Professional Documents
Culture Documents
Computer Science Mock
Computer Science Mock
Uploaded by
Muhtasim Ibne kamalOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Computer Science Mock
Computer Science Mock
Uploaded by
Muhtasim Ibne kamalCopyright:
Available Formats
Computer Science (H046, H446)
Y13 Jan Mock
CS teacher
Please note that you may see slight differences between
this paper and the original.
Duration: 150 mins
Candidates answer on the Question paper.
OCR supplied materials:
Additional resources may be supplied with this paper.
Other materials required:
• Pencil
• Ruler (cm/mm)
Candidate Candidate
forename surname
Centre number Candidate number
INSTRUCTIONS TO CANDIDATES
• Write your name, centre number and candidate number in the boxes above. Please write clearly and in capital letters.
• Use black ink. HB pencil may be used for graphs and diagrams only.
• Answer all the questions, unless your teacher tells you otherwise.
• Read each question carefully. Make sure you know what you have to do before starting your answer.
• Where space is provided below the question, please write your answer there.
• You may use additional paper, or a specific Answer sheet if one is provided, but you must clearly show your candidate
number, centre number and question number(s).
INFORMATION FOR CANDIDATES
• The quality of written communication is assessed in questions marked with either a pencil or an asterisk. In History and
Geography a Quality of extended response question is marked with an asterisk, while a pencil is used for questions in
which Spelling, punctuation and grammar and the use of specialist terminology is assessed.
• The number of marks is given in brackets [ ] at the end of each question or part question.
• The total number of marks for this paper is 147.
• The total number of marks may take into account some 'either/or' question choices.
© OCR 2023. You may photocopy this page. 1 of 42 Created in ExamBuilder
1(a) Intensive Care Units in hospitals are for patients in need of round the clock monitoring and support.
Computerised systems can be used to monitor patients’ vital signs (temperature, heart rate, blood pressure and
breathing). They can then alert medical professionals to any significant changes.
These systems usually run on an embedded, real-time, operating system.
(i) State what is meant by the term real-time.
[1]
(ii) Explain why a real-time operating system would be suitable for Intensive Care Units.
[2]
© OCR 2023. You may photocopy this page. 2 of 42 Created in ExamBuilder
(b) The hospital would like to update the system so that it automatically delivers doses of certain drugs to patients
based on the readings taken rather than leave delivery to medical staff.
Discuss the ethical benefits and drawbacks of this approach, explaining whether you would recommend making
this update.
[9]
© OCR 2023. You may photocopy this page. 3 of 42 Created in ExamBuilder
2(a) The following assembly code in Fig. 1 is written for the Little Man Computer instruction set.
State the output when the inputs are 13 followed by 5.
[1]
(b) In the line:
(i) State what opcode SUB does.
[1]
(ii) Name the register in which the result of this line is stored.
[1]
© OCR 2023. You may photocopy this page. 4 of 42 Created in ExamBuilder
(c)
(i) State what the program in Fig. 1 does.
[1]
(ii) Using pseudocode write a program for a procedural language that takes in two inputs and gives the same
output as the program in Fig. 1.
[2]
3 A software company decides to release a duplicate file finder which it has named “De-Duplicator”. Duplicate files
are files that are exactly the same (bit for bit identical). Space is often wasted on computers by having multiple
versions of the same file. Duplicate file finders are programs that find and identify duplicate files on a hard drive
so that they can be removed.
A duplicate file finder is an example of a utility. Describe what is meant by a utility.
[2]
4(a) State which bitwise manipulation on 00010101 would have achieved the same result as the calculation on part
(a).
[1]
(b) Two equal (unsigned) integers, shown below, are added together. Calculate the result, showing your working.
[2]
© OCR 2023. You may photocopy this page. 5 of 42 Created in ExamBuilder
(c) Describe why two’s complement may be preferable to sign and magnitude.
[2]
5 A gaming company decides to release a new video games console. The console will use a modified version of
an operating system called Linux.
Linux is open-source.
Explain how Linux being open-source would benefit the games company.
[2]
6 A company releases a utility called Utility software. The utility creates a virtual storage drive from an area of the
computer's RAM.
The utility periodically copies what is in the RAM drive to secondary storage, such as a hard disk. Explain why
this is necessary.
[2]
© OCR 2023. You may photocopy this page. 6 of 42 Created in ExamBuilder
7 A computer represents floating point binary numbers using a 6-bit mantissa and 4-bit exponent, both using two's
complement.
Add the following three numbers together and give the answer in the format described. You must show your
working.
[6]
© OCR 2023. You may photocopy this page. 7 of 42 Created in ExamBuilder
8 The following is a program written using the Little Man Computer instruction set.
Explain the buses and registers used when the line SUB one is executed.
[5]
© OCR 2023. You may photocopy this page. 8 of 42 Created in ExamBuilder
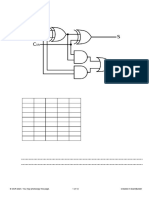
9(a) A set of logic gates are connected as below.
(i) Complete the Truth Table below:
A B Cin S Cout
1 1 1
1 1 0
1 0 1
1 0 0
0 1 1
0 1 0
0 0 1
0 0 0
[4]
(ii) Explain what the circuit does. You should refer to A, B, Cin, S and Cout in your answer.
© OCR 2023. You may photocopy this page. 9 of 42 Created in ExamBuilder
[4]
(b)
(i) Write a Boolean expression equivalent to S.
[1]
(ii) Write a Boolean expression equivalent to Cout.
[2]
10(a) A database stores information about songs on a music streaming service.
One of the tables called Song has the fields.
Explain why none of these fields would be suitable as a primary key.
[2]
© OCR 2023. You may photocopy this page. 10 of 42 Created in ExamBuilder
(b) Give one advantage and one disadvantage of indexing the field Artist.
Advantage
Disadvantage
[2]
(c) Users can build up playlists of their songs. Another table is created called Playlist.
Explain why a third table which we shall call PlayListEntry is needed. You should use an ER diagram to
illustrate your answer.
[4]
© OCR 2023. You may photocopy this page. 11 of 42 Created in ExamBuilder
(d) A band called RandomBits removes their permission for their songs to be streamed.
The company removes all the songs belonging to RandomBits from their service.
(i) Identify the law with which the company are complying.
[1]
(ii) Write an SQL statement that will remove all songs by RandomBits from the table Song.
[2]
(iii) When the songs have been removed, explain what must happen to the table PlayListEntry if the
database is to retain its referential integrity. (You are not expected to write the SQL to do this).
[1]
© OCR 2023. You may photocopy this page. 12 of 42 Created in ExamBuilder
11 A software development company is building an operating system for a mobile phone that is in the process of
being designed.
One of the developers is responsible for writing the code for what happens when the CPU receives an interrupt.
Outline what the code must do.
[6]
12 TCP/IP uses packet switching.
Explain what is meant by packet switching.
[4]
© OCR 2023. You may photocopy this page. 13 of 42 Created in ExamBuilder
13 The computers in a car showroom are connected in a network with all data being held in a central server. The
computers are used by the salesmen, but can also be used by customers to watch videos of the cars that are on
offer.
What is meant by a protocol?
[2]
14(a)
(i) Compare a Complex Instruction Set Computer (CISC) architecture with a Reduced Instruction Set Computer
(RISC) architecture.
[4]
(ii) Explain one advantage, other than cost, of RISC compared with CISC.
[2]
© OCR 2023. You may photocopy this page. 14 of 42 Created in ExamBuilder
(b)
(i) Give the name of the computer architecture that uses the fetch-execute cycle with a single control unit.
[1]
(ii) Registers used during the fetch-execute cycle include the current instruction register (CIR), memory address
register (MAR), memory data register (MDR) and program counter (PC).
Place ticks in the table to show which statements are correct during processing.
CIR MDR PC
Holds a binary value
Always holds only an address
May change more than once during a single cycle
May pass a value to the MAR
[4]
© OCR 2023. You may photocopy this page. 15 of 42 Created in ExamBuilder
15 The office workers of a large company each use a standalone computer.
The company is considering networking the machines.
(i) Describe what is meant by a LAN.
[2]
(ii) State two advantages of having a LAN instead of a set of stand-alone machines.
[2]
© OCR 2023. You may photocopy this page. 16 of 42 Created in ExamBuilder
16 A supermarket uses a stock control system.
Details of products are stored on a stock database.
The name of a product is stored using characters from the computer's character set.
(i) Explain what is meant by the character set of a computer.
[2]
(ii) Explain how codes are used to represent a character set.
[3]
© OCR 2023. You may photocopy this page. 17 of 42 Created in ExamBuilder
17 Laser Tag is a game where teams of players move round an arena shooting each other with infrared guns.
Players wear sensors that keep track of how many times they have been hit by the laser. This is known as being
‘tagged’.
Below is an extract from a Laser Tag company’s website:
The web page is written in HTML.
Write some HTML code which could have been used to produce this extract. You can assume it is already inside
<body> tags.
[4]
© OCR 2023. You may photocopy this page. 18 of 42 Created in ExamBuilder
18 Operating systems can use many different scheduling algorithms.
(i) State three different scheduling algorithms.
[3]
(ii) Explain the purpose of scheduling.
[3]
19 See And Believe is a company that specialises in computer-generated imagery (CGI) for films.
Producing CGI requires lots of processing power and so the company has a large number of high-performance
computers.
Explain why See And Believe would use a distributed operating system.
[3]
© OCR 2023. You may photocopy this page. 19 of 42 Created in ExamBuilder
20 A Little Man Computer (LMC) assembly language program is stored in memory as shown in Fig. 3.1.
In this variant of LMC the symbols & and # are used to denote different modes of addressing.
Explain how pipelining would help a CPU execute the code in Fig. 3.1 more quickly.
[3]
© OCR 2023. You may photocopy this page. 20 of 42 Created in ExamBuilder
21(a) Every bank account has an account number and sort code. The sort code identifies the bank branch (location of
the bank) with which the account is held and the account number uniquely identifies the bank account. An extract
from a bank's database table is shown in Fig. 5.1.
State why the table in Fig. 5.1 is not in Third Normal Form.
[1]
(b) Explain how the database could be put into Third Normal Form.
[3]
22(a) The XOR operator can be used to encrypt data.
Show the effect of applying XOR on Text and Key, by completing the last row of the table below.
[2]
© OCR 2023. You may photocopy this page. 21 of 42 Created in ExamBuilder
(b) Show the effect of applying XOR on your answer to part (a) and Key, by completing the first and last rows of the
table below.
[2]
(c) Explain whether the type of encryption described above is symmetric or asymmetric.
[2]
(d) Explain why asymmetric encryption is more suited to transactions over the internet than symmetric encryption.
[4]
© OCR 2023. You may photocopy this page. 22 of 42 Created in ExamBuilder
23(a) Explain what the code in Fig. 8.1 does.
[5]
(b) In certain scenarios the user's IP address is logged in a database.
(i) Describe what is meant by an IP Address.
[2]
(ii) Explain why the programmers have chosen to store the user's IP address.
[2]
© OCR 2023. You may photocopy this page. 23 of 42 Created in ExamBuilder
(c) An extract from the database is shown below:
(i) The username admin is entered into the form.
State what the value of statement would be after line 03 of the code in Fig. 8 .1 is run.
[1]
(ii) State what the value of hashInDB would be after line 04 of the code in Fig. 8.1 is run.
[1]
© OCR 2023. You may photocopy this page. 24 of 42 Created in ExamBuilder
(d) In SQL the character ; denotes the next statement and the characters –– denote a comment.
The username DenverJ34'; DROP TABLE users; –– is entered into the form.
(i) State what the value of statement would be after line 03 is run.
[1]
(ii) Describe what happens when line 04 is run.
[2]
(iii) State the name of a law the user has broken by entering the username
DenverJ34'; DROP TABLE users; --
[1]
© OCR 2023. You may photocopy this page. 25 of 42 Created in ExamBuilder
24(a)
State the Boolean expression represented by the Karnaugh map in Fig. 9.1, in its smallest form.
[4]
© OCR 2023. You may photocopy this page. 26 of 42 Created in ExamBuilder
(b) State the simplified versions of the following Boolean expressions:
(i) ¬ ¬A
[1]
(ii) (¬A Λ ¬B)
[1]
(iii) ¬(¬A Λ ¬B)
[1]
END OF QUESTION PAPER
© OCR 2023. You may photocopy this page. 27 of 42 Created in ExamBuilder
Mark Scheme
Question Answer/Indicative content Marks Guidance
1 a i The system gives a response within a 1 For 1 mark.
guaranteed time frame (1).
ii If something happens to a patient, a 2 Up to 2 marks for a valid explanation that
response must be immediate (1). demonstrates application of knowledge
Other types of system may have and understanding to given context.
delays in response (1).
This could result in a patient not
receiving treatment in time (1).
© OCR 2023. You may photocopy this page. 28 of 42 Created in ExamBuilder
Mark Scheme
Question Answer/Indicative content Marks Guidance
b *Mark Band 3–High Level 9 If only benefits or drawbacks considered -
(7–9 marks) MAX 5 marks.
The candidate demonstrates a thorough AO1: Knowledge and Understanding
knowledge and understanding of a wide The following is indicative of possible
range of ethical benefits and drawbacks; factors / evidence that candidates may
the material is generally accurate and refer to but is not prescriptive or
detailed. exhaustive:
The candidate is able to apply their
knowledge and understanding directly and Benefits:
consistently to the context provided.
Evidence / examples will be explicitly Medical staff are often overworked and
relevant to the explanation. tired and may be liable to make
The candidate is able to weigh up both mistake whereas a computer will
sides of the argument which results in a always act in a deterministic manner.
supported and realistic judgment as to The computer can respond instantly to
whether the update should be made. patients’ needs whereas there may be
There is a well-developed line of reasoning a delay in medical staff getting to them.
which is clear and logically structured. The The round the clock monitoring will
information presented is relevant and become more effective by using a
substantiated. computerised monitoring system as it
will allow staff to engage with patients
Mark Band 2-Mid Level at a specific time providing them
(4–6 marks) support.
The candidate demonstrates reasonable Staff shortages will not create issues
knowledge and understanding of a range for patients.
of ethical benefits and drawbacks; the
material is generally accurate but at times Drawbacks
underdeveloped.
The candidate is able to apply their A computer system may not have the
knowledge and understanding directly to programming to take into account all
the context provided although one or two the relevant factors whereas trained
opportunities are missed. medical staff will.
Evidence / examples are for the most part If there is a bug in the computer’s
implicitly relevant to the explanation. programming and if staff input any
The candidate makes a reasonable values incorrectly then patients could
attempt to come to a conclusion showing die due to incorrect diagnosis.
some recognition of influencing factors that As medical knowledge changes the
would determine whether an update should system may need reprogramming
be made. which can take longer than retraining
There is a line of reasoning presented with staff – also accept the reverse
some structure. The information presented argument that updates can be rolled
is in the most part relevant and supported out quicker than retraining staff.
by some evidence. Patients can have dialogue with
medical staff giving information that
Mark Band 1-Low Level may not be attainable via sensors.
(1–3 marks)
The candidate demonstrates a basic AO2.1: Application
knowledge of ethical benefits and The selected knowledge / examples should
drawbacks with limited understanding be directly related to the specific question.
© OCR 2023. You may photocopy this page. 29 of 42 Created in ExamBuilder
Mark Scheme
Question Answer/Indicative content Marks Guidance
shown; the material is basic and contains The following is indicative of possible
some inaccuracies. The candidate makes factors / evidence that candidates may
a limited attempt to apply acquired refer to but is not prescriptive or
knowledge and understanding to the exhaustive:
context provided. The candidate provides
nothing more than an unsupported
assertion. Discussion on how the computerised
The information is basic and round the clock monitoring system
communicated in an unstructured way. The would impact upon the staff workload
information is supported by limited of Intensive Care Units.
evidence and the relationship to the Discussion on the data protection act
evidence may not be clear. and the growth in using computerised
monitoring and other computerised
0 marks systems.
No attempt to answer the question or
response is not worthy of credit. AO3.3: Evaluation
The following is indicative of possible
factors / evidence that candidates may
refer to but is not prescriptive or
exhaustive:
Having considered the different sides to
the argument candidates will need to reach
a supported judgment based on the
evidence included in their response. They
will need to evaluate the use of
computerised monitoring system and the
ethical and legal issues involved around it.
e.g.
What can be the risks of using
computerised monitoring systems for
patients, What if the wrong data was
entered by staff?
How does computerised monitoring
system enable effective care for
patients?
Why would you recommend updating
computerised monitoring system
against the current computerised
system already in place?
Total 12
© OCR 2023. You may photocopy this page. 30 of 42 Created in ExamBuilder
Mark Scheme
Question Answer/Indicative content Marks Guidance
2 a It outputs 3 (1). 1 For 1 mark.
b i Performs subtraction (1). 1 For 1 mark.
ii The accumulator (1). 1 For 1 mark.
c i Calculates the remainder of two 1 For 1 mark.
numbers when the second is divided
by the first (1). Accept finds modulo / modulus.
ii Code takes in two values and provides 2 For 2 marks.
an output (1).
The output is the modulus of the two Allow follow through for second mark if
inputs (1). output matches answer to (i).
Accept MOD, % or any existing alternative.
Accept if candidate has calculated modulus
using alternative method (e.g. using a
loop).
Example:
Total 6
3 A utility performs a specific task (1) and 2 Up to 2 marks for a valid description.
is usually related to the upkeep of the
system (1).
Examples of a utility include a virus
checker (1) / disk defragmenter (1).
Total 2
4 a Shift left (1). 1 For 1 mark.
b 00101010 2 For 2 marks – award 1 mark for correct
111 answer and 1 mark for carrying bits.
c It is not easily possible to carry out 2 Up to 2 marks for a valid description.
calculations using sign and magnitude
(1) whereas they will work with two’s
complement (1).
Total 5
© OCR 2023. You may photocopy this page. 31 of 42 Created in ExamBuilder
Mark Scheme
Question Answer/Indicative content Marks Guidance
5 This means that a lot of the core 2 Up to 2 marks for a valid explanation.
functionality they need is already
available (1) so the company just has
to make amendments / additions
specific to their system (1) saving time
and money (1).
Total 2
6 – RAM is volatile meaning it loses 2
contents when power is off …
– … so must be copied to secondary
storage in case of unexpected power
failure
(1 per –,)
Total 2
7 6 If candidate fails to discard the overflowing
1 they can still get marks 1–4.
(1 per –)
Total 6
8 – The address of is stored in the 5 Accept MBR instead of MDR
MAR
– This value is sent along the address
bus AND the fetch signal is sent on the
control bus.
– The contents of are sent from
memory to the processer on the data bus
and stored in the MDR
– The contents of the MDR and ACC are
sent to the ALU
– The result is stored back in the ACC
(1 per –)
Total 5
© OCR 2023. You may photocopy this page. 32 of 42 Created in ExamBuilder
Mark Scheme
Question Answer/Indicative content Marks Guidance
9 a i 4
1 Mark for rows 1 and 2
1 Mark for rows 3 and 4
1 Mark for rows 5 and 6
1 Mark for rows 7 and 8
ii – Circuit adds two bits (and a carry bit) 4
together / is an adder.
– A B and Cin are added together
– The result is given in S
– And a carry bit in Cout
(1 per –)
b i 1 Accept XOR instead of ∨
Accept instead of ∨
ii 2 Accept XOR instead of ∨
Accept instead of ∨
One mark for ((A∨B) ∧ Cin)
Accept AND instead of ∧
One mark for ∨ (A ∧ B)
Accept OR instead of ∨
Accept + instead of ∨
Total 11
© OCR 2023. You may photocopy this page. 33 of 42 Created in ExamBuilder
Mark Scheme
Question Answer/Indicative content Marks Guidance
10 a – A primary key must have a unique 2
value for every record
– The values for all these fields could
repeat.
(1 per –)
b – Advantage: Searches of Artist can be 2
performed more quickly.
– Disadvantage: The index takes up
extra space in the database.
(1 per –)
c – would have a 4
many to many relationship
– This is not allowed
– Adding a table between them resolves
this
– Diagram to illustrate this.
(1 per –)
d i Copyright, Design and Patents Act 1 Accept Copyright Act / Law
ii 2
(1
mark per –, max 2)
iii All entries in which 1
contain songs by RandomBits must be
removed.
Total 12
© OCR 2023. You may photocopy this page. 34 of 42 Created in ExamBuilder
Mark Scheme
Question Answer/Indicative content Marks Guidance
11 – Complete the current FDE Cycle 6
– Check the priority of the incoming
interrupt.
– If its of a higher priority than the current
task.
– Contents of registers stored in
memory..
– … in a stack.
– The relevant interrupt service routine is
loaded …
– ..by loading the relevant value into the
program counter.
– When the ISR is complete the previous
state is popped from the stack
– And are loaded back into the registers.
(1 per –, max 6)
Total 6
12 Data is split into chunks called packets 4 Up to 2 marks for demonstrating
(1 – AO1.1) which have labels (1 – knowledge (AO1.1).
AO1.1) including address being sent to Up to 2 marks for demonstrating
(1 – AO1.1) and order (1 – AO1.1). understanding (AO1.2).
Each packet is sent on the most
convenient / avoidable route (1 –
AO1.2) meaning they may arrive in a
different order to which they were sent
(1 – AO1.2). Once packets arrive at
receiver they are reordered (1 –
AO1.2).
Total 4
13 A set of rules… 2 Must be rules – plural 1st bullet point
–…to govern data transmission (between
devices) Examiner's Comments
This question was well answered with most
candidates gaining full credit.
Total 2
© OCR 2023. You may photocopy this page. 35 of 42 Created in ExamBuilder
Mark Scheme
Question Answer/Indicative content Marks Guidance
14 a i CISC: 4 Max 3 marks for either CISC or RISC, total
Each instruction may take multiple cycles max 4
Single register set
Instructions have variable format Examiner's Comments
Many instructions are available
Many addressing modes are available There were a wide variety of answers to
Complicated processor design this question, ranging from the very
Integrated circuit is expensive accurate to the very vague. A significant
RISC: number of candidates said that RISC is
An instruction performs a simple task used in mobile phones, if the question had
Limited number of instructions available asked for an example this would probably
Complex tasks can only be performed by have been a good one. Those that missed
combining multiple instructions marks here generally talked about the
Simple processor design programming and its relative difficulty on
either type of processor rather than the
processor itself.
ii Programs run faster… 2
…due to simpler instructions Examiner's Comments
Most candidates got the first mark, the
more able candidates managed to get the
second, again, here the most common
erroneous answer was about the
merits/drawbacks of programming.
b i Von Neumann 1 cao
Examiner's Comments
A very well answered question, with only
one possible answer.
ii 4 One mark per correct row
Examiner's Comments
Again generally well answered, although a
small percentage of candidates were
seemingly unaware that you could put
more than one tick per row. Doing practice
questions should have got them used to
this, candidates should be reminded to
read question stems thoroughly.
Total 11
© OCR 2023. You may photocopy this page. 36 of 42 Created in ExamBuilder
Mark Scheme
Question Answer/Indicative content Marks Guidance
15 i Local Area network 2
(Over) a small geographical area
Use of hard-wiring / wireless
communication
ii Communication between machines / 2 Not: Shared processing power
workers
Any machine can be used Examiner's Comments
Easier to maintain / add / delete
software / files Most candidates scored well in this
Sharing of peripheral devices / question. There were some interesting
software / data variations on the accepted version of ‘local
Monitoring of workers area network’. There were those who
Simplifies backup procedures thought that the ‘a’ stood for ‘access’. This
sort of response was fine because the
candidate had the correct concept and was
able to go on and earn the marks, whereas
candidates who stated that the ‘l’ stood for
‘large’ would then go on to describe the
characteristics of a WAN and consequently
did not gain marks.
Total 4
16 i Normally equates to the symbols on a 2 Not: Stored on a computer
keyboard / digits / letters…
…that can be represented / interpreted
/ understood by a computer
May include control characters
ii Each symbol has a (binary) code / 3
number… Examiner's Comments
…which is unique.
Number of bits used for one character Many candidates adopted a scatter gun
= 1 byte approach to this pair of questions, inserting
Example code: ASCII / Unicode… the facts that they knew about character
…uses 8 bits /16 bits per character sets seemingly at random between the two
Use of more bits for extended parts.
character set Despite this most scored well here and
some candidates gave clear and well-
presented responses to both parts.
Total 5
© OCR 2023. You may photocopy this page. 37 of 42 Created in ExamBuilder
Mark Scheme
Question Answer/Indicative content Marks Guidance
17 Appropriate tags to make Reasons to 4 Up to 4 marks - 1 mark for each correct
Choose Us subheading (e.g. h1, h2, step in process.
h3). Accept b or strong if accompanied
by attribute to make increase font size Example:
(1).
Laser Tag italicised (e.g. i or em) (1).
ul used for bulleted list (1).
li to mark out elements of list (1).
Accept answers where same effect is
achieved using style attribute.
Total 4
18 i First Come First Served 3
Round Robin
Shortest Job First Accept any other processor scheduling
Shortest Remaining Time algorithm.
Multilevel Feedback Queues
Examiner's Comments
Generally well answered but there were a
small number of candidates who seem to
have got mixed up with stack and queue
operations.
ii To make the most efficient use of the 3
processor / resources Examiner's Comments
Be fair to all users / applications
Provide a reasonable response time A number of candidates seemed to have
Prevent processes from failing to run / taken an earlier answer to a similar
Process starvation / Deadlock question slightly out of context and implied
that the processor made sure that it got as
many users as possible. “Maximise the
number of users” on its own was not
considered enough for a mark.
Total 6
© OCR 2023. You may photocopy this page. 38 of 42 Created in ExamBuilder
Mark Scheme
Question Answer/Indicative content Marks Guidance
19 Any 2 from: 3
Examiner's Comments
Allow multiple computers / resources…
(AO1.1) Few candidates gained full marks on this
To be treated as one / work on the question. Many candidates described
same problem (AO1.1) general characteristics of a network
operating system rather than a distributed
1 from: operating system. Fewer appropriately
related their explanation to the scenario.
Meaning all the computers can work on
producing the same special effect.
(AO2.1)
Total 3
20 Pipelining would allow one instruction to be 3 Accept any valid example from the given
fetched as the previous one is being code.
decoded and the one before that is being
executed.(1)
For example OUT could be fetched (1). As
there are no jump/branch instructions it
pipelines well (as there is no need to flush
the pipeline). (1)
Total 3
21 a Branch name depends on Sort Code (i.e. 1
there is a transitive relationship).
b Create another table for Branches which 3
should include sort-code and branch name.
(1) Make sort code the primary key of the
BRANCH table/ Add a primary key to
BRANCH. (1) Remove Branch name from
Customers, leave sortcode as primary key/
Remove sort-code and branch name from
customers and add the primary key values
from BRANCS as the foreign key (1)
ALTERNATIVE ANSWER (ER-DIAGRAM)
Two tables CUSTOMER and BRANCH (or
similar names) (1)
Link from CUSTOMER to BRANCHES is
Many (1) to One (1)
Total 4
© OCR 2023. You may photocopy this page. 39 of 42 Created in ExamBuilder
Mark Scheme
Question Answer/Indicative content Marks Guidance
22 a 2
One byte correct (1) all three bytes
correct. (1)
b 2 Allow FT if (a) is incorrect but bottom row
must match XOR with top row and key.
One byte correct (1) all three bytes
correct. (1)
c Symmetric (1) …. as the same key is used 2 Allow FT for asymmetric if (b) indicates
to decrypt it as encrypt it (1) asymmetric encryption used
d Any four from: 4
Symmetric encryption would require both
parties to have copy of the key (1) this
couldn’t be transmitted over the internet or
an eavesdropper monitoring the message
may see it (1) Asymmetric gets round this
requirement as there are two different keys
(1) One key encrypts the data (1) which
can be publically distributed (1) and a
different key to decrypt it (1) which is kept
private (1)
Total 10
© OCR 2023. You may photocopy this page. 40 of 42 Created in ExamBuilder
Mark Scheme
Question Answer/Indicative content Marks Guidance
23 a Any five from: 5
Takes the username and password from
the form (1)
Uses the username to create an SQL
statement (1) to get the passwordHash
belonging to the given username (1) Runs
the SQL Statement (1) hashes the given
password and compares it to the retrieved
hash (1)
If they match it generates a success
webpage, otherwise it records the user’s IP
address. (1)
b i Any two from: 2
A numerical address made of 4 numbers
each between 0 and 255 / 32 hexadecimal
digits (1)
That uniquely identifies a device on a
network. (1)
It is a logical identifier (i.e. can change on a
physical device) (1)
ii IP address can help identify a user… (1) 2
…so company can potentially track users
attempting to gain unauthorised access (1)
c i SELECT passwordHash FROM users 1
WHERE name = ‘admin’
ii 0e5a511 1
d i SELECT passwordHash FROM users 1
WHERE name = ‘DenverJ34’; DROP
TABLE users; ’ --
ii Gets passwordHash for username 2
DenverJ34 (1)
then deletes the table called users. (1)
iii Computer Misuse Act 1
Total 15
© OCR 2023. You may photocopy this page. 41 of 42 Created in ExamBuilder
Mark Scheme
Question Answer/Indicative content Marks Guidance
24 a (¬A ∧¬D) ∨(A ∧B ∧C) ∨(¬B ∧¬C ∧¬D) 4
One mark for each bracketed section.
One mark for them being joined with ORs
b i A 1
ii ¬(A∨ B) 1
iii A∨B 1
Total 7
© OCR 2023. You may photocopy this page. 42 of 42 Created in ExamBuilder
Powered by TCPDF (www.tcpdf.org)
You might also like
- Amm Level 2 Cog MP Edited FinalDocument19 pagesAmm Level 2 Cog MP Edited FinalYankho NalimaNo ratings yet
- Computer Science NotesDocument36 pagesComputer Science NotesVinit HarishNo ratings yet
- KS3 Presentation - 24 Introduction To NetworksDocument48 pagesKS3 Presentation - 24 Introduction To Networkshunia abbass100% (1)
- Cambridge IGCSE (9-1) : Computer Science 0984/22Document2 pagesCambridge IGCSE (9-1) : Computer Science 0984/22mohammed mahdyNo ratings yet
- 02 - Fundamentals of Ethernet LANsDocument36 pages02 - Fundamentals of Ethernet LANsAdetayo OnanugaNo ratings yet
- Java and Multi ThreadingDocument44 pagesJava and Multi ThreadingShraddha Sheth100% (1)
- DC Lab 1 Data RepresentationDocument3 pagesDC Lab 1 Data RepresentationbhavnaNo ratings yet
- 4.understanding Internet Protocol: It Equals 11110000Document7 pages4.understanding Internet Protocol: It Equals 11110000Afif MananNo ratings yet
- ICS 4CC509 Assignment 2019Document7 pagesICS 4CC509 Assignment 2019waleed aboelenienNo ratings yet
- Full - Doc (LC Corrections)Document8 pagesFull - Doc (LC Corrections)Liam CarterNo ratings yet
- 5CC512 Assignment 2016 Ver2Document4 pages5CC512 Assignment 2016 Ver2Kieron CairnsNo ratings yet
- FRI Case StudyDocument7 pagesFRI Case StudyNishit KatiraNo ratings yet
- 1.3.1a Networks and Topologies (LANs)Document25 pages1.3.1a Networks and Topologies (LANs)emona.mockuNo ratings yet
- Industry Certification CostingDocument1 pageIndustry Certification Costinggarytck1911No ratings yet
- Computer Science GCSE Knowledge OrganisersDocument26 pagesComputer Science GCSE Knowledge OrganisersAnandhi VijayNo ratings yet
- Teachers HandbookDocument16 pagesTeachers HandbookRoberto PiresNo ratings yet
- 2.1 OCR Reference Language Guide (Exam Pseudocode)Document12 pages2.1 OCR Reference Language Guide (Exam Pseudocode)Ash GaindNo ratings yet
- Computer Science (Gcse) : Gcsepod: Memory, Secondary Storage, The Central Processing UnitDocument4 pagesComputer Science (Gcse) : Gcsepod: Memory, Secondary Storage, The Central Processing UnitEmmanuella MensahNo ratings yet
- Specification Gcse Computer Science j277Document48 pagesSpecification Gcse Computer Science j277Zeeshan KhalidNo ratings yet
- Cambridge International AS & A Level: Computer Science 9618/22Document94 pagesCambridge International AS & A Level: Computer Science 9618/22akpavanNo ratings yet
- Networks - Fundamentals of Computer Networks - AQA - GCSE Computer Science Revision - AQA - BBC BitesizeDocument3 pagesNetworks - Fundamentals of Computer Networks - AQA - GCSE Computer Science Revision - AQA - BBC BitesizeMike MikkelsenNo ratings yet
- Paper 2 Theory For 9618Document33 pagesPaper 2 Theory For 9618rayan.muzzammil5No ratings yet
- Computer Science: Mcqs and AnswersDocument4 pagesComputer Science: Mcqs and Answersluct0% (1)
- CCNA 200-301 Part 3Document192 pagesCCNA 200-301 Part 3bhogireddy7779801No ratings yet
- Input and Output DevicesDocument34 pagesInput and Output DevicesShivanya AnilNo ratings yet
- Isaac Cs Ocr Book 2022Document354 pagesIsaac Cs Ocr Book 2022Ricky JacobNo ratings yet
- AQA Computing A2 Exam Style QsDocument40 pagesAQA Computing A2 Exam Style QsKonstantinos KastanasNo ratings yet
- Computer Science Lesson Plan Week 3 - T3-PracticalDocument4 pagesComputer Science Lesson Plan Week 3 - T3-PracticalIshrat JehanNo ratings yet
- 2023 2025 SyllabusDocument55 pages2023 2025 Syllabusolawuyi greatNo ratings yet
- 9626 Learner Guide (For Examination From 2022)Document27 pages9626 Learner Guide (For Examination From 2022)gabkaimviNo ratings yet
- Gcse Information and Communication TechnologyDocument19 pagesGcse Information and Communication TechnologyAsif Zubayer PalakNo ratings yet
- 6 Image CompressionDocument45 pages6 Image CompressionMadhusudhana RaoNo ratings yet
- Curso de Installing and Configuring Windows Server PDFDocument11 pagesCurso de Installing and Configuring Windows Server PDFFernando CorderoNo ratings yet
- Trace Table QuestionsDocument6 pagesTrace Table QuestionsitsmeshimrithNo ratings yet
- Chapter 01 - Data Information Knowledge and Processing - NVDocument88 pagesChapter 01 - Data Information Knowledge and Processing - NVShakila ShakiNo ratings yet
- Practical File (Adarsh)Document53 pagesPractical File (Adarsh)Pandey UjjwalNo ratings yet
- Introduction To Open OfficeDocument12 pagesIntroduction To Open OfficeVithanalage WathsalaNo ratings yet
- Algorithms NotesDocument93 pagesAlgorithms NotesPrajakta BagalNo ratings yet
- FOC Practical Question SetDocument4 pagesFOC Practical Question SetShankarNo ratings yet
- Olevel Computer Science Notes 2210 PDFDocument18 pagesOlevel Computer Science Notes 2210 PDFEmaanNo ratings yet
- Types and Components of Computer Systems: 2016 © Provided by Anthi AristotelousDocument55 pagesTypes and Components of Computer Systems: 2016 © Provided by Anthi AristotelousWalid SassiNo ratings yet
- Storage Area NetworkDocument109 pagesStorage Area Networksunil kumarNo ratings yet
- Cala Guide 3Document5 pagesCala Guide 3Tiffany huniNo ratings yet
- Computational Thinking Worksheet 1 Thinking Abstractly-1Document2 pagesComputational Thinking Worksheet 1 Thinking Abstractly-1zhouzhouNo ratings yet
- Unit 2: Creating Systems To Manage InformationDocument10 pagesUnit 2: Creating Systems To Manage InformationbmashrequiNo ratings yet
- Presentation Layer PPT 1 PDFDocument16 pagesPresentation Layer PPT 1 PDFSai Krishna SKNo ratings yet
- Introduction To Networks: KVS Regional Office Jaipur - Session 2020-21 Page 14 of 19Document3 pagesIntroduction To Networks: KVS Regional Office Jaipur - Session 2020-21 Page 14 of 19adamNo ratings yet
- Data Representation Worksheet 4 ImagesDocument3 pagesData Representation Worksheet 4 ImagesUsman Malik100% (1)
- Unit 1: Understanding Ict: A.M. FRIDAY, 13 January 2012 1 HoursDocument20 pagesUnit 1: Understanding Ict: A.M. FRIDAY, 13 January 2012 1 HoursAsif Zubayer PalakNo ratings yet
- 20 Code Challenges PDFDocument11 pages20 Code Challenges PDFViet Quoc HoangNo ratings yet
- Ip Addressing and Subnetting WorkshopDocument33 pagesIp Addressing and Subnetting WorkshopSachin SadadekarNo ratings yet
- AS LEVEL 9626 A LEVEL 9626 Checking The Accuracy of DataDocument7 pagesAS LEVEL 9626 A LEVEL 9626 Checking The Accuracy of DataTooba FarooqNo ratings yet
- Cpu LMC WorksheetDocument8 pagesCpu LMC Worksheetrobertz_tolentino014No ratings yet
- Lecture 3.2 - Uml Class DiagramsDocument29 pagesLecture 3.2 - Uml Class Diagramsnicole anistonNo ratings yet
- A2 Level CIE 9618 9608 Computer Science - Complete Syllabus Topics Lectures VideosDocument7 pagesA2 Level CIE 9618 9608 Computer Science - Complete Syllabus Topics Lectures VideosDevesh KhaitanNo ratings yet
- Computer Science 2022-Practical FileDocument32 pagesComputer Science 2022-Practical FileThupten ChoedupNo ratings yet
- Quiz - 23 Data Transmission TechnologiesDocument8 pagesQuiz - 23 Data Transmission TechnologiesMugerwa CharlesNo ratings yet
- AS LEVEL IT 9626 A LEVEL IT 9626 Impact of Information TechnologyDocument10 pagesAS LEVEL IT 9626 A LEVEL IT 9626 Impact of Information TechnologyTooba FarooqNo ratings yet
- Network Management System A Complete Guide - 2020 EditionFrom EverandNetwork Management System A Complete Guide - 2020 EditionRating: 5 out of 5 stars5/5 (1)
- MCSA: Windows 10 Complete Study Guide: Exam 70-698 and Exam 70-697From EverandMCSA: Windows 10 Complete Study Guide: Exam 70-698 and Exam 70-697No ratings yet
- Computer Science 5Document40 pagesComputer Science 5Muhtasim Ibne kamalNo ratings yet
- Computer Science 4Document17 pagesComputer Science 4Muhtasim Ibne kamalNo ratings yet
- Computer Science 3Document123 pagesComputer Science 3Muhtasim Ibne kamalNo ratings yet
- Computer Science 2Document24 pagesComputer Science 2Muhtasim Ibne kamalNo ratings yet
- OCR ExamBuilder Test ExportDocument56 pagesOCR ExamBuilder Test ExportMuhtasim Ibne kamalNo ratings yet
- Computer Science 1Document20 pagesComputer Science 1Muhtasim Ibne kamalNo ratings yet
- All 6 Markers Paper 2Document76 pagesAll 6 Markers Paper 2Muhtasim Ibne kamalNo ratings yet
- 6 MarkarsDocument23 pages6 MarkarsMuhtasim Ibne kamalNo ratings yet
- All Markers Paper 1Document82 pagesAll Markers Paper 1Muhtasim Ibne kamalNo ratings yet
- Computer Science 5Document23 pagesComputer Science 5Muhtasim Ibne kamalNo ratings yet
- Computer Science 4Document13 pagesComputer Science 4Muhtasim Ibne kamalNo ratings yet
- Computer Science 3Document10 pagesComputer Science 3Muhtasim Ibne kamalNo ratings yet
- Computer Science 1Document27 pagesComputer Science 1Muhtasim Ibne kamalNo ratings yet
- Computer Science 2Document36 pagesComputer Science 2Muhtasim Ibne kamalNo ratings yet
- POM 1546. Activity7: 1 PointDocument2 pagesPOM 1546. Activity7: 1 PointJoshua LokinoNo ratings yet
- Exfo - Ftb-7600e-0034b Ftb-7000 Series Otdr For Ftb-200 v2 - User Guide-9234 2Document339 pagesExfo - Ftb-7600e-0034b Ftb-7000 Series Otdr For Ftb-200 v2 - User Guide-9234 2Bilal GayretliNo ratings yet
- Superposition TheoremDocument13 pagesSuperposition TheoremThiv TriNo ratings yet
- Hill Road Unit1Document20 pagesHill Road Unit1MaheshBhattaraiNo ratings yet
- Library Management SystemDocument15 pagesLibrary Management SystemGohar KietianNo ratings yet
- Advanced Computational Models FLUENT - NOTESDocument179 pagesAdvanced Computational Models FLUENT - NOTESapi-3803751100% (3)
- MC190402499 MTH 302. Assignment No. 2. Spring 2020Document3 pagesMC190402499 MTH 302. Assignment No. 2. Spring 2020studentcare mtnNo ratings yet
- YL50Wp, Yingli SolarDocument2 pagesYL50Wp, Yingli SolarSiham MajidNo ratings yet
- VBScript HandoutDocument78 pagesVBScript Handoutaruns2012No ratings yet
- TS00E v1.2 Student Noteset PDFDocument303 pagesTS00E v1.2 Student Noteset PDFpatrick morris100% (1)
- CMP1401: Introduction To Programming With C: Ece Gelal Soyak Bahc Es Ehir UniversitesiDocument24 pagesCMP1401: Introduction To Programming With C: Ece Gelal Soyak Bahc Es Ehir UniversitesidoaaNo ratings yet
- Test 1 SolutionsDocument4 pagesTest 1 SolutionsAswin Kumar TiriyaNo ratings yet
- Me 2309 Cad Lab Manual Part & Assemble DiagramsDocument23 pagesMe 2309 Cad Lab Manual Part & Assemble DiagramsShyam BharathiNo ratings yet
- Synthesis and Characterization of Cellulose Nanocrystals FromDocument93 pagesSynthesis and Characterization of Cellulose Nanocrystals FromSUWIPHA DAPHANo ratings yet
- DSP Chapter8 PDFDocument66 pagesDSP Chapter8 PDFTiến Bảo NguyễnNo ratings yet
- Pre CalculusDocument8 pagesPre CalculusBryan SaligaoNo ratings yet
- Hapter WO Bearing Capacity of Shallow FoundationsDocument16 pagesHapter WO Bearing Capacity of Shallow Foundationsdmz shetuNo ratings yet
- Time & Work Type - 15 - 14191057Document4 pagesTime & Work Type - 15 - 14191057hefadiy957No ratings yet
- C Language ComputerDocument215 pagesC Language Computergaddipati vyshnaviNo ratings yet
- Characterization of Au (OH) 3Document6 pagesCharacterization of Au (OH) 3Nguyen TrangNo ratings yet
- Me 235SDocument8 pagesMe 235SFernando Chacmana LinaresNo ratings yet
- Boiler Cleanup CycleDocument23 pagesBoiler Cleanup Cyclescentpcbarauni BARAUNINo ratings yet
- HKOH SNDL Int ReqDocument2 pagesHKOH SNDL Int ReqMuhammad AsfandyarNo ratings yet
- Nutec - Technical CeramicsDocument8 pagesNutec - Technical CeramicsCeramiatNo ratings yet
- FT.2 Procesor P02498-L21 96MPXECA-2.3-22M36 - Datasheet 20190705154145Document2 pagesFT.2 Procesor P02498-L21 96MPXECA-2.3-22M36 - Datasheet 20190705154145Ion MarinasNo ratings yet
- Components of A BridgeDocument4 pagesComponents of A BridgeBhemalee Tono DimalaluanNo ratings yet
- Kubernetes TasksDocument786 pagesKubernetes Taskscduran1983No ratings yet
- AA V4 I2 Turning To Rotor DynamicsDocument2 pagesAA V4 I2 Turning To Rotor DynamicsJan MacajNo ratings yet