Professional Documents
Culture Documents
Best Practices For: Managing Software Intellectual Property
Best Practices For: Managing Software Intellectual Property
Uploaded by
M Yasir HassanOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Best Practices For: Managing Software Intellectual Property
Best Practices For: Managing Software Intellectual Property
Uploaded by
M Yasir HassanCopyright:
Available Formats
Best Practices for
ManagingSoftwareIntellectualProperty
ExecutiveOverview
Over the past ten years, new technologies like the
Internet and open source software have enabled
developers to fundamentally change the way they
create software. Increasingly, distributed teams are
collaborating to assemble software from reusable
components and their own proprietary code rather
than building applications entirely from scratch.
Spurred by ubiquitous connectivity, developers
today can easily tap into rich software resources
inside their own organizations
and from around the world.
They obtain software modules
and libraries and even code
fragments from enormous stores
of high-quality, re-useable software
components. Open source projects
are a major new source of re-usable
code, but so too are the growing
in-house software repositories, and
the increasing amounts of modular code from third-
parties such as outsourcers.
With such broad availability, developers now focus
on selecting the best available components for their
projects, and rapidly incorporating them into their
own intellectual property (IP) to deliver applications
that provide optimal functionality, performance, and
reliability.
The component-based development model is
fundamentally changing the software industry. It
enables organizations that develop software, either
for commercial sale or for in-house use, to accelerate
project timelines, improve software quality, and
reduce development costs. But if not managed
properly, the complexity inherent in this new world
of mixed-IP can pose business and technical risks to
an organization.
This paper draws on the experiences of the Black
Duck Software team, our customers, and other
industry experts to propose new approaches to
managing intellectual property in this new world. It
describes a set of Best Practices that companies can
use to avoid the risks and gain the benefts of this
promising new approach to software development.
Component-basedDevelopment
A software applications design,
implementation, and maintenance
require the investment of
precious development personnel,
resources, and time. Development
organizations have long understood
the virtues of building new
applications by re-using components
already built and tested. Indeed,
the evolution and rapid adoption of component-
based architectures has been driven in part by their
effectiveness in promoting economically-signifcant
re-use. This effectiveness has stimulated the creation
of commercial component libraries, which give
development teams the option of purchasing pre-
built components rather than acquiring the expertise
and/or expending the time required to independently
create them. In short, the approach can result in
faster, less-expensive, and more effective software
development.
It is therefore appropriate to consider components
as intellectual property assets, optimize their usage,
and protect their integrity. This applies equally to all
components, whether they are internally developed
or developed externally by a third party.
Component-based
development is
fundamentally
changing the
software industry
1
A development team intent on exploiting an
externally developed commercial component does
not typically purchase ownership of that component.
Instead, they acquire a license to
use that component in a specifed
manner perhaps for only a certain
number of developers working
on a particular project, or with
a specifed royalty paid for each
instance of a shipped product that
includes the component.
Thus business judgment is required to ensure that
the cost of licensing a commercial component is
more than offset by the benefts the classic make
vs. buy tradeoff. Included in the cost analysis must
be the effort required to ensure compliance with
the license, e.g. limiting the components usage to
a specifc project, or tracking shipments in order to
accurately calculate royalty payments.
TheOpenSourceImpact
Over the past fve years, a powerful new approach
to development open source software has
risen to prominence, dramatically increasing the
opportunity to re-use existing software. With todays
powerful Internet search capabilities, developers
can readily locate potentially useful components
from among a wide array of re-usable software
components. Re-use can take many forms, including
bundling independent components, integrating
with or using libraries, and incorporating source
code or source code fragments. In some cases these
components can be modifed as required to improve
functionality, quality, performance, or footprint.
In many organizations, a developers skill with
Google
and SourceForge.net is as important as
his or her knowledge of software architecture and
implementation.
As with commercial components,
the ownership of externally
developed open source components
and fragments remains with their
authors. While most of these authors
allow the commercial use of their
software without initial payments
or royalties, many have chosen to
impose other constraints, such as
Attribution
Usage reporting
Publication of modifcations and improvements
License replication
Resulting software must be open source
Such constraints are imposed by means of licenses,
examples of which include
the Apache Software License (ASL)
the Common Public License (CPL)
the GNU General Public License (GPL)
the Mozilla Public License (MPL)
the New BSD License
The Linux operating system, for example, is
licensed under the GPL. A more complete listing
of open source licenses is provided at http://
www.opensource.org/licenses.
OpenSourceLicenseCompliance
Development teams that incorporate open source
components or fragments of open source components
in their projects must comply with the terms of the
Faster, less
expensive, and
more effective
software
development
2
licenses associated with those components. This
can be challenging for several reasons including the
following.
There is wide variation in the obligations
imposed by open source licenses, ranging from
the BSD license (which has few obligations) to
the GPL license (which has many).
Some open source licenses are legally complex,
introducing constraints whose business
implications may not be obvious to a developer
choosing to re-use a component.
The licenses of some commercial and open source
components are mutually incompatible.
The origin of a particular source code fragment
may be diffcult to determine, effectively
obscuring its license obligations.
Discovering the need to comply with a license
late in a projects lifecycle
can produce disagreeable
tradeoffs, e.g. publishing all of
the projects source code vs.
increasing time-to-market by
months while a component is
replaced.
In addition to the legal obligations
imposed by licenses, developers who incorporate
open source components into an organizations
projects may either be obligated by the terms of the
license or feel a moral obligation to give something
back to the community. The resulting actions may
result in the inadvertent dilution or loss of the
organizations intellectual property (IP).
ManagementAlternatives
Organizations can react to the challenges of open
source software licenses in one of three ways.
Some organizations turn a blind eye, ignoring the
issue until a catalyzing event or crisis occurs. But
the resulting misfortunes major code rewrites,
embarrassing negative publicity, delayed sales,
failed acquisitions make this an increasingly
untenable approach. This is especially true in the
new environment of increased business transparency,
executive responsibility, and potential shareholder
lawsuits.
Other organizations take the Draconian approach of
banning all open source software re-use. This strategy
is fawed because it:
Is diffcult to enforce
Decreases productivity and agility compared to
organizations that successfully re-use externally
developed components
De-motivates development teams by requiring
them to apply scarce resources to wheel re-
invention rather than to moving
forward
Further, both of the above
approaches are ineffective because
they fail to recognize the reality that
open source and component reuse
are here to stay.
The third and recommended alternative is to
encourage the re-use of both internally developed and
externally developed (commercial and open source)
components, while establishing controls at critical
points in the project lifecycle, for example:
when components are frst added to a project
when internally developed components are
created or modifed
at every build
at each phase transition in the development
process
Open source
and component
reuse are here
to stay
3
when considering the contribution of a
component to an open source project or the
transfer of its ownership to another party
before acquiring a signifcant ownership interest
in a software component
It is important to note that identifying problematic
licensing issues early in the
development cycle is tantamount to
detecting serious software defects:
the earlier a problem is detected,
the less expensive it is to fx. While
IP controls late in the development
cycle during QA or release
assembly, for example are better
than none, the earlier they happen
in the lifecycle, the better.
In the remainder of this report, we will outline several
Best Practices that facilitate the management of
software IP in the modern development organization.
While all of these Best Practices encourage a focus
on license compliance throughout the lifecycle,
each organization should adopt the subset of Best
Practices that meet their business needs. For example,
an organization may wish to give its developers
the fexibility to build prototypes using any open
source code with no pre-approval, but specify a
development phase transition beyond which all
externally developed components must be approved.
This provides the benefts of speed and effciency to
the developer, with the protection offered by a formal
review.
It should be noted that, while all of these processes
can be built and executed manually, their adoption
and usage will be more effective and effcient when
supported with an automated software compliance
management system.
PreparingforIPManagement
When beginning to adopt Best Practices, several
getting started tasks should be considered by the
individual or teams responsible for development and
licensing. An organization intent on managing its
software IP should identify the responsible business,
legal, and technical individuals who
will be involved in the process. The
organization also should designate
them as authorizers for each active
project, and commission them as
a group to oversee and manage
the planning, implementation,
and ongoing management of the
process.
A good frst step for the team is to defne the
boundary between internally developed and
externally developed components (e.g. for business
units, contractors, outsourcing organizations).
For example, a small organization that prefers
taking a conservative approach may deem all of the
code developed within its walls to be internal.
Conversely, that company would view as external
all software brought in from any outside source (e.g.
licensed proprietary, open source, contractors work
product, etc.).
A more trusting organization might extend its view
of internal software to include licensed proprietary
software and software developed by its contractor and
outsource partners. On the other hand, a department
of a large corporation may want to consider its
department internal and consider everyone else,
including other departments in the same company
to be external. Business judgment must be used to
determine where the boundary should lie.
The earlier
a problem is
detected, the
less expensive
it is to fx...
4
Another key task in the preparation process is for
the team to identify the development process phase
transitions at which component re-use reviews will
be conducted. The team also should defne criteria
for designating an internally developed component
as sensitive (due to intellectual property value for
example embodiment of trade secrets or patents,
or risk), and develop and maintain a list of these
sensitive items.
The organization also should consider establishing
and maintaining lists of:
Licenses that are prohibited by the organization
Externally developed components that, based on
previous reviews, are approved for use in projects,
and the situations in which use is approved
Internally developed components that, based on
previous reviews, are approved for contribution
to open source projects or disposition to third
parties
Once these lists have been created, the organization
can use them to conduct an initial assessment of its
existing code base(s). In this important preparatory
step, the organization identifes and establishes the
baseline pedigree, licenses, and components in use.
As with any process improvement, an acceptable
alternative approach involves introducing these steps
incrementally over time.
5
SevenBestPracticesforManagingSoftwareIntellectualProperty
Whenever a development team considers adding new features or refning existing functionality in a project, it
should explicitly seek internally developed and externally developed components that could accelerate delivery.
The team should establish criteria for selecting and procuring these components. As would be expected, any
component under consideration that fails to meet functionality, performance, reliability, maturity, or risk
requirements should be eliminated.
The team should also eliminate any externally developed component whose license is on the prohibited license
list, whose license obligations are fnancially or legally incompatible with the projects business objectives, or
that uses other external components or fragments whose licenses are similarly unacceptable. For example, an
organization developing a product that will be delivered under a proprietary license needs to be certain that
any open source or proprietary licensed code that is incorporated can be safely included without causing an
irreconcilable confict between licenses. Any components that pass this initial test should be subjected to a
make-buy analysis to determine whether or not its acquisition makes sense from a business perspective.
To protect the organizations critical intellectual property, the creation and modifcation of all internally
developed components should be tracked by recording a timestamp, the names of each author, and the
applicable objectives and constraints. If a newly-created or modifed component is suspected to be sensitive
(e.g. a patent is sought, the code embodies algorithms that give the company signifcant competitive advantage,
etc.), the projects legal, business, and technical reviewers should be convened. If these reviewers deem the
component to be sensitive, they should add it to the organizations list of sensitive internal components.
By assessing sensitivity and license obligations at the point where a component is frst being considered for
re-use, decisions can be based on verifable facts, eliminating last-minute surprises, guesswork, compromises,
and risk-taking. This dramatically reduces the risk of schedule slippage, cost overruns, and damage to the
organizations reputation. It also helps prevent the inappropriate re-use of critical intellectual property.
For each component that a projects development team proposes to use within a project, the team should
understand:
8est Pract|ce #2:
4RACKANDCONTROLCHANGESTOINTERNALCOMPONENTS
8est Pract|ce #3:
#ONTROLREUSEOFSENSITIVEOREXTERNALCOMPONENTS
6
8est Pract|ce #1:
2EUSEEXISTINGCOMPONENTSWHEREVERAPPROPRIATE
The intended use and rationale for inclusion
The components sensitivity
How the code will be incorporated
How the team deals with the component will depend, in part, on whether plans call for that component to be
used temporarily or permanently. For example, the intent may be to use that component for a limited amount
of time only to speed up prototyping or to advance the early phases of the development cycle, but not be
intended to be made a permanent part of the code base.
Another determination the team should make is whether a component will be used only as is, or if
modifcations will be allowed, and if so, under which approvals.
Development teams should describe the method of joining that will be used to incorporate the component into
the project. This is an effective step because different types of joining can create different licensing obligations
(e.g., an unmodifed copy will be used, a source code fragment will be copied and merged with other source
code, an executable will be packaged with the distribution, a statically linked library will be used, a dynamically
linked library will be used, etc.).
To achieve greater control over component re-use, teams should also take the following actions.
Determine whether the component has been previously approved for the proposed form of use (by
consulting the approved externally developed components list).
Declare the components version and understand its license obligations as well as those of any externally
developed components or fragments it contains or depends on. This requires a declaration from the
supplier of any externally developed component whose source code is unavailable for direct inspection.
Understand all potential incompatibilities between the components license obligations and the license
obligations of other externally developed components included in this project.
Present the above information to the projects legal, technical, and business authorizers and request
approval to use the component as described.
Approvals should be refected in the appropriate organization-wide lists.
If the component is internal and sensitive, the list that covers these items should be updated to note that
components inclusion in this project.
If the component is externally developed, its metadata and approval details (origin, version, license, license
obligations, permitted forms of use, permitted projects, approvers, approval date) should be recorded in the
list of approved external components.
7
Inspecting the code base on a regular basis decreases the likelihood that unexpected components will be
introduced without being noticed. Therefore, at the creation of each project build or at release assembly, the
development team should verify that:
No unapproved sensitive internally or externally developed components or fragments have been added to
the project.
No unapproved changes have been made to sensitive internally developed components.
No changes have been made to externally developed components whose form of use precludes changes, or
requires that all changes be approved.
Any inappropriate additions or changes discovered during verifcation should be immediately addressed,
either by obtaining approval from the projects legal, technical, and business reviewers, or by backing out the
offending modifcation. The root cause of any component misuse should be identifed and corrected to ensure
no subsequent regression.
By promptly and diligently assessing every build and release, the development team will be able to detect
errors when they are least expensive to correct. At the completion of each build or release, the key metadata
for all externally developed components should be recorded in the associated bill-of-materials. This enables
demonstrable compliance with license obligations, and eliminates any uncertainty caused by changes between
project releases by providing a clear audit trail.
As a project completes a major development process phase, its legal, technical, and business reviewers should do
the following.
Verify that no unapproved sensitive internal or external components or fragments are used in the project.
Verify that no unapproved changes were made to sensitive internal components, and that no unapproved or
precluded changes were made to external components.
Review the license obligations of all external components used in the project, and ensure compliance with
these obligations.
These phase reviews backstop the development team, and keep the legal, technical, and business reviewers
engaged in the management of software re-use. They also verify that changes in the projects objectives have not
created legal, technical, or fnancial inconsistencies with the licenses of components used in the project.
8est Pract|ce #4:
6ERIFYEVERYBUILDANDRELEASE
8est Pract|ce #5:
2EVIEWCOMPLIANCEATPROJECTPHASETRANSITIONS
8
The rationale for contributing components to an open source project is beyond the scope of this report, as are
the considerations involved in transferring ownership to a third party or creating a new open source project.
However, if a contribution or transfer of a candidate component or fragment is deemed appropriate, the
projects legal and business reviewers should
determine whether the candidate components sensitivity (if internally developed) is an impediment to
contribution or transfer.
verify the right to contribute or transfer every externally developed component or fragment contained
within the candidate.
This helps to ensure that the organization does not inadvertently contribute code that shouldnt be contributed
because of its sensitivity or because the organization is not entitled to contribute it.
If an organization is considering an acquisition that would include a signifcant interest in one or more software
components, the designated set of legal, technical, and business reviewers should be charged with the following.
Identifying all included components not owned by the supplier or target.
Assessing their license obligations with respect to the acquirors compliance, business objectives, and legal
policies.
Assessing the impact of any required rework or change on cost, revenue, and quality.
Note that this best practice applies to a variety of situations in which fnancial investments are involved. Such
situations include: company mergers and acquisitions, product acquisitions, joint venture formations, venture
capital investments, etc.
9
8est Pract|ce #7:
!SSESSSOFTWARECOMPONENTSBEFOREACQUISITION
8est Pract|ce #6:
#ONTROLCOMPONENTCONTRIBUTIONANDDISPOSITION
Conclusion
In summary, this report describes a set of seven
best practices whose objective is to encourage
development based on component re-use and
software assembly. By integrating these practices in
its development processes, organizations will have
far greater assurances of compliance with all relevant
license obligations and far more effective protection
of software intellectual property.
Adopting these practices will enable companies to be
more aggressive in their use of the software assembly
approach. That, in turn, will enable those companies
to more quickly gain the benefts and competitive
advantage this new development approach promises
including accelerated project timelines, improved
software quality, and reduced development costs.
We are interested in your feedback and comments on
this paper. Please send them to:
info@blackducksoftware.com.
10
AboutBlackDuckSoftware
Black Duck Software is the leading provider of
software compliance management solutions that help
companies govern how software assets are created,
managed and licensed. Black Ducks offerings help
businesses take maximum advantage of open source
software while at the same time ensure that they
satisfy the obligations associated with the code they
use. Black Ducks customer base includes enterprises,
product developers, outsourcers, law frms and other
organizations worldwide that are concerned with
protection of software intellectual property.
Contact
To learn more about how Black Ducks Software IP
Assessment Service can help your company validate
the contents of its software code quickly, easily, and
cost-effectively, please contact
info@blackducksoftware.com or call
+1.781.810.2020.
Additional information is available at Black Ducks
web site: www.blackducksoftware.com
2007 Black Duck Software, Inc. Black Duck
Software, the Black Duck logo, protexIP, exportIP,
transactIP and Know Your Code are trademarks of
Black Duck Software, Inc. All other trademarks are
property of their respective holders. Specifications
subject to change without notice.
You might also like
- Systems Analysis and Design 11th Edition Tilley Solutions ManualDocument7 pagesSystems Analysis and Design 11th Edition Tilley Solutions Manualbdelliumdimehqa100% (24)
- Night Horrors - Conquering HeroesDocument124 pagesNight Horrors - Conquering HeroesNeal Patrick Pico100% (15)
- Vmware Workspace One Overview and Documentation Reference GuideDocument29 pagesVmware Workspace One Overview and Documentation Reference GuideIon Vladescu100% (1)
- Week1-OSSoftware and EngineeringDocument18 pagesWeek1-OSSoftware and EngineeringarturogallardoedNo ratings yet
- Advantages of Open Source SoftwareDocument8 pagesAdvantages of Open Source SoftwareVino LakshmiNo ratings yet
- Modern Systems Analysis and Design 7th Edition Hoffer Solutions ManualDocument36 pagesModern Systems Analysis and Design 7th Edition Hoffer Solutions Manualinsuliteskinch4wjca100% (16)
- Open Source Software AssessmentDocument24 pagesOpen Source Software AssessmentPrashant RawatNo ratings yet
- Top Ten Ways To Reduce Software Costs: Practical Tips For Software Asset ManagementDocument4 pagesTop Ten Ways To Reduce Software Costs: Practical Tips For Software Asset ManagementvandyranaNo ratings yet
- OSS ReferenceDocument336 pagesOSS ReferenceMonish R Nath50% (2)
- sOFTWARE REUSEDocument48 pagessOFTWARE REUSENaresh KumarNo ratings yet
- White Paper: by Miguel Valdés Faura - Ceo and Co-Founder, BonitasoftDocument5 pagesWhite Paper: by Miguel Valdés Faura - Ceo and Co-Founder, BonitasoftNikola DubljevicNo ratings yet
- 3 Development of Enterprise SystemsDocument38 pages3 Development of Enterprise SystemsMagarsa BedasaNo ratings yet
- Successful Software UpgradesDocument4 pagesSuccessful Software UpgradesmailtopvvkNo ratings yet
- What Is SDLC - Phases of Software Development & ModelsDocument8 pagesWhat Is SDLC - Phases of Software Development & ModelsSarange AnneNo ratings yet
- Software Engineering Unit1 PrintDocument11 pagesSoftware Engineering Unit1 PrintBiju AngaleesNo ratings yet
- 7 SDLCDocument5 pages7 SDLCAlfredo Beltran IIINo ratings yet
- Homework Chapter 2Document4 pagesHomework Chapter 2Angela PintoNo ratings yet
- OOSEDocument29 pagesOOSEaknumsn7724No ratings yet
- The Origins of SoftwareDocument21 pagesThe Origins of SoftwareAditya BhusalNo ratings yet
- Unit I 9: Know More at Powered by WR1334Document11 pagesUnit I 9: Know More at Powered by WR1334Ankit KomarNo ratings yet
- Idera Whitepaper How To Choose Between Paid and Open Source Software SolutionsDocument10 pagesIdera Whitepaper How To Choose Between Paid and Open Source Software SolutionsMamadou ThioyeNo ratings yet
- Start Here: Devops: Digital Learning PortalDocument6 pagesStart Here: Devops: Digital Learning PortalAnonymous NeRBrZyAUbNo ratings yet
- 9 Open-Source Sofwtare and Software LicensesDocument5 pages9 Open-Source Sofwtare and Software Licensesيوسف محمد مغيمشNo ratings yet
- The Role of Open-Source Software: Enterprise Architecture - Chapter 6Document111 pagesThe Role of Open-Source Software: Enterprise Architecture - Chapter 6ondoy tvNo ratings yet
- Build Versus Buy: Executive SummaryDocument5 pagesBuild Versus Buy: Executive SummaryratheeshksNo ratings yet
- Unit - 5 - by Sachi MadamDocument42 pagesUnit - 5 - by Sachi MadamPraveen SinghNo ratings yet
- Systems Analysis and Design 11Th Edition Tilley Solutions Manual Full Chapter PDFDocument28 pagesSystems Analysis and Design 11Th Edition Tilley Solutions Manual Full Chapter PDFdariusluyen586100% (9)
- Implementation Issues TaskDocument18 pagesImplementation Issues Taskahmed emadNo ratings yet
- Unit1 1Document22 pagesUnit1 12130154006No ratings yet
- AIAA Open Source FEA in IndustryDocument12 pagesAIAA Open Source FEA in IndustrySergio PluchinskyNo ratings yet
- Master Thesis Decision MakingDocument14 pagesMaster Thesis Decision Makingjorisdeboer1997No ratings yet
- A Framework For Software Product Line Practice, Version 5.0: What's New in Version 5.0Document258 pagesA Framework For Software Product Line Practice, Version 5.0: What's New in Version 5.0Satana UccisoreNo ratings yet
- Soa Whitepaper Updated PDFDocument6 pagesSoa Whitepaper Updated PDFkrishna vengalasettyNo ratings yet
- Prototype SDocument2 pagesPrototype SDenisho DeeNo ratings yet
- What Is Application DevelopmentDocument9 pagesWhat Is Application DevelopmentJhemwel TisadoNo ratings yet
- Software Development Life Cycle (SDLC)Document25 pagesSoftware Development Life Cycle (SDLC)Al Muktadir MunamNo ratings yet
- Software Research & DevelopmentDocument17 pagesSoftware Research & DevelopmentSadaf Maqsood QaziNo ratings yet
- Software Development Life Cycle - A Complete GuideDocument9 pagesSoftware Development Life Cycle - A Complete GuideAleksandra VelickovicNo ratings yet
- Software Open Source Licence Chooser: Content SpaceDocument5 pagesSoftware Open Source Licence Chooser: Content SpacemyscrigaNo ratings yet
- Open Incremental Model-A Open Source Software Development Life Cycle Model (OSDLC)Document7 pagesOpen Incremental Model-A Open Source Software Development Life Cycle Model (OSDLC)ayushymNo ratings yet
- 2.0 The Origins of SoftwareDocument6 pages2.0 The Origins of Softwarewangui machariaNo ratings yet
- SW 2Document18 pagesSW 2ahmed emadNo ratings yet
- SPQM 1Document5 pagesSPQM 1Zuhaib AyazNo ratings yet
- Module - 7 Information Systems Development PDFDocument15 pagesModule - 7 Information Systems Development PDFJan JanNo ratings yet
- FosDocument3 pagesFosPabitha ChidambaramNo ratings yet
- Butler Group Technology AuditDocument8 pagesButler Group Technology AuditaukasickNo ratings yet
- Software Reuse Research: Status and Future: William B. Frakes and Kyo KangDocument8 pagesSoftware Reuse Research: Status and Future: William B. Frakes and Kyo KangMaurício Ama AlineNo ratings yet
- Chapter OneDocument6 pagesChapter OnewalelegneNo ratings yet
- Proposal 111Document6 pagesProposal 111ConillyMwaleNo ratings yet
- WP How APIs Enhance A Devops ModelDocument24 pagesWP How APIs Enhance A Devops ModelpramsNo ratings yet
- SDCL Pract 3Document6 pagesSDCL Pract 3Mahesh DarvankarNo ratings yet
- Conventional and Open Source Software Reuse at Orbotech PDFDocument8 pagesConventional and Open Source Software Reuse at Orbotech PDFDoThuThuyNo ratings yet
- hm6 Module3Document27 pageshm6 Module3Irene Asiong NagramaNo ratings yet
- A Pattern Language of Software LicensingDocument42 pagesA Pattern Language of Software LicensingMohamed HelmyNo ratings yet
- Open Source Vs Proprietary Software, A White PaperDocument8 pagesOpen Source Vs Proprietary Software, A White PaperAH JewelNo ratings yet
- Module 5 - Reading5 - SystemDevelopmentDocument13 pagesModule 5 - Reading5 - SystemDevelopmentChristopher AdvinculaNo ratings yet
- AssignmentDocument9 pagesAssignmentAkib ZabedNo ratings yet
- PRESENTED BY Ankita Seth Depertment Cse Class Roll 016 REGISTRATION NO 092360110006 ROLL NO 09236001031Document19 pagesPRESENTED BY Ankita Seth Depertment Cse Class Roll 016 REGISTRATION NO 092360110006 ROLL NO 09236001031Ankita SethNo ratings yet
- Ais Chapter 9Document10 pagesAis Chapter 9LaDolceDieylaNo ratings yet
- Software Testing Interview Questions You'll Most Likely Be AskedFrom EverandSoftware Testing Interview Questions You'll Most Likely Be AskedNo ratings yet
- Cost Estimation in Agile Software Development: Utilizing Functional Size Measurement MethodsFrom EverandCost Estimation in Agile Software Development: Utilizing Functional Size Measurement MethodsNo ratings yet
- Real FreewareDocument8 pagesReal Freewareapi-14658459No ratings yet
- ReadmeDocument18 pagesReadmeDaniel ShaneNo ratings yet
- WK 1 ProjgroupbDocument11 pagesWK 1 Projgroupbapi-281267078No ratings yet
- Googe DocsDocument15 pagesGooge DocsGOKUL KNo ratings yet
- 22634-2022-Winter-Model-Answer-Paper (Msbte Study Resources)Document25 pages22634-2022-Winter-Model-Answer-Paper (Msbte Study Resources)ashusonkamble979No ratings yet
- TIBCO Business Works: Narendra ThotaDocument51 pagesTIBCO Business Works: Narendra ThotaThangapandi MayikalaiNo ratings yet
- The Ultimate Guide To Starting Your First Ecommerce Business PDFDocument86 pagesThe Ultimate Guide To Starting Your First Ecommerce Business PDFzim1992No ratings yet
- Drools WB DocsDocument228 pagesDrools WB Docspsnspk100% (1)
- Computer AbbreviationsDocument54 pagesComputer AbbreviationsIrfan KhanNo ratings yet
- Web MiningDocument71 pagesWeb MiningNirav TrivediNo ratings yet
- 2021 Star Event Planning Process Summary PageDocument1 page2021 Star Event Planning Process Summary Pageapi-542325761No ratings yet
- Instagram Vs Snapchat Vs Twitter: CIS1-222 Shahid LowtherDocument11 pagesInstagram Vs Snapchat Vs Twitter: CIS1-222 Shahid LowtherShahidNo ratings yet
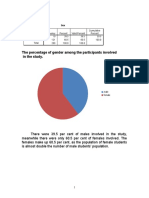
- Frequency Table: Frequency Percent Valid Percent Cumulative PercentDocument19 pagesFrequency Table: Frequency Percent Valid Percent Cumulative PercentAmierahIzzatiAisyahNo ratings yet
- William Stallings Data and Computer Communications 7 EditionDocument26 pagesWilliam Stallings Data and Computer Communications 7 Editioneng2011techNo ratings yet
- MGN 350Document9 pagesMGN 350Sabab ZamanNo ratings yet
- Deakin 2016Document16 pagesDeakin 2016Sultan PasolleNo ratings yet
- Install .NET Framework 3.5 in Windows 10Document7 pagesInstall .NET Framework 3.5 in Windows 10Soporte GruposamNo ratings yet
- 02 Upgrading Microsoft Dynamics CRM - Pre-Engagement QuestionnaireDocument19 pages02 Upgrading Microsoft Dynamics CRM - Pre-Engagement Questionnairezidanejason8No ratings yet
- Treasure Hunt RubricDocument1 pageTreasure Hunt Rubricapi-252684479No ratings yet
- Interior Design Thesis Topic IdeasDocument8 pagesInterior Design Thesis Topic Ideascandicehimwarren100% (2)
- 07 Task Performance 1Document1 page07 Task Performance 1Chubby QuerolNo ratings yet
- 1343637440moneysaver Shopping GuideDocument16 pages1343637440moneysaver Shopping GuideCoolerAdsNo ratings yet
- Industry Standards Activity OverviewDocument7 pagesIndustry Standards Activity OverviewHugo Soruco SolizNo ratings yet
- Grocery StoreDocument16 pagesGrocery StoreBhavyaNo ratings yet
- Mysearchengines 150208065440 Conversion Gate02Document22 pagesMysearchengines 150208065440 Conversion Gate02Franz Lawrenz De TorresNo ratings yet
- FlashFire: Overcoming The Performance Bottleneck of Flash Storage TechnologyDocument13 pagesFlashFire: Overcoming The Performance Bottleneck of Flash Storage Technologyalcuin99No ratings yet
- Student Clubs and Organization ManualDocument28 pagesStudent Clubs and Organization ManualPhoyagerNo ratings yet
- Alfresco Datasheet Records ManagementDocument3 pagesAlfresco Datasheet Records ManagementJelatang HinaNo ratings yet