Professional Documents
Culture Documents
Advanced Computer Architecture (MS1101: 1. Big-O Notation
Advanced Computer Architecture (MS1101: 1. Big-O Notation
Uploaded by
Mugabe DeogratiousOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Advanced Computer Architecture (MS1101: 1. Big-O Notation
Advanced Computer Architecture (MS1101: 1. Big-O Notation
Uploaded by
Mugabe DeogratiousCopyright:
Available Formats
Advanced Computer Architecture(MS1101
Explain the characterstics of high performance computing
Why is hardware security important?Explain with an example
Hardware security protects the machine and peripheral hardware from theft and from electronic
intrusion and damage. This comes in the form of a physical device rather than software that's installed
on the hardware of a computer system.
Some of the most common examples of hardware security are hardware firewalls, scanning devices,
proxy servers, etc
One of the primary importance of hardware security is, less accessibility compared to software that
might be vulnerable to the entire world of hackers. The attackers may not easily understand the security
built on the premise.
Below are other importance of handware security
Security in hardware offers performance and power consumption advantages over its software
equivalents.
◼ Increasing amounts of data being processed and the complexity of encryption algorithms slows down
security implementations severely.
◼ Often times these same encryption algorithms can be implemented in hardware.
Design and Analysis of Algorithms(MS1103)
How is an algorithm’s time efficiency measured?
Firstly, an algorithm is defined as a collection of unambiguous instructions occurring in some specific
sequence and such an algorithm should produce for given input in finite amount of time.
Time efficiency is one of the factors considered while analyzing the algorithm. It determines the amount
of time taken by an algorithm to run.
The efficiency can be measured by computing time complexity of each algorithm and this can be well
represented by using asymptotic notations.
There are mainly three asymptotic notations:
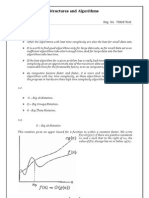
1. Big-O notation
This document has been classified as CONFIDENTIAL-EXTERNAL by Centenary Bank.
The big-o notation is denoted by ‘O’ .It is a method of representing the upper bound of algorithm’s
running time. Thus, it gives the worst-case complexity of an algorithm.
For a given function g(n), O(g(n)) is denoted by:
O(g(n)) = { f(n): there exist positive constants c and n 0
such that 0 ≤ f(n) ≤ cg(n) for all n ≥ n 0 }
The above expression can be described as a function f(n) belongs to the set O(g(n)) if there exists a
positive constant c such that it lies between 0 and cg(n), for sufficiently large n.
For any value of n, the running time of an algorithm does not cross the time provided by O(g(n)).
Since it gives the worst-case running time of an algorithm, it is widely used to analyze an algorithm as
we are always interested in the worst-case scenario.
2. Omega notation
It is denoted by Ω.This notation is used to represent the lower bound of algorithm’s running time.
Thus, it provides the best case complexity of an algorithm.
For a function g(n), Θ(g(n)) is given by the relation:
Ω(g(n)) = { f(n): there exist positive constants c and n 0
such that 0 ≤ cg(n) ≤ f(n) for all n ≥ n 0 }
The above expression can be described as a function f(n) belongs to the set Ω(g(n)) if there exists a
positive constant c such that it lies above cg(n), for sufficiently large n.
For any value of n, the minimum time required by the algorithm is given by Omega Ω(g(n)).
3. Theta Notation
It is denoted by Θ. This method represents the upper bound and the lower bound of the running
time. It is used for analyzing the average-case complexity of an algorithm.
For a function g(n), Θ(g(n)) is given by the relation:
Θ(g(n)) = { f(n): there exist positive constants c1, c2 and n0
such that 0 ≤ c 1g(n) ≤ f(n) ≤ c2g(n) for all n ≥ n0 }
The above expression can be described as a function f(n) belongs to the set Θ(g(n)) if there exist positive
constants c1 and c2 such that it can be sandwiched between c1g(n) and c2g(n), for sufficiently large n.
If a function f(n) lies anywhere in between c1g(n) and c2g(n) for all n ≥ n0, then f(n) is said to be
asymptotically tight bound.
This document has been classified as CONFIDENTIAL-EXTERNAL by Centenary Bank.
Data Modelling and Design(MS1102)
What Are the Three Types of Data Models?
What Does a Data Modeler Use Normalization For?
Normalization is a technique that systematically eliminates data redundancies in a relational database
by eliminating undesirable characteristics like Insertion, Update and Deletion anomalies. Failure to
eliminate anomalies leads to data redundancy and can cause data integrity and other problems as the
database grows.
1. It is used to remove the duplicate data and database anomalies from the relational table.
2. Normalization helps to reduce redundancy and complexity by examining new data types
used in the table.
3. It is helpful to divide the large database table into smaller tables and link them using
relationship.
4. It avoids duplicate data or no repeating groups into a table.
5. It reduces the chances for anomalies to occur in a database.
Advanced Java Programming - Theory & Practical(MS1104)
Explain with implementation about Inheritance and usage of Super keyword
Explain steps in JDBC and different types of statements in JDBC
Technical Communication for Business Leaders(MS1106)
Briefly explain why your appearance is important in communication?
You have been selected to educate a group officials regarding learning how to listen whenever there is
any communication on the current economic criss. Briefly explain why it is important to be a good
listener?
This document has been classified as CONFIDENTIAL-EXTERNAL by Centenary Bank.
You might also like
- Rocky Manual PDFDocument211 pagesRocky Manual PDFRaghul Ravi88% (8)
- Delete Dummy Shipment Data-NewDocument4 pagesDelete Dummy Shipment Data-NewPoorna Chandra GaralapatiNo ratings yet
- Informatica Complex Realtime ScenariosDocument2 pagesInformatica Complex Realtime ScenariosMahesh G Raju67% (3)
- Mcs 021Document171 pagesMcs 021Agnel ThomasNo ratings yet
- Datastructuers and Algorithms in C++Document5 pagesDatastructuers and Algorithms in C++sachin kumar shawNo ratings yet
- A Practical Introduction To Data Structures and Algorithm AnalysisDocument346 pagesA Practical Introduction To Data Structures and Algorithm AnalysisantenehgebNo ratings yet
- DAA Unit 1,2,3-1Document46 pagesDAA Unit 1,2,3-1abdulshahed231No ratings yet
- Mcs 21Document171 pagesMcs 21firstname234No ratings yet
- 351CS42 Data StructureDocument134 pages351CS42 Data Structurekamizachipango202No ratings yet
- Time and Space Analysis of AlgorithmsDocument5 pagesTime and Space Analysis of AlgorithmsAbhishek MitraNo ratings yet
- Analysis of AlgorithmDocument11 pagesAnalysis of Algorithmprerna kanawadeNo ratings yet
- Daa Unit-1: Introduction To AlgorithmsDocument16 pagesDaa Unit-1: Introduction To AlgorithmsmhghtgxdfhhjkjlNo ratings yet
- Throughput Comparison Results of Proposed Algorithm With Existing AlgorithmDocument7 pagesThroughput Comparison Results of Proposed Algorithm With Existing AlgorithmtheijesNo ratings yet
- DSA Using C - Quick GuideDocument71 pagesDSA Using C - Quick GuideAfroz Alam Ki VinesNo ratings yet
- Unit I Asymptotic Notations Asymptotic Notation: O, , !, andDocument59 pagesUnit I Asymptotic Notations Asymptotic Notation: O, , !, andsrivisundararajuNo ratings yet
- Asymptotic Analysis 2Document6 pagesAsymptotic Analysis 2Destiny OgahNo ratings yet
- Complexity Space N TimeDocument36 pagesComplexity Space N Timeapi-3814408100% (4)
- 'Lecture 1Document21 pages'Lecture 1Aditya YadavNo ratings yet
- Data Structure Typed Notes-Unit-1Document113 pagesData Structure Typed Notes-Unit-1Shyam VermaNo ratings yet
- Data Structures and Algorithms BBIT 2.2 L1Document5 pagesData Structures and Algorithms BBIT 2.2 L1wanjiku kibuiNo ratings yet
- Viva Questions For DAA UoPDocument10 pagesViva Questions For DAA UoPSuparnaNo ratings yet
- Upload Test123Document4 pagesUpload Test123Nabin ThapaNo ratings yet
- Analysis of AlgorithmsDocument4 pagesAnalysis of AlgorithmsNabin ThapaNo ratings yet
- Algorithm AnalysisDocument17 pagesAlgorithm Analysismuhammad amin ur rehman jani janiNo ratings yet
- Chapter 1 ComplexityDocument8 pagesChapter 1 ComplexityNE-5437 OfficialNo ratings yet
- Algorithms For Data Compression in Wireless Computing SystemsDocument7 pagesAlgorithms For Data Compression in Wireless Computing Systemsnikhilvbhatt9591No ratings yet
- Asymptotic Analysis of Algorithms in Data StructuresDocument11 pagesAsymptotic Analysis of Algorithms in Data StructuresHailu BadyeNo ratings yet
- AoA BasicsDocument3 pagesAoA Basics221nicole0006No ratings yet
- AlgorithmDocument885 pagesAlgorithmash23ish100% (1)
- DAA Notes CompleteDocument242 pagesDAA Notes CompleteVarnika TomarNo ratings yet
- Data Structure and AlgorithmDocument16 pagesData Structure and AlgorithmIchan KabirNo ratings yet
- Unit: I Fundamentals of Algorithms The Analysis of AlgorithmsDocument12 pagesUnit: I Fundamentals of Algorithms The Analysis of AlgorithmsPrakash SubramanianNo ratings yet
- Dogara Bashir COM/3182: To Display The First 12 Steps of The TriangleDocument9 pagesDogara Bashir COM/3182: To Display The First 12 Steps of The TriangleJibril ibrahim AbubakarNo ratings yet
- Chapter One1 Data Structure and AlgorithmsDocument14 pagesChapter One1 Data Structure and AlgorithmsHildana TamratNo ratings yet
- 2 MarksDocument16 pages2 MarkssiswariyaNo ratings yet
- DSA Unit 1Document28 pagesDSA Unit 1savitasainstarNo ratings yet
- Algorith and Data Structure Revision - 1Document9 pagesAlgorith and Data Structure Revision - 1Regina KadenyiNo ratings yet
- Data Structures 2Document31 pagesData Structures 2VIJAY V STUDENT -CSE DATASCIENCENo ratings yet
- Data Structure HandoutDocument80 pagesData Structure HandoutMohammed Abrar ShafiNo ratings yet
- Module 3 - Complexity of An AlgorithmDocument7 pagesModule 3 - Complexity of An AlgorithmarturogallardoedNo ratings yet
- Data Structure & Algorithm: Prepared by Ms. Chyril A. Concemino, Mba, MistDocument61 pagesData Structure & Algorithm: Prepared by Ms. Chyril A. Concemino, Mba, MistMaria Canete100% (1)
- Secure Tensor Decomposition Using Fully Homomorphic Encryption SchemeDocument8 pagesSecure Tensor Decomposition Using Fully Homomorphic Encryption SchemegopiNo ratings yet
- Analysis of Algorithm - Lecture 1Document9 pagesAnalysis of Algorithm - Lecture 1OyeladeAyoNo ratings yet
- Day 1 Data StructuresDocument126 pagesDay 1 Data StructuresRAAGA VEDANo ratings yet
- DAA All1Document56 pagesDAA All1jamdadeanujNo ratings yet
- Asymptotic NotationsDocument1 pageAsymptotic Notationsmedha.appallNo ratings yet
- Algorithm NewDocument35 pagesAlgorithm Newongakimary8No ratings yet
- Unit1 DaaDocument21 pagesUnit1 DaaArunachalam SelvaNo ratings yet
- DAA Assingment-1: Group:-1Document12 pagesDAA Assingment-1: Group:-1Sumedh VinayakNo ratings yet
- Block1 Unit1Document19 pagesBlock1 Unit1Not PersonalNo ratings yet
- Triple-DES VHDL ProjectDocument57 pagesTriple-DES VHDL ProjectRamanaButterflyNo ratings yet
- European SemiconductorDocument14 pagesEuropean SemiconductorSimbhu Ashok CNo ratings yet
- Cs2251 - Design and Analysis of Algorithms 2 Marks Questions With AnswersDocument27 pagesCs2251 - Design and Analysis of Algorithms 2 Marks Questions With AnswersMohan MohanbagavathiNo ratings yet
- Design and Analysis-Unit 1Document74 pagesDesign and Analysis-Unit 1jaipalsinghmalik47No ratings yet
- Algorithms and Data StructuresDocument11 pagesAlgorithms and Data StructuresMark Devlin DungoNo ratings yet
- DS HandoutDocument110 pagesDS HandoutRewina zerouNo ratings yet
- Data Structures & AlgorithmsDocument5 pagesData Structures & AlgorithmsDharshana MuthtettugodaNo ratings yet
- Data Structures Basic ProgramsDocument132 pagesData Structures Basic ProgramsNishant PatelNo ratings yet
- Lecture 1Document35 pagesLecture 1Mithal KothariNo ratings yet
- Algorithms and Data Structures: An Easy Guide to Programming SkillsFrom EverandAlgorithms and Data Structures: An Easy Guide to Programming SkillsNo ratings yet
- MS1104 1Document37 pagesMS1104 1Mugabe DeogratiousNo ratings yet
- MS1104 3Document21 pagesMS1104 3Mugabe DeogratiousNo ratings yet
- MS1104 5Document35 pagesMS1104 5Mugabe DeogratiousNo ratings yet
- MS1104 2Document52 pagesMS1104 2Mugabe DeogratiousNo ratings yet
- Chapter2 OopDocument159 pagesChapter2 OopMugabe DeogratiousNo ratings yet
- Database Systems: Architecture and Components: Masters of Science in Information TechnologyDocument33 pagesDatabase Systems: Architecture and Components: Masters of Science in Information TechnologyMugabe DeogratiousNo ratings yet
- The Entity-Relationship Model: Masters of Science in Information TechnologyDocument33 pagesThe Entity-Relationship Model: Masters of Science in Information TechnologyMugabe DeogratiousNo ratings yet
- MS115 - Communication Skills: Preparing Successful Management SpeechDocument14 pagesMS115 - Communication Skills: Preparing Successful Management SpeechMugabe DeogratiousNo ratings yet
- MS112 2Document22 pagesMS112 2Mugabe DeogratiousNo ratings yet
- Import LibrariesDocument5 pagesImport LibrariesMugabe DeogratiousNo ratings yet
- Infiniband (Ib) Is A Computer Networking Communications Standard Used in High-PerformanceDocument7 pagesInfiniband (Ib) Is A Computer Networking Communications Standard Used in High-PerformanceMugabe DeogratiousNo ratings yet
- UntitledDocument1 pageUntitledMugabe DeogratiousNo ratings yet
- This Document Has Been Classified As CONFIDENTIAL-EXTERNAL by Centenary BankDocument3 pagesThis Document Has Been Classified As CONFIDENTIAL-EXTERNAL by Centenary BankMugabe DeogratiousNo ratings yet
- (MS-ADTS) : Active Directory Technical SpecificationDocument620 pages(MS-ADTS) : Active Directory Technical SpecificationHoàng VũNo ratings yet
- Isilion X200 Instalation GuideDocument14 pagesIsilion X200 Instalation GuideCristian CostacheNo ratings yet
- Latest Features in Ab Initio - 2.14Document3 pagesLatest Features in Ab Initio - 2.14ahm117No ratings yet
- Computer Resource Centre - Piliyandala Education Zone Prince of Wales College, MoratuwaDocument13 pagesComputer Resource Centre - Piliyandala Education Zone Prince of Wales College, Moratuwajitha nipunikaNo ratings yet
- Basic Image Processing For Robotics ManualDocument103 pagesBasic Image Processing For Robotics Manualraduf517No ratings yet
- TISSearchand Replace InstructionsDocument4 pagesTISSearchand Replace Instructionsrudy12447No ratings yet
- Liferay Portal 6 1 Performance WhitepaperDocument15 pagesLiferay Portal 6 1 Performance WhitepaperoxynetNo ratings yet
- s7 Symbol Table Data TypeDocument4 pagess7 Symbol Table Data TypeSandip DhakalNo ratings yet
- Yasin 2020Document5 pagesYasin 2020Captain SkyNo ratings yet
- Mini Project 1Document15 pagesMini Project 1xyz644500No ratings yet
- 1.JAVA PracticalsDocument33 pages1.JAVA Practicalslesoves423No ratings yet
- Sample Network Vulnerability Assessment Report: Sales@purplesec - UsDocument5 pagesSample Network Vulnerability Assessment Report: Sales@purplesec - UsФарида ТаджибаеваNo ratings yet
- Laiba SrsDocument15 pagesLaiba SrsNeha AmjadNo ratings yet
- AJCL-JD - Principal Solution Architect - AmendedDocument2 pagesAJCL-JD - Principal Solution Architect - AmendedAmjad Ali GhumroNo ratings yet
- GNS3Document2 pagesGNS3xuankhanh333No ratings yet
- Online Rail Project ProposalDocument2 pagesOnline Rail Project Proposalb2uty77_593619754No ratings yet
- IT Data Structures Chapter 3Document53 pagesIT Data Structures Chapter 3romeofatima100% (1)
- LogDocument1,290 pagesLogibnunabawi22No ratings yet
- Packet-Optical Platform: Data SheetDocument3 pagesPacket-Optical Platform: Data SheettadilakshmikiranNo ratings yet
- CTPAT Minimum Security Criteria MSC For Sea CarriersDocument39 pagesCTPAT Minimum Security Criteria MSC For Sea CarriersCarlos MorenoNo ratings yet
- Introduction To Voice Gateways: Understanding Cisco Unified Communications Networks and The Role of GatewaysDocument193 pagesIntroduction To Voice Gateways: Understanding Cisco Unified Communications Networks and The Role of GatewaysGuillermo Ex TottiNo ratings yet
- Workshop User Guide of GrafcetDocument150 pagesWorkshop User Guide of GrafcetJames HabibNo ratings yet
- DATAcated Visualization Tools Guide 2021 - Update FEBDocument25 pagesDATAcated Visualization Tools Guide 2021 - Update FEBjsromeropNo ratings yet
- Employee Attendance Using Face Recorgnition and GpsproposalDocument14 pagesEmployee Attendance Using Face Recorgnition and GpsproposalOkullo AmbroseNo ratings yet
- Source Defense - The Essential Guide To PCI DSS 6.4.3 and 11.6.1Document14 pagesSource Defense - The Essential Guide To PCI DSS 6.4.3 and 11.6.1carlos.convitNo ratings yet
- TCS IT WIZ Sample Paper by DakshakDocument1 pageTCS IT WIZ Sample Paper by DakshakDakshak NagraleNo ratings yet
- ATT Chat Transcript July28th2022Document6 pagesATT Chat Transcript July28th2022asaNo ratings yet