Professional Documents
Culture Documents
0 ratings0% found this document useful (0 votes)
6 viewsWireshark Practices
Wireshark Practices
Uploaded by
xofoja7542I created this document to practice about wireshark to my students.
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
You might also like
- Wireshark Lab 5Document17 pagesWireshark Lab 5Truonganh BaoNo ratings yet
- 340 - Questions - CCNA - CCNA 200-301 - Billy CalvertDocument176 pages340 - Questions - CCNA - CCNA 200-301 - Billy Calvertjrchangir89100% (5)
- Wireshark Lab Report: Project Title College Major Name Student ID Beginning and Ending Time AdvisorDocument17 pagesWireshark Lab Report: Project Title College Major Name Student ID Beginning and Ending Time AdvisorMd Minaz HossainNo ratings yet
- CN Lab 6Document10 pagesCN Lab 6k214548No ratings yet
- Nguyen-Doan-Nhat-Minh 2b 3b 4a 4b 4cDocument32 pagesNguyen-Doan-Nhat-Minh 2b 3b 4a 4b 4cNhat MinhNo ratings yet
- HTTP: Stephan Benjamin Helmy:Wireshark Lab1Document8 pagesHTTP: Stephan Benjamin Helmy:Wireshark Lab1Stephan YouanasNo ratings yet
- Wireshark Lab 4aDocument14 pagesWireshark Lab 4aTruonganh BaoNo ratings yet
- Lab 6 1Document7 pagesLab 6 1gokuNo ratings yet
- Lab 8: Network Packet Inspection: Ethernet, IP and TCPDocument11 pagesLab 8: Network Packet Inspection: Ethernet, IP and TCPLêDương AnhTuấnNo ratings yet
- PES2UG22CS397CNLABWEEK1Document15 pagesPES2UG22CS397CNLABWEEK1Ashish GuptaNo ratings yet
- ICMP - Dinah Aryani Z 4ISA2Document2 pagesICMP - Dinah Aryani Z 4ISA2Dinah AryaniNo ratings yet
- Wireshark LabDocument5 pagesWireshark LabAmrit Kumar PatiNo ratings yet
- Format, Then Select Time-Of-Day.)Document31 pagesFormat, Then Select Time-Of-Day.)FinnNo ratings yet
- CCN Lab Report 05Document7 pagesCCN Lab Report 05Hamna YounisNo ratings yet
- LAB 5 IP and ICMPDocument5 pagesLAB 5 IP and ICMPParth PatelNo ratings yet
- Lab 7a: Ethernet, IP and TCP: 1 DetailsDocument14 pagesLab 7a: Ethernet, IP and TCP: 1 DetailsmNo ratings yet
- Nguyen Doan Nhat Minh - Lab5Document5 pagesNguyen Doan Nhat Minh - Lab5Nhat MinhNo ratings yet
- CEH Q BankDocument27 pagesCEH Q BankaakashNo ratings yet
- Assignment2 - Wireshark CN IT 501Document2 pagesAssignment2 - Wireshark CN IT 501omnoNo ratings yet
- Lab 9-10Document6 pagesLab 9-10Anant PatniNo ratings yet
- Lab01 ExerciseDocument2 pagesLab01 ExercisejeetendrasidhiNo ratings yet
- Lab4 COMP4337Document8 pagesLab4 COMP4337k85m8x7jy5No ratings yet
- Lab 03Document6 pagesLab 03Eduardo MonzaniNo ratings yet
- Nova Rusydiani Putri (Tugas ICMP Header Analysis)Document6 pagesNova Rusydiani Putri (Tugas ICMP Header Analysis)novaNo ratings yet
- Names of student: -Nguyễn Tiến Đức -Trần Hoàng Đăng Khoa Class: 16DTCLC1 Subject: Computer NetworkingDocument17 pagesNames of student: -Nguyễn Tiến Đức -Trần Hoàng Đăng Khoa Class: 16DTCLC1 Subject: Computer NetworkingAnonymous EAPWaVHfYp100% (1)
- (C) ITM301 Lab2 (2%) : What Is Your IP Address?Document2 pages(C) ITM301 Lab2 (2%) : What Is Your IP Address?Benjamin TaylorNo ratings yet
- Joshua Larkin CSC 251 Net-Centric Spring 2012: Host IP: 192.168.1.69 Destination IP: 72.14.204.160Document3 pagesJoshua Larkin CSC 251 Net-Centric Spring 2012: Host IP: 192.168.1.69 Destination IP: 72.14.204.160Ярик МаксNo ratings yet
- CSL59 CN Lab I Internals Questions ModifDocument7 pagesCSL59 CN Lab I Internals Questions ModifMohammed FaizanNo ratings yet
- Shad Lab CNDocument8 pagesShad Lab CNFardin ShariarNo ratings yet
- 07-Wireshark ICMP Solution July 22 2007Document7 pages07-Wireshark ICMP Solution July 22 2007Adson RichardsonNo ratings yet
- Lab 1: Getting StartedDocument51 pagesLab 1: Getting StartedAnonymous nnZSTLkNo ratings yet
- Determine The IP Address Configuration of A Computer (Answers Version)Document2 pagesDetermine The IP Address Configuration of A Computer (Answers Version)Simon MwangiNo ratings yet
- Assigment-Worksheet 2Document9 pagesAssigment-Worksheet 2HOD-DIT PSG-PTCNo ratings yet
- Pes1ug22cs363 Lab 1Document18 pagesPes1ug22cs363 Lab 1Ashish GuptaNo ratings yet
- 400+ SOC Interview QuestionsDocument98 pages400+ SOC Interview QuestionsAkhil KumarNo ratings yet
- NguyenHuuChien Inclass Day1Document20 pagesNguyenHuuChien Inclass Day1Nguyễn Hữu ChiếnNo ratings yet
- CN Labfile PDFDocument69 pagesCN Labfile PDFbt21103123 Onkar RamNo ratings yet
- IT Networking and Communication: MITS4004Document15 pagesIT Networking and Communication: MITS4004madan GaireNo ratings yet
- Thuc Hanh MMTNhom 2Document15 pagesThuc Hanh MMTNhom 2bobby04spencerNo ratings yet
- CCN Lab 8 ICMPDocument9 pagesCCN Lab 8 ICMPWaleed RazzaqNo ratings yet
- Wireshark Lab: ICMPDocument2 pagesWireshark Lab: ICMPمحمد عيدNo ratings yet
- Assignment 1Document4 pagesAssignment 1bnNo ratings yet
- Analyse and Fill The Following Table: Enp0s3 (Ethernet) 10.0.2.15 08:00:27:2B:43:3F Lo (Local Host) 127.0.0.1Document15 pagesAnalyse and Fill The Following Table: Enp0s3 (Ethernet) 10.0.2.15 08:00:27:2B:43:3F Lo (Local Host) 127.0.0.1Varun Y TirthaniNo ratings yet
- EGL202 - Lab - 4 - Network Traffic Analysis (Instructor) - Revisedv2Document6 pagesEGL202 - Lab - 4 - Network Traffic Analysis (Instructor) - Revisedv2xian huiNo ratings yet
- BC - MTTMT-đã chuyển đổiDocument63 pagesBC - MTTMT-đã chuyển đổiHuong TruongNo ratings yet
- Assignment On Wireshar1Document4 pagesAssignment On Wireshar1Anonymous zTBOZVNo ratings yet
- 2017 Advanced Computer Networks Homework 1Document6 pages2017 Advanced Computer Networks Homework 1Fadhli RahimNo ratings yet
- Lab 05Document2 pagesLab 05khanh.minhdoanNo ratings yet
- LAB ASSIGNMENT: Analyze The Network Traffic and Performance Parameters of Network Using Wireshark On Windows (Work On Live Captured Data)Document6 pagesLAB ASSIGNMENT: Analyze The Network Traffic and Performance Parameters of Network Using Wireshark On Windows (Work On Live Captured Data)TCS110-Riya SinghNo ratings yet
- Ettercap PluginDocument7 pagesEttercap PluginGunnery HartmanNo ratings yet
- Fardin Lab CNDocument9 pagesFardin Lab CNFardin ShariarNo ratings yet
- l201040 Lab8Document5 pagesl201040 Lab8Muhammad Burhan TahirNo ratings yet
- Lab 2Document11 pagesLab 2Nguyễn Hữu ChiếnNo ratings yet
- 5.1.2.6 Investigating NAT OperationDocument16 pages5.1.2.6 Investigating NAT OperationCristianFelipeSolarteOrozcoNo ratings yet
- Shark Fest 2014 Packet ChallengeDocument2 pagesShark Fest 2014 Packet ChallengeDiksha GangwarNo ratings yet
- CN Lab 1Document7 pagesCN Lab 1Sadia AwanNo ratings yet
- Nguyentiendat IcmpDocument10 pagesNguyentiendat IcmpĐạt NguyễnNo ratings yet
- L02 2110855 NguyenHuuChien Day2 In-ClassDocument11 pagesL02 2110855 NguyenHuuChien Day2 In-ClassNguyễn Hữu ChiếnNo ratings yet
Wireshark Practices
Wireshark Practices
Uploaded by
xofoja75420 ratings0% found this document useful (0 votes)
6 views4 pagesI created this document to practice about wireshark to my students.
Copyright
© © All Rights Reserved
Available Formats
PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentI created this document to practice about wireshark to my students.
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
Download as pdf or txt
0 ratings0% found this document useful (0 votes)
6 views4 pagesWireshark Practices
Wireshark Practices
Uploaded by
xofoja7542I created this document to practice about wireshark to my students.
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
Download as pdf or txt
You are on page 1of 4
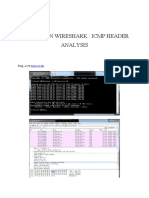
Wireshark Practices
Huseyin EKSI
All pcaps can be downloaded as a zip from here
Lab-1
Open lab1.pcap from link and answer the following questions…
1. What is the currencyCode value in the provided pcap file?(Hint:http)
2.What is the http response code in after applying http filter?
3. What is the domain name queried with the port number 51320 in the pcap file?
4. What are the two host names when you filter llmnr packets in the pcap file?
5.How many unique domains requested?
6.Is there IPV6 traffic?(Yes,No)
7.What is the largest MTU in the pcap file?
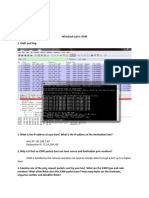
Lab-2
Open lab2.pcap from link and answer the following questions…
1. What is the DESKTOP-? name in the provided pcap file?
2. What is the suspicious domain name queried in the pcap file?
3. What is the IP address of that domain name in response in the pcap file?
4.Filter the IP for further investigation what is the name of the server that responded?
5.What is reputation of that IP address?(Good/Bad)
6.What is the local IP you find in the pcap belongs to the DESKTOP-..?
7.What is the mac address of that machine?
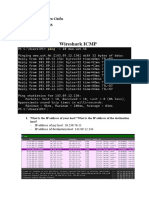
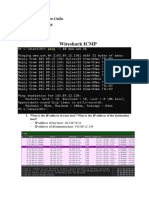
Lab-3
Open lab3.pcap from link and answer the following questions…
1. What is local IP of the victim in the provided pcap file?
2. What are the suspicious domain name queries in the provided pcap file?
3. What is the downloaded hta file name in the pcap file?
4.Decode the Powershell code and find a URL?
7.Can you find a probable PC name in the pcap?
You might also like
- Wireshark Lab 5Document17 pagesWireshark Lab 5Truonganh BaoNo ratings yet
- 340 - Questions - CCNA - CCNA 200-301 - Billy CalvertDocument176 pages340 - Questions - CCNA - CCNA 200-301 - Billy Calvertjrchangir89100% (5)
- Wireshark Lab Report: Project Title College Major Name Student ID Beginning and Ending Time AdvisorDocument17 pagesWireshark Lab Report: Project Title College Major Name Student ID Beginning and Ending Time AdvisorMd Minaz HossainNo ratings yet
- CN Lab 6Document10 pagesCN Lab 6k214548No ratings yet
- Nguyen-Doan-Nhat-Minh 2b 3b 4a 4b 4cDocument32 pagesNguyen-Doan-Nhat-Minh 2b 3b 4a 4b 4cNhat MinhNo ratings yet
- HTTP: Stephan Benjamin Helmy:Wireshark Lab1Document8 pagesHTTP: Stephan Benjamin Helmy:Wireshark Lab1Stephan YouanasNo ratings yet
- Wireshark Lab 4aDocument14 pagesWireshark Lab 4aTruonganh BaoNo ratings yet
- Lab 6 1Document7 pagesLab 6 1gokuNo ratings yet
- Lab 8: Network Packet Inspection: Ethernet, IP and TCPDocument11 pagesLab 8: Network Packet Inspection: Ethernet, IP and TCPLêDương AnhTuấnNo ratings yet
- PES2UG22CS397CNLABWEEK1Document15 pagesPES2UG22CS397CNLABWEEK1Ashish GuptaNo ratings yet
- ICMP - Dinah Aryani Z 4ISA2Document2 pagesICMP - Dinah Aryani Z 4ISA2Dinah AryaniNo ratings yet
- Wireshark LabDocument5 pagesWireshark LabAmrit Kumar PatiNo ratings yet
- Format, Then Select Time-Of-Day.)Document31 pagesFormat, Then Select Time-Of-Day.)FinnNo ratings yet
- CCN Lab Report 05Document7 pagesCCN Lab Report 05Hamna YounisNo ratings yet
- LAB 5 IP and ICMPDocument5 pagesLAB 5 IP and ICMPParth PatelNo ratings yet
- Lab 7a: Ethernet, IP and TCP: 1 DetailsDocument14 pagesLab 7a: Ethernet, IP and TCP: 1 DetailsmNo ratings yet
- Nguyen Doan Nhat Minh - Lab5Document5 pagesNguyen Doan Nhat Minh - Lab5Nhat MinhNo ratings yet
- CEH Q BankDocument27 pagesCEH Q BankaakashNo ratings yet
- Assignment2 - Wireshark CN IT 501Document2 pagesAssignment2 - Wireshark CN IT 501omnoNo ratings yet
- Lab 9-10Document6 pagesLab 9-10Anant PatniNo ratings yet
- Lab01 ExerciseDocument2 pagesLab01 ExercisejeetendrasidhiNo ratings yet
- Lab4 COMP4337Document8 pagesLab4 COMP4337k85m8x7jy5No ratings yet
- Lab 03Document6 pagesLab 03Eduardo MonzaniNo ratings yet
- Nova Rusydiani Putri (Tugas ICMP Header Analysis)Document6 pagesNova Rusydiani Putri (Tugas ICMP Header Analysis)novaNo ratings yet
- Names of student: -Nguyễn Tiến Đức -Trần Hoàng Đăng Khoa Class: 16DTCLC1 Subject: Computer NetworkingDocument17 pagesNames of student: -Nguyễn Tiến Đức -Trần Hoàng Đăng Khoa Class: 16DTCLC1 Subject: Computer NetworkingAnonymous EAPWaVHfYp100% (1)
- (C) ITM301 Lab2 (2%) : What Is Your IP Address?Document2 pages(C) ITM301 Lab2 (2%) : What Is Your IP Address?Benjamin TaylorNo ratings yet
- Joshua Larkin CSC 251 Net-Centric Spring 2012: Host IP: 192.168.1.69 Destination IP: 72.14.204.160Document3 pagesJoshua Larkin CSC 251 Net-Centric Spring 2012: Host IP: 192.168.1.69 Destination IP: 72.14.204.160Ярик МаксNo ratings yet
- CSL59 CN Lab I Internals Questions ModifDocument7 pagesCSL59 CN Lab I Internals Questions ModifMohammed FaizanNo ratings yet
- Shad Lab CNDocument8 pagesShad Lab CNFardin ShariarNo ratings yet
- 07-Wireshark ICMP Solution July 22 2007Document7 pages07-Wireshark ICMP Solution July 22 2007Adson RichardsonNo ratings yet
- Lab 1: Getting StartedDocument51 pagesLab 1: Getting StartedAnonymous nnZSTLkNo ratings yet
- Determine The IP Address Configuration of A Computer (Answers Version)Document2 pagesDetermine The IP Address Configuration of A Computer (Answers Version)Simon MwangiNo ratings yet
- Assigment-Worksheet 2Document9 pagesAssigment-Worksheet 2HOD-DIT PSG-PTCNo ratings yet
- Pes1ug22cs363 Lab 1Document18 pagesPes1ug22cs363 Lab 1Ashish GuptaNo ratings yet
- 400+ SOC Interview QuestionsDocument98 pages400+ SOC Interview QuestionsAkhil KumarNo ratings yet
- NguyenHuuChien Inclass Day1Document20 pagesNguyenHuuChien Inclass Day1Nguyễn Hữu ChiếnNo ratings yet
- CN Labfile PDFDocument69 pagesCN Labfile PDFbt21103123 Onkar RamNo ratings yet
- IT Networking and Communication: MITS4004Document15 pagesIT Networking and Communication: MITS4004madan GaireNo ratings yet
- Thuc Hanh MMTNhom 2Document15 pagesThuc Hanh MMTNhom 2bobby04spencerNo ratings yet
- CCN Lab 8 ICMPDocument9 pagesCCN Lab 8 ICMPWaleed RazzaqNo ratings yet
- Wireshark Lab: ICMPDocument2 pagesWireshark Lab: ICMPمحمد عيدNo ratings yet
- Assignment 1Document4 pagesAssignment 1bnNo ratings yet
- Analyse and Fill The Following Table: Enp0s3 (Ethernet) 10.0.2.15 08:00:27:2B:43:3F Lo (Local Host) 127.0.0.1Document15 pagesAnalyse and Fill The Following Table: Enp0s3 (Ethernet) 10.0.2.15 08:00:27:2B:43:3F Lo (Local Host) 127.0.0.1Varun Y TirthaniNo ratings yet
- EGL202 - Lab - 4 - Network Traffic Analysis (Instructor) - Revisedv2Document6 pagesEGL202 - Lab - 4 - Network Traffic Analysis (Instructor) - Revisedv2xian huiNo ratings yet
- BC - MTTMT-đã chuyển đổiDocument63 pagesBC - MTTMT-đã chuyển đổiHuong TruongNo ratings yet
- Assignment On Wireshar1Document4 pagesAssignment On Wireshar1Anonymous zTBOZVNo ratings yet
- 2017 Advanced Computer Networks Homework 1Document6 pages2017 Advanced Computer Networks Homework 1Fadhli RahimNo ratings yet
- Lab 05Document2 pagesLab 05khanh.minhdoanNo ratings yet
- LAB ASSIGNMENT: Analyze The Network Traffic and Performance Parameters of Network Using Wireshark On Windows (Work On Live Captured Data)Document6 pagesLAB ASSIGNMENT: Analyze The Network Traffic and Performance Parameters of Network Using Wireshark On Windows (Work On Live Captured Data)TCS110-Riya SinghNo ratings yet
- Ettercap PluginDocument7 pagesEttercap PluginGunnery HartmanNo ratings yet
- Fardin Lab CNDocument9 pagesFardin Lab CNFardin ShariarNo ratings yet
- l201040 Lab8Document5 pagesl201040 Lab8Muhammad Burhan TahirNo ratings yet
- Lab 2Document11 pagesLab 2Nguyễn Hữu ChiếnNo ratings yet
- 5.1.2.6 Investigating NAT OperationDocument16 pages5.1.2.6 Investigating NAT OperationCristianFelipeSolarteOrozcoNo ratings yet
- Shark Fest 2014 Packet ChallengeDocument2 pagesShark Fest 2014 Packet ChallengeDiksha GangwarNo ratings yet
- CN Lab 1Document7 pagesCN Lab 1Sadia AwanNo ratings yet
- Nguyentiendat IcmpDocument10 pagesNguyentiendat IcmpĐạt NguyễnNo ratings yet
- L02 2110855 NguyenHuuChien Day2 In-ClassDocument11 pagesL02 2110855 NguyenHuuChien Day2 In-ClassNguyễn Hữu ChiếnNo ratings yet