Professional Documents
Culture Documents
Testing Diagram
Testing Diagram
Uploaded by
Ming ZhaoCopyright:
Available Formats
You might also like
- BAMF LinkedIn Influencer ProgramDocument45 pagesBAMF LinkedIn Influencer ProgramAlina Zhoga100% (1)
- ATPG Methodology FlowDocument37 pagesATPG Methodology FlowAdhi SuruliNo ratings yet
- TCP Variants Performance Analysis in Mobile Ad Hoc NetworksDocument4 pagesTCP Variants Performance Analysis in Mobile Ad Hoc NetworksIISRTNo ratings yet
- Adventures in Bug HuntingDocument192 pagesAdventures in Bug Huntingice799No ratings yet
- Language Register Formal, Informal, and NeutralDocument29 pagesLanguage Register Formal, Informal, and NeutralDavid SamuelNo ratings yet
- Review of Related Literature Term PaperDocument6 pagesReview of Related Literature Term PaperAllyana Julienne100% (6)
- IPsec Tools ChecklistDocument3 pagesIPsec Tools ChecklistMerab TavartkiladzeNo ratings yet
- TCPIP Diagnosis Session Anaheim FEB 2011Document56 pagesTCPIP Diagnosis Session Anaheim FEB 2011Divyangkumar DarjiNo ratings yet
- Troubleshooting FWSM PerformanceDocument2 pagesTroubleshooting FWSM PerformanceDinkar SharmaNo ratings yet
- Sec 2Document55 pagesSec 2alexandraaaaaa111No ratings yet
- Cisco Security Troubleshooting: Part III - Intrusion Prevention SystemsDocument14 pagesCisco Security Troubleshooting: Part III - Intrusion Prevention SystemshoadiNo ratings yet
- TACSEC-2006 Troubleshooting Cisco Secure Firewall Cluster Failures and Packet Drops - 2023Document53 pagesTACSEC-2006 Troubleshooting Cisco Secure Firewall Cluster Failures and Packet Drops - 2023prakash1649No ratings yet
- How To Track When A Power Supply Dies or Redundant Supply Changes State Using SNMP - Cisco PDFDocument3 pagesHow To Track When A Power Supply Dies or Redundant Supply Changes State Using SNMP - Cisco PDFMauricio AbregúNo ratings yet
- packet_dropsDocument8 pagespacket_dropsfendyNo ratings yet
- Midterm F2018 SolutionDocument7 pagesMidterm F2018 SolutionSkylar WillNo ratings yet
- TRex - 0x14 Paper9 Talk PaperDocument10 pagesTRex - 0x14 Paper9 Talk PaperPraveen RaiNo ratings yet
- Unit 4Document27 pagesUnit 4srsr1987No ratings yet
- 8.6. 2 Lab1Document9 pages8.6. 2 Lab1Mai Huy HoàngNo ratings yet
- Lib P Cap Hakin 9 Luis Martin GarciaDocument9 pagesLib P Cap Hakin 9 Luis Martin Garciaf2zubacNo ratings yet
- ITCE 720A Autonomic Wireless Networking (Fall, 2009)Document24 pagesITCE 720A Autonomic Wireless Networking (Fall, 2009)Souhila SelmaNo ratings yet
- Lab VPNDocument9 pagesLab VPNhung kungNo ratings yet
- Port ScansDocument7 pagesPort ScansLju LjuNo ratings yet
- Computer Networks Andrew S. Tanenbaum David J. Wetherall Fifth EditionDocument7 pagesComputer Networks Andrew S. Tanenbaum David J. Wetherall Fifth Editiongopi9966957145No ratings yet
- Penetration Testing ToolsDocument24 pagesPenetration Testing ToolsMorteza ZNLNo ratings yet
- Packet Filtering FirewallDocument9 pagesPacket Filtering FirewallEnoch L SNo ratings yet
- Laboratory #3 IT Systems Security Lab University of Petroleum and Energy Studies, DehradunDocument5 pagesLaboratory #3 IT Systems Security Lab University of Petroleum and Energy Studies, DehradunMansi BishtNo ratings yet
- Cain Abel: Snort and Nmap - Two Sides of The Same CoinDocument8 pagesCain Abel: Snort and Nmap - Two Sides of The Same CoinDavid51No ratings yet
- Written Assignment Unit 7, Communications and NetworkingDocument4 pagesWritten Assignment Unit 7, Communications and Networkinglaurencenyendwa4No ratings yet
- IPTables AdvancedDocument12 pagesIPTables Advancedarunmanoj1355No ratings yet
- Digital Forensic: Project Phase 3 (4&5)Document4 pagesDigital Forensic: Project Phase 3 (4&5)Atif AliNo ratings yet
- Kernel DebugDocument6 pagesKernel Debugbombast2011No ratings yet
- Assignment 3Document13 pagesAssignment 3ZaskelNo ratings yet
- 8.5. 10 Lab3Document10 pages8.5. 10 Lab3Mai Huy HoàngNo ratings yet
- Packet Flow in RouterOS - RouterOS - MikroTik DocumentationDocument23 pagesPacket Flow in RouterOS - RouterOS - MikroTik DocumentationBayu RomadiNo ratings yet
- FirewallDocument116 pagesFirewallTabarez AhmedNo ratings yet
- Advanced VPC Operation and Troubleshooting - BRKCRS-3146 PDFDocument71 pagesAdvanced VPC Operation and Troubleshooting - BRKCRS-3146 PDFPadam DhamiNo ratings yet
- CS2105 DIY Exercise 2Document2 pagesCS2105 DIY Exercise 2weitsangNo ratings yet
- Linux' Packet MmapDocument87 pagesLinux' Packet MmapsmallakeNo ratings yet
- Embedding Covert Channels Into TCP/IPDocument15 pagesEmbedding Covert Channels Into TCP/IPkhssalahNo ratings yet
- 02 - Architecture Overview V2Document12 pages02 - Architecture Overview V2Mario NấmNo ratings yet
- ITCE 314 Lab Report 1Document7 pagesITCE 314 Lab Report 1Amna AzmatNo ratings yet
- Chaos TablesDocument18 pagesChaos TablesResearch GuyNo ratings yet
- IEEE 802.11-Saturation Throughput AnalysisDocument3 pagesIEEE 802.11-Saturation Throughput AnalysisvaibhavNo ratings yet
- Sa TestDocument12 pagesSa TestAZM pallab chowdhuryNo ratings yet
- PDF 24Document6 pagesPDF 24Raul Cespedes IchazoNo ratings yet
- Show Interface in DepthDocument12 pagesShow Interface in DepthIvan MachuzaNo ratings yet
- Hotcloud19 Paper LeiDocument7 pagesHotcloud19 Paper LeiAveNo ratings yet
- 03 - W02L01 - Circuit & Packet Switching, Multiplexing, Protocols & LayeringDocument22 pages03 - W02L01 - Circuit & Packet Switching, Multiplexing, Protocols & LayeringFartash ShahzaibNo ratings yet
- Diagaram Flow Packet MikrotikDocument6 pagesDiagaram Flow Packet Mikrotikawhy7No ratings yet
- Telecom Signaling Attacks On 3G and LTE Networks: From SS7 To all-IP, All OpenDocument64 pagesTelecom Signaling Attacks On 3G and LTE Networks: From SS7 To all-IP, All Openh2tonyNo ratings yet
- Topic 2 Commui (IcationDocument12 pagesTopic 2 Commui (IcationNayif AlhammashNo ratings yet
- Lab-1 CS F303Document9 pagesLab-1 CS F303MIHIKA PARAG DESHPANDENo ratings yet
- Wire SharkDocument32 pagesWire Sharkshankar3No ratings yet
- Final Paper N Simulaton FinalDocument5 pagesFinal Paper N Simulaton Finalsalman_ansari_pk4198No ratings yet
- Cs155 Pp3 SectionDocument30 pagesCs155 Pp3 SectionXozanNo ratings yet
- STE Practical 11-15Document24 pagesSTE Practical 11-15CO-352 Vedant DeshpandeNo ratings yet
- Manipulating Packets With MikroTikDocument28 pagesManipulating Packets With MikroTikBenya NamsaNo ratings yet
- Traffic PDFDocument162 pagesTraffic PDFSenan Alkaaby100% (4)
- 01b - Wireshark Training.1.03 - ALUDocument23 pages01b - Wireshark Training.1.03 - ALUleandre vanieNo ratings yet
- 1-16 Cisco Router ThroughputDocument3 pages1-16 Cisco Router ThroughputCassandra ShafferNo ratings yet
- CS155: Computer and Network Security: Programming Project 3 - Spring 2004Document30 pagesCS155: Computer and Network Security: Programming Project 3 - Spring 2004ashishbhangeNo ratings yet
- Basic Cisco Troubleshooting PDFDocument1 pageBasic Cisco Troubleshooting PDFshareefgs55600% (1)
- 1 - Hind SwarajDocument4 pages1 - Hind SwarajMing ZhaoNo ratings yet
- Manual For Ming'S Program Files 9/1/14Document6 pagesManual For Ming'S Program Files 9/1/14Ming ZhaoNo ratings yet
- Ntroduction TO Sychology: Spring 2014Document51 pagesNtroduction TO Sychology: Spring 2014Ming ZhaoNo ratings yet
- What Do You Wish To Do in The Rest of Your Time at Columbia? What Is One Thing You Would Redo About The Last Four Years?Document12 pagesWhat Do You Wish To Do in The Rest of Your Time at Columbia? What Is One Thing You Would Redo About The Last Four Years?Ming ZhaoNo ratings yet
- Synthesis of Steroid HormonesDocument54 pagesSynthesis of Steroid HormonesMing ZhaoNo ratings yet
- Summer Opportunities-PreproffDocument59 pagesSummer Opportunities-PreproffMing ZhaoNo ratings yet
- DiphthongsDocument21 pagesDiphthongsAlina PetrascoNo ratings yet
- Name SAP Technical Consultant Resume - 4+Document5 pagesName SAP Technical Consultant Resume - 4+Vinoth KumarNo ratings yet
- Shotaro Matsumoto Resume 2Document2 pagesShotaro Matsumoto Resume 2api-325013371No ratings yet
- History of CostumeDocument108 pagesHistory of CostumeMichi87% (15)
- Koç İlaç KatalogDocument40 pagesKoç İlaç KatalogMedina JusmaniNo ratings yet
- Harmonic SequenceDocument5 pagesHarmonic SequenceKian CepilloNo ratings yet
- 2018:19 Crime StatsDocument220 pages2018:19 Crime StatsBusinessTech64% (14)
- Right To Be InformedDocument19 pagesRight To Be InformedJonald B. DoradoNo ratings yet
- Chapter 5 Marketing StrategiesDocument13 pagesChapter 5 Marketing StrategiesMasood khanNo ratings yet
- ASTM D7710-14 Standard Test Method For Determination of Volume and Density of Rigid and Irregularity Shaped Molded Cellular MaterialsDocument3 pagesASTM D7710-14 Standard Test Method For Determination of Volume and Density of Rigid and Irregularity Shaped Molded Cellular Materialsynmer_cervantes0% (1)
- Property - Bar Ops 2009.combined - Atty - BatacanDocument36 pagesProperty - Bar Ops 2009.combined - Atty - BatacandavaounionNo ratings yet
- Introduction To Malaysian EnglishDocument4 pagesIntroduction To Malaysian EnglishNEYLA SHAKIRA FADILLAHNo ratings yet
- Math 4 Performance Task No. 3Document1 pageMath 4 Performance Task No. 3Kobe BinamiraNo ratings yet
- Mercado Vs ManzanoDocument7 pagesMercado Vs ManzanoApril Grace TenorioNo ratings yet
- CQI-9 Heat Treat System Assessment - Forms and Process Tables V3 2016Document83 pagesCQI-9 Heat Treat System Assessment - Forms and Process Tables V3 2016aperezpi26606No ratings yet
- Erdogan V Economics: A Scheme To Save The Lira Piles On The Risks InsteadDocument1 pageErdogan V Economics: A Scheme To Save The Lira Piles On The Risks InsteadRuslan AbduraxmanovNo ratings yet
- Hornbill & SnapshotDocument13 pagesHornbill & SnapshotMahin AhmedNo ratings yet
- Wiley India Textbooks Price List June 2015 PDFDocument152 pagesWiley India Textbooks Price List June 2015 PDFshailesh goralNo ratings yet
- Gaining Power and InfluenceDocument17 pagesGaining Power and InfluenceMd SelimNo ratings yet
- English Language and Linguistics Notes: RatingDocument1 pageEnglish Language and Linguistics Notes: RatingPrince Digital ComputersNo ratings yet
- Bengt B Broms Lateral Resistance of PileDocument43 pagesBengt B Broms Lateral Resistance of PileJerin LeenusNo ratings yet
- Meta Ads Video FrameworkDocument4 pagesMeta Ads Video FrameworkFakhzan BadiranNo ratings yet
- Sebastian vs. BajarDocument12 pagesSebastian vs. BajarAnisah AquilaNo ratings yet
- Biochem - Hormone and Signal TransductionDocument36 pagesBiochem - Hormone and Signal TransductionPrincess Jeyan PagatpatanNo ratings yet
- CMOSIC For Current-Mode PWM Power Supply: Hiroshi MaruyamaDocument6 pagesCMOSIC For Current-Mode PWM Power Supply: Hiroshi MaruyamaMalfo10No ratings yet
- The Girl With Green Eyes-John EscottDocument9 pagesThe Girl With Green Eyes-John EscottTanuiNo ratings yet
Testing Diagram
Testing Diagram
Uploaded by
Ming ZhaoOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Testing Diagram
Testing Diagram
Uploaded by
Ming ZhaoCopyright:
Available Formats
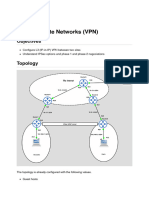
ZEEK TESTING
"zeek-level" "dissector-level"
live traffic tcpreplay** static pcaps
throughput TCP layer
fuzzing*
"normal" "abnormal" "normal" "abnormal" "normal" "abnormal"
*Invalidating packet integrity at the TCP-layer (e.g. bad checksum, wrong port, etc.) sometimes triggers an “exit condition”
where Zeek gives up parsing the packet before it even passes the connection object or control flow to the dissector (i.e. the
DNP3 dissector may never get to see the packet because Zeek dropped the effort too early). We need to figure out what
circumstances trigger such exit conditions.
** The purpose here is to use the same underlying traffic/pcaps for static and live capture and check for any differences in
output logs.
For each set of “normal” tests, only generate good/legitimate traffic: (1) write a script that creates packets which iterate
through all request function codes, response function codes, error codes, data object types (for DNP3), etc. and (2) let the
dissector run over a sample of legitimate traffic in the wild (e.g. let it sniff for XX minutes in our lab or upload/replay a sample
pcap that we know contains only legitimate traffic)
For each set of “abnormal” tests, generate malformed and potentially malicious traffic: Attacks in real life occur over the course
of (a) a single packet, (b) several packets on stateful protocols, or (c) months of “living off the land” where no individual
communication fragment is abnormal in itself versus the usual activity on that network. We expect our dissectors to
detect/raise exceptions on 100% of (a), most of (b) and none of (c). To test (a) we generate fuzzed packets in a systematic way
(i.e. control for what fields/parameters are being changed in each packet produced and keep all other parameters unchanged
so that we know which fields throw off the dissector). Note, we fuzz only at the protocol layer (ADU/PDU) to isolate dissector
behavior from possible Zeek “exit condition” behavior. To test (b) for stateful protocols such as DNP3 we need to craft a set of
packets where the anomaly occurs over the sequence of 2-5 packets (e.g. a response doesn’t match a request for MITM).
Perhaps the 3rd party samples of attack scenario pcaps are appropriate to test (b), but we need to figure out ahead of time what
are the specific weird artifacts/patterns within each attack sample.
For all “abnormal” traffic tests, we should predict ahead of time what types of weird.log warnings we expect from each
condition/iteration, and then verify whether our dissector actually returned those results.
You might also like
- BAMF LinkedIn Influencer ProgramDocument45 pagesBAMF LinkedIn Influencer ProgramAlina Zhoga100% (1)
- ATPG Methodology FlowDocument37 pagesATPG Methodology FlowAdhi SuruliNo ratings yet
- TCP Variants Performance Analysis in Mobile Ad Hoc NetworksDocument4 pagesTCP Variants Performance Analysis in Mobile Ad Hoc NetworksIISRTNo ratings yet
- Adventures in Bug HuntingDocument192 pagesAdventures in Bug Huntingice799No ratings yet
- Language Register Formal, Informal, and NeutralDocument29 pagesLanguage Register Formal, Informal, and NeutralDavid SamuelNo ratings yet
- Review of Related Literature Term PaperDocument6 pagesReview of Related Literature Term PaperAllyana Julienne100% (6)
- IPsec Tools ChecklistDocument3 pagesIPsec Tools ChecklistMerab TavartkiladzeNo ratings yet
- TCPIP Diagnosis Session Anaheim FEB 2011Document56 pagesTCPIP Diagnosis Session Anaheim FEB 2011Divyangkumar DarjiNo ratings yet
- Troubleshooting FWSM PerformanceDocument2 pagesTroubleshooting FWSM PerformanceDinkar SharmaNo ratings yet
- Sec 2Document55 pagesSec 2alexandraaaaaa111No ratings yet
- Cisco Security Troubleshooting: Part III - Intrusion Prevention SystemsDocument14 pagesCisco Security Troubleshooting: Part III - Intrusion Prevention SystemshoadiNo ratings yet
- TACSEC-2006 Troubleshooting Cisco Secure Firewall Cluster Failures and Packet Drops - 2023Document53 pagesTACSEC-2006 Troubleshooting Cisco Secure Firewall Cluster Failures and Packet Drops - 2023prakash1649No ratings yet
- How To Track When A Power Supply Dies or Redundant Supply Changes State Using SNMP - Cisco PDFDocument3 pagesHow To Track When A Power Supply Dies or Redundant Supply Changes State Using SNMP - Cisco PDFMauricio AbregúNo ratings yet
- packet_dropsDocument8 pagespacket_dropsfendyNo ratings yet
- Midterm F2018 SolutionDocument7 pagesMidterm F2018 SolutionSkylar WillNo ratings yet
- TRex - 0x14 Paper9 Talk PaperDocument10 pagesTRex - 0x14 Paper9 Talk PaperPraveen RaiNo ratings yet
- Unit 4Document27 pagesUnit 4srsr1987No ratings yet
- 8.6. 2 Lab1Document9 pages8.6. 2 Lab1Mai Huy HoàngNo ratings yet
- Lib P Cap Hakin 9 Luis Martin GarciaDocument9 pagesLib P Cap Hakin 9 Luis Martin Garciaf2zubacNo ratings yet
- ITCE 720A Autonomic Wireless Networking (Fall, 2009)Document24 pagesITCE 720A Autonomic Wireless Networking (Fall, 2009)Souhila SelmaNo ratings yet
- Lab VPNDocument9 pagesLab VPNhung kungNo ratings yet
- Port ScansDocument7 pagesPort ScansLju LjuNo ratings yet
- Computer Networks Andrew S. Tanenbaum David J. Wetherall Fifth EditionDocument7 pagesComputer Networks Andrew S. Tanenbaum David J. Wetherall Fifth Editiongopi9966957145No ratings yet
- Penetration Testing ToolsDocument24 pagesPenetration Testing ToolsMorteza ZNLNo ratings yet
- Packet Filtering FirewallDocument9 pagesPacket Filtering FirewallEnoch L SNo ratings yet
- Laboratory #3 IT Systems Security Lab University of Petroleum and Energy Studies, DehradunDocument5 pagesLaboratory #3 IT Systems Security Lab University of Petroleum and Energy Studies, DehradunMansi BishtNo ratings yet
- Cain Abel: Snort and Nmap - Two Sides of The Same CoinDocument8 pagesCain Abel: Snort and Nmap - Two Sides of The Same CoinDavid51No ratings yet
- Written Assignment Unit 7, Communications and NetworkingDocument4 pagesWritten Assignment Unit 7, Communications and Networkinglaurencenyendwa4No ratings yet
- IPTables AdvancedDocument12 pagesIPTables Advancedarunmanoj1355No ratings yet
- Digital Forensic: Project Phase 3 (4&5)Document4 pagesDigital Forensic: Project Phase 3 (4&5)Atif AliNo ratings yet
- Kernel DebugDocument6 pagesKernel Debugbombast2011No ratings yet
- Assignment 3Document13 pagesAssignment 3ZaskelNo ratings yet
- 8.5. 10 Lab3Document10 pages8.5. 10 Lab3Mai Huy HoàngNo ratings yet
- Packet Flow in RouterOS - RouterOS - MikroTik DocumentationDocument23 pagesPacket Flow in RouterOS - RouterOS - MikroTik DocumentationBayu RomadiNo ratings yet
- FirewallDocument116 pagesFirewallTabarez AhmedNo ratings yet
- Advanced VPC Operation and Troubleshooting - BRKCRS-3146 PDFDocument71 pagesAdvanced VPC Operation and Troubleshooting - BRKCRS-3146 PDFPadam DhamiNo ratings yet
- CS2105 DIY Exercise 2Document2 pagesCS2105 DIY Exercise 2weitsangNo ratings yet
- Linux' Packet MmapDocument87 pagesLinux' Packet MmapsmallakeNo ratings yet
- Embedding Covert Channels Into TCP/IPDocument15 pagesEmbedding Covert Channels Into TCP/IPkhssalahNo ratings yet
- 02 - Architecture Overview V2Document12 pages02 - Architecture Overview V2Mario NấmNo ratings yet
- ITCE 314 Lab Report 1Document7 pagesITCE 314 Lab Report 1Amna AzmatNo ratings yet
- Chaos TablesDocument18 pagesChaos TablesResearch GuyNo ratings yet
- IEEE 802.11-Saturation Throughput AnalysisDocument3 pagesIEEE 802.11-Saturation Throughput AnalysisvaibhavNo ratings yet
- Sa TestDocument12 pagesSa TestAZM pallab chowdhuryNo ratings yet
- PDF 24Document6 pagesPDF 24Raul Cespedes IchazoNo ratings yet
- Show Interface in DepthDocument12 pagesShow Interface in DepthIvan MachuzaNo ratings yet
- Hotcloud19 Paper LeiDocument7 pagesHotcloud19 Paper LeiAveNo ratings yet
- 03 - W02L01 - Circuit & Packet Switching, Multiplexing, Protocols & LayeringDocument22 pages03 - W02L01 - Circuit & Packet Switching, Multiplexing, Protocols & LayeringFartash ShahzaibNo ratings yet
- Diagaram Flow Packet MikrotikDocument6 pagesDiagaram Flow Packet Mikrotikawhy7No ratings yet
- Telecom Signaling Attacks On 3G and LTE Networks: From SS7 To all-IP, All OpenDocument64 pagesTelecom Signaling Attacks On 3G and LTE Networks: From SS7 To all-IP, All Openh2tonyNo ratings yet
- Topic 2 Commui (IcationDocument12 pagesTopic 2 Commui (IcationNayif AlhammashNo ratings yet
- Lab-1 CS F303Document9 pagesLab-1 CS F303MIHIKA PARAG DESHPANDENo ratings yet
- Wire SharkDocument32 pagesWire Sharkshankar3No ratings yet
- Final Paper N Simulaton FinalDocument5 pagesFinal Paper N Simulaton Finalsalman_ansari_pk4198No ratings yet
- Cs155 Pp3 SectionDocument30 pagesCs155 Pp3 SectionXozanNo ratings yet
- STE Practical 11-15Document24 pagesSTE Practical 11-15CO-352 Vedant DeshpandeNo ratings yet
- Manipulating Packets With MikroTikDocument28 pagesManipulating Packets With MikroTikBenya NamsaNo ratings yet
- Traffic PDFDocument162 pagesTraffic PDFSenan Alkaaby100% (4)
- 01b - Wireshark Training.1.03 - ALUDocument23 pages01b - Wireshark Training.1.03 - ALUleandre vanieNo ratings yet
- 1-16 Cisco Router ThroughputDocument3 pages1-16 Cisco Router ThroughputCassandra ShafferNo ratings yet
- CS155: Computer and Network Security: Programming Project 3 - Spring 2004Document30 pagesCS155: Computer and Network Security: Programming Project 3 - Spring 2004ashishbhangeNo ratings yet
- Basic Cisco Troubleshooting PDFDocument1 pageBasic Cisco Troubleshooting PDFshareefgs55600% (1)
- 1 - Hind SwarajDocument4 pages1 - Hind SwarajMing ZhaoNo ratings yet
- Manual For Ming'S Program Files 9/1/14Document6 pagesManual For Ming'S Program Files 9/1/14Ming ZhaoNo ratings yet
- Ntroduction TO Sychology: Spring 2014Document51 pagesNtroduction TO Sychology: Spring 2014Ming ZhaoNo ratings yet
- What Do You Wish To Do in The Rest of Your Time at Columbia? What Is One Thing You Would Redo About The Last Four Years?Document12 pagesWhat Do You Wish To Do in The Rest of Your Time at Columbia? What Is One Thing You Would Redo About The Last Four Years?Ming ZhaoNo ratings yet
- Synthesis of Steroid HormonesDocument54 pagesSynthesis of Steroid HormonesMing ZhaoNo ratings yet
- Summer Opportunities-PreproffDocument59 pagesSummer Opportunities-PreproffMing ZhaoNo ratings yet
- DiphthongsDocument21 pagesDiphthongsAlina PetrascoNo ratings yet
- Name SAP Technical Consultant Resume - 4+Document5 pagesName SAP Technical Consultant Resume - 4+Vinoth KumarNo ratings yet
- Shotaro Matsumoto Resume 2Document2 pagesShotaro Matsumoto Resume 2api-325013371No ratings yet
- History of CostumeDocument108 pagesHistory of CostumeMichi87% (15)
- Koç İlaç KatalogDocument40 pagesKoç İlaç KatalogMedina JusmaniNo ratings yet
- Harmonic SequenceDocument5 pagesHarmonic SequenceKian CepilloNo ratings yet
- 2018:19 Crime StatsDocument220 pages2018:19 Crime StatsBusinessTech64% (14)
- Right To Be InformedDocument19 pagesRight To Be InformedJonald B. DoradoNo ratings yet
- Chapter 5 Marketing StrategiesDocument13 pagesChapter 5 Marketing StrategiesMasood khanNo ratings yet
- ASTM D7710-14 Standard Test Method For Determination of Volume and Density of Rigid and Irregularity Shaped Molded Cellular MaterialsDocument3 pagesASTM D7710-14 Standard Test Method For Determination of Volume and Density of Rigid and Irregularity Shaped Molded Cellular Materialsynmer_cervantes0% (1)
- Property - Bar Ops 2009.combined - Atty - BatacanDocument36 pagesProperty - Bar Ops 2009.combined - Atty - BatacandavaounionNo ratings yet
- Introduction To Malaysian EnglishDocument4 pagesIntroduction To Malaysian EnglishNEYLA SHAKIRA FADILLAHNo ratings yet
- Math 4 Performance Task No. 3Document1 pageMath 4 Performance Task No. 3Kobe BinamiraNo ratings yet
- Mercado Vs ManzanoDocument7 pagesMercado Vs ManzanoApril Grace TenorioNo ratings yet
- CQI-9 Heat Treat System Assessment - Forms and Process Tables V3 2016Document83 pagesCQI-9 Heat Treat System Assessment - Forms and Process Tables V3 2016aperezpi26606No ratings yet
- Erdogan V Economics: A Scheme To Save The Lira Piles On The Risks InsteadDocument1 pageErdogan V Economics: A Scheme To Save The Lira Piles On The Risks InsteadRuslan AbduraxmanovNo ratings yet
- Hornbill & SnapshotDocument13 pagesHornbill & SnapshotMahin AhmedNo ratings yet
- Wiley India Textbooks Price List June 2015 PDFDocument152 pagesWiley India Textbooks Price List June 2015 PDFshailesh goralNo ratings yet
- Gaining Power and InfluenceDocument17 pagesGaining Power and InfluenceMd SelimNo ratings yet
- English Language and Linguistics Notes: RatingDocument1 pageEnglish Language and Linguistics Notes: RatingPrince Digital ComputersNo ratings yet
- Bengt B Broms Lateral Resistance of PileDocument43 pagesBengt B Broms Lateral Resistance of PileJerin LeenusNo ratings yet
- Meta Ads Video FrameworkDocument4 pagesMeta Ads Video FrameworkFakhzan BadiranNo ratings yet
- Sebastian vs. BajarDocument12 pagesSebastian vs. BajarAnisah AquilaNo ratings yet
- Biochem - Hormone and Signal TransductionDocument36 pagesBiochem - Hormone and Signal TransductionPrincess Jeyan PagatpatanNo ratings yet
- CMOSIC For Current-Mode PWM Power Supply: Hiroshi MaruyamaDocument6 pagesCMOSIC For Current-Mode PWM Power Supply: Hiroshi MaruyamaMalfo10No ratings yet
- The Girl With Green Eyes-John EscottDocument9 pagesThe Girl With Green Eyes-John EscottTanuiNo ratings yet