Professional Documents
Culture Documents
0 ratings0% found this document useful (0 votes)
24 viewsICT 320 Unit 8
ICT 320 Unit 8
Uploaded by
Michael SiameNetwork security involves protecting networks through identification, authentication, and access control methods. Cryptography uses encryption algorithms and keys to secure data in transmission. Identification uniquely identifies users, authentication verifies identities, and access control restricts access to resources. Encryption techniques include symmetric ciphers, public key cryptography, and digital signatures. The document discusses these network security and cryptography concepts at a high level.
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
You might also like
- Vocabulary by Aytan IsmayilzadaDocument26 pagesVocabulary by Aytan Ismayilzadanazrinxalilova2000No ratings yet
- CCNAS - Ch7 - Cryptographic SystemsDocument88 pagesCCNAS - Ch7 - Cryptographic SystemsVishal AvhadNo ratings yet
- Chapter 1 and 2 Obl IconDocument10 pagesChapter 1 and 2 Obl IconPia ValdezNo ratings yet
- Cryptography and Network SecurityDocument18 pagesCryptography and Network Securitykarishma vaidyaNo ratings yet
- Link Encryption: 3.1 Security ObjectivesDocument21 pagesLink Encryption: 3.1 Security ObjectivesThanh Phuong HuynhNo ratings yet
- Blowfish On FPGADocument6 pagesBlowfish On FPGAVinayak KumarNo ratings yet
- Guided by Vibjan Kolapati Mrs. Sheena Mathew CS-B, Roll No:97Document21 pagesGuided by Vibjan Kolapati Mrs. Sheena Mathew CS-B, Roll No:97Yassine SadqiNo ratings yet
- Presented By: Anurag Roll No:-1703233 Topic: Network SecurityDocument28 pagesPresented By: Anurag Roll No:-1703233 Topic: Network SecurityAnurag GuptaNo ratings yet
- Cloud Security Lecture 1Document50 pagesCloud Security Lecture 1Hossam EissaNo ratings yet
- Networ AssignmentDocument44 pagesNetwor Assignmentmargaa bacuraaNo ratings yet
- Cryptography-Applied Linear AlgebraDocument37 pagesCryptography-Applied Linear AlgebraHarsh RattewalNo ratings yet
- CryptographyDocument19 pagesCryptographySrilekha RajakumaranNo ratings yet
- Demystifying VPNDocument12 pagesDemystifying VPNMarcos Aurélio RodriguesNo ratings yet
- If You Have To Both Encrypt and Compress Data During Transmission, Which Would You Do First, and Why?Document20 pagesIf You Have To Both Encrypt and Compress Data During Transmission, Which Would You Do First, and Why?Pallavi BhartiNo ratings yet
- VPN SecurityDocument12 pagesVPN SecuritydondegNo ratings yet
- Encryption and Decryption System Using Rc4Document11 pagesEncryption and Decryption System Using Rc4Atul KhadeNo ratings yet
- Cryptography and Network SecurityDocument21 pagesCryptography and Network SecurityvinAY50% (2)
- Data Encryption StandardDocument37 pagesData Encryption Standardchristian MacNo ratings yet
- CryptographyDocument20 pagesCryptographySrilekha RajakumaranNo ratings yet
- Css AssignmentDocument3 pagesCss Assignmentsoftac solutionsNo ratings yet
- EncryptionDocument27 pagesEncryptionLavanyaNo ratings yet
- Term PaperDocument5 pagesTerm PaperSai Teja UppuluriNo ratings yet
- ProjectDocument7 pagesProjectpradeepkumar.it2020No ratings yet
- RC4 CryptographyDocument61 pagesRC4 Cryptographyga18392100% (3)
- Networksecurity ND CryptographyDocument20 pagesNetworksecurity ND CryptographyJohn GuerreroNo ratings yet
- Ist hw3Document3 pagesIst hw3Amaltas SinghNo ratings yet
- Presented By: Anurag Roll No:-1703233 Topic: Network SecurityDocument28 pagesPresented By: Anurag Roll No:-1703233 Topic: Network SecurityAnurag GuptaNo ratings yet
- 2 Marks CryptographyDocument13 pages2 Marks Cryptography219 DibyanshuKumarNo ratings yet
- Security Issues in Cloud ComputingDocument32 pagesSecurity Issues in Cloud Computingsingh400amitNo ratings yet
- Cryptography and Network Security 1Document11 pagesCryptography and Network Security 1Srini VasuluNo ratings yet
- CryptographyDocument7 pagesCryptographypradeepkumar.it2020No ratings yet
- A Study of Blowfish Encryption AlgorithmDocument4 pagesA Study of Blowfish Encryption AlgorithmShamnad Ps100% (1)
- Methods Toward Enhancing Rsa Algorithm: A SurveyDocument18 pagesMethods Toward Enhancing Rsa Algorithm: A SurveyAIRCC - IJNSANo ratings yet
- Networking Interview QuestionDocument19 pagesNetworking Interview QuestionSam RogerNo ratings yet
- What Is EncryptionDocument6 pagesWhat Is EncryptionMuhammad FarhanNo ratings yet
- CybersecDocument6 pagesCybersectalukdarranjan69No ratings yet
- Unit 6Document37 pagesUnit 6Remadan MohammedNo ratings yet
- Performance Evaluation of Various Symmetric Encryption AlgorithmsDocument5 pagesPerformance Evaluation of Various Symmetric Encryption Algorithmsg.divya0612No ratings yet
- Security & Savings With Virtual Private Networks: Everybody's ConnectingDocument13 pagesSecurity & Savings With Virtual Private Networks: Everybody's ConnectingAdi Chandra SetiawanNo ratings yet
- Ijcert JournalsDocument6 pagesIjcert JournalsIJCERT PUBLICATIONSNo ratings yet
- Network SecurityDocument8 pagesNetwork SecurityShanthan ReddyNo ratings yet
- Cryptography ReportDocument10 pagesCryptography ReportAkshath KandlurNo ratings yet
- It 2352-CNSDocument21 pagesIt 2352-CNSlakshmigajendranNo ratings yet
- Study On Security Issues in Computer Networks and Encryption TechniquesDocument6 pagesStudy On Security Issues in Computer Networks and Encryption TechniquesInternational Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- Cloud Cryptography and Data Security IJERTV10IS110100Document2 pagesCloud Cryptography and Data Security IJERTV10IS110100techieNo ratings yet
- Final RSA DocumentationDocument125 pagesFinal RSA DocumentationKishore PinnintiNo ratings yet
- Security in E-CommerceDocument29 pagesSecurity in E-CommerceAlex T BinoyNo ratings yet
- Paper Presentation Cryptography: BY Mothishkumar.S Sharath Abilash Ak Mohamed Ali Jinna A Muralidaran BeeceDocument6 pagesPaper Presentation Cryptography: BY Mothishkumar.S Sharath Abilash Ak Mohamed Ali Jinna A Muralidaran BeeceMohamed jinnaNo ratings yet
- Cryptography AnswersDocument21 pagesCryptography Answers219 DibyanshuKumarNo ratings yet
- Cns CheatDocument12 pagesCns CheatBIJOY MAJUMDERNo ratings yet
- Network Security & Cryptography: Paper ONDocument10 pagesNetwork Security & Cryptography: Paper ONapi-19799369No ratings yet
- Network Security Using CryptographyDocument11 pagesNetwork Security Using CryptographyARVIND100% (1)
- Security: Abenoja, Michael Joseph B Campos, Jennylyn T Dugenia, Marrieda CDocument19 pagesSecurity: Abenoja, Michael Joseph B Campos, Jennylyn T Dugenia, Marrieda CJenny AndresNo ratings yet
- Security in e - CommerceDocument4 pagesSecurity in e - CommerceAlex T BinoyNo ratings yet
- Cryptography Data Encryption: Bhaskar Kakulavarapu ISACA-Detroit ChapterDocument33 pagesCryptography Data Encryption: Bhaskar Kakulavarapu ISACA-Detroit ChapterDBNo ratings yet
- Sherwood-Gallo1990 Chapter TheApplicationOfSmartCardsForRDocument13 pagesSherwood-Gallo1990 Chapter TheApplicationOfSmartCardsForRRathnamNo ratings yet
- Lecture-5 Security DarkDocument35 pagesLecture-5 Security DarkMD. RAKIB HASSANNo ratings yet
- Mat 3.contoh Enkripsi Dan Dekripsi (Irfan Ramadhan 231) (Riyan Fujianto 229) Lesmana SaputraDocument41 pagesMat 3.contoh Enkripsi Dan Dekripsi (Irfan Ramadhan 231) (Riyan Fujianto 229) Lesmana SaputraPanNo ratings yet
- CS#3 - 3Document30 pagesCS#3 - 3faiza abdellaNo ratings yet
- KAVACH'23: Team: Key KeepersDocument9 pagesKAVACH'23: Team: Key Keeperspro coder MinecraftNo ratings yet
- REMOTE ACCESS VPN- SSL VPN: A deep dive into SSL VPN from basicFrom EverandREMOTE ACCESS VPN- SSL VPN: A deep dive into SSL VPN from basicRating: 5 out of 5 stars5/5 (1)
- Piramal Ar Full 2015 16Document292 pagesPiramal Ar Full 2015 16Naman TandonNo ratings yet
- (Download PDF) Economics For Healthcare Managers Fourth Edition Edition Robert H Lee Online Ebook All Chapter PDFDocument52 pages(Download PDF) Economics For Healthcare Managers Fourth Edition Edition Robert H Lee Online Ebook All Chapter PDFbenjamin.johnson786100% (13)
- Patricia Eldridge 4.19.23Document3 pagesPatricia Eldridge 4.19.23abhi kumarNo ratings yet
- Globaltouch West Africa Limited A Case For Reinvestment Toward ProfitabilityDocument7 pagesGlobaltouch West Africa Limited A Case For Reinvestment Toward ProfitabilityDyaji Charles BalaNo ratings yet
- Video Production TimelineDocument1 pageVideo Production TimelineLeisuread 2No ratings yet
- Self Declaration CertificateDocument1 pageSelf Declaration CertificatePuran SinghNo ratings yet
- Tenggara Backgrounder 2023 Jun 09 1 sPNFol6RDocument20 pagesTenggara Backgrounder 2023 Jun 09 1 sPNFol6RAlisa Syakila MaharaniNo ratings yet
- The Psychological ContractDocument5 pagesThe Psychological Contractანი გორგოძეNo ratings yet
- Law On Treaties Group 4Document51 pagesLaw On Treaties Group 4Seyre Eser ArymNo ratings yet
- 7BT60 Series: Vacuum Interrupter Test SetDocument2 pages7BT60 Series: Vacuum Interrupter Test SetenticoNo ratings yet
- SEM-3 - Business Process Integration (BPI)Document20 pagesSEM-3 - Business Process Integration (BPI)Hee ManNo ratings yet
- Catalog KiepeDocument6 pagesCatalog KiepeTacuNo ratings yet
- Commands ListDocument11 pagesCommands ListAll SubscribeNo ratings yet
- Sheet MetalDocument42 pagesSheet MetalNavtej Singh100% (3)
- FAQs On RMIBD - Hedging of Foreign Exchange Risk DTD July 14 2020Document7 pagesFAQs On RMIBD - Hedging of Foreign Exchange Risk DTD July 14 2020Anup SharmaNo ratings yet
- Tablet CoatingDocument7 pagesTablet CoatingLakmi Nurul UciiNo ratings yet
- Microtig 185 DaDocument40 pagesMicrotig 185 DaCONTROLES PHILLMATNo ratings yet
- Air France v. CA (1983)Document10 pagesAir France v. CA (1983)8111 aaa 1118No ratings yet
- Tata PowerDocument9 pagesTata PowerAnkita SinghNo ratings yet
- A Guide To Windows in Nathers SoftwareDocument6 pagesA Guide To Windows in Nathers Softwarezumrakaraca.auNo ratings yet
- Verantis BlowerDocument14 pagesVerantis BlowerTaniadi SuriaNo ratings yet
- Dissertation Research Project Report. 2Document86 pagesDissertation Research Project Report. 2Deep ChoudharyNo ratings yet
- 00 M5 PM ImtsDocument28 pages00 M5 PM ImtsTheresia AninditaNo ratings yet
- AHR 2016previewDocument29 pagesAHR 2016previewAnonymous XhkjXCxxsTNo ratings yet
- Industrial Training at Traco Cables Company Limited: Cochin University College of Engineering KUTTANADU-637215Document30 pagesIndustrial Training at Traco Cables Company Limited: Cochin University College of Engineering KUTTANADU-637215Vimal SudhakaranNo ratings yet
- Transfer PricingDocument12 pagesTransfer PricingMark Lorenz100% (1)
- Kel IV ReportDocument18 pagesKel IV ReportAnoopAsokan0% (1)
- Sports Economics 2017 1st Edition Berri Solutions ManualDocument8 pagesSports Economics 2017 1st Edition Berri Solutions Manualbrendabrownipnmktbzas100% (10)
ICT 320 Unit 8
ICT 320 Unit 8
Uploaded by
Michael Siame0 ratings0% found this document useful (0 votes)
24 views15 pagesNetwork security involves protecting networks through identification, authentication, and access control methods. Cryptography uses encryption algorithms and keys to secure data in transmission. Identification uniquely identifies users, authentication verifies identities, and access control restricts access to resources. Encryption techniques include symmetric ciphers, public key cryptography, and digital signatures. The document discusses these network security and cryptography concepts at a high level.
Original Description:
Original Title
ICT 320 unit 8
Copyright
© © All Rights Reserved
Available Formats
PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentNetwork security involves protecting networks through identification, authentication, and access control methods. Cryptography uses encryption algorithms and keys to secure data in transmission. Identification uniquely identifies users, authentication verifies identities, and access control restricts access to resources. Encryption techniques include symmetric ciphers, public key cryptography, and digital signatures. The document discusses these network security and cryptography concepts at a high level.
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
Download as pdf or txt
0 ratings0% found this document useful (0 votes)
24 views15 pagesICT 320 Unit 8
ICT 320 Unit 8
Uploaded by
Michael SiameNetwork security involves protecting networks through identification, authentication, and access control methods. Cryptography uses encryption algorithms and keys to secure data in transmission. Identification uniquely identifies users, authentication verifies identities, and access control restricts access to resources. Encryption techniques include symmetric ciphers, public key cryptography, and digital signatures. The document discusses these network security and cryptography concepts at a high level.
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
Download as pdf or txt
You are on page 1of 15
DATA Network Security and
COMMUNICATIONA AND Cryptography
By Mr. Chishala G
NETWORKING Email: gmakunka@yahoo.com
NETWORK SECURITY AND
CRYPTOGRAPHY
❑Network security consists of the provisions and policies adopted by a network administrator to
prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and
network-accessible resources.
❑ Network security involves the authorization of access to data in a network, which is controlled by the
network administrator.
❑Network security covers a variety of computer networks, both public and private, that are used in
everyday jobs conducting transactions and communications among businesses, government agencies
and individuals.
❑WHY DO WE NEED SECURITY?
❑Protect vital information while still allowing access to those who need it such as Trade secrets,
medical records, etc.
❑ Provide authentication and access control for resources
❑ Guarantee availability of resources
NETWORK SECURITY AND
CRYPTOGRAPHY
SECURITY OBJECTIVES:
❑IDENTIFICATION
❑AUTHENTICATION
❑ACCESS CONTROL
IDENTIFICATION:
❑Something which uniquely identifies a user and is called UserID. Sometimes users can select their ID
as long as it is given too another user.
❑UserID can be one or combination of the following:
▪User Name
▪User Student Number
▪User SSN
NETWORK SECURITY AND
AUTHENTICATION:
CRYPTOGRAPHY
❑The process of verifying the identity of a user Typically based on
▪Something user knows
▪Password
▪Something user have
▪Key, smart card, disk, or other device
▪Something user is fingerprint, voice, or retinal scans
❑AUTHENTICATION: 2 SUB CONCERNS
▪GENERAL ACCESS AUTHENTICATION
To control whether or not a particular user has ANY type of access right to the element in question.
Usually we consider these in the form of a “User Account”.
NETWORK SECURITY AND
CRYPTOGRAPHY
▪FUNCTIONAL AUTHORIZATION
Concern with individual user “rights”. What, for example, can a user do once authenticated? Can
they figure the device or only see data.
❑AUTHENTICATION: MAJOR PROTOCOLS
NETWORK SECURITY AND
❑ACCESS CONTROL: CRYPTOGRAPHY
❑Refers to security features that control who can access resources in the operating system.
❑Applications call access control functions to set who can access specific resources or control access
to resources provided by the application.
❑Firewalls:
▪A firewall can limit the types of transactions that enter a system, as well as the types of transactions
that leave a system.
▪Firewalls can be programmed to stop certain types or ranges of IP addresses, as well as certain types
of TCP port numbers (applications).
❑A packet filter firewall is essentially a router that has been programmed to filter out or allow to pass
certain IP addresses or TCP port numbers(Access list configuration).
❑A proxy server is a more advanced firewall that acts as a doorman into a corporate network. Any
external transaction that request something from the corporate network must enter through the proxy
server. Proxy servers are more advanced but make external accesses slower.
NETWORK SECURITY AND
CRYPTOGRAPHY
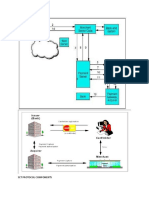
❑The fig below shows a fire wall as it stops certain internal and external transactions.
NETWORK SECURITY AND
❑Wireless Security:
CRYPTOGRAPHY
❑How do you make a wireless LAN secure? WEP (Wired Equivalency Protocol) was the first security
protocol used with wireless LANs.
❑It had weak 40-bit static keys and was too easy to break. WPA (Wi-Fi Protected Access) replaced
WEP.
❑Major improvement including dynamic key encryption and mutual authentication for wireless clients.
❑Both of these should eventually give way to a new protocol created by the IEEE - IEEE 802.11i.
802.11i allows the keys, the encryption algorithms, and negotiation to be dynamically assigned.
❑Also, AES encryption based on the Rijndael algorithm with 128-, 192-, or 256-bit keys is
incorporated.
❑Security Policy Design Issues:
❑What is the company’s desired level of security?
NETWORK SECURITY AND
CRYPTOGRAPHY
❑How much money is the company willing to invest in security? If the company is serious about
restricting access through an Internet link, what about restricting access through all other entry ways?
❑The company must have a well-designed security policy.
❑Basic Encryption and Decryption:
❑Cryptography is the study of creating and using encryption and decryption
techniques.
❑Plaintext is the data that before any encryption has been performed.
❑ Ciphertext is the data after encryption has been performed.
❑The key is the unique piece of information that is used to create ciphertext and
decrypt the ciphertext back into plaintext.
NETWORK SECURITY AND
CRYPTOGRAPHY
❑Basic encryption and decryption is shown below.
❑Mono alphabetic Substitution-based Ciphers: Monoalphabetic substitution-based ciphers replace a
character or characters with a different character or characters, based upon some key.
Replacing: abcdefghijklmnopqrstuvwxyz
with: POIUYTREWQLKJHGFDSAMNBVCXZ
The message: how about lunch at noon encodes into EGVPO GNMKN HIEPM HGGH
NETWORK SECURITY AND
CRYPTOGRAPHY
❑Transposition-based Ciphers:
❑In a transposition-based cipher, the order the plaintext is not preserved.
❑As a simple example, select a key such as COMPUTER. Number the letters of the word
COMPUTER in the order they appear in the alphabet.
14358726
COMPUTER
❑Now take the plaintext message and write it under the key.
14358726
COMPUTER
t h i s i s t h
eb es t c la
s s i havee
v e r taken
NETWORK SECURITY AND
CRYPTOGRAPHY
❑Then read the ciphertext down the columns, starting with the column numbered 1, followed by
column number 2.
▪TESVTLEEIEIRHBSESSHTHAENSCVKITAA
❑Public Key Cryptography:
❑Very powerful encryption technique in which two keys are used: the first key (the public key)
encrypts the message while the second key (the private key) decrypts the message.
❑Not possible to deduce one key from the other. Not possible to break the code given the public key.
❑ If you want someone to send you secure data, give them your public key, you keep the private key.
Secure sockets layer on the Internet is a common example of public key cryptography.
❑Data Encryption Standard:
▪Created in 1977 and in operation into the 1990s, the data encryption standard took a 64-bit block o
▪if data and subjected it to 16 levels of encryption.
NETWORK SECURITY AND
CRYPTOGRAPHY
❑The choice of encryption performed at each of the 16 levels depends on the 56-bit key applied.
❑Even though 56 bits provides over 72 quadrillion combinations, a system using this standard has been
cracked (in 1998 by Electronic Frontier Foundation in 3 days).
❑The basic operation of the data encryption standard:
NETWORK SECURITY AND
❑Triple-DES:
CRYPTOGRAPHY
❑A more powerful data encryption standard. Data is encrypted using DES three times: the first time by
the first key, the second time by a second key, and the third time by the first key again.
❑ (Can also have 3 unique keys.) While virtually unbreakable, triple-DES is CPU intensive. With more
smart cards, cell phones, and PDAs, a faster (and smaller) piece of code is highly desirable.
❑Advanced Encryption Standard (AES)
❑AES has more elegant mathematical formulas, requires only one pass, and was designed to be fast,
unbreakable, and able to support even the smallest computing device.
❑Estimated time to crack (assuming a machine could crack a DES key in 1 second) : 149 trillion years
very fast execution with very good use of resources.
❑Digital Signatures:
▪Document to be signed is sent through a complex mathematical computation that generates a hash.
NETWORK SECURITY AND
CRYPTOGRAPHY
❑Document to be signed is sent through a complex mathematical computation that generates a hash.
❑Hash is encoded with the owner’s private key then stored.
❑ To prove future ownership, stored hash is decoded using the owner’s public key and that hash is
compared with a current hash of the document.
❑If the two hashes agree, the document belongs to the owner. The U.S. has just approved legislation
to accept digitally signed documents as legal proof.
You might also like
- Vocabulary by Aytan IsmayilzadaDocument26 pagesVocabulary by Aytan Ismayilzadanazrinxalilova2000No ratings yet
- CCNAS - Ch7 - Cryptographic SystemsDocument88 pagesCCNAS - Ch7 - Cryptographic SystemsVishal AvhadNo ratings yet
- Chapter 1 and 2 Obl IconDocument10 pagesChapter 1 and 2 Obl IconPia ValdezNo ratings yet
- Cryptography and Network SecurityDocument18 pagesCryptography and Network Securitykarishma vaidyaNo ratings yet
- Link Encryption: 3.1 Security ObjectivesDocument21 pagesLink Encryption: 3.1 Security ObjectivesThanh Phuong HuynhNo ratings yet
- Blowfish On FPGADocument6 pagesBlowfish On FPGAVinayak KumarNo ratings yet
- Guided by Vibjan Kolapati Mrs. Sheena Mathew CS-B, Roll No:97Document21 pagesGuided by Vibjan Kolapati Mrs. Sheena Mathew CS-B, Roll No:97Yassine SadqiNo ratings yet
- Presented By: Anurag Roll No:-1703233 Topic: Network SecurityDocument28 pagesPresented By: Anurag Roll No:-1703233 Topic: Network SecurityAnurag GuptaNo ratings yet
- Cloud Security Lecture 1Document50 pagesCloud Security Lecture 1Hossam EissaNo ratings yet
- Networ AssignmentDocument44 pagesNetwor Assignmentmargaa bacuraaNo ratings yet
- Cryptography-Applied Linear AlgebraDocument37 pagesCryptography-Applied Linear AlgebraHarsh RattewalNo ratings yet
- CryptographyDocument19 pagesCryptographySrilekha RajakumaranNo ratings yet
- Demystifying VPNDocument12 pagesDemystifying VPNMarcos Aurélio RodriguesNo ratings yet
- If You Have To Both Encrypt and Compress Data During Transmission, Which Would You Do First, and Why?Document20 pagesIf You Have To Both Encrypt and Compress Data During Transmission, Which Would You Do First, and Why?Pallavi BhartiNo ratings yet
- VPN SecurityDocument12 pagesVPN SecuritydondegNo ratings yet
- Encryption and Decryption System Using Rc4Document11 pagesEncryption and Decryption System Using Rc4Atul KhadeNo ratings yet
- Cryptography and Network SecurityDocument21 pagesCryptography and Network SecurityvinAY50% (2)
- Data Encryption StandardDocument37 pagesData Encryption Standardchristian MacNo ratings yet
- CryptographyDocument20 pagesCryptographySrilekha RajakumaranNo ratings yet
- Css AssignmentDocument3 pagesCss Assignmentsoftac solutionsNo ratings yet
- EncryptionDocument27 pagesEncryptionLavanyaNo ratings yet
- Term PaperDocument5 pagesTerm PaperSai Teja UppuluriNo ratings yet
- ProjectDocument7 pagesProjectpradeepkumar.it2020No ratings yet
- RC4 CryptographyDocument61 pagesRC4 Cryptographyga18392100% (3)
- Networksecurity ND CryptographyDocument20 pagesNetworksecurity ND CryptographyJohn GuerreroNo ratings yet
- Ist hw3Document3 pagesIst hw3Amaltas SinghNo ratings yet
- Presented By: Anurag Roll No:-1703233 Topic: Network SecurityDocument28 pagesPresented By: Anurag Roll No:-1703233 Topic: Network SecurityAnurag GuptaNo ratings yet
- 2 Marks CryptographyDocument13 pages2 Marks Cryptography219 DibyanshuKumarNo ratings yet
- Security Issues in Cloud ComputingDocument32 pagesSecurity Issues in Cloud Computingsingh400amitNo ratings yet
- Cryptography and Network Security 1Document11 pagesCryptography and Network Security 1Srini VasuluNo ratings yet
- CryptographyDocument7 pagesCryptographypradeepkumar.it2020No ratings yet
- A Study of Blowfish Encryption AlgorithmDocument4 pagesA Study of Blowfish Encryption AlgorithmShamnad Ps100% (1)
- Methods Toward Enhancing Rsa Algorithm: A SurveyDocument18 pagesMethods Toward Enhancing Rsa Algorithm: A SurveyAIRCC - IJNSANo ratings yet
- Networking Interview QuestionDocument19 pagesNetworking Interview QuestionSam RogerNo ratings yet
- What Is EncryptionDocument6 pagesWhat Is EncryptionMuhammad FarhanNo ratings yet
- CybersecDocument6 pagesCybersectalukdarranjan69No ratings yet
- Unit 6Document37 pagesUnit 6Remadan MohammedNo ratings yet
- Performance Evaluation of Various Symmetric Encryption AlgorithmsDocument5 pagesPerformance Evaluation of Various Symmetric Encryption Algorithmsg.divya0612No ratings yet
- Security & Savings With Virtual Private Networks: Everybody's ConnectingDocument13 pagesSecurity & Savings With Virtual Private Networks: Everybody's ConnectingAdi Chandra SetiawanNo ratings yet
- Ijcert JournalsDocument6 pagesIjcert JournalsIJCERT PUBLICATIONSNo ratings yet
- Network SecurityDocument8 pagesNetwork SecurityShanthan ReddyNo ratings yet
- Cryptography ReportDocument10 pagesCryptography ReportAkshath KandlurNo ratings yet
- It 2352-CNSDocument21 pagesIt 2352-CNSlakshmigajendranNo ratings yet
- Study On Security Issues in Computer Networks and Encryption TechniquesDocument6 pagesStudy On Security Issues in Computer Networks and Encryption TechniquesInternational Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- Cloud Cryptography and Data Security IJERTV10IS110100Document2 pagesCloud Cryptography and Data Security IJERTV10IS110100techieNo ratings yet
- Final RSA DocumentationDocument125 pagesFinal RSA DocumentationKishore PinnintiNo ratings yet
- Security in E-CommerceDocument29 pagesSecurity in E-CommerceAlex T BinoyNo ratings yet
- Paper Presentation Cryptography: BY Mothishkumar.S Sharath Abilash Ak Mohamed Ali Jinna A Muralidaran BeeceDocument6 pagesPaper Presentation Cryptography: BY Mothishkumar.S Sharath Abilash Ak Mohamed Ali Jinna A Muralidaran BeeceMohamed jinnaNo ratings yet
- Cryptography AnswersDocument21 pagesCryptography Answers219 DibyanshuKumarNo ratings yet
- Cns CheatDocument12 pagesCns CheatBIJOY MAJUMDERNo ratings yet
- Network Security & Cryptography: Paper ONDocument10 pagesNetwork Security & Cryptography: Paper ONapi-19799369No ratings yet
- Network Security Using CryptographyDocument11 pagesNetwork Security Using CryptographyARVIND100% (1)
- Security: Abenoja, Michael Joseph B Campos, Jennylyn T Dugenia, Marrieda CDocument19 pagesSecurity: Abenoja, Michael Joseph B Campos, Jennylyn T Dugenia, Marrieda CJenny AndresNo ratings yet
- Security in e - CommerceDocument4 pagesSecurity in e - CommerceAlex T BinoyNo ratings yet
- Cryptography Data Encryption: Bhaskar Kakulavarapu ISACA-Detroit ChapterDocument33 pagesCryptography Data Encryption: Bhaskar Kakulavarapu ISACA-Detroit ChapterDBNo ratings yet
- Sherwood-Gallo1990 Chapter TheApplicationOfSmartCardsForRDocument13 pagesSherwood-Gallo1990 Chapter TheApplicationOfSmartCardsForRRathnamNo ratings yet
- Lecture-5 Security DarkDocument35 pagesLecture-5 Security DarkMD. RAKIB HASSANNo ratings yet
- Mat 3.contoh Enkripsi Dan Dekripsi (Irfan Ramadhan 231) (Riyan Fujianto 229) Lesmana SaputraDocument41 pagesMat 3.contoh Enkripsi Dan Dekripsi (Irfan Ramadhan 231) (Riyan Fujianto 229) Lesmana SaputraPanNo ratings yet
- CS#3 - 3Document30 pagesCS#3 - 3faiza abdellaNo ratings yet
- KAVACH'23: Team: Key KeepersDocument9 pagesKAVACH'23: Team: Key Keeperspro coder MinecraftNo ratings yet
- REMOTE ACCESS VPN- SSL VPN: A deep dive into SSL VPN from basicFrom EverandREMOTE ACCESS VPN- SSL VPN: A deep dive into SSL VPN from basicRating: 5 out of 5 stars5/5 (1)
- Piramal Ar Full 2015 16Document292 pagesPiramal Ar Full 2015 16Naman TandonNo ratings yet
- (Download PDF) Economics For Healthcare Managers Fourth Edition Edition Robert H Lee Online Ebook All Chapter PDFDocument52 pages(Download PDF) Economics For Healthcare Managers Fourth Edition Edition Robert H Lee Online Ebook All Chapter PDFbenjamin.johnson786100% (13)
- Patricia Eldridge 4.19.23Document3 pagesPatricia Eldridge 4.19.23abhi kumarNo ratings yet
- Globaltouch West Africa Limited A Case For Reinvestment Toward ProfitabilityDocument7 pagesGlobaltouch West Africa Limited A Case For Reinvestment Toward ProfitabilityDyaji Charles BalaNo ratings yet
- Video Production TimelineDocument1 pageVideo Production TimelineLeisuread 2No ratings yet
- Self Declaration CertificateDocument1 pageSelf Declaration CertificatePuran SinghNo ratings yet
- Tenggara Backgrounder 2023 Jun 09 1 sPNFol6RDocument20 pagesTenggara Backgrounder 2023 Jun 09 1 sPNFol6RAlisa Syakila MaharaniNo ratings yet
- The Psychological ContractDocument5 pagesThe Psychological Contractანი გორგოძეNo ratings yet
- Law On Treaties Group 4Document51 pagesLaw On Treaties Group 4Seyre Eser ArymNo ratings yet
- 7BT60 Series: Vacuum Interrupter Test SetDocument2 pages7BT60 Series: Vacuum Interrupter Test SetenticoNo ratings yet
- SEM-3 - Business Process Integration (BPI)Document20 pagesSEM-3 - Business Process Integration (BPI)Hee ManNo ratings yet
- Catalog KiepeDocument6 pagesCatalog KiepeTacuNo ratings yet
- Commands ListDocument11 pagesCommands ListAll SubscribeNo ratings yet
- Sheet MetalDocument42 pagesSheet MetalNavtej Singh100% (3)
- FAQs On RMIBD - Hedging of Foreign Exchange Risk DTD July 14 2020Document7 pagesFAQs On RMIBD - Hedging of Foreign Exchange Risk DTD July 14 2020Anup SharmaNo ratings yet
- Tablet CoatingDocument7 pagesTablet CoatingLakmi Nurul UciiNo ratings yet
- Microtig 185 DaDocument40 pagesMicrotig 185 DaCONTROLES PHILLMATNo ratings yet
- Air France v. CA (1983)Document10 pagesAir France v. CA (1983)8111 aaa 1118No ratings yet
- Tata PowerDocument9 pagesTata PowerAnkita SinghNo ratings yet
- A Guide To Windows in Nathers SoftwareDocument6 pagesA Guide To Windows in Nathers Softwarezumrakaraca.auNo ratings yet
- Verantis BlowerDocument14 pagesVerantis BlowerTaniadi SuriaNo ratings yet
- Dissertation Research Project Report. 2Document86 pagesDissertation Research Project Report. 2Deep ChoudharyNo ratings yet
- 00 M5 PM ImtsDocument28 pages00 M5 PM ImtsTheresia AninditaNo ratings yet
- AHR 2016previewDocument29 pagesAHR 2016previewAnonymous XhkjXCxxsTNo ratings yet
- Industrial Training at Traco Cables Company Limited: Cochin University College of Engineering KUTTANADU-637215Document30 pagesIndustrial Training at Traco Cables Company Limited: Cochin University College of Engineering KUTTANADU-637215Vimal SudhakaranNo ratings yet
- Transfer PricingDocument12 pagesTransfer PricingMark Lorenz100% (1)
- Kel IV ReportDocument18 pagesKel IV ReportAnoopAsokan0% (1)
- Sports Economics 2017 1st Edition Berri Solutions ManualDocument8 pagesSports Economics 2017 1st Edition Berri Solutions Manualbrendabrownipnmktbzas100% (10)