Professional Documents
Culture Documents
CSE2008 Syllabus
CSE2008 Syllabus
Uploaded by
ABHAY POTLURI 20BCI0017Original Description:
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
CSE2008 Syllabus
CSE2008 Syllabus
Uploaded by
ABHAY POTLURI 20BCI0017Copyright:
Available Formats
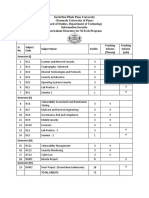
CSE2008 NETWORK SECURITY L T P J C
3 0 0 4 4
Pre-requisite Nil Syllabus version
1.0
Course Objectives:
1. To develop a fundamental understanding of computer and network security proper practices,
policies, technologies and standards
2.To impart familiarity with the security techniques that provide information and network security
3.To enable to evaluate the security of communication systems networks and protocols based on a
multitude of security factors
Expected Course Outcome:
1. Describe computer and network security fundamental concepts and principles.
2.Identify and assess different types of threats, malware, spyware, viruses, vulnerabilities, and
today’s attacks such as social engineering, rootkit, and botnets
3.Describe the inner-workings of today’s real time communication security, e-mail security and
wireless security
4.Demonstrate the ability to select among available network security technology and protocols such
as IDS, IPS, firewalls, honeynets, SSL, SSH, IPSec, TLS, VPNs, etc..
Student Learning Outcomes (SLO): 1,2,10,14,17
Module:1 INTRODUCTION ON NETWORKING AND 7 hours
SECURITY
Access Control and Site Security- Virtual Local Area Network (VLAN), Demilitarized zone
(DMZ) ATTACKS, SERVICES MECHANISMS Attack Methods – TCP/IP Internetworking,
Security problems in TCP/IP protocol suite, BGP security attacks, DNS Cache poisoning, Denial of
Service (DoS) attacks, Distributed Denial of Service (DDoS) attacks, IP Trace back attacks
Module:2 REAL-TIME COMMUNICATION 8 hours
SECURITY
Introduction to TCP/IP protocol stack -Implementation layers for security protocols and
implications - IPsec: AH and ESP- IPsec: IKE- SSL/TLS- Distribution lists-Establishing keys-
Privacy, Source Authentication, Message Integrity, Non-Repudiation, Proof of Submission, Proof
of Delivery, Message Flow Confidentiality, Anonymity – Packet filters-Application level gateways.
Module:3 INTERNET CONTROL MESSAGE 5 hours
PROTOCOL (ICMP)
ICMP Messages - Attacks Using ICMP Messages - Reconnaissance Scanning - ICMP Sweep-
Traceroute - Firewalk - Inverse Mapping - OS Fingerprinting - Exploiting Systems - ICMP Route
Redirect - ICMP informational messages - ICMP Router Discovery Messages - ICMP Floods -
Smurf - Keeping Access Covering The Tracks
Module:4 ELECTRONIC MAIL SECURITY 5 hours
Pretty Good Privacy – PGP services – Transmission and Reception of PGP Messages – PGP
Message Generation – PGP Message Reception
Module:5 Web Security 4 hours
Threats on the web – Secure Socket Layer and Transport Layer Security:SSL architecture – SSL
record protocol – Handshake protocols
Module:6 Wireless Security 7 hours
SSID vulnerabilities, Hotspot vulnerabilities, Privacy and security issues in WiFi, WPA,
Wireless Intrusion Prevention System (WIPS), - Audit records - Viruses and related threats
–Security of data oriented and voice oriented wireless networks (GSM UMTS, other models)
IOT SECURITY Introduction –Application Space – IoT Security Issues – Hardware, Software
and Network Security Solutions – Security Analysis
Module:7 Network Defense Solutions 7 hours
Firewall, VPNs, Intrusion Detection and Prevention filters, Covert channels and counter measures
in communication protocols, Techniques for shielding applications from an untrusted environment,
Client and Server Security tools and applications
Module:8 Recent Trends 2 hours
Industry Expert talk
Total Lecture hours: 45 hours
Text Book(s)
1. W. Stallings, Cryptography and Network Security: Principles and Practice, 5th Ed. Boston:
Prentice Hall, 2010. (ISBN No.: 978-0-13-609704-4).
2 A. Das and C. VeniMadhavan, Public-key Cryptography: Theory and Practice. New Delhi,
India: Pearson Education India, 2009. (ISBN No. : 978-8-13-170832-3).
Reference Books
1. D. R. Stinson, Cryptography: Theory and Practice, 3rd Ed. Boca Raton, FL: Chapman
Hall/CRC, 2005. (ISBN No.: 978-1-58-488508-5 ).
2. M. Rhodes-Ousley, Network security the complete reference (complete reference), 2nd ed.
New York, USA: McGraw-Hill Professional Publishing, 2013. (ISBN No. :
978-1-59749-535-6)
3. C. Kaufman, R. Perlman, and M. Speciner, Network Security: Private Communication in a
Public World, 2nd Ed. United States: Prentice Hall PTR, 2002. (ISBN No.:
978-0-13-046019-6 ).
4. A. Kahate, Cryptography and Network Security, 3rd Ed. New Delhi: Tata McGraw-Hill
Education, 2003.(ISBN No. : 978-0-07-049483-1)
5. A. Basta and M. Zgola, Database Security, 1st Ed. Boston, MA: Delmar Cengage Learning,
2012. (ISBN No.: 978 - 1 – 4354 – 5390 – 6)
Mode of Evaluation: CAT / Assignment / Quiz / FAT / Project / Seminar
Mode of assessment: Project/Activity
Recommended by Board of Studies 28-02-2017
Approved by Academic Council No. 41 Date 16-03-2017
You might also like
- Online PDF Editor: How To Edit PDF Files Online For FreeDocument15 pagesOnline PDF Editor: How To Edit PDF Files Online For FreeTrandafir Georgiana100% (1)
- Chapter 14 Supply Chain ManagementDocument46 pagesChapter 14 Supply Chain Managementkatherine cabrera100% (1)
- Ite4001 Network-And-Information-security Eth 1.1 47 Ite4001Document2 pagesIte4001 Network-And-Information-security Eth 1.1 47 Ite4001Vivek GopalshettyNo ratings yet
- Ite4001 Network-And-Information-security Eth 1.1 47 Ite4001Document2 pagesIte4001 Network-And-Information-security Eth 1.1 47 Ite4001Prateek AgarwalNo ratings yet
- CNS Theory Syllabus PDFDocument3 pagesCNS Theory Syllabus PDFnootiNo ratings yet
- Bcse309l Cryptography-And-Network-Security TH 1.0 67 Bcse309lDocument3 pagesBcse309l Cryptography-And-Network-Security TH 1.0 67 Bcse309lMohnish KodukullaNo ratings yet
- Computer Security and Audit Assurance SyllabusDocument23 pagesComputer Security and Audit Assurance Syllabus20-6214 Nani DandaNo ratings yet
- Course Content - Information Security PDFDocument13 pagesCourse Content - Information Security PDFAvaneet RanjanNo ratings yet
- Pgdcs CurriculumDocument10 pagesPgdcs Curriculumindraveer_rnsNo ratings yet
- Lesson Plan-Ns2Document4 pagesLesson Plan-Ns2priyeshNo ratings yet
- Cyber SecurityDocument3 pagesCyber Securitysweta.jethava24460No ratings yet
- B.Tech. Computer: Uka Tarsadia UniversityDocument6 pagesB.Tech. Computer: Uka Tarsadia UniversityPatelNo ratings yet
- Syllabus - UCS005E-Information and Network SecurityDocument2 pagesSyllabus - UCS005E-Information and Network Security2BA17CS056 SANTHOSHNo ratings yet
- VIII Sem IT Syllabus 2021-22290322115311Document9 pagesVIII Sem IT Syllabus 2021-22290322115311Nikhil JainNo ratings yet
- Pune University IS Tech. SyllabusDocument9 pagesPune University IS Tech. SyllabusPav TechnicalsNo ratings yet
- EC3401 NETWORKS AND SECURITY SyllabusDocument2 pagesEC3401 NETWORKS AND SECURITY SyllabuspoornimaNo ratings yet
- Pis SyllabusDocument2 pagesPis SyllabusM.K BhaiNo ratings yet
- CNS - M1L0Document18 pagesCNS - M1L0Viraj KaleNo ratings yet
- System SecurityDocument4 pagesSystem SecurityTanishka MayekarNo ratings yet
- CSE Live SyllabusDocument18 pagesCSE Live SyllabusAkbar ShakoorNo ratings yet
- 20SCN13-Information Seccurity Group 2Document2 pages20SCN13-Information Seccurity Group 2Sharanu AmaragattiNo ratings yet
- Network Security SyllabusDocument2 pagesNetwork Security SyllabusanithaNo ratings yet
- Ec3401 Networks and Security SyllabusDocument3 pagesEc3401 Networks and Security Syllabusabinayasundaramoorthi2000No ratings yet
- Cyber and Information Security SyllDocument4 pagesCyber and Information Security Syllmm8871No ratings yet
- MCSCB Cyber SecurityDocument16 pagesMCSCB Cyber SecurityKrishna Kumaran ThampiNo ratings yet
- 202CS002-Information and Network Security.Document2 pages202CS002-Information and Network Security.keerthiksNo ratings yet
- CNS, Sec Lab, CF SyllabusDocument6 pagesCNS, Sec Lab, CF SyllabusGayathri DeviNo ratings yet
- CNCS2004-Cybersecurity SyllabusDocument3 pagesCNCS2004-Cybersecurity SyllabusZoyaNo ratings yet
- Computersecurity OutlineDocument5 pagesComputersecurity Outlineshifara TesfayeNo ratings yet
- MTech Cyber I and II Sem SyllabusDocument24 pagesMTech Cyber I and II Sem SyllabusDarmoni LaishramNo ratings yet
- Course Outline - Network Security-BESE-3AB-Fall15 - 2 PDFDocument5 pagesCourse Outline - Network Security-BESE-3AB-Fall15 - 2 PDFPriya SatyaniNo ratings yet
- Code: 2 2 0 4: Iii Year Sem-1 B.Tech Cse Elective L T P CDocument2 pagesCode: 2 2 0 4: Iii Year Sem-1 B.Tech Cse Elective L T P CArul SenthilNo ratings yet
- Department of Information Technology National Instiute of Technology SrinagarDocument11 pagesDepartment of Information Technology National Instiute of Technology SrinagarAMRITESHWAR MISHRANo ratings yet
- AU Security Course OutlineDocument3 pagesAU Security Course OutlinesamuelNo ratings yet
- Cse1011 Cryptography-Fundamentals Eth 1.0 46 Cse1011Document2 pagesCse1011 Cryptography-Fundamentals Eth 1.0 46 Cse1011Akshat AgarwalNo ratings yet
- SyllabusDocument2 pagesSyllabusdummyfr07No ratings yet
- CSS - Orientation TE SEM VI FH - 22Document17 pagesCSS - Orientation TE SEM VI FH - 22Atul ShintreNo ratings yet
- Course Outline SCS4110Document3 pagesCourse Outline SCS4110n02019697mNo ratings yet
- T.Y B.Tech - Open Elective - 2021Document13 pagesT.Y B.Tech - Open Elective - 2021markeloff d'souzaNo ratings yet
- Network Security and Cryptography: Course Code: 15Cs1105 Pre-Requisites: Computer NetworksDocument3 pagesNetwork Security and Cryptography: Course Code: 15Cs1105 Pre-Requisites: Computer Networks17131A05K1 SHAIK RESHMANo ratings yet
- W.E.F Academic Year 2012-13 G' SchemeDocument5 pagesW.E.F Academic Year 2012-13 G' SchemeSanket bhosaleNo ratings yet
- 4-1 SyllabusDocument6 pages4-1 Syllabusvenulucky951No ratings yet
- R18 B.Tech - CSE Syllabus IV Year - Removed - Removed - RemovedDocument8 pagesR18 B.Tech - CSE Syllabus IV Year - Removed - Removed - Removedshamshuddin MdNo ratings yet
- Information SecurityDocument11 pagesInformation SecurityAppin Technology LabNo ratings yet
- 8th Sem SyllabusDocument9 pages8th Sem SyllabusEngineer BhaiyaNo ratings yet
- Cryptography and Network SecurityDocument2 pagesCryptography and Network SecurityVishwa Pratap SinghNo ratings yet
- Ns and CryptographyDocument3 pagesNs and CryptographyKodanda Rama Durgarao PoluriNo ratings yet
- CSS (Computer System Security)Document162 pagesCSS (Computer System Security)Ashmit JaiswalNo ratings yet
- Scheme and Detailed Syllabus: M.Tech. Cyber SecurityDocument8 pagesScheme and Detailed Syllabus: M.Tech. Cyber SecurityNeeraj PatelNo ratings yet
- Cs808: Advanced Computer Networks (Acn)Document1 pageCs808: Advanced Computer Networks (Acn)Pavan KumarNo ratings yet
- HC S 412 Course Outline 2019Document3 pagesHC S 412 Course Outline 2019tgotora0% (1)
- The Cyber Security ProfessionalDocument9 pagesThe Cyber Security ProfessionalGreggNo ratings yet
- Information and Network SecurityDocument4 pagesInformation and Network SecurityMananNo ratings yet
- Title 5Document2 pagesTitle 5М. ЭнэрэлтNo ratings yet
- Class Notes 2Document1 pageClass Notes 2SPNo ratings yet
- MCA 2nd Year Syllabus Sem III and IV 120617 QDocument1 pageMCA 2nd Year Syllabus Sem III and IV 120617 QSPNo ratings yet
- 4 Year 1 Semester SyllabusDocument9 pages4 Year 1 Semester SyllabusYasham GhalibNo ratings yet
- System and Networks SecurityDocument3 pagesSystem and Networks Security123vidyaNo ratings yet
- Network CsDocument5 pagesNetwork Csnotsubhash2000No ratings yet
- PUMPSDocument16 pagesPUMPSPajarillaga Franz Erick QuintoNo ratings yet
- LLM Use CasesDocument8 pagesLLM Use CasesShakti ShoaibNo ratings yet
- TR AppDocument12 pagesTR AppK POP SUCKSNo ratings yet
- Box Transport MechanismDocument24 pagesBox Transport MechanismInzi Gardezi82% (39)
- MechatronicsDocument16 pagesMechatronicsBhargav KondisettyNo ratings yet
- MTZ-2011-07 The New Hyundai-Kia 1,0 L Three-Cylinder Gasoline Engine PDFDocument8 pagesMTZ-2011-07 The New Hyundai-Kia 1,0 L Three-Cylinder Gasoline Engine PDFMiguel Alfonso Ruiz MendezNo ratings yet
- ABB Price Book 30Document1 pageABB Price Book 30Ralph MunozNo ratings yet
- SM - Project Report - Group-11Document15 pagesSM - Project Report - Group-110463SanjanaNo ratings yet
- Focus On Medical Power Supplies: Custom Power Solutions System Integration CapabilitiesDocument3 pagesFocus On Medical Power Supplies: Custom Power Solutions System Integration CapabilitiesABD ENOUR BOUALOULNo ratings yet
- RRL - RevisionDocument4 pagesRRL - RevisionMish Lei FranxhNo ratings yet
- Module 4 Diesel CycleDocument11 pagesModule 4 Diesel CycleRalph Bernard Dela RosaNo ratings yet
- Inter Networking: WAN and Internet AccessDocument18 pagesInter Networking: WAN and Internet AccessmadunixNo ratings yet
- BCS 011 June 2016 PDFDocument3 pagesBCS 011 June 2016 PDFMaheshNo ratings yet
- AKASH Report SeminarDocument2 pagesAKASH Report SeminarNehaNo ratings yet
- Information System Technology Exam 1 Review QuestionsDocument17 pagesInformation System Technology Exam 1 Review QuestionsAbi FleischmannNo ratings yet
- 33 MFR 18 80lbs Mfs 18 50lbs Programme Error Codes 54 54Document68 pages33 MFR 18 80lbs Mfs 18 50lbs Programme Error Codes 54 54alejandro vilelaNo ratings yet
- Request For Expressions of Interest (Reoi) For Design and Supervision Consultancy Services For Rural Roads Upgrading in Ogun StateDocument17 pagesRequest For Expressions of Interest (Reoi) For Design and Supervision Consultancy Services For Rural Roads Upgrading in Ogun StateDuncan josefNo ratings yet
- A Brief Python Tutorial: Sven H. Chilton University of California - BerkeleyDocument44 pagesA Brief Python Tutorial: Sven H. Chilton University of California - Berkeleyaishwarya kalyanNo ratings yet
- 2423 SpecDocument50 pages2423 SpecAssistant EngineerNo ratings yet
- Roller Bogie Wireline Slickline Applications Slickline Roller Bogie Tools EnableDocument13 pagesRoller Bogie Wireline Slickline Applications Slickline Roller Bogie Tools EnableFranklin NavarroNo ratings yet
- BX Concentration ControlDocument205 pagesBX Concentration ControlnghiNo ratings yet
- Name: Olabamiji Saheed Olalekan Matric No: 15/69/0001 Project Proposal Topic: Drugs Information Management SystemDocument4 pagesName: Olabamiji Saheed Olalekan Matric No: 15/69/0001 Project Proposal Topic: Drugs Information Management SystemkolawoleNo ratings yet
- Seminar Presentation BCT 2401Document2 pagesSeminar Presentation BCT 2401justin naitiraNo ratings yet
- Sales TemplateDocument22 pagesSales TemplateBobby InsanaNo ratings yet
- 2A201-384E - M - Asteion4 Site PlanningDocument100 pages2A201-384E - M - Asteion4 Site Planningmedical serviceNo ratings yet
- Manual de Instalacion BASICDocument356 pagesManual de Instalacion BASICeudoNo ratings yet
- Input Data Sheet For E-Class Record: Region Division School Name School Id School Year AddressDocument29 pagesInput Data Sheet For E-Class Record: Region Division School Name School Id School Year AddressJeisha Shayne CurayagNo ratings yet
- Bpo2 PPT 3Document12 pagesBpo2 PPT 3Mary Lynn Dela PeñaNo ratings yet