Professional Documents
Culture Documents
NSM Theory New
NSM Theory New
Uploaded by
guru shashankOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
NSM Theory New
NSM Theory New
Uploaded by
guru shashankCopyright:
Available Formats
Network Security & management (15CS62PT) Key Logger
KEY LOGGER
A keylogger, sometimes called a keystroke logger or keyboard capture, is a type of surveillance
technology used to monitor and record each keystroke on a specific computer. Keylogger
software is also available for use on smartphones, such as the Apple iPhone and Android
devices.
Keyloggers are often used as a spyware tool by cybercriminals to steal personally identifiable
information (PII), login credentials and sensitive enterprise data.
Some uses of keyloggers could be considered ethical or appropriate in varying degrees.
Keylogger recorders may also be used by:
• employers to observe employees' computer activities;
• parents to supervise their children's internet usage;
• device owners to track possible unauthorized activity on their devices; or
• law enforcement agencies to analyze incidents involving computer use.
Types of keyloggers
A hardware-based keylogger is a small device that serves as a connector between the keyboard
and the computer. The device is designed to resemble an ordinary keyboard PS/2 connector, part
of the computer cabling or a USB adaptor, making it relatively easy for someone who wants to
monitor a user's behavior to hide the device.
VI Sem, Dept of CSE, Siddaganga Polytechnic, Tumkur. Page 1
Network Security & management (15CS62PT) Key Logger
A keylogging software program does not require physical access to the user's computer for
installation. It can be purposefully downloaded by someone who wants to monitor activity on a
particular computer, or it can be malware downloaded unwittingly and executed as part of a
rootkit or remote administration Trojan (RAT). The rootkit can launch and operate stealthily to
evade manual detection or antivirus scans.
Most workstation keyboards plug into the back of the computer, keeping the connections out of
the user's line of sight. A hardware keylogger may also come in the form of a module that is
installed inside the keyboard itself. When the user types on the keyboard, the keylogger collects
each keystroke and saves it as text in its own hard drive, which may have a memory capacity up
to several gigabytes. The person who installed the keylogger must later return and physically
remove the device to access the gathered information. There are also wireless keylogger sniffers
that can intercept and decrypt data packets transferred between a wireless keyboard and its
receiver.
A common software keylogger typically consists of two files that get installed in the same
directory: a dynamic link library (DLL) file that does the recording and an executable file that
installs the DLL file and triggers it. The keylogger program records each keystroke the user types
and periodically uploads the information over the internet to whomever installed the program.
Hackers can design keylogging software to use keyboard application program interfaces (APIs)
to another application, malicious script injection or memory injection.
There are two main types of software keyloggers: user mode keyloggers and kernel mode
keyloggers.
VI Sem, Dept of CSE, Siddaganga Polytechnic, Tumkur. Page 2
Network Security & management (15CS62PT) Key Logger
A user mode keylogger uses a Windows API to intercept keyboard and mouse movements.
GetAsyncKeyState or GetKeyState API functions might also be captured depending on the
keylogger. These keyloggers require the attacker to actively monitor each keypress.
A kernel mode keylogger is a more powerful and complex software keylogging method. It works
with higher privileges and can be harder to locate in a system. Kernel mode keyloggers use filter
drivers that can intercept keystrokes. They can also modify the internal Windows system through
the kernel.
Some keylogging programs may also include functionality to record user data besides
keystrokes, such as capturing anything that has been copied to the clipboard and taking
screenshots of the user's screen or a single application.
Keylogger detection and removal
Due to the variety of keyloggers that use different techniques, no single detection or removal
method is considered the most effective. Since keyloggers can manipulate an operating system
kernel, examining a computer's Task Manager isn't necessarily enough to detect a keylogger.
Security software, such as an anti-keylogger software program, is designed specifically to scan
for software-based keyloggers by comparing the files on a computer against a keylogger
signature base or a checklist of common keylogger attributes. Using an anti-keylogger can be
more effective than an antivirus or antispyware program. The latter may accidentally identify a
keylogger as a legitimate program instead of spyware.
VI Sem, Dept of CSE, Siddaganga Polytechnic, Tumkur. Page 3
Network Security & management (15CS62PT) Key Logger
Depending on the technique an antispyware application uses, it may be able to locate and disable
keylogger software with lower privileges than it has. Using a network monitor will ensure the
user is notified each time an application tries to make a network connection, giving a security
team the opportunity to stop any possible keylogger activity.
Protection against keyloggers
While visual inspection can identify hardware keyloggers, it is impractical and time-consuming
to implement on a large scale. Instead, individuals can use a firewall to help protect against a
keylogger. Since keyloggers transmit data back and forth from the victim to the attacker, the
firewall could discover and prevent that data transfer.
Password managers that automatically fill in username and password fields may also help protect
against keyloggers. Monitoring software and antivirus software can also keep track of a system's
health and prevent keyloggers.
System cages that prevent access to or tampering with USB and PS/2 ports can be added to the
user's desktop setup. Extra precautions include using a security token as part of two-factor
authentication (2FA) to ensure an attacker cannot use a stolen password alone to log in to a user's
account, or using an onscreen keyboard and voice-to-text software to circumvent using a
physical keyboard.
Application allowlisting can also be used to allow only documented, authorized programs to run
on a system. It is also always a good idea to keep any system up to date.
VI Sem, Dept of CSE, Siddaganga Polytechnic, Tumkur. Page 4
You might also like
- Canara Bank Mobile Number Change and UpdateDocument1 pageCanara Bank Mobile Number Change and UpdateAnonymous YFac6px77% (44)
- Research Paper On KeyloggersDocument3 pagesResearch Paper On KeyloggersRish100% (1)
- IH-500 NI Transport Arm Troubleshooting V2.3Document27 pagesIH-500 NI Transport Arm Troubleshooting V2.3A ANo ratings yet
- Techdb Settings Guide: Cover PageDocument48 pagesTechdb Settings Guide: Cover PageionutNo ratings yet
- How To Protect Personal Information Against Keyloggers: Virus SignaturesDocument6 pagesHow To Protect Personal Information Against Keyloggers: Virus SignaturesFabienne MaryNo ratings yet
- Logik 26SDocument21 pagesLogik 26SRamsi SembiringNo ratings yet
- Keystroke LoggersDocument3 pagesKeystroke LoggersCherry MarieNo ratings yet
- Signum Soft KeyloggerDocument12 pagesSignum Soft KeyloggerLukaRaterNo ratings yet
- Synopsis of KeyloggerDocument17 pagesSynopsis of KeyloggerParvaiz RainaNo ratings yet
- CyberDocument9 pagesCyberbabulkiidNo ratings yet
- Automatic Timetable Generation Mini Project ReportDocument6 pagesAutomatic Timetable Generation Mini Project Reportabhineesh singhNo ratings yet
- Internship ReportDocument14 pagesInternship ReportPrashantNo ratings yet
- Keystroke LoggingDocument9 pagesKeystroke LoggingDarshan Singh ThakurNo ratings yet
- Seminar-I PPT Template-3rd Sem-21-22Document20 pagesSeminar-I PPT Template-3rd Sem-21-22ASAD BAIGNo ratings yet
- Subject: Network Security Topic: Keyloggers Working and TypesDocument15 pagesSubject: Network Security Topic: Keyloggers Working and TypesskjdfkjsdNo ratings yet
- Study On Key Logger: Challenges and SolutionsDocument10 pagesStudy On Key Logger: Challenges and SolutionsJeffrey walkerNo ratings yet
- Keylogger For Windows Using PythonDocument3 pagesKeylogger For Windows Using PythonEditor IJTSRDNo ratings yet
- A Survey of Keylogger in Cybersecurity EducationDocument5 pagesA Survey of Keylogger in Cybersecurity EducationEditor IJTSRDNo ratings yet
- (IJCT-V2I2P14) Authors: Ms.C.Sathya, Mr.R.B.Saroo RajDocument9 pages(IJCT-V2I2P14) Authors: Ms.C.Sathya, Mr.R.B.Saroo RajIjctJournalsNo ratings yet
- Key Logging PPT 2Document20 pagesKey Logging PPT 2Djqazxsw QazxswNo ratings yet
- Synopsis of Minor Project Keylogger': Dr. Brahampal Singh Tarun Chauhan 00820602019 1 ShiftDocument7 pagesSynopsis of Minor Project Keylogger': Dr. Brahampal Singh Tarun Chauhan 00820602019 1 ShiftTarun ChauhanNo ratings yet
- "Implementation of Keylogger Using HOOKUP Algorithm": Project SynopsisDocument7 pages"Implementation of Keylogger Using HOOKUP Algorithm": Project Synopsisraman dwivediNo ratings yet
- Key LoggersDocument3 pagesKey LoggersgiduguNo ratings yet
- Secure Software Project Report On: Key LoggerDocument10 pagesSecure Software Project Report On: Key LoggerAkash PruthiNo ratings yet
- Q.1 Mention Different Tools Used in Cyber Crime.: Ans: 1. WiresharkDocument17 pagesQ.1 Mention Different Tools Used in Cyber Crime.: Ans: 1. WiresharkayushNo ratings yet
- Windows Post Exploitation (MSF) Keylogger For SecurityDocument7 pagesWindows Post Exploitation (MSF) Keylogger For SecurityIJRASETPublicationsNo ratings yet
- Key LoggingDocument19 pagesKey LoggingJayant Pai0% (1)
- Minor Project Presentation Topic: Keylogger and PC Monitoring SystemDocument19 pagesMinor Project Presentation Topic: Keylogger and PC Monitoring SystemDivyansh Singh Sengar0% (1)
- Keylogger and SecurityDocument12 pagesKeylogger and SecuritySrikrishnarajan NatarajanNo ratings yet
- Z - Cybersecurity Unit 2Document12 pagesZ - Cybersecurity Unit 2blogsbyzmNo ratings yet
- Keylogger WPS OfficeDocument10 pagesKeylogger WPS Officeroyceangelo.buayaNo ratings yet
- Keyloger TemplateDocument20 pagesKeyloger Templatepragathi RoopaSriNo ratings yet
- Advanced Keylogger For Ethical HackingDocument5 pagesAdvanced Keylogger For Ethical HackingZoltán CserneiNo ratings yet
- Keyloggers in Cybersecurity Education: 2. An Overview of KeyloggingDocument7 pagesKeyloggers in Cybersecurity Education: 2. An Overview of KeyloggingSuresh ME100% (1)
- Key Loggers & SpywaresDocument29 pagesKey Loggers & SpywaresElit HakimiNo ratings yet
- Record The Keystrokes Made by User Using Keyloggers To Monitor The SystemsDocument4 pagesRecord The Keystrokes Made by User Using Keyloggers To Monitor The SystemsdevilNo ratings yet
- Actual Key-LoggerDocument8 pagesActual Key-LoggerdanielleNo ratings yet
- Remove Keyloggers Removal InstructionsDocument3 pagesRemove Keyloggers Removal InstructionsRihlesh ParlNo ratings yet
- Unprivileged Black-Box Detection of User-Space Key Loggers: AbstractDocument8 pagesUnprivileged Black-Box Detection of User-Space Key Loggers: AbstractInternational Journal of Engineering and TechniquesNo ratings yet
- Survey On Keyloggers A Monitoring ToolDocument3 pagesSurvey On Keyloggers A Monitoring ToolEditor IJTSRDNo ratings yet
- Cybersecurity Unit 2Document4 pagesCybersecurity Unit 2blogsbyzmNo ratings yet
- PWP MicroptojectDocument13 pagesPWP MicroptojectRed Light HackersNo ratings yet
- Ramiz 201370126Document5 pagesRamiz 201370126Ramiz IqbalNo ratings yet
- Connected Systems Require Hardware Based Security - Electronics For YouDocument3 pagesConnected Systems Require Hardware Based Security - Electronics For YouPavan Kumar ThopaNo ratings yet
- Keystroke Logging KeyloggingDocument14 pagesKeystroke Logging KeyloggingAnjali100% (1)
- SYCS TimeTableDocument3 pagesSYCS TimeTablepinkuchopra17No ratings yet
- Keystrokeinspector (Synopsis)Document10 pagesKeystrokeinspector (Synopsis)Parvaiz RainaNo ratings yet
- Key Loggers in Cyber Security EducationDocument6 pagesKey Loggers in Cyber Security EducationRama KrishnaNo ratings yet
- Hypervisor Based Mitigation Technique For Keylogger Spyware AttacksDocument6 pagesHypervisor Based Mitigation Technique For Keylogger Spyware AttacksOmar Neptali Montoya SalazarNo ratings yet
- Os AssignmentDocument5 pagesOs AssignmentRamiz IqbalNo ratings yet
- 09 KeyloggersDocument13 pages09 Keyloggersdhruv goswami50% (2)
- A Hybrid Approach Based Advanced KeyloggerDocument5 pagesA Hybrid Approach Based Advanced KeyloggerEditor IJTSRDNo ratings yet
- KeyloggerDocument6 pagesKeyloggerAnagha MNo ratings yet
- Chapter - 5 Network SecurityDocument36 pagesChapter - 5 Network SecuritySuman BhandariNo ratings yet
- NbnbifjdjvuvufjejDocument2 pagesNbnbifjdjvuvufjejLoganNo ratings yet
- KeyloggerDocument13 pagesKeyloggerStar BoyNo ratings yet
- Paper 1Document2 pagesPaper 1Aparna SadanandNo ratings yet
- Advanced Keylogger For Ethical HackingDocument6 pagesAdvanced Keylogger For Ethical HackingAnagha MNo ratings yet
- Securty FundamentalsDocument27 pagesSecurty Fundamentalssayid khalifNo ratings yet
- Keyloggers A Malicious AttackDocument5 pagesKeyloggers A Malicious AttackEditor IJTSRDNo ratings yet
- Practical 3 IsaDocument9 pagesPractical 3 IsammieduindiaanandNo ratings yet
- Cyber Unit 5 - 1627632179 - 1697003597Document10 pagesCyber Unit 5 - 1627632179 - 1697003597xyz705638No ratings yet
- Keylogger and SecurityDocument12 pagesKeylogger and SecuritySrikrishnarajan NatarajanNo ratings yet
- Sai Kiran UpdatedDocument13 pagesSai Kiran Updatedguru shashankNo ratings yet
- DC LabDocument20 pagesDC Labguru shashankNo ratings yet
- Loan Letter PDFDocument1 pageLoan Letter PDFguru shashankNo ratings yet
- Varun PDFDocument6 pagesVarun PDFguru shashankNo ratings yet
- Use Code " " To Unlock All Free Classes: Download Unacademy Learning AppDocument5 pagesUse Code " " To Unlock All Free Classes: Download Unacademy Learning AppAni Dutta100% (9)
- Database 101 - Guy Kawasaki - SsDocument2 pagesDatabase 101 - Guy Kawasaki - SsVelpandian ManiNo ratings yet
- Windows Desktop Interview Questions and AnswersDocument5 pagesWindows Desktop Interview Questions and AnswersVikas KumarNo ratings yet
- APA7 Template For IRRODL AuthorsDocument16 pagesAPA7 Template For IRRODL Authorsagus ariyanatoNo ratings yet
- Assignment AcpDocument5 pagesAssignment AcpMuhammad MohsinNo ratings yet
- JavaDocument309 pagesJavaKLMURALINo ratings yet
- S23 Guidance For Specifiers of VSS in Security Applications v4Document41 pagesS23 Guidance For Specifiers of VSS in Security Applications v4TestingtoolNo ratings yet
- Lifi PPT SlidesDocument15 pagesLifi PPT SlidesPrakash Varma100% (4)
- Online Agriculture Products StoreDocument77 pagesOnline Agriculture Products StoreShivesh ShivamNo ratings yet
- ZTE CS Low Level Design For Ethiopia Site V1.5-20150706Document171 pagesZTE CS Low Level Design For Ethiopia Site V1.5-20150706mengistu yirgaNo ratings yet
- Functions in C++Document17 pagesFunctions in C++libranhitesh7889No ratings yet
- Introduction To MultimediaDocument11 pagesIntroduction To MultimediaMichalcova Realisan JezzaNo ratings yet
- FusionCompute V100R005C00 Network Virtualization PDFDocument66 pagesFusionCompute V100R005C00 Network Virtualization PDFfirasibraheemNo ratings yet
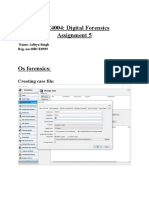
- CSE4004: Digital Forensics Assignment 5: Creating Case FileDocument12 pagesCSE4004: Digital Forensics Assignment 5: Creating Case FileADITYA SINGHNo ratings yet
- CP1252 (Windows 1252 Encoding) InfoDocument7 pagesCP1252 (Windows 1252 Encoding) InfoDulce LopezNo ratings yet
- Digital Servo Amplifier Servo Star 601... 620: Assembly, Installation, SetupDocument100 pagesDigital Servo Amplifier Servo Star 601... 620: Assembly, Installation, SetupPaul RidgeNo ratings yet
- Learning Book - AnyLogic 6 Enterprise Library Tutorial PDFDocument43 pagesLearning Book - AnyLogic 6 Enterprise Library Tutorial PDFhoussem eddineNo ratings yet
- jhtp7LM 14Document16 pagesjhtp7LM 14vicrattlehead2013No ratings yet
- Experiment Title-1: Introduction To DBMS, RDBMS, ORACLE, Basic SQL CommandsDocument7 pagesExperiment Title-1: Introduction To DBMS, RDBMS, ORACLE, Basic SQL CommandsShreyansh RajNo ratings yet
- Rosemount 702 Wireless Discrete Transmitter: Product Data SheetDocument20 pagesRosemount 702 Wireless Discrete Transmitter: Product Data SheetOmar Al SousliNo ratings yet
- Social InformaticsDocument19 pagesSocial InformaticsTUSHAR VIGHNo ratings yet
- Ergo User ManualDocument116 pagesErgo User ManualFayez AlnamarnehNo ratings yet
- TITLEDocument1 pageTITLEHarshit ChauhanNo ratings yet
- IATE API Reference 2001Document145 pagesIATE API Reference 2001LeonNo ratings yet
- Service Manual Led LCD Android SeriesDocument52 pagesService Manual Led LCD Android SeriesDarinell Marrugo GarridoNo ratings yet
- CS8451 Design and Analysis of Algorithms MCQDocument206 pagesCS8451 Design and Analysis of Algorithms MCQsanjana jadhavNo ratings yet