Professional Documents
Culture Documents
CNS-4,5,6 Session
CNS-4,5,6 Session
Uploaded by
Sadhana VOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
CNS-4,5,6 Session
CNS-4,5,6 Session
Uploaded by
Sadhana VCopyright:
Available Formats
PSG Institute of Technology and Applied Research
Neelambur, Coimbatore – 641 062
Department of Computer Science and Engineering
CS8792 Cryptography and
Network Security
Session 4,5,6
Dr.I.Kala
Associate Professor/CSE
PSGiTECH
Outline of the presentation
• Classical Encryption Techniques
– Substitution Technique
– Transposition Technique
9/1/2020 CS8792: Cryptography and Network Security / Dr I Kala, Associate Professor/CSE 2
Classical Substitution Ciphers
• where letters of plaintext are replaced by other letters or by
numbers or symbols
• or if plaintext is viewed as a sequence of bits, then
substitution involves replacing plaintext bit patterns with
ciphertext bit patterns
9/1/2020 CS8792: Cryptography and Network Security / Dr I Kala, Associate 3/97
Caesar Cipher
• can define transformation as:
a b c d e f g h i j k l m n o p q r s t u v w x y z
D E F G H I J K L M N O P Q R S T U V W X Y Z A B C
C = E(p) = (p + 3) mod (26)
p = D(C) = (C – 3) mod (26)
• mathematically give each letter a number
a b c d e f g h i j k l m
0 1 2 3 4 5 6 7 8 9 10 11 12
n o p q r s t u v w x y Z
13 14 15 16 17 18 19 20 21 22 23 24 25
• then have Caesar cipher as:
C = E(p) = (p + k) mod (26) Text : ATTACKATONCE
p = D(C) = (C – k) mod (26) Shift: 4
Cipher: EXXEGOEXSRGI
9/1/2020 CS8792: Cryptography and Network Security / Dr I Kala, Associate 4/97
Monoalphabetic Cipher
• rather than just shifting the alphabet
• could shuffle (jumble) the letters arbitrarily
• each plaintext letter maps to a different random ciphertext
letter
• hence key is 26 letters long
Plain: abcdefghijklmnopqrstuvwxyz
Cipher: DKVQFIBJWPESCXHTMYAUOLRGZN
Plaintext: ifwewishtoreplaceletters
Ciphertext: WIRFRWAJUHYFTSDVFSFUUFYA
9/1/2020 CS8792: Cryptography and Network Security / Dr I Kala, Associate 5/97
Playfair Cipher with Key Matrix
• a 5X5 matrix of letters based on a keyword
• fill in letters of keyword (sans duplicates)
• fill rest of matrix with other letters
• eg. using the keyword MONARCHY , Plain Text : baloon
MONAR
CHYBD
EFGIK
LPQST
UVWXZ
1. if a pair is a repeated letter, insert a filler like 'X', eg. "balloon" encrypts as "ba lx lo
on"
2. if both letters fall in the same row, replace each with letter to right (wrapping back to
start from end), eg. “ar" encrypts as "RM"
3. if both letters fall in the same column, replace each with the letter below it (again
wrapping to top from bottom), eg. “mu" encrypts to "CM"
4. otherwise each letter is replaced by the one in its row in the column of the other letter
of the pair, eg. “hs" encrypts to "BP", and “ea" to "IM" or "JM" (as desired)
9/1/2020 CS8792: Cryptography and Network Security / Dr I Kala, Associate 6/97
Encrypting and Decrypting
• plaintext encrypted two letters at a time:
1. if a pair is a repeated letter, insert a filler like 'X', eg. "balloon"
encrypts as "ba lx lo on"
2. if both letters fall in the same row, replace each with letter to
right (wrapping back to start from end), eg. “ar" encrypts as
"RM"
3. if both letters fall in the same column, replace each with the letter
below it (again wrapping to top from bottom), eg. “mu" encrypts
to "CM"
4. otherwise each letter is replaced by the one in its row in the
column of the other letter of the pair, eg. “hs" encrypts to "BP",
and “ea" to "IM" or "JM" (as desired)
• plaintext "hide the gold in the tree stump“
• key playfair example
9/1/2020 CS8792: Cryptography and Network Security / Dr I Kala, Associate 7/97
Playfair Cipher Example
plaintext "hide the gold in the tree stump“
key playfair example
Plain Text
Cipher Text
9/1/2020 CS8792: Cryptography and Network Security / Dr I Kala, Associate Professor/CSE 8
Polyalphabetic Ciphers
• another approach to improving security is to use multiple
cipher alphabets
• called polyalphabetic substitution ciphers
• makes cryptanalysis harder with more alphabets to guess
and flatter frequency distribution
• use a key to select which alphabet is used for each letter of
the message
• use each alphabet in turn
• repeat from start after end of key is reached
9/1/2020 CS8792: Cryptography and Network Security / Dr I Kala, Associate 9/97
Vigenère Cipher
• simplest polyalphabetic substitution cipher is the Vigenère Cipher
• effectively multiple caesar ciphers
• key is multiple letters long K = k1 k2 ... kd
key: deceptivedeceptivedeceptive
plaintext: wearediscoveredsaveyourself
ciphertext:ZICVTWQNGRZGVTWAVZHCQ
YGLMGJ
9/1/2020 CS8792: Cryptography and Network Security / Dr I Kala, Associate 10/97
Vigenere Cipher
9/1/2020 CS8792: Cryptography and Network Security / Dr I Kala, Associate Professor/CSE 11
Example
• write the plaintext out
• write the keyword repeated above it
• use each key letter as a caesar cipher key
• encrypt the corresponding plaintext letter
• eg using keyword deceptive
key: deceptivedeceptivedeceptive
plaintext: wearediscoveredsaveyourself
ciphertext:ZICVTWQNGRZGVTWAVZHCQYGLMGJ
9/1/2020 CS8792: Cryptography and Network Security / Dr I Kala, Associate 12/97
Vernam Cipher Example
9/1/2020 CS8792: Cryptography and Network Security / Dr I Kala, Associate Professor/CSE 13
One-Time Pad
• if a truly random key as long as the message is used, the cipher will be
secure
• is unbreakable since ciphertext bears no statistical relationship to the
plaintext
• since for any plaintext & any ciphertext there exists a key mapping
one to other
• can only use the key once though have problem of safe distribution of
key
9/1/2020 CS8792: Cryptography and Network Security / Dr I Kala, Associate 14/97
POLL QUESTION
•One time pad (Find the Plain text):
9/1/2020 CS8792: Cryptography and Network Security / Dr I Kala, Associate 15/97
Transposition Ciphers
• now consider classical transposition or permutation ciphers
• these hide the message by rearranging the letter order
• without altering the actual letters used
• can recognise these since have the same frequency distribution as the
original text
9/1/2020 CS8792: Cryptography and Network Security / Dr I Kala, Associate 16/97
Rail Fence cipher
• write message letters out diagonally over a number of rows
• then read off cipher row by row
• eg. write message out as:
m e m a t r h t g p r y
e t e f e t e o a a t
• giving ciphertext
MEMATRHTGPRYETEFETEOAAT
9/1/2020 CS8792: Cryptography and Network Security / Dr I Kala, Associate 17/97
Row Transposition Ciphers
• a more complex scheme
• write letters of message out in rows over a specified number of
columns
• then reorder the columns according to some key before reading off the
rows
Single Columnar Transposition
Key: 3 4 2 1 5 6 7
Plaintext: a t t a c k p
o s t p o n e
d u n t i l t
w o a m x y z
Ciphertext: TTNAAPTMTSUOAODWCOIXKNLYPETZ
Double Columnar Transposition
Key: 3 4 2 1 5 6 7
Plaintext: t t n a a p t
m t s u o a o
d w c o i x k
n l y p e t z
Ciphertext:AUOPNSCYTMDNTTWLAOIEPAXTTOKZ
9/1/2020 CS8792: Cryptography and Network Security / Dr I Kala, Associate 18/97
GUESS?
• Match the following:
GROUPA GROUPB
i. BOOB VOJWFSTJUZ - (a) psgitech
ii. YDOXDEOH - (b) anna university
iii. CHAMPION - (c) cryptographist
iv. CYTGAHSRPORPIT - (d) valuable
9/1/2020 CS8792: Cryptography and Network Security / Dr I Kala, Associate 19/97
???? HOW
• The months of the calendar have been coded in the
following ways:
January = 1071, February = 682, March = 1353, April = 154, May = 1335, June =
1046, July = 1047
August = 168
Predict the Cipher text for September?
9/1/2020 CS8792: Cryptography and Network Security / Dr I Kala, Associate 20/97
ANSWERS
1. Match the following and Infer the Encryption technique :
GROUPA GROUPB
i. BOOB VOJWFSTJUZ - anna university (TECHNIQUE Mono Alphabetic
Substitution)
ii. YDOXDEOH - valuable (TECHNIQUE
Caesar Cipher C=P+3)
iii. CHAMPION - psgitech (TECHNIQUE Poly Alphabetic
Substitution)
iv. CYTGAHSRPORPIT - cryptographist (TECHNIQUE railfence)
2. Cipher text for September : 1999 - 19 is Numerical value of
S , 9 is letters in September, 9 is 9th month
9/1/2020 CS8792: Cryptography and Network Security / Dr I Kala, Associate 21/97
QUIZ 1 – ASSESSMENT
9/1/2020 CS8792: Cryptography and Network Security / Dr I Kala, Associate Professor/CSE 22
FEEDBACK
9/1/2020 CS8792: Cryptography and Network Security / Dr I Kala, Associate Professor/CSE 23
Security Mechanisms (X.800)
– encipherment, digital signatures, access controls,
data integrity, authentication exchange, traffic
padding, routing control, notarization
9/1/2020 CS8792: Cryptography and Network Security / Dr I Kala, Associate Professor/CSE 24
Privacy Mechanisms
1. Encryption (Encipherment)
It is the process of encoding information into a secret
code by using a special key.
To read an encrypted file, you must have the key of the
decoding that enables you to decrypt it.
By using an algorithm for encryption we can protect our
personal information that we don’t want other people to
see such as:
- Credit-card information
- Bank-account information
- Medical information
9/1/2020 CS8792: Cryptography and Network Security / Dr I Kala, Associate Professor/CSE 25
Privacy Mechanisms
2. Digital Signature
A digital signature is basically a way to ensure that an
electronic document is authentic. Authentic means that
you know who created the document and that it has not
been altered.
9/1/2020 CS8792: Cryptography and Network Security / Dr I Kala, Associate Professor/CSE 26
Privacy Mechanisms
This figure tells us that 3. Hash Functions and
a hash function
creates a fixed length Message Digest
string from a block
of data. It is also
called a message
digest function.
These (fast)
functions analyze a
message and
produce a fixed
length digest which
is practically unique.
It is used to create a
signature for a
message which can
be used to verify its
integrity
9/1/2020 CS8792: Cryptography and Network Security / Dr I Kala, Associate Professor/CSE 27
Privacy Mechanisms
4. Access Control
Access control is way of talking about controlling access
to a web resource. Access can be granted or denied based
on a wide variety of criteria, such as the network address
of the client, the time of day, or the browser which the
visitor is using.
9/1/2020 CS8792: Cryptography and Network Security / Dr I Kala, Associate Professor/CSE 28
Privacy Mechanisms
5. Traffic Padding
• It is the process of intercepting and examining messages in
order to deduce information from patterns in
communication.
• The attacker might not know what A and B were talking
but he could know that they were talking and how much
they talked.
• Padding messages is a way to make it harder to do traffic
analysis. A number of random bits are appended to the end
of the message.
9/1/2020 CS8792: Cryptography and Network Security / Dr I Kala, Associate Professor/CSE 29
Privacy Mechanisms
6. Routing control
Enables selection of a particular physically secure route for
certain data and allows routing changes, especially when a
breach of security is suspected.
7. Notarization
It’s the use of a third party to assure the other party.
9/1/2020 CS8792: Cryptography and Network Security / Dr I Kala, Associate Professor/CSE 30
Interaction
9/1/2020 CS8792: Cryptography and Network Security / Dr I Kala, Associate Professor/CSE 31
You might also like
- NSC Unit Important QuestionsDocument50 pagesNSC Unit Important Questionsyuvaraaj aletiNo ratings yet
- Cryptography Techniques: Project Report ONDocument14 pagesCryptography Techniques: Project Report ONpratiksonu0% (1)
- SSL/TLS Under Lock and Key: A Guide to Understanding SSL/TLS CryptographyFrom EverandSSL/TLS Under Lock and Key: A Guide to Understanding SSL/TLS CryptographyRating: 4 out of 5 stars4/5 (1)
- Laporan Insight InstagramDocument87 pagesLaporan Insight Instagramferri fahrizalNo ratings yet
- ITSI-4.7.1-Administration ManualDocument353 pagesITSI-4.7.1-Administration ManualLu PhamNo ratings yet
- Vignere Cipher EtcDocument72 pagesVignere Cipher EtcAhsan JameelNo ratings yet
- Mod 2 Notes CryptoDocument66 pagesMod 2 Notes CryptoMahalaxmi GinnamNo ratings yet
- Classical Encryption Techniques in Cryptography and Network SecurityDocument46 pagesClassical Encryption Techniques in Cryptography and Network SecurityEswin AngelNo ratings yet
- Cryptography and Network SecurityDocument41 pagesCryptography and Network SecurityPrachiNo ratings yet
- Classical Encryption TechniquesDocument36 pagesClassical Encryption TechniquesShashank VenkatNo ratings yet
- Cys505 Lecture02Document56 pagesCys505 Lecture02Abdirizak AbokarNo ratings yet
- Cryptography and Network Security: Fourth Edition by William StallingsDocument41 pagesCryptography and Network Security: Fourth Edition by William Stallingskstu1112No ratings yet
- CH 02Document41 pagesCH 02aya mohamedNo ratings yet
- ch02Document66 pagesch02gingeevimalNo ratings yet
- Cybesecurity CryptographyDocument42 pagesCybesecurity CryptographyGallant RockNo ratings yet
- CNS Unit-IiDocument58 pagesCNS Unit-IinandanNo ratings yet
- L 05 Cryptographyandapplications 160825094546Document73 pagesL 05 Cryptographyandapplications 160825094546kavisandeepaniNo ratings yet
- Classical Encryption TechniquesDocument87 pagesClassical Encryption Techniquesshahaban aliNo ratings yet
- Cryptography Fundamentals: V.Madhu Viswanatham PH.D School of Computer Science and Engineering VITDocument38 pagesCryptography Fundamentals: V.Madhu Viswanatham PH.D School of Computer Science and Engineering VITabhinavNo ratings yet
- Classical Encryption TechniquesDocument39 pagesClassical Encryption TechniquesAbhishek UpadhyayNo ratings yet
- CH 02 Classical Encryption TechniqueDocument40 pagesCH 02 Classical Encryption TechniqueGurhale RushikeshNo ratings yet
- Symmetric Ciphers Classical Encryption TechniquesDocument5 pagesSymmetric Ciphers Classical Encryption TechniquesRocky IslamNo ratings yet
- Cryptography: Information and Network SecurityDocument44 pagesCryptography: Information and Network SecurityLeng Hour lengNo ratings yet
- 02.L2-L3-ch02 Classical Encryption TechniquesDocument49 pages02.L2-L3-ch02 Classical Encryption TechniquesvanshikaNo ratings yet
- By Marwan Al-Namari & Hafezah Ben Othman Author: William StallingsDocument40 pagesBy Marwan Al-Namari & Hafezah Ben Othman Author: William Stallingsreda elbarougyNo ratings yet
- Ch3 Cryptography and Public Key InfrastructureDocument15 pagesCh3 Cryptography and Public Key InfrastructureGebru GurmessaNo ratings yet
- 1st LectureDocument10 pages1st LectureAHMED DARAJNo ratings yet
- William Stallings Cryptography ch02Document38 pagesWilliam Stallings Cryptography ch02Suganya SelvarajNo ratings yet
- Lect 2Document27 pagesLect 2abhs82No ratings yet
- 1.8.substitution TechniquesDocument16 pages1.8.substitution TechniquesDHARINI R SIT 2020No ratings yet
- Computer Security (Chapter-3)Document88 pagesComputer Security (Chapter-3)Naoly GetNo ratings yet
- Classical Ciphers: by Mr. Fasee Ullah Cusit PeshawarDocument34 pagesClassical Ciphers: by Mr. Fasee Ullah Cusit PeshawarNewklear HurtedNo ratings yet
- Lecture 2 B Private Key CryptographyDocument21 pagesLecture 2 B Private Key CryptographyKedir MohammedNo ratings yet
- Enhancing The Data Security of Simple Columnar Transposition Cipher by Caesar Cipher and Rail Fence Cipher Technique.Document8 pagesEnhancing The Data Security of Simple Columnar Transposition Cipher by Caesar Cipher and Rail Fence Cipher Technique.Muh ElbinNo ratings yet
- Substitution TechniquesDocument25 pagesSubstitution Techniquessamir9952282706No ratings yet
- Classsical Encryption Techniques MukeshDocument13 pagesClasssical Encryption Techniques MukeshMukeshNo ratings yet
- ch8 Network PDFDocument22 pagesch8 Network PDFomerNo ratings yet
- Systems and Networks Security: 3-Basics of CryptographyDocument77 pagesSystems and Networks Security: 3-Basics of CryptographyEng-Nesreen EdainatNo ratings yet
- Lecture 2 Classical Encryption TechniquesDocument22 pagesLecture 2 Classical Encryption TechniquesNurdin YussufNo ratings yet
- Crypto Techniques VKDocument25 pagesCrypto Techniques VKVikas KNo ratings yet
- Hardware Design and Software Simulation For Four Classical CryptosystemsDocument6 pagesHardware Design and Software Simulation For Four Classical CryptosystemsAlice ShamirNo ratings yet
- Network Security & Cryptography Lecture 5 & 6Document66 pagesNetwork Security & Cryptography Lecture 5 & 6Udhay PrakashNo ratings yet
- Block DipherDocument37 pagesBlock DipherNitin PandeyNo ratings yet
- Ch08 CryptoConceptsDocument66 pagesCh08 CryptoConceptsRizwanKhatriNo ratings yet
- Classical Encryption TechniqueDocument18 pagesClassical Encryption TechniquetalebmuhsinNo ratings yet
- CNS LabmanualDocument21 pagesCNS LabmanualakiraNo ratings yet
- Computer Science & Engineering: Apex Institute of Technology Bachelor of Engineering (Information Security)Document10 pagesComputer Science & Engineering: Apex Institute of Technology Bachelor of Engineering (Information Security)RavleenNo ratings yet
- Cs6711 Security Laboratory Manual 2 PDFDocument66 pagesCs6711 Security Laboratory Manual 2 PDFrachanapatil123100% (1)
- Fahad AssignmentDocument4 pagesFahad Assignmenthussainremu038No ratings yet
- Lecture 2Document33 pagesLecture 2Jasleen VirdiNo ratings yet
- Module 1 Symmetric CiphersDocument51 pagesModule 1 Symmetric Ciphersshazia sulthanaNo ratings yet
- Network Security: Dr. Md. Imdadul IslamDocument50 pagesNetwork Security: Dr. Md. Imdadul IslamAnnondoOsruNo ratings yet
- Cryptography and Network SecurityDocument55 pagesCryptography and Network SecurityFatima IrfanNo ratings yet
- CH 02Document105 pagesCH 02Ramveer SinghNo ratings yet
- Cryptography and Network SecurityDocument18 pagesCryptography and Network SecurityMSM GamingNo ratings yet
- Thirumalai Engineering College Kilambi, Kanchipuram-631551: Department of Computer ScienceDocument89 pagesThirumalai Engineering College Kilambi, Kanchipuram-631551: Department of Computer ScienceJaganNo ratings yet
- Cryptology BasicsDocument11 pagesCryptology Basicsbuffet_jobsNo ratings yet
- Classical Encryption Techniques: Information System SecurityDocument54 pagesClassical Encryption Techniques: Information System SecurityYazanAlomariNo ratings yet
- Classical Encryption TechniquesDocument44 pagesClassical Encryption TechniquesSharukhNo ratings yet
- CryptoDocument14 pagesCryptoasdxws feNo ratings yet
- How To Configure TCS Webmail in Android MobileDocument4 pagesHow To Configure TCS Webmail in Android MobileBV1081No ratings yet
- 2a GNU Octave Online Compiler Refresher TutorialDocument26 pages2a GNU Octave Online Compiler Refresher TutorialernestNo ratings yet
- User Manual: Capture QualityDocument32 pagesUser Manual: Capture QualityMuhammad AwanNo ratings yet
- Power PlanningDocument12 pagesPower PlanningMohammad JoharNo ratings yet
- EM0505 3.0v1 Introduction To Sophos EmailDocument19 pagesEM0505 3.0v1 Introduction To Sophos EmailemendozaNo ratings yet
- 4ºESO - Unit8 - ChallengeDocument4 pages4ºESO - Unit8 - ChallengeLucía PJNo ratings yet
- Netbackup 8.0 Blueprint OpsCenterDocument59 pagesNetbackup 8.0 Blueprint OpsCenteralireza1023No ratings yet
- Network SinhalenDocument22 pagesNetwork SinhalenLasith MalingaNo ratings yet
- Brosur GE OEC 3DDocument9 pagesBrosur GE OEC 3DRlisastNo ratings yet
- Digital Logic Important Objective Questions Unit-2: 11101111111 1001000 011010 Ans-001100011 Ans-101001 Ans-1000011Document3 pagesDigital Logic Important Objective Questions Unit-2: 11101111111 1001000 011010 Ans-001100011 Ans-101001 Ans-1000011Soumen MitraNo ratings yet
- Tattle Tales - The Puzzle Place Wiki - FandomDocument4 pagesTattle Tales - The Puzzle Place Wiki - FandomchefchadsmithNo ratings yet
- Hart Application GuideDocument189 pagesHart Application GuideRoy RamosNo ratings yet
- (GB) 23292 - 07-23-21 - Southington Youth Summer Theater (James and The Giant Peach JR)Document8 pages(GB) 23292 - 07-23-21 - Southington Youth Summer Theater (James and The Giant Peach JR)TimothyNo ratings yet
- Shania Osburn Successful - ShaniaDocument2 pagesShania Osburn Successful - ShaniaPablo PerezNo ratings yet
- Java Enums PDFDocument3 pagesJava Enums PDFKrishna KumarNo ratings yet
- Form Isian Kebutuhan Perguran Tinggi - Final1Document2 pagesForm Isian Kebutuhan Perguran Tinggi - Final1jenkelanaNo ratings yet
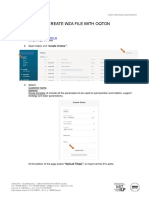
- Create WZA File With OqtonDocument6 pagesCreate WZA File With Oqtoncatalin lazarNo ratings yet
- Alarm Details Domain WiseDocument198 pagesAlarm Details Domain WiseDaveNo ratings yet
- Redhat: Red Hat Certified System Administrator (Rhcsa)Document4 pagesRedhat: Red Hat Certified System Administrator (Rhcsa)Nabila Ayaba0% (1)
- Biu Computer Programming - Lecture 1Document18 pagesBiu Computer Programming - Lecture 1Mulungu-Alinafe MpofuNo ratings yet
- Automated Stock Price Prediction Using Machine Learning: Mariam Moukalled Wassim El-Hajj Mohamad JaberDocument9 pagesAutomated Stock Price Prediction Using Machine Learning: Mariam Moukalled Wassim El-Hajj Mohamad JaberAkash GuptaNo ratings yet
- Building HP FlexFabric Data Centers, Rev 14.41 Student Guide Part1Document413 pagesBuilding HP FlexFabric Data Centers, Rev 14.41 Student Guide Part1RubenOrtegaNo ratings yet
- DifferentiationDocument30 pagesDifferentiationmikeful mirallesNo ratings yet
- Pcsfe BlueprintDocument4 pagesPcsfe Blueprintw.meloNo ratings yet
- Third Quarter TosDocument1 pageThird Quarter TosNorhana SamadNo ratings yet
- TLE10 ICT CSS Q1 M4 v3Document90 pagesTLE10 ICT CSS Q1 M4 v3lhuk banaag0% (1)
- Oop Lab ReportDocument6 pagesOop Lab ReportMd. Jahid Hasan PintuNo ratings yet
- SP Session 10 RevisedDocument83 pagesSP Session 10 RevisedMesbahuddinNo ratings yet