Professional Documents
Culture Documents
Always ON
Always ON
Uploaded by
Nikola TasevskiCopyright:
Available Formats
You might also like
- Network and Security Lab Report: Lab 4.1: Installing Certificate ServicesDocument67 pagesNetwork and Security Lab Report: Lab 4.1: Installing Certificate Serviceslucifer thomasNo ratings yet
- Mendix Advanced Exam GuideDocument12 pagesMendix Advanced Exam GuideShishir KondaiNo ratings yet
- OldSiteOperators and ServiceSkidder610E (6101101-6102600) Service (6101101-6102500) 44477AENGDocument740 pagesOldSiteOperators and ServiceSkidder610E (6101101-6102600) Service (6101101-6102500) 44477AENGmarceloNo ratings yet
- BS en 00500Document66 pagesBS en 00500bugseNo ratings yet
- Puhy P850tkaDocument160 pagesPuhy P850tkaBrandon Antonio Peralta López100% (1)
- Measurand ManualDocument191 pagesMeasurand ManualfarquinNo ratings yet
- Enhanced Visual Intelligence at The Network Edge: Product BriefDocument2 pagesEnhanced Visual Intelligence at The Network Edge: Product BriefdanydwarNo ratings yet
- Module 09 - Deploying and Managing CertificatesDocument19 pagesModule 09 - Deploying and Managing CertificatesCong TuanNo ratings yet
- Lab: Configuring and Troubleshooting TS GatewayDocument10 pagesLab: Configuring and Troubleshooting TS Gatewaypablodg1980No ratings yet
- Deploying Web Server Certificate For Site SystemsDocument18 pagesDeploying Web Server Certificate For Site SystemsLaeeqSiddiquiNo ratings yet
- Module 11 - Implementing and Administering AD RMSDocument15 pagesModule 11 - Implementing and Administering AD RMSCong TuanNo ratings yet
- Windows Logon Using PKI TokensDocument24 pagesWindows Logon Using PKI Tokenspcouzens83No ratings yet
- Bài Thực Hành Giữa Kì Môn Học An Toàn Và An Ninh MạngDocument90 pagesBài Thực Hành Giữa Kì Môn Học An Toàn Và An Ninh MạngHoang AncientNo ratings yet
- Direct AccessDocument10 pagesDirect AccessneomorpheustrinitymatrixNo ratings yet
- Business ObjectsDocument62 pagesBusiness ObjectsponmudirajaNo ratings yet
- Microsoft Certificate Lifecycle Manager Quick Start GuideDocument8 pagesMicrosoft Certificate Lifecycle Manager Quick Start GuidevicogeoNo ratings yet
- Ad RMSDocument93 pagesAd RMSHungAnhNo ratings yet
- Business Objects XI AdministratorDocument62 pagesBusiness Objects XI Administratorachary_apNo ratings yet
- Configuring A Windows Server For RADIUSDocument7 pagesConfiguring A Windows Server For RADIUSaami145No ratings yet
- Module 08 - Deploying and Managing AD CSDocument12 pagesModule 08 - Deploying and Managing AD CSCong TuanNo ratings yet
- QMS User Guide - Managing Your CentreDocument15 pagesQMS User Guide - Managing Your CentreDon SheensNo ratings yet
- 802.1x Authentication With Cisco ACSDocument20 pages802.1x Authentication With Cisco ACSRiteesh Agrawal100% (1)
- Microsoft SC-900 LAB GUIDEDocument105 pagesMicrosoft SC-900 LAB GUIDEArdanNizmaAsadyNo ratings yet
- End PointDocument3 pagesEnd PointShibu VargheseNo ratings yet
- 11 SQL Config SP3DDocument39 pages11 SQL Config SP3DgoodmorningfredNo ratings yet
- Configuring Service Authentication and Account Policies: This Lab Contains The Following Exercises and ActivitiesDocument17 pagesConfiguring Service Authentication and Account Policies: This Lab Contains The Following Exercises and ActivitiesGuri DhillonNo ratings yet
- Generating and Installing Domain Controller CertificateDocument2 pagesGenerating and Installing Domain Controller CertificateGabriel Morales AngaritaNo ratings yet
- Troubleshooting Windows Small Business Server 2003Document44 pagesTroubleshooting Windows Small Business Server 2003shahegdeNo ratings yet
- BranchCache-Windows Server 2012R2 Step by StepDocument26 pagesBranchCache-Windows Server 2012R2 Step by StepEduar Moreno AlcasNo ratings yet
- VLSC Software Assurance GuideDocument11 pagesVLSC Software Assurance Guideangel ludeña marcaquispeNo ratings yet
- Lab - 1 Active Directory InstallationDocument32 pagesLab - 1 Active Directory InstallationsugapriyaNo ratings yet
- Exercise 1 Explore Partner Sales & Demo ResourcesDocument2 pagesExercise 1 Explore Partner Sales & Demo ResourcesEzequiasSilvaNo ratings yet
- Document of User ManagementDocument31 pagesDocument of User Managementsheikhaziz2949No ratings yet
- Module 4 Implementing VPN PDFDocument7 pagesModule 4 Implementing VPN PDFAfendey ArthurNo ratings yet
- ENSA Module 5 - Replacement LabDocument5 pagesENSA Module 5 - Replacement LabKarthik GanesanNo ratings yet
- AME Service Contract Approval 1456324.1Document10 pagesAME Service Contract Approval 1456324.1sreenivasNo ratings yet
- Data Migration To Sap S/4Hana: OpensapDocument27 pagesData Migration To Sap S/4Hana: OpensapRonit GhoseNo ratings yet
- Helpdesk Configuration TZ NewDocument10 pagesHelpdesk Configuration TZ Newdonald cyasNo ratings yet
- Proxy Authentication PortalDocument19 pagesProxy Authentication PortalEarl Ryan TorresNo ratings yet
- Zimbra To Office 365 Migration GuideDocument6 pagesZimbra To Office 365 Migration GuideEDSON ARIEL AJÚ GARCÍANo ratings yet
- Partner Membership Center To Partner Center TransitionDocument45 pagesPartner Membership Center To Partner Center TransitionGopinath GandhavadiNo ratings yet
- ScepDocument6 pagesScepAndres Barrios SaenzNo ratings yet
- Practice LabsDocument44 pagesPractice LabsMARIJOSENo ratings yet
- Troubleshooting Errors While Using DSCDocument11 pagesTroubleshooting Errors While Using DSChareshmsNo ratings yet
- Microsoft AD and Checkpoint NG AI Secure ClientDocument14 pagesMicrosoft AD and Checkpoint NG AI Secure Clientshark_99_05No ratings yet
- Create Report Net Content StoreDocument26 pagesCreate Report Net Content StoreJi RedNo ratings yet
- 2001215591-BanhTienKyAnh-Lab02B-Ex01-Configuring The Main Office Servers For BranchCacheDocument20 pages2001215591-BanhTienKyAnh-Lab02B-Ex01-Configuring The Main Office Servers For BranchCachekyanhbanhtien347No ratings yet
- S7 AdmincenerDocument14 pagesS7 AdmincenerДмирий МысовNo ratings yet
- Lab 12Document16 pagesLab 12Miguel MikeNo ratings yet
- Configuring Single Sign-On From The Vmware Identity Manager Service To FreshserviceDocument9 pagesConfiguring Single Sign-On From The Vmware Identity Manager Service To FreshservicekarthikNo ratings yet
- Module 03 - Advanced AD DS Infrastructure ManagementDocument13 pagesModule 03 - Advanced AD DS Infrastructure ManagementCong TuanNo ratings yet
- How To Guide For Solution Manager Security Optimization Self Service (SOS) REPORTINGDocument8 pagesHow To Guide For Solution Manager Security Optimization Self Service (SOS) REPORTINGLeon BratzNo ratings yet
- SCCM InstallationDocument76 pagesSCCM InstallationrkanfiNo ratings yet
- SAP Master Data Governance, Cloud Edition Trial Getting Started GuideDocument19 pagesSAP Master Data Governance, Cloud Edition Trial Getting Started GuidejeefmNo ratings yet
- Lab Answer Key - Module 8 - Implementing and Administering AD FSDocument29 pagesLab Answer Key - Module 8 - Implementing and Administering AD FSffNo ratings yet
- Installing Governance Minder InstructionsDocument48 pagesInstalling Governance Minder Instructionsyasas.biz100% (1)
- Step-By-Step Guide To Renewing Your Cisco Select CertificationDocument7 pagesStep-By-Step Guide To Renewing Your Cisco Select CertificationadkadimNo ratings yet
- SVMX101 ILT Workbook - CORE 22.1 LightningDocument88 pagesSVMX101 ILT Workbook - CORE 22.1 LightningRygel OrionisNo ratings yet
- CUCM 9.x+ and ELM - License Upgrade and InstallationDocument13 pagesCUCM 9.x+ and ELM - License Upgrade and InstallationJuan GarciaNo ratings yet
- The CMTrace OverviewDocument3 pagesThe CMTrace Overviewjainamit0622No ratings yet
- CA Cloud Service Management A Complete Guide - 2020 EditionFrom EverandCA Cloud Service Management A Complete Guide - 2020 EditionNo ratings yet
- SCCM software change and configuration management Standard RequirementsFrom EverandSCCM software change and configuration management Standard RequirementsNo ratings yet
- ELT - 280 - 1 Offshore Generation Cable ConnectionsDocument3 pagesELT - 280 - 1 Offshore Generation Cable ConnectionsNam Hoai LeNo ratings yet
- FPGA Programming Technology and Interconnect ArchitectureDocument32 pagesFPGA Programming Technology and Interconnect ArchitectureSrikar BabuNo ratings yet
- Full Introduction About Xilinx FPGA and Its ArchitectureDocument19 pagesFull Introduction About Xilinx FPGA and Its ArchitecturejackNo ratings yet
- Control of Inverter-Based Distribution Generation Used To Provide Premium Power QualityDocument7 pagesControl of Inverter-Based Distribution Generation Used To Provide Premium Power QualityebrahimNo ratings yet
- WP Flow Simulation Gas MixingDocument5 pagesWP Flow Simulation Gas MixingpengkritikNo ratings yet
- Transducers CatalogueDocument56 pagesTransducers CatalogueRavindarReddyD0% (1)
- Mastery in Hacking & Cyber Security Engineering V4Document21 pagesMastery in Hacking & Cyber Security Engineering V4Eriz RaiNo ratings yet
- Lesson10 ICT 0417Document25 pagesLesson10 ICT 0417thamalieariyarathnaNo ratings yet
- COMPBBE39312rObjrBh - OOP UNIT 2 InheritanceDocument46 pagesCOMPBBE39312rObjrBh - OOP UNIT 2 Inheritancenani kartikNo ratings yet
- University of Gondar: Information Storage and Retrieval SystemDocument29 pagesUniversity of Gondar: Information Storage and Retrieval SystemAisha mNo ratings yet
- Zedboard AudioDocument5 pagesZedboard AudioHải TrầnNo ratings yet
- Advanced Troubleshooting CCIE Routing & Switching v5.0Document24 pagesAdvanced Troubleshooting CCIE Routing & Switching v5.0Thomas PSNo ratings yet
- FEDCO MSD High Pressure Feed Pump Flyer PDFDocument4 pagesFEDCO MSD High Pressure Feed Pump Flyer PDFgustavo alfredo modesto castilloNo ratings yet
- Apollo Roadmap and Test Plan For GTDDocument1 pageApollo Roadmap and Test Plan For GTDCristian GonzalezNo ratings yet
- Assignment 1 Chapter 1: The Contemporary WorkplaceDocument4 pagesAssignment 1 Chapter 1: The Contemporary WorkplacePriyanka100% (2)
- Physics ExperimentDocument3 pagesPhysics ExperimentKush Gautam0% (1)
- Mooring Test ProcedureDocument2 pagesMooring Test ProcedureJEORJENo ratings yet
- Came Wiring PlanDocument6 pagesCame Wiring PlanquailpieNo ratings yet
- Pranava J K: Internship Technical SkillsDocument4 pagesPranava J K: Internship Technical SkillsPranavaNo ratings yet
- Accounting and Financial Close - Group Ledger IFRS (1GA - FR) : Test Script SAP S/4HANA Cloud - 06-10-20Document56 pagesAccounting and Financial Close - Group Ledger IFRS (1GA - FR) : Test Script SAP S/4HANA Cloud - 06-10-20cricriAF33830No ratings yet
- Yamaha RX V579 RX V479 Manual EnglishDocument123 pagesYamaha RX V579 RX V479 Manual EnglishMarkNo ratings yet
- Sas Course Content Porak TechnologiesDocument8 pagesSas Course Content Porak TechnologiesSAS Online TrainingNo ratings yet
- Stop Light Switch CircuitDocument3 pagesStop Light Switch Circuitcelestino tuliaoNo ratings yet
- Types of Computer SoftwareDocument23 pagesTypes of Computer SoftwareRachel FrancisNo ratings yet
- ESF: An Efficient Security Framework For Wireless Sensor NetworkDocument19 pagesESF: An Efficient Security Framework For Wireless Sensor NetworkDrMadhuravani PeddiNo ratings yet
Always ON
Always ON
Uploaded by
Nikola TasevskiOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Always ON
Always ON
Uploaded by
Nikola TasevskiCopyright:
Available Formats
Required :
DC/DNS servers
NPS (RADIUS) server
Certification Authority (CA) server
Remote Access (Routing/VPN) server
Infrastructure :
On a server configured with Active Directory Domain Services:
- Enable certificate autoenrollment in Group Policy for both computers and
users,
Before you enable certificate autoenrollment in Group Policy, you must configure a
server certificate template by using the Certificate Templates Microsoft Management
Console snap-in on a CA that is running AD CS:
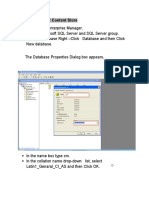
On CA1, in Server Manager, click Tools, and then click Certification Authority.
The Certification Authority Microsoft Management Console (MMC) opens.
In the MMC, double-click the CA name, right-click Certificate Templates, and
then click Manage.
The Certificate Templates console opens. All of the certificate templates are
displayed in the details pane.
In the details pane, click the RAS and IAS Server template.
Click the Action menu, and then click Duplicate Template. The
template Properties dialog box opens.
Click the Security tab.
On the Security tab, in Group or user names, click RAS and IAS servers.
In Permissions for RAS and IAS servers, under Allow, ensure that Enroll is
selected, and then select the Autoenroll check box. Click OK, and close the
Certificate Templates MMC.
In the Certification Authority MMC, click Certificate Templates. On
the Action menu, point to New, and then click Certificate Template to Issue.
The Enable Certificate Templates dialog box opens.
In Enable Certificate Templates, click the name of the certificate template that you just
configured, and then click OK. For example, if you did not change the default certificate
template name, click Copy of RAS and IAS Server, and then click OK.
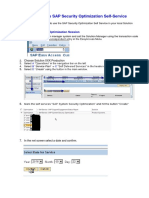
Configure server certificate auto-enrollment
On the computer where AD DS is installed, open Windows PowerShell®, type mmc, and
then press ENTER. The Microsoft Management Console opens.
On the File menu, click Add/Remove Snap-in. The Add or Remove Snap-ins dialog box
opens.
In Available snap-ins, scroll down to and double-click Group Policy Management Editor.
The Select Group Policy Object dialog box opens.
Important
Ensure that you select Group Policy Management Editor and not Group Policy
Management. If you select Group Policy Management, your configuration using these
instructions will fail and a server certificate will not be autoenrolled to your NPSs.
In Group Policy Object, click Browse. The Browse for a Group Policy Object dialog box
opens.
In Domains, OUs, and linked Group Policy Objects, click Default Domain Policy, and then
click OK.
Click Finish, and then click OK.
Double-click Default Domain Policy. In the console, expand the following path:
Computer Configuration, Policies, Windows Settings, Security Settings, and then Public
Key Policies.
Click Public Key Policies. In the details pane, double-click Certificate Services Client -
Auto-Enrollment. The Properties dialog box opens. Configure the following items, and
then click OK:
In Configuration Model, select Enabled.
Select the Renew expired certificates, update pending certificates, and remove revoked
certificates check box.
Select the Update certificates that use certificate templates check box.
Click OK.
-----------------------------------------------------------------------------------------------
Configure user certificate auto-enrollment
On the computer where AD DS is installed, open Windows PowerShell®, type mmc, and
then press ENTER. The Microsoft Management Console opens.
On the File menu, click Add/Remove Snap-in. The Add or Remove Snap-ins dialog box
opens.
In Available snap-ins, scroll down to and double-click Group Policy Management Editor.
The Select Group Policy Object dialog box opens.
Important
Ensure that you select Group Policy Management Editor and not Group Policy
Management. If you select Group Policy Management, your configuration using these
instructions will fail and a server certificate will not be autoenrolled to your NPSs.
In Group Policy Object, click Browse. The Browse for a Group Policy Object dialog box
opens.
In Domains, OUs, and linked Group Policy Objects, click Default Domain Policy, and then
click OK.
Click Finish, and then click OK.
Double-click Default Domain Policy. In the console, expand the following path: User
Configuration, Policies, Windows Settings, Security Settings.
Click Public Key Policies. In the details pane, double-click Certificate Services Client -
Auto-Enrollment. The Properties dialog box opens. Configure the following items, and
then click OK:
In Configuration Model, select Enabled.
Select the Renew expired certificates, update pending certificates, and remove revoked
certificates check box.
Select the Update certificates that use certificate templates check box.
Click OK.
- create the VPN Users Group, the VPN Servers Group, and the NPS Servers
Group, and add members to each group.
On an Active Directory Certificate Server CA: Create the User Authentication,
VPN Server Authentication, and NPS Server Authentication certificate templates.
On domain-joined Windows 10 clients: Enroll and validate user certificates.
You might also like
- Network and Security Lab Report: Lab 4.1: Installing Certificate ServicesDocument67 pagesNetwork and Security Lab Report: Lab 4.1: Installing Certificate Serviceslucifer thomasNo ratings yet
- Mendix Advanced Exam GuideDocument12 pagesMendix Advanced Exam GuideShishir KondaiNo ratings yet
- OldSiteOperators and ServiceSkidder610E (6101101-6102600) Service (6101101-6102500) 44477AENGDocument740 pagesOldSiteOperators and ServiceSkidder610E (6101101-6102600) Service (6101101-6102500) 44477AENGmarceloNo ratings yet
- BS en 00500Document66 pagesBS en 00500bugseNo ratings yet
- Puhy P850tkaDocument160 pagesPuhy P850tkaBrandon Antonio Peralta López100% (1)
- Measurand ManualDocument191 pagesMeasurand ManualfarquinNo ratings yet
- Enhanced Visual Intelligence at The Network Edge: Product BriefDocument2 pagesEnhanced Visual Intelligence at The Network Edge: Product BriefdanydwarNo ratings yet
- Module 09 - Deploying and Managing CertificatesDocument19 pagesModule 09 - Deploying and Managing CertificatesCong TuanNo ratings yet
- Lab: Configuring and Troubleshooting TS GatewayDocument10 pagesLab: Configuring and Troubleshooting TS Gatewaypablodg1980No ratings yet
- Deploying Web Server Certificate For Site SystemsDocument18 pagesDeploying Web Server Certificate For Site SystemsLaeeqSiddiquiNo ratings yet
- Module 11 - Implementing and Administering AD RMSDocument15 pagesModule 11 - Implementing and Administering AD RMSCong TuanNo ratings yet
- Windows Logon Using PKI TokensDocument24 pagesWindows Logon Using PKI Tokenspcouzens83No ratings yet
- Bài Thực Hành Giữa Kì Môn Học An Toàn Và An Ninh MạngDocument90 pagesBài Thực Hành Giữa Kì Môn Học An Toàn Và An Ninh MạngHoang AncientNo ratings yet
- Direct AccessDocument10 pagesDirect AccessneomorpheustrinitymatrixNo ratings yet
- Business ObjectsDocument62 pagesBusiness ObjectsponmudirajaNo ratings yet
- Microsoft Certificate Lifecycle Manager Quick Start GuideDocument8 pagesMicrosoft Certificate Lifecycle Manager Quick Start GuidevicogeoNo ratings yet
- Ad RMSDocument93 pagesAd RMSHungAnhNo ratings yet
- Business Objects XI AdministratorDocument62 pagesBusiness Objects XI Administratorachary_apNo ratings yet
- Configuring A Windows Server For RADIUSDocument7 pagesConfiguring A Windows Server For RADIUSaami145No ratings yet
- Module 08 - Deploying and Managing AD CSDocument12 pagesModule 08 - Deploying and Managing AD CSCong TuanNo ratings yet
- QMS User Guide - Managing Your CentreDocument15 pagesQMS User Guide - Managing Your CentreDon SheensNo ratings yet
- 802.1x Authentication With Cisco ACSDocument20 pages802.1x Authentication With Cisco ACSRiteesh Agrawal100% (1)
- Microsoft SC-900 LAB GUIDEDocument105 pagesMicrosoft SC-900 LAB GUIDEArdanNizmaAsadyNo ratings yet
- End PointDocument3 pagesEnd PointShibu VargheseNo ratings yet
- 11 SQL Config SP3DDocument39 pages11 SQL Config SP3DgoodmorningfredNo ratings yet
- Configuring Service Authentication and Account Policies: This Lab Contains The Following Exercises and ActivitiesDocument17 pagesConfiguring Service Authentication and Account Policies: This Lab Contains The Following Exercises and ActivitiesGuri DhillonNo ratings yet
- Generating and Installing Domain Controller CertificateDocument2 pagesGenerating and Installing Domain Controller CertificateGabriel Morales AngaritaNo ratings yet
- Troubleshooting Windows Small Business Server 2003Document44 pagesTroubleshooting Windows Small Business Server 2003shahegdeNo ratings yet
- BranchCache-Windows Server 2012R2 Step by StepDocument26 pagesBranchCache-Windows Server 2012R2 Step by StepEduar Moreno AlcasNo ratings yet
- VLSC Software Assurance GuideDocument11 pagesVLSC Software Assurance Guideangel ludeña marcaquispeNo ratings yet
- Lab - 1 Active Directory InstallationDocument32 pagesLab - 1 Active Directory InstallationsugapriyaNo ratings yet
- Exercise 1 Explore Partner Sales & Demo ResourcesDocument2 pagesExercise 1 Explore Partner Sales & Demo ResourcesEzequiasSilvaNo ratings yet
- Document of User ManagementDocument31 pagesDocument of User Managementsheikhaziz2949No ratings yet
- Module 4 Implementing VPN PDFDocument7 pagesModule 4 Implementing VPN PDFAfendey ArthurNo ratings yet
- ENSA Module 5 - Replacement LabDocument5 pagesENSA Module 5 - Replacement LabKarthik GanesanNo ratings yet
- AME Service Contract Approval 1456324.1Document10 pagesAME Service Contract Approval 1456324.1sreenivasNo ratings yet
- Data Migration To Sap S/4Hana: OpensapDocument27 pagesData Migration To Sap S/4Hana: OpensapRonit GhoseNo ratings yet
- Helpdesk Configuration TZ NewDocument10 pagesHelpdesk Configuration TZ Newdonald cyasNo ratings yet
- Proxy Authentication PortalDocument19 pagesProxy Authentication PortalEarl Ryan TorresNo ratings yet
- Zimbra To Office 365 Migration GuideDocument6 pagesZimbra To Office 365 Migration GuideEDSON ARIEL AJÚ GARCÍANo ratings yet
- Partner Membership Center To Partner Center TransitionDocument45 pagesPartner Membership Center To Partner Center TransitionGopinath GandhavadiNo ratings yet
- ScepDocument6 pagesScepAndres Barrios SaenzNo ratings yet
- Practice LabsDocument44 pagesPractice LabsMARIJOSENo ratings yet
- Troubleshooting Errors While Using DSCDocument11 pagesTroubleshooting Errors While Using DSChareshmsNo ratings yet
- Microsoft AD and Checkpoint NG AI Secure ClientDocument14 pagesMicrosoft AD and Checkpoint NG AI Secure Clientshark_99_05No ratings yet
- Create Report Net Content StoreDocument26 pagesCreate Report Net Content StoreJi RedNo ratings yet
- 2001215591-BanhTienKyAnh-Lab02B-Ex01-Configuring The Main Office Servers For BranchCacheDocument20 pages2001215591-BanhTienKyAnh-Lab02B-Ex01-Configuring The Main Office Servers For BranchCachekyanhbanhtien347No ratings yet
- S7 AdmincenerDocument14 pagesS7 AdmincenerДмирий МысовNo ratings yet
- Lab 12Document16 pagesLab 12Miguel MikeNo ratings yet
- Configuring Single Sign-On From The Vmware Identity Manager Service To FreshserviceDocument9 pagesConfiguring Single Sign-On From The Vmware Identity Manager Service To FreshservicekarthikNo ratings yet
- Module 03 - Advanced AD DS Infrastructure ManagementDocument13 pagesModule 03 - Advanced AD DS Infrastructure ManagementCong TuanNo ratings yet
- How To Guide For Solution Manager Security Optimization Self Service (SOS) REPORTINGDocument8 pagesHow To Guide For Solution Manager Security Optimization Self Service (SOS) REPORTINGLeon BratzNo ratings yet
- SCCM InstallationDocument76 pagesSCCM InstallationrkanfiNo ratings yet
- SAP Master Data Governance, Cloud Edition Trial Getting Started GuideDocument19 pagesSAP Master Data Governance, Cloud Edition Trial Getting Started GuidejeefmNo ratings yet
- Lab Answer Key - Module 8 - Implementing and Administering AD FSDocument29 pagesLab Answer Key - Module 8 - Implementing and Administering AD FSffNo ratings yet
- Installing Governance Minder InstructionsDocument48 pagesInstalling Governance Minder Instructionsyasas.biz100% (1)
- Step-By-Step Guide To Renewing Your Cisco Select CertificationDocument7 pagesStep-By-Step Guide To Renewing Your Cisco Select CertificationadkadimNo ratings yet
- SVMX101 ILT Workbook - CORE 22.1 LightningDocument88 pagesSVMX101 ILT Workbook - CORE 22.1 LightningRygel OrionisNo ratings yet
- CUCM 9.x+ and ELM - License Upgrade and InstallationDocument13 pagesCUCM 9.x+ and ELM - License Upgrade and InstallationJuan GarciaNo ratings yet
- The CMTrace OverviewDocument3 pagesThe CMTrace Overviewjainamit0622No ratings yet
- CA Cloud Service Management A Complete Guide - 2020 EditionFrom EverandCA Cloud Service Management A Complete Guide - 2020 EditionNo ratings yet
- SCCM software change and configuration management Standard RequirementsFrom EverandSCCM software change and configuration management Standard RequirementsNo ratings yet
- ELT - 280 - 1 Offshore Generation Cable ConnectionsDocument3 pagesELT - 280 - 1 Offshore Generation Cable ConnectionsNam Hoai LeNo ratings yet
- FPGA Programming Technology and Interconnect ArchitectureDocument32 pagesFPGA Programming Technology and Interconnect ArchitectureSrikar BabuNo ratings yet
- Full Introduction About Xilinx FPGA and Its ArchitectureDocument19 pagesFull Introduction About Xilinx FPGA and Its ArchitecturejackNo ratings yet
- Control of Inverter-Based Distribution Generation Used To Provide Premium Power QualityDocument7 pagesControl of Inverter-Based Distribution Generation Used To Provide Premium Power QualityebrahimNo ratings yet
- WP Flow Simulation Gas MixingDocument5 pagesWP Flow Simulation Gas MixingpengkritikNo ratings yet
- Transducers CatalogueDocument56 pagesTransducers CatalogueRavindarReddyD0% (1)
- Mastery in Hacking & Cyber Security Engineering V4Document21 pagesMastery in Hacking & Cyber Security Engineering V4Eriz RaiNo ratings yet
- Lesson10 ICT 0417Document25 pagesLesson10 ICT 0417thamalieariyarathnaNo ratings yet
- COMPBBE39312rObjrBh - OOP UNIT 2 InheritanceDocument46 pagesCOMPBBE39312rObjrBh - OOP UNIT 2 Inheritancenani kartikNo ratings yet
- University of Gondar: Information Storage and Retrieval SystemDocument29 pagesUniversity of Gondar: Information Storage and Retrieval SystemAisha mNo ratings yet
- Zedboard AudioDocument5 pagesZedboard AudioHải TrầnNo ratings yet
- Advanced Troubleshooting CCIE Routing & Switching v5.0Document24 pagesAdvanced Troubleshooting CCIE Routing & Switching v5.0Thomas PSNo ratings yet
- FEDCO MSD High Pressure Feed Pump Flyer PDFDocument4 pagesFEDCO MSD High Pressure Feed Pump Flyer PDFgustavo alfredo modesto castilloNo ratings yet
- Apollo Roadmap and Test Plan For GTDDocument1 pageApollo Roadmap and Test Plan For GTDCristian GonzalezNo ratings yet
- Assignment 1 Chapter 1: The Contemporary WorkplaceDocument4 pagesAssignment 1 Chapter 1: The Contemporary WorkplacePriyanka100% (2)
- Physics ExperimentDocument3 pagesPhysics ExperimentKush Gautam0% (1)
- Mooring Test ProcedureDocument2 pagesMooring Test ProcedureJEORJENo ratings yet
- Came Wiring PlanDocument6 pagesCame Wiring PlanquailpieNo ratings yet
- Pranava J K: Internship Technical SkillsDocument4 pagesPranava J K: Internship Technical SkillsPranavaNo ratings yet
- Accounting and Financial Close - Group Ledger IFRS (1GA - FR) : Test Script SAP S/4HANA Cloud - 06-10-20Document56 pagesAccounting and Financial Close - Group Ledger IFRS (1GA - FR) : Test Script SAP S/4HANA Cloud - 06-10-20cricriAF33830No ratings yet
- Yamaha RX V579 RX V479 Manual EnglishDocument123 pagesYamaha RX V579 RX V479 Manual EnglishMarkNo ratings yet
- Sas Course Content Porak TechnologiesDocument8 pagesSas Course Content Porak TechnologiesSAS Online TrainingNo ratings yet
- Stop Light Switch CircuitDocument3 pagesStop Light Switch Circuitcelestino tuliaoNo ratings yet
- Types of Computer SoftwareDocument23 pagesTypes of Computer SoftwareRachel FrancisNo ratings yet
- ESF: An Efficient Security Framework For Wireless Sensor NetworkDocument19 pagesESF: An Efficient Security Framework For Wireless Sensor NetworkDrMadhuravani PeddiNo ratings yet