Professional Documents
Culture Documents
0 ratings0% found this document useful (0 votes)
2 views5-Ex.4b - VPN-22-03-2024
5-Ex.4b - VPN-22-03-2024
Uploaded by
Shreyansh ChaubeyCopyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
You might also like
- Network Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityFrom EverandNetwork Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityNo ratings yet
- Enterprise Supply Planning (ESP) : by Venkata GopalaDocument33 pagesEnterprise Supply Planning (ESP) : by Venkata Gopalagopal_svsemails8998No ratings yet
- 7.1.2.4 Packet Tracer - Configuring VPNs (Optional) InstructionsDocument6 pages7.1.2.4 Packet Tracer - Configuring VPNs (Optional) InstructionsParitosh KumarNo ratings yet
- 7.3.2.8 Packet Tracer - Configuring GRE Over IPsec InstructionsDocument5 pages7.3.2.8 Packet Tracer - Configuring GRE Over IPsec InstructionsSergio CastañedaNo ratings yet
- 8.7.1.4 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN Using CLI - InstructorDocument5 pages8.7.1.4 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN Using CLI - InstructorSalem TrabelsiNo ratings yet
- 8.4.1.2 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN Using CLIDocument5 pages8.4.1.2 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN Using CLITalha Ur RehmanNo ratings yet
- Lab 2-1 EIGRP Configuration, Bandwidth, and Adjacencies: Learning ObjectivesDocument12 pagesLab 2-1 EIGRP Configuration, Bandwidth, and Adjacencies: Learning ObjectivesSergiy KalmukNo ratings yet
- Lab 17 - Configuring CUBE H.323-To-H.323 VoIP ConnectionsDocument9 pagesLab 17 - Configuring CUBE H.323-To-H.323 VoIP ConnectionsdjmckcNo ratings yet
- Microcontrollerprogramming Msp430fr2433andmsp430fr5994 Part2 PDFDocument301 pagesMicrocontrollerprogramming Msp430fr2433andmsp430fr5994 Part2 PDFAndrei Lazar100% (1)
- Yasser Auda CCIEv5 WorkbookDocument26 pagesYasser Auda CCIEv5 WorkbookphamvanhaNo ratings yet
- Technical ReportDocument19 pagesTechnical ReportUsmanNo ratings yet
- Configure and Verify A Site-To-Site IPsec VPN Using CLIDocument6 pagesConfigure and Verify A Site-To-Site IPsec VPN Using CLIMilošKovačevićNo ratings yet
- Configure and Verify A Site To Site IPsec VPN Using CLIDocument4 pagesConfigure and Verify A Site To Site IPsec VPN Using CLICristhian HadesNo ratings yet
- Gre Over Ipsec VPN: Lab TopologyDocument8 pagesGre Over Ipsec VPN: Lab TopologyyasserNo ratings yet
- IPSec VPNDocument5 pagesIPSec VPNcciersmanNo ratings yet
- 20.1.2 Lab Configure Secure DMVPN TunnelsDocument11 pages20.1.2 Lab Configure Secure DMVPN Tunnelshassa nestor theraNo ratings yet
- 7.3.2.8 Packet Tracer - Configuring GRE Over IPsec InstructionsDocument5 pages7.3.2.8 Packet Tracer - Configuring GRE Over IPsec InstructionsEncikPandaSiriusNo ratings yet
- 16.2.2 Packet Tracer - Configure and Verify A Site-to-Site IPsec VPN Using CLI - ITExamAnswersDocument6 pages16.2.2 Packet Tracer - Configure and Verify A Site-to-Site IPsec VPN Using CLI - ITExamAnswersimen loussaiefNo ratings yet
- Lab VPNDocument9 pagesLab VPNhung kungNo ratings yet
- Part 1: Configure Ipsec Parameters On R1: Version CommandDocument3 pagesPart 1: Configure Ipsec Parameters On R1: Version CommandArun TSNo ratings yet
- Discovery 17: Configure Static VTI Point-to-Point TunnelsDocument5 pagesDiscovery 17: Configure Static VTI Point-to-Point TunnelsIonut StanciuNo ratings yet
- Ipsec On Huawei Ar Router PDFDocument5 pagesIpsec On Huawei Ar Router PDFHussein DhafanNo ratings yet
- 19.5.5 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN - ITExamAnswersDocument5 pages19.5.5 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN - ITExamAnswersAna Maria Citlali Diaz HernandezNo ratings yet
- Lab EIGRP 2Document15 pagesLab EIGRP 2Danny Ricce EnriqueNo ratings yet
- EIGRP LAB TrickDocument20 pagesEIGRP LAB Trickziad Al-showaiterNo ratings yet
- Lab Cisco VPN-GenericDocument2 pagesLab Cisco VPN-Genericbliss21100% (5)
- Configuring A Cisco 827 For Pppoe With VPN Ipsec Nat OverloadingDocument9 pagesConfiguring A Cisco 827 For Pppoe With VPN Ipsec Nat OverloadingAndika PajriNo ratings yet
- CCNP1 Lab 2 1 enDocument11 pagesCCNP1 Lab 2 1 enMurtaxa KhanNo ratings yet
- Lan2lan VPNDocument6 pagesLan2lan VPNFelix BlasioNo ratings yet
- Configure and Verify A Site-To-Site IPsec VPN Using CLI AnswesDocument8 pagesConfigure and Verify A Site-To-Site IPsec VPN Using CLI AnswesAkram AliNo ratings yet
- ISAKMP Associations Using RSA KeysDocument4 pagesISAKMP Associations Using RSA Keyssgopal7No ratings yet
- 4.1 4-S2S-IPSecVPN-Tunnel-RouterDocument6 pages4.1 4-S2S-IPSecVPN-Tunnel-Routeramit_post2000No ratings yet
- 4.4.3.4 Lab - Configuring HSRP and GLBPDocument9 pages4.4.3.4 Lab - Configuring HSRP and GLBPLex Schneider0% (1)
- Creacion VPN IPSECDocument2 pagesCreacion VPN IPSECCarlos Amaranti GonzálezNo ratings yet
- 02-Implementing and Verifying EIGRPDocument24 pages02-Implementing and Verifying EIGRPPablo MotaNo ratings yet
- Configuring EIGRP: BSCI Module 2-2 - Implementing and Verifying EIGRPDocument24 pagesConfiguring EIGRP: BSCI Module 2-2 - Implementing and Verifying EIGRPHerlander FaloNo ratings yet
- Configuring HSRP and GLBPDocument9 pagesConfiguring HSRP and GLBPRajwecNo ratings yet
- Lab EIGRP 3Document13 pagesLab EIGRP 3Danny Ricce EnriqueNo ratings yet
- Case Study On Troubleshooting BGP Flaps Over IPSec Using FFTDocument12 pagesCase Study On Troubleshooting BGP Flaps Over IPSec Using FFTRamprasanth RajaNo ratings yet
- Router Vpnclient Pi StickDocument10 pagesRouter Vpnclient Pi Stickjames SpywangNo ratings yet
- S2S Ikev2 Configure-AsaDocument9 pagesS2S Ikev2 Configure-Asahesenzade38No ratings yet
- Site To Site IPSEC VPN Troubleshooting - ImpDocument8 pagesSite To Site IPSEC VPN Troubleshooting - ImpAsifNo ratings yet
- Ipsec TunnelDocument8 pagesIpsec TunnelHimansu Panda625No ratings yet
- Lab - Configure Basic Router Settings: Part 2: Configure Devices and Verify ConnectivityDocument6 pagesLab - Configure Basic Router Settings: Part 2: Configure Devices and Verify ConnectivityJosé Aarón AponteNo ratings yet
- CCNPv6 ROUTE Lab8-2 Manual IPv6 Tunnel EIGRP Student FormDocument6 pagesCCNPv6 ROUTE Lab8-2 Manual IPv6 Tunnel EIGRP Student FormMuvubuka KatimaniNo ratings yet
- Configuring Site To Site IPSec VPN Tunnel Between Cisco RoutersDocument6 pagesConfiguring Site To Site IPSec VPN Tunnel Between Cisco Routerskymk21No ratings yet
- Lab EIGRP 1Document9 pagesLab EIGRP 1Danny Ricce EnriqueNo ratings yet
- IPSec VPN LABDocument7 pagesIPSec VPN LABAparna Garg100% (2)
- Configuring Site To Site IPSec VPN Tunnel Between Cisco RoutersDocument4 pagesConfiguring Site To Site IPSec VPN Tunnel Between Cisco RoutersSuhas KanikarNo ratings yet
- Lab 13.8.1 Configuring A Site-To-Site Ipsec VPN Using Pre-Shared KeysDocument6 pagesLab 13.8.1 Configuring A Site-To-Site Ipsec VPN Using Pre-Shared KeysKishore Reddy KandiNo ratings yet
- IPsec Quick and DirtyDocument4 pagesIPsec Quick and Dirtysgopal7No ratings yet
- Configuring OSPF Brandon&KatieDocument8 pagesConfiguring OSPF Brandon&KatieLuis GonzalezNo ratings yet
- Somativa7 RedesDocument4 pagesSomativa7 RedesmatheuszanellatoNo ratings yet
- Chapter 8 Lab 8-2, Routing Protocol Authentication Topology: Ccnpv7 RouteDocument12 pagesChapter 8 Lab 8-2, Routing Protocol Authentication Topology: Ccnpv7 RoutengangaNo ratings yet
- InteropDocument6 pagesInteropSaurav LodhNo ratings yet
- Lab 7.7.3 Configuring IS-IS Over Frame Relay: AlternateDocument8 pagesLab 7.7.3 Configuring IS-IS Over Frame Relay: AlternateKishore Reddy KandiNo ratings yet
- 5.3.3.2 Lab - Troubleshoot LAN Traffic Using SPANDocument6 pages5.3.3.2 Lab - Troubleshoot LAN Traffic Using SPANYaser Samer0% (6)
- Updated - IPSec VPN Using Cisco Packet TracerDocument9 pagesUpdated - IPSec VPN Using Cisco Packet TracerAnvesh PenkeNo ratings yet
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkFrom EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkNo ratings yet
- Network with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationFrom EverandNetwork with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationNo ratings yet
- LEARN MPLS FROM SCRATCH PART-B: A Beginners guide to next level of networkingFrom EverandLEARN MPLS FROM SCRATCH PART-B: A Beginners guide to next level of networkingNo ratings yet
- ExtensiDocument47 pagesExtensiImam Imam Abadi Ibnu IsmailNo ratings yet
- An5342 Error Correction Code Ecc Management For Internal Memories Protection On stm32h7 Series StmicroelectronicsDocument15 pagesAn5342 Error Correction Code Ecc Management For Internal Memories Protection On stm32h7 Series Stmicroelectronicsnick choiNo ratings yet
- IntroductionDocument9 pagesIntroductiondyke ossyNo ratings yet
- Er330 WW QG 20201014Document28 pagesEr330 WW QG 20201014James DAvisNo ratings yet
- Datasheet Narda FieldmanDocument8 pagesDatasheet Narda FieldmanDaniel Puentes FermoselNo ratings yet
- Cisco ASA High Availability Failover ConfigurationDocument6 pagesCisco ASA High Availability Failover ConfigurationcciersmanNo ratings yet
- ART - MultiVerb Alpha 20 - ManualDocument61 pagesART - MultiVerb Alpha 20 - Manual0_x_0No ratings yet
- A Project Report On..Document39 pagesA Project Report On..Dabhi AnkitaNo ratings yet
- Introduction To Specification LanguageDocument25 pagesIntroduction To Specification LanguageNguyễn Đắc Thiên NgânNo ratings yet
- Mazda Ids-Users-ManualDocument93 pagesMazda Ids-Users-ManualGoulNo ratings yet
- Rajasthan Cooperative Recruitment Board: On-Line Examination - Recruitment of Manager & Sr. ManagerDocument7 pagesRajasthan Cooperative Recruitment Board: On-Line Examination - Recruitment of Manager & Sr. ManagerHardik MehraNo ratings yet
- Graphic Optimizing andDocument10 pagesGraphic Optimizing and贺He沁QinNo ratings yet
- 239CQH Hdmi2 EDIDDocument3 pages239CQH Hdmi2 EDIDZidni IlmanNo ratings yet
- Maintenance and Service Guide: HP 245 G7 Notebook PCDocument91 pagesMaintenance and Service Guide: HP 245 G7 Notebook PCrodrigokfwNo ratings yet
- Deauthentication (Aircrack-Ng)Document4 pagesDeauthentication (Aircrack-Ng)DCLXVINo ratings yet
- Signed Learning Material No. 6 Nature of Codes and CryptographyDocument49 pagesSigned Learning Material No. 6 Nature of Codes and CryptographyAira Mae Quinones OrendainNo ratings yet
- Build A Search Engine For Medium Stories Using Streamlit and Elasticsearch - by ChiaChong - Better ProgrammingDocument19 pagesBuild A Search Engine For Medium Stories Using Streamlit and Elasticsearch - by ChiaChong - Better ProgrammingRamón TruzzardiNo ratings yet
- C-CF CDMA2000 Principle-20071030-A-3.0Document78 pagesC-CF CDMA2000 Principle-20071030-A-3.0فاضل سجادNo ratings yet
- Streamiam General Agency Policy JulyDocument15 pagesStreamiam General Agency Policy JulymariNo ratings yet
- Finite Element Programming With MATLABDocument58 pagesFinite Element Programming With MATLABbharathjoda100% (8)
- SCU System ManualDocument61 pagesSCU System ManualMahen PereraNo ratings yet
- Zerto Virtual Replication VSphere Live DR TestingDocument32 pagesZerto Virtual Replication VSphere Live DR TestingrakNo ratings yet
- Sony KX FT 902 PDFDocument186 pagesSony KX FT 902 PDFpedavNo ratings yet
- Lab Report 3Document9 pagesLab Report 3asharNo ratings yet
- E15 Man Reva1 1-10 Eu Multi 20211021Document93 pagesE15 Man Reva1 1-10 Eu Multi 20211021Nam SonNo ratings yet
- Intelidrive Dcu Marine - 3.8.0 Global GuideDocument371 pagesIntelidrive Dcu Marine - 3.8.0 Global GuideEvgeniy BystroffNo ratings yet
- Bluetooth LE Developer Study Guide - Hands-On Lab (Apache Cordova) V5.1Document49 pagesBluetooth LE Developer Study Guide - Hands-On Lab (Apache Cordova) V5.1bizadiNo ratings yet
- Python: Print ("Hello World")Document14 pagesPython: Print ("Hello World")See KumariNo ratings yet
5-Ex.4b - VPN-22-03-2024
5-Ex.4b - VPN-22-03-2024
Uploaded by
Shreyansh Chaubey0 ratings0% found this document useful (0 votes)
2 views6 pagesOriginal Title
5-EX.4B - VPN-22-03-2024
Copyright
© © All Rights Reserved
Available Formats
PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
Download as pdf or txt
0 ratings0% found this document useful (0 votes)
2 views6 pages5-Ex.4b - VPN-22-03-2024
5-Ex.4b - VPN-22-03-2024
Uploaded by
Shreyansh ChaubeyCopyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
Download as pdf or txt
You are on page 1of 6
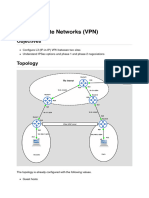
Initial Setup
1/ Use a crossover cable to connect the routers together. We are using
the 1941 Routers for this topology.
2/ Connect the other devices together using a straight through cable
connection.
3/ Perform initial router configuration.
Configure the interface IP addresses on the routers and a default route
on R_01 and R_03 pointing to the R_02 router. The R_02 router acts
as an internet provider and has no knowledge of other networks
except its directly connected network.
1 hostname R_01
interface g0/1
2 ip address 172.16.1.1 255.255.255.0
3 no shut
4 interface g0/0
5 ip address 100.100.100.1 255.255.255.0
no shut
6 exit
7 ip route 0.0.0.0 0.0.0.0 100.100.100.2
8
9 hostname R_02
10 interface g0/1
ip address 100.100.200.2 255.255.255.0
11 no shut
12 interface g0/0
13 ip address 100.100.100.2 255.255.255.0
14 no shut
exit
15
16 hostname R_03
17 interface g0/1
18 ip address 172.16.3.1 255.255.255.0
19 no shut
20 interface g0/0
ip address 100.100.200.1 255.255.255.0
21 no shut
22 exit
23 ip route 0.0.0.0 0.0.0.0 100.100.200.2
24
25
26
27
28
4/ Ensure that the laptops have static IP addresses configured.
Laptop0 should have IP 172.16.1.100/24. Laptop1 should have
172.16.3.100/24. Attempt pinging across from Laptop0 to Laptop1.
This should fail as R_02 does not know how to route this traffic.
1 !Laptop0
2 ping 172.16.3.100
3
4 !Laptop1
5 ping 172.16.1.100
5/ Activate licensing on the edge routers. Ensure that you have the
security license enabled on R_01 and R_03.
1 show version
2 license boot module c1900 technology-package securityk9
3 copy run start
4 reload
show version
5
IPSec VPN Configuration
For the IPSec Tunnel to come up. The configuration on both ends
need to be match for both Phase 1 and Phase 2 to be successful. The
tunnel will be formed between R_01 and R_03.
1/ Setup an ACL that will specify which interesting traffic will be
allowed to pass through the tunnel.
1 !R_01
2 access-list 100 permit ip 172.16.1.0 0.0.0.255 172.16.3.0 0.0.0.255
3
4 !R_03
access-list 100 permit ip 172.16.3.0 0.0.0.255 172.16.1.0 0.0.0.255
5
2/ Setup Phase 1 of the IPSec Tunnel. In this part, we define the
ISAKMP policy and specify that we will use a preshared key. This is
also defined in this case.
1
2 !R_01
3 crypto isakmp policy 10
4 encryption aes 256
authentication pre-share
5 group 5
6 !
7 crypto isakmp key Secret-2020 address 100.100.200.1
8
9 !R_03
10 crypto isakmp policy 10
encryption aes 256
11 authentication pre-share
12 group 5
13 !
14 crypto isakmp key Secret-2020 address 100.100.100.1
15
3/ Next, we setup phase 2 of the IPSec Tunnel (IPsec Transform-set).
This is where the IKE negotiation takes place. We will be using 256 bit
AES encryption with hash message authentication code providing
confidentiality, integrity and authentication.
1 ! R_01
2 crypto ipsec transform-set R_01-R_03 esp-aes 256 esp-sha-hmac
3
4 ! R_03
5 crypto ipsec transform-set R_03-R_01 esp-aes 256 esp-sha-hmac
4/ All we need to do next is to tie Phase 1 and Phase 2 together by
defining the crypto map
1 !R_01
crypto map IPSEC-CRYPTOMAP 100 ipsec-isakmp
2 set peer 100.100.200.1
3 set pfs group5
4 set security-association lifetime seconds 86400
5 set transform-set R_01-R_03
6 match address 100
7
!R_03
8 crypto map IPSEC-CRYPTOMAP 100 ipsec-isakmp
9 set peer 100.100.100.1
10 set pfs group5
11 set security-association lifetime seconds 86400
set transform-set R_03-R_01
12 match address 100
13
14
15
5/ We then activate IPSec on the outbound interface by applying the
crypto map to the interface.
1 !R_01
2 interface GigabitEthernet0/0
3 crypto map IPSEC-CRYPTOMAP
4
5 !R_03
6 interface GigabitEthernet0/0
crypto map IPSEC-CRYPTOMAP
7
6/ For the tunnel to comeuppance, we need to start pings through the
tunnel. Attempt pinging across from Laptop0 to Laptop1. The pings
may initially fail, but if all configuration is accurate, the pings should
succeed after a couple of tries.
1 !Laptop0
2 ping 172.16.3.10
3
4 !Laptop1
5 ping 172.16.1.10
7/ Finally, lets verify that the tunnel is up and running using the below
commands:
1 !R_01
2 show crypto ipsec sa
3
4 !R_03
5 show crypto ipsec sa
Output of Phase 2 being successful is shown below
1 R_01#show crypto ipsec sa
2
interface: GigabitEthernet0/0
3 Crypto map tag: IPSEC-MAP, local addr 100.100.100.1
4
5 protected vrf: (none)
6 local ident (addr/mask/prot/port): (172.16.1.0/255.255.255.0/0/0)
7 remote ident (addr/mask/prot/port): (172.16.3.0/255.255.255.0/0/0)
current_peer 100.100.200.1 port 500
8 PERMIT, flags={origin_is_acl,}
9 #pkts encaps: 7, #pkts encrypt: 7, #pkts digest: 0
10 #pkts decaps: 6, #pkts decrypt: 6, #pkts verify: 0
11 #pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
12 #pkts not decompressed: 0, #pkts decompress failed: 0
13 #send errors 1, #recv errors 0
14
15 local crypto endpt.: 100.100.100.1, remote crypto endpt.:100.100.200.1
16 path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet0/0
current outbound spi: 0xD0212CD7(3491835095)
17
18 inbound esp sas:
19 spi: 0x90BB08EE(2428176622)
20 transform: esp-aes 256 esp-sha-hmac ,
21 in use settings ={Tunnel, }
22 conn id: 2005, flow_id: FPGA:1, crypto map: IPSEC-MAP
sa timing: remaining key lifetime (k/sec): (4525504/86381)
23 IV size: 16 bytes
24 replay detection support: N
25 Status: ACTIVE
26
27 inbound ah sas:
28
inbound pcp sas:
29
30 outbound esp sas:
31 spi: 0xD0212CD7(3491835095)
32 transform: esp-aes 256 esp-sha-hmac ,
33 in use settings ={Tunnel, }
34 conn id: 2006, flow_id: FPGA:1, crypto map: IPSEC-MAP
sa timing: remaining key lifetime (k/sec): (4525504/86381)
35 IV size: 16 bytes
36 replay detection support: N
37 Status: ACTIVE
38
39 outbound ah sas:
40
41 outbound pcp sas:
42
You might also like
- Network Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityFrom EverandNetwork Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityNo ratings yet
- Enterprise Supply Planning (ESP) : by Venkata GopalaDocument33 pagesEnterprise Supply Planning (ESP) : by Venkata Gopalagopal_svsemails8998No ratings yet
- 7.1.2.4 Packet Tracer - Configuring VPNs (Optional) InstructionsDocument6 pages7.1.2.4 Packet Tracer - Configuring VPNs (Optional) InstructionsParitosh KumarNo ratings yet
- 7.3.2.8 Packet Tracer - Configuring GRE Over IPsec InstructionsDocument5 pages7.3.2.8 Packet Tracer - Configuring GRE Over IPsec InstructionsSergio CastañedaNo ratings yet
- 8.7.1.4 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN Using CLI - InstructorDocument5 pages8.7.1.4 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN Using CLI - InstructorSalem TrabelsiNo ratings yet
- 8.4.1.2 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN Using CLIDocument5 pages8.4.1.2 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN Using CLITalha Ur RehmanNo ratings yet
- Lab 2-1 EIGRP Configuration, Bandwidth, and Adjacencies: Learning ObjectivesDocument12 pagesLab 2-1 EIGRP Configuration, Bandwidth, and Adjacencies: Learning ObjectivesSergiy KalmukNo ratings yet
- Lab 17 - Configuring CUBE H.323-To-H.323 VoIP ConnectionsDocument9 pagesLab 17 - Configuring CUBE H.323-To-H.323 VoIP ConnectionsdjmckcNo ratings yet
- Microcontrollerprogramming Msp430fr2433andmsp430fr5994 Part2 PDFDocument301 pagesMicrocontrollerprogramming Msp430fr2433andmsp430fr5994 Part2 PDFAndrei Lazar100% (1)
- Yasser Auda CCIEv5 WorkbookDocument26 pagesYasser Auda CCIEv5 WorkbookphamvanhaNo ratings yet
- Technical ReportDocument19 pagesTechnical ReportUsmanNo ratings yet
- Configure and Verify A Site-To-Site IPsec VPN Using CLIDocument6 pagesConfigure and Verify A Site-To-Site IPsec VPN Using CLIMilošKovačevićNo ratings yet
- Configure and Verify A Site To Site IPsec VPN Using CLIDocument4 pagesConfigure and Verify A Site To Site IPsec VPN Using CLICristhian HadesNo ratings yet
- Gre Over Ipsec VPN: Lab TopologyDocument8 pagesGre Over Ipsec VPN: Lab TopologyyasserNo ratings yet
- IPSec VPNDocument5 pagesIPSec VPNcciersmanNo ratings yet
- 20.1.2 Lab Configure Secure DMVPN TunnelsDocument11 pages20.1.2 Lab Configure Secure DMVPN Tunnelshassa nestor theraNo ratings yet
- 7.3.2.8 Packet Tracer - Configuring GRE Over IPsec InstructionsDocument5 pages7.3.2.8 Packet Tracer - Configuring GRE Over IPsec InstructionsEncikPandaSiriusNo ratings yet
- 16.2.2 Packet Tracer - Configure and Verify A Site-to-Site IPsec VPN Using CLI - ITExamAnswersDocument6 pages16.2.2 Packet Tracer - Configure and Verify A Site-to-Site IPsec VPN Using CLI - ITExamAnswersimen loussaiefNo ratings yet
- Lab VPNDocument9 pagesLab VPNhung kungNo ratings yet
- Part 1: Configure Ipsec Parameters On R1: Version CommandDocument3 pagesPart 1: Configure Ipsec Parameters On R1: Version CommandArun TSNo ratings yet
- Discovery 17: Configure Static VTI Point-to-Point TunnelsDocument5 pagesDiscovery 17: Configure Static VTI Point-to-Point TunnelsIonut StanciuNo ratings yet
- Ipsec On Huawei Ar Router PDFDocument5 pagesIpsec On Huawei Ar Router PDFHussein DhafanNo ratings yet
- 19.5.5 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN - ITExamAnswersDocument5 pages19.5.5 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN - ITExamAnswersAna Maria Citlali Diaz HernandezNo ratings yet
- Lab EIGRP 2Document15 pagesLab EIGRP 2Danny Ricce EnriqueNo ratings yet
- EIGRP LAB TrickDocument20 pagesEIGRP LAB Trickziad Al-showaiterNo ratings yet
- Lab Cisco VPN-GenericDocument2 pagesLab Cisco VPN-Genericbliss21100% (5)
- Configuring A Cisco 827 For Pppoe With VPN Ipsec Nat OverloadingDocument9 pagesConfiguring A Cisco 827 For Pppoe With VPN Ipsec Nat OverloadingAndika PajriNo ratings yet
- CCNP1 Lab 2 1 enDocument11 pagesCCNP1 Lab 2 1 enMurtaxa KhanNo ratings yet
- Lan2lan VPNDocument6 pagesLan2lan VPNFelix BlasioNo ratings yet
- Configure and Verify A Site-To-Site IPsec VPN Using CLI AnswesDocument8 pagesConfigure and Verify A Site-To-Site IPsec VPN Using CLI AnswesAkram AliNo ratings yet
- ISAKMP Associations Using RSA KeysDocument4 pagesISAKMP Associations Using RSA Keyssgopal7No ratings yet
- 4.1 4-S2S-IPSecVPN-Tunnel-RouterDocument6 pages4.1 4-S2S-IPSecVPN-Tunnel-Routeramit_post2000No ratings yet
- 4.4.3.4 Lab - Configuring HSRP and GLBPDocument9 pages4.4.3.4 Lab - Configuring HSRP and GLBPLex Schneider0% (1)
- Creacion VPN IPSECDocument2 pagesCreacion VPN IPSECCarlos Amaranti GonzálezNo ratings yet
- 02-Implementing and Verifying EIGRPDocument24 pages02-Implementing and Verifying EIGRPPablo MotaNo ratings yet
- Configuring EIGRP: BSCI Module 2-2 - Implementing and Verifying EIGRPDocument24 pagesConfiguring EIGRP: BSCI Module 2-2 - Implementing and Verifying EIGRPHerlander FaloNo ratings yet
- Configuring HSRP and GLBPDocument9 pagesConfiguring HSRP and GLBPRajwecNo ratings yet
- Lab EIGRP 3Document13 pagesLab EIGRP 3Danny Ricce EnriqueNo ratings yet
- Case Study On Troubleshooting BGP Flaps Over IPSec Using FFTDocument12 pagesCase Study On Troubleshooting BGP Flaps Over IPSec Using FFTRamprasanth RajaNo ratings yet
- Router Vpnclient Pi StickDocument10 pagesRouter Vpnclient Pi Stickjames SpywangNo ratings yet
- S2S Ikev2 Configure-AsaDocument9 pagesS2S Ikev2 Configure-Asahesenzade38No ratings yet
- Site To Site IPSEC VPN Troubleshooting - ImpDocument8 pagesSite To Site IPSEC VPN Troubleshooting - ImpAsifNo ratings yet
- Ipsec TunnelDocument8 pagesIpsec TunnelHimansu Panda625No ratings yet
- Lab - Configure Basic Router Settings: Part 2: Configure Devices and Verify ConnectivityDocument6 pagesLab - Configure Basic Router Settings: Part 2: Configure Devices and Verify ConnectivityJosé Aarón AponteNo ratings yet
- CCNPv6 ROUTE Lab8-2 Manual IPv6 Tunnel EIGRP Student FormDocument6 pagesCCNPv6 ROUTE Lab8-2 Manual IPv6 Tunnel EIGRP Student FormMuvubuka KatimaniNo ratings yet
- Configuring Site To Site IPSec VPN Tunnel Between Cisco RoutersDocument6 pagesConfiguring Site To Site IPSec VPN Tunnel Between Cisco Routerskymk21No ratings yet
- Lab EIGRP 1Document9 pagesLab EIGRP 1Danny Ricce EnriqueNo ratings yet
- IPSec VPN LABDocument7 pagesIPSec VPN LABAparna Garg100% (2)
- Configuring Site To Site IPSec VPN Tunnel Between Cisco RoutersDocument4 pagesConfiguring Site To Site IPSec VPN Tunnel Between Cisco RoutersSuhas KanikarNo ratings yet
- Lab 13.8.1 Configuring A Site-To-Site Ipsec VPN Using Pre-Shared KeysDocument6 pagesLab 13.8.1 Configuring A Site-To-Site Ipsec VPN Using Pre-Shared KeysKishore Reddy KandiNo ratings yet
- IPsec Quick and DirtyDocument4 pagesIPsec Quick and Dirtysgopal7No ratings yet
- Configuring OSPF Brandon&KatieDocument8 pagesConfiguring OSPF Brandon&KatieLuis GonzalezNo ratings yet
- Somativa7 RedesDocument4 pagesSomativa7 RedesmatheuszanellatoNo ratings yet
- Chapter 8 Lab 8-2, Routing Protocol Authentication Topology: Ccnpv7 RouteDocument12 pagesChapter 8 Lab 8-2, Routing Protocol Authentication Topology: Ccnpv7 RoutengangaNo ratings yet
- InteropDocument6 pagesInteropSaurav LodhNo ratings yet
- Lab 7.7.3 Configuring IS-IS Over Frame Relay: AlternateDocument8 pagesLab 7.7.3 Configuring IS-IS Over Frame Relay: AlternateKishore Reddy KandiNo ratings yet
- 5.3.3.2 Lab - Troubleshoot LAN Traffic Using SPANDocument6 pages5.3.3.2 Lab - Troubleshoot LAN Traffic Using SPANYaser Samer0% (6)
- Updated - IPSec VPN Using Cisco Packet TracerDocument9 pagesUpdated - IPSec VPN Using Cisco Packet TracerAnvesh PenkeNo ratings yet
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkFrom EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkNo ratings yet
- Network with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationFrom EverandNetwork with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationNo ratings yet
- LEARN MPLS FROM SCRATCH PART-B: A Beginners guide to next level of networkingFrom EverandLEARN MPLS FROM SCRATCH PART-B: A Beginners guide to next level of networkingNo ratings yet
- ExtensiDocument47 pagesExtensiImam Imam Abadi Ibnu IsmailNo ratings yet
- An5342 Error Correction Code Ecc Management For Internal Memories Protection On stm32h7 Series StmicroelectronicsDocument15 pagesAn5342 Error Correction Code Ecc Management For Internal Memories Protection On stm32h7 Series Stmicroelectronicsnick choiNo ratings yet
- IntroductionDocument9 pagesIntroductiondyke ossyNo ratings yet
- Er330 WW QG 20201014Document28 pagesEr330 WW QG 20201014James DAvisNo ratings yet
- Datasheet Narda FieldmanDocument8 pagesDatasheet Narda FieldmanDaniel Puentes FermoselNo ratings yet
- Cisco ASA High Availability Failover ConfigurationDocument6 pagesCisco ASA High Availability Failover ConfigurationcciersmanNo ratings yet
- ART - MultiVerb Alpha 20 - ManualDocument61 pagesART - MultiVerb Alpha 20 - Manual0_x_0No ratings yet
- A Project Report On..Document39 pagesA Project Report On..Dabhi AnkitaNo ratings yet
- Introduction To Specification LanguageDocument25 pagesIntroduction To Specification LanguageNguyễn Đắc Thiên NgânNo ratings yet
- Mazda Ids-Users-ManualDocument93 pagesMazda Ids-Users-ManualGoulNo ratings yet
- Rajasthan Cooperative Recruitment Board: On-Line Examination - Recruitment of Manager & Sr. ManagerDocument7 pagesRajasthan Cooperative Recruitment Board: On-Line Examination - Recruitment of Manager & Sr. ManagerHardik MehraNo ratings yet
- Graphic Optimizing andDocument10 pagesGraphic Optimizing and贺He沁QinNo ratings yet
- 239CQH Hdmi2 EDIDDocument3 pages239CQH Hdmi2 EDIDZidni IlmanNo ratings yet
- Maintenance and Service Guide: HP 245 G7 Notebook PCDocument91 pagesMaintenance and Service Guide: HP 245 G7 Notebook PCrodrigokfwNo ratings yet
- Deauthentication (Aircrack-Ng)Document4 pagesDeauthentication (Aircrack-Ng)DCLXVINo ratings yet
- Signed Learning Material No. 6 Nature of Codes and CryptographyDocument49 pagesSigned Learning Material No. 6 Nature of Codes and CryptographyAira Mae Quinones OrendainNo ratings yet
- Build A Search Engine For Medium Stories Using Streamlit and Elasticsearch - by ChiaChong - Better ProgrammingDocument19 pagesBuild A Search Engine For Medium Stories Using Streamlit and Elasticsearch - by ChiaChong - Better ProgrammingRamón TruzzardiNo ratings yet
- C-CF CDMA2000 Principle-20071030-A-3.0Document78 pagesC-CF CDMA2000 Principle-20071030-A-3.0فاضل سجادNo ratings yet
- Streamiam General Agency Policy JulyDocument15 pagesStreamiam General Agency Policy JulymariNo ratings yet
- Finite Element Programming With MATLABDocument58 pagesFinite Element Programming With MATLABbharathjoda100% (8)
- SCU System ManualDocument61 pagesSCU System ManualMahen PereraNo ratings yet
- Zerto Virtual Replication VSphere Live DR TestingDocument32 pagesZerto Virtual Replication VSphere Live DR TestingrakNo ratings yet
- Sony KX FT 902 PDFDocument186 pagesSony KX FT 902 PDFpedavNo ratings yet
- Lab Report 3Document9 pagesLab Report 3asharNo ratings yet
- E15 Man Reva1 1-10 Eu Multi 20211021Document93 pagesE15 Man Reva1 1-10 Eu Multi 20211021Nam SonNo ratings yet
- Intelidrive Dcu Marine - 3.8.0 Global GuideDocument371 pagesIntelidrive Dcu Marine - 3.8.0 Global GuideEvgeniy BystroffNo ratings yet
- Bluetooth LE Developer Study Guide - Hands-On Lab (Apache Cordova) V5.1Document49 pagesBluetooth LE Developer Study Guide - Hands-On Lab (Apache Cordova) V5.1bizadiNo ratings yet
- Python: Print ("Hello World")Document14 pagesPython: Print ("Hello World")See KumariNo ratings yet