Professional Documents
Culture Documents
Unit-Iv Two Marks Questions: Software Engineering Dept of IT, SV Colleges
Unit-Iv Two Marks Questions: Software Engineering Dept of IT, SV Colleges
Uploaded by
Jyo ReddyOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Unit-Iv Two Marks Questions: Software Engineering Dept of IT, SV Colleges
Unit-Iv Two Marks Questions: Software Engineering Dept of IT, SV Colleges
Uploaded by
Jyo ReddyCopyright:
Available Formats
UNIT-IV TWO MARKS QUESTIONS
1. What Are The Golden Rules?
Ans: 1.Place the user in control.
2. Reduce the user’s memory load.
3. Make the interface consistent.
These golden rules actually form the basis for a set of user interface design principles that guide
this important aspect of software design.
2. What is coding?
Ans: Coding is the phase of a software development project where developer's actually input the
source code into a computer that will be compiled into the final software program.
3. What is software testing?
Ans: Software testing is the process of evaluation a software item to detect differences between
given input and expected output. Also to assess the feature of A software item. Testing assesses
the quality of the product. Software testing is a process that should be done during the
development process.
4. What is code review?
Ans: Code review is systematic examination (often as peer review) of computer source code. It is
intended to find and fix mistakes overlooked in the initial development phase, improving both
the overall quality of software and the developers' skills.
5. What is the software documentation?
Ans: Software documentation is written text that accompanies computer software. It either
explains how it operates or how to use it, or may mean different things to people in different
roles. Documentation is an important part of software engineering.
6. What is the user documentation?
Ans: User documentation refers to the documentation for a product or service provided to the
end users. The user documentation is designed to assist end users to use the product or service.
This is often referred to as user assistance.
7. What is SDD document?
Ans: A software design description (software design document or SDD) is a written description
of a software product, that a software designer writes in order to give a software development
team overall guidance to the architecture of the software project.
Software Engineering Dept of IT, SV Colleges
8. What is meant by unit testing?
Ans: Unit testing is a software development process in which the smallest testable parts of an
application, called units, are individually and independently scrutinized for proper
operation. Unit testing is often automated but it can also be done manually.
9. What is a black box testing?
Ans: Black-box testing is a method of software testing that examines the functionality of an
application without peering into its internal structures or workings. This method oftest can be
applied to virtually every level of software testing: unit, integration, system and acceptance.
10. What is glass box testing in software testing?
Ans: White-box testing (also known as clear box testing, glass box testing, transparent box
testing, and structural testing) is a method of testing software that tests internal structures or
workings of an application, as opposed to its functionality (i.e. black-box testing).
11. What is the meaning of white box?
Ans: In computer hardware, a white box is a personal computer or server without a well-known
brand name. For instance, the term applies to systems assembled by small system integrators and
to home-built computer systems assembled by end users from parts purchased separately at
retail.
12. What is meant by structural testing?
Ans: Structural testing, also known as glass box testing or white box testing is an approach
where the tests are derived from the knowledge of the software's structure or internal
implementation. The other names of structural testing include clear box testing, open box testing,
logic driven testing or path driven testing.
13. What is Integration testing?
Ans: Integration testing (sometimes called integration and testing, abbreviated I&T) is the phase
in software testing in which individual software modules are combined and tested as a group. It
occurs after unit testing and before validation testing.
14. What is bottom up testing?
Ans: Bottom Up Testing is an approach to integrated testing where the lowest level components
are tested first, then used to facilitate the testing of higher level components. The process is
repeated until the component at the top of the hierarchy is tested.
15. What is system testing?
Ans: System testing of software or hardware is testing conducted on a complete,
integrated system to evaluate the system's compliance with its specified requirements. System
testing falls within the scope of black-box testing, and as such, should require no knowledge of
the inner design of the code or logic.
Software Engineering Dept of IT, SV Colleges
UNIT-V TWO MARKS QUESTIONS
1. List the Responsibilities of a Software Project Manager.
Ans: The person responsible for developing, in conjunction with the Project Sponsor, a definition
of the project. The Project Manager then ensures that the project is delivered on time, to budget
and to the required quality standard (within agreed specifications). He/she ensures the project is
effectively resourced and manages relationships with a wide range of groups (including all
project contributors). The Project Manager is also responsible for managing the work of
consultants, allocating and utilising resources in an efficient manner and maintaining a co-
operative, motivated and successful team.
Managing People
Act as project leader
Liaison with stakeholders
Managing human resources
Setting up reporting hierarchy etc.
Managing Project
Defining and setting up project scope
Managing project management activities
Monitoring progress and performance
Risk analysis at every phase
Take necessary step to avoid or come out of problems
Act as project spokesperson
2. What is project planning?
Ans: Project planning is part of project management, which relates to the use of schedules such
as Gantt charts to plan and subsequently report progress within theproject environment. Initially,
the project scope is defined and the appropriate methods for completing the project are
determined.
3. Define Software Project
Ans: A Software Project is the complete procedure of software development from requirement
gathering to testing and maintenance, carried out according to the execution methodologies, in a
specified period of time to achieve intended software product.
4. What is Project Estimation?
Ans: For an effective management accurate estimation of various measures is a must. With
correct estimation managers can manage and control the project more efficiently and effectively.
Software Engineering Dept of IT, SV Colleges
Project estimation may involve the following:
Software size estimation
Software size may be estimated either in terms of KLOC (Kilo Line of Code) or by calculating
number of function points in the software. Lines of code depend upon coding practices and
Function points vary according to the user or software requirement.
Effort estimation
The managers estimate efforts in terms of personnel requirement and man-hour required to
produce the software. For effort estimation software size should be known. This can either be
derived by managers’ experience, organization’s historical data or software size can be converted
into efforts by using some standard formulae.
Time estimation
Once size and efforts are estimated, the time required to produce the software can be estimated.
Efforts required are segregated into sub categories as per the requirement specifications and
interdependency of various components of software. Software tasks are divided into smaller
tasks, activities or events by Work Breakthrough Structure (WBS). The tasks are scheduled on
day-to-day basis or in calendar months.
The sum of time required to complete all tasks in hours or days is the total time invested to
complete the project.
Cost estimation
This might be considered as the most difficult of all because it depends on more elements than
any of the previous ones. For estimating project cost, it is required to consider -
o Size of software
o Software quality
o Hardware
o Additional software or tools, licenses etc.
o Skilled personnel with task-specific skills
o Travel involved
o Communication
o Training and support
5. Empirical Estimation Techniques.
Ans: Empirical Estimation Technique
This technique uses empirically derived formulae to make estimation. These formulae are based
on LOC or FPs.
Putnam Model
This model is made by Lawrence H. Putnam, which is based on Norden’s frequency distribution
(Rayleigh curve). Putnam model maps time and efforts required with software size.
COCOMO
COCOMO stands for COnstructive COst MOdel, developed by Barry W. Boehm. It divides the
software product into three categories of software: organic, semi-detached and embedded.
Software Engineering Dept of IT, SV Colleges
6. Explain project Risk Management.
Ans: Risk management involves all activities pertaining to identification, analyzing and making
provision for predictable and non-predictable risks in the project. Risk may include the
following:
Experienced staff leaving the project and new staff coming in.
Change in organizational management.
Requirement change or misinterpreting requirement.
Under-estimation of required time and resources.
Technological changes, environmental changes, business competition.
7. Explain Norden’s Work.
Ans: Norden studied the staffing patterns of several R & D projects. He found that the staffing
pattern can be approximated by the Rayleigh distribution curve .
Norden represented the Rayleigh curve by the following equation:
E = K/t²d * t * e-t² / 2 t² d
Where E is the effort required at time t. E is an indication of the number of engineers (or the
staffing level) at any particular time during the duration of the project, K is the area under the
curve, and td is the time at which the curve attains its maximum value. It must be remembered
that the results of Norden are applicable to general R & D projects and were not meant to model
the staffing pattern of software development projects.
8. Explain Putnam’s Work.
Ans: Putnam studied the problem of staffing of software projects and found that the software
development has characteristics very similar to other R & D projects studied by Norden and that
the Rayleigh-Norden curve can be used to relate the number of delivered lines of code to the
effort and the time required to develop the project.
By analyzing a large number of army projects, Putnam derived the following expression:
L = Ck K1/3td 4/3
The various terms of this expression are as follows:
• K is the total effort expended (in PM) in the product development and L is the product size in
KLOC.
• td corresponds to the time of system and integration testing. Therefore, td can be approximately
considered as the time required to develop the software.
Software Engineering Dept of IT, SV Colleges
• Ck is the state of technology constant and reflects constraints that impede the progress of the
programmer. Typical values of Ck = 2 for poor development environment (no methodology,
poor documentation, and review, etc.), Ck = 8 for good software development environment
(software engineering principles are adhered to), Ck = 11 for an excellent environment (in
addition to following software engineering principles, automated tools and techniques are used).
The exact value of Ck for a specific project can be computed from the historical data of the
organization developing it.
9. Explain Risk assessment?
Ans: The objective of risk assessment is to rank the risks in terms of their damage causing
potential. For risk assessment, first each risk should be rated in two ways:
• The likelihood of a risk coming true (denoted as r).
• The consequence of the problems associated with that risk (denoted as s).
Based on these two factors, the priority of each risk can be computed:
p=r*s
Where, p is the priority with which the risk must be handled, r is the probability of the risk
becoming true, and s is the severity of damage caused due to the risk becoming true. If all
identified risks are prioritized, then the most likely and damaging risks can be handled first and
more comprehensive risk abatement procedures can be designed for these risks.
10. Explain Risk containment.
Ans: After all the identified risks of a project are assessed, plans must be made to contain the
most damaging and the most likely risks. Different risks require different containment
procedures. In fact, most risks require ingenuity on the part of the project manager in tackling the
risk.
There are three main strategies to plan for risk containment:
Avoid the risk: This may take several forms such as discussing with the customer to change the
requirements to reduce the scope of the work, giving incentives to the engineers to avoid the risk
of manpower turnover, etc.
Transfer the risk: This strategy involves getting the risky component developed by a third
party, buying insurance cover, etc.
Risk reduction: This involves planning ways to contain the damage due to a risk. For example,
if there is risk that some key personnel might leave, new recruitment may be planned.
Software Engineering Dept of IT, SV Colleges
UNIT-III TWO MARKS QUESTIONS
1)Describe Quality Attributes?
FURPS (functionality, usability, reliability, performance and supportability). The FURPS
quality attributes represent a target for all software design
Functionality is assessed by evaluating the feature set and capabilities of the program,
the generality of the functions that are delivered, and the security of the overall system.
Usability is assessed by considering human factors, overall aesthetics, consistency, and
documentation.
Reliability is evaluated by measuring the frequency and severity of failure, the accuracy
of output results, the mean-time-to-failure (MTTF), the ability to recover from failure,
and the predictability of the program.
Performance is measured by considering processing speed, response time, resource
consumption, throughput, and efficiency.
Supportability combines the ability to extend the program (extensibility), adaptability,
serviceability—these three attributes represent a more common term, maintainability—
and in addition, testability, compatibility, configurability the ease with which a system
can be installed, and the ease with which problems can be localized.
2) Explain procedural abstraction ?
A procedural abstraction refers to a sequence of instructions that have a specific and
limited function.
3) Explain procedural abstraction ?
A data abstraction is a named collection of data that describes a data object.
4) Patterns
“A pattern is a named nugget of insight which conveys the essence of a proven solution to a
recurring problem within a certain context amidst competing concerns”
The intent of each design pattern is to provide a description that enables a designer to determine
1) Whether the pattern is applicable to the current work,
2) Whether the pattern can be reused (hence, saving design time), and
3) Whether the pattern can serve as a guide for developing a similar, but functionally or
structurally different pattern.
5) Separation of Concerns
Software Engineering Dept of IT, SV Colleges
Separation of concerns is a design concept that suggests that any complex problem can be
more easily handled if it is subdivided into pieces that can each be solved and/or optimized
independently.
A concern is a feature or behavior that is specified as part of the requirements model for
the software.
6) Refinement
Refinement is actually a process of elaboration. You begin with a statement of function
(or description of information) that is defined at a high level of abstraction.
That is, the statement describes function or information conceptually but provides no
information about the internal workings of the function or the internal structure of the
information.
Abstraction and refinement are complementary concepts. Abstraction enables you to
specify procedure and data internally but suppress the need for “outsiders” to have knowledge of
low-level details. Refinement helps you to reveal low-level details as design progresses. Both
concepts allow you to create a complete design model as the design evolves.
7) Aspects
As requirements analysis occurs, a set of “concerns” is uncovered. These concerns
“include requirements, use cases, features, data structures, quality-of-service issues, variants,
intellectual property boundaries, collaborations, patterns and contracts”
8) Refactoring
“Refactoring is the process of changing software system in such a way that it does not
alter the external behavior of the code yet improves its internal structure.”
When software is refactored, the existing design is examined for redundancy, unused
design elements, inefficient or unnecessary algorithms, poorly constructed or inappropriate data
structures, or any other design failure that can be corrected to yield a better design.
9) What Is Architecture?
“The software architecture of a program or computing system is the structure or structures of the
system, which comprise software components, the externally visible properties of those
components, and the relationships among them”
The architecture is not the operational software. Rather, it is a representation that enables you to
1) Analyze the effectiveness of the design in meeting its stated requirements,
Software Engineering Dept of IT, SV Colleges
2) Consider architectural alternatives at a stage when making design changes is still relatively
easy, and
3) Reduce the risks associated with the construction of the software.
10) Why Is Architecture Important?
Three key reasons that software architecture is important
1. Representations of software architecture are an enabler for communication between all
parties (stakeholders) interested in the development of a computer-based system.
2. The architecture highlights early design decisions that will have a profound impact on all
software engineering work that follows and, as important, on the ultimate success of the
system as an operational entity.
3. Architecture “constitutes a relatively small, intellectually graspable model of how the
system is structured and how its components work together”
11) Architectural Genres
The architectural genre will often dictate the specific architectural approach to the
structure that must be built. In the context of architectural design, genre implies a specific
category within the overall software domain. Within each category, you encounter a number of
subcategories.
Grady Booch suggests the following architectural genres for software-based systems
Artificial intelligence—Systems that simulate or augment human cognition, locomotion,
or other organic processes.
Commercial and nonprofit—Systems that are fundamental to the operation of a
business enterprise.
Communications—Systems that provide the infrastructure for transferring and managing
data, for connecting users of that data, or for presenting data at the edge of an
infrastructure.
Content authoring—Systems that are used to create or manipulate textual or multimedia
artifacts.
Devices—Systems that interact with the physical world to provide some point service for
an individual.
Entertainment and sports—Systems that manage public events or that provide a large
group entertainment experience.
Financial—Systems that provide the infrastructure for transferring and managing money
and other securities.
Games—Systems that provide an entertainment experience for individuals or groups.
Software Engineering Dept of IT, SV Colleges
Government—Systems that support the conduct and operations of a local, state, federal,
global, or other political entity.
Industrial—Systems that simulate or control physical processes.
Legal—Systems that support the legal industry.
Medical—Systems that diagnose or heal or that contribute to medical research.
Military—Systems for consultation, communications, command, control, and
intelligence (C4I) as well as offensive and defensive weapons.
Operating systems—Systems that sit just above hardware to provide basic software
services.
Platforms—Systems that sit just above operating systems to provide advanced services.
Scientific—Systems that are used for scientific research and applications.
Tools—Systems that are used to develop other systems.
Transportation—Systems that control water, ground, air, or space vehicles.
Utilities—Systems that interact with other software to provide some point service.
12) Defining Archetypes
An archetype is a class or pattern that represents a core abstraction that is critical to the
design of architecture for the target system.
Continuing the discussion of the SafeHome home security function, you might define the
following archetypes:
Node: Represents a cohesive collection of input and output elements of the home
security function. For example a node might be comprised of
1) Various sensors and
2) A variety of alarm (output) indicators.
Detector: An abstraction that encompasses all sensing equipment that feeds information
into the target system.
Indicator. An abstraction that represents all mechanisms (e.g., alarm siren, flashing
lights, bell) for indicating that an alarm condition is occurring.
Controller. An abstraction that depicts the mechanism that allows the arming or
disarming of a node. If controllers reside on a network, they have the ability to
communicate with one another.
Software Engineering Dept of IT, SV Colleges
You might also like
- AU480-680 Basics of LIS CommunicationDocument54 pagesAU480-680 Basics of LIS CommunicationAssiaZ100% (2)
- 174M1A0431-PPT ON 6G TechnologyDocument17 pages174M1A0431-PPT ON 6G TechnologyApple Balu77% (13)
- DNC Setting On Fanuc-0mDocument3 pagesDNC Setting On Fanuc-0msunhuynhNo ratings yet
- Azure Storage PDFDocument1,305 pagesAzure Storage PDFSrinivasa VaradhanNo ratings yet
- Software Engineering Interview QuestionDocument23 pagesSoftware Engineering Interview QuestionHarpreet Singh BaggaNo ratings yet
- SOftware Engineering QuestionDocument19 pagesSOftware Engineering QuestionRana afaqNo ratings yet
- Software Engineering Two Marks Questions Unit-IDocument2 pagesSoftware Engineering Two Marks Questions Unit-IJyo ReddyNo ratings yet
- Unit 4 - Software Engineering - WWW - Rgpvnotes.inDocument11 pagesUnit 4 - Software Engineering - WWW - Rgpvnotes.insai projectNo ratings yet
- Category: This Is About All Aspects of (SW) Which Here Is Taken To Include The Following CategoriesDocument11 pagesCategory: This Is About All Aspects of (SW) Which Here Is Taken To Include The Following CategoriesKeval PatelNo ratings yet
- Software Engineering QuestionsDocument6 pagesSoftware Engineering QuestionsRajat PatraNo ratings yet
- Mock ExamDocument9 pagesMock ExamAntonateNo ratings yet
- Experiment No. 1: Name: Juili Maruti Kadu Te A Roll No: 19 UID: 118CP1102B Sub: Software EngineeringDocument32 pagesExperiment No. 1: Name: Juili Maruti Kadu Te A Roll No: 19 UID: 118CP1102B Sub: Software EngineeringJuili KNo ratings yet
- Solved SE Paper May 2013Document18 pagesSolved SE Paper May 2013yo menNo ratings yet
- Unit III Software Project PlanningDocument7 pagesUnit III Software Project PlanningamarmudirajNo ratings yet
- Answer Key - Sem-In-1 - Regular SE MID-1Document8 pagesAnswer Key - Sem-In-1 - Regular SE MID-1Chinnu JashuvaNo ratings yet
- Introduction To Software Engineering.Document31 pagesIntroduction To Software Engineering.AmardeepSinghNo ratings yet
- Software Engineering Interview Questions PDFDocument6 pagesSoftware Engineering Interview Questions PDFscatNo ratings yet
- Unit 4 - Software Engineering - WWW - Rgpvnotes.inDocument12 pagesUnit 4 - Software Engineering - WWW - Rgpvnotes.inNazma QureshiNo ratings yet
- SE Unit 1 NotesDocument25 pagesSE Unit 1 Notessahil sharmaNo ratings yet
- Se Register NewDocument42 pagesSe Register NewDark worldNo ratings yet
- Software Development (1) TT PDFDocument13 pagesSoftware Development (1) TT PDFRony GhoshNo ratings yet
- SPQM 1Document5 pagesSPQM 1Zuhaib AyazNo ratings yet
- Sepm U1Document22 pagesSepm U1AYUSHI KOLHENo ratings yet
- Chap 2 Software Project ManagementDocument11 pagesChap 2 Software Project ManagementmigadNo ratings yet
- Se Soln PDFDocument20 pagesSe Soln PDFRîshï VîjâÿNo ratings yet
- Software Engineering Interview QuestionsDocument9 pagesSoftware Engineering Interview Questionssriramganesh8107100% (1)
- Lect-9Document21 pagesLect-9PIYUSH YAYATINo ratings yet
- SDLCDocument6 pagesSDLCsameer 77No ratings yet
- 2K20 - CO - 011 - Aayush PatelDocument15 pages2K20 - CO - 011 - Aayush Patel2K20CO355 Ranjeet MadhavNo ratings yet
- Software Development Life Cycle (SDLC)Document25 pagesSoftware Development Life Cycle (SDLC)Al Muktadir MunamNo ratings yet
- Introduction To Software Engineering: Chapter-1Document112 pagesIntroduction To Software Engineering: Chapter-1Janabhawana CampusNo ratings yet
- M2 Cost and EstimatesDocument18 pagesM2 Cost and EstimatesAKHSATNo ratings yet
- Process Models 2Document11 pagesProcess Models 2areebaashraf3No ratings yet
- Project - Software Engineering TechniquesDocument141 pagesProject - Software Engineering TechniquesSwaminathanNo ratings yet
- Se Module 1Document22 pagesSe Module 1HARINo ratings yet
- Software Engineering: Interview QuestionsDocument13 pagesSoftware Engineering: Interview QuestionsParvez AhmedNo ratings yet
- Se Viva Practical Viva Questions For Software EngineeringDocument10 pagesSe Viva Practical Viva Questions For Software EngineeringAbhijeet Malabade50% (4)
- SDCL Pract 3Document6 pagesSDCL Pract 3Mahesh DarvankarNo ratings yet
- CCS356 - OOSE Question BankDocument28 pagesCCS356 - OOSE Question Bankjitbhav97No ratings yet
- SE Chapter4Document26 pagesSE Chapter4JasonDelumenNo ratings yet
- Chapter 1 Introduction To Development Approach SSAD and OOADDocument71 pagesChapter 1 Introduction To Development Approach SSAD and OOADPrashant Shitole100% (1)
- OOSE Chapter1Document80 pagesOOSE Chapter1Aadarsha Thapa MagarNo ratings yet
- Software Project Management ECS082Document28 pagesSoftware Project Management ECS082Ashutosh PandeyNo ratings yet
- Software Projec WPS Office1Document25 pagesSoftware Projec WPS Office1Bishu ThakurNo ratings yet
- Software Engineering ProblemDocument72 pagesSoftware Engineering ProblemAwesome DudeNo ratings yet
- Chapter 1Document31 pagesChapter 1yomiftamiru21No ratings yet
- Digi Notes 09-02-2016 ComputerDocument16 pagesDigi Notes 09-02-2016 ComputerAnzu HondaNo ratings yet
- Unit-1 - Software Process ModelDocument61 pagesUnit-1 - Software Process Model21EBKCS048Jyotsna BishtNo ratings yet
- TESTINGDocument82 pagesTESTINGchandan h lNo ratings yet
- HS Solved Paper 2Document6 pagesHS Solved Paper 2caNo ratings yet
- Sen Question Bank For PTT2Document12 pagesSen Question Bank For PTT231 Malim Aadib ANNo ratings yet
- Lecture 3.Document7 pagesLecture 3.Ümid NazarovNo ratings yet
- Assignment PGD-2103: Software EngineeringDocument20 pagesAssignment PGD-2103: Software EngineeringGurpreet SinghNo ratings yet
- SPM NotesDocument10 pagesSPM NotesSrikanth DeivasigamaniNo ratings yet
- 1st AnswerDocument3 pages1st AnswergNo ratings yet
- Unit - 1: Software Product and SDLCDocument15 pagesUnit - 1: Software Product and SDLCsirqaimNo ratings yet
- Unit I Introduction To Software Project ManagementDocument37 pagesUnit I Introduction To Software Project ManagementAbhishek BondardeNo ratings yet
- CS101Document2 pagesCS101TshahzadaNo ratings yet
- 3cs4-07 Software Engineering Unit - 1 NotesDocument30 pages3cs4-07 Software Engineering Unit - 1 Notesdileep bangadNo ratings yet
- 3CS4-07 Software Engineering Unit - 1 NotesDocument30 pages3CS4-07 Software Engineering Unit - 1 NotesMUSIC SAININo ratings yet
- Unit 1 Software EngineeringDocument60 pagesUnit 1 Software EngineeringyuitakanoakaNo ratings yet
- Phases of The SDLC and Software DesignDocument6 pagesPhases of The SDLC and Software DesignTahskNo ratings yet
- Important QuestionsDocument11 pagesImportant Questions236 Prajwal SheteNo ratings yet
- Software Testing Interview Questions You'll Most Likely Be AskedFrom EverandSoftware Testing Interview Questions You'll Most Likely Be AskedNo ratings yet
- Software Engineering Unit-Ii Two Marks Questions: 1. Define Requirements AnalysisDocument2 pagesSoftware Engineering Unit-Ii Two Marks Questions: 1. Define Requirements AnalysisJyo ReddyNo ratings yet
- Topics Beyond SyllabusDocument1 pageTopics Beyond SyllabusJyo ReddyNo ratings yet
- Software Engineering Two Marks Questions Unit-IDocument2 pagesSoftware Engineering Two Marks Questions Unit-IJyo ReddyNo ratings yet
- Unit - 1 QuestionsDocument2 pagesUnit - 1 QuestionsJyo ReddyNo ratings yet
- Information Technology Course File: Software EngineeringDocument10 pagesInformation Technology Course File: Software EngineeringJyo ReddyNo ratings yet
- Data Warehousing/Mining Comp 150 DW Chapter 5: Concept Description: Characterization and ComparisonDocument59 pagesData Warehousing/Mining Comp 150 DW Chapter 5: Concept Description: Characterization and ComparisonJyo ReddyNo ratings yet
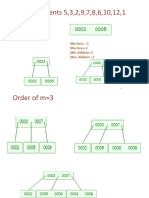
- Insert Elements 5,3,2,9,7,8,6,10,12,1: Min Keys 1 Max Keys 2 Min Children 2 Max Children 3Document10 pagesInsert Elements 5,3,2,9,7,8,6,10,12,1: Min Keys 1 Max Keys 2 Min Children 2 Max Children 3Jyo ReddyNo ratings yet
- Daa-2marks and 10 Marksdescriptive QuestionsDocument3 pagesDaa-2marks and 10 Marksdescriptive QuestionsJyo ReddyNo ratings yet
- Overview - Object-Oriented Analysis and DesignDocument76 pagesOverview - Object-Oriented Analysis and DesignJyo ReddyNo ratings yet
- Sensors: Noise Smoothing For Structural Vibration Test Signals Using An Improved Wavelet Thresholding TechniqueDocument16 pagesSensors: Noise Smoothing For Structural Vibration Test Signals Using An Improved Wavelet Thresholding TechniqueJyo ReddyNo ratings yet
- Vaishnavi Institute of Technology: Tirupati: Subject: Computer Networks (Bits)Document1 pageVaishnavi Institute of Technology: Tirupati: Subject: Computer Networks (Bits)Jyo ReddyNo ratings yet
- Laptop Bag ApprovalDocument2 pagesLaptop Bag ApprovalRidhi KhuranaNo ratings yet
- Arrays in C#Document17 pagesArrays in C#kotiramaNo ratings yet
- Leaflet HipertensiDocument4 pagesLeaflet HipertensiDefrianto BalanteNo ratings yet
- UnknownDocument4 pagesUnknownhchau6853No ratings yet
- 17CS563 Mod3Document13 pages17CS563 Mod3qwerty qwertyNo ratings yet
- Business Object ModelDocument7 pagesBusiness Object Modelapi-3853166No ratings yet
- Resume & Portfolio Fiyan Kurnia HidayatDocument18 pagesResume & Portfolio Fiyan Kurnia HidayatFiyan HidayatNo ratings yet
- H 264 DVRDocument1 pageH 264 DVRRamesh AnanthanarayananNo ratings yet
- Computer Hardware Devices Facts SheetDocument3 pagesComputer Hardware Devices Facts Sheetapi-360544753No ratings yet
- I & IInd Year (Pass Course) 1st To 4th Sem 2012-13Document35 pagesI & IInd Year (Pass Course) 1st To 4th Sem 2012-13HarshNo ratings yet
- D Paper2Document4 pagesD Paper2Vasanth PerniNo ratings yet
- Syllabus PDFDocument2 pagesSyllabus PDFDurgavajjala KarthikNo ratings yet
- PARTHIDocument13 pagesPARTHIsampathaboNo ratings yet
- VGD Aptitude and Artistic Determination Test AADT UpdatedDocument2 pagesVGD Aptitude and Artistic Determination Test AADT UpdatedAlberto T. ToledoNo ratings yet
- Aspire E5-522 - ZRZL - ZRZDocument40 pagesAspire E5-522 - ZRZL - ZRZAdmin 010% (1)
- User Manual Netsilon PDFDocument74 pagesUser Manual Netsilon PDFdexiNo ratings yet
- Oracle SlideDocument30 pagesOracle Slideshyam ranaNo ratings yet
- Baan PresentationDocument17 pagesBaan Presentationshazeb zafarNo ratings yet
- ICF I Lesson 9Document7 pagesICF I Lesson 9Princess JulianneNo ratings yet
- In The 80386 Microprocessor and LaterDocument1 pageIn The 80386 Microprocessor and LaterAnkit BhatnagarNo ratings yet
- PCI DSS v3 2 1 ROC S1 Contact InformationDocument14 pagesPCI DSS v3 2 1 ROC S1 Contact Informationmrehan2k2No ratings yet
- Dynamixel Ax 12aDocument11 pagesDynamixel Ax 12aAbrizen Duha PerbanggaNo ratings yet
- v6 ManualDocument495 pagesv6 ManualhikaaNo ratings yet
- CCcam - CFG SimpleDocument3 pagesCCcam - CFG SimpleSadia KanwalNo ratings yet
- License and CopyrightDocument1 pageLicense and CopyrightCarola M. GonzalezNo ratings yet
- Introduction To Software EngineeringDocument94 pagesIntroduction To Software EngineeringTsion KebedeNo ratings yet