Professional Documents
Culture Documents
Mitigating Security Risks at The Network's Edge: Best Practices For Distributed Enterprises
Mitigating Security Risks at The Network's Edge: Best Practices For Distributed Enterprises
Uploaded by
CyrllandCopyright:
Available Formats
You might also like
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeFrom EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeRating: 4 out of 5 stars4/5 (5834)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreFrom EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreRating: 4 out of 5 stars4/5 (1093)
- Never Split the Difference: Negotiating As If Your Life Depended On ItFrom EverandNever Split the Difference: Negotiating As If Your Life Depended On ItRating: 4.5 out of 5 stars4.5/5 (852)
- Grit: The Power of Passion and PerseveranceFrom EverandGrit: The Power of Passion and PerseveranceRating: 4 out of 5 stars4/5 (590)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceFrom EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceRating: 4 out of 5 stars4/5 (903)
- Shoe Dog: A Memoir by the Creator of NikeFrom EverandShoe Dog: A Memoir by the Creator of NikeRating: 4.5 out of 5 stars4.5/5 (541)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersFrom EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersRating: 4.5 out of 5 stars4.5/5 (349)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureFrom EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureRating: 4.5 out of 5 stars4.5/5 (474)
- Her Body and Other Parties: StoriesFrom EverandHer Body and Other Parties: StoriesRating: 4 out of 5 stars4/5 (823)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)From EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Rating: 4.5 out of 5 stars4.5/5 (122)
- The Emperor of All Maladies: A Biography of CancerFrom EverandThe Emperor of All Maladies: A Biography of CancerRating: 4.5 out of 5 stars4.5/5 (271)
- The Little Book of Hygge: Danish Secrets to Happy LivingFrom EverandThe Little Book of Hygge: Danish Secrets to Happy LivingRating: 3.5 out of 5 stars3.5/5 (405)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyFrom EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyRating: 3.5 out of 5 stars3.5/5 (2259)
- The Yellow House: A Memoir (2019 National Book Award Winner)From EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Rating: 4 out of 5 stars4/5 (98)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaFrom EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaRating: 4.5 out of 5 stars4.5/5 (266)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryFrom EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryRating: 3.5 out of 5 stars3.5/5 (231)
- Team of Rivals: The Political Genius of Abraham LincolnFrom EverandTeam of Rivals: The Political Genius of Abraham LincolnRating: 4.5 out of 5 stars4.5/5 (234)
- On Fire: The (Burning) Case for a Green New DealFrom EverandOn Fire: The (Burning) Case for a Green New DealRating: 4 out of 5 stars4/5 (74)
- The Unwinding: An Inner History of the New AmericaFrom EverandThe Unwinding: An Inner History of the New AmericaRating: 4 out of 5 stars4/5 (45)
- Manufacturing Execution System (MES) : Deployment GuideDocument47 pagesManufacturing Execution System (MES) : Deployment GuideNhat Tan MaiNo ratings yet
- Precision Fiber Products IncDocument3 pagesPrecision Fiber Products IncCyrllandNo ratings yet
- cyr-ENG-412E TCP IP Network FundamentalsDocument8 pagescyr-ENG-412E TCP IP Network FundamentalsCyrllandNo ratings yet
- Fundamentals of Wireless LansDocument1 pageFundamentals of Wireless LansCyrllandNo ratings yet
- MikroTik Training Terms & ConditionsDocument2 pagesMikroTik Training Terms & ConditionsCyrllandNo ratings yet
- Training Enquiry Form MTZADocument1 pageTraining Enquiry Form MTZACyrllandNo ratings yet
- AWS Certified Solutions Architect - Associate (SAA-C02) Exam GuideDocument2 pagesAWS Certified Solutions Architect - Associate (SAA-C02) Exam GuideCyrllandNo ratings yet
- CyberAces Module3-Python 5 PracticalUsesDocument15 pagesCyberAces Module3-Python 5 PracticalUsesCyrllandNo ratings yet
- Mobile Device Management: Key Components, V1.0: September 2012Document12 pagesMobile Device Management: Key Components, V1.0: September 2012CyrllandNo ratings yet
- CyberAces Module3-Python 3 ScriptsDocument16 pagesCyberAces Module3-Python 3 ScriptsCyrllandNo ratings yet
- CyberAces Module3-Python 2 FlowDocument17 pagesCyberAces Module3-Python 2 FlowCyrllandNo ratings yet
- 2018Q1 NSE 1 Master Course DescriptionDocument1 page2018Q1 NSE 1 Master Course DescriptionCyrllandNo ratings yet
- BYOD Solution Overview: Revised: August 7, 2013Document6 pagesBYOD Solution Overview: Revised: August 7, 2013CyrllandNo ratings yet
- 7 Steps To Upgrade IOS Image On Cisco Catalyst Switch or RouterDocument4 pages7 Steps To Upgrade IOS Image On Cisco Catalyst Switch or RouterCyrllandNo ratings yet
- CyberAces Module3-Python 1 IntroDocument19 pagesCyberAces Module3-Python 1 IntroCyrllandNo ratings yet
- Topic 3 DSS Methodologies and Technologies-V2Document28 pagesTopic 3 DSS Methodologies and Technologies-V2tofuNo ratings yet
- Lesson 27, 28,29Document2 pagesLesson 27, 28,29Nasheila Binti Abdul GaniNo ratings yet
- Component DiagramsDocument27 pagesComponent DiagramsSakshi RajputNo ratings yet
- 9 - Software TestingDocument61 pages9 - Software TestingAmitabha DeyNo ratings yet
- Imdrf Cons PPMDCDocument45 pagesImdrf Cons PPMDCAndres CañaveralNo ratings yet
- Bandwidth Monitoring Tools With Alert Management: Loo Kar Chung Tp012661Document19 pagesBandwidth Monitoring Tools With Alert Management: Loo Kar Chung Tp012661selvanskyNo ratings yet
- Hillstone POC Setting Guide iNGFW StoneOS 5.5R6 V2.1Document185 pagesHillstone POC Setting Guide iNGFW StoneOS 5.5R6 V2.1Carlos Alexandre Da Silva OvidioNo ratings yet
- Authentication Authorization and Accounting (AAA) Schemes in WiMAXDocument6 pagesAuthentication Authorization and Accounting (AAA) Schemes in WiMAXUsman MasoodNo ratings yet
- EME-Guide To Manage Enterprise MetadataDocument310 pagesEME-Guide To Manage Enterprise MetadataPraveen JoshiNo ratings yet
- Mi Microservices Eap 7 Reference Architecture 201606 enDocument153 pagesMi Microservices Eap 7 Reference Architecture 201606 enCarlosArturoQuirogaNo ratings yet
- How To Compress A Dump File in Data Pump Technology?Document11 pagesHow To Compress A Dump File in Data Pump Technology?srivasthavNo ratings yet
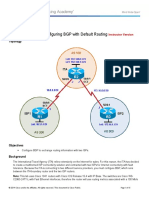
- CCNPv7 ROUTE Lab7-1 BGP Config InstructorDocument15 pagesCCNPv7 ROUTE Lab7-1 BGP Config InstructorAnonymous GK9mHwnrNo ratings yet
- MUCARBT200 ManualDocument31 pagesMUCARBT200 ManualNawi LaraNo ratings yet
- An Introduction To The BIOS: in This GuideDocument3 pagesAn Introduction To The BIOS: in This GuideAnilNo ratings yet
- Activity 2: Introduction To Assembly Language: Alcantara, John Joaquin S. (Student's Name) - September 2020Document8 pagesActivity 2: Introduction To Assembly Language: Alcantara, John Joaquin S. (Student's Name) - September 2020Kathleen Jhoren ReglosNo ratings yet
- Cyberops UndipDocument5 pagesCyberops UndipAdiNo ratings yet
- Huawei OceanStor 5000 V5 Series Hybrid Flash Storage Systems Technical White PaperDocument82 pagesHuawei OceanStor 5000 V5 Series Hybrid Flash Storage Systems Technical White PaperIvan CruzNo ratings yet
- Module 3 - Java ProgrammingDocument106 pagesModule 3 - Java ProgrammingPratham GuptaNo ratings yet
- Testing Energy Meter Compliance For Protocol & Performance As Per StandardsDocument23 pagesTesting Energy Meter Compliance For Protocol & Performance As Per StandardsceydaNo ratings yet
- Fast WCDMA Reselection at 2G CS Call Release Feature Delivery GuideDocument17 pagesFast WCDMA Reselection at 2G CS Call Release Feature Delivery GuideabojablNo ratings yet
- How Do You Control Pop-Up Windows in WinCC Unified PC RT and Comfort Panels Via S... - ID - 109810540 - Industry Support SiemensDocument12 pagesHow Do You Control Pop-Up Windows in WinCC Unified PC RT and Comfort Panels Via S... - ID - 109810540 - Industry Support SiemensAgnaldo JuniorNo ratings yet
- Summative Computer Maintenance css10Document3 pagesSummative Computer Maintenance css10Rolinn SicoNo ratings yet
- Status: Lan4 Lan3 Lan2 Lan1Document1 pageStatus: Lan4 Lan3 Lan2 Lan1Hasan Abdullah SahidNo ratings yet
- Dos Function Calls (Int 21H) : A. Terminate Program and Return To DosDocument5 pagesDos Function Calls (Int 21H) : A. Terminate Program and Return To DosgowthamvaniNo ratings yet
- SVVT Lab 2819044Document49 pagesSVVT Lab 2819044Prince KumarNo ratings yet
- ANEMAN User ManualDocument29 pagesANEMAN User ManualChaabane FaouziNo ratings yet
- E-Police Police Record Management SystemDocument4 pagesE-Police Police Record Management SystemMohammad Waqas100% (1)
- Sage CRM 6.0 Screen Customization GuideDocument133 pagesSage CRM 6.0 Screen Customization GuideMohamed MohamedNo ratings yet
- Firewall CrackingDocument14 pagesFirewall CrackingEldhose JacobNo ratings yet
Mitigating Security Risks at The Network's Edge: Best Practices For Distributed Enterprises
Mitigating Security Risks at The Network's Edge: Best Practices For Distributed Enterprises
Uploaded by
CyrllandOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Mitigating Security Risks at The Network's Edge: Best Practices For Distributed Enterprises
Mitigating Security Risks at The Network's Edge: Best Practices For Distributed Enterprises
Uploaded by
CyrllandCopyright:
Available Formats
White Paper / Security
Mitigating Security WHAT YOU’LL GET:
Risks at the ++ Threats in the distributed
enterprise and strategies
Network’s Edge for safer networks.
++ Network configuration
must-dos.
++ Information on cloud-based
Best Practices for security, PCI compliance, and
parallel networks.
Distributed Enterprises ++ 2 methods for increasing
security.
White Paper / Security
WHEN A SECURITY
BREACH OCCURS, 90%
OF MEAN TIME TO
Every year, the public relations specialists from at least one
blue-chip company invariably find themselves working around the RESOLUTION IS SPENT
clock on a crisis communications effort, attempting to explain to IDENTIFYING THE
an angry and justifiably fearful public what led to their company
compromising customer data. There’s always an immediate hit PROBLEM.1
to the company’s reputation, resulting in a loss of brand loyalty,
as customers take their business elsewhere. Of course, security
breaches are rife with many other consequences. IN 1300+ DATA
BREACH INCIDENTS
Potential impacts of a data breach:
IN 2013:
++ Legal costs
++ Loss of revenue or production due to unavailability of 91% OF THE
production resource
INCIDENTS ORIGINATED
++ Privacy compliance violation fines EXTERNALLY.
++ Payment Card Industry Data Security Standards violation
fines
88% TOOK MINUTES
++ Loss of intellectual, competitive or proprietary information
TO COMPROMISE
++ Loss of future profits resulting from an inability to AND EXFILTRATE.
demonstrate a strong security process to clients, vendors,
and partners
85% TOOK WEEKS
TO DISCOVER.
45% INCORPORATED
MALWARE.2
HQ
ALL OF THESE
PERCENTAGES
INCREASED
SIGNIFICANTLY FROM
THE PRIOR YEAR.
As the enterprise’s gateway to the Internet, distributed
enterprises at the network’s edge are highly vulnerable
to security threats.
©2015 Cradlepoint. All Rights Reserved. | +1.855.813.3385 | cradlepoint.com 2
White Paper / Security
ENTERPRISES WITH
SMALL DISTRIBUTED
LOCATIONS OR BRANCH
RISKS AT THE EDGE
OFFICES ARE AT THE
Enterprises with hundreds or thousands of locations face HIGHEST RISK OF
ongoing, massive challenges in maintaining network security
and are at a particularly high risk of suffering data breaches.
SUFFERING DATA
The highly vulnerable network edge must be carefully protected BREACHES.
against vulnerabilities, threats, and malicious attacks. Criminals
view the network’s edge as a soft target, since the distributed
locations frequently process highly sensitive data (e.g. credit 80% OF DATA BREACHES
cards) while often employing weaker security practices.
IN THE RETAIL
Factors contributing to security weaknesses in distributed edge INDUSTRY OCCURRED
networks include:
IN STORES WITH FEWER
++ No onsite IT support. Security measures like firmware THAN 100 EMPLOYEES.
updates and policy enforcement (e.g. firewall rules, access
control lists, wireless configurations, and VLANs) should
be conducted consistently, but can be easily be overlooked 24% OF ATTACKS
with no IT personnel on site. Even branches with local IT AFFECT INFORMATION
rarely have the resident expertise required to implement
and maintain complex security configurations. AND PROFESSIONAL
++ Lack of employee security awareness. In the age of SERVICES INDUSTRIES.
“Bring Your Own Device,” employee devices accessing
the corporate network present vulnerabilities through
rogue access points, phishing and other social engineering 34% OF DATA BREACHES
attacks. If not properly educated, employees put companies IMPACT FINANCIAL
at risk by opening emails or clicking links that allow
malware onto their device and the network.
ORGANIZATIONS.
++ Third parties & customers accessing the network.
Many enterprises interface with third parties that require 20% OF ATTACKS
Internet access. For example, an HVAC vendor may request TARGETED
to use the company’s network to monitor and adjust
heating and air settings. Kiosks within stores require MANUFACTURING AND
network access to transmit data, and customers demand RELATED INDUSTRIES.
WiFi for their handheld devices while shopping.
With multiple parties requiring Internet access and countless 30% OF DATA
risks for security breaches, enterprises must be ever vigilant BREACHES ARE
in developing, updating, and enforcing security policies on the
network’s edge. ACCESSED THROUGH
USER DEVICES.3
©2015 Cradlepoint. All Rights Reserved. | +1.855.813.3385 | cradlepoint.com 3
White Paper / Security
NETWORK ARCHITECTURES FOR THE
DISTRIBUTED ENTERPRISE
HUB-AND-SPOKE
HUB-AND-SPOKE: CONTROLLED ACCESS TO A ARCHITECTURE
CENTRALIZED DATA CENTER
USES VPN TO
“Hub-and-Spoke” describes architectures that leverage Virtual GRANT CONTROLLED
Private Networking (VPN) or Private Cloud Gateways. Some
virtual private networks may not use encryption to protect
ACCESS TO A
the privacy of data. While VPNs often provide security, an CENTRALIZED
unencrypted overlay network does not neatly fit within the
DATA CENTER.
secure or trusted categorization. VPNs should be configured to
act as a gateway to one or more segments of the environment,
leveraging robust authentication requirements, endpoint
inspection capabilities, and integration with virtual desktop,
proprietary device or Point-of-Sale technologies.
HQ
Store Unsecure Internet Connections
Secure VPN Network
©2015 Cradlepoint. All Rights Reserved. | +1.855.813.3385 | cradlepoint.com 4
White Paper / Security
BENEFITS KEY TO SUCCESS
Security. For multiple remote locations, a VPN can Secure the hub-and-spoke architecture with
save the cost of a dedicated Internet connection. isolation and segmentation. In the past, many
The maintenance of establishing a LAN connection organizations used single- or dual-firewall
through an Internet VPN is very low compared architecture that divided networks into segments
to traditional dedicated line solutions. With the at Layers 3 and 4, limiting IP address ranges and
proper encryption and authentication, the VPN Transmission Control Protocol (TCP) and User
architecture is a cost-effective and highly scalable Diagram Protocol (UDP) ports that could traverse
solution for transmitting data securely. one segment or another. While this network
security architecture is still the most common,
Threat detection. Data can be analyzed as it more organizations are starting to control traffic
moves through the network and used to identify at higher layers and use emerging technologies
potential threats or breaches. Leveraging the that facilitate traffic capture, analysis and control.
same intrusion prevention infrastructure in For more information, refer to page 11, “Two
the core of the network for the branch offices Methods for Increasing Security.”
minimizes chances of misconfiguration at the
edge of the network.
THE CLOUD FOR SECURITY SERVICES
Governance. Enterprises charged with
transmitting or storing highly sensitive data can Many organizations want the cost savings and
be more confident that they are in control of efficiencies of the cloud, but don’t want to
implementation and maintenance of the security sacrifice traditional levels of control and security.
architecture. Traditional network security solutions require
expensive and over-featured hardware, archaic
command line interfaces, intensive multi-day
RISKS training courses, certification programs, and 400-
page manuals.
Planning and configuration mistakes. Deploying
a VPN requires a high level of planning and When security is made too complex, the
configuration, along with consistent updating chances of configuration errors and unintended
of router firmware and enforcement of security consequences increase. For distributed
policies. Networks must be properly configured enterprises with little to no onsite IT support,
and regularly maintained. Improperly configured cloud-based security provides visibility,
segments may create security holes within the configuration, and control of thousands of
core network, which hackers may exploit to devices, anywhere in the world. Distributed
access sensitive data. enterprises should ideally deploy security
solutions that combine the immediacy of on-
Physical security is also important to prevent premise management with the simplicity and
theft of the edge router/gateway, which can be centralized control of the cloud.
used to access corporate networks and sensitive
data.
©2015 Cradlepoint. All Rights Reserved. | +1.855.813.3385 | cradlepoint.com 5
White Paper / Security
BENEFITS with on-premise solutions can be addressed
by logging on directly to the appliance to
Scalability and concentration. Increasing the scale engage vendor support faster. With cloud-based
of the cloud-based security architecture can be solutions, IT has to open a ticket and work
done in an easier, more cost-effective manner, externally to resolve issues, which may increase
requiring less planning than traditional hardware- the time to resolution.
based architectures. Security related processes,
threat responses, updates, and security patches Customization. With the appropriate level
can be applied more quickly through cloud-based of budget, resourcing, and time, on-premise
security applications architecture. solutions can be customized to meet an
organization’s specific security needs while
Threat management. Web traffic can be quickly providing a robust solution set. With cloud-
and dynamically authenticated, encrypted, and based security offerings, IT can address network
filtered with near-zero latency. External Internet- vulnerabilities but loses a level of customization
based attacks can be rejected while detecting and as a trade-off to speed and scalability.
preventing local malware.
Resource sharing and isolation failure. In a
Threat response. In contrast to many on- cloud-based security model, customers will share
premise solutions, event logs and alerts can provider resources with other customers. Cloud
be dynamically filtered through cloud-based providers generally implement isolation measures
algorithms for more detailed monitoring and to prevent “guest-hopping” or pivot attacks
actionable analytics. (wherein a hacker exploits vulnerabilities of one
operating system to obtain access to another
More flexible traffic routing. Simplified cloud- hosted on the same physical hardware), but there
based tunnels and security protocols to protect is always a risk that these measures will fail.
data in transit can be configured and deployed Because cloud services are extended to multiple
between remote sites and corporate headquarters clients with different risk levels, multi-tenant
much faster and without the cost of traditional segmentation (separation of tenant resources by
hardware headends. the cloud provider) is critical.
Data isolation. Enterprises can isolate frequently In addition, the provider may be incapable of
targeted applications like email from sensitive completely deleting data from hardware, as
data like cardholder information. clients often share or reuse hardware used by
other clients.
RISKS
Security compromise from within. If user
permissions and roles are not set up carefully,
Loss of governance. In a cloud-based model, data
a user might have the ability to delete or
and information are stored with a third party. It
modify their data within the cloud solution. For
may be difficult to inspect the provider’s data
example, an employee new to the solution with
handling practices. And while rare, there is always
administrative access to the cloud solution could
a possibility that a rogue employee of the cloud
delete important data while they are trying to
provider could compromise data.
learn the new solution or a malicious employee
may compromise data intentionally.
Time to resolution. For companies with
appropriately staffed IT organizations, problems
©2015 Cradlepoint. All Rights Reserved. | +1.855.813.3385 | cradlepoint.com 6
White Paper / Security
Data portability. It may be difficult, if not impossible, to move
data should you ever need to switch cloud providers, unless there
is prior agreement between the provider and the enterprise that EVEN COMPANIES
the information is owned by the enterprise. THAT DON’T
PROCESS CREDIT
KEYS TO SUCCESS CARD PAYMENTS
Maximize and automate cloud services with threat management
SHOULD CONSIDER
services. In addition to implementing isolation techniques IMPLEMENTING
and controls, distributed enterprises can reduce costs and
network complexity by collapsing their infrastructure to some
PCI-DSS 3.0 AS A
extent, while still employing multi-layered security throughout GENERAL SECURITY
their sites. Threat management services offer a combination
BASELINE. MANY
of services like anti-malware defense, anti-spam and mail
protection, content filtering, traditional Layer 3 and 4 firewall PCI SECURITY
rules, VPN and web proxy capabilities. STANDARDS
Many of these systems also include centralized, scalable cloud- ADDRESS GENERAL
based security as a service offering to augment and automate NETWORK RISKS
traffic inspection and provide tighter controls for sites with
limited staff or monitoring tools. OUTSIDE THE SCOPE
OF CARDHOLDER
For many enterprises, compliance is the major driver for changes
in both security and general IT operations. Any technology or DATA SECURITY.
internal design change that can limit or reduce the scope of the
environment subject to compliance can save money and time.
Isolation of systems, applications, and network segments that
handle payment card data, for example, can go a long way toward
limiting the scope of PCI-DSS 3.0 audits.
Secure Internet Connections
Virtual Private Networking Connection
HQ
Store
©2015 Cradlepoint. All Rights Reserved. | +1.855.813.3385 | cradlepoint.com 7
White Paper / Security
STRATEGIES FOR A SAFER NETWORK PHYSICALLY SECURE DEVICES & NETWORKS
ENFORCE DEVICE VISIBILITY—THE KEY TO PCI Security Standards require that servers,
networking equipment, and other payment
ANY SECURITY STRATEGY
card system components be kept in a locked,
access-controlled room—preferably with video
With many new mobile devices joining the
surveillance.4 This mitigates the risk of an
enterprise WLAN network, visibility into mobile
unauthorized individual stealing a device with
applications is becoming critical. Network
access to the network. Physical security of
administrators need the ability to identify,
devices also prevents attackers from attaching
track, and categorize all devices accessing the
extraneous devices to the router that could
network. Device visibility provides IT with real-
monitor and steal data from the network.
time inventory and security intelligence for active
remediation while allowing users to seamlessly
connect to the network without disruptions or
changes in end-user experience. CONDUCT REGULAR SECURITY ASSESSMENTS
Best practices for enforcing device visibility: During a security assessment, a professional
assessor “attacks” the network to identify and
++ Use several criteria to identify devices in recommend controls around any weaknesses in
addition to MAC and IP addresses (which security architectures, including physical security,
can be spoofed) like device IDs and system device key strength, network configuration, and
identifiers that use specific naming client device vulnerabilities.
conventions
Regular network penetration tests, or security
++ Leverage compliance and auditing tools to assessments, are required for PCI Compliance.
provide additional insight into risks and The goal is to test access from low-security
vulnerabilities environments to high-security environments.
This practice evaluates whether cardholder data
++ Enable alerting and enforcement actions is isolated from other segments on the network
for devices attempting to plug into the and verifies that no connectivity exists between
network in-scope and out-of-scope networks (networks
++ Regularly audit and maintain up-to-date that hold cardholder data and networks that
and accurate network topologies (logical do not). Businesses with high numbers of
and physical) facilities or system components may assess only
a sample of the total number of components,
++ Use a common set of security controls for though the sample should be large enough to
policy management provide reasonable assurance that all business
facilities or components are configured per the
++ Institute governance, risk, and compliance standard process. The security assessor must
security best practices verify that the standardized, centralized controls
++ Collaborate and communicate across teams are implemented and working effectively.5
within the IT organization PCI Security Standards recommend annual
penetration testing, at a minimum.
©2015 Cradlepoint. All Rights Reserved. | +1.855.813.3385 | cradlepoint.com 8
White Paper / Security
TEACH EMPLOYEES TO RECOGNIZE NETWORK ATTACKS
Unfortunately, no firewall or antivirus software can perfectly WEB & EMAIL
protect the network against every type of malware. Therefore, THREAT VECTORS
it is imperative for enterprises to teach and enforce employee
security protocols. In particular, employees should be trained to
ARE THE MOST
recognize and report phishing emails. SIGNIFICANT
Employees should know the common signs of a phishing email:
SOURCE OF
NETWORK ATTACKS.
++ Encouragement to click on links, especially ones that
are unfamiliar or do not match the supposed source’s
WEB-DERIVED
web address ATTACKS ARE 5x
++ Urgent requests to provide information, call a phone MORE LIKELY THAN
number, or download attachments EMAIL-DERIVED
++ Bad spelling or unusual grammar ATTACKS
OVERALL.6
NETWORK CONFIGURATION MUST-DOS
1. LOCK DOWN THE ROUTER ENTRY POINTS
++ Disable Universal Plug & Play. Don’t allow unprivileged
users to manipulate network configuration.
++ Disable WAN Pings. Don’t let hackers probe security
vulnerabilities.
++ Disable Remote Administration. Don’t let intruders access
the router’s user interface.
++ Use MAC Filtering. Create a list of devices that have
exclusive access or no access to the wireless network.
While MAC addresses can be faked, this creates an extra
barrier for the attacker.
++ Use IP Filter Rules. Restrict remote access to computers on
the local network.
++ Do not use public addressable WAN IP addresses at the
edge. Doing so leaves the edge of the network open to
attacks.
©2015 Cradlepoint. All Rights Reserved. | +1.855.813.3385 | cradlepoint.com 9
White Paper / Security
2. CONFIGURE THE NETWORK FIREWALL TWO METHODS FOR
FOR PCI COMPLIANCE INCREASING SECURITY
Five controls for PCI Compliance: 1. CREATE SECURITY ZONES FOR
NETWORK SEGMENTATION
++ Stateful Packet Inspection (SPI). Monitors
outgoing and incoming traffic to make
Network segmentation allows for the partitioning
sure that only valid responses to outgoing
of the network into “security zones,” or segments
requests are allowed to pass through the
separated by firewalls. Properly configured
firewall.
segments separate applications and prevent
++ Port Forwarding Rules. Opens ports on the access to sensitive data. A Point-of-Sale system,
firewall in a controlled manner for specific for example, should operate on a segment
applications. separate from third party applications, employee
email, or public WiFi.
++ Anti-Spoof. Checks packets to protect
against malicious users faking the source This limits the ability of attackers to pivot from
address in packets to hide themselves or one application to another, and allows network
impersonate someone else. administrators to manage the quality of service
(QoS) on specific segments, prioritizing bandwidth
++ De-Militarized Zone. Keeps most computers
usage for mission-critical applications.
running behind a firewall, while one or more
computers also run outside the firewall, or
First Steps for Network Segmentation
in the DMZ, to add an additional layer of
security to the enterprise network and give
Network segmentation is complex and requires
attackers access only to computers on the
meticulous, ongoing monitoring. This architecture,
network within the DMZ.
while highly secure if configured properly,
++ Updated Firmware. In addition to being an presents many opportunities for configuration
important security practice, up-to-date mistakes. Here are three steps to get you started:
router and modem firmware is required for
PCI Compliance. ++ Create Ethernet port groups. Logical
groupings of Ethernet ports allow
computers physically connected to Ethernet
While improved practices for network ports within a group to freely communicate.
implementation, maintenance, and security You may wish to disable one or all router
enforcement are important strategies for reducing SSIDs, or even the entire WiFi radio.
the risk of a data breach, we recommend network
segmentation or, better yet, application-specific ++ Use WPA2/Enterprise, RADIUS/TACACS+,
parallel networks to ensure that the security and PKI infrastructure. This will provide
vulnerabilities of one application cannot be a central repository for users or devices
compromised and pivoted off of to access data allowed to access the network and uses
from other applications, like Point-of-Sale certificates to authenticate server and
systems. device.
©2015 Cradlepoint. All Rights Reserved. | +1.855.813.3385 | cradlepoint.com 10
White Paper / Security
++ Leverage a PKI infrastructure for stronger Each segment should have its own IP address
security. configuration, Routing Mode, Access Control, and
Interfaces (i.e. WiFi SSIDs, Ethernet Groups, and
++ Use 2-Factor Authentication to minimize VLANs). Currently, no tool exists to automatically
theft of user accounts being used by third monitor and search for vulnerabilities within a
parties. segmented network or between segments—such
++ Create and configure VLAN segments. oversight must be conducted manually. For this
A VLAN enables devices to be grouped reason, many enterprises will find that parallel
together. After creating a VLAN, select the networking is a better overall solution for
LAN port(s) or Ethernet groups to which keeping sensitive data secure.
the VLAN ID should correspond.
Fig 1. Creating Secure Zones
Through Network Segmentation
Secure Internet
Connection
SSID #1 SSID #2 SSID #3 SSID #4
“Employee” “POS” “Vendor” “Public”
Employee POS Device Vendor Public
Segment Segment Segment Segment
©2015 Cradlepoint. All Rights Reserved. | +1.855.813.3385 | cradlepoint.com 11
White Paper / Security
2. KEEP IT SIMPLE WITH PARALLEL NETWORKS
In contrast to segmenting a single network, creating multiple parallel networks is a
relatively simple solution. Separate applications are assigned completely separate
networks, or “air-gapped.” This physical separation of data further prohibits attackers
from using a compromised device to pivot to other servers and networks, including
those that hold sensitive data.
For example, the enterprise should consider hosting customer WiFi, employee devices,
and Point-of-Sale systems on their own respective networks. Enterprises with parallel
networks expect third parties such as vendors, partners and kiosks who require
Internet access to “Bring Your Own Network.” By expecting third-parties to provide
their own parallel networks, the company can retain governance over its own network
functions, while reducing the overall scope of work to maintain network security.
Parallel networks significantly reduce the amount of time and expertise needed to
segment networks based on application, and limit the scope of work for maintaining
PCI Compliance on the network used for transmitting cardholder data.
Equip.
Room HQ
Customer Area
Security
System
Employee WiFi
Customer Smart Phone
IT
Back
Office
Point-of-Sale 3rd Party
Kiosk
Employee Network
Fig 2. Parrallel Networks Administered by One Source
©2015 Cradlepoint. All Rights Reserved. | +1.855.813.3385 | cradlepoint.com 12
White Paper / Security
CRADLEPOINT SOLUTIONS the cloud, but is transmitted directly to its
destination on the LAN or across the WAN.
DESIGNED FOR SECURITY AT THE
Designed for security: Management features
NETWORK’S EDGE
enable security compliance and device tracking
Cradlepoint’s router/firewall devices and cloud-
Enterprise Cloud Manager’s user interface and
based management software are designed
analytics help automate security configurations
to mitigate security risks and maintain PCI
and checklists, such as PCI DSS 3.0 Compliance.
Compliance for distributed enterprises using
Geo-fencing and location services give enterprises
all types of network architectures. A growing
real-time physical location of deployed devices
number of enterprises are transitioning to
utilizing GPS, WiFi, and location-based insights
parallel networking, finding that Cradlepoint’s
information. Enterprises can be notified when
4G solutions enable simpler and safer network
devices leave their normal locations, reducing
segmentation. Additionally, parallel networks
the risk that hackers will be able to use stolen
often reduce enterprises’ soft costs, including the
devices to access the network.
need for complex network configurations that
are subject to human error, more complicated
Enterprise Cloud Manager: A securely hosted
PCI Compliance audits, and the general quality of
solution
service (QoS) settings for specific applications on
the network.
Cradlepoint Enterprise Cloud Manager is hosted
at a world-class, third party storage facility
on a secure, enterprise-class server, providing
ENTERPRISE CLOUD MANAGER FOR equipment redundancy, always-on power, multiple
CENTRALIZED COMMAND AND CONTROL Internet channels, and backup and restoration
service. Enterprise Cloud Manager servers are
Massive scalability: Monitor and manage hardened, with unnecessary services disabled,
thousands of remotely deployed devices permissions limited, and logs monitored. The
servers are under patch management control
Enterprise Cloud Manager, Cradlepoint’s network to keep software versions and security patches
management and application platform, allows current. In addition, the servers and application
IT managers to rapidly deploy and dynamically undergo regular vulnerability assessments and
manage networks at geographically distributed remediation.
stores and branch locations. Cradlepoint solutions
are cloud-enabled for rapid deployment, dynamic All customer configurations reside in this secure
management, and enhanced intelligence. physical facility, with access limited to authorized
Enterprise Cloud Manager provides an out- individuals only. Passwords stored within
of-band control plane that separates network configurations are Advanced Encryption Standard
management data from user data. Management (AES) encrypted. The facility is constantly
data (such as configuration, statistics, and monitored and recorded, while access to the
monitoring) is transmitted from Cradlepoint facility requires multifactor authentication.
devices to the Cradlepoint cloud over a secure Access records are available and auditable.
Internet connection. User data (web browsing,
internal applications, etc.) does not go through
©2015 Cradlepoint. All Rights Reserved. | +1.855.813.3385 | cradlepoint.com 13
White Paper / Security
Fig 3. Enterprise Cloud Manager
Fig 4. Enterprise Cloud Manager
©2015 Cradlepoint. All Rights Reserved. | +1.855.813.3385 | cradlepoint.com 14
White Paper / Security
Easily manageable: Integrated, best-in-class
security software
Through a RESTful API, Cradlepoint has integrated
cloud-based security solutions for web filtering
and anti-malware into Enterprise Cloud Manager.
These security solutions allow IT and security
personnel to inspect web traffic with near-zero
latency.
Secure connectivity for always-on performance Fig. 5: Cradlepoint AER Series—Advanced Edge Routing
Cradlepoint’s routing solutions are designed for
the distributed enterprise to intelligently manage
converged wired and wireless connectivity for
a highly reliable “connected experience” at the
edge. Router 4G LTE Private Networking capability
leverages the cellular connection to become
an extension of the private network without
increasing the vulnerability of the network.
Fig. 6: Cradlepoint COR Series—IoT Applications &
Secure at the edge: Extensible hardware and Transportation
software features
Cradlepoint devices are designed for PCI
Compliance protecting assets with stateful
firewall, advanced encryption, network
segmentation, and VLAN support. Cradlepoint
devices also support Carrier Independent Overlay
Private Network solutions and advanced VPN
options.
Fig. 7: Cradlepoint ARC Series—Application Specific & Failover
Improve ease of security configuration with
Ethernet ports and WiFi SSIDs that can be
individually assigned to specific network
segments. Intrusion Detection and Prevention Sources
functionality scans packets for attacks, malware, 1
Source: ZK Research Nov 2011
and Denial of Service attacks that can be blocked Source: Verizon 2014 Data Breach Investigations Report
2
3
Verizon 2014 Data Breach Investigation Report
based on policy. Applications can be identified, 4
PCI Security Standards Data Storage Dos and Don’ts, https://www.
pcisecuritystandards.org/pdfs/pci_fs_data_storage.pdf
along with behaviors indicative of exploitation. 5
PCI Security Standards 3.0, p.15.
6
FireEye Advanced Threat Report 2013
TO LEARN MORE, VISIT CRADLEPOINT.COM
©2015 Cradlepoint. All Rights Reserved. | +1.855.813.3385 | cradlepoint.com 15
You might also like
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeFrom EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeRating: 4 out of 5 stars4/5 (5834)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreFrom EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreRating: 4 out of 5 stars4/5 (1093)
- Never Split the Difference: Negotiating As If Your Life Depended On ItFrom EverandNever Split the Difference: Negotiating As If Your Life Depended On ItRating: 4.5 out of 5 stars4.5/5 (852)
- Grit: The Power of Passion and PerseveranceFrom EverandGrit: The Power of Passion and PerseveranceRating: 4 out of 5 stars4/5 (590)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceFrom EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceRating: 4 out of 5 stars4/5 (903)
- Shoe Dog: A Memoir by the Creator of NikeFrom EverandShoe Dog: A Memoir by the Creator of NikeRating: 4.5 out of 5 stars4.5/5 (541)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersFrom EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersRating: 4.5 out of 5 stars4.5/5 (349)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureFrom EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureRating: 4.5 out of 5 stars4.5/5 (474)
- Her Body and Other Parties: StoriesFrom EverandHer Body and Other Parties: StoriesRating: 4 out of 5 stars4/5 (823)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)From EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Rating: 4.5 out of 5 stars4.5/5 (122)
- The Emperor of All Maladies: A Biography of CancerFrom EverandThe Emperor of All Maladies: A Biography of CancerRating: 4.5 out of 5 stars4.5/5 (271)
- The Little Book of Hygge: Danish Secrets to Happy LivingFrom EverandThe Little Book of Hygge: Danish Secrets to Happy LivingRating: 3.5 out of 5 stars3.5/5 (405)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyFrom EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyRating: 3.5 out of 5 stars3.5/5 (2259)
- The Yellow House: A Memoir (2019 National Book Award Winner)From EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Rating: 4 out of 5 stars4/5 (98)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaFrom EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaRating: 4.5 out of 5 stars4.5/5 (266)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryFrom EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryRating: 3.5 out of 5 stars3.5/5 (231)
- Team of Rivals: The Political Genius of Abraham LincolnFrom EverandTeam of Rivals: The Political Genius of Abraham LincolnRating: 4.5 out of 5 stars4.5/5 (234)
- On Fire: The (Burning) Case for a Green New DealFrom EverandOn Fire: The (Burning) Case for a Green New DealRating: 4 out of 5 stars4/5 (74)
- The Unwinding: An Inner History of the New AmericaFrom EverandThe Unwinding: An Inner History of the New AmericaRating: 4 out of 5 stars4/5 (45)
- Manufacturing Execution System (MES) : Deployment GuideDocument47 pagesManufacturing Execution System (MES) : Deployment GuideNhat Tan MaiNo ratings yet
- Precision Fiber Products IncDocument3 pagesPrecision Fiber Products IncCyrllandNo ratings yet
- cyr-ENG-412E TCP IP Network FundamentalsDocument8 pagescyr-ENG-412E TCP IP Network FundamentalsCyrllandNo ratings yet
- Fundamentals of Wireless LansDocument1 pageFundamentals of Wireless LansCyrllandNo ratings yet
- MikroTik Training Terms & ConditionsDocument2 pagesMikroTik Training Terms & ConditionsCyrllandNo ratings yet
- Training Enquiry Form MTZADocument1 pageTraining Enquiry Form MTZACyrllandNo ratings yet
- AWS Certified Solutions Architect - Associate (SAA-C02) Exam GuideDocument2 pagesAWS Certified Solutions Architect - Associate (SAA-C02) Exam GuideCyrllandNo ratings yet
- CyberAces Module3-Python 5 PracticalUsesDocument15 pagesCyberAces Module3-Python 5 PracticalUsesCyrllandNo ratings yet
- Mobile Device Management: Key Components, V1.0: September 2012Document12 pagesMobile Device Management: Key Components, V1.0: September 2012CyrllandNo ratings yet
- CyberAces Module3-Python 3 ScriptsDocument16 pagesCyberAces Module3-Python 3 ScriptsCyrllandNo ratings yet
- CyberAces Module3-Python 2 FlowDocument17 pagesCyberAces Module3-Python 2 FlowCyrllandNo ratings yet
- 2018Q1 NSE 1 Master Course DescriptionDocument1 page2018Q1 NSE 1 Master Course DescriptionCyrllandNo ratings yet
- BYOD Solution Overview: Revised: August 7, 2013Document6 pagesBYOD Solution Overview: Revised: August 7, 2013CyrllandNo ratings yet
- 7 Steps To Upgrade IOS Image On Cisco Catalyst Switch or RouterDocument4 pages7 Steps To Upgrade IOS Image On Cisco Catalyst Switch or RouterCyrllandNo ratings yet
- CyberAces Module3-Python 1 IntroDocument19 pagesCyberAces Module3-Python 1 IntroCyrllandNo ratings yet
- Topic 3 DSS Methodologies and Technologies-V2Document28 pagesTopic 3 DSS Methodologies and Technologies-V2tofuNo ratings yet
- Lesson 27, 28,29Document2 pagesLesson 27, 28,29Nasheila Binti Abdul GaniNo ratings yet
- Component DiagramsDocument27 pagesComponent DiagramsSakshi RajputNo ratings yet
- 9 - Software TestingDocument61 pages9 - Software TestingAmitabha DeyNo ratings yet
- Imdrf Cons PPMDCDocument45 pagesImdrf Cons PPMDCAndres CañaveralNo ratings yet
- Bandwidth Monitoring Tools With Alert Management: Loo Kar Chung Tp012661Document19 pagesBandwidth Monitoring Tools With Alert Management: Loo Kar Chung Tp012661selvanskyNo ratings yet
- Hillstone POC Setting Guide iNGFW StoneOS 5.5R6 V2.1Document185 pagesHillstone POC Setting Guide iNGFW StoneOS 5.5R6 V2.1Carlos Alexandre Da Silva OvidioNo ratings yet
- Authentication Authorization and Accounting (AAA) Schemes in WiMAXDocument6 pagesAuthentication Authorization and Accounting (AAA) Schemes in WiMAXUsman MasoodNo ratings yet
- EME-Guide To Manage Enterprise MetadataDocument310 pagesEME-Guide To Manage Enterprise MetadataPraveen JoshiNo ratings yet
- Mi Microservices Eap 7 Reference Architecture 201606 enDocument153 pagesMi Microservices Eap 7 Reference Architecture 201606 enCarlosArturoQuirogaNo ratings yet
- How To Compress A Dump File in Data Pump Technology?Document11 pagesHow To Compress A Dump File in Data Pump Technology?srivasthavNo ratings yet
- CCNPv7 ROUTE Lab7-1 BGP Config InstructorDocument15 pagesCCNPv7 ROUTE Lab7-1 BGP Config InstructorAnonymous GK9mHwnrNo ratings yet
- MUCARBT200 ManualDocument31 pagesMUCARBT200 ManualNawi LaraNo ratings yet
- An Introduction To The BIOS: in This GuideDocument3 pagesAn Introduction To The BIOS: in This GuideAnilNo ratings yet
- Activity 2: Introduction To Assembly Language: Alcantara, John Joaquin S. (Student's Name) - September 2020Document8 pagesActivity 2: Introduction To Assembly Language: Alcantara, John Joaquin S. (Student's Name) - September 2020Kathleen Jhoren ReglosNo ratings yet
- Cyberops UndipDocument5 pagesCyberops UndipAdiNo ratings yet
- Huawei OceanStor 5000 V5 Series Hybrid Flash Storage Systems Technical White PaperDocument82 pagesHuawei OceanStor 5000 V5 Series Hybrid Flash Storage Systems Technical White PaperIvan CruzNo ratings yet
- Module 3 - Java ProgrammingDocument106 pagesModule 3 - Java ProgrammingPratham GuptaNo ratings yet
- Testing Energy Meter Compliance For Protocol & Performance As Per StandardsDocument23 pagesTesting Energy Meter Compliance For Protocol & Performance As Per StandardsceydaNo ratings yet
- Fast WCDMA Reselection at 2G CS Call Release Feature Delivery GuideDocument17 pagesFast WCDMA Reselection at 2G CS Call Release Feature Delivery GuideabojablNo ratings yet
- How Do You Control Pop-Up Windows in WinCC Unified PC RT and Comfort Panels Via S... - ID - 109810540 - Industry Support SiemensDocument12 pagesHow Do You Control Pop-Up Windows in WinCC Unified PC RT and Comfort Panels Via S... - ID - 109810540 - Industry Support SiemensAgnaldo JuniorNo ratings yet
- Summative Computer Maintenance css10Document3 pagesSummative Computer Maintenance css10Rolinn SicoNo ratings yet
- Status: Lan4 Lan3 Lan2 Lan1Document1 pageStatus: Lan4 Lan3 Lan2 Lan1Hasan Abdullah SahidNo ratings yet
- Dos Function Calls (Int 21H) : A. Terminate Program and Return To DosDocument5 pagesDos Function Calls (Int 21H) : A. Terminate Program and Return To DosgowthamvaniNo ratings yet
- SVVT Lab 2819044Document49 pagesSVVT Lab 2819044Prince KumarNo ratings yet
- ANEMAN User ManualDocument29 pagesANEMAN User ManualChaabane FaouziNo ratings yet
- E-Police Police Record Management SystemDocument4 pagesE-Police Police Record Management SystemMohammad Waqas100% (1)
- Sage CRM 6.0 Screen Customization GuideDocument133 pagesSage CRM 6.0 Screen Customization GuideMohamed MohamedNo ratings yet
- Firewall CrackingDocument14 pagesFirewall CrackingEldhose JacobNo ratings yet