Professional Documents
Culture Documents
Cyber Attacks PDF 1640877857
Cyber Attacks PDF 1640877857
Uploaded by
jesusrhCopyright:
Available Formats
You might also like
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeFrom EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeRating: 4 out of 5 stars4/5 (5835)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreFrom EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreRating: 4 out of 5 stars4/5 (1093)
- Never Split the Difference: Negotiating As If Your Life Depended On ItFrom EverandNever Split the Difference: Negotiating As If Your Life Depended On ItRating: 4.5 out of 5 stars4.5/5 (852)
- Grit: The Power of Passion and PerseveranceFrom EverandGrit: The Power of Passion and PerseveranceRating: 4 out of 5 stars4/5 (590)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceFrom EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceRating: 4 out of 5 stars4/5 (903)
- Shoe Dog: A Memoir by the Creator of NikeFrom EverandShoe Dog: A Memoir by the Creator of NikeRating: 4.5 out of 5 stars4.5/5 (541)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersFrom EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersRating: 4.5 out of 5 stars4.5/5 (350)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureFrom EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureRating: 4.5 out of 5 stars4.5/5 (474)
- Her Body and Other Parties: StoriesFrom EverandHer Body and Other Parties: StoriesRating: 4 out of 5 stars4/5 (824)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)From EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Rating: 4.5 out of 5 stars4.5/5 (122)
- The Emperor of All Maladies: A Biography of CancerFrom EverandThe Emperor of All Maladies: A Biography of CancerRating: 4.5 out of 5 stars4.5/5 (271)
- The Little Book of Hygge: Danish Secrets to Happy LivingFrom EverandThe Little Book of Hygge: Danish Secrets to Happy LivingRating: 3.5 out of 5 stars3.5/5 (405)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyFrom EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyRating: 3.5 out of 5 stars3.5/5 (2259)
- The Yellow House: A Memoir (2019 National Book Award Winner)From EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Rating: 4 out of 5 stars4/5 (98)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaFrom EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaRating: 4.5 out of 5 stars4.5/5 (266)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryFrom EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryRating: 3.5 out of 5 stars3.5/5 (231)
- Team of Rivals: The Political Genius of Abraham LincolnFrom EverandTeam of Rivals: The Political Genius of Abraham LincolnRating: 4.5 out of 5 stars4.5/5 (234)
- On Fire: The (Burning) Case for a Green New DealFrom EverandOn Fire: The (Burning) Case for a Green New DealRating: 4 out of 5 stars4/5 (74)
- Sample Lifting Plan and Rigging StudyDocument13 pagesSample Lifting Plan and Rigging StudyKhawaja Arslan Ahmed88% (16)
- The Unwinding: An Inner History of the New AmericaFrom EverandThe Unwinding: An Inner History of the New AmericaRating: 4 out of 5 stars4/5 (45)
- HiFi ROSEDocument1 pageHiFi ROSEjesusrhNo ratings yet
- IAMCP Guide To Partering With MSFT 1621460045Document38 pagesIAMCP Guide To Partering With MSFT 1621460045jesusrhNo ratings yet
- Magazine PDFDocument72 pagesMagazine PDFjesusrhNo ratings yet
- The Ratchet 09 - Read MeDocument7 pagesThe Ratchet 09 - Read MejesusrhNo ratings yet
- TCS PaperDocument393 pagesTCS Papernikky2u20No ratings yet
- 8chan Hacked PDFDocument192 pages8chan Hacked PDFOBEY GODNo ratings yet
- Unicast Routing Protocols For Wireless Ad Hoc NetworksDocument49 pagesUnicast Routing Protocols For Wireless Ad Hoc NetworksRaja MadhuvanthiNo ratings yet
- Manual Book SICOMA MA02250 - 1500 SDocument61 pagesManual Book SICOMA MA02250 - 1500 SSitumorang David100% (1)
- HAND GESTURE MAGIC Capstone Project RepoDocument35 pagesHAND GESTURE MAGIC Capstone Project RepoAkash DidhariaNo ratings yet
- Assignment 5 - Worm GearDocument1 pageAssignment 5 - Worm GearSR SuryaNo ratings yet
- Kumpulan CD-Key KomputerDocument4 pagesKumpulan CD-Key KomputerKemz MayyerNo ratings yet
- Master Python Fundamentals The Ultimate Guide For BeginnersDocument346 pagesMaster Python Fundamentals The Ultimate Guide For Beginnersronaldopinheiro2009No ratings yet
- Solving Quadratic EquationsDocument4 pagesSolving Quadratic EquationsHelen MylonaNo ratings yet
- CLRD 4th GRADIING LESSON PLANDocument4 pagesCLRD 4th GRADIING LESSON PLANQueencess Ara TorresNo ratings yet
- Earthing & PP MCQ Part 1Document6 pagesEarthing & PP MCQ Part 1Abhishek KumarNo ratings yet
- What Is Direct Memory Access MDADocument1 pageWhat Is Direct Memory Access MDAJuan Ortega GuerraNo ratings yet
- Fagor 8055tcDocument50 pagesFagor 8055tcKamil BabiarzNo ratings yet
- Engineering Guide Flex and Rigid Flex PCBsDocument14 pagesEngineering Guide Flex and Rigid Flex PCBsMariano DiazNo ratings yet
- Michelle Marin Designed Resume PDFDocument1 pageMichelle Marin Designed Resume PDFMichelle MarinNo ratings yet
- Bedienungs-Und Wartungsanleitung: Operating and Maintenance InstructionsDocument17 pagesBedienungs-Und Wartungsanleitung: Operating and Maintenance Instructionsuuur35No ratings yet
- Deloitte Cover Letter RedditDocument5 pagesDeloitte Cover Letter Redditjcipchajd100% (3)
- Failure Forensics and Redesign of Draft Tube Trash Racks hv2012Document14 pagesFailure Forensics and Redesign of Draft Tube Trash Racks hv2012julio aliaga villegasNo ratings yet
- Chapter 2Document23 pagesChapter 2Chhin VisalNo ratings yet
- CV Veronika Majtasova DubaiDocument3 pagesCV Veronika Majtasova Dubaimohammed_accaNo ratings yet
- 史都華平台之仿生物演算法模糊強化學習控制與FPGA實現Document99 pages史都華平台之仿生物演算法模糊強化學習控制與FPGA實現李金輝No ratings yet
- Shaun of The Dead (Shots)Document11 pagesShaun of The Dead (Shots)mattdalbyNo ratings yet
- The Systems Theory of ManagementDocument10 pagesThe Systems Theory of ManagementRuchita SinghalNo ratings yet
- Solar 200 - Solar 300N - I-V 400 - Solar I-V - MPP 300 - Tht41Document16 pagesSolar 200 - Solar 300N - I-V 400 - Solar I-V - MPP 300 - Tht41luciano_gularteNo ratings yet
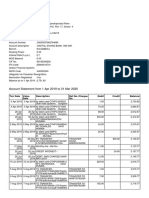
- Account Statement From 1 Apr 2019 To 31 Mar 2020: TXN Date Value Date Description Ref No./Cheque No. Debit Credit BalanceDocument7 pagesAccount Statement From 1 Apr 2019 To 31 Mar 2020: TXN Date Value Date Description Ref No./Cheque No. Debit Credit BalanceawddNo ratings yet
- Case Study - Org DevelopmentDocument13 pagesCase Study - Org DevelopmentShobhnaSharmaNo ratings yet
- The Assessment of Customer Satisfaction in ATM Service at Commercial Bank of Ethiopia in Wolaita Sodo BranchDocument11 pagesThe Assessment of Customer Satisfaction in ATM Service at Commercial Bank of Ethiopia in Wolaita Sodo BranchZemene HailuNo ratings yet
- Cluster (Oracle)Document5 pagesCluster (Oracle)Nilesh KumarNo ratings yet
- Math 10Document6 pagesMath 10Renelyn LeriaNo ratings yet
Cyber Attacks PDF 1640877857
Cyber Attacks PDF 1640877857
Uploaded by
jesusrhCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Cyber Attacks PDF 1640877857
Cyber Attacks PDF 1640877857
Uploaded by
jesusrhCopyright:
Available Formats
Trojans
Spyware
Spyware
Malware
Worms
Malware Adware
Botnets Bots
Phishing
Rootkits
Botnet
Technology
Viruses
Keystroke
ZeuS Exploit tools and kits Logger
Monitor
Email harvesters
Technology Using localized networks
Bluetooth-enabled devices planted at gas pumps to
read credit card details
Wi-fi Tools Using Mobile tech
Data breaches at large companies (TJ Maxx,
Using tablets
Heartland, ...)
Precedents
Updates
Pharmamed.php (email harvesting)
Software Customized Scripts
Bluesnarfing, bluebugging, HeloMoto
Loaded externally
War-driving
Hacking
Eavesdropping
Espionage (Leslie) Trojans
Password-based attacks
Hacking
PDF attachments
Compromised-key attacks
Meeting Requests with Attachments
Man-in-the-middle attacks
Email DOC attachments
Sniffers
Picture attachments
Stealing devices
Physical acquisition
Software updates
Acquiring improperly disposed-of device
USB/external devices
Pharming Phishing
Methods
Computers
Employees
P2P services Mass rebellion
Contractors/Consultants
Disgruntled employees
Outsiders with Access
Bribery Disclosure by employees
Peer-to-Peer networks
Unintentional disclosure
Cyber Identity Theft (Laura)
Posing as authority, mass-emailing victims of past
identity theft Scam within a scam Planting a Mole
Cyber Attacks Internal
Spoofing Disgruntled Employee
Posing
Sabotage
Registering another person for a dating site, for Activists
example Pranking
External Terrorist Groups
War-dialing
State Actors
Eavesdropping
Methods
Send Message
Password-based attacks Hacking Website Defacement
Methods
Publicity
Sniffers
Deter Communication
Bluebugging and bluesnarfing
Denial of Service
Suspend System Activity (permanently or
Smishing Phishing temporarily)
Disgruntled employees Exploiting Defaults Faulty IIS (Internet Information Service)
Mobile devices
Bribery Disclosure by employees Data Mining
Internet
Unintentional disclosure Authorization Bypass
Stealing devices Cyber Terrorism (Joe) Trojan Horse
Physical acquisition
Acquiring improperly disposed-of device Software Virus
Looking over the user's shoulder Worm
Direct observation
Camera/video capabilities on devices Wired Hardware
ATM skimming Dictionary Attacks
Exploitation of mobile GPS location information Stealing Password Hybrid Attacks
More attacks on social networking sites Predictions (2011) Brute Force Attacks
Increase in "mixed threats" (email, Web, social media) Technology Phishing
Email Man-in-the-Middle DNS hijacking
URL manipulation
Eavesdropping
Wireless Interference
Packet Sniffing
You might also like
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeFrom EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeRating: 4 out of 5 stars4/5 (5835)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreFrom EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreRating: 4 out of 5 stars4/5 (1093)
- Never Split the Difference: Negotiating As If Your Life Depended On ItFrom EverandNever Split the Difference: Negotiating As If Your Life Depended On ItRating: 4.5 out of 5 stars4.5/5 (852)
- Grit: The Power of Passion and PerseveranceFrom EverandGrit: The Power of Passion and PerseveranceRating: 4 out of 5 stars4/5 (590)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceFrom EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceRating: 4 out of 5 stars4/5 (903)
- Shoe Dog: A Memoir by the Creator of NikeFrom EverandShoe Dog: A Memoir by the Creator of NikeRating: 4.5 out of 5 stars4.5/5 (541)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersFrom EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersRating: 4.5 out of 5 stars4.5/5 (350)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureFrom EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureRating: 4.5 out of 5 stars4.5/5 (474)
- Her Body and Other Parties: StoriesFrom EverandHer Body and Other Parties: StoriesRating: 4 out of 5 stars4/5 (824)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)From EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Rating: 4.5 out of 5 stars4.5/5 (122)
- The Emperor of All Maladies: A Biography of CancerFrom EverandThe Emperor of All Maladies: A Biography of CancerRating: 4.5 out of 5 stars4.5/5 (271)
- The Little Book of Hygge: Danish Secrets to Happy LivingFrom EverandThe Little Book of Hygge: Danish Secrets to Happy LivingRating: 3.5 out of 5 stars3.5/5 (405)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyFrom EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyRating: 3.5 out of 5 stars3.5/5 (2259)
- The Yellow House: A Memoir (2019 National Book Award Winner)From EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Rating: 4 out of 5 stars4/5 (98)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaFrom EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaRating: 4.5 out of 5 stars4.5/5 (266)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryFrom EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryRating: 3.5 out of 5 stars3.5/5 (231)
- Team of Rivals: The Political Genius of Abraham LincolnFrom EverandTeam of Rivals: The Political Genius of Abraham LincolnRating: 4.5 out of 5 stars4.5/5 (234)
- On Fire: The (Burning) Case for a Green New DealFrom EverandOn Fire: The (Burning) Case for a Green New DealRating: 4 out of 5 stars4/5 (74)
- Sample Lifting Plan and Rigging StudyDocument13 pagesSample Lifting Plan and Rigging StudyKhawaja Arslan Ahmed88% (16)
- The Unwinding: An Inner History of the New AmericaFrom EverandThe Unwinding: An Inner History of the New AmericaRating: 4 out of 5 stars4/5 (45)
- HiFi ROSEDocument1 pageHiFi ROSEjesusrhNo ratings yet
- IAMCP Guide To Partering With MSFT 1621460045Document38 pagesIAMCP Guide To Partering With MSFT 1621460045jesusrhNo ratings yet
- Magazine PDFDocument72 pagesMagazine PDFjesusrhNo ratings yet
- The Ratchet 09 - Read MeDocument7 pagesThe Ratchet 09 - Read MejesusrhNo ratings yet
- TCS PaperDocument393 pagesTCS Papernikky2u20No ratings yet
- 8chan Hacked PDFDocument192 pages8chan Hacked PDFOBEY GODNo ratings yet
- Unicast Routing Protocols For Wireless Ad Hoc NetworksDocument49 pagesUnicast Routing Protocols For Wireless Ad Hoc NetworksRaja MadhuvanthiNo ratings yet
- Manual Book SICOMA MA02250 - 1500 SDocument61 pagesManual Book SICOMA MA02250 - 1500 SSitumorang David100% (1)
- HAND GESTURE MAGIC Capstone Project RepoDocument35 pagesHAND GESTURE MAGIC Capstone Project RepoAkash DidhariaNo ratings yet
- Assignment 5 - Worm GearDocument1 pageAssignment 5 - Worm GearSR SuryaNo ratings yet
- Kumpulan CD-Key KomputerDocument4 pagesKumpulan CD-Key KomputerKemz MayyerNo ratings yet
- Master Python Fundamentals The Ultimate Guide For BeginnersDocument346 pagesMaster Python Fundamentals The Ultimate Guide For Beginnersronaldopinheiro2009No ratings yet
- Solving Quadratic EquationsDocument4 pagesSolving Quadratic EquationsHelen MylonaNo ratings yet
- CLRD 4th GRADIING LESSON PLANDocument4 pagesCLRD 4th GRADIING LESSON PLANQueencess Ara TorresNo ratings yet
- Earthing & PP MCQ Part 1Document6 pagesEarthing & PP MCQ Part 1Abhishek KumarNo ratings yet
- What Is Direct Memory Access MDADocument1 pageWhat Is Direct Memory Access MDAJuan Ortega GuerraNo ratings yet
- Fagor 8055tcDocument50 pagesFagor 8055tcKamil BabiarzNo ratings yet
- Engineering Guide Flex and Rigid Flex PCBsDocument14 pagesEngineering Guide Flex and Rigid Flex PCBsMariano DiazNo ratings yet
- Michelle Marin Designed Resume PDFDocument1 pageMichelle Marin Designed Resume PDFMichelle MarinNo ratings yet
- Bedienungs-Und Wartungsanleitung: Operating and Maintenance InstructionsDocument17 pagesBedienungs-Und Wartungsanleitung: Operating and Maintenance Instructionsuuur35No ratings yet
- Deloitte Cover Letter RedditDocument5 pagesDeloitte Cover Letter Redditjcipchajd100% (3)
- Failure Forensics and Redesign of Draft Tube Trash Racks hv2012Document14 pagesFailure Forensics and Redesign of Draft Tube Trash Racks hv2012julio aliaga villegasNo ratings yet
- Chapter 2Document23 pagesChapter 2Chhin VisalNo ratings yet
- CV Veronika Majtasova DubaiDocument3 pagesCV Veronika Majtasova Dubaimohammed_accaNo ratings yet
- 史都華平台之仿生物演算法模糊強化學習控制與FPGA實現Document99 pages史都華平台之仿生物演算法模糊強化學習控制與FPGA實現李金輝No ratings yet
- Shaun of The Dead (Shots)Document11 pagesShaun of The Dead (Shots)mattdalbyNo ratings yet
- The Systems Theory of ManagementDocument10 pagesThe Systems Theory of ManagementRuchita SinghalNo ratings yet
- Solar 200 - Solar 300N - I-V 400 - Solar I-V - MPP 300 - Tht41Document16 pagesSolar 200 - Solar 300N - I-V 400 - Solar I-V - MPP 300 - Tht41luciano_gularteNo ratings yet
- Account Statement From 1 Apr 2019 To 31 Mar 2020: TXN Date Value Date Description Ref No./Cheque No. Debit Credit BalanceDocument7 pagesAccount Statement From 1 Apr 2019 To 31 Mar 2020: TXN Date Value Date Description Ref No./Cheque No. Debit Credit BalanceawddNo ratings yet
- Case Study - Org DevelopmentDocument13 pagesCase Study - Org DevelopmentShobhnaSharmaNo ratings yet
- The Assessment of Customer Satisfaction in ATM Service at Commercial Bank of Ethiopia in Wolaita Sodo BranchDocument11 pagesThe Assessment of Customer Satisfaction in ATM Service at Commercial Bank of Ethiopia in Wolaita Sodo BranchZemene HailuNo ratings yet
- Cluster (Oracle)Document5 pagesCluster (Oracle)Nilesh KumarNo ratings yet
- Math 10Document6 pagesMath 10Renelyn LeriaNo ratings yet