Professional Documents
Culture Documents
2023-01-26 Hostedscan Report
2023-01-26 Hostedscan Report
Uploaded by
Hemraj Patel BhuriCopyright:
Available Formats
You might also like
- Web Application Penetration Testing Report of Juice ShopDocument15 pagesWeb Application Penetration Testing Report of Juice ShopPavan Reddy50% (2)
- CFB ISD Proof of Residency Form With Another CFB FamilyDocument2 pagesCFB ISD Proof of Residency Form With Another CFB Familysail-doNo ratings yet
- Excavation Inspection HSE ChecklistDocument3 pagesExcavation Inspection HSE ChecklistSarfraz RandhawaNo ratings yet
- Personalism To RelationismDocument7 pagesPersonalism To RelationismRenatoNo ratings yet
- Peterbilt Rear Air Suspensions AdjustmentDocument42 pagesPeterbilt Rear Air Suspensions AdjustmentCellblocX83% (6)
- 2023-01-10 Hostedscan ReportDocument30 pages2023-01-10 Hostedscan ReportHemraj Patel BhuriNo ratings yet
- Owasp Zap Hostedscan Report 2024-02-12Document17 pagesOwasp Zap Hostedscan Report 2024-02-12faizan.rezaNo ratings yet
- Vulnerability Scan: Prepared byDocument14 pagesVulnerability Scan: Prepared byzitexitNo ratings yet
- Vulnerability Scan: Prepared byDocument13 pagesVulnerability Scan: Prepared byzitexitNo ratings yet
- Vulnerability Scan: Prepared byDocument17 pagesVulnerability Scan: Prepared byzitexitNo ratings yet
- Owasp Zap Hostedscan Report 2024-04-30Document16 pagesOwasp Zap Hostedscan Report 2024-04-30Tymmz AlloteyNo ratings yet
- Vulnerability Scan: Prepared byDocument20 pagesVulnerability Scan: Prepared byDiego MorenoNo ratings yet
- Cargill Web Application Scanning ReportDocument27 pagesCargill Web Application Scanning ReportHari KingNo ratings yet
- Vulnerabiliades - DiccionarioDocument142 pagesVulnerabiliades - DiccionarioJohan MorilloNo ratings yet
- ZAP Scanning: Project 2Document24 pagesZAP Scanning: Project 2Sabyasachi duttaNo ratings yet
- Vulnerability Scan: Prepared byDocument9 pagesVulnerability Scan: Prepared byPutra BagusNo ratings yet
- Rapport de Scan ThecniqueDocument10 pagesRapport de Scan ThecniqueayariimedNo ratings yet
- Security Analysis For - SnykDocument2 pagesSecurity Analysis For - SnykVivek GuptaNo ratings yet
- ZAP Scanning Report: Site: Https://webapps - Bps.go - IdDocument4 pagesZAP Scanning Report: Site: Https://webapps - Bps.go - Idyoga_wpNo ratings yet
- Cross Site Scripting (XSS)Document11 pagesCross Site Scripting (XSS)Jithukrishnan vNo ratings yet
- Security Sample VAPT ReportDocument28 pagesSecurity Sample VAPT ReportRavi GiriNo ratings yet
- Website Vulnerability Scanner Report (Light)Document4 pagesWebsite Vulnerability Scanner Report (Light)MasBaNo ratings yet
- Ridho Abdul MajidDocument24 pagesRidho Abdul MajidRidho Abdul MajidNo ratings yet
- Astra Security - Sample Report For VAPTDocument30 pagesAstra Security - Sample Report For VAPTIndian OpinionNo ratings yet
- Burp Scanner ReportDocument3 pagesBurp Scanner ReportPr RabariNo ratings yet
- Openvas Hostedscan Report 2024-04-30Document18 pagesOpenvas Hostedscan Report 2024-04-30Tymmz AlloteyNo ratings yet
- (Divi Report) Daptatech RepDocument5 pages(Divi Report) Daptatech RepcarlosNo ratings yet
- Astra Security Sample VAPT ReportDocument28 pagesAstra Security Sample VAPT Reporthanuman1999No ratings yet
- PentestTools WebsiteScanner ReportDocument5 pagesPentestTools WebsiteScanner ReportmiguelNo ratings yet
- XssauditorDocument9 pagesXssauditorcajeha6903No ratings yet
- PentestTools WebsiteScanner ReportDocument5 pagesPentestTools WebsiteScanner ReportSunil Kumar SharmaNo ratings yet
- Executive Summary: Table of ContentsDocument6 pagesExecutive Summary: Table of Contentsharitripathi52552gmail.comNo ratings yet
- Cross Site ScriptingDocument15 pagesCross Site ScriptingHiNo ratings yet
- 05.HTTPS Flood Protection ModuleDocument6 pages05.HTTPS Flood Protection ModuleLe Vinh HienNo ratings yet
- OWASP LA The Last XSS Defense Talk Jim Manico 2018 08Document75 pagesOWASP LA The Last XSS Defense Talk Jim Manico 2018 08Ismael OliveiraNo ratings yet
- Adopting Active Risk For Vulnerability PrioritizationDocument12 pagesAdopting Active Risk For Vulnerability PrioritizationRuben BorregaNo ratings yet
- PentestTools WebsiteScanner ReportDocument7 pagesPentestTools WebsiteScanner ReportMauricio CerratoNo ratings yet
- What Is Cross-Site Scripting (XSS) and How To Prevent It - WebDocument6 pagesWhat Is Cross-Site Scripting (XSS) and How To Prevent It - WebYouNo ratings yet
- XSS in Theory: Cross-Site ScriptingDocument12 pagesXSS in Theory: Cross-Site ScriptingHesham MedhatNo ratings yet
- Cross-Site Scripting (XSS) - OWASPDocument9 pagesCross-Site Scripting (XSS) - OWASPCha OsNo ratings yet
- Owasp Zap Scanner Output 2024-02-29Document21 pagesOwasp Zap Scanner Output 2024-02-29b.nandhu2810No ratings yet
- Comprehensive Report: Acunetix Threat Level 3Document37 pagesComprehensive Report: Acunetix Threat Level 3Yudha Trias RusmanaNo ratings yet
- Website Vulnerability Scanner Report (Light)Document5 pagesWebsite Vulnerability Scanner Report (Light)Ilija DodevskiNo ratings yet
- Website Vulnerability Scanner Report (Light)Document5 pagesWebsite Vulnerability Scanner Report (Light)Muhammad LuludNo ratings yet
- Don't Trust The Locals: Investigating The Prevalence of Persistent Client-Side Cross-Site Scripting in The WildDocument15 pagesDon't Trust The Locals: Investigating The Prevalence of Persistent Client-Side Cross-Site Scripting in The Wildraed waheedNo ratings yet
- Sample Report WebDocument19 pagesSample Report WebMuhammad AwaisNo ratings yet
- Scan Meteored AcunetixDocument5 pagesScan Meteored AcunetixAlejandro Antonio Loyola RuizNo ratings yet
- Detect and Respond To Attacks AimDocument5 pagesDetect and Respond To Attacks Aimreddy ramya sri ghantasalaNo ratings yet
- A Novel Technique To Prevent SQL Injection and Cross-Site Scripting Attacks Using Knuth-Morris-Pratt String Match AlgorithmDocument14 pagesA Novel Technique To Prevent SQL Injection and Cross-Site Scripting Attacks Using Knuth-Morris-Pratt String Match AlgorithmChandan NareshNo ratings yet
- Threat Model For BwappDocument38 pagesThreat Model For Bwappshinde_jayesh2005No ratings yet
- 2023 08 03 ZAP ReportDocument58 pages2023 08 03 ZAP ReportQuang Hà ĐặngNo ratings yet
- Foundation of Cyber SecurityDocument58 pagesFoundation of Cyber SecurityPradip SarkerNo ratings yet
- Executive Summary: Table of ContentsDocument7 pagesExecutive Summary: Table of Contentsharitripathi52552gmail.comNo ratings yet
- Documentation On Xss VulnerabilityDocument3 pagesDocumentation On Xss VulnerabilitySujithNo ratings yet
- AssessmentDocument50 pagesAssessmentPham Dinh ChungNo ratings yet
- Big-Ip Asm Comprehensive: Application SecurityDocument17 pagesBig-Ip Asm Comprehensive: Application SecurityLuis DiazNo ratings yet
- Website Vulnerability Scanner Report (Light)Document6 pagesWebsite Vulnerability Scanner Report (Light)Stevi NangonNo ratings yet
- PentestTools WebsiteScanner ReportDocument5 pagesPentestTools WebsiteScanner ReportrayjoneskeNo ratings yet
- Hillstone_I-Series_sBDS-V3.0_ENDocument4 pagesHillstone_I-Series_sBDS-V3.0_ENDonny TahirNo ratings yet
- Infrastructure SecurityDocument107 pagesInfrastructure SecurityDoctor LyricsNo ratings yet
- Ios Static Analysis Report: Mini Militia Mini Militia (4.3.2) (4.3.2)Document17 pagesIos Static Analysis Report: Mini Militia Mini Militia (4.3.2) (4.3.2)Karan KisnaniNo ratings yet
- Research Paper On XssDocument6 pagesResearch Paper On Xssfapavelyfel2100% (1)
- Hack2Secure Web Application Security Testing Workshop Reference GuideDocument9 pagesHack2Secure Web Application Security Testing Workshop Reference GuideJavvedNo ratings yet
- Penetration Testing Fundamentals-2: Penetration Testing Study Guide To Breaking Into SystemsFrom EverandPenetration Testing Fundamentals-2: Penetration Testing Study Guide To Breaking Into SystemsNo ratings yet
- Unit - 1Document2 pagesUnit - 1Hemraj Patel BhuriNo ratings yet
- Unit - 2Document1 pageUnit - 2Hemraj Patel BhuriNo ratings yet
- Quetion BankDocument1 pageQuetion BankHemraj Patel BhuriNo ratings yet
- Machine Learning LibrariesDocument38 pagesMachine Learning LibrariesHemraj Patel BhuriNo ratings yet
- Quetion Bank NSMLDocument6 pagesQuetion Bank NSMLHemraj Patel BhuriNo ratings yet
- Unit 1: Advanced Computer Networks & SecurityDocument64 pagesUnit 1: Advanced Computer Networks & SecurityHemraj Patel BhuriNo ratings yet
- Lab ManualDocument54 pagesLab ManualHemraj Patel BhuriNo ratings yet
- 2023-01-10 Hostedscan ReportDocument30 pages2023-01-10 Hostedscan ReportHemraj Patel BhuriNo ratings yet
- Project ReportDocument41 pagesProject ReportHemraj Patel BhuriNo ratings yet
- Internship (Soc)Document11 pagesInternship (Soc)Hemraj Patel BhuriNo ratings yet
- Iso 27001 2013 - IsmsDocument34 pagesIso 27001 2013 - IsmsHemraj Patel BhuriNo ratings yet
- RulebookDocument8 pagesRulebookEren Koyunoğlu100% (1)
- "Good" LeadershipDocument5 pages"Good" LeadershipSyidiq Nack RajinNo ratings yet
- Philips Automatic Hand SanitaizerDocument24 pagesPhilips Automatic Hand SanitaizerAjith9410No ratings yet
- Chapter 9: FOREX MARKET Key PointsDocument6 pagesChapter 9: FOREX MARKET Key PointsDanica AbelardoNo ratings yet
- Beam Design Detail Report: Material and Design DataDocument33 pagesBeam Design Detail Report: Material and Design DataazwanNo ratings yet
- PracResearch2 Grade-12 Q4 Mod5 Data-Collection-Presentation-and-Analysis Version4Document59 pagesPracResearch2 Grade-12 Q4 Mod5 Data-Collection-Presentation-and-Analysis Version4MichiOdevilasNo ratings yet
- 07) YHT Realty vs. CA, GR No. 126780, Feb. 17, 2005Document15 pages07) YHT Realty vs. CA, GR No. 126780, Feb. 17, 2005justinmauricioNo ratings yet
- Full Ebook of Lipidomics Methods and Protocols 2Nd Edition Sanjoy K Bhattacharya Editor Online PDF All ChapterDocument69 pagesFull Ebook of Lipidomics Methods and Protocols 2Nd Edition Sanjoy K Bhattacharya Editor Online PDF All Chapterandrewmolina926227100% (4)
- Rocket ManualDocument1 pageRocket ManualJonEatonNo ratings yet
- CAMEE Tool 7 2 Agreement MEP Client 2013Document15 pagesCAMEE Tool 7 2 Agreement MEP Client 2013SAID RGONo ratings yet
- Name Email Phone Hometown: Authorized To Work in The US For Any EmployerDocument3 pagesName Email Phone Hometown: Authorized To Work in The US For Any EmployerR.T. CoffmanNo ratings yet
- Program of WorksDocument2 pagesProgram of WorksSimply RoseNo ratings yet
- Chapter No 03 Class 6th Notes For Computer Science English MediumDocument5 pagesChapter No 03 Class 6th Notes For Computer Science English MediumAbid HussainNo ratings yet
- Nerf2Real: Sim2Real Transfer of Vision-Guided Bipedal Motion Skills Using Neural Radiance FieldsDocument12 pagesNerf2Real: Sim2Real Transfer of Vision-Guided Bipedal Motion Skills Using Neural Radiance Fields武怡No ratings yet
- Sump Well-20 KL PDFDocument3 pagesSump Well-20 KL PDFvisali garikapatiNo ratings yet
- 2016-12-15 St. Mary's County TimesDocument32 pages2016-12-15 St. Mary's County TimesSouthern Maryland OnlineNo ratings yet
- Chapter 3Document5 pagesChapter 3Sheila ShamimiNo ratings yet
- INF1520 May 2012 Exam Answers DoneDocument7 pagesINF1520 May 2012 Exam Answers DoneNthabiseng MahlasiNo ratings yet
- Cannes Lions 2019: Digital Craft Lions ShortlistDocument18 pagesCannes Lions 2019: Digital Craft Lions Shortlistadobo magazineNo ratings yet
- Dixie ProjectorDocument2 pagesDixie ProjectorBagus SaputroNo ratings yet
- NX Shop Documentation Plug-In BaseDocument10 pagesNX Shop Documentation Plug-In BaseLÊ VĂN ĐỨCNo ratings yet
- Pricelist Laptop & PrinterDocument7 pagesPricelist Laptop & PrinterKharis FreefireNo ratings yet
- Case Concerning Rights of Nationals of The US in Morocco Summary of JudgmentDocument2 pagesCase Concerning Rights of Nationals of The US in Morocco Summary of JudgmentClarissa Beth DegamoNo ratings yet
- Buffering DataDocument4 pagesBuffering DataLeonard-Tiberiu SandorNo ratings yet
- Japan AwardsDocument3 pagesJapan AwardsLeonard LyonsNo ratings yet
- MelEye - CatalogDocument4 pagesMelEye - CatalogChinmay GhoshNo ratings yet
2023-01-26 Hostedscan Report
2023-01-26 Hostedscan Report
Uploaded by
Hemraj Patel BhuriOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
2023-01-26 Hostedscan Report
2023-01-26 Hostedscan Report
Uploaded by
Hemraj Patel BhuriCopyright:
Available Formats
Vulnerability Scan Report
BY
HostedScan Security
GENERATED ON 1/26/2023
1/26/2023 HostedScan Security 1/30
Table of Contents
Report Summary
Passive Web Application Vulnerabilities
Active Web Application Vulnerabilities
SSL/TLS Security
Network Vulnerabilities
Open TCP Ports
Open UDP Ports
1/26/2023 HostedScan Security 2/30
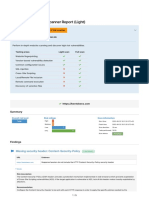
Report Summary
This report contains information on all of the risks found from your vulnerability scans. Each risk is assigned a threat level (high,
medium, or low).
Total Risks
Total number of risks found by severity.
1
12
9
0
High Medium Low Accepted
1/26/2023 HostedScan Security 3/30
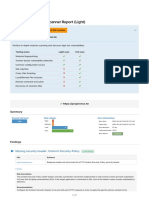
Passive Web Application Vulnerabilities
The OWASP ZAP passive web application scan crawls the pages of a web application. It inspects the web pages as well as the
requests and responses sent between the server. The passive scan checks for vulnerabilities such as cross-domain
misconfigurations, insecure cookies, vulnerable js dependencies, and more.
Total Risks
Total number of risks found by the passive web application vulnerability scan.
0
5
4
0
High Medium Low Accepted
Risks Summary
Summary of detected risks.
Open Accepted
Threat Level Title
Count Count
MEDIUM Absence of Anti-CSRF Tokens 1 0
MEDIUM Vulnerable JS Library 1 0
MEDIUM CSP: Wildcard Directive 1 0
MEDIUM CSP: script-src unsafe-inline 1 0
MEDIUM CSP: style-src unsafe-inline 1 0
LOW X-Content-Type-Options Header Missing 1 0
LOW Cross-Domain JavaScript Source File Inclusion 1 0
LOW Cookie with SameSite Attribute None 1 0
LOW CSP: Notices 1 0
Risks Per Target Summary
1/26/2023 HostedScan Security 4/30
Breakdown of risk counts for each target.
Target High Medium Low Accepted
https://www.jobreg.no/ 0 5 4 0
Full Risk Details
Detailed information about each risk found by the scan.
Absence of Anti-CSRF Tokens MEDIUM
Name Absence of Anti-CSRF Tokens
No Anti-CSRF tokens were found in a HTML submission form.
A cross-site request forgery is an attack that involves forcing a victim to send an HTTP request to a target
destination without their knowledge or intent in order to perform an action as the victim. The underlying
cause is application functionality using predictable URL/form actions in a repeatable way. The nature of
the attack is that CSRF exploits the trust that a web site has for a user. By contrast, cross-site scripting
(XSS) exploits the trust that a user has for a web site. Like XSS, CSRF attacks are not necessarily cross-
site, but they can be. Cross-site request forgery is also known as CSRF, XSRF, one-click attack, session
riding, confused deputy, and sea surf.
CSRF attacks are effective in a number of situations, including:
Description
* The victim has an active session on the target site.
* The victim is authenticated via HTTP auth on the target site.
* The victim is on the same local network as the target site.
CSRF has primarily been used to perform an action against a target site using the victim's privileges, but
recent techniques have been discovered to disclose information by gaining access to the response. The
risk of information disclosure is dramatically increased when the target site is vulnerable to XSS, because
XSS can be used as a platform for CSRF, allowing the attack to operate within the bounds of the same-
origin policy.
1/26/2023 HostedScan Security 5/30
Phase: Architecture and Design
Use a vetted library or framework that does not allow this weakness to occur or provides constructs that
make this weakness easier to avoid.
For example, use anti-CSRF packages such as the OWASP CSRFGuard.
Phase: Implementation
Ensure that your application is free of cross-site scripting issues, because most CSRF defenses can be
bypassed using attacker-controlled script.
Phase: Architecture and Design
Generate a unique nonce for each form, place the nonce into the form, and verify the nonce upon receipt of
the form. Be sure that the nonce is not predictable (CWE-330).
Solution Note that this can be bypassed using XSS.
Identify especially dangerous operations. When the user performs a dangerous operation, send a separate
confirmation request to ensure that the user intended to perform that operation.
Note that this can be bypassed using XSS.
Use the ESAPI Session Management control.
This control includes a component for CSRF.
Do not use the GET method for any request that triggers a state change.
Phase: Implementation
Check the HTTP Referer header to see if the request originated from an expected page. This could break
legitimate functionality, because users or proxies may have disabled sending the Referer for privacy
reasons.
http://projects.webappsec.org/Cross-Site-Request-Forgery
Reference
http://cwe.mitre.org/data/definitions/352.html
CWE Id 352
WASC Id 9
No known Anti-CSRF token [anticsrf, CSRFToken, __RequestVerificationToken, csrfmiddlewaretoken,
Other
authenticity_token, OWASP_CSRFTOKEN, anoncsrf, csrf_token, _csrf, _csrfSecret, __csrf_magic, CSRF,
Information
_token, _csrf_token] was found in the following HTML form: [Form 1: "id" ].
Vulnerable Target Accepted Notes
https://www.jobreg.no/
Vulnerable JS Library MEDIUM
Name Vulnerable JS Library
Description The identified library jquery, version 2.2.4 is vulnerable.
1/26/2023 HostedScan Security 6/30
Solution Please upgrade to the latest version of jquery.
https://github.com/jquery/jquery/issues/2432
http://blog.jquery.com/2016/01/08/jquery-2-2-and-1-12-released/
http://research.insecurelabs.org/jquery/test/
https://blog.jquery.com/2019/04/10/jquery-3-4-0-released/
Reference https://nvd.nist.gov/vuln/detail/CVE-2019-11358
https://nvd.nist.gov/vuln/detail/CVE-2015-9251
https://github.com/jquery/jquery/commit/753d591aea698e57d6db58c9f722cd0808619b1b
https://bugs.jquery.com/ticket/11974
https://blog.jquery.com/2020/04/10/jquery-3-5-0-released/
CWE Id 829
WASC Id -1
CVE-2020-11023
CVE-2020-11022
Other
Information
CVE-2015-9251
CVE-2019-11358
Vulnerable Target Accepted Notes
https://www.jobreg.no/
CSP: Wildcard Directive MEDIUM
Name CSP: Wildcard Directive
Content Security Policy (CSP) is an added layer of security that helps to detect and mitigate certain types
of attacks. Including (but not limited to) Cross Site Scripting (XSS), and data injection attacks. These
attacks are used for everything from data theft to site defacement or distribution of malware. CSP
Description
provides a set of standard HTTP headers that allow website owners to declare approved sources of
content that browsers should be allowed to load on that page — covered types are JavaScript, CSS, HTML
frames, fonts, images and embeddable objects such as Java applets, ActiveX, audio and video files.
Ensure that your web server, application server, load balancer, etc. is properly configured to set the
Solution
Content-Security-Policy header.
1/26/2023 HostedScan Security 7/30
http://www.w3.org/TR/CSP2/
http://www.w3.org/TR/CSP/
http://caniuse.com/#search=content+security+policy
Reference
http://content-security-policy.com/
https://github.com/shapesecurity/salvation
https://developers.google.com/web/fundamentals/security/csp#policy_applies_to_a_wide_variety_of_res
ources
CWE Id 693
WASC Id 15
The following directives either allow wildcard sources (or ancestors), are not defined, or are overly broadly
defined:
Other
img-src, form-action
Information
The directive(s): form-action are among the directives that do not fallback to default-src,
missing/excluding them is the same as allowing anything.
Vulnerable Target Accepted Notes
https://www.jobreg.no/
CSP: script-src unsafe-inline MEDIUM
Name CSP: script-src unsafe-inline
Content Security Policy (CSP) is an added layer of security that helps to detect and mitigate certain types
of attacks. Including (but not limited to) Cross Site Scripting (XSS), and data injection attacks. These
attacks are used for everything from data theft to site defacement or distribution of malware. CSP
Description
provides a set of standard HTTP headers that allow website owners to declare approved sources of
content that browsers should be allowed to load on that page — covered types are JavaScript, CSS, HTML
frames, fonts, images and embeddable objects such as Java applets, ActiveX, audio and video files.
Ensure that your web server, application server, load balancer, etc. is properly configured to set the
Solution
Content-Security-Policy header.
http://www.w3.org/TR/CSP2/
http://www.w3.org/TR/CSP/
http://caniuse.com/#search=content+security+policy
Reference
http://content-security-policy.com/
https://github.com/shapesecurity/salvation
https://developers.google.com/web/fundamentals/security/csp#policy_applies_to_a_wide_variety_of_res
ources
CWE Id 693
1/26/2023 HostedScan Security 8/30
WASC Id 15
Other
script-src includes unsafe-inline.
Information
Vulnerable Target Accepted Notes
https://www.jobreg.no/
CSP: style-src unsafe-inline MEDIUM
Name CSP: style-src unsafe-inline
Content Security Policy (CSP) is an added layer of security that helps to detect and mitigate certain types
of attacks. Including (but not limited to) Cross Site Scripting (XSS), and data injection attacks. These
attacks are used for everything from data theft to site defacement or distribution of malware. CSP
Description
provides a set of standard HTTP headers that allow website owners to declare approved sources of
content that browsers should be allowed to load on that page — covered types are JavaScript, CSS, HTML
frames, fonts, images and embeddable objects such as Java applets, ActiveX, audio and video files.
Ensure that your web server, application server, load balancer, etc. is properly configured to set the
Solution
Content-Security-Policy header.
http://www.w3.org/TR/CSP2/
http://www.w3.org/TR/CSP/
http://caniuse.com/#search=content+security+policy
Reference
http://content-security-policy.com/
https://github.com/shapesecurity/salvation
https://developers.google.com/web/fundamentals/security/csp#policy_applies_to_a_wide_variety_of_res
ources
CWE Id 693
WASC Id 15
Other
style-src includes unsafe-inline.
Information
Vulnerable Target Accepted Notes
https://www.jobreg.no/
X-Content-Type-Options Header Missing LOW
Name X-Content-Type-Options Header Missing
1/26/2023 HostedScan Security 9/30
The Anti-MIME-Sniffing header X-Content-Type-Options was not set to 'nosniff'. This allows older versions
of Internet Explorer and Chrome to perform MIME-sniffing on the response body, potentially causing the
Description response body to be interpreted and displayed as a content type other than the declared content type.
Current (early 2014) and legacy versions of Firefox will use the declared content type (if one is set), rather
than performing MIME-sniffing.
Ensure that the application/web server sets the Content-Type header appropriately, and that it sets the X-
Content-Type-Options header to 'nosniff' for all web pages.
Solution
If possible, ensure that the end user uses a standards-compliant and modern web browser that does not
perform MIME-sniffing at all, or that can be directed by the web application/web server to not perform
MIME-sniffing.
http://msdn.microsoft.com/en-us/library/ie/gg622941%28v=vs.85%29.aspx
Reference
https://owasp.org/www-community/Security_Headers
CWE Id 693
WASC Id 15
This issue still applies to error type pages (401, 403, 500, etc.) as those pages are often still affected by
injection issues, in which case there is still concern for browsers sniffing pages away from their actual
Other
content type.
Information
At "High" threshold this scan rule will not alert on client or server error responses.
Vulnerable Target Accepted Notes
https://www.jobreg.no/
Cross-Domain JavaScript Source File Inclusion LOW
Name Cross-Domain JavaScript Source File Inclusion
Description The page includes one or more script files from a third-party domain.
Ensure JavaScript source files are loaded from only trusted sources, and the sources can't be controlled by
Solution
end users of the application.
Reference
CWE Id 829
WASC Id 15
Other
Information
Vulnerable Target Accepted Notes
https://www.jobreg.no/
1/26/2023 HostedScan Security 10/30
Cookie with SameSite Attribute None LOW
Name Cookie with SameSite Attribute None
A cookie has been set with its SameSite attribute set to "none", which means that the cookie can be sent as
Description a result of a 'cross-site' request. The SameSite attribute is an effective counter measure to cross-site
request forgery, cross-site script inclusion, and timing attacks.
Solution Ensure that the SameSite attribute is set to either 'lax' or ideally 'strict' for all cookies.
Reference https://tools.ietf.org/html/draft-ietf-httpbis-cookie-same-site
CWE Id 1275
WASC Id 13
Other
Information
Vulnerable Target Accepted Notes
https://www.jobreg.no/
CSP: Notices LOW
Name CSP: Notices
Content Security Policy (CSP) is an added layer of security that helps to detect and mitigate certain types
of attacks. Including (but not limited to) Cross Site Scripting (XSS), and data injection attacks. These
attacks are used for everything from data theft to site defacement or distribution of malware. CSP
Description
provides a set of standard HTTP headers that allow website owners to declare approved sources of
content that browsers should be allowed to load on that page — covered types are JavaScript, CSS, HTML
frames, fonts, images and embeddable objects such as Java applets, ActiveX, audio and video files.
Ensure that your web server, application server, load balancer, etc. is properly configured to set the
Solution
Content-Security-Policy header.
http://www.w3.org/TR/CSP2/
http://www.w3.org/TR/CSP/
http://caniuse.com/#search=content+security+policy
Reference
http://content-security-policy.com/
https://github.com/shapesecurity/salvation
https://developers.google.com/web/fundamentals/security/csp#policy_applies_to_a_wide_variety_of_res
ources
1/26/2023 HostedScan Security 11/30
CWE Id 693
WASC Id 15
Warnings:
Other
The report-uri directive has ben deprecated in favor of the new report-to directive
Information
Duplicate scheme data:
Vulnerable Target Accepted Notes
https://www.jobreg.no/
1/26/2023 HostedScan Security 12/30
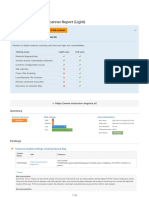
Active Web Application Vulnerabilities
The OWASP ZAP active web application scan crawls the pages of a web application. It scans for all of the passive scan checks and
additionally makes requests and submits forms to actively test for more vulnerabilities. The active scan checks for vulnerabilities
such as SQL injection, remote command execution, XSS, and more.
Total Risks
Total number of risks found by the active web application vulnerability scan.
1
5
4
0
High Medium Low Accepted
Risks Summary
Summary of detected risks.
Open Accepted
Threat Level Title
Count Count
HIGH Path Traversal 1 0
MEDIUM Absence of Anti-CSRF Tokens 1 0
MEDIUM Vulnerable JS Library 1 0
MEDIUM CSP: Wildcard Directive 1 0
MEDIUM CSP: script-src unsafe-inline 1 0
MEDIUM CSP: style-src unsafe-inline 1 0
LOW Cross-Domain JavaScript Source File Inclusion 1 0
LOW X-Content-Type-Options Header Missing 1 0
LOW Cookie without SameSite Attribute 1 0
LOW CSP: Notices 1 0
1/26/2023 HostedScan Security 13/30
Risks Per Target Summary
Breakdown of risk counts for each target.
Target High Medium Low Accepted
https://www.jobreg.no/ 1 5 4 0
Full Risk Details
Detailed information about each risk found by the scan.
Path Traversal HIGH
Name Path Traversal
The Path Traversal attack technique allows an attacker access to files, directories, and commands that
potentially reside outside the web document root directory. An attacker may manipulate a URL in such a
way that the web site will execute or reveal the contents of arbitrary files anywhere on the web server. Any
device that exposes an HTTP-based interface is potentially vulnerable to Path Traversal.
Most web sites restrict user access to a specific portion of the file-system, typically called the "web
document root" or "CGI root" directory. These directories contain the files intended for user access and the
executable necessary to drive web application functionality. To access files or execute commands
anywhere on the file-system, Path Traversal attacks will utilize the ability of special-characters sequences.
The most basic Path Traversal attack uses the "../" special-character sequence to alter the resource
location requested in the URL. Although most popular web servers will prevent this technique from
Description escaping the web document root, alternate encodings of the "../" sequence may help bypass the security
filters. These method variations include valid and invalid Unicode-encoding ("..%u2216" or "..%c0%af") of the
forward slash character, backslash characters ("..\") on Windows-based servers, URL encoded characters
"%2e%2e%2f"), and double URL encoding ("..%255c") of the backslash character.
Even if the web server properly restricts Path Traversal attempts in the URL path, a web application itself
may still be vulnerable due to improper handling of user-supplied input. This is a common problem of web
applications that use template mechanisms or load static text from files. In variations of the attack, the
original URL parameter value is substituted with the file name of one of the web application's dynamic
scripts. Consequently, the results can reveal source code because the file is interpreted as text instead of
an executable script. These techniques often employ additional special characters such as the dot (".") to
reveal the listing of the current working directory, or "%00" NULL characters in order to bypass rudimentary
file extension checks.
1/26/2023 HostedScan Security 14/30
Assume all input is malicious. Use an "accept known good" input validation strategy, i.e., use an allow list of
acceptable inputs that strictly conform to specifications. Reject any input that does not strictly conform to
specifications, or transform it into something that does. Do not rely exclusively on looking for malicious or
malformed inputs (i.e., do not rely on a deny list). However, deny lists can be useful for detecting potential
attacks or determining which inputs are so malformed that they should be rejected outright.
When performing input validation, consider all potentially relevant properties, including length, type of
input, the full range of acceptable values, missing or extra inputs, syntax, consistency across related fields,
and conformance to business rules. As an example of business rule logic, "boat" may be syntactically valid
because it only contains alphanumeric characters, but it is not valid if you are expecting colors such as
"red" or "blue."
For filenames, use stringent allow lists that limit the character set to be used. If feasible, only allow a single
"." character in the filename to avoid weaknesses, and exclude directory separators such as "/". Use an
allow list of allowable file extensions.
Warning: if you attempt to cleanse your data, then do so that the end result is not in the form that can be
dangerous. A sanitizing mechanism can remove characters such as '.' and ';' which may be required for
some exploits. An attacker can try to fool the sanitizing mechanism into "cleaning" data into a dangerous
form. Suppose the attacker injects a '.' inside a filename (e.g. "sensi.tiveFile") and the sanitizing mechanism
removes the character resulting in the valid filename, "sensitiveFile". If the input data are now assumed to
be safe, then the file may be compromised.
Inputs should be decoded and canonicalized to the application's current internal representation before
Solution being validated. Make sure that your application does not decode the same input twice. Such errors could
be used to bypass allow list schemes by introducing dangerous inputs after they have been checked.
Use a built-in path canonicalization function (such as realpath() in C) that produces the canonical version
of the pathname, which effectively removes ".." sequences and symbolic links.
Run your code using the lowest privileges that are required to accomplish the necessary tasks. If possible,
create isolated accounts with limited privileges that are only used for a single task. That way, a successful
attack will not immediately give the attacker access to the rest of the software or its environment. For
example, database applications rarely need to run as the database administrator, especially in day-to-day
operations.
When the set of acceptable objects, such as filenames or URLs, is limited or known, create a mapping from
a set of fixed input values (such as numeric IDs) to the actual filenames or URLs, and reject all other inputs.
Run your code in a "jail" or similar sandbox environment that enforces strict boundaries between the
process and the operating system. This may effectively restrict which files can be accessed in a particular
directory or which commands can be executed by your software.
OS-level examples include the Unix chroot jail, AppArmor, and SELinux. In general, managed code may
provide some protection. For example, java.io.FilePermission in the Java SecurityManager allows you to
specify restrictions on file operations.
This may not be a feasible solution, and it only limits the impact to the operating system; the rest of your
application may still be subject to compromise.
http://projects.webappsec.org/Path-Traversal
Reference
http://cwe.mitre.org/data/definitions/22.html
CWE Id 22
WASC Id 33
Other
Check 3
Information
Vulnerable Target Accepted Notes
https://www.jobreg.no/
1/26/2023 HostedScan Security 15/30
Absence of Anti-CSRF Tokens MEDIUM
Name Absence of Anti-CSRF Tokens
No Anti-CSRF tokens were found in a HTML submission form.
A cross-site request forgery is an attack that involves forcing a victim to send an HTTP request to a target
destination without their knowledge or intent in order to perform an action as the victim. The underlying
cause is application functionality using predictable URL/form actions in a repeatable way. The nature of
the attack is that CSRF exploits the trust that a web site has for a user. By contrast, cross-site scripting
(XSS) exploits the trust that a user has for a web site. Like XSS, CSRF attacks are not necessarily cross-
site, but they can be. Cross-site request forgery is also known as CSRF, XSRF, one-click attack, session
riding, confused deputy, and sea surf.
CSRF attacks are effective in a number of situations, including:
Description
* The victim has an active session on the target site.
* The victim is authenticated via HTTP auth on the target site.
* The victim is on the same local network as the target site.
CSRF has primarily been used to perform an action against a target site using the victim's privileges, but
recent techniques have been discovered to disclose information by gaining access to the response. The
risk of information disclosure is dramatically increased when the target site is vulnerable to XSS, because
XSS can be used as a platform for CSRF, allowing the attack to operate within the bounds of the same-
origin policy.
Phase: Architecture and Design
Use a vetted library or framework that does not allow this weakness to occur or provides constructs that
make this weakness easier to avoid.
For example, use anti-CSRF packages such as the OWASP CSRFGuard.
Phase: Implementation
Ensure that your application is free of cross-site scripting issues, because most CSRF defenses can be
bypassed using attacker-controlled script.
Phase: Architecture and Design
Generate a unique nonce for each form, place the nonce into the form, and verify the nonce upon receipt of
the form. Be sure that the nonce is not predictable (CWE-330).
Solution Note that this can be bypassed using XSS.
Identify especially dangerous operations. When the user performs a dangerous operation, send a separate
confirmation request to ensure that the user intended to perform that operation.
Note that this can be bypassed using XSS.
Use the ESAPI Session Management control.
This control includes a component for CSRF.
Do not use the GET method for any request that triggers a state change.
Phase: Implementation
Check the HTTP Referer header to see if the request originated from an expected page. This could break
legitimate functionality, because users or proxies may have disabled sending the Referer for privacy
reasons.
1/26/2023 HostedScan Security 16/30
http://projects.webappsec.org/Cross-Site-Request-Forgery
Reference
http://cwe.mitre.org/data/definitions/352.html
CWE Id 352
WASC Id 9
No known Anti-CSRF token [anticsrf, CSRFToken, __RequestVerificationToken, csrfmiddlewaretoken,
Other
authenticity_token, OWASP_CSRFTOKEN, anoncsrf, csrf_token, _csrf, _csrfSecret, __csrf_magic, CSRF,
Information
_token, _csrf_token] was found in the following HTML form: [Form 1: "id" ].
Vulnerable Target Accepted Notes
https://www.jobreg.no/
Vulnerable JS Library MEDIUM
Name Vulnerable JS Library
Description The identified library jquery, version 2.2.4 is vulnerable.
Solution Please upgrade to the latest version of jquery.
https://github.com/jquery/jquery/issues/2432
http://blog.jquery.com/2016/01/08/jquery-2-2-and-1-12-released/
http://research.insecurelabs.org/jquery/test/
https://blog.jquery.com/2019/04/10/jquery-3-4-0-released/
Reference https://nvd.nist.gov/vuln/detail/CVE-2019-11358
https://nvd.nist.gov/vuln/detail/CVE-2015-9251
https://github.com/jquery/jquery/commit/753d591aea698e57d6db58c9f722cd0808619b1b
https://bugs.jquery.com/ticket/11974
https://blog.jquery.com/2020/04/10/jquery-3-5-0-released/
CWE Id 829
WASC Id -1
CVE-2020-11023
Other CVE-2020-11022
Information CVE-2015-9251
CVE-2019-11358
1/26/2023 HostedScan Security 17/30
Vulnerable Target Accepted Notes
https://www.jobreg.no/
CSP: Wildcard Directive MEDIUM
Name CSP: Wildcard Directive
Content Security Policy (CSP) is an added layer of security that helps to detect and mitigate certain types
of attacks. Including (but not limited to) Cross Site Scripting (XSS), and data injection attacks. These
attacks are used for everything from data theft to site defacement or distribution of malware. CSP
Description
provides a set of standard HTTP headers that allow website owners to declare approved sources of
content that browsers should be allowed to load on that page — covered types are JavaScript, CSS, HTML
frames, fonts, images and embeddable objects such as Java applets, ActiveX, audio and video files.
Ensure that your web server, application server, load balancer, etc. is properly configured to set the
Solution
Content-Security-Policy header.
http://www.w3.org/TR/CSP2/
http://www.w3.org/TR/CSP/
http://caniuse.com/#search=content+security+policy
Reference http://content-security-policy.com/
https://github.com/shapesecurity/salvation
https://developers.google.com/web/fundamentals/security/csp#policy_applies_to_a_wide_variety_of_res
ources
CWE Id 693
WASC Id 15
The following directives either allow wildcard sources (or ancestors), are not defined, or are overly broadly
defined:
Other
img-src, form-action
Information
The directive(s): form-action are among the directives that do not fallback to default-src,
missing/excluding them is the same as allowing anything.
Vulnerable Target Accepted Notes
https://www.jobreg.no/
CSP: script-src unsafe-inline MEDIUM
Name CSP: script-src unsafe-inline
1/26/2023 HostedScan Security 18/30
Content Security Policy (CSP) is an added layer of security that helps to detect and mitigate certain types
of attacks. Including (but not limited to) Cross Site Scripting (XSS), and data injection attacks. These
attacks are used for everything from data theft to site defacement or distribution of malware. CSP
Description
provides a set of standard HTTP headers that allow website owners to declare approved sources of
content that browsers should be allowed to load on that page — covered types are JavaScript, CSS, HTML
frames, fonts, images and embeddable objects such as Java applets, ActiveX, audio and video files.
Ensure that your web server, application server, load balancer, etc. is properly configured to set the
Solution
Content-Security-Policy header.
http://www.w3.org/TR/CSP2/
http://www.w3.org/TR/CSP/
http://caniuse.com/#search=content+security+policy
Reference
http://content-security-policy.com/
https://github.com/shapesecurity/salvation
https://developers.google.com/web/fundamentals/security/csp#policy_applies_to_a_wide_variety_of_res
ources
CWE Id 693
WASC Id 15
Other
script-src includes unsafe-inline.
Information
Vulnerable Target Accepted Notes
https://www.jobreg.no/
CSP: style-src unsafe-inline MEDIUM
Name CSP: style-src unsafe-inline
Content Security Policy (CSP) is an added layer of security that helps to detect and mitigate certain types
of attacks. Including (but not limited to) Cross Site Scripting (XSS), and data injection attacks. These
attacks are used for everything from data theft to site defacement or distribution of malware. CSP
Description
provides a set of standard HTTP headers that allow website owners to declare approved sources of
content that browsers should be allowed to load on that page — covered types are JavaScript, CSS, HTML
frames, fonts, images and embeddable objects such as Java applets, ActiveX, audio and video files.
Ensure that your web server, application server, load balancer, etc. is properly configured to set the
Solution
Content-Security-Policy header.
1/26/2023 HostedScan Security 19/30
http://www.w3.org/TR/CSP2/
http://www.w3.org/TR/CSP/
http://caniuse.com/#search=content+security+policy
Reference http://content-security-policy.com/
https://github.com/shapesecurity/salvation
https://developers.google.com/web/fundamentals/security/csp#policy_applies_to_a_wide_variety_of_res
ources
CWE Id 693
WASC Id 15
Other
style-src includes unsafe-inline.
Information
Vulnerable Target Accepted Notes
https://www.jobreg.no/
Cross-Domain JavaScript Source File Inclusion LOW
Name Cross-Domain JavaScript Source File Inclusion
Description The page includes one or more script files from a third-party domain.
Ensure JavaScript source files are loaded from only trusted sources, and the sources can't be controlled by
Solution
end users of the application.
Reference
CWE Id 829
WASC Id 15
Other
Information
Vulnerable Target Accepted Notes
https://www.jobreg.no/
X-Content-Type-Options Header Missing LOW
Name X-Content-Type-Options Header Missing
1/26/2023 HostedScan Security 20/30
The Anti-MIME-Sniffing header X-Content-Type-Options was not set to 'nosniff'. This allows older versions
of Internet Explorer and Chrome to perform MIME-sniffing on the response body, potentially causing the
Description response body to be interpreted and displayed as a content type other than the declared content type.
Current (early 2014) and legacy versions of Firefox will use the declared content type (if one is set), rather
than performing MIME-sniffing.
Ensure that the application/web server sets the Content-Type header appropriately, and that it sets the X-
Content-Type-Options header to 'nosniff' for all web pages.
Solution
If possible, ensure that the end user uses a standards-compliant and modern web browser that does not
perform MIME-sniffing at all, or that can be directed by the web application/web server to not perform
MIME-sniffing.
http://msdn.microsoft.com/en-us/library/ie/gg622941%28v=vs.85%29.aspx
Reference
https://owasp.org/www-community/Security_Headers
CWE Id 693
WASC Id 15
This issue still applies to error type pages (401, 403, 500, etc.) as those pages are often still affected by
Other injection issues, in which case there is still concern for browsers sniffing pages away from their actual
Information content type.
At "High" threshold this scan rule will not alert on client or server error responses.
Vulnerable Target Accepted Notes
https://www.jobreg.no/
Cookie without SameSite Attribute LOW
Name Cookie without SameSite Attribute
A cookie has been set without the SameSite attribute, which means that the cookie can be sent as a result
Description of a 'cross-site' request. The SameSite attribute is an effective counter measure to cross-site request
forgery, cross-site script inclusion, and timing attacks.
Solution Ensure that the SameSite attribute is set to either 'lax' or ideally 'strict' for all cookies.
Reference https://tools.ietf.org/html/draft-ietf-httpbis-cookie-same-site
CWE Id 1275
WASC Id 13
Other
Information
Vulnerable Target Accepted Notes
1/26/2023 HostedScan Security 21/30
https://www.jobreg.no/
CSP: Notices LOW
Name CSP: Notices
Content Security Policy (CSP) is an added layer of security that helps to detect and mitigate certain types
of attacks. Including (but not limited to) Cross Site Scripting (XSS), and data injection attacks. These
attacks are used for everything from data theft to site defacement or distribution of malware. CSP
Description
provides a set of standard HTTP headers that allow website owners to declare approved sources of
content that browsers should be allowed to load on that page — covered types are JavaScript, CSS, HTML
frames, fonts, images and embeddable objects such as Java applets, ActiveX, audio and video files.
Ensure that your web server, application server, load balancer, etc. is properly configured to set the
Solution
Content-Security-Policy header.
http://www.w3.org/TR/CSP2/
http://www.w3.org/TR/CSP/
http://caniuse.com/#search=content+security+policy
Reference http://content-security-policy.com/
https://github.com/shapesecurity/salvation
https://developers.google.com/web/fundamentals/security/csp#policy_applies_to_a_wide_variety_of_res
ources
CWE Id 693
WASC Id 15
Warnings:
Other
The report-uri directive has ben deprecated in favor of the new report-to directive
Information
Duplicate scheme data:
Vulnerable Target Accepted Notes
https://www.jobreg.no/
1/26/2023 HostedScan Security 22/30
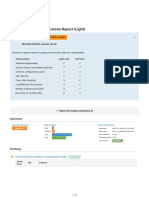
SSL/TLS Security
The SSLyze security scan checks for misconfigured SSL/TLS certificates, expired certificates, weak ciphers, and SSL/TLS
vulnerabilities such as Heartbleed.
Total Risks
Total number of risks found by the SSL/TLS security scan.
0
0
0
0
High Medium Low Accepted
1/26/2023 HostedScan Security 23/30
Network Vulnerabilities
The OpenVAS network vulnerability scan tests servers and network connected devices for over 50,000 vulnerabilities.
Total Risks
Total number of risks found by the network vulnerability scan.
0
0
1
0
High Medium Low Accepted
Risks Summary
Summary of detected risks.
CVSS Open Accepted
Threat Level Title
Score Count Count
LOW TCP timestamps 2.6 1 0
Risks Per Target Summary
Breakdown of risk counts for each target.
Target High Medium Low Accepted
https://www.jobreg.no/ 0 0 1 0
Full Risk Details
Detailed information about each risk found by the scan.
TCP timestamps LOW
nvt
oid 1.3.6.1.4.1.25623.1.0.80091
type nvt
1/26/2023 HostedScan Security 24/30
name TCP timestamps
family General
cvss_base 2.6
score 2.6
type cvss_base_v2
origin
severities
severity date 2008-10-24T21:33:44Z
score 2.6
value AV:N/AC:H/Au:N/C:P/I:N/A:N
cvss_base_
AV:N/AC:H/Au:N/C:P/I:N/A:N
vector
The remote host implements TCP timestamps and therefore
summary
allows to compute
the uptime.
The remote host implements TCP timestamps, as defined by
insight
RFC1323/RFC7323.
affected TCP implementations that implement RFC1323/RFC7323.
tags A side effect of this feature is that the uptime of the remote
host
impact
can sometimes be computed.
To disable TCP timestamps on linux add the line
solution
'net.ipv4.tcp_timestamps
Special IP packets are forged and sent with a little delay in
vuldetect between to the
target IP. The responses are searched for a
timestamps. If found, the timestamps are reported.
solution_ty
Mitigation
pe
To disable TCP timestamps on linux add the line
'net.ipv4.tcp_timestamps = 0' to
/etc/sysctl.conf. Execute 'sysctl -p'
to apply the settings at runtime.
To disable TCP timestamps on
Windows execute 'netsh int tcp set global timestamps=disabled'
Starting with Windows Server 2008 and Vista, the timestamp can
_
not be completely disabled.
The default behavior of the TCP/IP
solution
stack on this Systems is to not use the
Timestamp options when
initiating TCP connections, but use them if the TCP peer
that is
initiating communication includes them in their synchronize (SYN)
segment.
See the references for more information.
type Mitigation
1/26/2023 HostedScan Security 25/30
type url
id http://www.ietf.org/rfc/rfc1323.txt
type url
refs ref id http://www.ietf.org/rfc/rfc7323.txt
type url
https://web.archive.org/web/2015121307
id 2445/http://www.microsoft.com/en-
us/download/details.aspx?id=9152
threat Low
severity 2.6
value 80
qod
type
Vulnerable Target Accepted Notes
https://www.jobreg.no/
1/26/2023 HostedScan Security 26/30
Open TCP Ports
The NMAP TCP port scan discovers open ports on with a complete scan of ports 0 to 65535.
Total Risks
Total number of risks found by the TCP port scan.
0
2
0
0
High Medium Low Accepted
Open Ports Summary
Summary of detected open ports.
Open Accepted
Threat Level Title
Count Count
MEDIUM Open TCP Port: 443 1 0
MEDIUM Open TCP Port: 80 1 0
Open Ports per Target
Breakdown of open ports for each target.
Target High Medium Low Accepted
https://www.jobreg.no/ 0 2 0 0
Full Open Port Details
Complete list of each open port found by the scan.
Open TCP Port: 443 MEDIUM
Title Open Port: 443
1/26/2023 HostedScan Security 27/30
An open port may be an expected configuration. For example, web servers use port 80 to serve websites
over http and port 443 to serve websites over https. For a list of commonly used ports see
https://en.wikipedia.org/wiki/List_of_TCP_and_UDP_port_numbers.
Details
An unexpected open port could give unintended access to applications, data, and private networks. Open
ports can also be dangerous when expected services are out of date and exploited through security
vulnerabilities.
Vulnerable Target Accepted Notes
https://www.jobreg.no/
Open TCP Port: 80 MEDIUM
Title Open Port: 80
An open port may be an expected configuration. For example, web servers use port 80 to serve websites
over http and port 443 to serve websites over https. For a list of commonly used ports see
https://en.wikipedia.org/wiki/List_of_TCP_and_UDP_port_numbers.
Details
An unexpected open port could give unintended access to applications, data, and private networks. Open
ports can also be dangerous when expected services are out of date and exploited through security
vulnerabilities.
Vulnerable Target Accepted Notes
https://www.jobreg.no/
1/26/2023 HostedScan Security 28/30
Open UDP Ports
The NMAP UDP port scan discovers open ports of common UDP services.
Total Risks
Total number of risks found by the UDP port scan.
0
0
0
0
High Medium Low Accepted
1/26/2023 HostedScan Security 29/30
1/26/2023 HostedScan Security 30/30
You might also like
- Web Application Penetration Testing Report of Juice ShopDocument15 pagesWeb Application Penetration Testing Report of Juice ShopPavan Reddy50% (2)
- CFB ISD Proof of Residency Form With Another CFB FamilyDocument2 pagesCFB ISD Proof of Residency Form With Another CFB Familysail-doNo ratings yet
- Excavation Inspection HSE ChecklistDocument3 pagesExcavation Inspection HSE ChecklistSarfraz RandhawaNo ratings yet
- Personalism To RelationismDocument7 pagesPersonalism To RelationismRenatoNo ratings yet
- Peterbilt Rear Air Suspensions AdjustmentDocument42 pagesPeterbilt Rear Air Suspensions AdjustmentCellblocX83% (6)
- 2023-01-10 Hostedscan ReportDocument30 pages2023-01-10 Hostedscan ReportHemraj Patel BhuriNo ratings yet
- Owasp Zap Hostedscan Report 2024-02-12Document17 pagesOwasp Zap Hostedscan Report 2024-02-12faizan.rezaNo ratings yet
- Vulnerability Scan: Prepared byDocument14 pagesVulnerability Scan: Prepared byzitexitNo ratings yet
- Vulnerability Scan: Prepared byDocument13 pagesVulnerability Scan: Prepared byzitexitNo ratings yet
- Vulnerability Scan: Prepared byDocument17 pagesVulnerability Scan: Prepared byzitexitNo ratings yet
- Owasp Zap Hostedscan Report 2024-04-30Document16 pagesOwasp Zap Hostedscan Report 2024-04-30Tymmz AlloteyNo ratings yet
- Vulnerability Scan: Prepared byDocument20 pagesVulnerability Scan: Prepared byDiego MorenoNo ratings yet
- Cargill Web Application Scanning ReportDocument27 pagesCargill Web Application Scanning ReportHari KingNo ratings yet
- Vulnerabiliades - DiccionarioDocument142 pagesVulnerabiliades - DiccionarioJohan MorilloNo ratings yet
- ZAP Scanning: Project 2Document24 pagesZAP Scanning: Project 2Sabyasachi duttaNo ratings yet
- Vulnerability Scan: Prepared byDocument9 pagesVulnerability Scan: Prepared byPutra BagusNo ratings yet
- Rapport de Scan ThecniqueDocument10 pagesRapport de Scan ThecniqueayariimedNo ratings yet
- Security Analysis For - SnykDocument2 pagesSecurity Analysis For - SnykVivek GuptaNo ratings yet
- ZAP Scanning Report: Site: Https://webapps - Bps.go - IdDocument4 pagesZAP Scanning Report: Site: Https://webapps - Bps.go - Idyoga_wpNo ratings yet
- Cross Site Scripting (XSS)Document11 pagesCross Site Scripting (XSS)Jithukrishnan vNo ratings yet
- Security Sample VAPT ReportDocument28 pagesSecurity Sample VAPT ReportRavi GiriNo ratings yet
- Website Vulnerability Scanner Report (Light)Document4 pagesWebsite Vulnerability Scanner Report (Light)MasBaNo ratings yet
- Ridho Abdul MajidDocument24 pagesRidho Abdul MajidRidho Abdul MajidNo ratings yet
- Astra Security - Sample Report For VAPTDocument30 pagesAstra Security - Sample Report For VAPTIndian OpinionNo ratings yet
- Burp Scanner ReportDocument3 pagesBurp Scanner ReportPr RabariNo ratings yet
- Openvas Hostedscan Report 2024-04-30Document18 pagesOpenvas Hostedscan Report 2024-04-30Tymmz AlloteyNo ratings yet
- (Divi Report) Daptatech RepDocument5 pages(Divi Report) Daptatech RepcarlosNo ratings yet
- Astra Security Sample VAPT ReportDocument28 pagesAstra Security Sample VAPT Reporthanuman1999No ratings yet
- PentestTools WebsiteScanner ReportDocument5 pagesPentestTools WebsiteScanner ReportmiguelNo ratings yet
- XssauditorDocument9 pagesXssauditorcajeha6903No ratings yet
- PentestTools WebsiteScanner ReportDocument5 pagesPentestTools WebsiteScanner ReportSunil Kumar SharmaNo ratings yet
- Executive Summary: Table of ContentsDocument6 pagesExecutive Summary: Table of Contentsharitripathi52552gmail.comNo ratings yet
- Cross Site ScriptingDocument15 pagesCross Site ScriptingHiNo ratings yet
- 05.HTTPS Flood Protection ModuleDocument6 pages05.HTTPS Flood Protection ModuleLe Vinh HienNo ratings yet
- OWASP LA The Last XSS Defense Talk Jim Manico 2018 08Document75 pagesOWASP LA The Last XSS Defense Talk Jim Manico 2018 08Ismael OliveiraNo ratings yet
- Adopting Active Risk For Vulnerability PrioritizationDocument12 pagesAdopting Active Risk For Vulnerability PrioritizationRuben BorregaNo ratings yet
- PentestTools WebsiteScanner ReportDocument7 pagesPentestTools WebsiteScanner ReportMauricio CerratoNo ratings yet
- What Is Cross-Site Scripting (XSS) and How To Prevent It - WebDocument6 pagesWhat Is Cross-Site Scripting (XSS) and How To Prevent It - WebYouNo ratings yet
- XSS in Theory: Cross-Site ScriptingDocument12 pagesXSS in Theory: Cross-Site ScriptingHesham MedhatNo ratings yet
- Cross-Site Scripting (XSS) - OWASPDocument9 pagesCross-Site Scripting (XSS) - OWASPCha OsNo ratings yet
- Owasp Zap Scanner Output 2024-02-29Document21 pagesOwasp Zap Scanner Output 2024-02-29b.nandhu2810No ratings yet
- Comprehensive Report: Acunetix Threat Level 3Document37 pagesComprehensive Report: Acunetix Threat Level 3Yudha Trias RusmanaNo ratings yet
- Website Vulnerability Scanner Report (Light)Document5 pagesWebsite Vulnerability Scanner Report (Light)Ilija DodevskiNo ratings yet
- Website Vulnerability Scanner Report (Light)Document5 pagesWebsite Vulnerability Scanner Report (Light)Muhammad LuludNo ratings yet
- Don't Trust The Locals: Investigating The Prevalence of Persistent Client-Side Cross-Site Scripting in The WildDocument15 pagesDon't Trust The Locals: Investigating The Prevalence of Persistent Client-Side Cross-Site Scripting in The Wildraed waheedNo ratings yet
- Sample Report WebDocument19 pagesSample Report WebMuhammad AwaisNo ratings yet
- Scan Meteored AcunetixDocument5 pagesScan Meteored AcunetixAlejandro Antonio Loyola RuizNo ratings yet
- Detect and Respond To Attacks AimDocument5 pagesDetect and Respond To Attacks Aimreddy ramya sri ghantasalaNo ratings yet
- A Novel Technique To Prevent SQL Injection and Cross-Site Scripting Attacks Using Knuth-Morris-Pratt String Match AlgorithmDocument14 pagesA Novel Technique To Prevent SQL Injection and Cross-Site Scripting Attacks Using Knuth-Morris-Pratt String Match AlgorithmChandan NareshNo ratings yet
- Threat Model For BwappDocument38 pagesThreat Model For Bwappshinde_jayesh2005No ratings yet
- 2023 08 03 ZAP ReportDocument58 pages2023 08 03 ZAP ReportQuang Hà ĐặngNo ratings yet
- Foundation of Cyber SecurityDocument58 pagesFoundation of Cyber SecurityPradip SarkerNo ratings yet
- Executive Summary: Table of ContentsDocument7 pagesExecutive Summary: Table of Contentsharitripathi52552gmail.comNo ratings yet
- Documentation On Xss VulnerabilityDocument3 pagesDocumentation On Xss VulnerabilitySujithNo ratings yet
- AssessmentDocument50 pagesAssessmentPham Dinh ChungNo ratings yet
- Big-Ip Asm Comprehensive: Application SecurityDocument17 pagesBig-Ip Asm Comprehensive: Application SecurityLuis DiazNo ratings yet
- Website Vulnerability Scanner Report (Light)Document6 pagesWebsite Vulnerability Scanner Report (Light)Stevi NangonNo ratings yet
- PentestTools WebsiteScanner ReportDocument5 pagesPentestTools WebsiteScanner ReportrayjoneskeNo ratings yet
- Hillstone_I-Series_sBDS-V3.0_ENDocument4 pagesHillstone_I-Series_sBDS-V3.0_ENDonny TahirNo ratings yet
- Infrastructure SecurityDocument107 pagesInfrastructure SecurityDoctor LyricsNo ratings yet
- Ios Static Analysis Report: Mini Militia Mini Militia (4.3.2) (4.3.2)Document17 pagesIos Static Analysis Report: Mini Militia Mini Militia (4.3.2) (4.3.2)Karan KisnaniNo ratings yet
- Research Paper On XssDocument6 pagesResearch Paper On Xssfapavelyfel2100% (1)
- Hack2Secure Web Application Security Testing Workshop Reference GuideDocument9 pagesHack2Secure Web Application Security Testing Workshop Reference GuideJavvedNo ratings yet
- Penetration Testing Fundamentals-2: Penetration Testing Study Guide To Breaking Into SystemsFrom EverandPenetration Testing Fundamentals-2: Penetration Testing Study Guide To Breaking Into SystemsNo ratings yet
- Unit - 1Document2 pagesUnit - 1Hemraj Patel BhuriNo ratings yet
- Unit - 2Document1 pageUnit - 2Hemraj Patel BhuriNo ratings yet
- Quetion BankDocument1 pageQuetion BankHemraj Patel BhuriNo ratings yet
- Machine Learning LibrariesDocument38 pagesMachine Learning LibrariesHemraj Patel BhuriNo ratings yet
- Quetion Bank NSMLDocument6 pagesQuetion Bank NSMLHemraj Patel BhuriNo ratings yet
- Unit 1: Advanced Computer Networks & SecurityDocument64 pagesUnit 1: Advanced Computer Networks & SecurityHemraj Patel BhuriNo ratings yet
- Lab ManualDocument54 pagesLab ManualHemraj Patel BhuriNo ratings yet
- 2023-01-10 Hostedscan ReportDocument30 pages2023-01-10 Hostedscan ReportHemraj Patel BhuriNo ratings yet
- Project ReportDocument41 pagesProject ReportHemraj Patel BhuriNo ratings yet
- Internship (Soc)Document11 pagesInternship (Soc)Hemraj Patel BhuriNo ratings yet
- Iso 27001 2013 - IsmsDocument34 pagesIso 27001 2013 - IsmsHemraj Patel BhuriNo ratings yet
- RulebookDocument8 pagesRulebookEren Koyunoğlu100% (1)
- "Good" LeadershipDocument5 pages"Good" LeadershipSyidiq Nack RajinNo ratings yet
- Philips Automatic Hand SanitaizerDocument24 pagesPhilips Automatic Hand SanitaizerAjith9410No ratings yet
- Chapter 9: FOREX MARKET Key PointsDocument6 pagesChapter 9: FOREX MARKET Key PointsDanica AbelardoNo ratings yet
- Beam Design Detail Report: Material and Design DataDocument33 pagesBeam Design Detail Report: Material and Design DataazwanNo ratings yet
- PracResearch2 Grade-12 Q4 Mod5 Data-Collection-Presentation-and-Analysis Version4Document59 pagesPracResearch2 Grade-12 Q4 Mod5 Data-Collection-Presentation-and-Analysis Version4MichiOdevilasNo ratings yet
- 07) YHT Realty vs. CA, GR No. 126780, Feb. 17, 2005Document15 pages07) YHT Realty vs. CA, GR No. 126780, Feb. 17, 2005justinmauricioNo ratings yet
- Full Ebook of Lipidomics Methods and Protocols 2Nd Edition Sanjoy K Bhattacharya Editor Online PDF All ChapterDocument69 pagesFull Ebook of Lipidomics Methods and Protocols 2Nd Edition Sanjoy K Bhattacharya Editor Online PDF All Chapterandrewmolina926227100% (4)
- Rocket ManualDocument1 pageRocket ManualJonEatonNo ratings yet
- CAMEE Tool 7 2 Agreement MEP Client 2013Document15 pagesCAMEE Tool 7 2 Agreement MEP Client 2013SAID RGONo ratings yet
- Name Email Phone Hometown: Authorized To Work in The US For Any EmployerDocument3 pagesName Email Phone Hometown: Authorized To Work in The US For Any EmployerR.T. CoffmanNo ratings yet
- Program of WorksDocument2 pagesProgram of WorksSimply RoseNo ratings yet
- Chapter No 03 Class 6th Notes For Computer Science English MediumDocument5 pagesChapter No 03 Class 6th Notes For Computer Science English MediumAbid HussainNo ratings yet
- Nerf2Real: Sim2Real Transfer of Vision-Guided Bipedal Motion Skills Using Neural Radiance FieldsDocument12 pagesNerf2Real: Sim2Real Transfer of Vision-Guided Bipedal Motion Skills Using Neural Radiance Fields武怡No ratings yet
- Sump Well-20 KL PDFDocument3 pagesSump Well-20 KL PDFvisali garikapatiNo ratings yet
- 2016-12-15 St. Mary's County TimesDocument32 pages2016-12-15 St. Mary's County TimesSouthern Maryland OnlineNo ratings yet
- Chapter 3Document5 pagesChapter 3Sheila ShamimiNo ratings yet
- INF1520 May 2012 Exam Answers DoneDocument7 pagesINF1520 May 2012 Exam Answers DoneNthabiseng MahlasiNo ratings yet
- Cannes Lions 2019: Digital Craft Lions ShortlistDocument18 pagesCannes Lions 2019: Digital Craft Lions Shortlistadobo magazineNo ratings yet
- Dixie ProjectorDocument2 pagesDixie ProjectorBagus SaputroNo ratings yet
- NX Shop Documentation Plug-In BaseDocument10 pagesNX Shop Documentation Plug-In BaseLÊ VĂN ĐỨCNo ratings yet
- Pricelist Laptop & PrinterDocument7 pagesPricelist Laptop & PrinterKharis FreefireNo ratings yet
- Case Concerning Rights of Nationals of The US in Morocco Summary of JudgmentDocument2 pagesCase Concerning Rights of Nationals of The US in Morocco Summary of JudgmentClarissa Beth DegamoNo ratings yet
- Buffering DataDocument4 pagesBuffering DataLeonard-Tiberiu SandorNo ratings yet
- Japan AwardsDocument3 pagesJapan AwardsLeonard LyonsNo ratings yet
- MelEye - CatalogDocument4 pagesMelEye - CatalogChinmay GhoshNo ratings yet