Professional Documents
Culture Documents
Jntuh College of Engineering Hyderabad Dept of Computer Science and Engineering
Jntuh College of Engineering Hyderabad Dept of Computer Science and Engineering
Uploaded by
sidOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Jntuh College of Engineering Hyderabad Dept of Computer Science and Engineering
Jntuh College of Engineering Hyderabad Dept of Computer Science and Engineering
Uploaded by
sidCopyright:
Available Formats
JNTUH COLLEGE OF ENGINEERING HYDERABAD
Dept of Computer Science and Engineering
IV Year B.Tech. CSE I-Sem B. Tech. (Computer Science) - IDDMP
SECURITY IN COMPUTING
Unit I
Security Problem in Computing
Computer Security, Threats, Attacks, Computer Criminals, Defense Methods,
Cryptography
Symmetric and Public-key Encryption, Uses of Encryption.
Unit II
Program Security
Secure Programs, Viruses and other Malicious Code, Control against Program Threats
Protection in General-Purpose OS
Protected Objects and Methods of Protection, Memory and Address Protection, Control of Access to General
Objects, File Protection Mechanism, User Authentication.
Unit III
Designing Trusted OS
What is Trusted System?, Security Policies, Models of Security, Trusted Operating System Design
Database and Data Mining Security
Security Requirements, Reliability and Integrity, Sensitive Data, Inference, Multilevel Databases, Proposals
for Multilevel Security, Data Mining
Unit IV
Security in Networks
Threats in Networks, Network Security Controls, Firewalls, Intrusion Detection System, Secure E-Mail
Administering Security
Security Planning, Organizational Security Policies, Physical Security
Economics of Cybersecurity
Quantifying Security, Modeling Cybersecurity, Current Research and Future directions
Unit V
Privacy in Computing
Privacy Concepts, Privacy Principles and Policies, Authentication and Privacy, Privacy on the Web
Legal and Ethical Issues in Computer Security
Protecting Programs and Data, Computer Crime, Ethical Issues in Computer Security, Case Studies of Ethics
Security in Service-Oriented Architecture (SOA)
Web Services, XML Firewalls
Prescribed Text Book
C. P. Fleeger and S. L. Fleeger, Security in Computing, Pears
Department of Computer Engineering
Course Plan
Academic year 2020-21
(Faculty: B SIDDARTH )
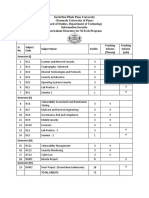
3. Course Plan/Schedule:
No. of
S. No. Topics / Sub. Topics / Experiments Classes Remarks
Estimated
1 UNIT I 2
Security Problem in Computing
Computer Security, Threats, Attacks,
Computer Criminals, Defense
Methods,
2 Cryptography 2
Symmetric and Public-key
Encryption, Uses of Encryption.
3 1
Uses of Encryption.
4 UNIT II 2
Program Security
Secure Programs, Viruses and other
Malicious Code, Control against
Program Threats
5 2
Protection in General-Purpose OS
Protected Objects and Methods
of Protection, Memory and
Address Protection
6 Control of Access to General Objects, 1
File Protection Mechanism, User
Authentication.
UNIT III 2
7
Designing Trusted OS
What is Trusted System?, Security
Policies, Models of Security, Trusted
Operating System Design
8 2
Database and Data Mining Security
Security Requirements, Reliability
and Integrity, Sensitive Data,
Inference, Multilevel Databases,
Proposals for Multilevel Security,
Data Mining
9 Unit IV 2
Security in Networks
Threats in Networks, Network
Security Controls, Firewalls, Intrusion
Detection System, Secure E-Mail
10 Administering Security 2
Security Planning, Organizational
Security Policies, Physical Security
11 1
Economics of Cybersecurity
Quantifying Security, Modeling
Cybersecurity, Current Research and
Future directions
12 Unit V 2
Privacy in Computing
Privacy Concepts, Privacy Principles
and Policies, Authentication and
Privacy, Privacy on the Web
13 Legal and Ethical Issues in 2
Computer Security
Protecting Programs and Data,
Computer Crime, Ethical Issues in
Computer Security, Case Studies of
Ethics
14 Security in Service-Oriented 2
Architecture (SOA)
Web Services, XML Firewalls
You might also like
- Firewall V 18Document5 pagesFirewall V 18mustafa ayaydin0% (4)
- Computer Security Lecture Plan MCA-505: Unit Topic Hours RequiredDocument2 pagesComputer Security Lecture Plan MCA-505: Unit Topic Hours RequiredAnonymous nDBwyakhNo ratings yet
- W.E.F Academic Year 2012-13 G' SchemeDocument5 pagesW.E.F Academic Year 2012-13 G' SchemeSanket bhosaleNo ratings yet
- System SecurityDocument4 pagesSystem SecurityTanishka MayekarNo ratings yet
- Lesson PlanDocument2 pagesLesson Plandanish_83No ratings yet
- CNCS2004-Cybersecurity SyllabusDocument3 pagesCNCS2004-Cybersecurity SyllabusZoyaNo ratings yet
- Lesson 1493761882Document1 pageLesson 1493761882santhi saranyaNo ratings yet
- BE - IT CBCS VII & VIII Syllabus - Information Security-CbitDocument2 pagesBE - IT CBCS VII & VIII Syllabus - Information Security-Cbitmuninder ITNo ratings yet
- IT 513 Course OutlineDocument4 pagesIT 513 Course OutlineWaleed HussainNo ratings yet
- Cyber SecurityDocument3 pagesCyber Securitysweta.jethava24460No ratings yet
- Course Outline NewDocument2 pagesCourse Outline NewsamuelNo ratings yet
- Cyberlaws and SecurityDocument1 pageCyberlaws and Security17001009023 HINGULA BHATNo ratings yet
- Course Outline SCS4110Document3 pagesCourse Outline SCS4110n02019697mNo ratings yet
- CSD4003 Network-And-System-Security LP 1.0 6 CSD4003Document3 pagesCSD4003 Network-And-System-Security LP 1.0 6 CSD4003VibhuNo ratings yet
- Is Scouse Outline VFDocument4 pagesIs Scouse Outline VFMuller MuleyNo ratings yet
- Course Plan Information SecurityDocument7 pagesCourse Plan Information SecurityMalik KashifNo ratings yet
- Information System SecurityDocument2 pagesInformation System Securitymakangara22No ratings yet
- Cyber Security SyllabusDocument1 pageCyber Security Syllabusshubh1996sriNo ratings yet
- Title 5Document2 pagesTitle 5М. ЭнэрэлтNo ratings yet
- Syllabus For Diploma in Cyber SecurityDocument4 pagesSyllabus For Diploma in Cyber SecurityppghoshinNo ratings yet
- (R17A0526) Information Security Digital NotesDocument143 pages(R17A0526) Information Security Digital NotesPrafulla Durgadhar GawandeNo ratings yet
- MTech Cyber I and II Sem SyllabusDocument24 pagesMTech Cyber I and II Sem SyllabusDarmoni LaishramNo ratings yet
- IIT Jammu Times Offers Post Graduate Diploma in Cyber Security - BrochureDocument22 pagesIIT Jammu Times Offers Post Graduate Diploma in Cyber Security - BrochureKhushal OzaNo ratings yet
- Cyber Security BrochureDocument5 pagesCyber Security BrochureShweta HosmaniNo ratings yet
- CSE403 Network SecurityDocument2 pagesCSE403 Network SecurityrajatNo ratings yet
- ISS404: Security Architecture, Design and Models SyllabusDocument2 pagesISS404: Security Architecture, Design and Models SyllabusLeNantais SonderangeboteNo ratings yet
- RCS 322 Computer System SecurityDocument5 pagesRCS 322 Computer System SecuritymkweleboiNo ratings yet
- Strawman IASDocument12 pagesStrawman IASwallofkleinNo ratings yet
- Information Security: Dr. Pranita UpadhyayaDocument35 pagesInformation Security: Dr. Pranita UpadhyayaMANOJNo ratings yet
- Exam Questions Computer Systems Information SecurityDocument1 pageExam Questions Computer Systems Information SecurityAbbas ElouzeirNo ratings yet
- Course OutlineDocument3 pagesCourse OutlineFasiledesNo ratings yet
- CSE329 - CS CIF NBA FormatDocument3 pagesCSE329 - CS CIF NBA FormatHAQNo ratings yet
- (An Introduction To Computer) : SecurityDocument51 pages(An Introduction To Computer) : SecurityguntureanNo ratings yet
- MCS-054 Block-4Document87 pagesMCS-054 Block-4Kamal TiwariNo ratings yet
- Cyber Security Notes 4-1Document81 pagesCyber Security Notes 4-1Sripriya BellaryNo ratings yet
- Unit1 RoshanJameelDocument104 pagesUnit1 RoshanJameelSarfirey GamersNo ratings yet
- Introduction To Information SecurityDocument5 pagesIntroduction To Information SecurityjamesNo ratings yet
- CNS - M1L0Document18 pagesCNS - M1L0Viraj KaleNo ratings yet
- Module 1 - CSDocument85 pagesModule 1 - CSAneeq Qawi AbzariNo ratings yet
- ChapterDocument16 pagesChapterutkl5848No ratings yet
- SecurityOfCriticalInfrastructure V2assignmentDocument4 pagesSecurityOfCriticalInfrastructure V2assignmentAyushNo ratings yet
- Computersecurity OutlineDocument5 pagesComputersecurity Outlineshifara TesfayeNo ratings yet
- Pune University IS Tech. SyllabusDocument9 pagesPune University IS Tech. SyllabusPav TechnicalsNo ratings yet
- Pgdcs CurriculumDocument10 pagesPgdcs Curriculumindraveer_rnsNo ratings yet
- Lecture1 IntroductionDocument45 pagesLecture1 Introductionasmm.rahamanNo ratings yet
- Internet Security E-BookDocument128 pagesInternet Security E-BookMONIKA R PSGRKCWNo ratings yet
- Unit 1Document18 pagesUnit 1shikshj9No ratings yet
- ChapterDocument17 pagesChapterutkl5848No ratings yet
- MCSCB Cyber SecurityDocument16 pagesMCSCB Cyber SecurityKrishna Kumaran ThampiNo ratings yet
- UF1RAP01 - Security of computing systemDocument2 pagesUF1RAP01 - Security of computing systemArun Kumar PalanichamyNo ratings yet
- Network Security & Cryptography BookDocument204 pagesNetwork Security & Cryptography BookYash Bhardwaj100% (1)
- Information Security and Cyber LawsDocument2 pagesInformation Security and Cyber LawsPrasanta DebNo ratings yet
- Cyber Security - Iot: 4. Unauthorized Access or ControlDocument4 pagesCyber Security - Iot: 4. Unauthorized Access or ControlKhushal SinghNo ratings yet
- B.Tech. Computer: Uka Tarsadia UniversityDocument6 pagesB.Tech. Computer: Uka Tarsadia UniversityPatelNo ratings yet
- Cyber Security 06012022Document3 pagesCyber Security 06012022Nilesh Waikar 2No ratings yet
- CNS SyllabusDocument1 pageCNS SyllabusgdeepthiNo ratings yet
- Research Cyber SecurityDocument2 pagesResearch Cyber Securityketis27211No ratings yet
- Information Security Management 2Document34 pagesInformation Security Management 2tuffahati meydina100% (1)
- Dcap516 Computer SecurityDocument193 pagesDcap516 Computer Securitynirajaadithya.dasireddiNo ratings yet
- 1.1 To 1.4Document33 pages1.1 To 1.4Ayush VishnoiNo ratings yet
- CYBER SECURITY HANDBOOK Part-2: Lock, Stock, and Cyber: A Comprehensive Security HandbookFrom EverandCYBER SECURITY HANDBOOK Part-2: Lock, Stock, and Cyber: A Comprehensive Security HandbookNo ratings yet
- Powertech ™ 4045Tfm75 Diesel Engine: Marine Propulsion Engine SpecificationsDocument2 pagesPowertech ™ 4045Tfm75 Diesel Engine: Marine Propulsion Engine SpecificationsDAVIDNo ratings yet
- Carla Jensen ResumeDocument1 pageCarla Jensen ResumesiddeshwarNo ratings yet
- Exercise - 15 Graphical Calculation ViewsDocument9 pagesExercise - 15 Graphical Calculation ViewsKhaled Abd El HadyNo ratings yet
- Toyota Motor Manufacturing: Case Study AnalysisDocument19 pagesToyota Motor Manufacturing: Case Study AnalysisSahil ChaudharyNo ratings yet
- HTTTKT Bài 10.1 DangDocument1 pageHTTTKT Bài 10.1 DangDANG PHAM HAINo ratings yet
- WiNG5 Mesh How-ToDocument22 pagesWiNG5 Mesh How-TopankrezyNo ratings yet
- EZ Board Manual Rev 1Document111 pagesEZ Board Manual Rev 1Top Hat ElectronicsNo ratings yet
- Laptop Hard Drive Circuit Board RepairDocument33 pagesLaptop Hard Drive Circuit Board Repairz4rm4r80% (20)
- Our World Second Edition - Installation ManualDocument6 pagesOur World Second Edition - Installation ManualAll CastilloNo ratings yet
- Gujarat Technological University: Induction MachinesDocument3 pagesGujarat Technological University: Induction Machinesjijo123408No ratings yet
- Daikin Reiri Catalogue v2Document21 pagesDaikin Reiri Catalogue v2Royal EagleNo ratings yet
- 0009 - USDA 5000 Tonnage SPOB-1Document7 pages0009 - USDA 5000 Tonnage SPOB-1lutvi engineeringNo ratings yet
- Cisco Cloud Services Router 1000V: Q A Q ADocument6 pagesCisco Cloud Services Router 1000V: Q A Q AAsish PratikNo ratings yet
- Form 2: Desktop Stereolithography 3D PrinterDocument27 pagesForm 2: Desktop Stereolithography 3D PrinterNick KaraiskosNo ratings yet
- MCI D45 CRT CHARGE BrochureDocument9 pagesMCI D45 CRT CHARGE BrochureRomanvi1980No ratings yet
- Math Terms 2 RefresherDocument3 pagesMath Terms 2 Refreshercat buenafeNo ratings yet
- Electronic Engineer CVDocument3 pagesElectronic Engineer CVAbdoAbuzantNo ratings yet
- Export - Import - 139Document24 pagesExport - Import - 139EconaurNo ratings yet
- B2.2 Configuring The Domain Controller (Windows Server 2016/windows Server 2012 R2)Document2 pagesB2.2 Configuring The Domain Controller (Windows Server 2016/windows Server 2012 R2)Filipe LinoNo ratings yet
- Detection of Hyperpartisan News Articles - 2022 - International Journal of InfoDocument10 pagesDetection of Hyperpartisan News Articles - 2022 - International Journal of Infoᕮᖇᓰᔕ ᕮᙀᗩNo ratings yet
- Introduction To Data ScienceDocument16 pagesIntroduction To Data ScienceTopo ChandraNo ratings yet
- CAPS - 3170507 - Coomon Assignment With AcknowDocument12 pagesCAPS - 3170507 - Coomon Assignment With AcknowVarun pandeyNo ratings yet
- NSTWPDocument442 pagesNSTWPborysmrNo ratings yet
- Rec670 Iec61850 Pixit 2.2Document21 pagesRec670 Iec61850 Pixit 2.2Ho Van ToanNo ratings yet
- G120 Fieldbuses FH17 0116 Eng en-USDocument244 pagesG120 Fieldbuses FH17 0116 Eng en-USPoom YoosornNo ratings yet
- 4 Wan Loadbalancing - Icyflame StudioDocument3 pages4 Wan Loadbalancing - Icyflame StudioLTI MaintenanceNo ratings yet
- Four Stroke Engine Cycles and TimingDocument27 pagesFour Stroke Engine Cycles and TimingOğuz Çavdar100% (1)
- ComAp Electronic Engines Support For Perkins 2Document15 pagesComAp Electronic Engines Support For Perkins 2Bhuneshwar Prasad100% (2)
- Voxengo SPAN Plus User Guide enDocument8 pagesVoxengo SPAN Plus User Guide enMarin GanciuNo ratings yet