Professional Documents
Culture Documents
Beyaz Şapkalı Hacker Eğitimi
Beyaz Şapkalı Hacker Eğitimi
Uploaded by
Soner ÇelikCopyright:
Available Formats
You might also like
- Az 305Document150 pagesAz 305Syafiq HaziqNo ratings yet
- CompTIA Security+ SY0-601 Exam Objectives (3.0)Document28 pagesCompTIA Security+ SY0-601 Exam Objectives (3.0)Treylan RNo ratings yet
- CompTIA Security (SY0-601) Exam ObjectivesDocument24 pagesCompTIA Security (SY0-601) Exam ObjectivesRoy Murillo100% (1)
- Comptia Security Sy0 601 Exam Objectives (2 0)Document24 pagesComptia Security Sy0 601 Exam Objectives (2 0)tha_flameNo ratings yet
- Ethical Hacking PPT Download4575Document21 pagesEthical Hacking PPT Download4575Gyan Prakash100% (2)
- Hacking ExposedDocument202 pagesHacking Exposedبوبيسكو كالينNo ratings yet
- The Certified Ethical Hacker Exam - version 8 (The concise study guide)From EverandThe Certified Ethical Hacker Exam - version 8 (The concise study guide)Rating: 3 out of 5 stars3/5 (9)
- Principles: Attendees Will Learn AboutDocument3 pagesPrinciples: Attendees Will Learn AboutRajNo ratings yet
- CEH Exam Blueprint v4.0: EC-CouncilDocument5 pagesCEH Exam Blueprint v4.0: EC-CouncilGustavoBuschNo ratings yet
- CEH Exam Blueprint v4.0: EC-CouncilDocument10 pagesCEH Exam Blueprint v4.0: EC-CouncilAnderson SilvaNo ratings yet
- Certified Ethical HackingDocument5 pagesCertified Ethical HackingOwen MasiberahNo ratings yet
- Why - Ethical Hacking: Social Engineering Automated Attacks Protection From Possible External AttacksDocument14 pagesWhy - Ethical Hacking: Social Engineering Automated Attacks Protection From Possible External AttacksfaizaNo ratings yet
- EC Council Certified Ethical Hacker CEH v9.0Document5 pagesEC Council Certified Ethical Hacker CEH v9.0Juan Ignacio Concha AguirreNo ratings yet
- Certified Ethical Hacker v9Document9 pagesCertified Ethical Hacker v9JJ Asonyer100% (1)
- Ethical Hacking Syllabus: Rooman Technologies PVT LTDDocument7 pagesEthical Hacking Syllabus: Rooman Technologies PVT LTDNepsonNo ratings yet
- CEHDocument6 pagesCEHmela4ever125No ratings yet
- Security: Concept, Threats (User, Data), MeasuresDocument23 pagesSecurity: Concept, Threats (User, Data), Measurespariyal malikNo ratings yet
- Security+ SY0-501 Exam ObjectivesDocument20 pagesSecurity+ SY0-501 Exam ObjectiveskasimNo ratings yet
- CompTIA SecurityPlus601 Objectives 1.0 Threats Attacks VulnerabilitiesDocument4 pagesCompTIA SecurityPlus601 Objectives 1.0 Threats Attacks VulnerabilitiesUdhaya kumar PNo ratings yet
- Introduction To Ethical HackingDocument4 pagesIntroduction To Ethical HackingPreethi PreethiNo ratings yet
- ANDROID?HACKERSDocument18 pagesANDROID?HACKERSRicardo Da Silva ZanataNo ratings yet
- Comptia Security Sy0 501 Exam ObjectivesDocument20 pagesComptia Security Sy0 501 Exam ObjectivesHans Joshep O'BrienNo ratings yet
- Mobile Device Security: Somesh Sawhney Sales Director - META & India Rohit Sinha Technical Director - META & IndiaDocument15 pagesMobile Device Security: Somesh Sawhney Sales Director - META & India Rohit Sinha Technical Director - META & IndiaKaran OjhaNo ratings yet
- Certified Ethical Hacking v9: EC-Council CEH Training PhilippinesDocument6 pagesCertified Ethical Hacking v9: EC-Council CEH Training PhilippinesjdgregorioNo ratings yet
- CEH Exam Blueprint 3.0: EC-CouncilDocument5 pagesCEH Exam Blueprint 3.0: EC-CouncilYONIWO EDWARD TSEMINo ratings yet
- Cyber Security PathwayDocument1 pageCyber Security Pathwaysphaart12No ratings yet
- Challenges in The Digital WorldDocument4 pagesChallenges in The Digital WorldJames Matthew BedayoNo ratings yet
- Intrusion Detection/Prevention SystemsDocument29 pagesIntrusion Detection/Prevention SystemsDereje Chinkl100% (1)
- 1 - Info Security and Cyber Security FundamentalsDocument5 pages1 - Info Security and Cyber Security Fundamentalsshimaa ashrafNo ratings yet
- Comptia Security Sy0 601 Exam Objectives (6 0)Document24 pagesComptia Security Sy0 601 Exam Objectives (6 0)Erick CamiloNo ratings yet
- CEHv10 Course OutlineDocument46 pagesCEHv10 Course OutlineNaitik Haiking0% (1)
- Hacking Techniques: Asst Professor - Anindita Malik Department of Forensic Science Lovely Professional ScienceDocument17 pagesHacking Techniques: Asst Professor - Anindita Malik Department of Forensic Science Lovely Professional ScienceMaithiliNo ratings yet
- Security + Category Chart (SYO-401)Document31 pagesSecurity + Category Chart (SYO-401)Klayton DorseyNo ratings yet
- Information About Ethical HackingDocument2 pagesInformation About Ethical HackingSoham SawantNo ratings yet
- CISSP, CISA, CISM, GIAC, CCNA, Security +Document1 pageCISSP, CISA, CISM, GIAC, CCNA, Security +Ali AdamNo ratings yet
- Ids Tech2Document13 pagesIds Tech2dhammdips304No ratings yet
- Cyber Threat IntelligenceDocument41 pagesCyber Threat Intelligencekt06121999No ratings yet
- Certified Information Security Expert (CISE Level 1 v2) Detailed Course ModuleDocument18 pagesCertified Information Security Expert (CISE Level 1 v2) Detailed Course ModuleAkhil SreenadhNo ratings yet
- Ethical Hacking V9: DescriptionDocument5 pagesEthical Hacking V9: DescriptionramanaNo ratings yet
- Chapter 2 - Information Security MechanismsDocument93 pagesChapter 2 - Information Security MechanismsVako VeiiNo ratings yet
- Certified Information Security Expert (CISE Level 1 v2) Detailed Course ModuleDocument18 pagesCertified Information Security Expert (CISE Level 1 v2) Detailed Course ModuleAmila KulathungaNo ratings yet
- Cyberthreya Elite MasteryDocument17 pagesCyberthreya Elite MasteryPa1No ratings yet
- Trend Micro Deep Discovery InspectorDocument3 pagesTrend Micro Deep Discovery InspectorhaivadiNo ratings yet
- 03.bobak Group IB Portfolio UpdateDocument32 pages03.bobak Group IB Portfolio Updateericstevens77777No ratings yet
- Ethical HackingDocument170 pagesEthical Hackingkaran128100% (1)
- CSIA ReviewerDocument5 pagesCSIA ReviewerNyrl TavitaNo ratings yet
- An Introduction To Hacking and Cyber SecurityDocument19 pagesAn Introduction To Hacking and Cyber SecurityArjav JainNo ratings yet
- Informing Cyber Threat Intelligence Through Dark Web SituationalDocument10 pagesInforming Cyber Threat Intelligence Through Dark Web SituationalshangNo ratings yet
- EC-Council Certified Ethical Hacker (CEH) v.12 Courses - New HorizonsDocument7 pagesEC-Council Certified Ethical Hacker (CEH) v.12 Courses - New Horizonsdaliodsouza1019No ratings yet
- Chap 1Document24 pagesChap 1RVCE EIENo ratings yet
- Honeypot Vicky1Document42 pagesHoneypot Vicky1vickyNo ratings yet
- Ethical HackingDocument30 pagesEthical Hackingszc18enxx2No ratings yet
- Cyber Security Vendor LandscapeDocument4 pagesCyber Security Vendor Landscapejags_mcp100% (1)
- 3.1. LECTURE PPT - FootprintingDocument15 pages3.1. LECTURE PPT - FootprintingVictor udorjiNo ratings yet
- Honeypots & Honeynets: Tech TalkDocument16 pagesHoneypots & Honeynets: Tech Talkthaidt229No ratings yet
- Cyber Security ApponixDocument4 pagesCyber Security ApponixAshokNo ratings yet
- Fall Semester 2023-24 CSE2011 ETH AP2023242000177 Reference Material I 01-Aug-2023 Introduction Chapter 1Document60 pagesFall Semester 2023-24 CSE2011 ETH AP2023242000177 Reference Material I 01-Aug-2023 Introduction Chapter 1Himanshu SanadhyaNo ratings yet
- MDR Flyer - Threat ManagementDocument2 pagesMDR Flyer - Threat ManagementDasha DeckwerthNo ratings yet
- Cyber Espionage, Infiltration and Combating Techniques: - by Atul Agarwal & CERT-INDocument22 pagesCyber Espionage, Infiltration and Combating Techniques: - by Atul Agarwal & CERT-INyawahabNo ratings yet
- Your System's Sweetspots: CEO's Advice on Basic Cyber Security: CEO's Advice on Computer ScienceFrom EverandYour System's Sweetspots: CEO's Advice on Basic Cyber Security: CEO's Advice on Computer ScienceNo ratings yet
- D67016GC20 Exadata Workshop Part2Document150 pagesD67016GC20 Exadata Workshop Part2Nik20132013No ratings yet
- Di Audio Datasheet X Npmien54 En1 2Document2 pagesDi Audio Datasheet X Npmien54 En1 2Bryan BayacaNo ratings yet
- TANCET MCA Model Paper With Answers 1Document12 pagesTANCET MCA Model Paper With Answers 1TK5013100% (2)
- IR Jammer 1 0Document24 pagesIR Jammer 1 01234567890awsNo ratings yet
- EE236 - Chapter 2Document141 pagesEE236 - Chapter 2S AlshNo ratings yet
- PPL Unit 1 NotesDocument31 pagesPPL Unit 1 NotesIndhu RithikNo ratings yet
- DEA 2342 Basic of Electronic Engineering: Lab Sheet 4Document6 pagesDEA 2342 Basic of Electronic Engineering: Lab Sheet 4Afieza TumijanNo ratings yet
- C# Collections and GenericsDocument40 pagesC# Collections and Genericstim tomNo ratings yet
- GettingStartedenUS en USDocument242 pagesGettingStartedenUS en USKadir BoyluNo ratings yet
- Code PCMDocument9 pagesCode PCMMehdi HsseinNo ratings yet
- IGBT Intelligent PwrMods SerbanDocument18 pagesIGBT Intelligent PwrMods SerbanjaphlmsNo ratings yet
- MaintenanceDocument58 pagesMaintenancedineshkbunker08No ratings yet
- Textbook Windows Server 2016 Unleashed 1St Edition Coll Ebook All Chapter PDFDocument53 pagesTextbook Windows Server 2016 Unleashed 1St Edition Coll Ebook All Chapter PDFeric.huether323100% (3)
- Project Report of The Network Design and Implementation For A Media CompanyDocument124 pagesProject Report of The Network Design and Implementation For A Media CompanySsenyonga JeromeNo ratings yet
- Universal Kit For Split Inverter Air ConditionerDocument48 pagesUniversal Kit For Split Inverter Air Conditionerniltoncebra100% (1)
- Experiment 1Document4 pagesExperiment 1Santosh JoshiNo ratings yet
- Deplyser ReportDocument69 pagesDeplyser ReportPriyaranjan RajNo ratings yet
- MS2420 / MS2430: Installation and User's GuideDocument81 pagesMS2420 / MS2430: Installation and User's GuideMauricio MatuteNo ratings yet
- Software Requirements Specification Format Fit India Mini ProjectDocument4 pagesSoftware Requirements Specification Format Fit India Mini ProjectRAMESH PATELNo ratings yet
- Sybase Adaptive Server Enterprise 12Document2 pagesSybase Adaptive Server Enterprise 12CxHNo ratings yet
- Product Data Sheet: APC Smart-UPS RT 6000VA, 230V, 8x IEC 60320 C13 & 4x IEC Jumpers & 2x IEC 60320 C19 OutletsDocument4 pagesProduct Data Sheet: APC Smart-UPS RT 6000VA, 230V, 8x IEC 60320 C13 & 4x IEC Jumpers & 2x IEC 60320 C19 OutletsOsvaldo Leonardo LetowskiNo ratings yet
- Smart MirrorDocument12 pagesSmart MirrorDaman Deep Singh ArnejaNo ratings yet
- Java Script AssignmentDocument7 pagesJava Script Assignmenthanima4No ratings yet
- SNA-486 Markcode S4Document5 pagesSNA-486 Markcode S4CharlesNo ratings yet
- Chapter 3 - Arrays - ControllingFlowDocument47 pagesChapter 3 - Arrays - ControllingFlowamin khalilianNo ratings yet
- ULN2065Document12 pagesULN2065Ishaq BhattiNo ratings yet
- g200 MmsDocument4 pagesg200 MmsazzszoNo ratings yet
- On Load Tap ChangerDocument2 pagesOn Load Tap Changerashish_patel111No ratings yet
- In Mmwave 5G Validation TestDocument36 pagesIn Mmwave 5G Validation TestPetros TsenesNo ratings yet
Beyaz Şapkalı Hacker Eğitimi
Beyaz Şapkalı Hacker Eğitimi
Uploaded by
Soner ÇelikOriginal Description:
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Beyaz Şapkalı Hacker Eğitimi
Beyaz Şapkalı Hacker Eğitimi
Uploaded by
Soner ÇelikCopyright:
Available Formats
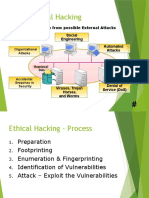
Topic Details
Information Security and Ethical Hacking Overview
- Information Security Overview
- Cyber Kill Chain Concepts
Introduction to Ethical - Hacking Concepts
Hacking - Ethical Hacking Concepts
- Information Security Controls
- Information Security Laws and Standards
Reconnaissance Techniques
- Footprinting Concepts
- Footprinting Methodology
- Footprinting through Search Engines
- Footprinting through Web Services
- Footprinting through Social Networking Sites
- Website Footprinting
Footprinting and
- Email Footprinting
Reconnaissance
- Whois Footprinting
- DNS Footprinting
- Network Footprinting
- Footprinting through Social Engineering
- Footprinting Tools
- Footprinting Countermeasures
- Network Scanning Concepts
- Scanning Tools
- Host Discovery
Scanning Networks - Port and Service Discovery
- OS Discovery (Banner Grabbing/OS Fingerprinting)
- Scanning Beyond IDS and Firewall
- Draw Network Diagrams
- Enumeration Concepts
- NetBIOS Enumeration
- SNMP Enumeration
- LDAP Enumeration
Enumeration - NTP and NFS Enumeration
- SMTP and DNS Enumeration
- Other Enumeration Techniques (IPsec, VoIP, RPC, Unix/Linux,
Telnet, FTP, TFTP, SMB, IPv6, and BGP enumeration)
- Enumeration Countermeasures
System Hacking Phases and Attack Techniques
- Vulnerability Assessment Concepts
- Vulnerability Classification and Assessment Types
Vulnerability Analysis
- Vulnerability Assessment Solutions and Tools
- Vulnerability Assessment Reports
System Hacking - System Hacking Concepts
- Gaining Access
- Cracking Passwords
- Vulnerability Exploitation
- Escalating Privileges
- Maintaining Access
- Executing Applications
- Hiding Files
- Clearing Logs
- Malware Concepts
- APT Concepts
- Trojan Concepts
- Virus and Worm Concepts
Malware Threats
- File-less Malware Concepts
- Malware Analysis
- Malware Countermeasures
- Anti-Malware Software
Network and Perimeter Hacking
- Sniffing Concepts
- Sniffing Technique: MAC Attacks
- Sniffing Technique: DHCP Attacks
- Sniffing Technique: ARP Poisoning
Sniffing - Sniffing Technique: Spoofing Attacks
- Sniffing Technique: DNS Poisoning
- Sniffing Tools
- Sniffing Countermeasures
- Sniffing Detection Techniques
- Social Engineering Concepts
- Social Engineering Techniques
- Insider Threats
Social Engineering - Impersonation on Social
- Networking Sites
- Identity Theft
- Social Engineering Countermeasures
- DoS/DDoS Concepts
- DoS/DDoS Attack Techniques
- Botnets
- DDoS
Denial-of-Service
- Case Study
- DoS/DDoS Attack Tools
- DoS/DDoS Countermeasures
- DoS/DDoS Protection Tools
- Session Hijacking Concepts
- Application Level Session Hijacking
Session Hijacking - Network Level Session Hijacking
- Session Hijacking Tools
- Session Hijacking Countermeasures
- IDS, IPS, Firewall, and Honeypot Concepts
- IDS, IPS, Firewall, and Honeypot Solutions
- Evading IDS
Evading IDS, Firewalls, and
- Evading Firewalls
Honeypots
- IDS/Firewall Evading Tools
- Detecting Honeypots
- IDS/Firewall Evasion Countermeasures
Web Application Hacking
Hacking Web Servers - Web Server Concepts
- Web Server Attacks
- Web Server Attack Methodology
- Web Server Attack Tools
- Web Server Countermeasures
- Patch Management
- Web Server Security Tools
- Web App Concepts
- Web App Threats
- Web App Hacking Methodology
- Footprint Web Infrastructure
- Analyze Web Applications
- Bypass Client-Side Controls
- Attack Authentication Mechanism
- Attack Authorization Schemes
- Attack Access Controls
Hacking Web Applications
- Attack Session Management Mechanism
- Perform Injection Attacks
- Attack Application Logic Flaws
- Attack Shared Environments
- Attack Database Connectivity
- Attack Web App Client
- Attack Web Services
- Web API, Webhooks and Web Shell
- Web App Security
- SQL Injection Concepts
- Types of SQL Injection
- SQL Injection Methodology
SQL Injection
- SQL Injection Tools
- Evasion Techniques
- SQL Injection Countermeasures
Wireless Network Hacking
- Wireless Concepts
- Wireless Encryption
- Wireless Threats
- Wireless Hacking Methodology
Hacking Wireless Networks
- Wireless Hacking Tools
- Bluetooth Hacking
- Wireless Countermeasures
- Wireless Security Tools
Mobile Platform, IoT, and OT Hacking
- Mobile Platform Attack Vectors
- Hacking Android OS
Hacking Mobile Platforms - Hacking iOS
- Mobile Device Management
- Mobile Security Guidelines and Tools
IoT and OT Hacking - IoT Concepts
- IoT Attacks
- IoT Hacking Methodology
- IoT Hacking Tools
- IoT Countermeasures
- OT Concepts
- OT Attacks
- OT Hacking Methodology
- OT Hacking Tools
- OT Countermeasures
Cloud Computing
- Cloud Computing Concepts
- Container Technology
- Serverless Computing
Cloud Computing
- Cloud Computing Threats
- Cloud Hacking
- Cloud Security
Cryptography
- Cryptography Concepts
- Encryption Algorithms
- Cryptography Tools
- Public Key Infrastructure (PKI)
Cryptography
- Email Encryption
- Disk Encryption
- Cryptanalysis
- Countermeasures
You might also like
- Az 305Document150 pagesAz 305Syafiq HaziqNo ratings yet
- CompTIA Security+ SY0-601 Exam Objectives (3.0)Document28 pagesCompTIA Security+ SY0-601 Exam Objectives (3.0)Treylan RNo ratings yet
- CompTIA Security (SY0-601) Exam ObjectivesDocument24 pagesCompTIA Security (SY0-601) Exam ObjectivesRoy Murillo100% (1)
- Comptia Security Sy0 601 Exam Objectives (2 0)Document24 pagesComptia Security Sy0 601 Exam Objectives (2 0)tha_flameNo ratings yet
- Ethical Hacking PPT Download4575Document21 pagesEthical Hacking PPT Download4575Gyan Prakash100% (2)
- Hacking ExposedDocument202 pagesHacking Exposedبوبيسكو كالينNo ratings yet
- The Certified Ethical Hacker Exam - version 8 (The concise study guide)From EverandThe Certified Ethical Hacker Exam - version 8 (The concise study guide)Rating: 3 out of 5 stars3/5 (9)
- Principles: Attendees Will Learn AboutDocument3 pagesPrinciples: Attendees Will Learn AboutRajNo ratings yet
- CEH Exam Blueprint v4.0: EC-CouncilDocument5 pagesCEH Exam Blueprint v4.0: EC-CouncilGustavoBuschNo ratings yet
- CEH Exam Blueprint v4.0: EC-CouncilDocument10 pagesCEH Exam Blueprint v4.0: EC-CouncilAnderson SilvaNo ratings yet
- Certified Ethical HackingDocument5 pagesCertified Ethical HackingOwen MasiberahNo ratings yet
- Why - Ethical Hacking: Social Engineering Automated Attacks Protection From Possible External AttacksDocument14 pagesWhy - Ethical Hacking: Social Engineering Automated Attacks Protection From Possible External AttacksfaizaNo ratings yet
- EC Council Certified Ethical Hacker CEH v9.0Document5 pagesEC Council Certified Ethical Hacker CEH v9.0Juan Ignacio Concha AguirreNo ratings yet
- Certified Ethical Hacker v9Document9 pagesCertified Ethical Hacker v9JJ Asonyer100% (1)
- Ethical Hacking Syllabus: Rooman Technologies PVT LTDDocument7 pagesEthical Hacking Syllabus: Rooman Technologies PVT LTDNepsonNo ratings yet
- CEHDocument6 pagesCEHmela4ever125No ratings yet
- Security: Concept, Threats (User, Data), MeasuresDocument23 pagesSecurity: Concept, Threats (User, Data), Measurespariyal malikNo ratings yet
- Security+ SY0-501 Exam ObjectivesDocument20 pagesSecurity+ SY0-501 Exam ObjectiveskasimNo ratings yet
- CompTIA SecurityPlus601 Objectives 1.0 Threats Attacks VulnerabilitiesDocument4 pagesCompTIA SecurityPlus601 Objectives 1.0 Threats Attacks VulnerabilitiesUdhaya kumar PNo ratings yet
- Introduction To Ethical HackingDocument4 pagesIntroduction To Ethical HackingPreethi PreethiNo ratings yet
- ANDROID?HACKERSDocument18 pagesANDROID?HACKERSRicardo Da Silva ZanataNo ratings yet
- Comptia Security Sy0 501 Exam ObjectivesDocument20 pagesComptia Security Sy0 501 Exam ObjectivesHans Joshep O'BrienNo ratings yet
- Mobile Device Security: Somesh Sawhney Sales Director - META & India Rohit Sinha Technical Director - META & IndiaDocument15 pagesMobile Device Security: Somesh Sawhney Sales Director - META & India Rohit Sinha Technical Director - META & IndiaKaran OjhaNo ratings yet
- Certified Ethical Hacking v9: EC-Council CEH Training PhilippinesDocument6 pagesCertified Ethical Hacking v9: EC-Council CEH Training PhilippinesjdgregorioNo ratings yet
- CEH Exam Blueprint 3.0: EC-CouncilDocument5 pagesCEH Exam Blueprint 3.0: EC-CouncilYONIWO EDWARD TSEMINo ratings yet
- Cyber Security PathwayDocument1 pageCyber Security Pathwaysphaart12No ratings yet
- Challenges in The Digital WorldDocument4 pagesChallenges in The Digital WorldJames Matthew BedayoNo ratings yet
- Intrusion Detection/Prevention SystemsDocument29 pagesIntrusion Detection/Prevention SystemsDereje Chinkl100% (1)
- 1 - Info Security and Cyber Security FundamentalsDocument5 pages1 - Info Security and Cyber Security Fundamentalsshimaa ashrafNo ratings yet
- Comptia Security Sy0 601 Exam Objectives (6 0)Document24 pagesComptia Security Sy0 601 Exam Objectives (6 0)Erick CamiloNo ratings yet
- CEHv10 Course OutlineDocument46 pagesCEHv10 Course OutlineNaitik Haiking0% (1)
- Hacking Techniques: Asst Professor - Anindita Malik Department of Forensic Science Lovely Professional ScienceDocument17 pagesHacking Techniques: Asst Professor - Anindita Malik Department of Forensic Science Lovely Professional ScienceMaithiliNo ratings yet
- Security + Category Chart (SYO-401)Document31 pagesSecurity + Category Chart (SYO-401)Klayton DorseyNo ratings yet
- Information About Ethical HackingDocument2 pagesInformation About Ethical HackingSoham SawantNo ratings yet
- CISSP, CISA, CISM, GIAC, CCNA, Security +Document1 pageCISSP, CISA, CISM, GIAC, CCNA, Security +Ali AdamNo ratings yet
- Ids Tech2Document13 pagesIds Tech2dhammdips304No ratings yet
- Cyber Threat IntelligenceDocument41 pagesCyber Threat Intelligencekt06121999No ratings yet
- Certified Information Security Expert (CISE Level 1 v2) Detailed Course ModuleDocument18 pagesCertified Information Security Expert (CISE Level 1 v2) Detailed Course ModuleAkhil SreenadhNo ratings yet
- Ethical Hacking V9: DescriptionDocument5 pagesEthical Hacking V9: DescriptionramanaNo ratings yet
- Chapter 2 - Information Security MechanismsDocument93 pagesChapter 2 - Information Security MechanismsVako VeiiNo ratings yet
- Certified Information Security Expert (CISE Level 1 v2) Detailed Course ModuleDocument18 pagesCertified Information Security Expert (CISE Level 1 v2) Detailed Course ModuleAmila KulathungaNo ratings yet
- Cyberthreya Elite MasteryDocument17 pagesCyberthreya Elite MasteryPa1No ratings yet
- Trend Micro Deep Discovery InspectorDocument3 pagesTrend Micro Deep Discovery InspectorhaivadiNo ratings yet
- 03.bobak Group IB Portfolio UpdateDocument32 pages03.bobak Group IB Portfolio Updateericstevens77777No ratings yet
- Ethical HackingDocument170 pagesEthical Hackingkaran128100% (1)
- CSIA ReviewerDocument5 pagesCSIA ReviewerNyrl TavitaNo ratings yet
- An Introduction To Hacking and Cyber SecurityDocument19 pagesAn Introduction To Hacking and Cyber SecurityArjav JainNo ratings yet
- Informing Cyber Threat Intelligence Through Dark Web SituationalDocument10 pagesInforming Cyber Threat Intelligence Through Dark Web SituationalshangNo ratings yet
- EC-Council Certified Ethical Hacker (CEH) v.12 Courses - New HorizonsDocument7 pagesEC-Council Certified Ethical Hacker (CEH) v.12 Courses - New Horizonsdaliodsouza1019No ratings yet
- Chap 1Document24 pagesChap 1RVCE EIENo ratings yet
- Honeypot Vicky1Document42 pagesHoneypot Vicky1vickyNo ratings yet
- Ethical HackingDocument30 pagesEthical Hackingszc18enxx2No ratings yet
- Cyber Security Vendor LandscapeDocument4 pagesCyber Security Vendor Landscapejags_mcp100% (1)
- 3.1. LECTURE PPT - FootprintingDocument15 pages3.1. LECTURE PPT - FootprintingVictor udorjiNo ratings yet
- Honeypots & Honeynets: Tech TalkDocument16 pagesHoneypots & Honeynets: Tech Talkthaidt229No ratings yet
- Cyber Security ApponixDocument4 pagesCyber Security ApponixAshokNo ratings yet
- Fall Semester 2023-24 CSE2011 ETH AP2023242000177 Reference Material I 01-Aug-2023 Introduction Chapter 1Document60 pagesFall Semester 2023-24 CSE2011 ETH AP2023242000177 Reference Material I 01-Aug-2023 Introduction Chapter 1Himanshu SanadhyaNo ratings yet
- MDR Flyer - Threat ManagementDocument2 pagesMDR Flyer - Threat ManagementDasha DeckwerthNo ratings yet
- Cyber Espionage, Infiltration and Combating Techniques: - by Atul Agarwal & CERT-INDocument22 pagesCyber Espionage, Infiltration and Combating Techniques: - by Atul Agarwal & CERT-INyawahabNo ratings yet
- Your System's Sweetspots: CEO's Advice on Basic Cyber Security: CEO's Advice on Computer ScienceFrom EverandYour System's Sweetspots: CEO's Advice on Basic Cyber Security: CEO's Advice on Computer ScienceNo ratings yet
- D67016GC20 Exadata Workshop Part2Document150 pagesD67016GC20 Exadata Workshop Part2Nik20132013No ratings yet
- Di Audio Datasheet X Npmien54 En1 2Document2 pagesDi Audio Datasheet X Npmien54 En1 2Bryan BayacaNo ratings yet
- TANCET MCA Model Paper With Answers 1Document12 pagesTANCET MCA Model Paper With Answers 1TK5013100% (2)
- IR Jammer 1 0Document24 pagesIR Jammer 1 01234567890awsNo ratings yet
- EE236 - Chapter 2Document141 pagesEE236 - Chapter 2S AlshNo ratings yet
- PPL Unit 1 NotesDocument31 pagesPPL Unit 1 NotesIndhu RithikNo ratings yet
- DEA 2342 Basic of Electronic Engineering: Lab Sheet 4Document6 pagesDEA 2342 Basic of Electronic Engineering: Lab Sheet 4Afieza TumijanNo ratings yet
- C# Collections and GenericsDocument40 pagesC# Collections and Genericstim tomNo ratings yet
- GettingStartedenUS en USDocument242 pagesGettingStartedenUS en USKadir BoyluNo ratings yet
- Code PCMDocument9 pagesCode PCMMehdi HsseinNo ratings yet
- IGBT Intelligent PwrMods SerbanDocument18 pagesIGBT Intelligent PwrMods SerbanjaphlmsNo ratings yet
- MaintenanceDocument58 pagesMaintenancedineshkbunker08No ratings yet
- Textbook Windows Server 2016 Unleashed 1St Edition Coll Ebook All Chapter PDFDocument53 pagesTextbook Windows Server 2016 Unleashed 1St Edition Coll Ebook All Chapter PDFeric.huether323100% (3)
- Project Report of The Network Design and Implementation For A Media CompanyDocument124 pagesProject Report of The Network Design and Implementation For A Media CompanySsenyonga JeromeNo ratings yet
- Universal Kit For Split Inverter Air ConditionerDocument48 pagesUniversal Kit For Split Inverter Air Conditionerniltoncebra100% (1)
- Experiment 1Document4 pagesExperiment 1Santosh JoshiNo ratings yet
- Deplyser ReportDocument69 pagesDeplyser ReportPriyaranjan RajNo ratings yet
- MS2420 / MS2430: Installation and User's GuideDocument81 pagesMS2420 / MS2430: Installation and User's GuideMauricio MatuteNo ratings yet
- Software Requirements Specification Format Fit India Mini ProjectDocument4 pagesSoftware Requirements Specification Format Fit India Mini ProjectRAMESH PATELNo ratings yet
- Sybase Adaptive Server Enterprise 12Document2 pagesSybase Adaptive Server Enterprise 12CxHNo ratings yet
- Product Data Sheet: APC Smart-UPS RT 6000VA, 230V, 8x IEC 60320 C13 & 4x IEC Jumpers & 2x IEC 60320 C19 OutletsDocument4 pagesProduct Data Sheet: APC Smart-UPS RT 6000VA, 230V, 8x IEC 60320 C13 & 4x IEC Jumpers & 2x IEC 60320 C19 OutletsOsvaldo Leonardo LetowskiNo ratings yet
- Smart MirrorDocument12 pagesSmart MirrorDaman Deep Singh ArnejaNo ratings yet
- Java Script AssignmentDocument7 pagesJava Script Assignmenthanima4No ratings yet
- SNA-486 Markcode S4Document5 pagesSNA-486 Markcode S4CharlesNo ratings yet
- Chapter 3 - Arrays - ControllingFlowDocument47 pagesChapter 3 - Arrays - ControllingFlowamin khalilianNo ratings yet
- ULN2065Document12 pagesULN2065Ishaq BhattiNo ratings yet
- g200 MmsDocument4 pagesg200 MmsazzszoNo ratings yet
- On Load Tap ChangerDocument2 pagesOn Load Tap Changerashish_patel111No ratings yet
- In Mmwave 5G Validation TestDocument36 pagesIn Mmwave 5G Validation TestPetros TsenesNo ratings yet