Professional Documents
Culture Documents
Business Logic Flaws: What Is It?
Business Logic Flaws: What Is It?
Uploaded by
Jose LuisCopyright:
Available Formats
You might also like
- Scrum : Mastery - The Essential Guide to Scrum and Agile Project Management: Lean Guides with Scrum, Sprint, Kanban, DSDM, XP & Crystal Book, #5From EverandScrum : Mastery - The Essential Guide to Scrum and Agile Project Management: Lean Guides with Scrum, Sprint, Kanban, DSDM, XP & Crystal Book, #5No ratings yet
- BITS Pilani: Computer Programming (MATLAB) Dr. Samir Kale Contact Session: 10.30-12.30Document20 pagesBITS Pilani: Computer Programming (MATLAB) Dr. Samir Kale Contact Session: 10.30-12.30scribd2020No ratings yet
- Changing The WIP Calculation Basis On Manufacturing OrdersDocument3 pagesChanging The WIP Calculation Basis On Manufacturing OrdersHuba HorompolyNo ratings yet
- Amazon Quicksight UserDocument359 pagesAmazon Quicksight Userspanda3j3No ratings yet
- Pentaho Data Integration Fundamentals: Course Code DI1000 7.0Document10 pagesPentaho Data Integration Fundamentals: Course Code DI1000 7.0Yonathan GambinNo ratings yet
- Example of Severity and PriorityDocument5 pagesExample of Severity and Prioritywillbark2day100% (1)
- Defect Severity and Defect Priority With ExamplesDocument2 pagesDefect Severity and Defect Priority With ExamplesBalajiNRamalingam100% (1)
- NbvLwU Camunda BPM Compared To Alternatives 08 2015Document13 pagesNbvLwU Camunda BPM Compared To Alternatives 08 2015mhenley8059No ratings yet
- Why Decisions EbookDocument8 pagesWhy Decisions Ebookskouti9No ratings yet
- Understanding PerformanceDocument65 pagesUnderstanding PerformanceClaudia AfinekNo ratings yet
- Bug Reporting - Art and Advocacy: What We DidDocument4 pagesBug Reporting - Art and Advocacy: What We DidVinay GawliNo ratings yet
- Get Performance Requirements Right - Think Like A User: by Scott BarberDocument8 pagesGet Performance Requirements Right - Think Like A User: by Scott BarberwajNo ratings yet
- Seven Steps For Your Ecommerce Program SuccessDocument4 pagesSeven Steps For Your Ecommerce Program Successjorge rodriguezNo ratings yet
- SAP GRC (Basic) ,: Biju (Jays)Document42 pagesSAP GRC (Basic) ,: Biju (Jays)Peter PanterNo ratings yet
- Software Estimation For DummiesDocument5 pagesSoftware Estimation For DummiesMurali Chemuturi100% (2)
- 80746b28d951-Suppose An Outsourcer Handles Your Credit Card Transactions and Leaves A SoftwareDocument1 page80746b28d951-Suppose An Outsourcer Handles Your Credit Card Transactions and Leaves A SoftwareCurios cornerNo ratings yet
- Ecommerce Metrics EbookDocument12 pagesEcommerce Metrics EbookShanti Peeters0% (1)
- StorySplitting - 8 Useful Strategies For Splitting Large User Stories (And A Cheatsheet)Document16 pagesStorySplitting - 8 Useful Strategies For Splitting Large User Stories (And A Cheatsheet)jm.doumontNo ratings yet
- Software Testing Is A Process of Searching For Software ErrorsDocument9 pagesSoftware Testing Is A Process of Searching For Software ErrorsAnarchimiNo ratings yet
- The Action - Executor PatternDocument12 pagesThe Action - Executor PatternmanitcorNo ratings yet
- E BiCycleDocument7 pagesE BiCycleMuhammad MazaribNo ratings yet
- What Is Role Remediation in SAPDocument14 pagesWhat Is Role Remediation in SAPdsaNo ratings yet
- Serio Problem ManagementDocument13 pagesSerio Problem ManagementrkamundimuNo ratings yet
- Ebook For SaaS CompanyDocument13 pagesEbook For SaaS CompanyshanmugaNo ratings yet
- GRC Basic-1 PDFDocument42 pagesGRC Basic-1 PDFsupriyacnaikNo ratings yet
- Basics For GRCDocument42 pagesBasics For GRCSharan Mathapati100% (1)
- 10 Design Patterns Every Software Architect and Software Engineer Must Know - by Ravindra Elicherla - MediumDocument14 pages10 Design Patterns Every Software Architect and Software Engineer Must Know - by Ravindra Elicherla - Mediumabenito1313No ratings yet
- 03 Procure To PayDocument22 pages03 Procure To PayKalaignar ThangarajuNo ratings yet
- 10 Strategies CRM SuccessDocument7 pages10 Strategies CRM SuccessVijay VittalNo ratings yet
- Computer Shop ManagementDocument34 pagesComputer Shop ManagementHassan Shafique100% (2)
- Agile Requirements Change ManagementDocument5 pagesAgile Requirements Change ManagementSantosh KumarNo ratings yet
- Oracle Cloud5Document11 pagesOracle Cloud5venkat0316No ratings yet
- Ebook For SaaS CompanyDocument13 pagesEbook For SaaS CompanyRyan SkinnerNo ratings yet
- Debugging CRM Middle WareDocument41 pagesDebugging CRM Middle WareSarika Gupta100% (1)
- Examples of Severity and PriorityDocument11 pagesExamples of Severity and PriorityEntertainment world wideNo ratings yet
- Field SymbolsDocument7 pagesField SymbolsAndrés GómezNo ratings yet
- HITBsecDocument76 pagesHITBsecCasie JakeNo ratings yet
- Workflow: A Foundational Element of Business ApplicationsDocument16 pagesWorkflow: A Foundational Element of Business ApplicationsEka NusaNo ratings yet
- What Is TestingDocument10 pagesWhat Is Testingapi-3833376No ratings yet
- 8020 A New Model For Business Process DesignDocument36 pages8020 A New Model For Business Process DesignIan Ramsay100% (1)
- Agile User Story MappingDocument16 pagesAgile User Story MappingRaghavendra KuthadiNo ratings yet
- Breaking The Business LogicsDocument10 pagesBreaking The Business LogicsJuan Sebastian MartinezNo ratings yet
- Ap Automation For Retail ManagementDocument15 pagesAp Automation For Retail Managementchella_duraiNo ratings yet
- Role of A Business Analyst in Agile ModeDocument3 pagesRole of A Business Analyst in Agile ModeSaurabh GuptaNo ratings yet
- Polarion Goes ScrumDocument14 pagesPolarion Goes ScrumABUTANINo ratings yet
- Agree & Dismiss: This Website Uses Cookies To Ensure You Get The Best Experience On Our WebsiteDocument20 pagesAgree & Dismiss: This Website Uses Cookies To Ensure You Get The Best Experience On Our WebsiteSHREYNo ratings yet
- Ebook 10 Dysfunctions of Product Management V2Document26 pagesEbook 10 Dysfunctions of Product Management V2DirkRabauNo ratings yet
- Reading Sample Sappress 1481 Sap System Security GuideDocument39 pagesReading Sample Sappress 1481 Sap System Security GuideVitlenNo ratings yet
- Is Agile Really My ThingDocument2 pagesIs Agile Really My ThingB AnikNo ratings yet
- How To Deliver Software SuccessfullyDocument13 pagesHow To Deliver Software Successfullyhttr1No ratings yet
- Chapter 4 - Writing RequirementsDocument31 pagesChapter 4 - Writing RequirementsNardos KumlachewNo ratings yet
- QUEST - 10 Steps To Cleaning Up Act - 0Document26 pagesQUEST - 10 Steps To Cleaning Up Act - 0Maheish AyyerNo ratings yet
- Defect Report Core - USBDocument9 pagesDefect Report Core - USBMarco Antonio Veizaga MoyaNo ratings yet
- Inhouse Vs Off The Shelf MayDocument5 pagesInhouse Vs Off The Shelf MayJeffry BinabiseNo ratings yet
- EgzonaFida (Ef26398 - SWLcase - I)Document24 pagesEgzonaFida (Ef26398 - SWLcase - I)Egzona FidaNo ratings yet
- SODDocument2 pagesSODAnonymous dQ6ohSOLRNo ratings yet
- Feature Hrmantra Other Indian HR & Payroll Software'SDocument6 pagesFeature Hrmantra Other Indian HR & Payroll Software'SVivek ViswanathanNo ratings yet
- HowToBuildCaseForPasswordManager RefrshDocument5 pagesHowToBuildCaseForPasswordManager RefrshprinsloojustineNo ratings yet
- The IT Manager’s Guide to Continuous Delivery: Delivering Software in DaysFrom EverandThe IT Manager’s Guide to Continuous Delivery: Delivering Software in DaysNo ratings yet
- Data Management Security IoT A Complete Guide - 2019 EditionFrom EverandData Management Security IoT A Complete Guide - 2019 EditionNo ratings yet
- IoT Software Product Manager A Complete Guide - 2019 EditionFrom EverandIoT Software Product Manager A Complete Guide - 2019 EditionNo ratings yet
- Office Automation Tools II Unit 1Document24 pagesOffice Automation Tools II Unit 1Khalid AbdulkarimNo ratings yet
- HP Z6 G4 Workstation: A Future-Proof PowerhouseDocument4 pagesHP Z6 G4 Workstation: A Future-Proof Powerhousetranhuy3110No ratings yet
- OOPS Mid TermDocument25 pagesOOPS Mid TermH paliwalNo ratings yet
- Elios 2 - Product Offering - v1.9 - EURDocument12 pagesElios 2 - Product Offering - v1.9 - EURTranzmitterNo ratings yet
- E PosterDocument1 pageE PosterZainab AshrafNo ratings yet
- MEI Cashflow SC83 / SCN83 Installation & Operation ManualDocument30 pagesMEI Cashflow SC83 / SCN83 Installation & Operation ManualTran TtPNo ratings yet
- CMSC 197 (Game Development and Design) Machine Problem 1Document2 pagesCMSC 197 (Game Development and Design) Machine Problem 1Claudine BustilloNo ratings yet
- CS112 Assignment-2 (G9-G12)Document4 pagesCS112 Assignment-2 (G9-G12)Shubham rajNo ratings yet
- Winnicott - Adam PhillipsDocument110 pagesWinnicott - Adam PhillipsRafael LFNo ratings yet
- Prerequisite Customizing Required For LegacyDocument3 pagesPrerequisite Customizing Required For LegacyFranki Giassi MeurerNo ratings yet
- Sazzad Hossain Shohan - Literature ReviewDocument27 pagesSazzad Hossain Shohan - Literature ReviewSazzad Hossain ShohanNo ratings yet
- Confio Statistical Analysis Database Performance DelaysDocument4 pagesConfio Statistical Analysis Database Performance DelaysRavmiNo ratings yet
- User Interfaces and Visualization: Prof - Pravin V.ShindeDocument24 pagesUser Interfaces and Visualization: Prof - Pravin V.ShindePravin ShindeNo ratings yet
- 2-A Case of Dynamic Program Analysis - CS510 Software EngineeringDocument42 pages2-A Case of Dynamic Program Analysis - CS510 Software Engineeringrunqi fanNo ratings yet
- Software Project Proposal For: Library Management SystemDocument8 pagesSoftware Project Proposal For: Library Management SystemMaria AsifNo ratings yet
- MySQL Perf Tuning OOW2015 DimDocument141 pagesMySQL Perf Tuning OOW2015 Dimcristiano.viniciusNo ratings yet
- Make Opera Yours: Get StartedDocument12 pagesMake Opera Yours: Get StartedAndrewnelaonNo ratings yet
- Hardware Hacking 101: Bsides Munich 2019 Radek Domanski, Johannes WagnerDocument38 pagesHardware Hacking 101: Bsides Munich 2019 Radek Domanski, Johannes WagnerSadry Fievet100% (1)
- Suman Patra - Java Developer - 2 YearDocument3 pagesSuman Patra - Java Developer - 2 YearMohammed AbdulNo ratings yet
- Dell Storage Manager 2018 R1.20Document31 pagesDell Storage Manager 2018 R1.20jameseklieNo ratings yet
- Aph Convolutional Networks For Android Malware Detection With System Call GraphsDocument10 pagesAph Convolutional Networks For Android Malware Detection With System Call Graphsziklonn xNo ratings yet
- Architect Tutorial Sixth Edition SampleDocument24 pagesArchitect Tutorial Sixth Edition SampleLê Minh TuấnNo ratings yet
- C Data Structure PracticeDocument507 pagesC Data Structure Practicedivyam singhNo ratings yet
- Google Colab - RugmaDocument17 pagesGoogle Colab - RugmaGaurav SrivastavaNo ratings yet
- BJ-W7200 TRMDocument212 pagesBJ-W7200 TRMCraig LindowNo ratings yet
- S18 ADipIT08 A1 CW1 QPDocument5 pagesS18 ADipIT08 A1 CW1 QPalenNo ratings yet
- Limits of AI TodayDocument3 pagesLimits of AI TodayРома КравчукNo ratings yet
Business Logic Flaws: What Is It?
Business Logic Flaws: What Is It?
Uploaded by
Jose LuisOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Business Logic Flaws: What Is It?
Business Logic Flaws: What Is It?
Uploaded by
Jose LuisCopyright:
Available Formats
👔
Business logic flaws
What is it?
Business logic flaws often arise from different situations. They occur when users
pass values to the target which are not expected. This can cause several
unforseen things to occur. These things might not always be as impactful but
sometimes they can be devistating. The analysts make assumptions about use
behavior but these can be wrong. This will lead to flaws in the design and the
implementation of the logic.
The reason i love Logic flaws so much is because they are really hard to look for.
Normal use of the application will not always show these and we have to
specifically look for them. This makes it nearly impossibly for automated tools to
be created that will find logic vulnerabilities on a consistant basis.
Business process usually consists of:
Analysis > Development > Testing > Production
I know this process is very simplified but it's not important to know the details
right now. Usually several "Stories" or "Features" get taken up into a release cycle.
If the analysis from the start contains logic flaws, this is an entry point for our
attack.
What also sometimes happens is that a piece of software might be developed and
a couple of years later an expansion or adaptation might be requested. Usually
documentation is a big problem in companies so when a change has to be made
to a certain feature, the developers will have to dig into the code where they
might remove certain important features that gaurd the sanity of the users
actions.
Business logic flaws 1
What is the impact?
The impact is highly dependant on the specific target and logic flaw that you
found. It is related to the impacted functionality as well.
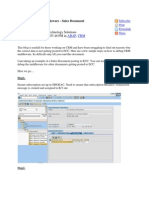
Client side calculations of prices in a clothing webshop - High/Crit
This is core business for the target so any issue related to the core
business will automatically be more impactful
When brute forcing usernames, you get a 200 OK status when the username
you are trying to brute force exists and a 403 if it does not exist on the login
page - Low
This is rather low unless those usernames really have to be secret, you'd
have to brute force the login names and then you have to still guess the
correct password. This is more usefull on a pentest job.
Negative amounts of items on a webshop lead to negative prices - High/Crit
This is core business for the target so any issue related to the core
business will automatically be more impactful above all, impact on money
directly is very important
If price = integer and amount = integer and total price = interger we can
overflow total price when we price * amount - Critical
This might lead to the target returning us money which is certainly not
desireable
Registering with the same username as an existing user takes over the
account - Critical
Account takeovers are always higher on the severity scale
The user manual might tell you that you can't deactivate super admin users,
but after trying it you can - Medium
You have to be a priviledged user to even be allowed into the user
management system so this lowers the severity a bit
Field in the response that's not in the original request but does get processed
by the server when you add it - Nothing/Critical
Business logic flaws 2
This really depends on the fields that is being processed here. If you can
change your accounttype from "User" to "Admin" This would ofcourse be a
big problem.
Importing products with the same name as existing ones overwrites them.
Even if the products do not belong to you and you should not be able to
overwrite them. - Medium
You are already in a priviledged position before you can import products,
this lowers the severity
Business logic flaws 3
You might also like
- Scrum : Mastery - The Essential Guide to Scrum and Agile Project Management: Lean Guides with Scrum, Sprint, Kanban, DSDM, XP & Crystal Book, #5From EverandScrum : Mastery - The Essential Guide to Scrum and Agile Project Management: Lean Guides with Scrum, Sprint, Kanban, DSDM, XP & Crystal Book, #5No ratings yet
- BITS Pilani: Computer Programming (MATLAB) Dr. Samir Kale Contact Session: 10.30-12.30Document20 pagesBITS Pilani: Computer Programming (MATLAB) Dr. Samir Kale Contact Session: 10.30-12.30scribd2020No ratings yet
- Changing The WIP Calculation Basis On Manufacturing OrdersDocument3 pagesChanging The WIP Calculation Basis On Manufacturing OrdersHuba HorompolyNo ratings yet
- Amazon Quicksight UserDocument359 pagesAmazon Quicksight Userspanda3j3No ratings yet
- Pentaho Data Integration Fundamentals: Course Code DI1000 7.0Document10 pagesPentaho Data Integration Fundamentals: Course Code DI1000 7.0Yonathan GambinNo ratings yet
- Example of Severity and PriorityDocument5 pagesExample of Severity and Prioritywillbark2day100% (1)
- Defect Severity and Defect Priority With ExamplesDocument2 pagesDefect Severity and Defect Priority With ExamplesBalajiNRamalingam100% (1)
- NbvLwU Camunda BPM Compared To Alternatives 08 2015Document13 pagesNbvLwU Camunda BPM Compared To Alternatives 08 2015mhenley8059No ratings yet
- Why Decisions EbookDocument8 pagesWhy Decisions Ebookskouti9No ratings yet
- Understanding PerformanceDocument65 pagesUnderstanding PerformanceClaudia AfinekNo ratings yet
- Bug Reporting - Art and Advocacy: What We DidDocument4 pagesBug Reporting - Art and Advocacy: What We DidVinay GawliNo ratings yet
- Get Performance Requirements Right - Think Like A User: by Scott BarberDocument8 pagesGet Performance Requirements Right - Think Like A User: by Scott BarberwajNo ratings yet
- Seven Steps For Your Ecommerce Program SuccessDocument4 pagesSeven Steps For Your Ecommerce Program Successjorge rodriguezNo ratings yet
- SAP GRC (Basic) ,: Biju (Jays)Document42 pagesSAP GRC (Basic) ,: Biju (Jays)Peter PanterNo ratings yet
- Software Estimation For DummiesDocument5 pagesSoftware Estimation For DummiesMurali Chemuturi100% (2)
- 80746b28d951-Suppose An Outsourcer Handles Your Credit Card Transactions and Leaves A SoftwareDocument1 page80746b28d951-Suppose An Outsourcer Handles Your Credit Card Transactions and Leaves A SoftwareCurios cornerNo ratings yet
- Ecommerce Metrics EbookDocument12 pagesEcommerce Metrics EbookShanti Peeters0% (1)
- StorySplitting - 8 Useful Strategies For Splitting Large User Stories (And A Cheatsheet)Document16 pagesStorySplitting - 8 Useful Strategies For Splitting Large User Stories (And A Cheatsheet)jm.doumontNo ratings yet
- Software Testing Is A Process of Searching For Software ErrorsDocument9 pagesSoftware Testing Is A Process of Searching For Software ErrorsAnarchimiNo ratings yet
- The Action - Executor PatternDocument12 pagesThe Action - Executor PatternmanitcorNo ratings yet
- E BiCycleDocument7 pagesE BiCycleMuhammad MazaribNo ratings yet
- What Is Role Remediation in SAPDocument14 pagesWhat Is Role Remediation in SAPdsaNo ratings yet
- Serio Problem ManagementDocument13 pagesSerio Problem ManagementrkamundimuNo ratings yet
- Ebook For SaaS CompanyDocument13 pagesEbook For SaaS CompanyshanmugaNo ratings yet
- GRC Basic-1 PDFDocument42 pagesGRC Basic-1 PDFsupriyacnaikNo ratings yet
- Basics For GRCDocument42 pagesBasics For GRCSharan Mathapati100% (1)
- 10 Design Patterns Every Software Architect and Software Engineer Must Know - by Ravindra Elicherla - MediumDocument14 pages10 Design Patterns Every Software Architect and Software Engineer Must Know - by Ravindra Elicherla - Mediumabenito1313No ratings yet
- 03 Procure To PayDocument22 pages03 Procure To PayKalaignar ThangarajuNo ratings yet
- 10 Strategies CRM SuccessDocument7 pages10 Strategies CRM SuccessVijay VittalNo ratings yet
- Computer Shop ManagementDocument34 pagesComputer Shop ManagementHassan Shafique100% (2)
- Agile Requirements Change ManagementDocument5 pagesAgile Requirements Change ManagementSantosh KumarNo ratings yet
- Oracle Cloud5Document11 pagesOracle Cloud5venkat0316No ratings yet
- Ebook For SaaS CompanyDocument13 pagesEbook For SaaS CompanyRyan SkinnerNo ratings yet
- Debugging CRM Middle WareDocument41 pagesDebugging CRM Middle WareSarika Gupta100% (1)
- Examples of Severity and PriorityDocument11 pagesExamples of Severity and PriorityEntertainment world wideNo ratings yet
- Field SymbolsDocument7 pagesField SymbolsAndrés GómezNo ratings yet
- HITBsecDocument76 pagesHITBsecCasie JakeNo ratings yet
- Workflow: A Foundational Element of Business ApplicationsDocument16 pagesWorkflow: A Foundational Element of Business ApplicationsEka NusaNo ratings yet
- What Is TestingDocument10 pagesWhat Is Testingapi-3833376No ratings yet
- 8020 A New Model For Business Process DesignDocument36 pages8020 A New Model For Business Process DesignIan Ramsay100% (1)
- Agile User Story MappingDocument16 pagesAgile User Story MappingRaghavendra KuthadiNo ratings yet
- Breaking The Business LogicsDocument10 pagesBreaking The Business LogicsJuan Sebastian MartinezNo ratings yet
- Ap Automation For Retail ManagementDocument15 pagesAp Automation For Retail Managementchella_duraiNo ratings yet
- Role of A Business Analyst in Agile ModeDocument3 pagesRole of A Business Analyst in Agile ModeSaurabh GuptaNo ratings yet
- Polarion Goes ScrumDocument14 pagesPolarion Goes ScrumABUTANINo ratings yet
- Agree & Dismiss: This Website Uses Cookies To Ensure You Get The Best Experience On Our WebsiteDocument20 pagesAgree & Dismiss: This Website Uses Cookies To Ensure You Get The Best Experience On Our WebsiteSHREYNo ratings yet
- Ebook 10 Dysfunctions of Product Management V2Document26 pagesEbook 10 Dysfunctions of Product Management V2DirkRabauNo ratings yet
- Reading Sample Sappress 1481 Sap System Security GuideDocument39 pagesReading Sample Sappress 1481 Sap System Security GuideVitlenNo ratings yet
- Is Agile Really My ThingDocument2 pagesIs Agile Really My ThingB AnikNo ratings yet
- How To Deliver Software SuccessfullyDocument13 pagesHow To Deliver Software Successfullyhttr1No ratings yet
- Chapter 4 - Writing RequirementsDocument31 pagesChapter 4 - Writing RequirementsNardos KumlachewNo ratings yet
- QUEST - 10 Steps To Cleaning Up Act - 0Document26 pagesQUEST - 10 Steps To Cleaning Up Act - 0Maheish AyyerNo ratings yet
- Defect Report Core - USBDocument9 pagesDefect Report Core - USBMarco Antonio Veizaga MoyaNo ratings yet
- Inhouse Vs Off The Shelf MayDocument5 pagesInhouse Vs Off The Shelf MayJeffry BinabiseNo ratings yet
- EgzonaFida (Ef26398 - SWLcase - I)Document24 pagesEgzonaFida (Ef26398 - SWLcase - I)Egzona FidaNo ratings yet
- SODDocument2 pagesSODAnonymous dQ6ohSOLRNo ratings yet
- Feature Hrmantra Other Indian HR & Payroll Software'SDocument6 pagesFeature Hrmantra Other Indian HR & Payroll Software'SVivek ViswanathanNo ratings yet
- HowToBuildCaseForPasswordManager RefrshDocument5 pagesHowToBuildCaseForPasswordManager RefrshprinsloojustineNo ratings yet
- The IT Manager’s Guide to Continuous Delivery: Delivering Software in DaysFrom EverandThe IT Manager’s Guide to Continuous Delivery: Delivering Software in DaysNo ratings yet
- Data Management Security IoT A Complete Guide - 2019 EditionFrom EverandData Management Security IoT A Complete Guide - 2019 EditionNo ratings yet
- IoT Software Product Manager A Complete Guide - 2019 EditionFrom EverandIoT Software Product Manager A Complete Guide - 2019 EditionNo ratings yet
- Office Automation Tools II Unit 1Document24 pagesOffice Automation Tools II Unit 1Khalid AbdulkarimNo ratings yet
- HP Z6 G4 Workstation: A Future-Proof PowerhouseDocument4 pagesHP Z6 G4 Workstation: A Future-Proof Powerhousetranhuy3110No ratings yet
- OOPS Mid TermDocument25 pagesOOPS Mid TermH paliwalNo ratings yet
- Elios 2 - Product Offering - v1.9 - EURDocument12 pagesElios 2 - Product Offering - v1.9 - EURTranzmitterNo ratings yet
- E PosterDocument1 pageE PosterZainab AshrafNo ratings yet
- MEI Cashflow SC83 / SCN83 Installation & Operation ManualDocument30 pagesMEI Cashflow SC83 / SCN83 Installation & Operation ManualTran TtPNo ratings yet
- CMSC 197 (Game Development and Design) Machine Problem 1Document2 pagesCMSC 197 (Game Development and Design) Machine Problem 1Claudine BustilloNo ratings yet
- CS112 Assignment-2 (G9-G12)Document4 pagesCS112 Assignment-2 (G9-G12)Shubham rajNo ratings yet
- Winnicott - Adam PhillipsDocument110 pagesWinnicott - Adam PhillipsRafael LFNo ratings yet
- Prerequisite Customizing Required For LegacyDocument3 pagesPrerequisite Customizing Required For LegacyFranki Giassi MeurerNo ratings yet
- Sazzad Hossain Shohan - Literature ReviewDocument27 pagesSazzad Hossain Shohan - Literature ReviewSazzad Hossain ShohanNo ratings yet
- Confio Statistical Analysis Database Performance DelaysDocument4 pagesConfio Statistical Analysis Database Performance DelaysRavmiNo ratings yet
- User Interfaces and Visualization: Prof - Pravin V.ShindeDocument24 pagesUser Interfaces and Visualization: Prof - Pravin V.ShindePravin ShindeNo ratings yet
- 2-A Case of Dynamic Program Analysis - CS510 Software EngineeringDocument42 pages2-A Case of Dynamic Program Analysis - CS510 Software Engineeringrunqi fanNo ratings yet
- Software Project Proposal For: Library Management SystemDocument8 pagesSoftware Project Proposal For: Library Management SystemMaria AsifNo ratings yet
- MySQL Perf Tuning OOW2015 DimDocument141 pagesMySQL Perf Tuning OOW2015 Dimcristiano.viniciusNo ratings yet
- Make Opera Yours: Get StartedDocument12 pagesMake Opera Yours: Get StartedAndrewnelaonNo ratings yet
- Hardware Hacking 101: Bsides Munich 2019 Radek Domanski, Johannes WagnerDocument38 pagesHardware Hacking 101: Bsides Munich 2019 Radek Domanski, Johannes WagnerSadry Fievet100% (1)
- Suman Patra - Java Developer - 2 YearDocument3 pagesSuman Patra - Java Developer - 2 YearMohammed AbdulNo ratings yet
- Dell Storage Manager 2018 R1.20Document31 pagesDell Storage Manager 2018 R1.20jameseklieNo ratings yet
- Aph Convolutional Networks For Android Malware Detection With System Call GraphsDocument10 pagesAph Convolutional Networks For Android Malware Detection With System Call Graphsziklonn xNo ratings yet
- Architect Tutorial Sixth Edition SampleDocument24 pagesArchitect Tutorial Sixth Edition SampleLê Minh TuấnNo ratings yet
- C Data Structure PracticeDocument507 pagesC Data Structure Practicedivyam singhNo ratings yet
- Google Colab - RugmaDocument17 pagesGoogle Colab - RugmaGaurav SrivastavaNo ratings yet
- BJ-W7200 TRMDocument212 pagesBJ-W7200 TRMCraig LindowNo ratings yet
- S18 ADipIT08 A1 CW1 QPDocument5 pagesS18 ADipIT08 A1 CW1 QPalenNo ratings yet
- Limits of AI TodayDocument3 pagesLimits of AI TodayРома КравчукNo ratings yet