Professional Documents
Culture Documents
Hill Cipher
Hill Cipher
Uploaded by
Sarathbabu ROriginal Description:
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Hill Cipher
Hill Cipher
Uploaded by
Sarathbabu RCopyright:
Available Formats
Ex.
No : 1(b) Date :
Hill Cipher
AIM: To implement a program to encrypt and decrypt using the Hill cipher substitution technique
ALGORITHM: 1. In the Hill cipher Each letter is represented by a number modulo 26. 2. To encrypt a
message, each block of n letters is multiplied by an invertible n x n matrix, again modulus 26. 3. To
decrypt the message, each block is multiplied by the inverse of the matrix used for encryption. 4. The
matrix used for encryption is the cipher key, and it should be chosen randomly from the set of
invertible n × n matrices (modulo 26). 5. The cipher can, be adapted to an alphabet with any number
of letters. 6. All arithmetic just needs to be done modulo the number of letters instead of modulo 26.
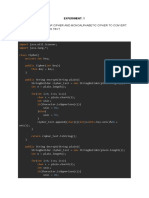
PROGRAM: HillCipher.java class hillCipher { /* 3x3 key matrix for 3 characters at once */ public
static int[][] keymat = new int[][] { { 1, 2, 1 }, { 2, 3, 2 }, { 2, 2, 1 } }; /* key inverse matrix */
public static int[][] invkeymat = new int[][] { { -1, 0, 1 }, { 2, -1, 0 }, { -2, 2, -1 } }; public static String
key = "ABCDEFGHIJKLMNOPQRSTUVWXYZ";
private static String encode(char a, char b, char c) { String ret = ""; int x, y, z; int posa
= (int) a - 65; int posb = (int) b - 65; int posc = (int) c - 65; x = posa * keymat[0][0] + posb
* keymat[1][0] + posc * keymat[2][0]; y = posa * keymat[0][1] + posb * keymat[1][1] + posc *
keymat[2][1]; z = posa * keymat[0][2] + posb * keymat[1][2] + posc * keymat[2][2]; a=
key.charAt(x % 26); b = key.charAt(y % 26);
c = key.charAt(z % 26); ret = "" + a + b + c; return ret; }
private static String decode(char a, char b, char c) { String ret = ""; int x, y, z; int posa
= (int) a - 65; int posb = (int) b - 65; int posc = (int) c - 65; x = posa * invkeymat[0][0] +
posb * invkeymat[1][0] + posc * invkeymat[2][0]; y = posa * invkeymat[0][1] + posb *
invkeymat[1][1] + posc * invkeymat[2][1]; z = posa * invkeymat[0][2] + posb * invkeymat[1][2] +
posc * invkeymat[2][2]; a = key.charAt((x % 26 < 0) ? (26 + x % 26) : (x % 26));
b = key.charAt((y % 26 < 0) ? (26 + y % 26) : (y % 26)); c = key.charAt((z % 26 < 0) ? (26 + z %
26) : (z % 26)); ret = "" + a + b + c; return ret; }
public static void main(String[] args) throws java.lang.Exception { String msg; String enc =
""; String dec = ""; int n; msg = ("SecurityLaboratory");
System.out.println("simulation of Hill Cipher\n-------------------------"); System.out.println("Input
message : " + msg); msg = msg.toUpperCase(); msg = msg.replaceAll("\\s", ""); /*
remove spaces */ n = msg.length() % 3; /* append padding text X */ if (n != 0) { for (int i =
1; i <= (3 - n); i++) { msg += 'X'; }
} System.out.println("padded message : " + msg); char[] pdchars = msg.toCharArray();
for (int i = 0; i < msg.length(); i += 3) { enc += encode(pdchars[i], pdchars[i + 1], pdchars[i + 2]);
} System.out.println("encoded message : " + enc); char[] dechars = enc.toCharArray();
for (int i = 0; i < enc.length(); i += 3) { dec += decode(dechars[i], dechars[i + 1], dechars[i + 2]);
} System.out.println("decoded message : " + dec); } }
OUTPUT: Simulating Hill Cipher ------------------------------- Input Message : SecurityLaboratory Padded
Message : SECURITYLABORATORY Encrypted Message : EACSDKLCAEFQDUKSXU Decrypted
Message : SECURITYLABORATORY
RESULT: Thus the program for hill cipher encryption and decryption algorithm has been
implemented and the output verified successfully.
You might also like
- Using Social Engineering Techniques To Plan An Attack (3e)Document9 pagesUsing Social Engineering Techniques To Plan An Attack (3e)Hamza BhattiNo ratings yet
- FREE ML ACCOUNTS 2021 p86 by Pycco GDocument9 pagesFREE ML ACCOUNTS 2021 p86 by Pycco GSykee Nozaki80% (5)
- Transposition CipherDocument4 pagesTransposition CipherDil Prasad Kunwar100% (1)
- Lab 02 - Data Security and ApplicationsDocument6 pagesLab 02 - Data Security and ApplicationsAmna AroojNo ratings yet
- EX - NO: 1C Date:: IT8761 LaboratoryDocument3 pagesEX - NO: 1C Date:: IT8761 LaboratoryPaper ArtNo ratings yet
- Cns Rec PitDocument60 pagesCns Rec PitShirly NNo ratings yet
- IT8761 Security Laboratory ManualDocument16 pagesIT8761 Security Laboratory Manualhemacsc2003No ratings yet
- IT8761 Security Laboratory Manual P and OPDocument54 pagesIT8761 Security Laboratory Manual P and OPshohiNo ratings yet
- IT8761 Security Laboratory ManualDocument50 pagesIT8761 Security Laboratory ManualsowrishalNo ratings yet
- Chandrakant HDocument33 pagesChandrakant HJayanth V 19CS045No ratings yet
- IT8761 - Security Lab RecordDocument90 pagesIT8761 - Security Lab Record20CS001 Abinaya S CSENo ratings yet
- Final Cns MergedDocument60 pagesFinal Cns MergedDeepan KumarNo ratings yet
- Knowledge Institute of Technology SALEM - 637504: Laboratory Manual FOR It8761 - Security LaboratoryDocument49 pagesKnowledge Institute of Technology SALEM - 637504: Laboratory Manual FOR It8761 - Security LaboratoryCHANDRU MNo ratings yet
- Lab Cat Crypto FinalDocument42 pagesLab Cat Crypto Finalgunjanbhartia2003No ratings yet
- Index 1Document20 pagesIndex 1tedcweNo ratings yet
- ISS Lab 3Document5 pagesISS Lab 3Ronaldo ONo ratings yet
- IT8761Document49 pagesIT8761sans mahe1No ratings yet
- Crypto RecordDocument47 pagesCrypto RecordKarthikeyan GovindarajNo ratings yet
- Lab Da1Document12 pagesLab Da1harish2646thebestNo ratings yet
- Hill CipherDocument3 pagesHill Cipherchime dolkarNo ratings yet
- Cyber Security Mid 2Document8 pagesCyber Security Mid 2Hemang agarwalNo ratings yet
- Sec Lab Lab Programs With Screen ShotsDocument51 pagesSec Lab Lab Programs With Screen Shotsrajkumar184No ratings yet
- Security LaboratoryDocument48 pagesSecurity LaboratorySurìyáNo ratings yet
- Lab Assessment - 1: Classical EncryptionDocument18 pagesLab Assessment - 1: Classical EncryptionASHNA CHOUDHARY 20BCI0158No ratings yet
- Cis Lab NotesDocument12 pagesCis Lab NotesKarthikeyan GovindarajNo ratings yet
- Network SecurityDocument5 pagesNetwork SecuritySubanandhini SNo ratings yet
- Security Lab PrintDocument38 pagesSecurity Lab PrintAni AnbuNo ratings yet
- Cryptography and Network Security Aat: SL. No. TopicsDocument14 pagesCryptography and Network Security Aat: SL. No. TopicsAyush JethwaniNo ratings yet
- Cns Lab FileDocument22 pagesCns Lab FilePrashant Kumar SinghNo ratings yet
- Assign1 & Assign 2Document23 pagesAssign1 & Assign 2najam iqbalNo ratings yet
- NTC FileDocument49 pagesNTC FileSOUMY PRAJAPATINo ratings yet
- NspractsDocument27 pagesNspractsapi-375436301No ratings yet
- EngineeringDocument18 pagesEngineeringNitya SunkaraNo ratings yet
- Twisha Twisha ChattopadhyayDocument39 pagesTwisha Twisha ChattopadhyayJatin Kumar GargNo ratings yet
- 21bci0056 VL2023240503640 Ast01Document17 pages21bci0056 VL2023240503640 Ast01Rajvardhan PatilNo ratings yet
- Encrypt and Decrypt Text File Using CDocument13 pagesEncrypt and Decrypt Text File Using CbilisummaaNo ratings yet
- Affine CiphersDocument6 pagesAffine CiphersDENI123No ratings yet
- MessageDocument3 pagesMessageAndrei ButNo ratings yet
- Ins Practical1-6Document43 pagesIns Practical1-6Vishal Brijesh kanojiyaNo ratings yet
- Security LabDocument49 pagesSecurity LabdanaNo ratings yet
- Print Lab 11 - AllDocument22 pagesPrint Lab 11 - AllLord GamerNo ratings yet
- Advanced Cryptography Lesson4Document48 pagesAdvanced Cryptography Lesson4rtyujkNo ratings yet
- CNS LabPrograms PDFDocument14 pagesCNS LabPrograms PDFBunnyNo ratings yet
- To PrintDocument54 pagesTo PrintAbhishek DograNo ratings yet
- Program No. 1: AIM: Write A C++ Program To Perform Encryption and Decryption Using TheDocument29 pagesProgram No. 1: AIM: Write A C++ Program To Perform Encryption and Decryption Using TheSagar MishraNo ratings yet
- Crypto Assignment 2Document9 pagesCrypto Assignment 2devNo ratings yet
- Information Security Lab Name-Tushar Parmar Class - Is - 13A Lab MST Submitted To - Tanu DhimanDocument3 pagesInformation Security Lab Name-Tushar Parmar Class - Is - 13A Lab MST Submitted To - Tanu DhimanWhite WolfNo ratings yet
- Cns Lab MainDocument27 pagesCns Lab MainPrakash RajNo ratings yet
- Write A Program To Implement Monoalphabetic Cipher AlgorithmDocument6 pagesWrite A Program To Implement Monoalphabetic Cipher AlgorithmPalak BansalNo ratings yet
- Play Fair CipherDocument51 pagesPlay Fair Ciphervaibhav.chaurasia2021No ratings yet
- Security Lab RecordDocument43 pagesSecurity Lab RecordkarthikNo ratings yet
- Cryptography Forouzan Code ImplementationDocument172 pagesCryptography Forouzan Code ImplementationAnubhav SahNo ratings yet
- Fundamental Graphics FunctionsDocument17 pagesFundamental Graphics Functionsశ్రీనివాస బాబ్జి జోస్యులNo ratings yet
- Ins FileDocument31 pagesIns Filekartikaysinghco20b446No ratings yet
- Crypto Da2Document11 pagesCrypto Da2Arun SrNo ratings yet
- C&NS Lab ManualDocument26 pagesC&NS Lab ManualtexxasNo ratings yet
- Eces Experiment - 1Document4 pagesEces Experiment - 1JaimishNo ratings yet
- Ex - No:2a: DES Date:17.9.20 AimDocument17 pagesEx - No:2a: DES Date:17.9.20 AimPratheep DspNo ratings yet
- Advanced C Concepts and Programming: First EditionFrom EverandAdvanced C Concepts and Programming: First EditionRating: 3 out of 5 stars3/5 (1)
- Configuring AAA Servers and The Local DatabaseDocument22 pagesConfiguring AAA Servers and The Local DatabaseTarun TiwariNo ratings yet
- T PZ 1670410340 Escape Room The Enigma Puzzle - Ver - 2Document21 pagesT PZ 1670410340 Escape Room The Enigma Puzzle - Ver - 2andres perezNo ratings yet
- IT ACT 2000: Scope, Impacts and Amendments: Aastha Bhardwaj, Ms Priyanka GuptaDocument5 pagesIT ACT 2000: Scope, Impacts and Amendments: Aastha Bhardwaj, Ms Priyanka GuptaasheangeNo ratings yet
- By Dr. Rana AljanabiDocument31 pagesBy Dr. Rana AljanabigamerNo ratings yet
- Mobile Device Security: Somesh Sawhney Sales Director - META & India Rohit Sinha Technical Director - META & IndiaDocument15 pagesMobile Device Security: Somesh Sawhney Sales Director - META & India Rohit Sinha Technical Director - META & IndiaKaran OjhaNo ratings yet
- Licencias by Flako 02.08.2020Document3 pagesLicencias by Flako 02.08.2020antonio cruz jimenezNo ratings yet
- Readme!Document5 pagesReadme!Jovin CoolNo ratings yet
- SAP Single Sign-On Und Secure Connections Via SNC Adapter Basierend Auf Kerberosv5 enDocument14 pagesSAP Single Sign-On Und Secure Connections Via SNC Adapter Basierend Auf Kerberosv5 enabhisheksapbiNo ratings yet
- Worksheet 01: Software LAN Wi-Fi Attachments Virus Worm Resolves AntiDocument7 pagesWorksheet 01: Software LAN Wi-Fi Attachments Virus Worm Resolves AntiAisha AnwarNo ratings yet
- Internet and Cyber Security PresentationDocument13 pagesInternet and Cyber Security PresentationNihariNo ratings yet
- Data Encryption Standard (Des)Document17 pagesData Encryption Standard (Des)DuttaUdayaVenkataChegondiNo ratings yet
- Ahmad's CVDocument1 pageAhmad's CVAhmad ShreetehNo ratings yet
- RC4 PaperDocument6 pagesRC4 PaperTyler Manning-DahanNo ratings yet
- CN 4Document13 pagesCN 4Quan TranNo ratings yet
- Vision: Value Addition Material - 2018Document23 pagesVision: Value Addition Material - 2018ShivamNo ratings yet
- NPTEL CC Assignment 6Document4 pagesNPTEL CC Assignment 6Arun Kumar100% (2)
- 4 A Study of Encryption AlgorithmsDocument9 pages4 A Study of Encryption AlgorithmsVivekNo ratings yet
- PDF Piling LarangDocument11 pagesPDF Piling LarangSmurf SmurfNo ratings yet
- Honeypot System: An Intrusion Detection System: Mr. Ajinkya S. Gudadhe Prof. D. H. Deshmukh Prof. KalbandeDocument3 pagesHoneypot System: An Intrusion Detection System: Mr. Ajinkya S. Gudadhe Prof. D. H. Deshmukh Prof. KalbandeEditor IJRITCCNo ratings yet
- HP Unified Wired-WLAN Products Security Configuration GuideDocument465 pagesHP Unified Wired-WLAN Products Security Configuration Guidearora1984No ratings yet
- Linux701 800Document100 pagesLinux701 800sureshNo ratings yet
- Thayer Cyber Hacking in Southeast Asia BibliographyDocument2 pagesThayer Cyber Hacking in Southeast Asia BibliographyCarlyle Alan ThayerNo ratings yet
- The Evolving Role of The CISODocument6 pagesThe Evolving Role of The CISOThilakPathirageNo ratings yet
- Cryptography Lab Manual-FinalDocument36 pagesCryptography Lab Manual-FinalPraveen TPNo ratings yet
- Secure Software: Confidentiality Integrity Data SecurityDocument8 pagesSecure Software: Confidentiality Integrity Data SecurityAbhinav DakshaNo ratings yet
- Topic 1.1 - Introduction To Information and Communication TechnologyDocument36 pagesTopic 1.1 - Introduction To Information and Communication TechnologyIbnu Tuan Hj DaudNo ratings yet
- FuzzingBluetooth Paul ShenDocument8 pagesFuzzingBluetooth Paul Shen许昆No ratings yet
- Madhuri ResumeDocument2 pagesMadhuri ResumeshahkeelNo ratings yet