Professional Documents
Culture Documents
NSM Theory Deekshi
NSM Theory Deekshi
Uploaded by
Bhoomika BhuvanOriginal Description:
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
NSM Theory Deekshi
NSM Theory Deekshi
Uploaded by
Bhoomika BhuvanCopyright:
Available Formats
Network security and management (15CS62T) Security monitoring
Security monitoring
Security monitoring sometimes referred to as "security information monitoring
(SIM)" or "security event monitoring (SEM)," involves collecting and analyzing
information to detect suspicious behavior or unauthorized system changes on
your network, defining which types of behavior should trigger alerts, and taking
action on alerts as needed.
Security monitoring software detects and analyzes vulnerabilities, alerting you
of potential security issues. Cybersecurity warnings allow you to quickly protect
your organization from network intrusions and subsequent disasters.
security monitoring software collects metrics around client-server
communications, network payload, encrypted traffic sessions, and other
network operations to uncover cybersecurity threats. You can also use the
network security monitoring software to detect patterns in network traffic flows.
Moreover, you can use the software to generate automatic security alerts and
reports, enabling you to quickly respond to any suspicious activity and take
appropriate remedial actions.
leverage visualizations such as charts and graphs provided by network security
monitoring tools to pinpoint malicious activities and troubleshoot cybersecurity
threats.
VI Sem, Dept of CSE, Siddaganga Polytechnic, Tumkur 1
Network security and management (15CS62T) Security monitoring
The Difference Between Network Monitoring and Security Monitoring
A network monitoring application examines and tracks network activity for
problems caused by malfunctioning hardware or overloaded resources such as
servers, routers, and network connections. Network monitoring measures three
main metrics:
Network availability (uptime). This indicates how well the network
responds to the connectivity and throughput demands.
Network performance. This measures the network’s bandwidth,
throughput, latency, error rates, and jitter.
Network configuration. This process assigns network settings, policies,
controls, and flows to support communication.
A network monitoring tool can alert you by a short messaging system (SMS) or
email when it detects any problem with availability, performance, or
configuration.
As a network administrator, you need to understand your network topology,
configurations, performance, and even security to troubleshoot and correct the
problem.
VI Sem, Dept of CSE, Siddaganga Polytechnic, Tumkur 2
Network security and management (15CS62T) Security monitoring
A network security monitoring system, in contrast, protects the organization
from potential vulnerabilities and exploits.
Unlike network monitoring that offers generic monitoring, network security
monitoring analyzes multiple factors, including:
Network payload
Network protocols
Client-server communications
Traffic patterns
Encrypted traffic sessions
Traffic flow
The primary goal of network security monitoring is to provide continuous
service that checks the business environment for suspicious activities and
threats.
IT teams can then investigate the reported activities and take appropriate
corrective measures.
Although distinct, network monitoring and network security monitoring tools
often overlap. For example, the focus of network monitoring is to help you
understand the composition, availability status, performance, and configuration
of the network components.
However, network security monitoring is woven inexorably into each network
monitoring responsibility.
For example, you cannot achieve high throughput if an attacker floods the
network with malware that takes advantage of network configurations, leaving
your network vulnerable to exploits.
For these reasons, it’s typical to have network administrators work directly with
security teams to perform several tasks and correlate results.
VI Sem, Dept of CSE, Siddaganga Polytechnic, Tumkur 3
Network security and management (15CS62T) Security monitoring
Advantages of Security Monitoring
Achieve effective security without vigilance, and the cybersecurity world is no
different. Network security monitoring is the best way to vigilance in a
connected world.
Some advantages of network security monitoring are shorter cyber-threat
response times, easier security testing, and easier detection of subtle and new
threats.
Minimize the Cyber-Threat Response Time Significantly
Most attackers seem to seek out easy targets that have unprotected systems or
don’t watch their networks closely enough. Network security monitoring can
help you reduce the response time if a hacker tries to intrude.
Without an effective security monitoring solution, it can take months for you to
discover that your company has been hacked.
Simplify Security Testing
With an appropriate network security monitoring application, you can always
tweak the configurations in the settings menu. You can then use the application
to test the network to determine if it is still foolproof after configuring the
settings to your liking. Discover new threats
Because the cybersecurity landscape is changing continuously, you need an
intelligent tool that does not simply rely on known threats. With an effective
network security monitoring solution, you can always look for suspicious
activities and take corrective measures.
By discovering non-specific patterns, network monitoring solutions can help
you detect new threats such as “zero-day” attacks that would otherwise have
been difficult without one. Detect subtle threats more easily
Some attacks are obvious to detect in the network, while others are elusive. For
example, a blatant ransomware attack could lock up the entire PC, only
VI Sem, Dept of CSE, Siddaganga Polytechnic, Tumkur 4
Network security and management (15CS62T) Security monitoring
displaying the ransom note. On the other hand, bandwidth hijacking and botnets
are far more challenging to detect.
An effective network security monitoring solution can help you keep an eye on
any abnormal pattern, such as bandwidth hijacking and distributed denial-of-
service (DDoS) attacks.
Protecting Your Data with Parallels RAS
Digitization is no longer a competitive advantage or savvy option for today’s
businesses—it’s a necessity. However, as more and more companies undergo
digital transformation, cybersecurity attacks rise.
Secure and reliable networks safeguard the organization’s operations and
interests and any customer who exchanges data with the company.
Parallels® Remote Application Server (RAS) is an all-in-one, secure-by-design
desktop virtualization solution that simplifies access to corporate resources
while promoting organization productivity.
As a desktop virtualization solution, Parallels RAS centralizes the management
of IT resources. This provides employees with encrypted connections to the
datacenter using transport layer security (TSL) and Federal Information
Processing Standard (FIPS) 140-2 protocols.
IT teams can enable the right level of access to corporate resources based on
device, user profiles, network, or even location, for every employee, partner, or
contractor.
Centralized IT administration and access control policies allow the organization
to prevent data loss, ensure privacy and safeguard organization assets while
comprehensive real-time monitoring and reporting support compliance efforts.
VI Sem, Dept of CSE, Siddaganga Polytechnic, Tumkur 5
Network security and management (15CS62T) Security monitoring
Disadvantages of Security Monitoring
Security monitoring users may rest assured that their data is secure and well-
protected. The credit goes to the competency of network security. The area is
however challenged with a few drawbacks yet nothing outrageous that is
capable of outweighing its benefits. Let us look into the few disadvantages of
network security.
Expensive Set-Up
The installation of a network security solution might be costly. The expense of
purchasing software, installing it, and so on can add up quickly, especially in
smaller networks.
We're not talking about a single computer here, but rather a network of
computers that can store vast amounts of data. Since security is so important, it
will undoubtedly cost more. It must not be overlooked at any cost.
Time Consuming
Some of the software on some networks is difficult to use. To maintain double
security, it requires authentication using two passwords, one of which must be
entered every time you update a document.
It also necessitates the use of numbers, special characters, and alphabets in the
passwords. It's possible that the user will have to type a number of example
passwords before settling on one, which can take a long time.
Necessitates the employment of qualified personnel
Managing huge networks is a difficult endeavor. It necessitates highly trained
experts capable of dealing with any security issue that may develop. To
guarantee that the network runs well, a network administrator must be hired. To
meet the criterion, he must be properly trained.
VI Sem, Dept of CSE, Siddaganga Polytechnic, Tumkur 6
Network security and management (15CS62T) Security monitoring
Unscrupulous administration
When the best software is deployed and put in place and all of the necessary
tasks have been completed, it is natural for the administrator to become careless
at times. It is his responsibility to review the logs on a frequent basis in order to
keep an eye on the malicious users.
But there are instances when he simply trusts the system, and this is when the
attack occurs. Consequently, it is critical that the administrator be watchful at all
times.
Conclusion
Security monitoring operation within their organization. I used the open source
SO suite to show how to put NSM to work in a rapid and cost-effective manner.
This final section of the book shows several other options for NSM and related
operations. My goal is to show how NSM applies to other areas of digital
defense and how I think NSM will adapt to increasingly complex information
processing requirements.
VI Sem, Dept of CSE, Siddaganga Polytechnic, Tumkur 7
You might also like
- Security Operations Center - Analyst Guide: SIEM Technology, Use Cases and PracticesFrom EverandSecurity Operations Center - Analyst Guide: SIEM Technology, Use Cases and PracticesRating: 4 out of 5 stars4/5 (1)
- E85014-0012 - EST4 Network FirewallsDocument4 pagesE85014-0012 - EST4 Network Firewallsjunrey dasigNo ratings yet
- Presetation Report ON Network Security: Submitted To:-Submitted By: - Ms. Amba Ramneek Kaur Faculty, MRIU FET/CS(s) /2092Document19 pagesPresetation Report ON Network Security: Submitted To:-Submitted By: - Ms. Amba Ramneek Kaur Faculty, MRIU FET/CS(s) /2092Tushar ChandhokNo ratings yet
- Chapter 4 Computer SecurityDocument10 pagesChapter 4 Computer SecurityYared AyeleNo ratings yet
- Cybersecurity Analyst Interview Questions and AnswersDocument21 pagesCybersecurity Analyst Interview Questions and AnswersDhanraj chavanNo ratings yet
- CPPPMUSABDocument74 pagesCPPPMUSABMusabNo ratings yet
- Network Security: Compiled: Engineer M. Mago, Mba, MSC (Electronics & Automation Engineering, Telecoms)Document16 pagesNetwork Security: Compiled: Engineer M. Mago, Mba, MSC (Electronics & Automation Engineering, Telecoms)prosper mukaroNo ratings yet
- SOC Interview Questions and Answers 1716919142Document26 pagesSOC Interview Questions and Answers 1716919142Raghavendar Reddy BobbalaNo ratings yet
- Banking System Have ApplicationsDocument6 pagesBanking System Have ApplicationsRahul SurapaneniNo ratings yet
- Module 8 INFOSEC TECHNOLOGY COMPONENTSDocument25 pagesModule 8 INFOSEC TECHNOLOGY COMPONENTSlemonademagnumNo ratings yet
- A Methodology For Secure Network DesignDocument11 pagesA Methodology For Secure Network Designsaleem raza100% (1)
- Institute of Road and Transport Technology: ErodeDocument13 pagesInstitute of Road and Transport Technology: ErodeRishikaa RamNo ratings yet
- ForeScout Solution BrochureDocument6 pagesForeScout Solution BrochuresisiwansNo ratings yet
- Soc Interview Questions and Answers CYBER SECURITY ANALYSTDocument25 pagesSoc Interview Questions and Answers CYBER SECURITY ANALYSTelias kariuki100% (2)
- Network Security Research Papers 2015Document5 pagesNetwork Security Research Papers 2015humin1byjig2100% (1)
- Network Security Pros and ClassificationsDocument8 pagesNetwork Security Pros and ClassificationsAdam CooperNo ratings yet
- CRC Handbook of Modern Telecommunications, Second Edition (101-199)Document99 pagesCRC Handbook of Modern Telecommunications, Second Edition (101-199)2051150120No ratings yet
- NetworksecurityDocument3 pagesNetworksecurityRaymond RamirezNo ratings yet
- Saintgits Institute of Management: Project Phase-3Document5 pagesSaintgits Institute of Management: Project Phase-3Elroy JohnsonNo ratings yet
- Vulnerability Assessment For Applications Security Through Penetration Simulation and TestingDocument22 pagesVulnerability Assessment For Applications Security Through Penetration Simulation and TestingshameerNo ratings yet
- CPPPMUSABDocument75 pagesCPPPMUSABMusabNo ratings yet
- Eb Converged It and OtDocument14 pagesEb Converged It and OtmykillerdroneNo ratings yet
- The Importance of Security Inspection Procedure: Crishyl Mae Delfin-10 EinsteinDocument2 pagesThe Importance of Security Inspection Procedure: Crishyl Mae Delfin-10 EinsteinCaren MondiaNo ratings yet
- Module 3eDocument4 pagesModule 3ezackaryaskingNo ratings yet
- IT Security Management Checklist: 9 Key Recommendations To Keep Your Network SafeDocument11 pagesIT Security Management Checklist: 9 Key Recommendations To Keep Your Network SafeshabuzmushfiqueNo ratings yet
- Lancope Identity-Aware NetFlowDocument3 pagesLancope Identity-Aware NetFlowMorteza NekoeiNo ratings yet
- Chapert 3 and 4 PDF-1Document26 pagesChapert 3 and 4 PDF-1Tora SarkarNo ratings yet
- Acme Credit Reporting: Vulnerability and Management Implementation: Gatekeeper PlanDocument4 pagesAcme Credit Reporting: Vulnerability and Management Implementation: Gatekeeper PlanJaylon RansomNo ratings yet
- ASC Network ForensicsDocument13 pagesASC Network ForensicscrazysmellydogNo ratings yet
- Information Security Solution and Services (Security 360 Degree)Document7 pagesInformation Security Solution and Services (Security 360 Degree)shalinikuthe82No ratings yet
- Cop NetworkDocument5 pagesCop NetworkMiraculous MiracleNo ratings yet
- What Is Network Security - Cisco PDFDocument6 pagesWhat Is Network Security - Cisco PDFbhavesh_balasNo ratings yet
- Thesis - Computer-Security-Audit PDFDocument34 pagesThesis - Computer-Security-Audit PDFLoverianNo ratings yet
- Submitted by Pigu 3335Document39 pagesSubmitted by Pigu 3335Tiju SinghNo ratings yet
- Business Plan Network SecurityDocument4 pagesBusiness Plan Network SecurityxdjzssovfNo ratings yet
- Csi Zero Trust Network Environment PillarDocument12 pagesCsi Zero Trust Network Environment PillarAzaelCarionNo ratings yet
- SOC in A BoxDocument9 pagesSOC in A BoxA JosephNo ratings yet
- Security Assignment BriefDocument21 pagesSecurity Assignment BriefvishirushikaNo ratings yet
- Research Paper Topics in Network SecurityDocument5 pagesResearch Paper Topics in Network Securityp1zajywigyd2100% (1)
- Security Analytics Use CasesDocument12 pagesSecurity Analytics Use CasesLakshya SadanaNo ratings yet
- What Is Continuous Penetration Testing - BreachPointDocument4 pagesWhat Is Continuous Penetration Testing - BreachPointTehleel ManzoorNo ratings yet
- Best Practices For Securing Your Enterprise:: 10 Things You Need To KnowDocument10 pagesBest Practices For Securing Your Enterprise:: 10 Things You Need To KnowShubham GuptaNo ratings yet
- Manageengi: Net Wor K Moni T or I NGDocument9 pagesManageengi: Net Wor K Moni T or I NGLee KhanhNo ratings yet
- It ws05 Web SecurityDocument2 pagesIt ws05 Web Securityonezareden9No ratings yet
- Intrusion Detection and Prevention TechnologiesWA.1Document12 pagesIntrusion Detection and Prevention TechnologiesWA.1wasirifieNo ratings yet
- Day 1 PCD CYBERSEC Cybersecurity Day 1Document186 pagesDay 1 PCD CYBERSEC Cybersecurity Day 1Gabriel OdunugaNo ratings yet
- Security MonitoringDocument8 pagesSecurity MonitoringCockaMouseNo ratings yet
- CYB 220 Project Three Evaluation of Network Protection Technologies Abu AlamDocument5 pagesCYB 220 Project Three Evaluation of Network Protection Technologies Abu AlamAbu AlamNo ratings yet
- Lesson-2 1Document12 pagesLesson-2 1Bagongon, Jacob Yrrje C.No ratings yet
- Vinay Kumar ResumeDocument2 pagesVinay Kumar ResumeSathyam TakurNo ratings yet
- Controls Which Came Along The Way: Technical ControlsDocument6 pagesControls Which Came Along The Way: Technical ControlsGAURAV SOLANKINo ratings yet
- Cisco TetrationDocument2 pagesCisco TetrationShailesh JoshiNo ratings yet
- Security Architecture - D3-5Document216 pagesSecurity Architecture - D3-5Macprince danielNo ratings yet
- CYBERDocument13 pagesCYBERHassan SesayNo ratings yet
- Thesis Paper On Network SecurityDocument4 pagesThesis Paper On Network SecurityJessica Thompson100% (2)
- Visionary Innovation Leadership: Frost & Sullivan Best Practices AwardDocument10 pagesVisionary Innovation Leadership: Frost & Sullivan Best Practices AwardAparnaNo ratings yet
- Cyber Unit4 Lecture 4Document5 pagesCyber Unit4 Lecture 4Nitish YadavNo ratings yet
- Security Operations Centre Soc Buyers GuideDocument10 pagesSecurity Operations Centre Soc Buyers Guideep230842No ratings yet
- Ijnsa 050214Document14 pagesIjnsa 050214AIRCC - IJNSANo ratings yet
- Research Paper Network Security PDFDocument8 pagesResearch Paper Network Security PDFd1fytyt1man3100% (1)
- Cryptography and Data Security Book 1: Proper Guide to Data Security in Communication Networks. Cryptography and Data Security in PracticeFrom EverandCryptography and Data Security Book 1: Proper Guide to Data Security in Communication Networks. Cryptography and Data Security in PracticeNo ratings yet
- 4G LTE Integration TrainingDocument21 pages4G LTE Integration TrainingHichamHassaniNo ratings yet
- Imagerunner C1028I C1028If: You CanDocument4 pagesImagerunner C1028I C1028If: You CanAlex Alex AlexNo ratings yet
- L Guralp Cmg-dm24s3dcmDocument11 pagesL Guralp Cmg-dm24s3dcmRisky AftartuNo ratings yet
- Router Wi-Fi Wireless Access Point Repeater Configuration1Document13 pagesRouter Wi-Fi Wireless Access Point Repeater Configuration1Gerry Areola AquinoNo ratings yet
- Enterprise System Integration With Web Services: A Case Study With A Book Broker ApplicationDocument156 pagesEnterprise System Integration With Web Services: A Case Study With A Book Broker ApplicationAnonymous 2WKRBqFlfNo ratings yet
- 7KS70160 MegaLine F6-90 S-F Flex - 4x2xAWG 27-7 PIMF - 900 MHZDocument2 pages7KS70160 MegaLine F6-90 S-F Flex - 4x2xAWG 27-7 PIMF - 900 MHZRava SatrianiNo ratings yet
- Teldat-M1-Asociacion Vida YurimaguasDocument5 pagesTeldat-M1-Asociacion Vida YurimaguasJack Michell Cárdenas RubioNo ratings yet
- Qube XP-D Series 2 Operations Manual v1.0 - EnglishDocument91 pagesQube XP-D Series 2 Operations Manual v1.0 - Englishguerrero100% (1)
- M90 ZDocument2 pagesM90 ZaolloxNo ratings yet
- Understanding Y.1731 Performance MonitoringDocument6 pagesUnderstanding Y.1731 Performance Monitoringअमित सचानNo ratings yet
- Depliant SAMIP Release Mars GB 2011Document16 pagesDepliant SAMIP Release Mars GB 2011Shariq Ahmed KhanNo ratings yet
- 62TEDocument4 pages62TEFSR140780% (5)
- AIX (R) Version 7.1 Commands Reference, V - IBMDocument764 pagesAIX (R) Version 7.1 Commands Reference, V - IBMslimane00No ratings yet
- MicroNet MN 50 Controller Installation Instructions F-26617 - 07.10Document16 pagesMicroNet MN 50 Controller Installation Instructions F-26617 - 07.10Sergio HitcarNo ratings yet
- TP Fo Trimmed NNF Protocol 9.29Document275 pagesTP Fo Trimmed NNF Protocol 9.29Madhusoodan ShanbhagNo ratings yet
- Dial-Gate Softswitch by DialexiaDocument2 pagesDial-Gate Softswitch by DialexiaDialexia CommunicationsNo ratings yet
- Elvox - 2017Document51 pagesElvox - 2017jmcfeNo ratings yet
- A Presentation On PRTG Monitoring Software Used in Managing A NetworkDocument10 pagesA Presentation On PRTG Monitoring Software Used in Managing A NetworkkingNo ratings yet
- Hawk Series 2Xx/3Xxe/6Xx/6Xxe: Installation InstructionsDocument12 pagesHawk Series 2Xx/3Xxe/6Xx/6Xxe: Installation InstructionsErmiasNo ratings yet
- Different Networking Devices: Passive Hub Active HubDocument9 pagesDifferent Networking Devices: Passive Hub Active HubRodryan Karl GarayNo ratings yet
- Advanced MPLS 2014 PDFDocument470 pagesAdvanced MPLS 2014 PDFSaffanArainNo ratings yet
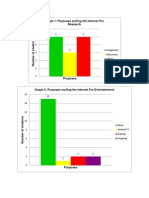
- Graph 1: Purposes Surfing The Internet For ResearchDocument2 pagesGraph 1: Purposes Surfing The Internet For ResearchNana KawaiiNo ratings yet
- An Effective Bandwidth Management by Compression Technique For Performance Enhancement in A SystemDocument7 pagesAn Effective Bandwidth Management by Compression Technique For Performance Enhancement in A SystemijsretNo ratings yet
- SAME DIRECTORY STRUCTURE - ACTIVE DATABASE DUPLICATION SERVER TO SERVER - (11g) PDFDocument17 pagesSAME DIRECTORY STRUCTURE - ACTIVE DATABASE DUPLICATION SERVER TO SERVER - (11g) PDFG.R.THIYAGU ; Oracle DBANo ratings yet
- Netbackup - Difference Between Multiplexing and Multi StreamingDocument2 pagesNetbackup - Difference Between Multiplexing and Multi StreamingamsreekuNo ratings yet
- Digsi 5 Iec61850 GooseDocument12 pagesDigsi 5 Iec61850 GooseWalter Andres Estevez VasquezNo ratings yet
- EGP2-X401 DatasheetDocument1 pageEGP2-X401 DatasheettakjeNo ratings yet
- ACER ACER Aspire V5-531pDocument103 pagesACER ACER Aspire V5-531pRicardo OlivaresNo ratings yet
- Research Paper - An Overview - ScienceDirect TopicsDocument10 pagesResearch Paper - An Overview - ScienceDirect TopicsTỪ TÀI HUỲNHNo ratings yet