Professional Documents
Culture Documents
Cloud Matrix
Cloud Matrix
Uploaded by
Nuryadin Usman Abdurrahim AsSampiti IICopyright:
Available Formats
You might also like
- CompTIA Server+ Certification All-in-One Exam Guide, Second Edition (Exam SK0-005)From EverandCompTIA Server+ Certification All-in-One Exam Guide, Second Edition (Exam SK0-005)No ratings yet
- Introduction To TeradataDocument51 pagesIntroduction To Teradataraghavendra.nieNo ratings yet
- Cyber Security Interview QuestionsDocument16 pagesCyber Security Interview QuestionsrakivanatanNo ratings yet
- Integration Framework Overview r15 PDFDocument17 pagesIntegration Framework Overview r15 PDFigomez100% (1)
- T24 Close of Business (COB) - T24 HelperDocument17 pagesT24 Close of Business (COB) - T24 HelperNett2k100% (9)
- Containers MatrixDocument1 pageContainers MatrixNuryadin Usman Abdurrahim AsSampiti IINo ratings yet
- Network MatrixDocument1 pageNetwork MatrixrakivanatanNo ratings yet
- Mitre Att&ck v9Document22 pagesMitre Att&ck v9Fabiano DiscacciatiNo ratings yet
- Conti (s0575)Document5 pagesConti (s0575)anup.tilekar.86No ratings yet
- Peter O & Alessandra Di Carlo - Lessons From The Frontlines - Ransomware Attacks, New Techniques and Old TricksDocument23 pagesPeter O & Alessandra Di Carlo - Lessons From The Frontlines - Ransomware Attacks, New Techniques and Old TricksFranklin CordeiroNo ratings yet
- ATTCK Matrix For EnterpriseDocument1 pageATTCK Matrix For EnterpriseNuryadin Usman Abdurrahim AsSampiti IINo ratings yet
- Defense EvasionDocument1 pageDefense EvasionrakivanatanNo ratings yet
- iOS AttackDocument1 pageiOS AttackrakivanatanNo ratings yet
- Mobile Attack Cheat Sheet 1708115239Document1 pageMobile Attack Cheat Sheet 1708115239Joash MacentonNo ratings yet
- MITRE ATT&CK Wheel of FortuneDocument122 pagesMITRE ATT&CK Wheel of FortuneMilin ShahNo ratings yet
- Mitre Overview 2021-01-16Document5 pagesMitre Overview 2021-01-16iaas labsNo ratings yet
- Ipam Automation For Cloud With Vmware Vcloud Automation Center & Infoblox DdiDocument21 pagesIpam Automation For Cloud With Vmware Vcloud Automation Center & Infoblox Ddialnaddaf7546No ratings yet
- Automated For Snowflake: Security & PrivacyDocument2 pagesAutomated For Snowflake: Security & PrivacyResolehtmai DonNo ratings yet
- XWorm RAT MalwareDocument2 pagesXWorm RAT MalwareFarah YaminNo ratings yet
- Account Security ChecklistDocument15 pagesAccount Security ChecklistRyalapeta Venu YadavNo ratings yet
- Lista de Tablas GPDocument196 pagesLista de Tablas GPNatalia MoragaNo ratings yet
- CiTRANS 600 Series PTN Product Configuration Guide - Login - Quality of Service PDFDocument129 pagesCiTRANS 600 Series PTN Product Configuration Guide - Login - Quality of Service PDFakishtaiahNo ratings yet
- TTC Office365 D A01.Service IntroductionDocument52 pagesTTC Office365 D A01.Service Introductionfeed BackNo ratings yet
- 2017-04-18 ZKTime Web 2.0 Software IntoductionDocument37 pages2017-04-18 ZKTime Web 2.0 Software IntoductionCompraVentaNo ratings yet
- Oracle Transportation and Global Trade Management 20A Release NotesDocument125 pagesOracle Transportation and Global Trade Management 20A Release NotesRahul Harsh RajéNo ratings yet
- FAMUGDocument1,994 pagesFAMUGArun ParthasarathyNo ratings yet
- SPPA - T3000 System Administrator: EgyptDocument2 pagesSPPA - T3000 System Administrator: EgyptvishadkapadiaNo ratings yet
- Making Mitre Att&Ck Framework New Hunting Standard: January 2020 SentineloneDocument14 pagesMaking Mitre Att&Ck Framework New Hunting Standard: January 2020 SentineloneShreekanth MuraliNo ratings yet
- Cloud Computing NETW1009: Course Instructor: Dr. - Ing. Maggie MashalyDocument34 pagesCloud Computing NETW1009: Course Instructor: Dr. - Ing. Maggie MashalyAhmed GramerNo ratings yet
- EMP056EA-02 (Trending)Document39 pagesEMP056EA-02 (Trending)scottt_84No ratings yet
- Tally PrimeDocument2 pagesTally PrimeMohd ShahidNo ratings yet
- Windows MatrixDocument1 pageWindows MatrixfolalikNo ratings yet
- t3tws3tws Overview r15pdf PDFDocument13 pagest3tws3tws Overview r15pdf PDFtranhieu5959100% (1)
- Opentouch Suite: Cloud Connect Operation OverviewDocument14 pagesOpentouch Suite: Cloud Connect Operation Overviewissa galalNo ratings yet
- Alibaba Cloud Apsara Stack Enterprise V3 12 0 MaxCompute User GuideDocument705 pagesAlibaba Cloud Apsara Stack Enterprise V3 12 0 MaxCompute User GuidekaptriNo ratings yet
- Softing Easy Way Send Plant Floor PLC Data To IIoT Apps Aug 2022Document13 pagesSofting Easy Way Send Plant Floor PLC Data To IIoT Apps Aug 2022Erwin RojasNo ratings yet
- Ebs Enterprise Command Center Quick Start Guide PDFDocument6 pagesEbs Enterprise Command Center Quick Start Guide PDFMaqbulhusenNo ratings yet
- Business Strategy and Scrum Using Wardley Mapping WelcomeDocument14 pagesBusiness Strategy and Scrum Using Wardley Mapping WelcomeJohnNo ratings yet
- CSA - TTPs of Indicted APT40 Actors Associated With China MSS Hainan State Security DepartmentDocument14 pagesCSA - TTPs of Indicted APT40 Actors Associated With China MSS Hainan State Security Departmentmalikjavaid093No ratings yet
- Building An Enterprise CMDB For ITSM-Progress EnergyDocument100 pagesBuilding An Enterprise CMDB For ITSM-Progress Energyshivani_marwahaNo ratings yet
- T24 Close of Business (COB) : 1 Free Org Charß MakerDocument17 pagesT24 Close of Business (COB) : 1 Free Org Charß Makervikki chowdaryNo ratings yet
- CPQ-1824586 OrderingDocumentDocument12 pagesCPQ-1824586 OrderingDocumentsjNo ratings yet
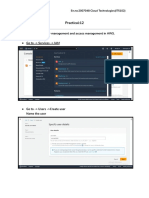
- Practical 12 Cloud PDFDocument7 pagesPractical 12 Cloud PDFJZNIXCNo ratings yet
- Credential AccessDocument1 pageCredential AccessNuryadin Usman Abdurrahim AsSampiti IINo ratings yet
- Alibaba Cloud Apsara Stack Enterprise 2105Document161 pagesAlibaba Cloud Apsara Stack Enterprise 2105Badhrul SalmanNo ratings yet
- CB en DI Cookbook DataIntegrationDocument52 pagesCB en DI Cookbook DataIntegrationAnonymous xMYE0TiNBc100% (1)
- Skylight Solution Overview June 2019Document14 pagesSkylight Solution Overview June 2019CharlesNo ratings yet
- XBRL US Pacific Rim Workshop Database and Business Intelligence Workshop Karen Hsu Director Product Marketing, InformaticaDocument18 pagesXBRL US Pacific Rim Workshop Database and Business Intelligence Workshop Karen Hsu Director Product Marketing, InformaticaUmapathi BaskarNo ratings yet
- MITRE LockBit 3.0Document2 pagesMITRE LockBit 3.0kuronekonokanojoNo ratings yet
- SSS Deep Dive - MOPDocument1 pageSSS Deep Dive - MOPAditya NarayanNo ratings yet
- Leading Workplace Insurer Automates IP Address ManagementDocument2 pagesLeading Workplace Insurer Automates IP Address ManagementPaulo RodriguesNo ratings yet
- Slides Introduction of Blockchain Recap + Q&ADocument9 pagesSlides Introduction of Blockchain Recap + Q&AZulaika AliNo ratings yet
- LTIMindtree - Cloud Capabilities 20240417Document20 pagesLTIMindtree - Cloud Capabilities 20240417asma.abbouzNo ratings yet
- Company Profile - Buyer OoredooDocument7 pagesCompany Profile - Buyer OoredooZHaneeNo ratings yet
- Tenableio and Thycotic Integration GuideDocument16 pagesTenableio and Thycotic Integration GuidedfgdfsgNo ratings yet
- Solaris SCSAIDocument24 pagesSolaris SCSAIsrinivasNo ratings yet
- 2a. Administration and Implementation TasksDocument31 pages2a. Administration and Implementation TasksCarlos XistraNo ratings yet
- Hikvision T&A Integrate SolutionDocument28 pagesHikvision T&A Integrate SolutionsoftwebprojectsNo ratings yet
- Value of EnterpriseDocument1 pageValue of EnterpriseAnwesh Kumar MaddikuntaNo ratings yet
- How To Integrate and Manage Cloud and Traditional Services - Living in A World of Hybrid ITDocument20 pagesHow To Integrate and Manage Cloud and Traditional Services - Living in A World of Hybrid ITpantmukulNo ratings yet
- If the Cloud Is a Game Changer, Who's Playing?From EverandIf the Cloud Is a Game Changer, Who's Playing?Rating: 4 out of 5 stars4/5 (1)
- iOS AttackDocument1 pageiOS AttackrakivanatanNo ratings yet
- T Rec Y.2774 201903 I!!pdf eDocument22 pagesT Rec Y.2774 201903 I!!pdf erakivanatanNo ratings yet
- An Adaptive Fusion Framework For Fault-Tolerant MuDocument192 pagesAn Adaptive Fusion Framework For Fault-Tolerant MurakivanatanNo ratings yet
- Windows Internet Key (IKE) Remote Code Excusion Vulnerability AnalysisDocument11 pagesWindows Internet Key (IKE) Remote Code Excusion Vulnerability AnalysisrakivanatanNo ratings yet
- Palo Alto Os Release NotesDocument366 pagesPalo Alto Os Release NotesrakivanatanNo ratings yet
- What Is An SBC?: Alan D. Percy November 2018Document36 pagesWhat Is An SBC?: Alan D. Percy November 2018rakivanatanNo ratings yet
- Cyber Threat Intelligence Sharing: Lessons Learned, Observamons, RecommendamonsDocument18 pagesCyber Threat Intelligence Sharing: Lessons Learned, Observamons, RecommendamonsrakivanatanNo ratings yet
- Sbx908 Ds RevzjDocument8 pagesSbx908 Ds RevzjrakivanatanNo ratings yet
- 6500 Data Sheet PDFDocument5 pages6500 Data Sheet PDFrakivanatanNo ratings yet
- Cisco Catalyst 6500 Series Supervisor Engine 2T: Product OverviewDocument8 pagesCisco Catalyst 6500 Series Supervisor Engine 2T: Product OverviewrakivanatanNo ratings yet
- Cisco Catalyst 6500 Series 10 Gigabit Ethernet Modules: Data SheetDocument7 pagesCisco Catalyst 6500 Series 10 Gigabit Ethernet Modules: Data SheetrakivanatanNo ratings yet
- s71500 Structure and Use of The PLC Memory Function Manual en-US en-USDocument82 pagess71500 Structure and Use of The PLC Memory Function Manual en-US en-USTonheca RockkNo ratings yet
- Microprocessor: Motorola 6800Document19 pagesMicroprocessor: Motorola 6800Anupam SinghNo ratings yet
- Tech Talk Understand The Benefits of Wi Sun For Long Range Industrial Applications JapaneseDocument26 pagesTech Talk Understand The Benefits of Wi Sun For Long Range Industrial Applications JapanesefabcostaNo ratings yet
- MCQ Based On SeriesDocument9 pagesMCQ Based On SeriessubbuNo ratings yet
- Overview SCADADocument13 pagesOverview SCADAJustin NovitaNo ratings yet
- EC302Document23 pagesEC302api-3853441No ratings yet
- Battery Calibration - Li IonDocument4 pagesBattery Calibration - Li IonHugh Ell - auNo ratings yet
- MS-16GC Disassembly GuideDocument18 pagesMS-16GC Disassembly GuideAriyawira BinuiNo ratings yet
- Secure QR Code System: Raed M. Bani-Hani Yarub A. Wahsheh Mohammad B. Al-SarhanDocument6 pagesSecure QR Code System: Raed M. Bani-Hani Yarub A. Wahsheh Mohammad B. Al-SarhanAnonymous HeroNo ratings yet
- D77766GC10 1080544 UsDocument3 pagesD77766GC10 1080544 UsvineetNo ratings yet
- Ws c2960 48tc L DatasheetDocument5 pagesWs c2960 48tc L DatasheetMasterB.E.RNo ratings yet
- Full Custom Design Flow For A Transimpedance Amplifier Using Cadence VirtuosoDocument6 pagesFull Custom Design Flow For A Transimpedance Amplifier Using Cadence VirtuosoRajasekar PanneerselvamNo ratings yet
- M877 Brochure 02-25-12Document2 pagesM877 Brochure 02-25-12Nudin SeninNo ratings yet
- Performance Analysis and Optimization For BPC 10Document8 pagesPerformance Analysis and Optimization For BPC 10KalyanNo ratings yet
- Motherboard, Motherboard Contents and Its FunctionsDocument7 pagesMotherboard, Motherboard Contents and Its FunctionsLavanya_123No ratings yet
- Ad1939 PDFDocument32 pagesAd1939 PDFMax MaierNo ratings yet
- How To Bypass LCD TV Inverter BoardDocument5 pagesHow To Bypass LCD TV Inverter BoardMecael DesuyoNo ratings yet
- Object Oriented Programming LabDocument33 pagesObject Oriented Programming LabTakfirul Alam DisneyNo ratings yet
- 8I845GVM RZ Rev.1.0 0Document34 pages8I845GVM RZ Rev.1.0 0zokiNo ratings yet
- VHDL Processes: Cwru Eecs 318Document24 pagesVHDL Processes: Cwru Eecs 318KarThikNo ratings yet
- Cisco 400G QSFP-DD High-Power (Bright) Optical Module Data SheetDocument8 pagesCisco 400G QSFP-DD High-Power (Bright) Optical Module Data Sheetbruna.tobiakaNo ratings yet
- Mbe Fix32Document5 pagesMbe Fix32Cristina MonteiroNo ratings yet
- Multimedia Devices: in This Chapter You Will LearnDocument69 pagesMultimedia Devices: in This Chapter You Will LearnJakim LopezNo ratings yet
- CBCS ComputerDocument82 pagesCBCS ComputerDeep Narayan PaulNo ratings yet
- Unity Quantum Training ManualDocument194 pagesUnity Quantum Training ManualAqeel Joud AlhujailiNo ratings yet
- Ieee Vlsi Titles 2021 2022: S. No Domain Title YearDocument4 pagesIeee Vlsi Titles 2021 2022: S. No Domain Title YearMadhanDhonianNo ratings yet
- Computer & IT-1-10.#Posted by Kabil MahmudDocument8 pagesComputer & IT-1-10.#Posted by Kabil MahmudMd. Aminul HaqueNo ratings yet
- Fujitsu CELSIUS M470 Workstation: Data SheetDocument7 pagesFujitsu CELSIUS M470 Workstation: Data SheetIbrahim GamalNo ratings yet
- 47Lm7600 Interconnect Diagram: P702 N/C Backlight B+ 60V LD701 ErrorDocument1 page47Lm7600 Interconnect Diagram: P702 N/C Backlight B+ 60V LD701 Errorruben mapaloNo ratings yet
Cloud Matrix
Cloud Matrix
Uploaded by
Nuryadin Usman Abdurrahim AsSampiti IICopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Cloud Matrix
Cloud Matrix
Uploaded by
Nuryadin Usman Abdurrahim AsSampiti IICopyright:
Available Formats
MITRE ATT&CK-Cloud Matrix ID:TA0001 Initial Access ID:TA0002 Execution
T1189 - Drive-by Comprise T1648 - Services Execution
T1190 - Exploit Public-Facing Application T1204 - User Execution
T1566 - Phishing Malicious Image
Spearphishing Link
T1199 - Trusted Relationship
T1078 - Valid Accounts
Default Accounts
Cloud Accounts
ID:TA0005 Defense Evasion ID:TA0004 Privilege Escalation ID:TA0003 Persistence
T1484 - Domain Policy Modification T1484 - Domain Policy Modification T1098 - Account Manipulation
Domain Trust Modification Domain Trust Modification Additional Cloud Credentials
T1564 - Hide Artifacts T1546 - Event Triggered Execution Additional Email Delegate Permissions
Email Hiding Rules T1078 - Valid Accounts Additional Cloud Roles
T1562 - Impair Defenses Default Accounts SSH Authorized Keys
Device Registration
Disable or Modify Tools Cloud Accounts
T1136 - Create Account
Disable or Modify Cloud Firewall
Disable Cloud Logs Cloud Account
T1546 - Event Triggered Execution
T1070 - Indicator Removal
T1525 - Implant Internal Image
Clear Mailbox Data
T1556 - Modify Authentication Process
T1556 - Modify Authentication Process
Multi-Factor Authentication
Multi-Factor Authentication
Hybrid Identity
Hybrid Identity
T1137 - Office Application Startup
T1578 - Modify Cloud Compute Infrastructure
Office Template Macros
Create Snapshot
Office Test
Create Cloud Instance
Outlook Forms
Delete Cloud Instance
Outlook Home Page
Revert Cloud Instance
Outlook Rules
T1535 - Unused/Unsupported Cloud Regions
Add-ins
T1550 - Use Alternate Authentication Material
T1078 - Valid Accounts
Application Access Token
Default Accounts
Web Session Cookie
Cloud Accounts
T1078 - Valid Accounts
Default Accounts
Cloud Accounts
ID:TA0006 Credential Access ID:TA0007 Discovery
T1110 - Brute Force T1087 - Account Discovery
Password Guessing Email Account
Password Cracking Cloud Account
Password Spraying T1580 - Cloud Infrastructure Discovery
Credential Stuffing T1538 - Cloud Service Dashboard
T1606 - Forge Web Credentials T1526 - Cloud Service Discovery
Web Cookies T1619 - Cloud Storage Object Discovery
SAML Tokens T1046 - Network Service Discovery
T1040 - Network Sniffing
T1556- Modify Authentication Process
T1201 - Password Policy Discovery
Multi-Factor Authentication
T1069 - Permission Groups Discovery
Hybrid Identity
Cloud Groups
T1621 - Multi-Factor Authentication Request Generation
T1040 - Network Sniffing T1518 - Software Discovery
T1528 - Steal Application Access Token Security Software Discovery
T1649 - Steal or Forge Authentication Certificates T1082 - System Information Discovery
T1539 - Steal Web Session Cookie T1614 - System Location Discovery
T1552 - Unsecured Credentials T1049 - System Network Connections Discovery
Credentials In Files
Cloud Instance Metadata API
ID:TA0009 Collection ID:TA0008 Lateral Movement
T1119 - Automated Collection T1534 - Internal Spearphishing
T1530 - Data from Cloud Storage T1080 - Taint Shared Content
T1213 - Data from Information Repositories T1550 - Use Alternate Authentication Material
Confluence Application Access Token
Sharepoint Web Session Cookie
Code Repositories
T1074 - Data Staged
Remote Data Staging
T1114 - Email Collection
Remote Email Collection
Email Forwarding Rule
ID:TA0010 Exfiltration ID:TA0040 Impact
T1537 - Transfer Data to Cloud Account T1531 - Account Access Removal
T1485 - Data Destruction
T1486 - Data Encrypted for Impact
T1491 - Defacement
@hackinarticles External Defacement
T1499 - Endpoint Denial of Service
https://github.com/Ignitetechnologies
Service Exhaustion Flood
Application Exhaustion Flood
https://in.linkedin.com/company/hackingarticles Application or System Exploitation
T1498 - Network Denial of Service
Direct Network Flood
Reflection Amplification
T1496- Resource Hijacking
You might also like
- CompTIA Server+ Certification All-in-One Exam Guide, Second Edition (Exam SK0-005)From EverandCompTIA Server+ Certification All-in-One Exam Guide, Second Edition (Exam SK0-005)No ratings yet
- Introduction To TeradataDocument51 pagesIntroduction To Teradataraghavendra.nieNo ratings yet
- Cyber Security Interview QuestionsDocument16 pagesCyber Security Interview QuestionsrakivanatanNo ratings yet
- Integration Framework Overview r15 PDFDocument17 pagesIntegration Framework Overview r15 PDFigomez100% (1)
- T24 Close of Business (COB) - T24 HelperDocument17 pagesT24 Close of Business (COB) - T24 HelperNett2k100% (9)
- Containers MatrixDocument1 pageContainers MatrixNuryadin Usman Abdurrahim AsSampiti IINo ratings yet
- Network MatrixDocument1 pageNetwork MatrixrakivanatanNo ratings yet
- Mitre Att&ck v9Document22 pagesMitre Att&ck v9Fabiano DiscacciatiNo ratings yet
- Conti (s0575)Document5 pagesConti (s0575)anup.tilekar.86No ratings yet
- Peter O & Alessandra Di Carlo - Lessons From The Frontlines - Ransomware Attacks, New Techniques and Old TricksDocument23 pagesPeter O & Alessandra Di Carlo - Lessons From The Frontlines - Ransomware Attacks, New Techniques and Old TricksFranklin CordeiroNo ratings yet
- ATTCK Matrix For EnterpriseDocument1 pageATTCK Matrix For EnterpriseNuryadin Usman Abdurrahim AsSampiti IINo ratings yet
- Defense EvasionDocument1 pageDefense EvasionrakivanatanNo ratings yet
- iOS AttackDocument1 pageiOS AttackrakivanatanNo ratings yet
- Mobile Attack Cheat Sheet 1708115239Document1 pageMobile Attack Cheat Sheet 1708115239Joash MacentonNo ratings yet
- MITRE ATT&CK Wheel of FortuneDocument122 pagesMITRE ATT&CK Wheel of FortuneMilin ShahNo ratings yet
- Mitre Overview 2021-01-16Document5 pagesMitre Overview 2021-01-16iaas labsNo ratings yet
- Ipam Automation For Cloud With Vmware Vcloud Automation Center & Infoblox DdiDocument21 pagesIpam Automation For Cloud With Vmware Vcloud Automation Center & Infoblox Ddialnaddaf7546No ratings yet
- Automated For Snowflake: Security & PrivacyDocument2 pagesAutomated For Snowflake: Security & PrivacyResolehtmai DonNo ratings yet
- XWorm RAT MalwareDocument2 pagesXWorm RAT MalwareFarah YaminNo ratings yet
- Account Security ChecklistDocument15 pagesAccount Security ChecklistRyalapeta Venu YadavNo ratings yet
- Lista de Tablas GPDocument196 pagesLista de Tablas GPNatalia MoragaNo ratings yet
- CiTRANS 600 Series PTN Product Configuration Guide - Login - Quality of Service PDFDocument129 pagesCiTRANS 600 Series PTN Product Configuration Guide - Login - Quality of Service PDFakishtaiahNo ratings yet
- TTC Office365 D A01.Service IntroductionDocument52 pagesTTC Office365 D A01.Service Introductionfeed BackNo ratings yet
- 2017-04-18 ZKTime Web 2.0 Software IntoductionDocument37 pages2017-04-18 ZKTime Web 2.0 Software IntoductionCompraVentaNo ratings yet
- Oracle Transportation and Global Trade Management 20A Release NotesDocument125 pagesOracle Transportation and Global Trade Management 20A Release NotesRahul Harsh RajéNo ratings yet
- FAMUGDocument1,994 pagesFAMUGArun ParthasarathyNo ratings yet
- SPPA - T3000 System Administrator: EgyptDocument2 pagesSPPA - T3000 System Administrator: EgyptvishadkapadiaNo ratings yet
- Making Mitre Att&Ck Framework New Hunting Standard: January 2020 SentineloneDocument14 pagesMaking Mitre Att&Ck Framework New Hunting Standard: January 2020 SentineloneShreekanth MuraliNo ratings yet
- Cloud Computing NETW1009: Course Instructor: Dr. - Ing. Maggie MashalyDocument34 pagesCloud Computing NETW1009: Course Instructor: Dr. - Ing. Maggie MashalyAhmed GramerNo ratings yet
- EMP056EA-02 (Trending)Document39 pagesEMP056EA-02 (Trending)scottt_84No ratings yet
- Tally PrimeDocument2 pagesTally PrimeMohd ShahidNo ratings yet
- Windows MatrixDocument1 pageWindows MatrixfolalikNo ratings yet
- t3tws3tws Overview r15pdf PDFDocument13 pagest3tws3tws Overview r15pdf PDFtranhieu5959100% (1)
- Opentouch Suite: Cloud Connect Operation OverviewDocument14 pagesOpentouch Suite: Cloud Connect Operation Overviewissa galalNo ratings yet
- Alibaba Cloud Apsara Stack Enterprise V3 12 0 MaxCompute User GuideDocument705 pagesAlibaba Cloud Apsara Stack Enterprise V3 12 0 MaxCompute User GuidekaptriNo ratings yet
- Softing Easy Way Send Plant Floor PLC Data To IIoT Apps Aug 2022Document13 pagesSofting Easy Way Send Plant Floor PLC Data To IIoT Apps Aug 2022Erwin RojasNo ratings yet
- Ebs Enterprise Command Center Quick Start Guide PDFDocument6 pagesEbs Enterprise Command Center Quick Start Guide PDFMaqbulhusenNo ratings yet
- Business Strategy and Scrum Using Wardley Mapping WelcomeDocument14 pagesBusiness Strategy and Scrum Using Wardley Mapping WelcomeJohnNo ratings yet
- CSA - TTPs of Indicted APT40 Actors Associated With China MSS Hainan State Security DepartmentDocument14 pagesCSA - TTPs of Indicted APT40 Actors Associated With China MSS Hainan State Security Departmentmalikjavaid093No ratings yet
- Building An Enterprise CMDB For ITSM-Progress EnergyDocument100 pagesBuilding An Enterprise CMDB For ITSM-Progress Energyshivani_marwahaNo ratings yet
- T24 Close of Business (COB) : 1 Free Org Charß MakerDocument17 pagesT24 Close of Business (COB) : 1 Free Org Charß Makervikki chowdaryNo ratings yet
- CPQ-1824586 OrderingDocumentDocument12 pagesCPQ-1824586 OrderingDocumentsjNo ratings yet
- Practical 12 Cloud PDFDocument7 pagesPractical 12 Cloud PDFJZNIXCNo ratings yet
- Credential AccessDocument1 pageCredential AccessNuryadin Usman Abdurrahim AsSampiti IINo ratings yet
- Alibaba Cloud Apsara Stack Enterprise 2105Document161 pagesAlibaba Cloud Apsara Stack Enterprise 2105Badhrul SalmanNo ratings yet
- CB en DI Cookbook DataIntegrationDocument52 pagesCB en DI Cookbook DataIntegrationAnonymous xMYE0TiNBc100% (1)
- Skylight Solution Overview June 2019Document14 pagesSkylight Solution Overview June 2019CharlesNo ratings yet
- XBRL US Pacific Rim Workshop Database and Business Intelligence Workshop Karen Hsu Director Product Marketing, InformaticaDocument18 pagesXBRL US Pacific Rim Workshop Database and Business Intelligence Workshop Karen Hsu Director Product Marketing, InformaticaUmapathi BaskarNo ratings yet
- MITRE LockBit 3.0Document2 pagesMITRE LockBit 3.0kuronekonokanojoNo ratings yet
- SSS Deep Dive - MOPDocument1 pageSSS Deep Dive - MOPAditya NarayanNo ratings yet
- Leading Workplace Insurer Automates IP Address ManagementDocument2 pagesLeading Workplace Insurer Automates IP Address ManagementPaulo RodriguesNo ratings yet
- Slides Introduction of Blockchain Recap + Q&ADocument9 pagesSlides Introduction of Blockchain Recap + Q&AZulaika AliNo ratings yet
- LTIMindtree - Cloud Capabilities 20240417Document20 pagesLTIMindtree - Cloud Capabilities 20240417asma.abbouzNo ratings yet
- Company Profile - Buyer OoredooDocument7 pagesCompany Profile - Buyer OoredooZHaneeNo ratings yet
- Tenableio and Thycotic Integration GuideDocument16 pagesTenableio and Thycotic Integration GuidedfgdfsgNo ratings yet
- Solaris SCSAIDocument24 pagesSolaris SCSAIsrinivasNo ratings yet
- 2a. Administration and Implementation TasksDocument31 pages2a. Administration and Implementation TasksCarlos XistraNo ratings yet
- Hikvision T&A Integrate SolutionDocument28 pagesHikvision T&A Integrate SolutionsoftwebprojectsNo ratings yet
- Value of EnterpriseDocument1 pageValue of EnterpriseAnwesh Kumar MaddikuntaNo ratings yet
- How To Integrate and Manage Cloud and Traditional Services - Living in A World of Hybrid ITDocument20 pagesHow To Integrate and Manage Cloud and Traditional Services - Living in A World of Hybrid ITpantmukulNo ratings yet
- If the Cloud Is a Game Changer, Who's Playing?From EverandIf the Cloud Is a Game Changer, Who's Playing?Rating: 4 out of 5 stars4/5 (1)
- iOS AttackDocument1 pageiOS AttackrakivanatanNo ratings yet
- T Rec Y.2774 201903 I!!pdf eDocument22 pagesT Rec Y.2774 201903 I!!pdf erakivanatanNo ratings yet
- An Adaptive Fusion Framework For Fault-Tolerant MuDocument192 pagesAn Adaptive Fusion Framework For Fault-Tolerant MurakivanatanNo ratings yet
- Windows Internet Key (IKE) Remote Code Excusion Vulnerability AnalysisDocument11 pagesWindows Internet Key (IKE) Remote Code Excusion Vulnerability AnalysisrakivanatanNo ratings yet
- Palo Alto Os Release NotesDocument366 pagesPalo Alto Os Release NotesrakivanatanNo ratings yet
- What Is An SBC?: Alan D. Percy November 2018Document36 pagesWhat Is An SBC?: Alan D. Percy November 2018rakivanatanNo ratings yet
- Cyber Threat Intelligence Sharing: Lessons Learned, Observamons, RecommendamonsDocument18 pagesCyber Threat Intelligence Sharing: Lessons Learned, Observamons, RecommendamonsrakivanatanNo ratings yet
- Sbx908 Ds RevzjDocument8 pagesSbx908 Ds RevzjrakivanatanNo ratings yet
- 6500 Data Sheet PDFDocument5 pages6500 Data Sheet PDFrakivanatanNo ratings yet
- Cisco Catalyst 6500 Series Supervisor Engine 2T: Product OverviewDocument8 pagesCisco Catalyst 6500 Series Supervisor Engine 2T: Product OverviewrakivanatanNo ratings yet
- Cisco Catalyst 6500 Series 10 Gigabit Ethernet Modules: Data SheetDocument7 pagesCisco Catalyst 6500 Series 10 Gigabit Ethernet Modules: Data SheetrakivanatanNo ratings yet
- s71500 Structure and Use of The PLC Memory Function Manual en-US en-USDocument82 pagess71500 Structure and Use of The PLC Memory Function Manual en-US en-USTonheca RockkNo ratings yet
- Microprocessor: Motorola 6800Document19 pagesMicroprocessor: Motorola 6800Anupam SinghNo ratings yet
- Tech Talk Understand The Benefits of Wi Sun For Long Range Industrial Applications JapaneseDocument26 pagesTech Talk Understand The Benefits of Wi Sun For Long Range Industrial Applications JapanesefabcostaNo ratings yet
- MCQ Based On SeriesDocument9 pagesMCQ Based On SeriessubbuNo ratings yet
- Overview SCADADocument13 pagesOverview SCADAJustin NovitaNo ratings yet
- EC302Document23 pagesEC302api-3853441No ratings yet
- Battery Calibration - Li IonDocument4 pagesBattery Calibration - Li IonHugh Ell - auNo ratings yet
- MS-16GC Disassembly GuideDocument18 pagesMS-16GC Disassembly GuideAriyawira BinuiNo ratings yet
- Secure QR Code System: Raed M. Bani-Hani Yarub A. Wahsheh Mohammad B. Al-SarhanDocument6 pagesSecure QR Code System: Raed M. Bani-Hani Yarub A. Wahsheh Mohammad B. Al-SarhanAnonymous HeroNo ratings yet
- D77766GC10 1080544 UsDocument3 pagesD77766GC10 1080544 UsvineetNo ratings yet
- Ws c2960 48tc L DatasheetDocument5 pagesWs c2960 48tc L DatasheetMasterB.E.RNo ratings yet
- Full Custom Design Flow For A Transimpedance Amplifier Using Cadence VirtuosoDocument6 pagesFull Custom Design Flow For A Transimpedance Amplifier Using Cadence VirtuosoRajasekar PanneerselvamNo ratings yet
- M877 Brochure 02-25-12Document2 pagesM877 Brochure 02-25-12Nudin SeninNo ratings yet
- Performance Analysis and Optimization For BPC 10Document8 pagesPerformance Analysis and Optimization For BPC 10KalyanNo ratings yet
- Motherboard, Motherboard Contents and Its FunctionsDocument7 pagesMotherboard, Motherboard Contents and Its FunctionsLavanya_123No ratings yet
- Ad1939 PDFDocument32 pagesAd1939 PDFMax MaierNo ratings yet
- How To Bypass LCD TV Inverter BoardDocument5 pagesHow To Bypass LCD TV Inverter BoardMecael DesuyoNo ratings yet
- Object Oriented Programming LabDocument33 pagesObject Oriented Programming LabTakfirul Alam DisneyNo ratings yet
- 8I845GVM RZ Rev.1.0 0Document34 pages8I845GVM RZ Rev.1.0 0zokiNo ratings yet
- VHDL Processes: Cwru Eecs 318Document24 pagesVHDL Processes: Cwru Eecs 318KarThikNo ratings yet
- Cisco 400G QSFP-DD High-Power (Bright) Optical Module Data SheetDocument8 pagesCisco 400G QSFP-DD High-Power (Bright) Optical Module Data Sheetbruna.tobiakaNo ratings yet
- Mbe Fix32Document5 pagesMbe Fix32Cristina MonteiroNo ratings yet
- Multimedia Devices: in This Chapter You Will LearnDocument69 pagesMultimedia Devices: in This Chapter You Will LearnJakim LopezNo ratings yet
- CBCS ComputerDocument82 pagesCBCS ComputerDeep Narayan PaulNo ratings yet
- Unity Quantum Training ManualDocument194 pagesUnity Quantum Training ManualAqeel Joud AlhujailiNo ratings yet
- Ieee Vlsi Titles 2021 2022: S. No Domain Title YearDocument4 pagesIeee Vlsi Titles 2021 2022: S. No Domain Title YearMadhanDhonianNo ratings yet
- Computer & IT-1-10.#Posted by Kabil MahmudDocument8 pagesComputer & IT-1-10.#Posted by Kabil MahmudMd. Aminul HaqueNo ratings yet
- Fujitsu CELSIUS M470 Workstation: Data SheetDocument7 pagesFujitsu CELSIUS M470 Workstation: Data SheetIbrahim GamalNo ratings yet
- 47Lm7600 Interconnect Diagram: P702 N/C Backlight B+ 60V LD701 ErrorDocument1 page47Lm7600 Interconnect Diagram: P702 N/C Backlight B+ 60V LD701 Errorruben mapaloNo ratings yet