Professional Documents
Culture Documents
AIWAF - Solution Brief - EN
AIWAF - Solution Brief - EN
Uploaded by
Paul RubberOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
AIWAF - Solution Brief - EN
AIWAF - Solution Brief - EN
Uploaded by
Paul RubberCopyright:
Available Formats
Intelligent Web Application Firewall
WAF
2020.11. VER 5.0
Contents
1. Need for WEB Security
2. WAF INTRODUCTION
3. WAF FEATURES
4. Configuration Methods & Case Studies
1. Need for WEB Security
1. Need for web security
Changes in IT Environment
IT Environment Increased Value of Information as an Asset
• Smart devices, allowing individuals to bring work • Majority of web services require basic personal
wherever they go information
• Accessible and easy to use, central data and • Increase in data breach attacks
information are concentrated on the web • Brand image and financial loss in an event of a
• Increase in various web services such as finance, breach
shopping, and medical care
IT Compliance & Law Limitations of Existing Solutions
• Increased IT compliance needs • Ports for web services must be open at all times
• Need for ISMS certification • IPS is not capable of defending against SSL
communication (excessive system load when used)
• Strict personal information protection act
and does not provide detailed policy setting
• Need a powerful and professional solution for web
APPLICATION INSIGHT WAF | 4
1. Need for web security
Limitations of Existing Security System
■ Firewall/IPS v.s. Web Application Firewall
Firewall IPS Web Application Firewall
• Provides L3 – L7 Layer security
• Focus on protecting network • Insufficient ability to defend
• Expert-level security for HTTP
infrastructure against SSL communication
and HTTPS
• 80, and 443 ports are considered • Since it depends on the signature
Functions • Positive security model can
normal communications method, a large number of
block even unknown/less-
• Unable to control web protocol detour vulnerable sections occur
known attacks
(HTTP, HTTPS) • No detailed policy
implementation
APPLICATION INSIGHT WAF | 5
1. Need for web security
WAF Vs IPS / NG FW
Web Application Intrusion Prevention Next-Generation
Firewall System Firewall
Multiprotocol
Security
IP Reputation
Web Attack Signatures
Web Vulnerabilities
Signatures
Automatic
Policy Learning
URL, Parameter, Cookie,
And From Protection
Leverage Vulnerabilities
Scan Results
= good to very good = average on fair = below average
Source: Gartner
APPLICATION INSIGHT WAF | 6
1. Need for web security
Changes in Web Application
OWASP Top 10-2013 OWASP Top 10-2017
A1-Injection A1:2017-Injection
A2:2017-Broken Authentication and Session
A2-Broken Authentication and Session Management Management
A3-Cross-Site Scripting (XSS) A3:2017-Cross-Site Scripting (XSS)
A4-Insecure Direct Object References [Merged with A7] A4:2017-XML External Entity (XXE) [NEW]
A5-Security Misconfiguration A5:2017-Broken Access Control [Merged]
A6-Sensitive Data Exposure A6:2017-Security Misconfiguration
A7-Missing Function Level Access Control [Merged with A7:2017-Cross-site Scripting (XSS)
A4}
A8-Cross-site Request Forgery (CSRF) A8:2017-Insecure Deserialization [NEW, Community]
A9-Using Components with Known Vulnerabilities A9:2017-Using components with Known Vulnerabilities
A10-Unvalidated Redirects and Forwards A10:2017-Insufficient Logging & Monitoring[NEW,
Community]
Source : https://www.owasp.org
APPLICATION INSIGHT WAF | 7
1. Need for web security
Key Points
In order to provide services, web servers are always open to the public
Because of its vulnerability, 80% of hacking incidents happen on the web (or uses the web as an entry point)
Vulnerabilities within the source code are the problem and it takes an average of 100 days to solve even 50%
of the issues
Hackers find new vulnerabilities with new technologies and improved skills. Unresolved web security
vulnerabilities can cause serious information leakage as it has happened with SONY and AT&T
APPLICATION INSIGHT WAF | 8
2. WAF
INTRODUCTION
2. AIWAF Introduction
APPLICATION INSIGHT WAF Line-UP
Specification AIWAF-100_Y20 AIWAF-200_Y20 AIWAF-500_Y20 AIWAF-1000_Y20 AIWAF-2000_Y20 AIWAF-4000_Y20 AIWAF-8000_Y20
Appearance
RAM 4GB 8GB (최대 128GB) 16GB (최대 128GB) 32GB (최대 2TB) 32GB (최대 2TB) 64GB (최대 2TB) 64GB (최대 2TB)
HDD 500G 500G 500G 2TB 2TB 2TB 2TB
- Mgmt 1 UTP Port - Mgmt 1 UTP Port - Mgmt 1 UTP Port - Mgmt 1 UTP Port - Mgmt 1 UTP Port - Mgmt 1 UTP Port - Mgmt 1 UTP Port
MGMT / HA
- HA 1 UTP Port - HA 1 UTP Port - HA 1 UTP Port - HA 1 UTP Port - HA 1 UTP Port - HA 1 UTP Port - HA 1 UTP Port
Network
1G UTP * 2 1G UTP * 4 1G UTP * 4 - - - -
(Default)
Slot 1 Slot 1 8 Slot 8 Slot 8 Slot 8 Slot
Network
- - 1G UTP 4Port - 1G UTP 4Port - 1G UTP 4Port - 1G UTP 4Port - 1G UTP 4Port - 1G UTP 4Port
(Option)
- 1G Fiber 4Port - 1G Fiber 4Port - 1G Fiber 4Port - 1G Fiber 4Port - 1G Fiber 4Port - 1G Fiber 4Port
- 10G Fiber 2Port - 10G Fiber 2Port - 10G Fiber 2Port - 10G Fiber 2Port - 10G Fiber 2Port - 10G Fiber 2Port
CPS
5,000/1,500 30,000/10,000 55,000/15,000 130,000/35,000 200,000/50,000 250,000/70,000 350,000/100,000
HTTP / HTTPS
TPS
9,000/5,000 55,000/35,000 80,000/55,000 250,000/100,000 300,000/150,000 400,000/200,000 550,000/300,000
HTTP / HTTPS
Throughput
400M/200M 2G/1G 4G/2G 10G/5G 14G/8G 15G/9G 16G/10G
HTTP / HTTPS
• NIC modules can be selected/combined in the slot and an SSL accelerator card can be installed as an option.
• Specifications of this product are subject to change without prior notice for performance improvement.
• Performance figures may differ depending on the instrument profile and environment. Please refer to the APPLIANCE SHEET for
the measurement environment.
APPLICATION INSIGHT WAF | 10
2. AIWAF Introduction
Full Transparent Proxy
■ Simple deployment without changes in the network configuration
- APPLICATION INSIGHT WAF is operated in a stealth mode without additional IP assigned to it.
- No changes to existing network configuration
Transparent Proxy
Proxy base Full Transparent Mode – Patented Tech (Kor) (No. 10-0695489)
APPLICATION INSIGHT WAF | 11
2. AIWAF Introduction
Cyber Threat Intelligence Platform Link
■ Proactive response to various threats that cannot be solved by security rules alone
- Real-time response to various web attack threats through cyber threat intelligence platform linkage
- Comprehensive/physical response system for proxy IP, Black Client IP, C&C IP, and malicious code link insertion
- Reputation information about the attack IP
AICC(Application Insight Cloud Center)
APPLICATION INSIGHT WAF | 12
2. AIWAF Introduction
Machine Learning Based Unknown Attack Detection
■ Efficient response to new web vulnerabilities that does not, yet, have response patterns
- Syncing with machine learning (cloud center) technology to detect anomalies and threats
- Protect web-based applications from known and unknown threats
Machine Learning
APPLICATION INSIGHT WAF | 13
2. AIWAF Introduction
HTTP/2 Protocol Control
■ Ease of transition to HTTP/2 from existing web service
- HTTP/2 is a completely different protocol from HTTP/1.1 and supports only encrypted (HTTPS) communication.
- Full parsing for HTTP/2 traffic and the same security function can be applied
APPLICATION INSIGHT WAF | 14
2. AIWAF Introduction
Adaptive Profiling Technology
■ Effective for post-analysis
- Develop profile DB based on normal client request and web server response by self-learning engine
- Block abnormal traffic by using normal traffic profiling
- Perfect defense model against unknown attacks
APPLICATION INSIGHT WAF | 15
2. AIWAF Introduction
Malware Stopover 〮 Exploitation Detection
■ Protect website visitors and brand value
- The main purpose of the webserver attack is to leak information as well as to use it to distribute malicious
codes.
- By detecting malicious code embedded in the response page for all the response data of the web server, it is
possible to detect attacks that have bypassed the web firewall or exploitation of malicious code via/distribution
before and after the introduction of the web firewall.
Multi 〮 Double Encoding Attack Detection
■ Detection↑ False-positive↓
- Some web services (pages) communicate with various types of encoded data as needed
- When an attack phrase is inserted in the encoded query value or payload value, a gap in the security policy
occurs
- After decoding data encoded by various methods, perform inspection through normalization
- URL, HEX, UNICODE, BASE64 encoding support
APPLICATION INSIGHT WAF | 16
2. AIWAF Introduction
Multi-Domain Policy and Traffic Control
■ Effective domain (service) maintenance by domain
- Different policies can be set for different domains in a server.
- Independent monitoring/log analysis/policy setting through different administrator accounts for each domain
- QoS bandwidth limit setting per website (domain)
Master Admin
Admin A, B Domain admin
A Domain
admin
Policies www.a.com www.b.com www.c.com
SQL INJECTON ON ON ON
XSS ON
ON ON ON
CSRF ON OFF ON
Web Shell ON
ON ON OFF
Brute Force ON OFF OFF
APPLICATION INSIGHT WAF | 17
2. AIWAF Introduction
Easy and Flexible HTTPS Traffic Control
■ HTTPS service control to minimize points of failure
Increase in HTTPS traffic due to wide usage of SSL/TLS
Flexible cryptographic traffic control and high-performance processing power are key points of the web firewall
solution.
-Support TLS 1.3
-Multi-domain certificate support
-Easy certificate registration by supporting various extensions (no need for certificate
conversion process)
-Synchronization with actual web server activation protocol version and Cipher-Suite
list (automatic setting)
-Notification of certificate expiration and automatic bypass when certificate expires
Default protocol https is used by 59.6% (2020. 04)
APPLICATION INSIGHT WAF | 18
2. AIWAF Introduction
Security Policy Optimization
■ Security Gap↓
Granular policy control
- In case of false positive, service is uninterrupted and security gap minimized through exception handling for
each rule
- Applied IP/URL and exception IP/URL setting
- Customizable block page setting
- Customizable disable pattern setting
- Schedule setting
Non HTTP Traffic Control
■ Eliminate inconvenience caused by managing multiple web servers
- In case of non HTTP(S) service, automatic traffic bypass for non WEB traffic through protocol type analysis
- Efficient operation options for possible service failures due to human error
APPLICATION INSIGHT WAF | 19
2. AIWAF Introduction
Web Service Quality Monitoring
■ Checking for the cause in the case of web service error
- Real-time web service status monitoring for protected web servers
- Actually HTTP(S) traffic health check instead of TCP Port check
- Provides current quality of the webserver, such as current status, response speed (min, max, average), and
availability. It is used to determine whether the service is interrupted or slowed down by the firewall.
Self Policy Check
■ Fast detection of a new vulnerability
- Enter a sample code when a new vulnerability occurs, or perform a self-test on which rules or patterns are
detected in the firewall for the purpose of checking policy and mock hacking (web vulnerability diagnosis).
- Easy management with error, duplication, detection of security rules established by the user
APPLICATION INSIGHT WAF | 20
3. WAF
FEATURES
3. AIWAF Features
APPLICATION INSIGHT WAF Main Features (Summary)
Policy Functions Details
Configuration of WAF operating mode, web server health-check, pattern update, policy
Basic Settings Operating Mode
synchronization, etc.
Registration of protected HTTP, HTTPS web server and configuration of SSL
Protected Web Server
offload/termination
Admin Policy IP Policy Configuration of IP White List, IP Black List
DoS Policy Detect and block TCP Session limit, Slow DoS attack
Domain Domain registration and maintenance, QoS setting by domain, origin IP header detection,
Domain Registration
Management admin by domain
Threshold- Forced browsing, HTTP request flooding, click fraud, login fraud, attacker IP auto-detection
Based Security Threshold-Based Policy attempts inflow more than the threshold, the source IP will be added to a blacklist and
Policy detect or block within the configured time
OWASP TOP 10 SQL injection, XSS, cookie forgery, CSRF, forced browsing, malicious file upload, command
Vulnerability Detection injection, directory access, and other vulnerability detection and block
Detection
Other Vulnerability Detection Application vulnerability, scanner/proxy/spambot, and other vulnerability detection and block
An abnormal HTTP request, HTTP method restriction, bugger overflow, unverified redirect,
HTTP Header Detection
HTTP header/payloads/queries check to detect or block based on the policy setting
Create a profile by learning access information of users for a specified period, and profiling.
Application Profiling
Detect and block access attempts that violate policy.
Abnormal Detect and block undefined extension requests by defining extensions that can be requested
Request/Respo URL Extension Access Control
nse from clients
Honeypot URL Block users accessing Honeypot URL as a tool (crawler, Scraper, etc.)
Bot detection based on the client’s script analysis after inserting Java script in the response
Script Authentication
data
APPLICATION INSIGHT WAF | 22
3. AIWAF Features
APPLICATION INSIGHT WAF Main Features (Summary)
Policy Functions Details
Personal Information Detect and Mask / Block the personal information leakage by checking the HTTP response
Input/output Detection data
Page Forgery Detection Detect URL page forgery and restore the original page
Remove the header information of the HTTP response packet containing the important
Header Cloaking
information of the web server and send it to the user
Server/Data
Protection If the web server’s response code is an error code (or DBMS error), a block page appears
Error Page Cloaking
instead of the error page
Detects and blocks leakage of the server’s directory file and information from erroneous
Directory Listing
settings
Malware Distribution Detect and block when the web server is infected with malicious code and has malicious
Detection data embedded in the reply page.
URL Access Rule Detect and block access to specified URL based on the client’s IP
Keyword Filtering Rule Detect and block profanity or advertisement keyword input
User-Defined
Detection Create custom patterns that combine methods, URL paths, headers, cookies, queries, and
User-Defined Rule
payloads
Check the web server’s error code and in the case of specified error code, then send a
Error Page Cloaking
customized response to the client
Web Socket
WebSocket Detect and block WebSocket attack traffic that’s not normal HTTP(S)
Detection
Web Accelerator
Web Accelerator Web server setting according to URL when web acceleration function is activated
Policy
URL / IP Group URL and client IP group configuration
Group/Block
Page Settings
Block Page Block page setting to send to clients when an HTTP request violates a policy.
APPLICATION INSIGHT WAF | 23
3. AIWAF Features
APPLICATION INSIGHT WAF Main Features
Vulnerability Attack
- Defense against major security vulnerabilities
• SQL injection
• LDAP injection
• XSS
• CSRF
• Cookie forgery detection
• Malicious file upload
• Malicious file access
• Command injection
• Directory access
• Vulnerable page access
• System file access
• Web server/application vulnerability
• Header vulnerability
• Scanner/proxy/spambot
APPLICATION INSIGHT WAF | 24
3. AIWAF Features
APPLICATION INSIGHT WAF Main Features
Abnormal Request/Response
- Abnormal request/response data detection
• HTTP abnormal request
• HTTP method restrictions
• Character set limit
• Buffer overflow
• POST request approval
• Unverified redirect
• Application profiling
• URL extension access control
• Hidden field tempering
• Honeypot URL
• Script Authentication
APPLICATION INSIGHT WAF | 25
3. AIWAF Features
APPLICATION INSIGHT WAF Main Features
Server/Data Protection
- Key security features for protecting server data
• Personal information inflow/ outflow
• Page forgery
• Header clocking
• Error page clocking (DBMS error detection)
• Comment cloaking
• Directory listing
• Malware distribution detection
User-defined Detection
- Additional user-defined security settings
• URL access rules
• Keyword filtering rules
• User defined pattern rules
APPLICATION INSIGHT WAF | 26
3. AIWAF Features
APPLICATION INSIGHT WAF Main Features
Threshold based defense
- Flooding and brute force attack detection
• Automatic attacker IP detection
• Forced browsing detection
• HTTP request flooding detection
• Click fraud detection
• Fraudulent login detection
WebSocket
- Malicious syntax detection, such as SQL
injection and XSS, by analyzing websocket
data
APPLICATION INSIGHT WAF | 27
3. AIWAF Features
APPLICATION INSIGHT WAF Main Features
Trouble Shooting
- Separate UI for product management and
troubleshooting for technical support engineers or
advanced administrators
• Product patch
• Product initialization
• Emergency recovery mode
• Password reset
• Debug Log collection
• TCPDUMP collection
• Automatic information logging needed for error
analysis
• Important setting changes and value
modification and monitoring
APPLICATION INSIGHT WAF | 28
4. Configuration Methods
& Case Studies
4. Configuration Methods & Case Studies
Various Configuration Methods
Transparent Proxy(IN-Line) Port Redirection(Out-of-path)
• Operating mode: Transparent Proxy • Operating mode: Port Redirection
• Physical configuration: IN-Line • Physical configuration: One-Armed
• In-line configuration in the form of a bridge on the • Port Redirection required for L3 and L4 switches
network path • During configuration or in case of an error, service is
• Operate as Transparent Proxy Mode without an IP not interrupted
• All security features provided • All security features provided
• 80% of references are deployed this way • 5% of references are deployed this way
APPLICATION INSIGHT WAF | 30
4. Configuration Methods & Case Studies
Various Configuration Methods
Sniffing(In-Line) Mirroring(Out-of-path)
• Operating mode: Sniffing • Operating Mode: Mirroring
• Physical configuration: IN-Line • Physical configuration: One-Armed
• Provides high performance with sniffing type via • Copy traffic from switch or TAP
packet copying method • Block attack traffic through a separate blocking
• Supports RSA type HTTPS traffic only interface
• Provides 85% of security functions • Provides 85% of security functions
• 5% of references are deployed this way • 5% of references are deployed this way
APPLICATION INSIGHT WAF | 31
4. Configuration Methods & Case Studies
Various Configuration Methods
Reverse Proxy(Out-of-Path)
• Operating mode: Reverse Proxy
• Physical configuration: Out-Of-Path
• Change web server IP to firewall IP in the DNS information
• Provides extensive protection to a distributed group of web servers in a single firewall system
• Supports Multi-Segment
• 5% of references are deployed this way
APPLICATION INSIGHT WAF | 32
4. Configuration Methods & Case Studies
Supports Various Network Environments
Port Trunk Multi-Segment
• Port Trunk, Tag VLAN, LACP configuration • Suppports N number of segments (depends on
support the number of interfaces)
• No configuration changes in network or web • NO configuration changes in network or web
server’s IP server’s IP.
• Provides fail-open for each segment
APPLICATION INSIGHT WAF | 33
4. Configuration Methods & Case Studies
Supports Various Network Environments
Active-Standby Asynchronous
• Checks health status of between the firewalls • Asynchronous traffic forwarding between the
• In the case of system error provides HA (fail-over) firewalls
• Automatic fail-back through master and slave • Multi-Segment environment support
settings
APPLICATION INSIGHT WAF | 34
4. Configuration Methods & Case Studies
Case Study (Public Sector – Organization I)
Overview
• Different policies for different web services (multi-domain)
• Accepts tagged VLAN environment
• Guaranteed service availability even in case of system
failure through the physical bypass function built into the
web firewall
Deployment
• 1 firewall accommodates distributed web servers
• 3 Multi Segment configuration
Effectiveness
• Maintaining all the environment configuration of the
existing network (no need to change environment settings)
• Efficient defense system for external/internal services
• Provide security policy setting environment for each web
server administrator
Main Policy
• SQL INJECTION, XSS, application vulnerability detection
APPLICATION INSIGHT WAF | 35
4. Configuration Methods & Case Studies
Case Study (Public Sector– Organization H)
Overview
• Provides control over detailed parameters that cannot be
controlled by IPS
• Separation of URLs to allow access according to user
classification
• Proactive defense against web servers using vulnerable
library versions (openssl, bash, etc.)
Deployment
• L4 switch port redirection setting- HTTP / HTTPS
-Two-way traffic filter (Service Port)
• Suitable for handling low-volume web traffic compared to
overall network capacity
Effectiveness
• Improved detection rate by 19.4% compared to IPS
(compare the number of undetected IPS)
• Defends against zeroday attacks even before web server
patching
• Can separate accessible web services depending on the user
IP
Main Policy
• URL access rules, header vulnerability detection, and web
server vulnerability detection
APPLICATION INSIGHT WAF | 36
4. Configuration Methods & Case Studies
Case Study (Private Sector– Company P)
Overview
• Asynchronous traffic network environnent support
• Comprehensive website defense to counter warnings from
well-known hacker groups
• Check access to already uploaded web shell files and block
uploads of new web shell files
Deployment
• Bypass TAP based in-line configuration
• Async port connection between WAF systems for
asynchronous traffic processing
Effectiveness
• Asynchronous traffic processing using session forwarding
function
• 98% defense rate during a client's own mock hacking(2%
false positive)
• Malicious file upload rate decreased by 22.8%
Main Policy
• SQL INJECTION, malicious file upload detection, and
malicious file access detection
APPLICATION INSIGHT WAF | 37
THANK YOU
MONITORAPP INC. | Address: 3162 S Colonial Ave. Ontario, CA 91761 | Tel : 951-800-0012 | Web : www.monitorapp.com
E-mail : sales@monitorapp.com | Copyright 2018 MONITORAPP Co.,Ltd. All rights reserved.
You might also like
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeFrom EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeRating: 4 out of 5 stars4/5 (5834)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreFrom EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreRating: 4 out of 5 stars4/5 (1093)
- Never Split the Difference: Negotiating As If Your Life Depended On ItFrom EverandNever Split the Difference: Negotiating As If Your Life Depended On ItRating: 4.5 out of 5 stars4.5/5 (852)
- Grit: The Power of Passion and PerseveranceFrom EverandGrit: The Power of Passion and PerseveranceRating: 4 out of 5 stars4/5 (590)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceFrom EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceRating: 4 out of 5 stars4/5 (903)
- Shoe Dog: A Memoir by the Creator of NikeFrom EverandShoe Dog: A Memoir by the Creator of NikeRating: 4.5 out of 5 stars4.5/5 (541)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersFrom EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersRating: 4.5 out of 5 stars4.5/5 (350)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureFrom EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureRating: 4.5 out of 5 stars4.5/5 (474)
- Her Body and Other Parties: StoriesFrom EverandHer Body and Other Parties: StoriesRating: 4 out of 5 stars4/5 (824)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)From EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Rating: 4.5 out of 5 stars4.5/5 (122)
- The Emperor of All Maladies: A Biography of CancerFrom EverandThe Emperor of All Maladies: A Biography of CancerRating: 4.5 out of 5 stars4.5/5 (271)
- The Little Book of Hygge: Danish Secrets to Happy LivingFrom EverandThe Little Book of Hygge: Danish Secrets to Happy LivingRating: 3.5 out of 5 stars3.5/5 (405)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyFrom EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyRating: 3.5 out of 5 stars3.5/5 (2259)
- The Yellow House: A Memoir (2019 National Book Award Winner)From EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Rating: 4 out of 5 stars4/5 (98)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaFrom EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaRating: 4.5 out of 5 stars4.5/5 (266)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryFrom EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryRating: 3.5 out of 5 stars3.5/5 (231)
- Team of Rivals: The Political Genius of Abraham LincolnFrom EverandTeam of Rivals: The Political Genius of Abraham LincolnRating: 4.5 out of 5 stars4.5/5 (234)
- On Fire: The (Burning) Case for a Green New DealFrom EverandOn Fire: The (Burning) Case for a Green New DealRating: 4 out of 5 stars4/5 (74)
- The Unwinding: An Inner History of the New AmericaFrom EverandThe Unwinding: An Inner History of the New AmericaRating: 4 out of 5 stars4/5 (45)
- EB7781356Document410 pagesEB7781356Andrej MiladinovicNo ratings yet
- Digital Wine Marketing Social Media Marketing ForDocument5 pagesDigital Wine Marketing Social Media Marketing ForCudera EduardNo ratings yet
- Lightspeed Mobile Manager V1.0Document148 pagesLightspeed Mobile Manager V1.0lwfrancis68No ratings yet
- MOER 1 Teacher's BookDocument107 pagesMOER 1 Teacher's BookAnh NgoNo ratings yet
- Service Manual - Micro Series V. 1.00Document184 pagesService Manual - Micro Series V. 1.00Edgar Mendoza García100% (1)
- CompTIA Pentest Study Guide PDFDocument71 pagesCompTIA Pentest Study Guide PDFscastell77No ratings yet
- Cyber Psychology 2017Document5 pagesCyber Psychology 2017Bhavika LargotraNo ratings yet
- 0417 s17 QP 32Document8 pages0417 s17 QP 32Mohamed AliNo ratings yet
- Qs Titan HostKeysDocument8 pagesQs Titan HostKeysjasser koukiNo ratings yet
- Toshiba E-Studio 182 - ManualDocument226 pagesToshiba E-Studio 182 - ManualGopi EmNo ratings yet
- Word Exercise 4Document3 pagesWord Exercise 4Farhan KhanNo ratings yet
- Admin Free - Active Directory and Windows, Part 1 - Understanding Privileged Groups in AD - An Infrastructure Geek Floating in A Sea of UberCoders - Site Home - TechNet BlogsDocument7 pagesAdmin Free - Active Directory and Windows, Part 1 - Understanding Privileged Groups in AD - An Infrastructure Geek Floating in A Sea of UberCoders - Site Home - TechNet Blogsferro4uNo ratings yet
- Huawei Hg532e User Manual (v100r001 02)Document31 pagesHuawei Hg532e User Manual (v100r001 02)Ismael Francisco Diaz GomezNo ratings yet
- Polimerico y PorcelantoDocument4 pagesPolimerico y Porcelantoreivin27No ratings yet
- Online Ticket Reservation For Cinema Hall: A Project Report OnDocument43 pagesOnline Ticket Reservation For Cinema Hall: A Project Report Onusman kebato100% (1)
- Module 1: Introduction To Cyber Ethics - Concepts, Perspectives, and Methodological Frameworks Week 1 Learning OutcomesDocument13 pagesModule 1: Introduction To Cyber Ethics - Concepts, Perspectives, and Methodological Frameworks Week 1 Learning OutcomesBeybee BuzzNo ratings yet
- WDO - About - Definition of Industrial DesignDocument3 pagesWDO - About - Definition of Industrial DesignSebastián BejaranoNo ratings yet
- W5 Practical Exercise D-ITG ManualDocument2 pagesW5 Practical Exercise D-ITG Manualiotossiche50% (2)
- Lesson 2 Notes and VocabularyDocument6 pagesLesson 2 Notes and Vocabularyapi-241719162No ratings yet
- TSM NotesDocument6 pagesTSM NotessruthiNo ratings yet
- VMCE - V9.exam.104q: Number: VMCE - V9 Passing Score: 800 Time Limit: 120 MinDocument49 pagesVMCE - V9.exam.104q: Number: VMCE - V9 Passing Score: 800 Time Limit: 120 MinDennis DubeNo ratings yet
- Chapter 8 Process TechnologyDocument22 pagesChapter 8 Process TechnologyfozNo ratings yet
- How To Copy The Content in NotepadDocument17 pagesHow To Copy The Content in NotepadDeepak KumarNo ratings yet
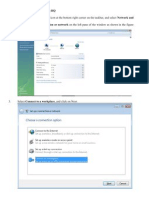
- Setting Up A VPN Connectivity With HQ (Vista)Document7 pagesSetting Up A VPN Connectivity With HQ (Vista)anon_175499549No ratings yet
- ( (Otrs) ) : Open Ticket Request SystemDocument9 pages( (Otrs) ) : Open Ticket Request SystemGustavo MorielNo ratings yet
- Routings - Mind MapDocument1 pageRoutings - Mind MapSaptarshi GhoshNo ratings yet
- Developers Guide To AwsDocument20 pagesDevelopers Guide To AwspafgoncalvesNo ratings yet
- Cryptography and Its TypesDocument1 pageCryptography and Its TypesSweta BarnwalNo ratings yet
- Gilssely Polanco Resume 2016Document1 pageGilssely Polanco Resume 2016api-280452614No ratings yet
- BSNL AnswersDocument10 pagesBSNL Answerssuyog nikamNo ratings yet