Professional Documents
Culture Documents
Computer Science 2
Computer Science 2
Uploaded by
Muhtasim Ibne kamalOriginal Description:
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Computer Science 2
Computer Science 2
Uploaded by
Muhtasim Ibne kamalCopyright:
Available Formats
1 A software company decides to release a duplicate file finder which it has named “De-Duplicator”.
Duplicate files
are files that are exactly the same (bit for bit identical). Space is often wasted on computers by having multiple
versions of the same file. Duplicate file finders are programs that find and identify duplicate files on a hard drive
so that they can be removed.
Every time the program encounters a file it takes a hash of the file and checks it against a list. If the hash exists
in the list, the file is marked to be deleted. If the hash does not exist it is added to the list.
(i) Explain two characteristics you would look for in a hashing algorithm for this purpose.
[4]
(ii) After running the program a user finds that they still have apparent duplicates of some of their images.
Explain why these apparent duplicates might still be present.
[2]
© OCR 2023. You may photocopy this page. 1 of 24 Created in ExamBuilder
2 All videos that are streamed are compressed. Customers have the option to choose from watching the videos
with lossy compression or lossless compression.
Explain how this choice will impact the customer.
[5]
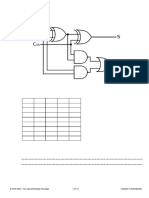
3(a) The XOR operator can be used to encrypt data.
Show the effect of applying XOR on Text and Key, by completing the last row of the table below.
[2]
© OCR 2023. You may photocopy this page. 2 of 24 Created in ExamBuilder
(b) Show the effect of applying XOR on your answer to part (a) and Key, by completing the first and last rows of the
table below.
[2]
(c) Explain whether the type of encryption described above is symmetric or asymmetric.
[2]
(d) Explain why asymmetric encryption is more suited to transactions over the internet than symmetric encryption.
[4]
© OCR 2023. You may photocopy this page. 3 of 24 Created in ExamBuilder
4(a) A charitable organisation is trying to make the works of William Shakespeare available to more people.
The organisation decides to make a copy of Shakespeare’s entire works available as a downloadable text file
from its website. It further decides to compress the file before making it available to download.
(i) State an advantage to the website’s visitors of the file being compressed.
[1]
(ii) Explain why the company should use lossless and not lossy compression.
[3]
© OCR 2023. You may photocopy this page. 4 of 24 Created in ExamBuilder
(b)
The organisation looks at using either run length encoding or dictionary encoding to compress the file
described in part (a).
Discuss the two compression methods and justify which you would recommend. You may refer to the extract of
text below to illustrate your argument.
What’s in a name? that which we call a rose
By any other name would smell as sweet;
So Romeo would, were he not Romeo call’d, [12]
© OCR 2023. You may photocopy this page. 5 of 24 Created in ExamBuilder
© OCR 2023. You may photocopy this page. 6 of 24 Created in ExamBuilder
5(a) A web forum stores all its content in a database.
The forum stores details of its users in the table called Users. An extract of Users is shown below.
userID username passwordHash locked
1 Zeus 8dfa46a79248037752bba6166fcb34f8 1
2 Hera 74d39d60507eb55e000c6ec5c1265891 0
3 Poseidon b015d770d0208ddcce2c2c719fe29371 0
Describe what is meant by the term ‘primary key’, giving an example from the table above.
[2]
© OCR 2023. You may photocopy this page. 7 of 24 Created in ExamBuilder
(b) The user’s password is passed to a function that generates a hash and the result is stored in passwordHash.
(i) Describe what is meant by the term ‘hash’.
[1]
(ii) Describe one advantage to storing the password as a hash.
[2]
© OCR 2023. You may photocopy this page. 8 of 24 Created in ExamBuilder
(c)
Write an SQL statement to get just the passwordHash and locked values of the user Apollo.
[3]
(d)
Sometimes users can have their accounts locked if they behave inappropriately. When this is the case the
locked field is set to 1 rather than 0.
Write an SQL statement that locks the account of the user Hades
[3]
© OCR 2023. You may photocopy this page. 9 of 24 Created in ExamBuilder
(e) The function checkAccess takes in the password the user has entered (givenPassword) along with the
password hash (passwordHash) and locked value (locked).
passwordHash and locked have already been extracted from the database before being passed to the
function. It should return the value true if a user should be allowed access to a system and false if they aren’t.
Your function should make use of the pre-written function hash() which takes in a string and returns the hash
of that string.
e.g.
hash("Hello") returns f7ff9e8b7bb2e09b70935a5d785e0cc5d9d0abf0
Complete the function checkAccess.
function checkAccess (givenPassword, passwordHash, locked)
© OCR 2023. You may photocopy this page. 10 of 24 Created in ExamBuilder
endfunction
[4]
6 * Modern encryption is much stronger than the method described in the first part of this question.
Discuss the impact of modern encryption on society. You should refer to:
• The importance of asymmetric encryption and how it differs from symmetric encryption.
• Different circumstances in which symmetric and asymmetric encryption may be used.
© OCR 2023. You may photocopy this page. 11 of 24 Created in ExamBuilder
[9]
© OCR 2023. You may photocopy this page. 12 of 24 Created in ExamBuilder
7(a) A survey is carried out to look at the types of vehicle that travel down a stretch of motorway.
For each vehicle that passes by, a letter is entered into the system.
For a car ‘C’ is entered.
For a motorbike ‘M’ is entered.
For a lorry ‘L’ is entered.
For any other vehicle ‘O’ is entered.
It is decided to compress the data that has been generated.
State what is meant by the term ‘compression’.
[1]
(b) It is decided that Run Length Encoding will be used.
The following sequence has been compressed using Run Length Encoding.
3C3M4C
Show the result of decompressing the sequence.
[2]
© OCR 2023. You may photocopy this page. 13 of 24 Created in ExamBuilder
(c) Show the result of using Run Length Encoding to compress the sequence:
CCCCOLLLCCCCCMOCCCCC
[3]
8 Shreya is a web developer who creates webpages for a variety of different companies.
Photographs on a webpage are usually compressed.
(i) State which method of compression is most likely to be used for this purpose.
[1]
(ii) Explain the need to compress photographs in this situation.
[2]
END OF QUESTION PAPER
© OCR 2023. You may photocopy this page. 14 of 24 Created in ExamBuilder
Mark Scheme
Question Answer/Indicative content Marks Guidance
1 i Low chance of collision (i.e. different 4 1 mark for each correct identification
inputs giving same output) (1 – AO1.2) (AO1.2) up to a maximum of two
to reduce risk of different files being identifications
marked as the same (1 – AO2.1).
Quick to calculate (1 – AO1.2) as lots 1 mark for each valid explanation (AO2.1)
of files need to be hashed / needs to up to a maximum of two explanations.
be quicker than a bitwise comparison
to make it worthwhile (1 – AO2.1). No credit for function being one way as this
Provides a smaller output than input (1 serves no benefit in this scenario.
– AO1.2) so quicker to compare
hashes than original data (1 – AO2.1).
ii Hashing works on the data / bits (1) 2 Up to 2 marks for a valid explanation.
and so two images may appear the
same but not be identical at a bit level Accept any other sensible examples of
(1). This could be because they are changes to images that might not be
different file types (1) / different sizes immediately apparent to someone viewing
(1). Even the change of a single bit the image.
may result in a completely different
hash (1).
Total 6
2 Lossy permanently removes data 5 Do not allow answers relating to speed of
Lossless rewrites original data in more download unless this clearly refers to the
efficient format video starting or reduction in buffering –
Lossless is able to recreate the original scenario is video being streamed, not
file // Lossy is not able to recreate the downloaded.
original file
Lossy reduces quality of videos // Examiner’s Comments
Lossless keeps original quality Candidates tended to write at length for
Lossy file size is smaller than if this question, but often made the same
lossless were used point twice. Many missed marks for not
Lossy: compression ratio may be making the comparison between lossy and
adjusted depending on bandwidth lossless and only gave one side. Some
Resulting in a noticeable decrease in candidates discussed the videos being
quality on slower connections. downloaded rather than streamed.
Lossy: the video will buffer less /
quicker to start watching the video //
Lossless: the video will buffer more /
slower to start watching the video
Total 5
3 a 2
One byte correct (1) all three bytes
correct. (1)
© OCR 2023. You may photocopy this page. 15 of 24 Created in ExamBuilder
Mark Scheme
Question Answer/Indicative content Marks Guidance
b 2 Allow FT if (a) is incorrect but bottom row
must match XOR with top row and key.
One byte correct (1) all three bytes
correct. (1)
c Symmetric (1) …. as the same key is used 2 Allow FT for asymmetric if (b) indicates
to decrypt it as encrypt it (1) asymmetric encryption used
d Any four from: 4
Symmetric encryption would require both
parties to have copy of the key (1) this
couldn’t be transmitted over the internet or
an eavesdropper monitoring the message
may see it (1) Asymmetric gets round this
requirement as there are two different keys
(1) One key encrypts the data (1) which
can be publically distributed (1) and a
different key to decrypt it (1) which is kept
private (1)
Total 10
© OCR 2023. You may photocopy this page. 16 of 24 Created in ExamBuilder
Mark Scheme
Question Answer/Indicative content Marks Guidance
4 a i Downloads quicker. (1) 1 Do not accept ‘saves the user space on
Saves user money by using less their device’.
bandwidth / on data usage. (1) (AO1.2)
Examiner’s Comments
This question was well received by most
(Max 1) candidates, invariably scoring most marks.
ii Lossy takes away some of the 3
information from the original. (1) (AO1.1 –
Lossless preserves all the 2
information from the original. (1) marks
With text the loss of small amounts AO2.1 –
of information will make it 1mark)
unreadable. (1)
b Mark Band 3–High Level (9–12 marks) AO1.1 Points may include but aren’t limited to:
The candidate demonstrates a thorough (2) AO1 Knowledge and Understanding
knowledge and understanding of dictionary
and run length encoding for compression. AO1.2 Run length encoding relies on consecutive
The material is generally accurate and pieces of data / characters being the same.
detailed.
(2)
The candidate is able to apply their Each set of consecutive symbols can be
knowledge and understanding directly and AO2.1 represented by the symbol and its number
consistently to the context provided. of occurrences
Evidence / examples will be explicitly (3) e.g. AAAABBBBBCCC could be
relevant to the explanation. represented as 4A5B3C (or A4B5C3 or
any sensible RLE encoding)
AO3.3
The candidate is able to weigh up both In dictionary encoding frequently occurring
forms of compression and justify dictionary (5) pieces of data / groups of characters are
encoding being the better choice. replaced by symbols / tokens / smaller
groups of characters / indexes.
There is a well-developed line of reasoning A dictionary is then used to say which
which is clear and logically structured. The symbols / tokens / characters / indexes
information presented is relevant and 12 match which groups of characters.
substantiated. When decompressed the dictionary is used
to replace the tokens with the original text.
Mark Band 2-Mid Level (5–8 marks)
The candidate demonstrates reasonable AO2.1 Application
knowledge and understanding of dictionary Run Length Encoding is very unsuitable for
and run length encoding for compression; the example text. There are very few
the material is generally accurate but at consecutive repeating symbols in the text.
times underdeveloped. only instances being ll and ee
these still require 2 characters to represent
them 2l and 2e
© OCR 2023. You may photocopy this page. 17 of 24 Created in ExamBuilder
Mark Scheme
Question Answer/Indicative content Marks Guidance
The candidate is able to apply their Dictionary encoding is well suited.
knowledge and understanding directly to There are lots of repeating groups of
the context provided although one or two characters
opportunities are missed. Evidence / For example ‘call’ ‘name’ ‘[SPACE]we’
examples are for the most part implicitly ‘Romeo’
relevant to the explanation. We could for example have:
What’s in53? that which2 15 rose
The candidate makes a reasonable
attempt to come to a conclusion as to By5ny other3 would smell5s sweet;
which form of compression is better suited.
So4would,2re he not41’d
There is a line of reasoning presented with
some structure. The information presented 1:call
is in the most part relevant and supported
by some evidence. 2:[space]we
Mark Band 1-Low Level (1–4 marks) 3:[space]name
The candidate demonstrates a basic 4:[space]Romeo[space]
knowledge of dictionary and run length
encoding for compression; the material is 5:[space]a
basic and contains some inaccuracies. The
candidate makes a limited attempt to apply (NB candidates are unlikely to show full
acquired knowledge and understanding to compression, just a demonstration of the
the context provided. principle is sufficient. The best candidates
are likely to show an awareness that space
The candidate provides nothing more than is a character that can be used in
an unsupported assertion. compression and that upper and lowercase
letters are different. Demonstrating this is
0 marks indicative of but not a requisite of the
band.)
No attempt to answer the question or
response is not worthy of credit. AO3.3: Evaluation
Run length encoding is not suited to
natural language (more likely to be used in
simple images).
Applying it to the example the resulting text
would be the same size as the original /
worse than the original (if we use 1s to
represent every individual instance of a
character).
Dictionary encoding works well. We can
already see benefit on small piece of text.
Would fare substantially better on full
works.
© OCR 2023. You may photocopy this page. 18 of 24 Created in ExamBuilder
Mark Scheme
Question Answer/Indicative content Marks Guidance
Dictionary encoding is the best
compression method for this scenario.
Examiner’s Comments
Candidates were assessed on the quality
of their extended response in this question.
Most candidates could describe each of
the given types of compression
appropriately, with many applying them to
the scenario. Many candidates correctly
concluded that dictionary encoding was the
most appropriate in this case, but few then
went on to give clear and appropriate
justification for their assertion. In general,
most candidates scored well on this
question.
Total 16
© OCR 2023. You may photocopy this page. 19 of 24 Created in ExamBuilder
Mark Scheme
Question Answer/Indicative content Marks Guidance
5 a A field which has a unique value for every 2
record / A unique identifier. (1)
(AO1.1 –
E.g. userID (1) 1, AO2.1
-1)
Examiner’s Comments
Well received and answered by most
candidates.
b i A result generated by applying an 1
algorithm / numeric process to a value. (1)
(AO1.1)
ii Hash functions are one way / can’t 2
be reverse (1)
If someone gains access to the (AO1.2 1
database they cannot access user’s mark,
password. (1) Examiner’s Comments
AO2.1 Many candidates achieved the mark in
part i) few achieved both marks in part ii)
1 mark) mostly stating as opposed to describing the
advantage e.g. ‘those who gain
unauthorised access cannot access
passwords’ without going on to say ‘hash
functions are one way’.
c SELECT passwordHash, locked (1) 3 Do not award first mark for SELECT *
FROM Users (1)
WHERE username=‘Apollo’ (1) (AO 3.2)
Examiner’s Comments
In most cases, candidates who achieved
marks in c) went on to achieve marks in d)
with few candidates achieving all marks in
either. Many candidates did not use correct
SQL statement structure or syntax e.g.
confusing attribute names with string
literals.
© OCR 2023. You may photocopy this page. 20 of 24 Created in ExamBuilder
Mark Scheme
Question Answer/Indicative content Marks Guidance
d UPDATE Users (1) 3 Allow other updating method
SET locked=1 (1) e.g. a DELETE statement followed by an
INSERT statement, for full marks e.g.
(AO 3.2)
WHERE username=‘Hades’ (1)
Examiner’s Comments
In most cases, candidates who achieved
marks in c) went on to achieve marks in d)
with few candidates achieving all marks in
either. Many candidates did not use correct
SQL statement structure or syntax e.g.
confusing attribute names with string
literals.
e Takes a hash of givenPassword 4 Example code:
(NB this may be done inline e.g.
if hash (givenPassword)==pa (AO 3.2)
sswordHash and locked==0
then (1)
Returns true if password is correct
and account is unlocked. (1) Candidates may have taken a different
approach - any solution that fulfils the
Returns false if account is locked (1) criteria on the left should get them marks.
Returns false if password is
incorrect (1)
Examiner’s Comments
Candidates were asked to complete a
function in this question. Although many
students demonstrated reasonable logic in
solving this problem, some used output
statements rather than returned values
from the function, therefore, not gaining full
marks.
Total 15
© OCR 2023. You may photocopy this page. 21 of 24 Created in ExamBuilder
Mark Scheme
Question Answer/Indicative content Marks Guidance
6 Mark Band 3-High Level (7-9 marks) 9 AO1.1 AO1
The candidate demonstrates a thorough (2) AO1.2 Modern encryption is many orders stronger
knowledge and understanding of modern (2) AO2.1 than that used in a pre-computer era.
encryption and the difference between (2) AO3.3 Asymmetric encryption uses different keys
symmetric and asymmetric encryption. The (3) for encryption and decryption.
material is generally accurate and detailed. Symmetric encryption uses the same key
for encryption and decryption.
The candidate is able to apply their Asymmetric encryption algorithms tend to
knowledge and understanding directly and involve more processing than symmetric
consistently to the context provided. algorithms.
Evidence/examples will be explicitly
relevant to the explanation.
AO2
The candidate provides a thorough Modern encryption can be used without
discussion which is well balanced. specialist knowledge. Often users may not
Evaluative comments are consistently even be aware their data is being
relevant and well-considered. encrypted (e.g. HTTPS, messaging
systems)
There is a well-developed line of reasoning Asymmetric encryption is often used when
which is clear and logically structured. The exchanging data.
information presented is relevant and For example credit card details over the
substantiated. internet.
Symmetric encryption is best suited when
Mark Band 2-Mid Level (4-6 marks) The the same person is encrypting and
candidate demonstrates reasonable decrypting.
knowledge and understanding of modern For example when backing up data.
encryption and the difference between
symmetric and asymmetric encryption; the
material is generally accurate but at times AO3
underdeveloped. The strength and ease of use of encryption
has made it widely used on the Internet.
The candidate is able to apply their E-Commerce would not be possible
knowledge and understanding directly to without it.
the context provided although one or two Governments are no longer able to easily
opportunities are missed. crack encrypted messages they intercept
Evidence/examples are for the most part (as far as we know).
implicitly relevant to the explanation. This gives individuals unprecedented
levels of privacy
The candidate provides a sound But also means those communicating for
discussion, the majority of which is nefarious purposes can do so undetected.
focused. Evaluative comments are for the
most part appropriate, although one or two Examiner’s Comments
opportunities for development are missed.
Candidates were assessed on the quality
There is a line of reasoning presented with of their extended response in this question.
some structure. The information presented Many candidates explained the difference
is in the most part relevant and supported between symmetric and asymmetric
by some evidence. encryption very well. Some went on to
describe the circumstances in which they
© OCR 2023. You may photocopy this page. 22 of 24 Created in ExamBuilder
Mark Scheme
Question Answer/Indicative content Marks Guidance
Mark Band 1-Low Level (1-3 marks) are used equally well. Few discussed the
The candidate demonstrates a basic impact on society. Many candidates scored
knowledge modern encryption and the in the mid band on this question.
difference between symmetric and
asymmetric encryption; the material is
basic and contains some inaccuracies. The
candidate makes a limited attempt to apply
acquired knowledge and understanding to
the context provided.
The candidate provides a limited
discussion which is narrow in focus.
Judgments if made are weak and
unsubstantiated. The information is basic
and communicated in an unstructured way.
The information is supported by limited
evidence and the relationship to the
evidence may not be clear.
0 marks
No attempt to answer the question or
response is not worthy of credit
Total 9
7 a (The process of) making a file smaller/take 1
up less storage
AO1.1
b Full answer CCCMMMCCCC 2
AO1.2
– CCC
– … followed by MMMCCCC
(1 per -, max 2)
c 4C1O3L5C1M1O5C 3 Accept answer without 1s
AO1.2 Examiner’s Comments
– 4C1O
– Followed by 3L5C Well answered by most candidates,
– Followed by 1M1O5C demonstrating clear understanding of Run
Length Encoding as a method of
compression.
Total 6
© OCR 2023. You may photocopy this page. 23 of 24 Created in ExamBuilder
Mark Scheme
Question Answer/Indicative content Marks Guidance
8 i Lossy 1
AO2.1
(1)
ii 1 mark per bullet up to a maximum of 2 2
marks, e.g.: AO2.1
(2)
Reduces the size of the image file
Uses lower bandwidth in transmission
Takes up less storage (on the HTTP
server)
Total 3
© OCR 2023. You may photocopy this page. 24 of 24 Created in ExamBuilder
Powered by TCPDF (www.tcpdf.org)
You might also like
- 1.3.3_-_NetworksDocument49 pages1.3.3_-_NetworksKingNo ratings yet
- Computer Science 2Document36 pagesComputer Science 2Muhtasim Ibne kamalNo ratings yet
- Binary & Data Structure QDocument164 pagesBinary & Data Structure QddNo ratings yet
- Duration: Not Set: © Ocr 2023. You May Photocopy This Page. 1 of 20 Created in ExambuilderDocument20 pagesDuration: Not Set: © Ocr 2023. You May Photocopy This Page. 1 of 20 Created in ExambuilderYousif OmerNo ratings yet
- Computer Science 4Document13 pagesComputer Science 4Muhtasim Ibne kamalNo ratings yet
- H04601 Computing Principles June 2023Document29 pagesH04601 Computing Principles June 2023aljulanda1233No ratings yet
- 1.4.2 Data StructuresDocument15 pages1.4.2 Data Structuresaljulanda1233No ratings yet
- Computing PrinciplesDocument160 pagesComputing PrinciplesDeep PatelNo ratings yet
- June 2017 A-Level Paper 1 (With MS)Document62 pagesJune 2017 A-Level Paper 1 (With MS)Tyler WilcockNo ratings yet
- CTEC - QuestionsDocument7 pagesCTEC - Questionsmolahe8688No ratings yet
- Computer Science 1Document20 pagesComputer Science 1Muhtasim Ibne kamalNo ratings yet
- 1.3.4 Web TechnologiesDocument15 pages1.3.4 Web Technologiesuma9sathiyakailashNo ratings yet
- Computer Science 5Document23 pagesComputer Science 5Muhtasim Ibne kamalNo ratings yet
- June 2016 AS Paper 1 (With MS)Document26 pagesJune 2016 AS Paper 1 (With MS)Tyler WilcockNo ratings yet
- Duration: Not Set: © Ocr 2023. You May Photocopy This Page. 1 of 47 Created in ExambuilderDocument47 pagesDuration: Not Set: © Ocr 2023. You May Photocopy This Page. 1 of 47 Created in ExambuilderYousif OmerNo ratings yet
- Computer Science 3Document10 pagesComputer Science 3Muhtasim Ibne kamalNo ratings yet
- Paper 1 Revision Booklet 1Document266 pagesPaper 1 Revision Booklet 1lucigutmar2009No ratings yet
- 10com Network Qs PrepDocument7 pages10com Network Qs Prepreerik.comNo ratings yet
- IB Computer Science (Year 1) 2024 Sem 2 EOYDocument4 pagesIB Computer Science (Year 1) 2024 Sem 2 EOYKiat Seng, Jason LeeNo ratings yet
- CSS and HTMLDocument5 pagesCSS and HTMLgoldengloowastakenNo ratings yet
- Systems and Architecture MH Practice PaperDocument19 pagesSystems and Architecture MH Practice PaperLucia Paredes GroucottNo ratings yet
- Merge Insertion Bubble Linear and Binary SearchDocument73 pagesMerge Insertion Bubble Linear and Binary Searchsammytest30No ratings yet
- November 2004 Paper 1Document4 pagesNovember 2004 Paper 1api-3753397No ratings yet
- Computer Science MockDocument42 pagesComputer Science MockMuhtasim Ibne kamalNo ratings yet
- COMPUTER SC. SL PAPER ONE in ENGLISHDocument5 pagesCOMPUTER SC. SL PAPER ONE in ENGLISHOliver NixNo ratings yet
- June 2017 AS Paper 1 (With MS)Document34 pagesJune 2017 AS Paper 1 (With MS)Tyler WilcockNo ratings yet
- Visit Braindump2go and Download Full Version AZ-204 Exam DumpsDocument7 pagesVisit Braindump2go and Download Full Version AZ-204 Exam DumpsAndre AyalaNo ratings yet
- 12th CS 1 Prelims Exam 26 - 03 - 2021Document4 pages12th CS 1 Prelims Exam 26 - 03 - 2021naveenkenchgunde10No ratings yet
- OCR ExamBuilder Test ExportDocument56 pagesOCR ExamBuilder Test ExportMuhtasim Ibne kamalNo ratings yet
- November 2005 Paper 3Document4 pagesNovember 2005 Paper 3api-3753397No ratings yet
- wkuAmNnTMeiFCVuwGrCtQ - CM2025 Past Exam Sep 2022Document7 pageswkuAmNnTMeiFCVuwGrCtQ - CM2025 Past Exam Sep 2022chaudhary.ahmadNo ratings yet
- CLOUD COMPUTING FinalDocument58 pagesCLOUD COMPUTING FinalDishita ChughNo ratings yet
- Computational Thinking QDocument57 pagesComputational Thinking QddNo ratings yet
- PEQs 231 AlgorithmsDocument281 pagesPEQs 231 Algorithmsharoon.sham13No ratings yet
- St. Augustine'S High School Computing Paper 1: Term 1 U6 End of Term Exam 2014 Instructions: Answer All QuestionsDocument2 pagesSt. Augustine'S High School Computing Paper 1: Term 1 U6 End of Term Exam 2014 Instructions: Answer All Questionssipiwe phiriNo ratings yet
- Software & Programming QDocument58 pagesSoftware & Programming QddNo ratings yet
- g-12 p-1 TestDocument5 pagesg-12 p-1 TestDev SethiNo ratings yet
- New FileDocument52 pagesNew FilecastroxfourNo ratings yet
- 1.1.3 InputOutputStorage SLR3Document23 pages1.1.3 InputOutputStorage SLR3melisag06130No ratings yet
- MCSE - PGCS203B - SECURE SOFTWARE DESIGN AND ENTERPRISE COMPUTING - R18 - BookletDocument2 pagesMCSE - PGCS203B - SECURE SOFTWARE DESIGN AND ENTERPRISE COMPUTING - R18 - Bookletitsnishu445No ratings yet
- INSTRUCTIONS: Answer Question One & ANY OTHER TWO Questions. Question One (30 Marks)Document3 pagesINSTRUCTIONS: Answer Question One & ANY OTHER TWO Questions. Question One (30 Marks)omoshNo ratings yet
- Azure 303 Practice Test 01Document74 pagesAzure 303 Practice Test 01Anonymous iz83EL9No ratings yet
- Bca Semester-Vi 2023-24Document4 pagesBca Semester-Vi 2023-24laserbolt2002No ratings yet
- Topic 1: Contoso, LTD Topic 2: Misc. Questions: Exam Topic Breakdown Exam Topic Number of QuestionsDocument146 pagesTopic 1: Contoso, LTD Topic 2: Misc. Questions: Exam Topic Breakdown Exam Topic Number of QuestionsJosé MaldonadoNo ratings yet
- 2015 Multimedia and Webtech - Outside DelhiDocument11 pages2015 Multimedia and Webtech - Outside DelhiKishwar FatimaNo ratings yet
- Cambridge University - Computer Science Tripos - y2023PAPER3Document10 pagesCambridge University - Computer Science Tripos - y2023PAPER3GtrendsCE AccountNo ratings yet
- Pgpccjune22 - Aws - Project5Document12 pagesPgpccjune22 - Aws - Project5Ruchi BishtNo ratings yet
- Az-103 Questionsanswersdumps PDFDocument30 pagesAz-103 Questionsanswersdumps PDFnicoNo ratings yet
- Cambridge International Examinations General Certificate of Education Advanced Subsidiary Level and Advanced Level Computing Paper 3 October / November 2003Document4 pagesCambridge International Examinations General Certificate of Education Advanced Subsidiary Level and Advanced Level Computing Paper 3 October / November 2003Neha RmdsNo ratings yet
- Hsslive Xii Cs Key Model 2024.Document5 pagesHsslive Xii Cs Key Model 2024.mavrick87654321No ratings yet
- Azure Container RegistryDocument6 pagesAzure Container RegistryHassan SalviNo ratings yet
- Unit 2 Assessment AnswersDocument5 pagesUnit 2 Assessment Answersreyyanqasim7No ratings yet
- Computer Science Paper 1 HLDocument7 pagesComputer Science Paper 1 HLnnabhani78No ratings yet
- Unix and Shell ProgrammingDocument4 pagesUnix and Shell ProgrammingWael AbdulalNo ratings yet
- 009 - BCS-053 D18 - Compressed PDFDocument4 pages009 - BCS-053 D18 - Compressed PDFManmohan RathoreNo ratings yet
- Describe Cloud ConceptsDocument30 pagesDescribe Cloud ConceptsLuis EnriqueNo ratings yet
- 70 533Document88 pages70 533WiNgeneAbr100% (1)
- AWS Solutions Architect Certification Case Based Practice Questions Latest Edition 2023From EverandAWS Solutions Architect Certification Case Based Practice Questions Latest Edition 2023No ratings yet
- Cloud Computing with the Windows Azure PlatformFrom EverandCloud Computing with the Windows Azure PlatformRating: 3.5 out of 5 stars3.5/5 (3)
- AZ-900 Microsoft Azure Fundamentals: Exam Prep Question BankFrom EverandAZ-900 Microsoft Azure Fundamentals: Exam Prep Question BankNo ratings yet
- Computer Science 5Document40 pagesComputer Science 5Muhtasim Ibne kamalNo ratings yet
- OCR ExamBuilder Test ExportDocument56 pagesOCR ExamBuilder Test ExportMuhtasim Ibne kamalNo ratings yet
- Computer Science 4Document17 pagesComputer Science 4Muhtasim Ibne kamalNo ratings yet
- Computer Science 3Document123 pagesComputer Science 3Muhtasim Ibne kamalNo ratings yet
- Computer Science 1Document20 pagesComputer Science 1Muhtasim Ibne kamalNo ratings yet
- Computer Science MockDocument42 pagesComputer Science MockMuhtasim Ibne kamalNo ratings yet
- All Markers Paper 1Document82 pagesAll Markers Paper 1Muhtasim Ibne kamalNo ratings yet
- All 6 Markers Paper 2Document76 pagesAll 6 Markers Paper 2Muhtasim Ibne kamalNo ratings yet
- 6 MarkarsDocument23 pages6 MarkarsMuhtasim Ibne kamalNo ratings yet
- Computer Science 4Document13 pagesComputer Science 4Muhtasim Ibne kamalNo ratings yet
- Computer Science 5Document23 pagesComputer Science 5Muhtasim Ibne kamalNo ratings yet
- Computer Science 2Document36 pagesComputer Science 2Muhtasim Ibne kamalNo ratings yet
- Computer Science 3Document10 pagesComputer Science 3Muhtasim Ibne kamalNo ratings yet
- Computer Science 1Document27 pagesComputer Science 1Muhtasim Ibne kamalNo ratings yet
- CYB102 Module 2Document5 pagesCYB102 Module 2Umar FaruqNo ratings yet
- Model: Rp-Um003 Ravpower Portable SSD: User GuideDocument34 pagesModel: Rp-Um003 Ravpower Portable SSD: User GuidejacksonNo ratings yet
- Randomx: Security AuditDocument27 pagesRandomx: Security AuditMaximuNo ratings yet
- Cryptographic Techniques PDFDocument41 pagesCryptographic Techniques PDFMuhammad Sikandar DarNo ratings yet
- Mhos PedsfDocument29 pagesMhos PedsfshashiNo ratings yet
- CNS - Unit IDocument60 pagesCNS - Unit IAyush GandhiNo ratings yet
- 1 Chapter 15 Resilience Engineering 13/11/2014Document63 pages1 Chapter 15 Resilience Engineering 13/11/2014Ask NameNo ratings yet
- 140 Service Manual - Travelmate 6292Document101 pages140 Service Manual - Travelmate 6292Soporte Tecnico Buenos AiresNo ratings yet
- Technology Challenges in Accounting & Finance (IV)Document15 pagesTechnology Challenges in Accounting & Finance (IV)najiath mzeeNo ratings yet
- BioEntry W2 RevisionNotes V1.6.3 ENDocument25 pagesBioEntry W2 RevisionNotes V1.6.3 ENalexander valleNo ratings yet
- Tendernotice 1Document44 pagesTendernotice 1Raja G Circles SafetyNo ratings yet
- Security Handbook: Network-Enabled Devices, AOS v7.xDocument39 pagesSecurity Handbook: Network-Enabled Devices, AOS v7.xM Aulia RahmanNo ratings yet
- Irjet V5i4919Document5 pagesIrjet V5i4919ghada sayedNo ratings yet
- A Presentation On Topic: "Encrypted Cloud Service"Document25 pagesA Presentation On Topic: "Encrypted Cloud Service"abhinav chowdhuryNo ratings yet
- Data Encryption Standard (DES) Set 1 - GeeksforGeeksDocument18 pagesData Encryption Standard (DES) Set 1 - GeeksforGeeksxativiy256No ratings yet
- Store Files To Synology NASDocument6 pagesStore Files To Synology NASCristian FilioreanuNo ratings yet
- Chat de WhatsApp Con ChaparroDocument25 pagesChat de WhatsApp Con Chaparroadrish845No ratings yet
- Assignment 2 Front Sheet: Qualification BTEC Level 5 HND Diploma in Computing Unit Number and Title Submission DateDocument18 pagesAssignment 2 Front Sheet: Qualification BTEC Level 5 HND Diploma in Computing Unit Number and Title Submission DateNguyen Manh TaiNo ratings yet
- What Is SSL Offloading?: SSL Acceleration SSL TerminationDocument2 pagesWhat Is SSL Offloading?: SSL Acceleration SSL Terminationsyed_engrNo ratings yet
- NIST SP 800-171 Assessment Methodology Version 1.2.1 6.24.2020Document21 pagesNIST SP 800-171 Assessment Methodology Version 1.2.1 6.24.2020awesome_600No ratings yet
- SecurityDocument5 pagesSecurityHector OnatoNo ratings yet
- Project Proposal - Phishing Attack - T5CS1105DDocument15 pagesProject Proposal - Phishing Attack - T5CS1105DirdinashahiraNo ratings yet
- CH 31 Network Security Multiple Choice Questions and Answers PDFDocument9 pagesCH 31 Network Security Multiple Choice Questions and Answers PDFaadi1988100% (1)
- University of Northern Philippines: College of Communication and Information TechnologyDocument5 pagesUniversity of Northern Philippines: College of Communication and Information TechnologyJanelle BilgeraNo ratings yet
- What Is Apache NifiDocument10 pagesWhat Is Apache Nifirisdianto sigmaNo ratings yet
- Um 11126Document1,222 pagesUm 11126vipul#123No ratings yet
- Cryptography and Network SecurityDocument11 pagesCryptography and Network Securityapi-26830587100% (2)
- Unit 4 - Cloud Computing - WWW - Rgpvnotes.in PDFDocument13 pagesUnit 4 - Cloud Computing - WWW - Rgpvnotes.in PDFprince keshriNo ratings yet
- Online Secure Banking Authentication System Using Blockchain TechnologyDocument30 pagesOnline Secure Banking Authentication System Using Blockchain TechnologyPooja G100% (1)
- AN1125: Creating and Using A Secure EZSP Host-to-NCP InterfaceDocument17 pagesAN1125: Creating and Using A Secure EZSP Host-to-NCP InterfaceLê HiếuNo ratings yet