Professional Documents
Culture Documents
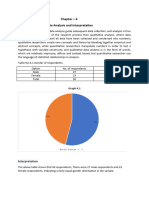
SEMRPT1
SEMRPT1
Uploaded by
ImrannkhanCopyright:
Available Formats
You might also like
- Project 3a Hacking Web Apps With Command Injections and Patching ThemDocument3 pagesProject 3a Hacking Web Apps With Command Injections and Patching Themmaylinpatydakin0% (1)
- Product Comparisons Avaya IP Office Vs Panasonic KX TDA and EDocument2 pagesProduct Comparisons Avaya IP Office Vs Panasonic KX TDA and Ejorgerh1017100% (1)
- Command Injection - OWASPDocument5 pagesCommand Injection - OWASPANIMESH301No ratings yet
- Commix: Detecting and Exploiting Command Injection FlawsDocument9 pagesCommix: Detecting and Exploiting Command Injection Flawsdoudi doudaNo ratings yet
- OS Command Injection PDF 1634745915Document36 pagesOS Command Injection PDF 1634745915Rodrigo JuanNo ratings yet
- ABSTRACTDocument1 pageABSTRACTImrannkhanNo ratings yet
- Comando Shell PDFDocument108 pagesComando Shell PDFOctavio CarmonaNo ratings yet
- Master Semminar Injection ExploitsDocument24 pagesMaster Semminar Injection ExploitsKarol StępniewskiNo ratings yet
- Evidence Gathering System For Input Attacks: Deepak Singh Tomar, J.L.Rana and S.C.ShrivastavaDocument4 pagesEvidence Gathering System For Input Attacks: Deepak Singh Tomar, J.L.Rana and S.C.Shrivastavavol1no1No ratings yet
- Copmtia Security+ Part2Document104 pagesCopmtia Security+ Part2MANAL BENNOUFNo ratings yet
- Practical Dynamic Taint Analysis For Countering Input Validation Attacks On Web ApplicationsDocument15 pagesPractical Dynamic Taint Analysis For Countering Input Validation Attacks On Web Applicationsthanga_sharmiNo ratings yet
- Command Inj OverflowDocument8 pagesCommand Inj OverflowSoumitri MukherjeeNo ratings yet
- Implementasi Penutupan Celah Keamanan Pada Aplikasi Web Berbasis Joomla 1.5.5 Serta Server Berbasis Ubuntu 8.04 Dengan Kernel 2.6.24Document8 pagesImplementasi Penutupan Celah Keamanan Pada Aplikasi Web Berbasis Joomla 1.5.5 Serta Server Berbasis Ubuntu 8.04 Dengan Kernel 2.6.24Yudi 'Goemon' PrabowoNo ratings yet
- Wa0006Document3 pagesWa000621UGDF005 Akhΐl.KNo ratings yet
- A 201720 InjectionDocument8 pagesA 201720 InjectionMuhammad YaqubNo ratings yet
- Mini Project On Information and Cyber Security: SQL (Structured Query Language) InjectionDocument9 pagesMini Project On Information and Cyber Security: SQL (Structured Query Language) Injectioncyan whiteNo ratings yet
- Building Secure High-Performance Web Services With OKWS: Maxwell Krohn, MIT Computer Science and AI LaboratoryDocument14 pagesBuilding Secure High-Performance Web Services With OKWS: Maxwell Krohn, MIT Computer Science and AI LaboratoryalkalacidNo ratings yet
- Hacking Web ApplicationsDocument5 pagesHacking Web ApplicationsDeandryn RussellNo ratings yet
- Reference 1 - 2017Document13 pagesReference 1 - 2017abenezer ketemaNo ratings yet
- WSF: An HTTP-level Firewall For Hardening Web Servers: Threat ModelDocument6 pagesWSF: An HTTP-level Firewall For Hardening Web Servers: Threat ModeltestNo ratings yet
- 5 Common Web Application VulnerabilitiesDocument4 pages5 Common Web Application VulnerabilitiesAnonymous Fhs3ufkCNo ratings yet
- InjectiomDocument2 pagesInjectiomAdu-Boahene ChristianNo ratings yet
- SQL ProtectorDocument5 pagesSQL ProtectorGunanto SNo ratings yet
- Software Quality AssuranceDocument24 pagesSoftware Quality AssuranceSYED SUMAIR AHMED JAFFRINo ratings yet
- A.1 Cross-Site ScriptingDocument7 pagesA.1 Cross-Site ScriptingJastine AnneNo ratings yet
- WP SQL Injection 20Document11 pagesWP SQL Injection 20Abdul Basit ZulkefliNo ratings yet
- Security+ 601 Test 2Document61 pagesSecurity+ 601 Test 2Kalen StarNo ratings yet
- Hacking Module 14Document24 pagesHacking Module 14Jitendra Kumar Dash100% (1)
- Lectre 13Document6 pagesLectre 13AkRajNo ratings yet
- Application Security: Coding PracticesDocument3 pagesApplication Security: Coding PracticesSridhar PNo ratings yet
- Web Application Security VulnerabilitiesDocument5 pagesWeb Application Security VulnerabilitiesHailu TsegaNo ratings yet
- Incident HandlingDocument18 pagesIncident HandlingDijanaaaaaaNo ratings yet
- Detection of SQL Injection Attack in Web Applications Using Web ServicesDocument8 pagesDetection of SQL Injection Attack in Web Applications Using Web ServicesInternational Organization of Scientific Research (IOSR)No ratings yet
- Security Testing MatDocument9 pagesSecurity Testing MatLias JassiNo ratings yet
- Chris Choyce An Exploration of Injection AttacksDocument13 pagesChris Choyce An Exploration of Injection AttacksDurgesh PrabhugaonkarNo ratings yet
- An Architectural Approach To Forestalling Code InjectionDocument52 pagesAn Architectural Approach To Forestalling Code InjectionRaghavendra Shivaram0% (1)
- System HookingDocument17 pagesSystem HookingdomeleuNo ratings yet
- Ceh Chap8 QuizletDocument2 pagesCeh Chap8 QuizletlynnverbNo ratings yet
- Injections 101 Cissp WorkbookDocument27 pagesInjections 101 Cissp WorkbookmarutidivekarNo ratings yet
- CEH-Module-6 ShortDocument346 pagesCEH-Module-6 Shortmaddy moviesNo ratings yet
- Practical Insight Into InjectionsDocument27 pagesPractical Insight Into InjectionsasdffNo ratings yet
- L28 - Security 1Document20 pagesL28 - Security 1C-dawgNo ratings yet
- Rial Approach For Preventing SQLDocument6 pagesRial Approach For Preventing SQLShaik NooruddinNo ratings yet
- KotlinDocument10 pagesKotlinAlif ErfanNo ratings yet
- Developers:: 1) Shreyash Mahadik 2) Vishakha Kadam 3) Anurag Gupta 4) Prajakta KhatalDocument11 pagesDevelopers:: 1) Shreyash Mahadik 2) Vishakha Kadam 3) Anurag Gupta 4) Prajakta KhatalShreyash MahadikNo ratings yet
- Detection and Evasion of Web Application Attacks: K. K. MookheyDocument66 pagesDetection and Evasion of Web Application Attacks: K. K. Mookheyggst81No ratings yet
- Information Security: Muhammad Aon BalouchDocument8 pagesInformation Security: Muhammad Aon BalouchBilal Khan RindNo ratings yet
- By Hari RuthalaDocument37 pagesBy Hari RuthalaRao Ali ShanNo ratings yet
- Lecture Videos: 2. Intrusion Detection 4. Symmetric EncryptionDocument19 pagesLecture Videos: 2. Intrusion Detection 4. Symmetric EncryptiongodilaliNo ratings yet
- 05563777(1)+++Document5 pages05563777(1)+++MhackSahuNo ratings yet
- 01 - Security EssentialsDocument34 pages01 - Security EssentialsMan ModiNo ratings yet
- Analyzing SQL Meta Characters and Preven PDFDocument4 pagesAnalyzing SQL Meta Characters and Preven PDFPramono PramonoNo ratings yet
- Security Code Review-Identifying Web Vulnerabilities: Kiran Maraju, CISSP, CEH, ITIL, SCJPDocument10 pagesSecurity Code Review-Identifying Web Vulnerabilities: Kiran Maraju, CISSP, CEH, ITIL, SCJPSanjay PrajapatiNo ratings yet
- Information PDFDocument1 pageInformation PDFNikita SoniNo ratings yet
- Udemy Dump 2Document111 pagesUdemy Dump 2Gani RKNo ratings yet
- With Emphasis On Web Applications Security Related IssuesDocument28 pagesWith Emphasis On Web Applications Security Related IssuesFsohailNo ratings yet
- Infrastructure SecurityDocument107 pagesInfrastructure SecurityDoctor LyricsNo ratings yet
- Establishing Application SecurityDocument6 pagesEstablishing Application SecurityKarl Alvin Reyes HipolitoNo ratings yet
- SQL Injection: What Is It?Document8 pagesSQL Injection: What Is It?Shabari GirishNo ratings yet
- Application Security - Secure Software DevelopmentDocument7 pagesApplication Security - Secure Software DevelopmentSampth KarunarathneNo ratings yet
- Securing Application Deployment with Obfuscation and Code Signing: How to Create 3 Layers of Protection for .NET Release BuildFrom EverandSecuring Application Deployment with Obfuscation and Code Signing: How to Create 3 Layers of Protection for .NET Release BuildNo ratings yet
- Chapter 4Document23 pagesChapter 4ImrannkhanNo ratings yet
- Formulating Interacting Population: ModelDocument22 pagesFormulating Interacting Population: ModelImrannkhanNo ratings yet
- Verilog HDL Lab CodesDocument30 pagesVerilog HDL Lab CodesImrannkhanNo ratings yet
- Synopsis Final LastDocument15 pagesSynopsis Final LastImrannkhanNo ratings yet
- Verilog HDL Lab CodesDocument30 pagesVerilog HDL Lab CodesImrannkhanNo ratings yet
- 1.1 Mobile Terminal Power Consumption Reduction With Continuous Packet ConnectivityDocument14 pages1.1 Mobile Terminal Power Consumption Reduction With Continuous Packet ConnectivityImrannkhanNo ratings yet
- CONTENTDocument1 pageCONTENTImrannkhanNo ratings yet
- An Emergence of An Artificial Neural Network (ANN) As A Tool For Analysis of DifferentDocument1 pageAn Emergence of An Artificial Neural Network (ANN) As A Tool For Analysis of DifferentImrannkhanNo ratings yet
- A - B Sercos IDNsDocument64 pagesA - B Sercos IDNsleobooneNo ratings yet
- SFIN Pre-Check Report For Migrating To New Asset AccoutingDocument5 pagesSFIN Pre-Check Report For Migrating To New Asset AccoutingDeven ShuklaNo ratings yet
- sw10n65 swp10n65 swf10n65Document7 pagessw10n65 swp10n65 swf10n65jose luisNo ratings yet
- Grundfosliterature 130Document4 pagesGrundfosliterature 130Sorin DiaconuNo ratings yet
- WinCC Flexible SQL Datenbank enDocument30 pagesWinCC Flexible SQL Datenbank engj42107No ratings yet
- Electronic Assignment QuestionsDocument6 pagesElectronic Assignment QuestionsCalculus Chong Wei ChoonNo ratings yet
- PT0-101 NetworkArmyDocument84 pagesPT0-101 NetworkArmyMohammad Malek KhataeiNo ratings yet
- Ics 2370 Compiler Construction: Mr. Ussen KimanukaDocument19 pagesIcs 2370 Compiler Construction: Mr. Ussen KimanukaIAMMARKSNo ratings yet
- The Impact of Software Process Improvement On Quality: in Theory and PracticeDocument14 pagesThe Impact of Software Process Improvement On Quality: in Theory and PracticeJoan BakerlyNo ratings yet
- Root Causes AnalysisDocument3 pagesRoot Causes Analysisraviranchi02No ratings yet
- 02 Network Hardware EssentialsDocument38 pages02 Network Hardware EssentialsCheryl Marie AlimbaNo ratings yet
- Innodisk m5s0 Bgm2oavp-3317554Document22 pagesInnodisk m5s0 Bgm2oavp-3317554ManunoghiNo ratings yet
- Implementing Memristor Circuits Using LtspiceDocument9 pagesImplementing Memristor Circuits Using LtspiceGanagadhar CHNo ratings yet
- Application Note 149 January 2015 Modeling and Loop Compensation Design of Switching Mode Power SuppliesDocument22 pagesApplication Note 149 January 2015 Modeling and Loop Compensation Design of Switching Mode Power SuppliesArumugam RajendranNo ratings yet
- Dynex Dx-46l262a12 SMDocument52 pagesDynex Dx-46l262a12 SMMiguel angel SuarezNo ratings yet
- Electronic CircuitsDocument5 pagesElectronic CircuitsSubhan50No ratings yet
- IManager U2000 V200R018C66 Software Installation and Commissioning Guide (2288H V5 Server, Physics Machine) 01-CDocument82 pagesIManager U2000 V200R018C66 Software Installation and Commissioning Guide (2288H V5 Server, Physics Machine) 01-CyugNo ratings yet
- Network Device AuditDocument2 pagesNetwork Device AuditpathakdhavalNo ratings yet
- Crash 2024 01 28 - 20.27.00 ClientDocument20 pagesCrash 2024 01 28 - 20.27.00 Clientguilhermejob54No ratings yet
- Realisme Pada Komputer GrafikDocument39 pagesRealisme Pada Komputer GrafikFathoni Mahardika IINo ratings yet
- MA - Artist Installation Guide - v5.02 - ENDocument90 pagesMA - Artist Installation Guide - v5.02 - ENErik Romero CNo ratings yet
- J3160 ItxDocument56 pagesJ3160 ItxDigitriXNo ratings yet
- ReadmeDocument13 pagesReadmeLalo RuizNo ratings yet
- Anite 2Document76 pagesAnite 2Vamshi PoshalaNo ratings yet
- Trellix Network Security Data SheetDocument8 pagesTrellix Network Security Data SheetDuy NguyenNo ratings yet
- Micom T390 Universal Power Line Carrier: Amplifier Description and ConfigurationDocument44 pagesMicom T390 Universal Power Line Carrier: Amplifier Description and Configurationsaleem100% (1)
- CAN BusDocument11 pagesCAN BusDragan Lugonić100% (1)
- Qosmio F45-AV411Document4 pagesQosmio F45-AV411crisnavartaNo ratings yet
- SPA AngularJS DraftDocument155 pagesSPA AngularJS DraftsatyamtdNo ratings yet
SEMRPT1
SEMRPT1
Uploaded by
ImrannkhanOriginal Description:
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
SEMRPT1
SEMRPT1
Uploaded by
ImrannkhanCopyright:
Available Formats
OS COMMAND INJECTION
1. INTRODUCTION
In this section, we explain what OS command injection is, and describe how vulnerabilities
can be detected and exploited. We also show you some useful commands and techniques for
different operating systems, and describe how to prevent OS command injection. OS
command injection is also known as shell injection. It allows an attacker to execute operating
system (OS) commands on the server that is running an application, and typically fully
compromise the application and its data. Often, an attacker can leverage an OS command
injection vulnerability to compromise other parts of the hosting infrastructure, and exploit
trust relationships to pivot the attack to other systems within the organization. In a command
injection attack, an attacker tries to take control of the host operating system by injecting
arbitrary commands into a vulnerable application. Regardless of any security measures, these
commands can be carried out and potentially be used to steal data, crash systems, corrupt
databases, and even install malware that can be used later. In most cases, the lack of proper
input validation and sanitization allows attackers to exploit the command injection
vulnerability on the application. Attackers can execute malicious commands when the
application passes insecure user-supplied data to the system shell, such as cookies, form data,
or HTTP headers. There are many different types of command injection, including the direct
execution of shell commands, uploading of malicious files into the server's runtime
environment, and the exploitation of configuration file flaws.
Department of Computer Science and Engineering
PDA College of Engineering, Kalaburagi Page 1
OS COMMAND INJECTION
2. OS COMMAND INJECTION
2.1 What is OS Command Injection?
Command Injection is also referred to as Shell Injection or OS Injection. OS command
injection vulnerability allows attackers to execute arbitrary system commands on the attacked
party’s host operating system (OS). Doing this can override the original command to gain
access to a system, obtain sensitive data, or even execute an entire takeover of the application
server.
Some typical examples of command injection attacks include the insertion of harmful files
into the runtime environment of the vulnerable application’s server, shell command
execution, and abuse of configuration file vulnerabilities.
2.2 How Command Injection Occurs?
There are many situations when the developers try to include some functionalities into their
web application by making the use of the operating system commands. However, if the
application passes the user-supplied input directly to the server without any validation, thus
the application might become vulnerable to command injection attacks.
Fig: OS injection attack
Department of Computer Science and Engineering
PDA College of Engineering, Kalaburagi Page 2
OS COMMAND INJECTION
Command injection attack is performed in a system level commands to enable the attacker to
gain an unauthorized access or to retrieve information from a vulnerable web application
server. These are the steps of how OS commands inject works:
i. Attackers must identify vulnerabilities of the targeted web application; this allow attackers
to insert a malicious code into the OS and gain (some) functionality of the web application
without having direct access to the OS.
ii. Attackers alters the website content using HTML language by inserting the malicious code
in a form of cookies or HTTP headers.
iii. Once the malicious code is inserted into the web application server and become as an
origin code of the infected web application, now, browsers interpret this code and allow
attacker to execute specific commands across victim’s computers.
It is clearly that OS command injection vulnerability occurs when the user input is not
validated properly, instead, a malicious code inserted by an attacker is passed to the web
server without any sanitization. For example, a web application provides a ping functionality
for any IP address through his web application interface to any user to confirm a host
connection. That means, the ping command is passed directly to the web server. At this stage,
attacker can inject unwanted system command along with ping command using
metacharacters. Thus, the web application passes it to the web server for execution and allow
a gain control of that particular web server.
Fig. illustrates the OS command injection
Department of Computer Science and Engineering
PDA College of Engineering, Kalaburagi Page 3
OS COMMAND INJECTION
2.3 The basics of command injection vulnerabilities
A command injection attack can occur with web applications that run OS commands to
interact with the host and file systems. They execute system commands, start applications in a
different language, or execute shell, Python, Perl, or PHP scripts. While this functionality is
standard, it can be used for cyber attacks.
The main loophole through which command injection can be executed is when user-supplied
input is not validated in applications. This input is used in the construction of commands that
will be executed. Such cyber-attacks are possible when a web application passes the
unverified user input (cookies, forms, HTTP headers, and the like) directly to OS functions
like exec() and system(). The input is always a string (string cmd) linked to a constant string
of the application, which shapes the full command.
Command injection is also known as shell injection. The arbitrary commands that the attacker
applies to the system shell of the webserver running the application can compromise all
relevant data. The command injection can also attack other systems in the infrastructure
connected to and trusted by the initial one. This is how the attacker can use the privileges of
the targeted application to gain wider control over the system.
Most OS command injections are blind security risks. The targeted application doesn’t return
the command output within the HTTP response. Still, blind injections are a security threat
and can be used to compromise a system.
Department of Computer Science and Engineering
PDA College of Engineering, Kalaburagi Page 4
OS COMMAND INJECTION
2.4 Examples of command injection and attacks scenario
Now that we have understood what command injection is let’s look at how it works.
PHP code example:
<?php
$address = $_GET["address"];
$output = shell_exec("ping -n 3 $address");
echo "<pre>$output</pre>";
?>
The PHP application developer wants the user to be able to access the web application's
output from the Windows ping command. So, the application requests the user's IP address
before sending ICMP pings to that address. Unfortunately, the developer needs to remember
to use the input validation mechanism.
The GET method is used to pass the IP address, which is then used in running a shell
command using the shell_exec function.
The shell_exec function runs the following operating system command:
ping -n 3 192.168.2.2&hostname. OS commands are separated in Windows by the &
symbol. As a result, the vulnerable application runs an additional command hostname and
shows the command's output.
Department of Computer Science and Engineering
PDA College of Engineering, Kalaburagi Page 5
OS COMMAND INJECTION
Python code example:
Let's look at a simple application that uses the nslookup command to perform a DNS lookup
on a domain. The application requests the domain name. When we enter the domain name,
the IP address from the DNS lookup is returned. To execute the command, we will
use subprocess module.
import subprocess
domain_name = input("Enter the domain name: ")
command = "nslookup {}".format(domain_name)
response = subprocess.check_output(command,shell=True,encoding='UTF-8')
print(response)
The output
The related IP address was returned when we entered google.com.
Department of Computer Science and Engineering
PDA College of Engineering, Kalaburagi Page 6
OS COMMAND INJECTION
2.5 The differences between command injection and code injection
While they seem similar, code and command injection are different types of vulnerabilities.
Code injection entails an attacker inserting new malicious code into a vulnerable application,
which executes. The attack is based on insufficient input validation of the malicious version
of user data. Therefore, the code injection attack is limited to the functionalities of the
application that is being targeted.
In contrast, a command injection is a case when an attacker modifies the default function of
the application that executes system commands. Thus, no new code is being inserted.
However, with a command injection, an attacker can target the server or systems of the
application and other trusted infrastructure by using the compromised application’s
privileges.
Department of Computer Science and Engineering
PDA College of Engineering, Kalaburagi Page 7
OS COMMAND INJECTION
2.6 Command Injection Methods
Here are some of the vulnerabilities that commonly lead to a command injection attack.
• Arbitrary command injection:
Some applications may enable users to run arbitrary commands, and run these commands
as is to the underlying host.
• Arbitrary file uploads:
If an application allows users to upload files with arbitrary file extensions, these files could
include malicious commands. On most web servers, placing such files in the webroot will
result in command injection.
• Insecure serialization:
Server-side code is typically used to deserialise user inputs. If deserialization is performed
without proper verification, it can result in command injection.
• Server-side template injection (SSTI):
Many web applications use server-side templates to generate dynamic HTML responses. This
makes it possible for attackers to insert malicious server-side templates. SSTI occurs when
user input is embedded in a template in an insecure manner, and code is executed remotely on
the server.
• XML external entity injection (XXE):
XXE occurs in applications that use a poorly-configured XML parser to parse user-controlled
XML input. This vulnerability can cause exposure of sensitive data, server-side request
forgery (SSRF), or denial of service attacks.
Department of Computer Science and Engineering
PDA College of Engineering, Kalaburagi Page 8
OS COMMAND INJECTION
2.7 How you can detect OS command injection attacks
There are many ways to detect command injection attacks. One way is to look at the request
parameters and see whether there are any suspicious strings. Another method is to examine
the response body and see whether there are unexpected results.
If you find that some of you’re application’s parameters have been modified, it could mean
someone has performed a command injection attack against your application.
Department of Computer Science and Engineering
PDA College of Engineering, Kalaburagi Page 9
OS COMMAND INJECTION
2.8 Types of Command Injection
Result based command injection
Blind command injection
o The time-based technique (Blind)
o The file-based technique (Semi blind)
Department of Computer Science and Engineering
PDA College of Engineering, Kalaburagi Page 10
OS COMMAND INJECTION
2.8.1.Result based command injection:
The output of the executed command would be visible in the response
An attacker can view the results of the command executed was success or not
Scenario: The application executes a shell command containing user-supplied product and
store IDs, and returns the raw output from the command in its response.
Output: Here the vulnerable parameter is stored.
Explanation: Here we have used the command whoami. It displays the name of the current
user.
Department of Computer Science and Engineering
PDA College of Engineering, Kalaburagi Page 11
OS COMMAND INJECTION
2.8.2Blind Command Injection:
The output of the executed command is not visible in the response
An attacker cannot view the results of the command executed
There are two types of blind command injection.
The time-based technique (Blind)
File-based technique (Semi Blind)
2.8.2.1 Time-based technique (Blind):
It is based on time delays
It can be determined by the length of the output, time is taken for delay
Once confirmed we can export char by char the output of the injected command using a
chain of OS commands, such as “cut”, “head” etc.
Scenario: The application executes a shell command containing the user-supplied details.
The output from the command is not returned in the response.
Output: Here the vulnerable parameter is an email address.
Image 1: As seen in the snapshot, we have captured the request of the feedback form.
Department of Computer Science and Engineering
PDA College of Engineering, Kalaburagi Page 12
OS COMMAND INJECTION
Image 2: As seen in the snapshot, the email parameter is vulnerable to blind command
injection.
Explanation: Here we have used ping command for time delay, as it lets you specify the
number of ICMP packets to send, and the time taken for the command to run: ping -c 10
127.0.0.1 This command will cause the application to ping its loopback network adapter for
10 seconds.
Department of Computer Science and Engineering
PDA College of Engineering, Kalaburagi Page 13
OS COMMAND INJECTION
2.8.2.2 File-based technique (semi-blind):
This technique is used when we are not able to view the results of the command injection,
but we can write it to a file accessible by us. Scenario: The application executes a shell
command containing the user-supplied details. The output from the command is not
returned in the response. You can use output redirection to capture the output from the
command. There is a writable folder at: /var/www/images/
Output: Here the vulnerable parameter is an email address.
Image 1: As seen in the snapshot, the email parameter is vulnerable and the output is
written in the output.txt file.
Department of Computer Science and Engineering
PDA College of Engineering, Kalaburagi Page 14
OS COMMAND INJECTION
Image 2: As seen in the snapshot, we are clicking on view details of the image and
capturing the request.
Department of Computer Science and Engineering
PDA College of Engineering, Kalaburagi Page 15
OS COMMAND INJECTION
2.9 Tool for exploiting command injection:
Commix :
Commix (a short for command injection exploiter) is a software tool aiming at facilitating
web developers, penetration testers and security researchers to test web applications with
the view to find bugs, errors or vulnerabilities related to command injection attacks.
https://github.com/stasinopoulos/commix
Written in Python programming language. Python version 2.6.x or 2.7.x is required.
Cross-platform application
o Linux
o Mac OS X
o Windows (experimental)
It is Open Source Software.
Commix also comes as a plugin, on the following penetration testing frameworks:
o The Penetration Testers Framework (PTF)
o PentestBox
o Weaker than
o CTF-Tools.
Department of Computer Science and Engineering
PDA College of Engineering, Kalaburagi Page 16
OS COMMAND INJECTION
3. IMPACT OF COMMAND INJECTION VULNERABILITIES
Command injection vulnerabilities can be difficult to detect and exploit, making them a
serious threat to businesses and individuals alike. It is often considered a high severity
vulnerability due to the wide-ranging impact it can have on an organization. Many popular
web applications and devices are vulnerable to command injection, which makes this type of
attack relatively easy to carry out.
Some Consequences of Command Injection Vulnerability are:
1. An attacker can execute arbitrary code on the target system, which can lead to a
complete compromise of the system.
2. An attacker can gain access to sensitive information stored on the target system.
3. An attacker can Denial of Service (DoS) the target system by injecting malicious
commands that consume all available resources.
4. An attacker can manipulate data stored on the target system, which can lead to
incorrect results or data loss.
5. An attacker can redirect network traffic from the target system to another system
under their control, allowing them to intercept and view confidential data.
6. An attacker can use command injection to pivot and attacking other systems on
the same network as the vulnerable system.
Department of Computer Science and Engineering
PDA College of Engineering, Kalaburagi Page 17
OS COMMAND INJECTION
4. COMMAND INJECTION PREVENTION:
Here are several practices you can implement in order to prevent command injections:
• Avoid system calls and user input—to prevent threat actors from inserting
characters into the OS command.
• Set up input validation—to prevent attacks like XSS and SQL Injection.
• Create a white list—of possible inputs, to ensure the system accepts only pre-
approved inputs.
• Use only secure APIs—when executing system commands such as execFile().
• Use execFile() securely—prevent users from gaining control over the name of the
program. You should also map user input to command arguments in a way that
ensures user input does not pass as-is into program execution.
• Sanitize user input: Make sure to properly validate and cleanse all user input before
using it in shell commands.
• Use parameterized queries: Use prepared statements with bound parameters instead of
dynamically building up shell commands from user input.
• Escape special characters: Properly escape all special characters in user input before
using it in shell commands.
• Disable command execution: Disable the ability to execute shell commands altogether
if possible.
• Use a web application firewall: use a WAF to help protect against command injection
attacks.
• Validate user input: Always validate user input to ensure that it is what you expect
and is within the bounds of what is allowed.
• Use a whitelist approach: Only allow input that matches a whitelist of known and
expected values.
• Disabling dangerous functions and commands: Many shells provide built-in functions
that can be used to execute commands. These functions should be disabled if not
needed, or properly restricted if they are needed.
• Use least privilege: Always run shell commands with the least amount of privileges
necessary. This will help limit the damage that can be done if a command injection
vulnerability is exploited.
• Logging and monitoring: Properly log all shell commands that are executed, and
monitor these logs for suspicious activity. This can help give you visibility into what
is happening on your systems and help detect potential command injection attacks
• Checking for malicious input: Always check user input for malicious content before
passing it to any system command. This includes things like checking for illegal
characters, attempting to execute commands, and more.
• Updating and patching: Keep your systems up-to-date with the latest security patches
and updates.
Department of Computer Science and Engineering
PDA College of Engineering, Kalaburagi Page 18
OS COMMAND INJECTION
• Implement security measures at the application level: In addition to implementing
security measures at the operating system level, it is also important to implement
security measures at the application level. This can help to further protect your
systems against command injection attacks.
• Educate your users: One of the best ways to help prevent command injection attacks.
Department of Computer Science and Engineering
PDA College of Engineering, Kalaburagi Page 19
OS COMMAND INJECTION
To check for blind command injections, you can use various detection techniques, such as
time delays, redirecting output and checking the file manually, or running an OOB network
interaction with an external server.
You can use some common parameters to test for operating system command injections:
cmd
exec
command
execute
ping
query
jump
code
reg
do
func
arg
option
load
process
step
read
function
req
feature
exe
module
payload
run
print
Department of Computer Science and Engineering
PDA College of Engineering, Kalaburagi Page 20
OS COMMAND INJECTION
Rejecting unacceptable code user input validation and sanitizing to the web server is
required by the server to avoid injecting unwanted code by an attacker and that can be
achieved by creating:
o Blacklist which contain different commonly combinations of metacharacters to
protect their web applications from OS command attack. As a result, OS
command attack using metacharacters only work when developers forget to
add a specific metacharacter combination to his blacklist.
o Whitelist which contain only the values list that are accepted by the web server
and reject all other values.
Department of Computer Science and Engineering
PDA College of Engineering, Kalaburagi Page 21
OS COMMAND INJECTION
5. CONCLUSION
In this seminar, we have presented the formal definition of command injection attacks in
web applications. User inputs are treated as isolated lexical entities which, if not properly
sanitized, can cause the web application to generate unintended output. This is called a
command injection attack, which poses a serious threat to web application security. To
conclude, OS command injection can result in unauthorized code execution and potential
data breaches, allowing attackers to gain control over systems, execute malicious
commands, and access sensitive information. Many shells provide built-in functions that can
be used to execute commands to avoid these command injections. These functions should be
disabled if not needed, or properly restricted if they are needed. Always check user input for
malicious content before passing it to any system command. This includes things like
checking for illegal characters, attempting to execute commands, and more. Keep your
systems up-to-date with the latest security patches and updates. In addition to implementing
security measures at the operating system level, it is also important to implement security
measures at the application level. This can help to further protect your systems against
command injection attacks.
Department of Computer Science and Engineering
PDA College of Engineering, Kalaburagi Page 22
OS COMMAND INJECTION
6. REFERENCES
• https://www.imperva.com/learn/application-security/command-injection/
• https://www.hackingarticles.in/comprehensive-guide-on-os-command-injection/
• https://cheatsheetseries.owasp.org/cheatsheets/
• https://www.cobalt.io/blog/introduction-to-command-injection-vulnerability/
• https://www.researchgate.net/publication/The-essence-of-command-injection-attacks-
in-webapplications/
• Open Web Application Security Project (OWASP). (2017). OWASP Top Ten Project.
Retrieved 15, February 2021, from https://www.owasp.org.
• Open Web Application Security Project (OWASP). (2010). OWASP Top Ten
Project. Retrieved 15, February 2021, from https://www.owasp.org. 3.
• Open Web Application Security Project (OWASP). (2013). OWASP Top Ten Project.
Retrieved 15, February 2021, from https://www.owasp.org.
• Al-Khurafi, O.B.; and Al-Ahmad, M.A. (2015). Survey of web application
vulnerability attacks. 4th International Conference on Advanced Computer Science
Applications and Technologies (ACSAT). Kuala Lumpur, Malaysia, 154-158.
• Chandel, R. (2021). Comprehensive guide on OS command injection. Retrieved 15,
February 2021, from https://www.hackingarticles.in/comprehensive-guideon-os-
command-injection/
• Barracuda Networks, I. (2021). OS-command injection. Retrieved 18 February 2021,
from https://campus.barracuda.com.
Department of Computer Science and Engineering
PDA College of Engineering, Kalaburagi Page 23
You might also like
- Project 3a Hacking Web Apps With Command Injections and Patching ThemDocument3 pagesProject 3a Hacking Web Apps With Command Injections and Patching Themmaylinpatydakin0% (1)
- Product Comparisons Avaya IP Office Vs Panasonic KX TDA and EDocument2 pagesProduct Comparisons Avaya IP Office Vs Panasonic KX TDA and Ejorgerh1017100% (1)
- Command Injection - OWASPDocument5 pagesCommand Injection - OWASPANIMESH301No ratings yet
- Commix: Detecting and Exploiting Command Injection FlawsDocument9 pagesCommix: Detecting and Exploiting Command Injection Flawsdoudi doudaNo ratings yet
- OS Command Injection PDF 1634745915Document36 pagesOS Command Injection PDF 1634745915Rodrigo JuanNo ratings yet
- ABSTRACTDocument1 pageABSTRACTImrannkhanNo ratings yet
- Comando Shell PDFDocument108 pagesComando Shell PDFOctavio CarmonaNo ratings yet
- Master Semminar Injection ExploitsDocument24 pagesMaster Semminar Injection ExploitsKarol StępniewskiNo ratings yet
- Evidence Gathering System For Input Attacks: Deepak Singh Tomar, J.L.Rana and S.C.ShrivastavaDocument4 pagesEvidence Gathering System For Input Attacks: Deepak Singh Tomar, J.L.Rana and S.C.Shrivastavavol1no1No ratings yet
- Copmtia Security+ Part2Document104 pagesCopmtia Security+ Part2MANAL BENNOUFNo ratings yet
- Practical Dynamic Taint Analysis For Countering Input Validation Attacks On Web ApplicationsDocument15 pagesPractical Dynamic Taint Analysis For Countering Input Validation Attacks On Web Applicationsthanga_sharmiNo ratings yet
- Command Inj OverflowDocument8 pagesCommand Inj OverflowSoumitri MukherjeeNo ratings yet
- Implementasi Penutupan Celah Keamanan Pada Aplikasi Web Berbasis Joomla 1.5.5 Serta Server Berbasis Ubuntu 8.04 Dengan Kernel 2.6.24Document8 pagesImplementasi Penutupan Celah Keamanan Pada Aplikasi Web Berbasis Joomla 1.5.5 Serta Server Berbasis Ubuntu 8.04 Dengan Kernel 2.6.24Yudi 'Goemon' PrabowoNo ratings yet
- Wa0006Document3 pagesWa000621UGDF005 Akhΐl.KNo ratings yet
- A 201720 InjectionDocument8 pagesA 201720 InjectionMuhammad YaqubNo ratings yet
- Mini Project On Information and Cyber Security: SQL (Structured Query Language) InjectionDocument9 pagesMini Project On Information and Cyber Security: SQL (Structured Query Language) Injectioncyan whiteNo ratings yet
- Building Secure High-Performance Web Services With OKWS: Maxwell Krohn, MIT Computer Science and AI LaboratoryDocument14 pagesBuilding Secure High-Performance Web Services With OKWS: Maxwell Krohn, MIT Computer Science and AI LaboratoryalkalacidNo ratings yet
- Hacking Web ApplicationsDocument5 pagesHacking Web ApplicationsDeandryn RussellNo ratings yet
- Reference 1 - 2017Document13 pagesReference 1 - 2017abenezer ketemaNo ratings yet
- WSF: An HTTP-level Firewall For Hardening Web Servers: Threat ModelDocument6 pagesWSF: An HTTP-level Firewall For Hardening Web Servers: Threat ModeltestNo ratings yet
- 5 Common Web Application VulnerabilitiesDocument4 pages5 Common Web Application VulnerabilitiesAnonymous Fhs3ufkCNo ratings yet
- InjectiomDocument2 pagesInjectiomAdu-Boahene ChristianNo ratings yet
- SQL ProtectorDocument5 pagesSQL ProtectorGunanto SNo ratings yet
- Software Quality AssuranceDocument24 pagesSoftware Quality AssuranceSYED SUMAIR AHMED JAFFRINo ratings yet
- A.1 Cross-Site ScriptingDocument7 pagesA.1 Cross-Site ScriptingJastine AnneNo ratings yet
- WP SQL Injection 20Document11 pagesWP SQL Injection 20Abdul Basit ZulkefliNo ratings yet
- Security+ 601 Test 2Document61 pagesSecurity+ 601 Test 2Kalen StarNo ratings yet
- Hacking Module 14Document24 pagesHacking Module 14Jitendra Kumar Dash100% (1)
- Lectre 13Document6 pagesLectre 13AkRajNo ratings yet
- Application Security: Coding PracticesDocument3 pagesApplication Security: Coding PracticesSridhar PNo ratings yet
- Web Application Security VulnerabilitiesDocument5 pagesWeb Application Security VulnerabilitiesHailu TsegaNo ratings yet
- Incident HandlingDocument18 pagesIncident HandlingDijanaaaaaaNo ratings yet
- Detection of SQL Injection Attack in Web Applications Using Web ServicesDocument8 pagesDetection of SQL Injection Attack in Web Applications Using Web ServicesInternational Organization of Scientific Research (IOSR)No ratings yet
- Security Testing MatDocument9 pagesSecurity Testing MatLias JassiNo ratings yet
- Chris Choyce An Exploration of Injection AttacksDocument13 pagesChris Choyce An Exploration of Injection AttacksDurgesh PrabhugaonkarNo ratings yet
- An Architectural Approach To Forestalling Code InjectionDocument52 pagesAn Architectural Approach To Forestalling Code InjectionRaghavendra Shivaram0% (1)
- System HookingDocument17 pagesSystem HookingdomeleuNo ratings yet
- Ceh Chap8 QuizletDocument2 pagesCeh Chap8 QuizletlynnverbNo ratings yet
- Injections 101 Cissp WorkbookDocument27 pagesInjections 101 Cissp WorkbookmarutidivekarNo ratings yet
- CEH-Module-6 ShortDocument346 pagesCEH-Module-6 Shortmaddy moviesNo ratings yet
- Practical Insight Into InjectionsDocument27 pagesPractical Insight Into InjectionsasdffNo ratings yet
- L28 - Security 1Document20 pagesL28 - Security 1C-dawgNo ratings yet
- Rial Approach For Preventing SQLDocument6 pagesRial Approach For Preventing SQLShaik NooruddinNo ratings yet
- KotlinDocument10 pagesKotlinAlif ErfanNo ratings yet
- Developers:: 1) Shreyash Mahadik 2) Vishakha Kadam 3) Anurag Gupta 4) Prajakta KhatalDocument11 pagesDevelopers:: 1) Shreyash Mahadik 2) Vishakha Kadam 3) Anurag Gupta 4) Prajakta KhatalShreyash MahadikNo ratings yet
- Detection and Evasion of Web Application Attacks: K. K. MookheyDocument66 pagesDetection and Evasion of Web Application Attacks: K. K. Mookheyggst81No ratings yet
- Information Security: Muhammad Aon BalouchDocument8 pagesInformation Security: Muhammad Aon BalouchBilal Khan RindNo ratings yet
- By Hari RuthalaDocument37 pagesBy Hari RuthalaRao Ali ShanNo ratings yet
- Lecture Videos: 2. Intrusion Detection 4. Symmetric EncryptionDocument19 pagesLecture Videos: 2. Intrusion Detection 4. Symmetric EncryptiongodilaliNo ratings yet
- 05563777(1)+++Document5 pages05563777(1)+++MhackSahuNo ratings yet
- 01 - Security EssentialsDocument34 pages01 - Security EssentialsMan ModiNo ratings yet
- Analyzing SQL Meta Characters and Preven PDFDocument4 pagesAnalyzing SQL Meta Characters and Preven PDFPramono PramonoNo ratings yet
- Security Code Review-Identifying Web Vulnerabilities: Kiran Maraju, CISSP, CEH, ITIL, SCJPDocument10 pagesSecurity Code Review-Identifying Web Vulnerabilities: Kiran Maraju, CISSP, CEH, ITIL, SCJPSanjay PrajapatiNo ratings yet
- Information PDFDocument1 pageInformation PDFNikita SoniNo ratings yet
- Udemy Dump 2Document111 pagesUdemy Dump 2Gani RKNo ratings yet
- With Emphasis On Web Applications Security Related IssuesDocument28 pagesWith Emphasis On Web Applications Security Related IssuesFsohailNo ratings yet
- Infrastructure SecurityDocument107 pagesInfrastructure SecurityDoctor LyricsNo ratings yet
- Establishing Application SecurityDocument6 pagesEstablishing Application SecurityKarl Alvin Reyes HipolitoNo ratings yet
- SQL Injection: What Is It?Document8 pagesSQL Injection: What Is It?Shabari GirishNo ratings yet
- Application Security - Secure Software DevelopmentDocument7 pagesApplication Security - Secure Software DevelopmentSampth KarunarathneNo ratings yet
- Securing Application Deployment with Obfuscation and Code Signing: How to Create 3 Layers of Protection for .NET Release BuildFrom EverandSecuring Application Deployment with Obfuscation and Code Signing: How to Create 3 Layers of Protection for .NET Release BuildNo ratings yet
- Chapter 4Document23 pagesChapter 4ImrannkhanNo ratings yet
- Formulating Interacting Population: ModelDocument22 pagesFormulating Interacting Population: ModelImrannkhanNo ratings yet
- Verilog HDL Lab CodesDocument30 pagesVerilog HDL Lab CodesImrannkhanNo ratings yet
- Synopsis Final LastDocument15 pagesSynopsis Final LastImrannkhanNo ratings yet
- Verilog HDL Lab CodesDocument30 pagesVerilog HDL Lab CodesImrannkhanNo ratings yet
- 1.1 Mobile Terminal Power Consumption Reduction With Continuous Packet ConnectivityDocument14 pages1.1 Mobile Terminal Power Consumption Reduction With Continuous Packet ConnectivityImrannkhanNo ratings yet
- CONTENTDocument1 pageCONTENTImrannkhanNo ratings yet
- An Emergence of An Artificial Neural Network (ANN) As A Tool For Analysis of DifferentDocument1 pageAn Emergence of An Artificial Neural Network (ANN) As A Tool For Analysis of DifferentImrannkhanNo ratings yet
- A - B Sercos IDNsDocument64 pagesA - B Sercos IDNsleobooneNo ratings yet
- SFIN Pre-Check Report For Migrating To New Asset AccoutingDocument5 pagesSFIN Pre-Check Report For Migrating To New Asset AccoutingDeven ShuklaNo ratings yet
- sw10n65 swp10n65 swf10n65Document7 pagessw10n65 swp10n65 swf10n65jose luisNo ratings yet
- Grundfosliterature 130Document4 pagesGrundfosliterature 130Sorin DiaconuNo ratings yet
- WinCC Flexible SQL Datenbank enDocument30 pagesWinCC Flexible SQL Datenbank engj42107No ratings yet
- Electronic Assignment QuestionsDocument6 pagesElectronic Assignment QuestionsCalculus Chong Wei ChoonNo ratings yet
- PT0-101 NetworkArmyDocument84 pagesPT0-101 NetworkArmyMohammad Malek KhataeiNo ratings yet
- Ics 2370 Compiler Construction: Mr. Ussen KimanukaDocument19 pagesIcs 2370 Compiler Construction: Mr. Ussen KimanukaIAMMARKSNo ratings yet
- The Impact of Software Process Improvement On Quality: in Theory and PracticeDocument14 pagesThe Impact of Software Process Improvement On Quality: in Theory and PracticeJoan BakerlyNo ratings yet
- Root Causes AnalysisDocument3 pagesRoot Causes Analysisraviranchi02No ratings yet
- 02 Network Hardware EssentialsDocument38 pages02 Network Hardware EssentialsCheryl Marie AlimbaNo ratings yet
- Innodisk m5s0 Bgm2oavp-3317554Document22 pagesInnodisk m5s0 Bgm2oavp-3317554ManunoghiNo ratings yet
- Implementing Memristor Circuits Using LtspiceDocument9 pagesImplementing Memristor Circuits Using LtspiceGanagadhar CHNo ratings yet
- Application Note 149 January 2015 Modeling and Loop Compensation Design of Switching Mode Power SuppliesDocument22 pagesApplication Note 149 January 2015 Modeling and Loop Compensation Design of Switching Mode Power SuppliesArumugam RajendranNo ratings yet
- Dynex Dx-46l262a12 SMDocument52 pagesDynex Dx-46l262a12 SMMiguel angel SuarezNo ratings yet
- Electronic CircuitsDocument5 pagesElectronic CircuitsSubhan50No ratings yet
- IManager U2000 V200R018C66 Software Installation and Commissioning Guide (2288H V5 Server, Physics Machine) 01-CDocument82 pagesIManager U2000 V200R018C66 Software Installation and Commissioning Guide (2288H V5 Server, Physics Machine) 01-CyugNo ratings yet
- Network Device AuditDocument2 pagesNetwork Device AuditpathakdhavalNo ratings yet
- Crash 2024 01 28 - 20.27.00 ClientDocument20 pagesCrash 2024 01 28 - 20.27.00 Clientguilhermejob54No ratings yet
- Realisme Pada Komputer GrafikDocument39 pagesRealisme Pada Komputer GrafikFathoni Mahardika IINo ratings yet
- MA - Artist Installation Guide - v5.02 - ENDocument90 pagesMA - Artist Installation Guide - v5.02 - ENErik Romero CNo ratings yet
- J3160 ItxDocument56 pagesJ3160 ItxDigitriXNo ratings yet
- ReadmeDocument13 pagesReadmeLalo RuizNo ratings yet
- Anite 2Document76 pagesAnite 2Vamshi PoshalaNo ratings yet
- Trellix Network Security Data SheetDocument8 pagesTrellix Network Security Data SheetDuy NguyenNo ratings yet
- Micom T390 Universal Power Line Carrier: Amplifier Description and ConfigurationDocument44 pagesMicom T390 Universal Power Line Carrier: Amplifier Description and Configurationsaleem100% (1)
- CAN BusDocument11 pagesCAN BusDragan Lugonić100% (1)
- Qosmio F45-AV411Document4 pagesQosmio F45-AV411crisnavartaNo ratings yet
- SPA AngularJS DraftDocument155 pagesSPA AngularJS DraftsatyamtdNo ratings yet