Professional Documents
Culture Documents
Lab 05
Lab 05
Uploaded by
khanh.minhdoanOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Lab 05
Lab 05
Uploaded by
khanh.minhdoanCopyright:
Available Formats
Lab 05:
Inspecting IP Header & Examining IP fragmentation
1. Overview
In this lab, the students will investigate the IP protocol, focusing on the IP datagram. We’ll do so by
analyzing a trace of IP datagrams sent and received by the execution of the ping program. Students
will inspect the various fields of the IP datagram, and study IP fragmentation in detail.
2. Objectives
This lab aims to provide students with ability:
a) To get familiar with linux terminal and working in command line of the Linux OS (Alpine);
b) To use tcpdump for inspecting the Ethernet frame header of network packets;
c) To use tcpdump for inspecting the various fields of IP header;
d) To understand the fragmentation of IP datagram which is one function of IP protocol for large
data transmission in some circumstances.
3. Lab Environment preparation
a) Install VMWare workstation/VirtualBox on your Windows Computer.
b) A minimal Alpine linux virtual machine can be downloaded from here
c) Ping from one VM to make sure that you can get the reply messages from the other end.
An alternative way to do the lab is creating a containerized environment in docker (highly
recommended). Follow this link to set it up.
The docker setup will create a LAN connecting 2 hosts as in the following figure:
4. Tasks
For the logical knowledge acquisition as well as skills gaining, all following tasks needed to be done
with tcpdump, do not use other utility like Wireshark because the comfortability of the software will spoil
your effort.
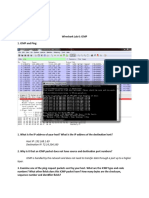
4.1. Inspecting IP Header:
Read various fields of IP header of the first packet from saved file in the above task. Answer the
following questions:
1. Is this packet have optional data? 4. Is this packet fragmented?
2. Tos (type of service) (in hex)? 5. TTL (in hex)?
3. Identifier? 6. Protocol ID (TCP/UDP/Others)?
7. Length (in decimal)? 9. Source IP (dotted-decimal, Hex)
8. Checksum (in hex)? 10. Destination IP (dotted-decimal, Hex)
4.2. Inspecting ICMP packets:
Read the first 2 packets from saved file in the above task. Answer the following questions:
1. What is the value of Type, Code fields?
2. What is the value of Identifier, Sequence number fields?
3. Are the data bytes similar for those packets?
4.3. Study IP datagrams for large data transmission
In this task, you will send icmp with large packet size (2000 - 4000) to inspect the fragmentation in
details:
1. In the terminal of host-172.16.10.5, run tcpdump to sniff icmp packets, specify -w option to save
captures packets to file;
2. In the terminal of host-172.16.10.6, ping host-172.16.10.5:
(prompt):~$ ping 172.16.10.5 -c4 -s 2500 then
-s specify size option, 2500 is the data size.
3. Read the captured file, examine the 1st Echo request packet and answer the following
questions:
a) Within the IP packet header, what is the value in the upper layer protocol field?
b) How many bytes are there in the IP header? How many bytes are there in the payload of
the IP datagram? Explain how you determined the number of payload bytes.
c) Has this IP datagram been fragmented across more than one? Explain how you
determined whether or not the datagram has been fragmented.
d) Watch out the the first fragmented IP datagram. What information in the IP header indicates
that the datagram been fragmented? What information in the IP header indicates whether
this is the first fragment versus a latter fragment? How long is this IP datagram?
e) Watch out the second fragment of the fragmented IP datagram. What information in the IP
header indicates that this is not the first datagram fragment? Are there more fragments?
How can you tell?
f) What fields change in the IP header between the first and second fragment?
4. Ping host-172.16.10.5 with size option specifies to 4000. Answer the following questions:
a) How many echo reply messages are there for each echo request in comparison to the case
when the size 2500 is specified? Explain the difference?
b) Check out the fragment fields in the series of a fragmented echo reply/request messages
to verify your answer in (a).
You might also like
- MPLS L3VPN On IOS XR PDFDocument8 pagesMPLS L3VPN On IOS XR PDFBruce XyaNo ratings yet
- IPv4 Subnetting for Beginners: Your Complete Guide to Master IP Subnetting in 4 Simple Steps: Computer Networking, #1From EverandIPv4 Subnetting for Beginners: Your Complete Guide to Master IP Subnetting in 4 Simple Steps: Computer Networking, #1Rating: 5 out of 5 stars5/5 (3)
- CCNA 3 v7 Modules 9 - 12 - Optimize, Monitor, and Troubleshoot Networks Exam AnswersDocument34 pagesCCNA 3 v7 Modules 9 - 12 - Optimize, Monitor, and Troubleshoot Networks Exam AnswersBrali Dioulson NguemaNo ratings yet
- MP3Document5 pagesMP3Kapil Kale0% (1)
- Wireshark Icmp Solution v6.0Document7 pagesWireshark Icmp Solution v6.0Sumi Gargi100% (1)
- Wireshark Lab 4: IP: Joshua Larkin CSC 251 Net-Centric Spring 2012Document4 pagesWireshark Lab 4: IP: Joshua Larkin CSC 251 Net-Centric Spring 2012Frann BizNo ratings yet
- LAB 5 IP and ICMPDocument5 pagesLAB 5 IP and ICMPParth PatelNo ratings yet
- IT Networking and Communication: MITS4004Document15 pagesIT Networking and Communication: MITS4004madan GaireNo ratings yet
- Solution: What Is The IP Address of Your Computer?Document6 pagesSolution: What Is The IP Address of Your Computer?Trần Nhật HuyNo ratings yet
- Lab 6 1Document7 pagesLab 6 1gokuNo ratings yet
- Wireshark Lab 4aDocument14 pagesWireshark Lab 4aTruonganh BaoNo ratings yet
- 2017 Advanced Computer Networks Homework 1Document6 pages2017 Advanced Computer Networks Homework 1Fadhli RahimNo ratings yet
- Lab 5 SolDocument8 pagesLab 5 SolSujal PrakashNo ratings yet
- Wireshark IP v6.0 Solution Wireshark IP v6.0 SolutionDocument7 pagesWireshark IP v6.0 Solution Wireshark IP v6.0 SolutionЯрик МаксNo ratings yet
- Week # 3.1aDocument3 pagesWeek # 3.1anitin10685No ratings yet
- EP1 - Gabarito - IP Com Wireshark (Solution)Document6 pagesEP1 - Gabarito - IP Com Wireshark (Solution)Hồ Ngọc HoàngNo ratings yet
- Network AssignmentDocument4 pagesNetwork AssignmentAnkit DuggalNo ratings yet
- Solution To Wireshark Lab: IP: 1. What Is The IP Address of Your Computer?Document6 pagesSolution To Wireshark Lab: IP: 1. What Is The IP Address of Your Computer?Duong Ly HoangNo ratings yet
- Lab01 ExerciseDocument2 pagesLab01 ExercisejeetendrasidhiNo ratings yet
- LABDocument3 pagesLABLê Hoàng ChínhNo ratings yet
- Lab 4 Udp + Lab 5 IpDocument11 pagesLab 4 Udp + Lab 5 IpLê Hoàng ChínhNo ratings yet
- Wireshark Lab: IP: Top-Down Approach, 7 Ed., J.F. KuroseDocument7 pagesWireshark Lab: IP: Top-Down Approach, 7 Ed., J.F. KuroseCarlos HenriqueNo ratings yet
- This Chapter Covers The Following SubjectsDocument46 pagesThis Chapter Covers The Following SubjectsAnh TieuNo ratings yet
- Wireshark Arp GayDocument6 pagesWireshark Arp GayyalaboukNo ratings yet
- CIR 209 (Lecture 4f) OSI - ModelDocument16 pagesCIR 209 (Lecture 4f) OSI - Modeldancanongori9No ratings yet
- 06-Wireshark IP Solution July 22Document6 pages06-Wireshark IP Solution July 22Waqas JavedNo ratings yet
- Names of student: -Nguyễn Tiến Đức -Trần Hoàng Đăng Khoa Class: 16DTCLC1 Subject: Computer NetworkingDocument17 pagesNames of student: -Nguyễn Tiến Đức -Trần Hoàng Đăng Khoa Class: 16DTCLC1 Subject: Computer NetworkingAnonymous EAPWaVHfYp100% (1)
- Lab Sheet - IP - ICMPDocument10 pagesLab Sheet - IP - ICMPMIHIKA PARAG DESHPANDENo ratings yet
- Assignment 4 PDFDocument2 pagesAssignment 4 PDFBhuiyan Muhammad Mustansir MustafaNo ratings yet
- Lab04 EthernetDocument2 pagesLab04 Ethernetkhanh.minhdoanNo ratings yet
- Lab 5 - Use Wireshark To View Network TrafficDocument5 pagesLab 5 - Use Wireshark To View Network Traffichiba92398No ratings yet
- Lab4 ReportDocument8 pagesLab4 ReportKian YingNo ratings yet
- Joshua Larkin CSC 251 Net-Centric Spring 2012: Host IP: 192.168.1.69 Destination IP: 72.14.204.160Document3 pagesJoshua Larkin CSC 251 Net-Centric Spring 2012: Host IP: 192.168.1.69 Destination IP: 72.14.204.160Ярик МаксNo ratings yet
- Exno1 Study of Layering in Tcp/Ip Using Wireshark and Study of Basic Networking Commands 9/jan/2024 AimDocument8 pagesExno1 Study of Layering in Tcp/Ip Using Wireshark and Study of Basic Networking Commands 9/jan/2024 AimSABARILAL A KNo ratings yet
- Lab 09 - ACN - IPDocument3 pagesLab 09 - ACN - IPIqbal Uddin KhanNo ratings yet
- Lab05Document14 pagesLab05speech6 labNo ratings yet
- Cccure 04. Communication and Network Security Cissp Practice Test With Answer and ExplanationDocument421 pagesCccure 04. Communication and Network Security Cissp Practice Test With Answer and ExplanationMona AdelNo ratings yet
- Ismaeel Laith Fahmi - ICMPDocument13 pagesIsmaeel Laith Fahmi - ICMPفيدل كاستروNo ratings yet
- IP Wireshark LabDocument25 pagesIP Wireshark LabAhmed AlaaNo ratings yet
- Exploiting The ICMP ProtocolDocument30 pagesExploiting The ICMP ProtocolCarlos Alberto Mendes BetinhoNo ratings yet
- CybeOps QuestionsDocument21 pagesCybeOps QuestionsJayz JoeNo ratings yet
- Comptia Network+ Fall 2017 Wireshark Introduction: What Is Wireshark Used For?Document7 pagesComptia Network+ Fall 2017 Wireshark Introduction: What Is Wireshark Used For?Cameron HulseNo ratings yet
- Wireshark Assignment 05Document19 pagesWireshark Assignment 05JiyaNo ratings yet
- IcmpDocument5 pagesIcmpusamaNo ratings yet
- Nguyen Doan Nhat Minh - Lab5Document5 pagesNguyen Doan Nhat Minh - Lab5Nhat MinhNo ratings yet
- Wireshark Lab: Ethernet and ARPDocument9 pagesWireshark Lab: Ethernet and ARPmailsanjayhere8362No ratings yet
- Assignment 8 - Wireshark Lab 5 - IPDocument4 pagesAssignment 8 - Wireshark Lab 5 - IP徐逸明No ratings yet
- 07-Wireshark ICMP Solution July 22 2007Document7 pages07-Wireshark ICMP Solution July 22 2007Adson RichardsonNo ratings yet
- IP Wireshark Lab SolutionDocument7 pagesIP Wireshark Lab Solutionsyayumi100% (1)
- CCN EXP.6 WiresharkDocument8 pagesCCN EXP.6 WiresharkLou LouNo ratings yet
- Syed Hasnat 18ktele0564 Data Comm LabsDocument64 pagesSyed Hasnat 18ktele0564 Data Comm LabsAmbreen IqbalNo ratings yet
- 5.1.1.7 Lab - Using Wireshark To Examine Ethernet FramesDocument9 pages5.1.1.7 Lab - Using Wireshark To Examine Ethernet FramesAlex Box0% (1)
- 18581Document13 pages18581Rodrigo ZapataNo ratings yet
- LAB ASSIGNMENT: Analyze The Network Traffic and Performance Parameters of Network Using Wireshark On Windows (Work On Live Captured Data)Document6 pagesLAB ASSIGNMENT: Analyze The Network Traffic and Performance Parameters of Network Using Wireshark On Windows (Work On Live Captured Data)TCS110-Riya SinghNo ratings yet
- 8.2.8 Lab - Using Wireshark To Examine Ethernet FramesDocument7 pages8.2.8 Lab - Using Wireshark To Examine Ethernet Framesbui lamNo ratings yet
- Internet Protocols g10 Chs EdzDocument49 pagesInternet Protocols g10 Chs EdzJoan Sarahan100% (1)
- Lab 6.7.2: Examining ICMP Packets: (Instructor Version)Document8 pagesLab 6.7.2: Examining ICMP Packets: (Instructor Version)StarkXDNo ratings yet
- The Compete Ccna 200-301 Study Guide: Network Engineering EditionFrom EverandThe Compete Ccna 200-301 Study Guide: Network Engineering EditionRating: 5 out of 5 stars5/5 (4)
- CCNA Certification All-in-One For DummiesFrom EverandCCNA Certification All-in-One For DummiesRating: 5 out of 5 stars5/5 (1)
- LEARN MPLS FROM SCRATCH PART-A: A Beginner's Guide to Next Level of NetworkingFrom EverandLEARN MPLS FROM SCRATCH PART-A: A Beginner's Guide to Next Level of NetworkingNo ratings yet
- 2G To 4G Re-Selection IssueDocument4 pages2G To 4G Re-Selection IssueAnonymous yzm4usswsNo ratings yet
- IBM UPS NMC 81y1034 GuideDocument110 pagesIBM UPS NMC 81y1034 GuidemironbasovicNo ratings yet
- The Fastest The Most ComplexDocument2 pagesThe Fastest The Most ComplexDiHLoSNo ratings yet
- Ds-3E0526P-E 24-Port Gigabit Unmanaged Poe Switch: Feature and FunctionDocument5 pagesDs-3E0526P-E 24-Port Gigabit Unmanaged Poe Switch: Feature and FunctionSebastian BadilaNo ratings yet
- 11.6.2 Lab - Switch Security Configuration - ILMDocument19 pages11.6.2 Lab - Switch Security Configuration - ILMGonzalo OrtizNo ratings yet
- Discussed Last Time: QCI ARP GBR MBR Apn-Ambr Ue-AmbrDocument4 pagesDiscussed Last Time: QCI ARP GBR MBR Apn-Ambr Ue-AmbrAditya RajNo ratings yet
- Manual Atstorm Relay Remote ModuleDocument12 pagesManual Atstorm Relay Remote ModuleRAFAEL FREITAS FERREIRANo ratings yet
- Location Wise Details MASTERDocument2 pagesLocation Wise Details MASTERSunil PatelNo ratings yet
- Deploying The Analytics Products Iapp Template in The F5 Big-Ip SystemDocument19 pagesDeploying The Analytics Products Iapp Template in The F5 Big-Ip SystemD14CQAT01-N Nguyen Huynh Quoc DoanhNo ratings yet
- HostsDocument4 pagesHostsPrimera CuadrillaNo ratings yet
- VMWARE INTERVIEW Questions 1Document37 pagesVMWARE INTERVIEW Questions 1Ramesh PriyaNo ratings yet
- CCNA3-G11 CertificadoDocument1 pageCCNA3-G11 CertificadoJorge Félix González AcostaNo ratings yet
- Product Data Sheet Downhole Wireless PT Sensor System Roxar en 81890Document2 pagesProduct Data Sheet Downhole Wireless PT Sensor System Roxar en 81890Adonis SaidlerNo ratings yet
- Fireeye Email Deployment ModesDocument3 pagesFireeye Email Deployment Modesrachidi1100% (1)
- CC Mini Project Report - RA2111003010417, 359, 361Document20 pagesCC Mini Project Report - RA2111003010417, 359, 361RAMUJI DONIPARTHI (RA2111003010359)No ratings yet
- MPR IP AddressingDocument13 pagesMPR IP Addressingmansour14No ratings yet
- Knowl AssDocument11 pagesKnowl AssbayushNo ratings yet
- Wire LibraryDocument1 pageWire LibraryLyndon PadamaNo ratings yet
- Brkucc 3662 PDFDocument115 pagesBrkucc 3662 PDFprakashrjsekarNo ratings yet
- TRP-C34H: Ethernet To 4 RS232/422/485 ConverterDocument44 pagesTRP-C34H: Ethernet To 4 RS232/422/485 ConverterAlberto AlvesNo ratings yet
- Ipv4 - Address ClassesDocument2 pagesIpv4 - Address ClassesRifat IqbalNo ratings yet
- How To Setup The Hik-Connect FNA081716 PDFDocument7 pagesHow To Setup The Hik-Connect FNA081716 PDFITM TuguNo ratings yet
- Quickstart Guide: Forticlient Ems 7.0.3Document54 pagesQuickstart Guide: Forticlient Ems 7.0.3Aptoner sistemasNo ratings yet
- Command Manual (Ipv4 Routing Volume I) : Router/Ethernet SwitchDocument139 pagesCommand Manual (Ipv4 Routing Volume I) : Router/Ethernet SwitchLitebohoNo ratings yet
- Rutx50 Datasheet v15 1Document11 pagesRutx50 Datasheet v15 1Destin CanNo ratings yet
- Catalyst Switched Port Analyzer (SPAN RSPAN) Configuration ExampleDocument38 pagesCatalyst Switched Port Analyzer (SPAN RSPAN) Configuration Exampleadm20037No ratings yet
- Mikrotik Basix MTCNA ExamDocument7 pagesMikrotik Basix MTCNA ExamMarco Antonio Urquiola RivasNo ratings yet
- CSE 461: Introduction: OutlineDocument12 pagesCSE 461: Introduction: OutlineShahban ktkNo ratings yet