Computer Science Notes 2210 PDFDocument18 pagesOlevel Computer Science Notes 2210 PDFEmaanNo ratings yet
- Difference Between Baseband and Broadband TransmissionDocument3 pagesDifference Between Baseband and Broadband Transmissionfellix smithNo ratings yet
- GCC Unit 1Document83 pagesGCC Unit 1Bhargava TipirisettyNo ratings yet
- Selected Topics in Computer Science CHDocument24 pagesSelected Topics in Computer Science CHMehari TemesgenNo ratings yet
- High-Level Language & Low-Level Language PDFDocument5 pagesHigh-Level Language & Low-Level Language PDFImran MuhammadNo ratings yet
- Data Structures and Algorithms: Module - 3 Linked ListDocument44 pagesData Structures and Algorithms: Module - 3 Linked Listbhumika.verma00No ratings yet
- Data Communication and Networking Slides Chap 1Document31 pagesData Communication and Networking Slides Chap 1Takarookie67% (3)
- Lecture 8 - TCP IpDocument24 pagesLecture 8 - TCP IpAbdul Rehman100% (1)
- Week 2 - Data Representation - StudDocument25 pagesWeek 2 - Data Representation - Studtipu tipuNo ratings yet
- Algorithms NotesDocument93 pagesAlgorithms NotesPrajakta BagalNo ratings yet
- Information Technology (9626) - A Level Notes Information Technology (9626) - A Level NotesDocument49 pagesInformation Technology (9626) - A Level Notes Information Technology (9626) - A Level NotesKatherine PierceNo ratings yet
- 9626 Learner Guide (For Examination From 2022)Document27 pages9626 Learner Guide (For Examination From 2022)gabkaimviNo ratings yet
- Compu TalentDocument2 pagesCompu TalentNitin Wandre100% (1)
- Balancing Function and FashionDocument41 pagesBalancing Function and FashionFernand Torres LayugNo ratings yet
- Cloud Computing Unit-4Document61 pagesCloud Computing Unit-4Aswini LayaNo ratings yet
- Sample EndDocument120 pagesSample Endairjaffna.lk100% (1)
- Question Bank For Computer ArchitectureDocument23 pagesQuestion Bank For Computer ArchitecturesuryaNo ratings yet
- Module-1 Chapter1Document55 pagesModule-1 Chapter1Disha ShettyNo ratings yet
- Internet SecurityDocument3 pagesInternet Securityannelireino100% (1)
- OSI Model CheatSheet - ATech (Waqas Karim) v1.2 PDFDocument1 pageOSI Model CheatSheet - ATech (Waqas Karim) v1.2 PDFSeptian Rahman HakimNo ratings yet
- CN Stop and Wait ProtocolDocument3 pagesCN Stop and Wait ProtocolPriyadarshini RNo ratings yet
- 1.3.1a Networks and Topologies (LANs)Document25 pages1.3.1a Networks and Topologies (LANs)emona.mockuNo ratings yet
- CN Unit1 8-7-10Document20 pagesCN Unit1 8-7-10nallapatiharika0% (1)
- Module 2 - Lecture 3 - Network Configuration - LAN SetupDocument28 pagesModule 2 - Lecture 3 - Network Configuration - LAN SetupZeeshan BhattiNo ratings yet
- 1.1 AlgorithmsDocument68 pages1.1 AlgorithmsJCNo ratings yet
- Network Management System A Complete Guide - 2020 EditionFrom EverandNetwork Management System A Complete Guide - 2020 EditionRating: 5 out of 5 stars5/5 (1)
- Block Cipher PrincipalDocument4 pagesBlock Cipher PrincipalAnurag PokhriyalNo ratings yet
- CFD Analysis On Hdpe Double Pipe Heat ExchangerDocument8 pagesCFD Analysis On Hdpe Double Pipe Heat ExchangerSai Krishna SKNo ratings yet
- Oracle in Erp: Presenting By: Sai Krishna Jaligama 16K81A03D6Document9 pagesOracle in Erp: Presenting By: Sai Krishna Jaligama 16K81A03D6Sai Krishna SKNo ratings yet
- Take Away Kit PDFDocument2 pagesTake Away Kit PDFSai Krishna SKNo ratings yet
- Slide 1prinicipal Component AnalysisDocument2 pagesSlide 1prinicipal Component AnalysisSai Krishna SKNo ratings yet
- Sae Baja Chassis: Step 1: Step 1: LEARN THE RULES!!!!!Document17 pagesSae Baja Chassis: Step 1: Step 1: LEARN THE RULES!!!!!Sai Krishna SKNo ratings yet
- CFD Analysis of Automotive Ventilated Disc Brake Rotor: Amol V. More, Prof - Sivakumar RDocument5 pagesCFD Analysis of Automotive Ventilated Disc Brake Rotor: Amol V. More, Prof - Sivakumar RSai Krishna SKNo ratings yet
- ExternalDocument17 pagesExternalSai Krishna SKNo ratings yet
- Seminar Presentation: Types of Geo-Thermal Power PlantsDocument7 pagesSeminar Presentation: Types of Geo-Thermal Power PlantsSai Krishna SKNo ratings yet
- Take Away KitDocument2 pagesTake Away KitSai Krishna SKNo ratings yet
- Charan SeminorDocument19 pagesCharan SeminorSai Krishna SKNo ratings yet
- SAEDocument12 pagesSAESai Krishna SKNo ratings yet
- Cad CamDocument50 pagesCad CamSai Krishna SKNo ratings yet
- Baja SAE - 2018 Cost Report SubmissionDocument23 pagesBaja SAE - 2018 Cost Report SubmissionSai Krishna SKNo ratings yet
- Oop in Python Best ResourcesDocument1 pageOop in Python Best ResourcesSamuel ForknerNo ratings yet
- SFD, BMD and Deflection of Beams Question SheetDocument4 pagesSFD, BMD and Deflection of Beams Question SheetSai Krishna SKNo ratings yet
- Simple Stresses and Strains PDFDocument2 pagesSimple Stresses and Strains PDFSai Krishna SK100% (1)
- SOM Sheet 3: Complex Stresses - 2 Minute QuestionsDocument2 pagesSOM Sheet 3: Complex Stresses - 2 Minute QuestionsSai Krishna SKNo ratings yet
- Simple Stresses and Strains PDFDocument2 pagesSimple Stresses and Strains PDFSai Krishna SK100% (1)
- Ansys PDFDocument9 pagesAnsys PDFSai Krishna SKNo ratings yet
- Caesar Cipher ReportDocument5 pagesCaesar Cipher ReportAnonymous troowCm6PRNo ratings yet
- Confidentiality and Privacy ControlsDocument4 pagesConfidentiality and Privacy ControlsAmara Prabasari100% (1)
- Privacy Protection Based Access Control Scheme in Cloud-Based Services - 1crore ProjectsDocument5 pagesPrivacy Protection Based Access Control Scheme in Cloud-Based Services - 1crore ProjectsLalitha PonnamNo ratings yet
- C235 - IT Security and Management: Modern Symmetric CiphersDocument33 pagesC235 - IT Security and Management: Modern Symmetric CiphersSundeel Bin HaleemNo ratings yet
- Basic CryptanalysisDocument363 pagesBasic CryptanalysisToma XtraNo ratings yet
- Cryptography and Number Theory - Presentation - MARSDocument21 pagesCryptography and Number Theory - Presentation - MARSsunil_38No ratings yet
- Cryptodict m3Document15 pagesCryptodict m3Velibor SabanNo ratings yet
- Classical Encryption TechniquesDocument12 pagesClassical Encryption Techniquessushantluitel39No ratings yet
- UNIT-3 Notes CNSDocument19 pagesUNIT-3 Notes CNSramNo ratings yet
- Difference Between Steganography and CryptographyDocument1 pageDifference Between Steganography and CryptographyMohamed AliNo ratings yet
- Public KeyDocument320 pagesPublic Keytayel67% (3)
- A Lightweight Encryption Algorithm IOTDocument10 pagesA Lightweight Encryption Algorithm IOTMohammed F. Albrawy100% (1)
- Class Test 1Document3 pagesClass Test 1Magi100% (1)
- CH 02Document35 pagesCH 02ojaym alojaymNo ratings yet
- Jit QPDocument61 pagesJit QPKumar kumarNo ratings yet
- Cryptanalysis and Types of AttacksDocument3 pagesCryptanalysis and Types of AttacksSourav DebnathNo ratings yet
- Applications For Public-Key CryptosystemsDocument25 pagesApplications For Public-Key CryptosystemsRanjanNo ratings yet
- Instapdf - in Computer System and Application Tybcom Sem 6 MCQ 903Document12 pagesInstapdf - in Computer System and Application Tybcom Sem 6 MCQ 903Alok RanjanNo ratings yet
- Unit6 SecurityDocument78 pagesUnit6 SecuritygloudpsdkNo ratings yet
- KSA T318 MTA FALL 2022 2023 AnswerDocument6 pagesKSA T318 MTA FALL 2022 2023 AnswerMohamed El ShazlyNo ratings yet
- Deniability CipherDocument7 pagesDeniability CipherCasandra EdwardsNo ratings yet
- Real-Time Segregation of Encrypted Data Using EntropyDocument10 pagesReal-Time Segregation of Encrypted Data Using EntropyammuvijuNo ratings yet
- AES11Document51 pagesAES11Karthiga MuruganNo ratings yet
- CYB102 Module 2Document5 pagesCYB102 Module 2Umar FaruqNo ratings yet
- PHD DissertationDocument197 pagesPHD DissertationLennin GalvezNo ratings yet
- Cie2 Set2 CNSDocument2 pagesCie2 Set2 CNSThiru KumaraNo ratings yet
- 01-Introduction To CryptographyDocument107 pages01-Introduction To CryptographyHggNo ratings yet
- Encrypting Data With The Blowfish AlgorithmDocument4 pagesEncrypting Data With The Blowfish AlgorithmramachandraNo ratings yet
- An Analysis of Port Knocking and Single Packet Authorization Sebastien JeanquierDocument76 pagesAn Analysis of Port Knocking and Single Packet Authorization Sebastien JeanquierHenry OseiNo ratings yet