Professional Documents
Culture Documents
0 ratings0% found this document useful (0 votes)
59 viewsIGCSE Security
IGCSE Security
Uploaded by
Caroline Muvirimi1. The document provides instructions for answering questions about data security and ethics. It asks to define different types of internet security threats like viruses, phishing, and pharming.
2. Questions are asked to match security issues like pharming, phishing, and viruses to their definitions. Terms related to data security are also defined, including hacking, spyware, cookies, encryption, secure socket layer, proxy server, and denial of service attacks.
3. The document asks how tools like secure socket layer and firewalls can keep data safe during transmission and storage, and what additional security measures a company should take to protect customer data stored on its computer systems.
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
You might also like
- CEH: Certified Ethical Hacker v11 : Exam Cram Notes - First Edition - 2021From EverandCEH: Certified Ethical Hacker v11 : Exam Cram Notes - First Edition - 2021No ratings yet
- A) What Is A Hacker?Document2 pagesA) What Is A Hacker?ANDREI VNo ratings yet
- Database Security IssuesDocument53 pagesDatabase Security IssuesUMM-E-RUBABNo ratings yet
- 0478/12/M/J/15 © Ucles 2015Document6 pages0478/12/M/J/15 © Ucles 2015Panashe ChitakunyeNo ratings yet
- Questions From Chapter 8Document4 pagesQuestions From Chapter 8Syeda Wahida SabrinaNo ratings yet
- 1.2.3 Internet Principles of Operation 22Document14 pages1.2.3 Internet Principles of Operation 22Riaz KhanNo ratings yet
- AHMED HASSAN - Computer Science Week 4 H.W June 22 TH Till 26th JuneDocument3 pagesAHMED HASSAN - Computer Science Week 4 H.W June 22 TH Till 26th JuneAhmed HassanNo ratings yet
- Safety and Security ANSWERSDocument3 pagesSafety and Security ANSWERSUmm ArafaNo ratings yet
- Ut 2 SolutionDocument13 pagesUt 2 SolutionIF21 Minit ChitrodaNo ratings yet
- TLE 10-4Q - Week 3-4Document7 pagesTLE 10-4Q - Week 3-4Kevin AlibongNo ratings yet
- Top 50 Cyber Security Interview Questions and Answers 2022Document15 pagesTop 50 Cyber Security Interview Questions and Answers 2022Anirban deyNo ratings yet
- CSS L-1Document5 pagesCSS L-1Utkarsh Singh MagarauthiyaNo ratings yet
- (539.92KB) Handout Chapter-8Document3 pages(539.92KB) Handout Chapter-8kalroskalokNo ratings yet
- Grade 9 Notes Printed - 15 - 2010 - Data Security - To Print 2210Document6 pagesGrade 9 Notes Printed - 15 - 2010 - Data Security - To Print 2210hltNo ratings yet
- CLASS 9TH - (CHAP 7 Cyber Safety)Document4 pagesCLASS 9TH - (CHAP 7 Cyber Safety)Nischith VkNo ratings yet
- Soal Kuis Sequrity - ClarissaDocument9 pagesSoal Kuis Sequrity - ClarissaAmiliya AfriyaNo ratings yet
- Chapter 5 IGCSE COMP SCIDocument4 pagesChapter 5 IGCSE COMP SCIigcse8230No ratings yet
- Security Issues Unit 2Document10 pagesSecurity Issues Unit 2Richa GargNo ratings yet
- Welcome To International Journal of Engineering Research and Development (IJERD)Document5 pagesWelcome To International Journal of Engineering Research and Development (IJERD)IJERDNo ratings yet
- Section 1: Basic Introduction To Cyber Security and Information SecurityDocument5 pagesSection 1: Basic Introduction To Cyber Security and Information SecuritynadaNo ratings yet
- A N Tcybersecurity Awareness Jul 23Document19 pagesA N Tcybersecurity Awareness Jul 23Subramanian RamakrishnanNo ratings yet
- Computer System Security: 1-1 W (CC-Sem-3 & 4)Document155 pagesComputer System Security: 1-1 W (CC-Sem-3 & 4)श्री KrishnaNo ratings yet
- Activity 2: Lozano, Mary Dyan I. Bsit 4Document6 pagesActivity 2: Lozano, Mary Dyan I. Bsit 4Lozano RegieNo ratings yet
- MAWE1Document6 pagesMAWE1mukeshNo ratings yet
- Computer System Security (KNC 301) : Ver. No.: 1.1Document20 pagesComputer System Security (KNC 301) : Ver. No.: 1.1Ansh AroraNo ratings yet
- Chapter 8 - Security and Ethics - Computer Science IGCSEDocument7 pagesChapter 8 - Security and Ethics - Computer Science IGCSEAleck PhiriNo ratings yet
- Fundamentals of ProgrammingDocument7 pagesFundamentals of Programmingcharlene.dilig.mnlNo ratings yet
- CIT 315 Tutorial QuestionsDocument5 pagesCIT 315 Tutorial QuestionsArriana Blake100% (1)
- VIDEO DISCUSSION 18 Virtual Infrastructure Security & Risks Lesson 5 Part 2Document8 pagesVIDEO DISCUSSION 18 Virtual Infrastructure Security & Risks Lesson 5 Part 2Yo Han SongNo ratings yet
- Bbit 443Document3 pagesBbit 443Kiki KymsNo ratings yet
- 1.2.2. Computer ScienceDocument5 pages1.2.2. Computer ScienceMaria ZotovaNo ratings yet
- Unit 6: Network Security and Public Key Infrastructure: Saujanya Raj Shrestha 017BSCIT041Document31 pagesUnit 6: Network Security and Public Key Infrastructure: Saujanya Raj Shrestha 017BSCIT041Saujanya ShresthaNo ratings yet
- Chapter 7b Networking & Distributed Security Spring04 Victor SawmaDocument29 pagesChapter 7b Networking & Distributed Security Spring04 Victor Sawmazeinabibrahim592No ratings yet
- Measures To Secure Existing College NetworkDocument8 pagesMeasures To Secure Existing College NetworkkunjanpbharadeNo ratings yet
- 2022 Network SecurityFinal AssessmentDocument6 pages2022 Network SecurityFinal AssessmentMd. Ziaul Haque ShiponNo ratings yet
- Cyber Security TheoryDocument5 pagesCyber Security TheoryYashNo ratings yet
- Ciso2 0Document6 pagesCiso2 0PolisettyGupthaNo ratings yet
- Cloud Data Storage Security Enhancement Using Identity Based EncryptionDocument6 pagesCloud Data Storage Security Enhancement Using Identity Based EncryptionInternational Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- Mid-I Questions and AnswersDocument11 pagesMid-I Questions and Answersksaipraneeth1103No ratings yet
- Section Quiz CH 1 - CH 14Document494 pagesSection Quiz CH 1 - CH 14Christopher L OwobuNo ratings yet
- The Internet Homework 3Document3 pagesThe Internet Homework 3patrickv352No ratings yet
- U5 AQ5 With AnswersDocument14 pagesU5 AQ5 With Answersshubh agrawalNo ratings yet
- Information SecurityDocument51 pagesInformation Securityk leeNo ratings yet
- Cia Part 3 - Study Unit 11 IT Security and Application Development Core ConceptsDocument3 pagesCia Part 3 - Study Unit 11 IT Security and Application Development Core ConceptsfloricelfloricelNo ratings yet
- DatasecurityDocument5 pagesDatasecurityowuor PeterNo ratings yet
- Net SecDocument18 pagesNet SecNavier ClementineNo ratings yet
- 2.3 Cloud SecurityDocument34 pages2.3 Cloud SecurityTanjul SaratheNo ratings yet
- Resource 20231229205405 Unit 4 Web App and SecurityDocument5 pagesResource 20231229205405 Unit 4 Web App and Securitywiseclass69No ratings yet
- International Journal of Appligcation or PDFDocument6 pagesInternational Journal of Appligcation or PDFibrahim1No ratings yet
- Information Security and Cypersecurity-2Document27 pagesInformation Security and Cypersecurity-2donweenaNo ratings yet
- InternetandsecuritypaperDocument7 pagesInternetandsecuritypapermagesh parthasarathyNo ratings yet
- Sri Vidya College of Engineering & TechnologyDocument5 pagesSri Vidya College of Engineering & TechnologyAbhishemNo ratings yet
- OS Challanges and SecurityDocument5 pagesOS Challanges and SecuritymuhammadNo ratings yet
- Bit324 Bit-029-920Document33 pagesBit324 Bit-029-920Muktar MuhammadNo ratings yet
- E Commerce 10Document65 pagesE Commerce 10premaNo ratings yet
- ENGG1003 05 InformationSecurityDataPrivacy 副本Document55 pagesENGG1003 05 InformationSecurityDataPrivacy 副本fangwenxi05No ratings yet
- Cyber Security !Document3 pagesCyber Security !kavya keerthiNo ratings yet
- Solutions To Computer Security ThreatsDocument8 pagesSolutions To Computer Security ThreatsJeetamitra NayakNo ratings yet
- Chapter 4 Network SecurityDocument10 pagesChapter 4 Network SecurityalextawekeNo ratings yet
- ITE6 Instructor Materials Chapter12Document23 pagesITE6 Instructor Materials Chapter12bantayehu abebawuNo ratings yet
- Security Threats To E-Commerce-Requirements DefinitionDocument8 pagesSecurity Threats To E-Commerce-Requirements Definitioncap2010No ratings yet
- CNS Unit 3Document38 pagesCNS Unit 3bhavana16686No ratings yet
- Philippines As A Threat For Cyber AttacksDocument1 pagePhilippines As A Threat For Cyber AttacksPaolo CasungcadNo ratings yet
- Virus Port MikrotikDocument2 pagesVirus Port MikrotikMaulana KurniantoroNo ratings yet
- Intrusion Detection SystemDocument16 pagesIntrusion Detection Systemravidanny23No ratings yet
- CCSP Dump5 PDFDocument6 pagesCCSP Dump5 PDFkumar dharm50% (2)
- PAM DocumentationDocument8 pagesPAM DocumentationsidNo ratings yet
- ISO 27001 ControlsDocument20 pagesISO 27001 ControlsNarasimha Rao AkundiNo ratings yet
- File Password Is 44556677Document1 pageFile Password Is 44556677EMMANUEL TV INDIANo ratings yet
- Chapter - 5 Network SecurityDocument36 pagesChapter - 5 Network SecuritySuman BhandariNo ratings yet
- Project Synopsis: (An Autonomous Institution Affiliated To VTU, Accredited With NAAC A' Grade)Document2 pagesProject Synopsis: (An Autonomous Institution Affiliated To VTU, Accredited With NAAC A' Grade)Nehal Sharan ChanduNo ratings yet
- PCVL Brgy 1207004Document20 pagesPCVL Brgy 1207004Yes Tirol DumaganNo ratings yet
- Client: (Deleted For Confidentiality) Project: Information Security and Encryption QuestionsDocument5 pagesClient: (Deleted For Confidentiality) Project: Information Security and Encryption QuestionsShruti Edlabadkar SandheNo ratings yet
- TUTANESCU I-Anatomy and Types of Attacks Against Computer .Document6 pagesTUTANESCU I-Anatomy and Types of Attacks Against Computer .Jalal BhayoNo ratings yet
- Network Security Class NotesDocument43 pagesNetwork Security Class Notess200849298No ratings yet
- Performance of Barangay Police Security Officers: Developing InterventionsDocument8 pagesPerformance of Barangay Police Security Officers: Developing InterventionsPrime DzaiNo ratings yet
- Overview of Cyber Security-IJRASETDocument6 pagesOverview of Cyber Security-IJRASETIJRASETPublicationsNo ratings yet
- Wa0000.Document1 pageWa0000.limamot12No ratings yet
- Cryptography by Mr. Agbor AndersonDocument5 pagesCryptography by Mr. Agbor AndersonmrickNo ratings yet
- Cryptography 10Document38 pagesCryptography 10api-3774860No ratings yet
- P2PE v2.0 r1.2 Component P-ROV TemplateDocument254 pagesP2PE v2.0 r1.2 Component P-ROV Templatenv546878No ratings yet
- Cybersecurity InfographicsDocument7 pagesCybersecurity InfographicsSamarth KumarNo ratings yet
- SHA256 (Secure Hash Algorithm)Document12 pagesSHA256 (Secure Hash Algorithm)sri harshaphaniNo ratings yet
- Hacking 3 Books in 1 A Beginners Guide For Hackers (How To Hack Websites, Smartphones, Wireless Networks) + Linux Basic For... (Julian James McKinnon) - English (Z-Library)Document432 pagesHacking 3 Books in 1 A Beginners Guide For Hackers (How To Hack Websites, Smartphones, Wireless Networks) + Linux Basic For... (Julian James McKinnon) - English (Z-Library)Hello100% (3)
- MandaVax Privacy NoticeDocument3 pagesMandaVax Privacy NoticeAlgebric sepnio bayonaNo ratings yet
- 15A05702 Information SecurityDocument1 page15A05702 Information SecurityBilal AhmedNo ratings yet
- Cyber SecurityDocument17 pagesCyber SecurityanjulNo ratings yet
- B2B Vs B2C: 2. Discuss About Public & Private Key EncryptionsDocument4 pagesB2B Vs B2C: 2. Discuss About Public & Private Key EncryptionsAnonymous K0ZhcHT2iuNo ratings yet
- The European Commission Authentication System (ECAS)Document18 pagesThe European Commission Authentication System (ECAS)mgafeinNo ratings yet
- Xerox Workcentre 5225 - NVRAM PDFDocument1 pageXerox Workcentre 5225 - NVRAM PDFkarl_frederick100% (1)
IGCSE Security
IGCSE Security
Uploaded by
Caroline Muvirimi0 ratings0% found this document useful (0 votes)
59 views3 pages1. The document provides instructions for answering questions about data security and ethics. It asks to define different types of internet security threats like viruses, phishing, and pharming.
2. Questions are asked to match security issues like pharming, phishing, and viruses to their definitions. Terms related to data security are also defined, including hacking, spyware, cookies, encryption, secure socket layer, proxy server, and denial of service attacks.
3. The document asks how tools like secure socket layer and firewalls can keep data safe during transmission and storage, and what additional security measures a company should take to protect customer data stored on its computer systems.
Original Description:
Copyright
© © All Rights Reserved
Available Formats
PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this Document1. The document provides instructions for answering questions about data security and ethics. It asks to define different types of internet security threats like viruses, phishing, and pharming.
2. Questions are asked to match security issues like pharming, phishing, and viruses to their definitions. Terms related to data security are also defined, including hacking, spyware, cookies, encryption, secure socket layer, proxy server, and denial of service attacks.
3. The document asks how tools like secure socket layer and firewalls can keep data safe during transmission and storage, and what additional security measures a company should take to protect customer data stored on its computer systems.
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
Download as pdf or txt
0 ratings0% found this document useful (0 votes)
59 views3 pagesIGCSE Security
IGCSE Security
Uploaded by
Caroline Muvirimi1. The document provides instructions for answering questions about data security and ethics. It asks to define different types of internet security threats like viruses, phishing, and pharming.
2. Questions are asked to match security issues like pharming, phishing, and viruses to their definitions. Terms related to data security are also defined, including hacking, spyware, cookies, encryption, secure socket layer, proxy server, and denial of service attacks.
3. The document asks how tools like secure socket layer and firewalls can keep data safe during transmission and storage, and what additional security measures a company should take to protect customer data stored on its computer systems.
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
Download as pdf or txt
You are on page 1of 3
Friday 28 May 2021
Security and Ethics: Security
Instructions
Write your answers in complete sentences
Highlight the answer
Write neatly and legibly
1. Data is valuable. It needs to be kept secure and can easily be
damaged. Give three different ways that data can be easily
damaged. [3]
2. Viruses, Phishing and Pharming are examples of internet security
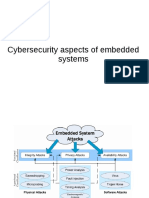
issues. Explain what is meant by each of these three terms. [6]
3. Six security issues and six descriptions are shown below. Link each
security issue to the correct description
Security Issue Description
a. Pharming illegal access to a computer system without
the owner’s consent or knowledge.
b. Phishing software that gathers information by
monitoring key presses on a user’s
keyboard, the data is sent back to the
originator of the software.
c. Viruses malicious code installed on the hard drive
of a user’s computer or on a web server,
this code will re-direct the user to a fake
website without the user’s knowledge.
d. Hacking creator of code sends out a legitimate-
looking email in the hope of gathering
personal and financial information from the
recipient; it requires the user to click on the
link in the email or attachment.
e. Spyware a message given to a web browser by a web
server, it is stored in a text file; the message
is then sent back to the server each time a
browser requests a page from the server.
f. Cookies program or code that replicates itself,
designed to amend, delete or copy data or
files on a user’s computer; often causes the
computer to crash or run slowly.
g. Encryption computer that acts as an intermediary
between a web browser and the internet.
h. Secure Socket Layer scrambles data for secure transmission.
i. Proxy Server provides a secure connection between web
browsers and websites allowing secure
transmission of private data. [9]
4. Explain what is meant by a denial of service attack. [2]
5. a) Data is transmitted between offices over the Internet. In order to
keep the data safe the company is using Secure Socket Layer (SSL)
protocol and a firewall at each office.
Explain how SSL protocol and a firewall keep the company’s data
safe. [4]
b) A company stores personal details of its customers on a computer
system behind a firewall. Explain with reasons, what else the company
should do to keep this data safe. [6]
Total: 30 Marks
You might also like
- CEH: Certified Ethical Hacker v11 : Exam Cram Notes - First Edition - 2021From EverandCEH: Certified Ethical Hacker v11 : Exam Cram Notes - First Edition - 2021No ratings yet
- A) What Is A Hacker?Document2 pagesA) What Is A Hacker?ANDREI VNo ratings yet
- Database Security IssuesDocument53 pagesDatabase Security IssuesUMM-E-RUBABNo ratings yet
- 0478/12/M/J/15 © Ucles 2015Document6 pages0478/12/M/J/15 © Ucles 2015Panashe ChitakunyeNo ratings yet
- Questions From Chapter 8Document4 pagesQuestions From Chapter 8Syeda Wahida SabrinaNo ratings yet
- 1.2.3 Internet Principles of Operation 22Document14 pages1.2.3 Internet Principles of Operation 22Riaz KhanNo ratings yet
- AHMED HASSAN - Computer Science Week 4 H.W June 22 TH Till 26th JuneDocument3 pagesAHMED HASSAN - Computer Science Week 4 H.W June 22 TH Till 26th JuneAhmed HassanNo ratings yet
- Safety and Security ANSWERSDocument3 pagesSafety and Security ANSWERSUmm ArafaNo ratings yet
- Ut 2 SolutionDocument13 pagesUt 2 SolutionIF21 Minit ChitrodaNo ratings yet
- TLE 10-4Q - Week 3-4Document7 pagesTLE 10-4Q - Week 3-4Kevin AlibongNo ratings yet
- Top 50 Cyber Security Interview Questions and Answers 2022Document15 pagesTop 50 Cyber Security Interview Questions and Answers 2022Anirban deyNo ratings yet
- CSS L-1Document5 pagesCSS L-1Utkarsh Singh MagarauthiyaNo ratings yet
- (539.92KB) Handout Chapter-8Document3 pages(539.92KB) Handout Chapter-8kalroskalokNo ratings yet
- Grade 9 Notes Printed - 15 - 2010 - Data Security - To Print 2210Document6 pagesGrade 9 Notes Printed - 15 - 2010 - Data Security - To Print 2210hltNo ratings yet
- CLASS 9TH - (CHAP 7 Cyber Safety)Document4 pagesCLASS 9TH - (CHAP 7 Cyber Safety)Nischith VkNo ratings yet
- Soal Kuis Sequrity - ClarissaDocument9 pagesSoal Kuis Sequrity - ClarissaAmiliya AfriyaNo ratings yet
- Chapter 5 IGCSE COMP SCIDocument4 pagesChapter 5 IGCSE COMP SCIigcse8230No ratings yet
- Security Issues Unit 2Document10 pagesSecurity Issues Unit 2Richa GargNo ratings yet
- Welcome To International Journal of Engineering Research and Development (IJERD)Document5 pagesWelcome To International Journal of Engineering Research and Development (IJERD)IJERDNo ratings yet
- Section 1: Basic Introduction To Cyber Security and Information SecurityDocument5 pagesSection 1: Basic Introduction To Cyber Security and Information SecuritynadaNo ratings yet
- A N Tcybersecurity Awareness Jul 23Document19 pagesA N Tcybersecurity Awareness Jul 23Subramanian RamakrishnanNo ratings yet
- Computer System Security: 1-1 W (CC-Sem-3 & 4)Document155 pagesComputer System Security: 1-1 W (CC-Sem-3 & 4)श्री KrishnaNo ratings yet
- Activity 2: Lozano, Mary Dyan I. Bsit 4Document6 pagesActivity 2: Lozano, Mary Dyan I. Bsit 4Lozano RegieNo ratings yet
- MAWE1Document6 pagesMAWE1mukeshNo ratings yet
- Computer System Security (KNC 301) : Ver. No.: 1.1Document20 pagesComputer System Security (KNC 301) : Ver. No.: 1.1Ansh AroraNo ratings yet
- Chapter 8 - Security and Ethics - Computer Science IGCSEDocument7 pagesChapter 8 - Security and Ethics - Computer Science IGCSEAleck PhiriNo ratings yet
- Fundamentals of ProgrammingDocument7 pagesFundamentals of Programmingcharlene.dilig.mnlNo ratings yet
- CIT 315 Tutorial QuestionsDocument5 pagesCIT 315 Tutorial QuestionsArriana Blake100% (1)
- VIDEO DISCUSSION 18 Virtual Infrastructure Security & Risks Lesson 5 Part 2Document8 pagesVIDEO DISCUSSION 18 Virtual Infrastructure Security & Risks Lesson 5 Part 2Yo Han SongNo ratings yet
- Bbit 443Document3 pagesBbit 443Kiki KymsNo ratings yet
- 1.2.2. Computer ScienceDocument5 pages1.2.2. Computer ScienceMaria ZotovaNo ratings yet
- Unit 6: Network Security and Public Key Infrastructure: Saujanya Raj Shrestha 017BSCIT041Document31 pagesUnit 6: Network Security and Public Key Infrastructure: Saujanya Raj Shrestha 017BSCIT041Saujanya ShresthaNo ratings yet
- Chapter 7b Networking & Distributed Security Spring04 Victor SawmaDocument29 pagesChapter 7b Networking & Distributed Security Spring04 Victor Sawmazeinabibrahim592No ratings yet
- Measures To Secure Existing College NetworkDocument8 pagesMeasures To Secure Existing College NetworkkunjanpbharadeNo ratings yet
- 2022 Network SecurityFinal AssessmentDocument6 pages2022 Network SecurityFinal AssessmentMd. Ziaul Haque ShiponNo ratings yet
- Cyber Security TheoryDocument5 pagesCyber Security TheoryYashNo ratings yet
- Ciso2 0Document6 pagesCiso2 0PolisettyGupthaNo ratings yet
- Cloud Data Storage Security Enhancement Using Identity Based EncryptionDocument6 pagesCloud Data Storage Security Enhancement Using Identity Based EncryptionInternational Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- Mid-I Questions and AnswersDocument11 pagesMid-I Questions and Answersksaipraneeth1103No ratings yet
- Section Quiz CH 1 - CH 14Document494 pagesSection Quiz CH 1 - CH 14Christopher L OwobuNo ratings yet
- The Internet Homework 3Document3 pagesThe Internet Homework 3patrickv352No ratings yet
- U5 AQ5 With AnswersDocument14 pagesU5 AQ5 With Answersshubh agrawalNo ratings yet
- Information SecurityDocument51 pagesInformation Securityk leeNo ratings yet
- Cia Part 3 - Study Unit 11 IT Security and Application Development Core ConceptsDocument3 pagesCia Part 3 - Study Unit 11 IT Security and Application Development Core ConceptsfloricelfloricelNo ratings yet
- DatasecurityDocument5 pagesDatasecurityowuor PeterNo ratings yet
- Net SecDocument18 pagesNet SecNavier ClementineNo ratings yet
- 2.3 Cloud SecurityDocument34 pages2.3 Cloud SecurityTanjul SaratheNo ratings yet
- Resource 20231229205405 Unit 4 Web App and SecurityDocument5 pagesResource 20231229205405 Unit 4 Web App and Securitywiseclass69No ratings yet
- International Journal of Appligcation or PDFDocument6 pagesInternational Journal of Appligcation or PDFibrahim1No ratings yet
- Information Security and Cypersecurity-2Document27 pagesInformation Security and Cypersecurity-2donweenaNo ratings yet
- InternetandsecuritypaperDocument7 pagesInternetandsecuritypapermagesh parthasarathyNo ratings yet
- Sri Vidya College of Engineering & TechnologyDocument5 pagesSri Vidya College of Engineering & TechnologyAbhishemNo ratings yet
- OS Challanges and SecurityDocument5 pagesOS Challanges and SecuritymuhammadNo ratings yet
- Bit324 Bit-029-920Document33 pagesBit324 Bit-029-920Muktar MuhammadNo ratings yet
- E Commerce 10Document65 pagesE Commerce 10premaNo ratings yet
- ENGG1003 05 InformationSecurityDataPrivacy 副本Document55 pagesENGG1003 05 InformationSecurityDataPrivacy 副本fangwenxi05No ratings yet
- Cyber Security !Document3 pagesCyber Security !kavya keerthiNo ratings yet
- Solutions To Computer Security ThreatsDocument8 pagesSolutions To Computer Security ThreatsJeetamitra NayakNo ratings yet
- Chapter 4 Network SecurityDocument10 pagesChapter 4 Network SecurityalextawekeNo ratings yet
- ITE6 Instructor Materials Chapter12Document23 pagesITE6 Instructor Materials Chapter12bantayehu abebawuNo ratings yet
- Security Threats To E-Commerce-Requirements DefinitionDocument8 pagesSecurity Threats To E-Commerce-Requirements Definitioncap2010No ratings yet
- CNS Unit 3Document38 pagesCNS Unit 3bhavana16686No ratings yet
- Philippines As A Threat For Cyber AttacksDocument1 pagePhilippines As A Threat For Cyber AttacksPaolo CasungcadNo ratings yet
- Virus Port MikrotikDocument2 pagesVirus Port MikrotikMaulana KurniantoroNo ratings yet
- Intrusion Detection SystemDocument16 pagesIntrusion Detection Systemravidanny23No ratings yet
- CCSP Dump5 PDFDocument6 pagesCCSP Dump5 PDFkumar dharm50% (2)
- PAM DocumentationDocument8 pagesPAM DocumentationsidNo ratings yet
- ISO 27001 ControlsDocument20 pagesISO 27001 ControlsNarasimha Rao AkundiNo ratings yet
- File Password Is 44556677Document1 pageFile Password Is 44556677EMMANUEL TV INDIANo ratings yet
- Chapter - 5 Network SecurityDocument36 pagesChapter - 5 Network SecuritySuman BhandariNo ratings yet
- Project Synopsis: (An Autonomous Institution Affiliated To VTU, Accredited With NAAC A' Grade)Document2 pagesProject Synopsis: (An Autonomous Institution Affiliated To VTU, Accredited With NAAC A' Grade)Nehal Sharan ChanduNo ratings yet
- PCVL Brgy 1207004Document20 pagesPCVL Brgy 1207004Yes Tirol DumaganNo ratings yet
- Client: (Deleted For Confidentiality) Project: Information Security and Encryption QuestionsDocument5 pagesClient: (Deleted For Confidentiality) Project: Information Security and Encryption QuestionsShruti Edlabadkar SandheNo ratings yet
- TUTANESCU I-Anatomy and Types of Attacks Against Computer .Document6 pagesTUTANESCU I-Anatomy and Types of Attacks Against Computer .Jalal BhayoNo ratings yet
- Network Security Class NotesDocument43 pagesNetwork Security Class Notess200849298No ratings yet
- Performance of Barangay Police Security Officers: Developing InterventionsDocument8 pagesPerformance of Barangay Police Security Officers: Developing InterventionsPrime DzaiNo ratings yet
- Overview of Cyber Security-IJRASETDocument6 pagesOverview of Cyber Security-IJRASETIJRASETPublicationsNo ratings yet
- Wa0000.Document1 pageWa0000.limamot12No ratings yet
- Cryptography by Mr. Agbor AndersonDocument5 pagesCryptography by Mr. Agbor AndersonmrickNo ratings yet
- Cryptography 10Document38 pagesCryptography 10api-3774860No ratings yet
- P2PE v2.0 r1.2 Component P-ROV TemplateDocument254 pagesP2PE v2.0 r1.2 Component P-ROV Templatenv546878No ratings yet
- Cybersecurity InfographicsDocument7 pagesCybersecurity InfographicsSamarth KumarNo ratings yet
- SHA256 (Secure Hash Algorithm)Document12 pagesSHA256 (Secure Hash Algorithm)sri harshaphaniNo ratings yet
- Hacking 3 Books in 1 A Beginners Guide For Hackers (How To Hack Websites, Smartphones, Wireless Networks) + Linux Basic For... (Julian James McKinnon) - English (Z-Library)Document432 pagesHacking 3 Books in 1 A Beginners Guide For Hackers (How To Hack Websites, Smartphones, Wireless Networks) + Linux Basic For... (Julian James McKinnon) - English (Z-Library)Hello100% (3)
- MandaVax Privacy NoticeDocument3 pagesMandaVax Privacy NoticeAlgebric sepnio bayonaNo ratings yet
- 15A05702 Information SecurityDocument1 page15A05702 Information SecurityBilal AhmedNo ratings yet
- Cyber SecurityDocument17 pagesCyber SecurityanjulNo ratings yet
- B2B Vs B2C: 2. Discuss About Public & Private Key EncryptionsDocument4 pagesB2B Vs B2C: 2. Discuss About Public & Private Key EncryptionsAnonymous K0ZhcHT2iuNo ratings yet
- The European Commission Authentication System (ECAS)Document18 pagesThe European Commission Authentication System (ECAS)mgafeinNo ratings yet
- Xerox Workcentre 5225 - NVRAM PDFDocument1 pageXerox Workcentre 5225 - NVRAM PDFkarl_frederick100% (1)