Professional Documents
Culture Documents
5 2+Information+Security+Roles+and+Responsibilities
5 2+Information+Security+Roles+and+Responsibilities
Uploaded by
pomowoh476Copyright:
Available Formats
You might also like
- Issue Specific Security PolicyDocument3 pagesIssue Specific Security PolicyAnusha KNo ratings yet
- Information Security Governance & Risk ManagementDocument37 pagesInformation Security Governance & Risk Managementsamirdas_hyd70% (10)
- Lab #4 - Assessment Worksheet Craft A Layered Security Management Policy - Separation of Duties ABC Credit Union Policy Name+ Policy StatementDocument4 pagesLab #4 - Assessment Worksheet Craft A Layered Security Management Policy - Separation of Duties ABC Credit Union Policy Name+ Policy StatementVo Minh Khanh (K14 HCM)No ratings yet
- SS Brewtech 1V Using Omron E5CC PID Cheat SheetDocument2 pagesSS Brewtech 1V Using Omron E5CC PID Cheat SheetJNo ratings yet
- International Business and TradeDocument20 pagesInternational Business and TradeShook Ga100% (9)
- ISO/ IEC 27001:2013 Lead Implementer Training Trainer: Trivesh Sharma, Oyuntugs BDocument7 pagesISO/ IEC 27001:2013 Lead Implementer Training Trainer: Trivesh Sharma, Oyuntugs BTrivesh SharmaNo ratings yet
- Information Security PolicyDocument16 pagesInformation Security Policymohammed oumerNo ratings yet
- IAS ReviewerDocument11 pagesIAS ReviewerRaissa GonzagaNo ratings yet
- Information Security Policy ExampleDocument5 pagesInformation Security Policy ExampleScribdTranslationsNo ratings yet
- Information Security Policy TEMPLATE V1Document6 pagesInformation Security Policy TEMPLATE V1norsyalizaNo ratings yet
- GSU Cyber Security CharterDocument14 pagesGSU Cyber Security CharterAreefNo ratings yet
- Security Policy DocumentDocument5 pagesSecurity Policy DocumentKefa MwitaNo ratings yet
- Cybersecurity Framework PolicyDocument5 pagesCybersecurity Framework PolicyrabiaNo ratings yet
- Lab01 - IAP301 - L Duy Vinh - HE163984Document4 pagesLab01 - IAP301 - L Duy Vinh - HE163984vinhldhe163984No ratings yet
- Lecture Notes ISMSDocument37 pagesLecture Notes ISMS山石恭纷No ratings yet
- Lab4-Le Quang Vu-SE160967-IA1702Document8 pagesLab4-Le Quang Vu-SE160967-IA1702Le Quang Vu (K16HCM)No ratings yet
- Assignment#2 200963Document3 pagesAssignment#2 200963Aoun MuhammadNo ratings yet
- Module 7 Assignment Section 10 Implementation Compliance EnforcementDocument5 pagesModule 7 Assignment Section 10 Implementation Compliance Enforcementapi-360051483No ratings yet
- BSI ISOIEC27001 Assessment Checklist UK enDocument3 pagesBSI ISOIEC27001 Assessment Checklist UK enDanushkaPereraNo ratings yet
- Incident Component RolesDocument14 pagesIncident Component RolesANIRUDH B K 19BIT0348No ratings yet
- Information Security Policy TemplateDocument5 pagesInformation Security Policy TemplatePrateekNo ratings yet
- The Structure of ISO 27001Document11 pagesThe Structure of ISO 27001Mohammed Abdus Subhan100% (1)
- 5 3+Segregation+of+DutiesDocument2 pages5 3+Segregation+of+Dutiespomowoh476No ratings yet
- Incident Component Roles: Dr.I.Sumaiya Thaseen, Associate Professor, SITEDocument14 pagesIncident Component Roles: Dr.I.Sumaiya Thaseen, Associate Professor, SITEuday kiranNo ratings yet
- RohitDocument75 pagesRohitRobin PalanNo ratings yet
- Information Technology - Remote Access - SOPDocument4 pagesInformation Technology - Remote Access - SOPKaitlyn PawlowskiNo ratings yet
- IT Security Policy For BISEDocument7 pagesIT Security Policy For BISENawal SafdarNo ratings yet
- Iso 17799Document44 pagesIso 17799deltafx1No ratings yet
- SBCP Information Security and Governance OverviewDocument8 pagesSBCP Information Security and Governance OverviewKavya GopakumarNo ratings yet
- Information Security Policy - GlomantechDocument3 pagesInformation Security Policy - GlomantechDavid KoiralaNo ratings yet
- QuestionnaireDocument9 pagesQuestionnairejayasree donakondaNo ratings yet
- BIT2318: Topic 6: Protection of Information AssetsDocument44 pagesBIT2318: Topic 6: Protection of Information AssetszatoNo ratings yet
- Information Systems and Technology SecurityDocument5 pagesInformation Systems and Technology SecurityTanteNo ratings yet
- Information Security FundamentalsDocument8 pagesInformation Security Fundamentalshiranya33No ratings yet
- Information Security PolicyDocument20 pagesInformation Security PolicyKapil SinghalNo ratings yet
- Information Security Management and MetricsDocument30 pagesInformation Security Management and MetricsAdityaNo ratings yet
- Information Security GovernanceDocument14 pagesInformation Security GovernanceAla' Esam ZayadeenNo ratings yet
- Module 1 AssignmentDocument4 pagesModule 1 Assignmentapi-360051483No ratings yet
- IT Availability and Capacity Policy and ProcedureDocument25 pagesIT Availability and Capacity Policy and Procedureislam108No ratings yet
- ISO27002 Policy IndexDocument11 pagesISO27002 Policy IndexMLastTryNo ratings yet
- Information Security Officer Job DescriptionDocument11 pagesInformation Security Officer Job DescriptionMohammed AlkhayalNo ratings yet
- ISO27001 Server Security Best Practices ChecklistDocument4 pagesISO27001 Server Security Best Practices Checklistfnky_byNo ratings yet
- Information Governance Policy For UEH IDocument6 pagesInformation Governance Policy For UEH IAdeel AhmedNo ratings yet
- IT Security StrategyDocument6 pagesIT Security StrategyGaurav AgarwalNo ratings yet
- Account Management PolicyDocument5 pagesAccount Management PolicyLyman MubukaniNo ratings yet
- Security PrinciplesDocument10 pagesSecurity PrinciplessecureuxNo ratings yet
- 8 - Information Classification and Protection PolicyDocument6 pages8 - Information Classification and Protection Policypentesting.443No ratings yet
- Cle Unit - 3 PDFDocument31 pagesCle Unit - 3 PDFYugal SingamNo ratings yet
- Information Security Delivery - Scenario 7Document21 pagesInformation Security Delivery - Scenario 7ScribdTranslationsNo ratings yet
- Information Security Roles & Responsibilities: PurposeDocument5 pagesInformation Security Roles & Responsibilities: PurposeLuis Fernando Quintero Henao100% (1)
- The Scope and Functions of The Professional Safety Position PDFDocument5 pagesThe Scope and Functions of The Professional Safety Position PDFTrainer 1 TVSNo ratings yet
- ISO 270012013 A17 Information Security Aspects of Business ContinuitynbspmanagementDocument17 pagesISO 270012013 A17 Information Security Aspects of Business Continuitynbspmanagementfitriah adjisNo ratings yet
- Industrial Safety Management PYQ AnsDocument54 pagesIndustrial Safety Management PYQ AnsNagendra KumarNo ratings yet
- c808 APPENDIX 75BDocument8 pagesc808 APPENDIX 75Balan dumsNo ratings yet
- 2.4 The Information Systems Function in BusinessDocument2 pages2.4 The Information Systems Function in BusinessGlorrya TambotoNo ratings yet
- 2.2 Cyber Security Policy Development and Implementation-1-1Document17 pages2.2 Cyber Security Policy Development and Implementation-1-1Llal SantiagoNo ratings yet
- Lecture 8 Organizational StructureDocument25 pagesLecture 8 Organizational Structurekaren07leonenNo ratings yet
- Information Security Management System Policies - V8Document32 pagesInformation Security Management System Policies - V8Sekar KrishNo ratings yet
- Cs-Csps Niap Ism Job Description Eng v1.1Document7 pagesCs-Csps Niap Ism Job Description Eng v1.1daniel hamdaniNo ratings yet
- CCISO Course OutlineDocument15 pagesCCISO Course OutlineshrikantNo ratings yet
- Full Value of Data: Driving Business Success with the Full Value of Data. Part 3From EverandFull Value of Data: Driving Business Success with the Full Value of Data. Part 3No ratings yet
- IS Auditor - Process of Auditing: Information Systems Auditor, #1From EverandIS Auditor - Process of Auditing: Information Systems Auditor, #1No ratings yet
- Vendor Management: Definition and UsesDocument3 pagesVendor Management: Definition and UsessnowFlakes A0% (1)
- Creating String in PythonDocument12 pagesCreating String in PythonJames NgugiNo ratings yet
- IR 392mammo 01EDocument504 pagesIR 392mammo 01Ekrsrinivasaraju100% (1)
- Huawei HyperClone Technical White Paper PDFDocument14 pagesHuawei HyperClone Technical White Paper PDFMenganoFulanoNo ratings yet
- Computer Organization Architecture - Topic 4Document67 pagesComputer Organization Architecture - Topic 4asj233510377No ratings yet
- Artificial Intelligence To Assist Mathematical ReasoningDocument89 pagesArtificial Intelligence To Assist Mathematical Reasoningabcdef0567890No ratings yet
- Inventory AllDocument20 pagesInventory Alldidier arizaNo ratings yet
- g6 Os Installation GuideDocument7 pagesg6 Os Installation GuideRK shuklaNo ratings yet
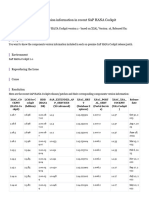
- Components Version Information in Recent SAP HANA Cockpit Releases PatchesDocument2 pagesComponents Version Information in Recent SAP HANA Cockpit Releases PatchesankurbamelNo ratings yet
- GIS Mapping 13932 - ACF1Document6 pagesGIS Mapping 13932 - ACF1mp dcNo ratings yet
- Learning Path 1 - Lab 1 - Exercise 1 - Explore Microsoft 365 DefenderDocument4 pagesLearning Path 1 - Lab 1 - Exercise 1 - Explore Microsoft 365 DefendernanoanxoNo ratings yet
- Uplift Modeling: A Quick Introduction: Learn How Uplift Modeling Can Improve Classic Data Science ApplicationsDocument1 pageUplift Modeling: A Quick Introduction: Learn How Uplift Modeling Can Improve Classic Data Science ApplicationsFares HasnaouiNo ratings yet
- Phase 2 (Second Half)Document9 pagesPhase 2 (Second Half)gan.yek2018No ratings yet
- The Role of The Via: Home Defining The Via Types For Use With Your Board in Altium DesignerDocument5 pagesThe Role of The Via: Home Defining The Via Types For Use With Your Board in Altium DesignerBenyamin Farzaneh AghajarieNo ratings yet
- Oracle Taleo Enterprise Edition: Implementing AssessmentDocument56 pagesOracle Taleo Enterprise Edition: Implementing AssessmentAbdallah FayezNo ratings yet
- Form 5 Paper 2 2020Document18 pagesForm 5 Paper 2 2020Noor AimanNo ratings yet
- Bose Home Speaker 500Document44 pagesBose Home Speaker 500mona srivastavaNo ratings yet
- (Technical) Pen-Testing ResourcesDocument108 pages(Technical) Pen-Testing ResourcesRamirez Altamirano Renne JaysonNo ratings yet
- Getting STM32Document20 pagesGetting STM32Senat Polmed100% (1)
- BACC401 - Forensic Accounting Investigative TechniquesDocument5 pagesBACC401 - Forensic Accounting Investigative TechniquesChad RaffertyNo ratings yet
- Web ProjectsDocument10 pagesWeb Projectspepito.supermarket.baliNo ratings yet
- Geography - AE - AEE - Civil Engineering Handwritten Notes (CivilEnggForAll - Com) PDFDocument220 pagesGeography - AE - AEE - Civil Engineering Handwritten Notes (CivilEnggForAll - Com) PDFMANJUNo ratings yet
- Lec-3 Layer OSI ModelDocument34 pagesLec-3 Layer OSI ModelDivya GuptaNo ratings yet
- Apb Status TrackerDocument4 pagesApb Status Trackerjakk234No ratings yet
- Technical Description: BoilerDocument151 pagesTechnical Description: BoilerÍcaro VianaNo ratings yet
- Cert Week SC900Document12 pagesCert Week SC900AMD INFO100% (1)
- Multi-Head Self-Attention Transformer For Dogecoin Price PredictionDocument6 pagesMulti-Head Self-Attention Transformer For Dogecoin Price PredictionThu GiangNo ratings yet
- Exploring Microsoft PowerPoint AI, Using PythonDocument16 pagesExploring Microsoft PowerPoint AI, Using Pythonferdad4realNo ratings yet
5 2+Information+Security+Roles+and+Responsibilities
5 2+Information+Security+Roles+and+Responsibilities
Uploaded by
pomowoh476Original Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
5 2+Information+Security+Roles+and+Responsibilities
5 2+Information+Security+Roles+and+Responsibilities
Uploaded by
pomowoh476Copyright:
Available Formats
Information Security Roles and Responsibilities Policy
Objective: To ensure that personnel understand their roles and responsibilities in
maintaining the confidentiality, integrity, and availability of information.
Scope: This policy applies to all personnel and other interested parties who access or
manage information assets within the organization.
Policy Statement:
Roles and Responsibilities:
a. Senior management is responsible for providing direction and oversight of the
information security program.
b. The information security manager is responsible for the development,
implementation, and maintenance of the information security program.
c. Information owners are responsible for the classification, protection, and use of
information within their domain.
d. Information custodians are responsible for implementing the protection measures
specified by the information owners.
e. Personnel are responsible for following information security policies and procedures
and reporting any incidents or vulnerabilities to their supervisors.
Information Security Management System (ISMS):
a. The information security manager is responsible for the development,
implementation, and maintenance of the ISMS.
b. All personnel are responsible for complying with the ISMS and reporting any incidents
or vulnerabilities to their supervisors.
Access Control:
a. Information owners are responsible for defining the access requirements for their
information assets.
b. Information custodians are responsible for implementing the access controls
specified by the information owners.
c. Personnel are responsible for following access control policies and procedures.
Physical and Environmental Security:
a. Information owners are responsible for defining the physical and environmental
protection requirements for their information assets.
b. Information custodians are responsible for implementing the physical and
environmental protection measures specified by the information owners.
c. Personnel are responsible for following physical and environmental security policies
and procedures.
Information Systems Operations:
a. Information owners are responsible for defining the operational requirements for their
information assets.
b. Information custodians are responsible for implementing the operational measures
specified by the information owners.
c. Personnel are responsible for following information systems operations policies and
procedures.
Information Security Incident Management:
a. All personnel are responsible for reporting information security incidents to their
supervisors.
b. Supervisors are responsible for escalating incidents to the information security
manager.
c. The information security manager is responsible for managing information security
incidents and coordinating response efforts.
Responsibility: All personnel and other interested parties who access or manage
information assets are responsible for understanding and complying with their roles and
responsibilities as outlined in this policy.
Compliance: Non-compliance with this policy may result in disciplinary action, up to
and including termination of employment or contract.
Review: This policy will be reviewed annually or as necessary to ensure its continued
relevance and effectiveness in maintaining the confidentiality, integrity, and availability
of information.
The support of top management is crucial for successful implementation of the information
security management system.
The top management role is assigned to a person or group of persons who manage and control
the organization at its highest level.
The persons in this role are responsible for definition of the organization's strategy, definition of
goals, and the scope of the information security management system.
Leadership and involvement with regard to the Information Security Management System.
Definition of Roles.
Assignment of Responsibilities and rights in the Organization.
Provision of Resources and budget Approval.
Participation in management Reviews and isms Improvement.
The person in this role in the context of data protection should be aware of his or her influence
on
the goals, strategy and improvement of the Information Security Management system compliant
with ISO
The internal auditor role is responsible for the participation in the audit management process,
preparation and distribution of the audit report.
Assessment of organizations compliance with approved security measures in Statement of
Applicability.
Preparation of audit criteria to increase its quality development of technical expert skills in the
areas required in the organization.
Improvement and development of management systems in the organization.
The person in this role should be able to combine the practice of auditing information security
management
systems with knowledge on the organization and its security measures in terms of information
security.
You might also like
- Issue Specific Security PolicyDocument3 pagesIssue Specific Security PolicyAnusha KNo ratings yet
- Information Security Governance & Risk ManagementDocument37 pagesInformation Security Governance & Risk Managementsamirdas_hyd70% (10)
- Lab #4 - Assessment Worksheet Craft A Layered Security Management Policy - Separation of Duties ABC Credit Union Policy Name+ Policy StatementDocument4 pagesLab #4 - Assessment Worksheet Craft A Layered Security Management Policy - Separation of Duties ABC Credit Union Policy Name+ Policy StatementVo Minh Khanh (K14 HCM)No ratings yet
- SS Brewtech 1V Using Omron E5CC PID Cheat SheetDocument2 pagesSS Brewtech 1V Using Omron E5CC PID Cheat SheetJNo ratings yet
- International Business and TradeDocument20 pagesInternational Business and TradeShook Ga100% (9)
- ISO/ IEC 27001:2013 Lead Implementer Training Trainer: Trivesh Sharma, Oyuntugs BDocument7 pagesISO/ IEC 27001:2013 Lead Implementer Training Trainer: Trivesh Sharma, Oyuntugs BTrivesh SharmaNo ratings yet
- Information Security PolicyDocument16 pagesInformation Security Policymohammed oumerNo ratings yet
- IAS ReviewerDocument11 pagesIAS ReviewerRaissa GonzagaNo ratings yet
- Information Security Policy ExampleDocument5 pagesInformation Security Policy ExampleScribdTranslationsNo ratings yet
- Information Security Policy TEMPLATE V1Document6 pagesInformation Security Policy TEMPLATE V1norsyalizaNo ratings yet
- GSU Cyber Security CharterDocument14 pagesGSU Cyber Security CharterAreefNo ratings yet
- Security Policy DocumentDocument5 pagesSecurity Policy DocumentKefa MwitaNo ratings yet
- Cybersecurity Framework PolicyDocument5 pagesCybersecurity Framework PolicyrabiaNo ratings yet
- Lab01 - IAP301 - L Duy Vinh - HE163984Document4 pagesLab01 - IAP301 - L Duy Vinh - HE163984vinhldhe163984No ratings yet
- Lecture Notes ISMSDocument37 pagesLecture Notes ISMS山石恭纷No ratings yet
- Lab4-Le Quang Vu-SE160967-IA1702Document8 pagesLab4-Le Quang Vu-SE160967-IA1702Le Quang Vu (K16HCM)No ratings yet
- Assignment#2 200963Document3 pagesAssignment#2 200963Aoun MuhammadNo ratings yet
- Module 7 Assignment Section 10 Implementation Compliance EnforcementDocument5 pagesModule 7 Assignment Section 10 Implementation Compliance Enforcementapi-360051483No ratings yet
- BSI ISOIEC27001 Assessment Checklist UK enDocument3 pagesBSI ISOIEC27001 Assessment Checklist UK enDanushkaPereraNo ratings yet
- Incident Component RolesDocument14 pagesIncident Component RolesANIRUDH B K 19BIT0348No ratings yet
- Information Security Policy TemplateDocument5 pagesInformation Security Policy TemplatePrateekNo ratings yet
- The Structure of ISO 27001Document11 pagesThe Structure of ISO 27001Mohammed Abdus Subhan100% (1)
- 5 3+Segregation+of+DutiesDocument2 pages5 3+Segregation+of+Dutiespomowoh476No ratings yet
- Incident Component Roles: Dr.I.Sumaiya Thaseen, Associate Professor, SITEDocument14 pagesIncident Component Roles: Dr.I.Sumaiya Thaseen, Associate Professor, SITEuday kiranNo ratings yet
- RohitDocument75 pagesRohitRobin PalanNo ratings yet
- Information Technology - Remote Access - SOPDocument4 pagesInformation Technology - Remote Access - SOPKaitlyn PawlowskiNo ratings yet
- IT Security Policy For BISEDocument7 pagesIT Security Policy For BISENawal SafdarNo ratings yet
- Iso 17799Document44 pagesIso 17799deltafx1No ratings yet
- SBCP Information Security and Governance OverviewDocument8 pagesSBCP Information Security and Governance OverviewKavya GopakumarNo ratings yet
- Information Security Policy - GlomantechDocument3 pagesInformation Security Policy - GlomantechDavid KoiralaNo ratings yet
- QuestionnaireDocument9 pagesQuestionnairejayasree donakondaNo ratings yet
- BIT2318: Topic 6: Protection of Information AssetsDocument44 pagesBIT2318: Topic 6: Protection of Information AssetszatoNo ratings yet
- Information Systems and Technology SecurityDocument5 pagesInformation Systems and Technology SecurityTanteNo ratings yet
- Information Security FundamentalsDocument8 pagesInformation Security Fundamentalshiranya33No ratings yet
- Information Security PolicyDocument20 pagesInformation Security PolicyKapil SinghalNo ratings yet
- Information Security Management and MetricsDocument30 pagesInformation Security Management and MetricsAdityaNo ratings yet
- Information Security GovernanceDocument14 pagesInformation Security GovernanceAla' Esam ZayadeenNo ratings yet
- Module 1 AssignmentDocument4 pagesModule 1 Assignmentapi-360051483No ratings yet
- IT Availability and Capacity Policy and ProcedureDocument25 pagesIT Availability and Capacity Policy and Procedureislam108No ratings yet
- ISO27002 Policy IndexDocument11 pagesISO27002 Policy IndexMLastTryNo ratings yet
- Information Security Officer Job DescriptionDocument11 pagesInformation Security Officer Job DescriptionMohammed AlkhayalNo ratings yet
- ISO27001 Server Security Best Practices ChecklistDocument4 pagesISO27001 Server Security Best Practices Checklistfnky_byNo ratings yet
- Information Governance Policy For UEH IDocument6 pagesInformation Governance Policy For UEH IAdeel AhmedNo ratings yet
- IT Security StrategyDocument6 pagesIT Security StrategyGaurav AgarwalNo ratings yet
- Account Management PolicyDocument5 pagesAccount Management PolicyLyman MubukaniNo ratings yet
- Security PrinciplesDocument10 pagesSecurity PrinciplessecureuxNo ratings yet
- 8 - Information Classification and Protection PolicyDocument6 pages8 - Information Classification and Protection Policypentesting.443No ratings yet
- Cle Unit - 3 PDFDocument31 pagesCle Unit - 3 PDFYugal SingamNo ratings yet
- Information Security Delivery - Scenario 7Document21 pagesInformation Security Delivery - Scenario 7ScribdTranslationsNo ratings yet
- Information Security Roles & Responsibilities: PurposeDocument5 pagesInformation Security Roles & Responsibilities: PurposeLuis Fernando Quintero Henao100% (1)
- The Scope and Functions of The Professional Safety Position PDFDocument5 pagesThe Scope and Functions of The Professional Safety Position PDFTrainer 1 TVSNo ratings yet
- ISO 270012013 A17 Information Security Aspects of Business ContinuitynbspmanagementDocument17 pagesISO 270012013 A17 Information Security Aspects of Business Continuitynbspmanagementfitriah adjisNo ratings yet
- Industrial Safety Management PYQ AnsDocument54 pagesIndustrial Safety Management PYQ AnsNagendra KumarNo ratings yet
- c808 APPENDIX 75BDocument8 pagesc808 APPENDIX 75Balan dumsNo ratings yet
- 2.4 The Information Systems Function in BusinessDocument2 pages2.4 The Information Systems Function in BusinessGlorrya TambotoNo ratings yet
- 2.2 Cyber Security Policy Development and Implementation-1-1Document17 pages2.2 Cyber Security Policy Development and Implementation-1-1Llal SantiagoNo ratings yet
- Lecture 8 Organizational StructureDocument25 pagesLecture 8 Organizational Structurekaren07leonenNo ratings yet
- Information Security Management System Policies - V8Document32 pagesInformation Security Management System Policies - V8Sekar KrishNo ratings yet
- Cs-Csps Niap Ism Job Description Eng v1.1Document7 pagesCs-Csps Niap Ism Job Description Eng v1.1daniel hamdaniNo ratings yet
- CCISO Course OutlineDocument15 pagesCCISO Course OutlineshrikantNo ratings yet
- Full Value of Data: Driving Business Success with the Full Value of Data. Part 3From EverandFull Value of Data: Driving Business Success with the Full Value of Data. Part 3No ratings yet
- IS Auditor - Process of Auditing: Information Systems Auditor, #1From EverandIS Auditor - Process of Auditing: Information Systems Auditor, #1No ratings yet
- Vendor Management: Definition and UsesDocument3 pagesVendor Management: Definition and UsessnowFlakes A0% (1)
- Creating String in PythonDocument12 pagesCreating String in PythonJames NgugiNo ratings yet
- IR 392mammo 01EDocument504 pagesIR 392mammo 01Ekrsrinivasaraju100% (1)
- Huawei HyperClone Technical White Paper PDFDocument14 pagesHuawei HyperClone Technical White Paper PDFMenganoFulanoNo ratings yet
- Computer Organization Architecture - Topic 4Document67 pagesComputer Organization Architecture - Topic 4asj233510377No ratings yet
- Artificial Intelligence To Assist Mathematical ReasoningDocument89 pagesArtificial Intelligence To Assist Mathematical Reasoningabcdef0567890No ratings yet
- Inventory AllDocument20 pagesInventory Alldidier arizaNo ratings yet
- g6 Os Installation GuideDocument7 pagesg6 Os Installation GuideRK shuklaNo ratings yet
- Components Version Information in Recent SAP HANA Cockpit Releases PatchesDocument2 pagesComponents Version Information in Recent SAP HANA Cockpit Releases PatchesankurbamelNo ratings yet
- GIS Mapping 13932 - ACF1Document6 pagesGIS Mapping 13932 - ACF1mp dcNo ratings yet
- Learning Path 1 - Lab 1 - Exercise 1 - Explore Microsoft 365 DefenderDocument4 pagesLearning Path 1 - Lab 1 - Exercise 1 - Explore Microsoft 365 DefendernanoanxoNo ratings yet
- Uplift Modeling: A Quick Introduction: Learn How Uplift Modeling Can Improve Classic Data Science ApplicationsDocument1 pageUplift Modeling: A Quick Introduction: Learn How Uplift Modeling Can Improve Classic Data Science ApplicationsFares HasnaouiNo ratings yet
- Phase 2 (Second Half)Document9 pagesPhase 2 (Second Half)gan.yek2018No ratings yet
- The Role of The Via: Home Defining The Via Types For Use With Your Board in Altium DesignerDocument5 pagesThe Role of The Via: Home Defining The Via Types For Use With Your Board in Altium DesignerBenyamin Farzaneh AghajarieNo ratings yet
- Oracle Taleo Enterprise Edition: Implementing AssessmentDocument56 pagesOracle Taleo Enterprise Edition: Implementing AssessmentAbdallah FayezNo ratings yet
- Form 5 Paper 2 2020Document18 pagesForm 5 Paper 2 2020Noor AimanNo ratings yet
- Bose Home Speaker 500Document44 pagesBose Home Speaker 500mona srivastavaNo ratings yet
- (Technical) Pen-Testing ResourcesDocument108 pages(Technical) Pen-Testing ResourcesRamirez Altamirano Renne JaysonNo ratings yet
- Getting STM32Document20 pagesGetting STM32Senat Polmed100% (1)
- BACC401 - Forensic Accounting Investigative TechniquesDocument5 pagesBACC401 - Forensic Accounting Investigative TechniquesChad RaffertyNo ratings yet
- Web ProjectsDocument10 pagesWeb Projectspepito.supermarket.baliNo ratings yet
- Geography - AE - AEE - Civil Engineering Handwritten Notes (CivilEnggForAll - Com) PDFDocument220 pagesGeography - AE - AEE - Civil Engineering Handwritten Notes (CivilEnggForAll - Com) PDFMANJUNo ratings yet
- Lec-3 Layer OSI ModelDocument34 pagesLec-3 Layer OSI ModelDivya GuptaNo ratings yet
- Apb Status TrackerDocument4 pagesApb Status Trackerjakk234No ratings yet
- Technical Description: BoilerDocument151 pagesTechnical Description: BoilerÍcaro VianaNo ratings yet
- Cert Week SC900Document12 pagesCert Week SC900AMD INFO100% (1)
- Multi-Head Self-Attention Transformer For Dogecoin Price PredictionDocument6 pagesMulti-Head Self-Attention Transformer For Dogecoin Price PredictionThu GiangNo ratings yet
- Exploring Microsoft PowerPoint AI, Using PythonDocument16 pagesExploring Microsoft PowerPoint AI, Using Pythonferdad4realNo ratings yet