Professional Documents
Culture Documents
0 ratings0% found this document useful (0 votes)
1 viewsUntitled Document
Untitled Document
Uploaded by
ockiyacliffcCopyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
You might also like
- Lbti LTD Cybersecurity - 073153Document5 pagesLbti LTD Cybersecurity - 073153LIGHTHOUSE BUSINESS AND TECHNOLOGY INTEGRATION LTDNo ratings yet
- Computer Networks Security From Scratch To Advanced: Dr. Mohammad AdlyDocument14 pagesComputer Networks Security From Scratch To Advanced: Dr. Mohammad AdlyRichthofen Flies Bf109No ratings yet
- Name of The Faculty: Mrs.M.Akilandeeswari Subject Name & Code: Branch & Department: B.Tech & AI&DS Year & Semester: 2023 / VI Academic Year:2023-24Document15 pagesName of The Faculty: Mrs.M.Akilandeeswari Subject Name & Code: Branch & Department: B.Tech & AI&DS Year & Semester: 2023 / VI Academic Year:2023-24Aiswarya IlangoNo ratings yet
- Pgdcs CurriculumDocument10 pagesPgdcs Curriculumindraveer_rnsNo ratings yet
- Course Content - Information Security PDFDocument13 pagesCourse Content - Information Security PDFAvaneet RanjanNo ratings yet
- AU Security Course OutlineDocument3 pagesAU Security Course OutlinesamuelNo ratings yet
- Course Outline SCS4110Document3 pagesCourse Outline SCS4110n02019697mNo ratings yet
- UntitledDocument5 pagesUntitledHemal KarmakarNo ratings yet
- Cur SuriDocument252 pagesCur SuriAlex CiacîruNo ratings yet
- Networking Syllabus and MCQ SitesDocument1 pageNetworking Syllabus and MCQ Siteskumar vijayNo ratings yet
- Networking Syllabus and MCQ SitesDocument1 pageNetworking Syllabus and MCQ Siteskumar vijayNo ratings yet
- Information SecurityDocument11 pagesInformation SecurityAppin Technology LabNo ratings yet
- Stormshield ICS Protocol GatewaysDocument325 pagesStormshield ICS Protocol Gatewaystran truongNo ratings yet
- TA4 - Cyber Security - 1688734977204Document66 pagesTA4 - Cyber Security - 1688734977204Deepak KumarNo ratings yet
- Module 1: Cyber Security FundamentalsDocument6 pagesModule 1: Cyber Security FundamentalsAravind VbkNo ratings yet
- इ रसेट Iriset: Cyber SecurityDocument67 pagesइ रसेट Iriset: Cyber SecurityJay VishnuNo ratings yet
- Security Course DetailsDocument5 pagesSecurity Course DetailsNourhan TarekNo ratings yet
- PPW3 Personal Report4Document6 pagesPPW3 Personal Report4Alexander WaddellNo ratings yet
- CompTIA Selected ReviewDocument3 pagesCompTIA Selected ReviewPartha Sarathi NandiNo ratings yet
- Paper-1: Ethical Hacking ContentsDocument7 pagesPaper-1: Ethical Hacking Contents9630455310No ratings yet
- PPW3 Personal Report2Document6 pagesPPW3 Personal Report2Alexander WaddellNo ratings yet
- Digital Forensics and NetworkingDocument29 pagesDigital Forensics and NetworkingMHuyNo ratings yet
- Sec 1Document27 pagesSec 1alexandraaaaaa111No ratings yet
- Lect 12Document29 pagesLect 12dungnthe172688No ratings yet
- Security Chapter ThreeDocument36 pagesSecurity Chapter ThreeBetelhem NigusseNo ratings yet
- 3 Telecom+Network Part1Document105 pages3 Telecom+Network Part1花繼利No ratings yet
- Cys505 Lecture01Document44 pagesCys505 Lecture01Abdirizak AbokarNo ratings yet
- Chatgpt SourceDocument3 pagesChatgpt SourceRobel AmareNo ratings yet
- Advance Networking: Outline of The CourseDocument3 pagesAdvance Networking: Outline of The Courseअमित सिंह100% (1)
- Title 5Document2 pagesTitle 5М. ЭнэрэлтNo ratings yet
- ECCU 500 - Page 1 10 CND Module 01 Computer Network and Defense FundamentalsDocument10 pagesECCU 500 - Page 1 10 CND Module 01 Computer Network and Defense FundamentalssifatullahNo ratings yet
- Akhil - Tech - Repoort 4444Document30 pagesAkhil - Tech - Repoort 4444kalyanjagiri1No ratings yet
- Certified Ethical HackingDocument5 pagesCertified Ethical HackingOwen MasiberahNo ratings yet
- Presentation IT MohammedDocument12 pagesPresentation IT Mohammedaleen8511No ratings yet
- ISS404: Security Architecture, Design and Models SyllabusDocument2 pagesISS404: Security Architecture, Design and Models SyllabusLeNantais SonderangeboteNo ratings yet
- Pune University IS Tech. SyllabusDocument9 pagesPune University IS Tech. SyllabusPav TechnicalsNo ratings yet
- Final PresenDocument14 pagesFinal PresenThana JamalNo ratings yet
- Communication & Network Security: (CNS) Code: EC6112Document69 pagesCommunication & Network Security: (CNS) Code: EC6112291SWAYAM BEHERANo ratings yet
- Department of Information Technology National Instiute of Technology SrinagarDocument11 pagesDepartment of Information Technology National Instiute of Technology SrinagarAMRITESHWAR MISHRANo ratings yet
- Computer Architecture and Security: Fundamentals of Designing Secure Computer SystemsFrom EverandComputer Architecture and Security: Fundamentals of Designing Secure Computer SystemsNo ratings yet
- Analysis of Honeypot Networks and Intrusion Prevention System IPS On Wireless NetworksDocument7 pagesAnalysis of Honeypot Networks and Intrusion Prevention System IPS On Wireless NetworksEditor IJTSRDNo ratings yet
- CCNA 1 v6 Instructor Material - Chapter 1 Explore The NetworkDocument7 pagesCCNA 1 v6 Instructor Material - Chapter 1 Explore The NetworkSándor PetrócziNo ratings yet
- Information Security & Ethical Hacking Course ContentDocument12 pagesInformation Security & Ethical Hacking Course Contentappin_modinagarNo ratings yet
- SecurityOfCriticalInfrastructure V2assignmentDocument4 pagesSecurityOfCriticalInfrastructure V2assignmentAyushNo ratings yet
- Unit 1 Booklet QuestionsDocument36 pagesUnit 1 Booklet QuestionsRini SandeepNo ratings yet
- Hacking Exposed Cisco Networks - Cisco Security Secrets & Solutions by Andrew Vladimirov, Konstantin Gavrilenko and Andrei MikhailovskyDocument1,096 pagesHacking Exposed Cisco Networks - Cisco Security Secrets & Solutions by Andrew Vladimirov, Konstantin Gavrilenko and Andrei MikhailovskyUli UliNo ratings yet
- ZigBeeZigBee PRO Security Assessment Based On Compromised Cryptographic KeysDocument6 pagesZigBeeZigBee PRO Security Assessment Based On Compromised Cryptographic KeysMohammad MohammadNo ratings yet
- CS QB EndDocument6 pagesCS QB EndKUSHANK PATILNo ratings yet
- Lesson Plan-Ns2Document4 pagesLesson Plan-Ns2priyeshNo ratings yet
- Monitoring and Diagnosing Networks: Dr. Jasim SaeedDocument11 pagesMonitoring and Diagnosing Networks: Dr. Jasim SaeedSameer SohailNo ratings yet
- Network SecurityDocument3 pagesNetwork SecuritySubash .SNo ratings yet
- ISEHV7 Course ContentDocument12 pagesISEHV7 Course ContentAppin NitinNo ratings yet
- EC8702 Adhoc SyllabusDocument3 pagesEC8702 Adhoc SyllabusThahsin ThahirNo ratings yet
- EC8702 Adhoc Syllabus PDFDocument3 pagesEC8702 Adhoc Syllabus PDFThahsin Thahir100% (1)
- Chapter 12 Security Monitoring Operational ChallengesDocument12 pagesChapter 12 Security Monitoring Operational ChallengesAkshata ChawhanNo ratings yet
- MTech Cyber I and II Sem SyllabusDocument24 pagesMTech Cyber I and II Sem SyllabusDarmoni LaishramNo ratings yet
- Practical FirewallsDocument295 pagesPractical Firewallsvivekpatle100% (1)
- Chapter 2 Network Security Devices and Cloud ServicesDocument36 pagesChapter 2 Network Security Devices and Cloud ServicesAkshata ChawhanNo ratings yet
- The Fifth International Conference On Ad Hoc, Sensor & Ubiquitous Computing (ASUC-2014)Document2 pagesThe Fifth International Conference On Ad Hoc, Sensor & Ubiquitous Computing (ASUC-2014)CS & ITNo ratings yet
- What Makes a Successful MarriageDocument3 pagesWhat Makes a Successful MarriageockiyacliffcNo ratings yet
- Ledger CorrectDocument1 pageLedger CorrectockiyacliffcNo ratings yet
- Omons SlideDocument20 pagesOmons SlideockiyacliffcNo ratings yet
- Ayama PresentationDocument8 pagesAyama PresentationockiyacliffcNo ratings yet
- Elder Tami's Project PresentationDocument19 pagesElder Tami's Project PresentationockiyacliffcNo ratings yet
- 227052-Article Text-553060-1-10-20220617Document14 pages227052-Article Text-553060-1-10-20220617ockiyacliffcNo ratings yet
- Production and Characterization of Bio-Based (Bambusa Vulgaris) Porous Activated Carbon For Use As Electrode Material in SupercapacitorDocument15 pagesProduction and Characterization of Bio-Based (Bambusa Vulgaris) Porous Activated Carbon For Use As Electrode Material in SupercapacitorockiyacliffcNo ratings yet
- Modeling and Simulation of LPG Plant From Flare Gas For Community Utilization in The Niger Delta, Nigeria.Document14 pagesModeling and Simulation of LPG Plant From Flare Gas For Community Utilization in The Niger Delta, Nigeria.ockiyacliffcNo ratings yet
Untitled Document
Untitled Document
Uploaded by
ockiyacliffc0 ratings0% found this document useful (0 votes)
1 views2 pagesOriginal Title
Untitled document
Copyright
© © All Rights Reserved
Available Formats
PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
Download as pdf or txt
0 ratings0% found this document useful (0 votes)
1 views2 pagesUntitled Document
Untitled Document
Uploaded by
ockiyacliffcCopyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
Download as pdf or txt
You are on page 1of 2
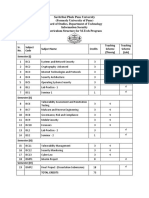
NETWORK CYBER SECURITY COURSE OUTLINE
First Phase:
1. INTRODUCTION OF COMPUTER NETWORK
Introduction
What is a computer Network?
Computer Networks Topologies
Computer network categories
Computer networks Devices and services
Computer networks transmission media
2. ISO/OSI MODEL (7 LAYERS)
Why ISO/OSI model?
Application , presentation, and session
Transport and network layer
Date link and physical layers
ISO/OSI model in action
3. TCP/IP PROTOCOL SUITE
Introduction to computer networks protocols
IP protocol
TCP and UDP protocols
Application Protocols
TCP/IP characteristics and Tools
4. WIRELESS NETWORKS
Wireless networks benefits
Wireless networks types
Wireless networks protocols (WI-FI)
Wireless networks devices
Wireless networks drawbacks
5. COMPUTER NETWORKS SECURITY
Security goals
Securing the network design
TCP/IP Security and tools
Port scanning and tools
Sniffing tools
6. FIREWALLS AND HONEYPOTS
Why use a firewall ?
Firewalls rules
Firewalls filtering
honey pots
Bypassing firewalls
7. INTRUSION DETECTION AND PREVENTION SYSTEMS (IDS/IPS)
What are intrusion detection systems (IDMS)?
Network IDS (NIDS)
NIDS challenges
Snort as NIDS
Intrusion prevention systems (IPS)
8. WIRELESS NETWORKS SECURITY
Wired Equivalent Privacy WEP attacking
WPA and AES Protocols
Wireless Security Misconceptions
Wireless attacks mitigation
Secure Network Design with Wireless
9. PHYSICAL SECURITY AND INCIDENT HANDLING
Physical security objectives
Physical threats and mitigation
Defense in depth (DiD)
What is an incident ?
Incident Handling
10. COMPUTER NETWORKS SECURITY CONCLUSION
Confidentiality, integrity, and availability (CIA)
Assets, threats, and Vulnerabilities
Risks and Network intrusion
Common Attackes
Security Recommendations
You might also like
- Lbti LTD Cybersecurity - 073153Document5 pagesLbti LTD Cybersecurity - 073153LIGHTHOUSE BUSINESS AND TECHNOLOGY INTEGRATION LTDNo ratings yet
- Computer Networks Security From Scratch To Advanced: Dr. Mohammad AdlyDocument14 pagesComputer Networks Security From Scratch To Advanced: Dr. Mohammad AdlyRichthofen Flies Bf109No ratings yet
- Name of The Faculty: Mrs.M.Akilandeeswari Subject Name & Code: Branch & Department: B.Tech & AI&DS Year & Semester: 2023 / VI Academic Year:2023-24Document15 pagesName of The Faculty: Mrs.M.Akilandeeswari Subject Name & Code: Branch & Department: B.Tech & AI&DS Year & Semester: 2023 / VI Academic Year:2023-24Aiswarya IlangoNo ratings yet
- Pgdcs CurriculumDocument10 pagesPgdcs Curriculumindraveer_rnsNo ratings yet
- Course Content - Information Security PDFDocument13 pagesCourse Content - Information Security PDFAvaneet RanjanNo ratings yet
- AU Security Course OutlineDocument3 pagesAU Security Course OutlinesamuelNo ratings yet
- Course Outline SCS4110Document3 pagesCourse Outline SCS4110n02019697mNo ratings yet
- UntitledDocument5 pagesUntitledHemal KarmakarNo ratings yet
- Cur SuriDocument252 pagesCur SuriAlex CiacîruNo ratings yet
- Networking Syllabus and MCQ SitesDocument1 pageNetworking Syllabus and MCQ Siteskumar vijayNo ratings yet
- Networking Syllabus and MCQ SitesDocument1 pageNetworking Syllabus and MCQ Siteskumar vijayNo ratings yet
- Information SecurityDocument11 pagesInformation SecurityAppin Technology LabNo ratings yet
- Stormshield ICS Protocol GatewaysDocument325 pagesStormshield ICS Protocol Gatewaystran truongNo ratings yet
- TA4 - Cyber Security - 1688734977204Document66 pagesTA4 - Cyber Security - 1688734977204Deepak KumarNo ratings yet
- Module 1: Cyber Security FundamentalsDocument6 pagesModule 1: Cyber Security FundamentalsAravind VbkNo ratings yet
- इ रसेट Iriset: Cyber SecurityDocument67 pagesइ रसेट Iriset: Cyber SecurityJay VishnuNo ratings yet
- Security Course DetailsDocument5 pagesSecurity Course DetailsNourhan TarekNo ratings yet
- PPW3 Personal Report4Document6 pagesPPW3 Personal Report4Alexander WaddellNo ratings yet
- CompTIA Selected ReviewDocument3 pagesCompTIA Selected ReviewPartha Sarathi NandiNo ratings yet
- Paper-1: Ethical Hacking ContentsDocument7 pagesPaper-1: Ethical Hacking Contents9630455310No ratings yet
- PPW3 Personal Report2Document6 pagesPPW3 Personal Report2Alexander WaddellNo ratings yet
- Digital Forensics and NetworkingDocument29 pagesDigital Forensics and NetworkingMHuyNo ratings yet
- Sec 1Document27 pagesSec 1alexandraaaaaa111No ratings yet
- Lect 12Document29 pagesLect 12dungnthe172688No ratings yet
- Security Chapter ThreeDocument36 pagesSecurity Chapter ThreeBetelhem NigusseNo ratings yet
- 3 Telecom+Network Part1Document105 pages3 Telecom+Network Part1花繼利No ratings yet
- Cys505 Lecture01Document44 pagesCys505 Lecture01Abdirizak AbokarNo ratings yet
- Chatgpt SourceDocument3 pagesChatgpt SourceRobel AmareNo ratings yet
- Advance Networking: Outline of The CourseDocument3 pagesAdvance Networking: Outline of The Courseअमित सिंह100% (1)
- Title 5Document2 pagesTitle 5М. ЭнэрэлтNo ratings yet
- ECCU 500 - Page 1 10 CND Module 01 Computer Network and Defense FundamentalsDocument10 pagesECCU 500 - Page 1 10 CND Module 01 Computer Network and Defense FundamentalssifatullahNo ratings yet
- Akhil - Tech - Repoort 4444Document30 pagesAkhil - Tech - Repoort 4444kalyanjagiri1No ratings yet
- Certified Ethical HackingDocument5 pagesCertified Ethical HackingOwen MasiberahNo ratings yet
- Presentation IT MohammedDocument12 pagesPresentation IT Mohammedaleen8511No ratings yet
- ISS404: Security Architecture, Design and Models SyllabusDocument2 pagesISS404: Security Architecture, Design and Models SyllabusLeNantais SonderangeboteNo ratings yet
- Pune University IS Tech. SyllabusDocument9 pagesPune University IS Tech. SyllabusPav TechnicalsNo ratings yet
- Final PresenDocument14 pagesFinal PresenThana JamalNo ratings yet
- Communication & Network Security: (CNS) Code: EC6112Document69 pagesCommunication & Network Security: (CNS) Code: EC6112291SWAYAM BEHERANo ratings yet
- Department of Information Technology National Instiute of Technology SrinagarDocument11 pagesDepartment of Information Technology National Instiute of Technology SrinagarAMRITESHWAR MISHRANo ratings yet
- Computer Architecture and Security: Fundamentals of Designing Secure Computer SystemsFrom EverandComputer Architecture and Security: Fundamentals of Designing Secure Computer SystemsNo ratings yet
- Analysis of Honeypot Networks and Intrusion Prevention System IPS On Wireless NetworksDocument7 pagesAnalysis of Honeypot Networks and Intrusion Prevention System IPS On Wireless NetworksEditor IJTSRDNo ratings yet
- CCNA 1 v6 Instructor Material - Chapter 1 Explore The NetworkDocument7 pagesCCNA 1 v6 Instructor Material - Chapter 1 Explore The NetworkSándor PetrócziNo ratings yet
- Information Security & Ethical Hacking Course ContentDocument12 pagesInformation Security & Ethical Hacking Course Contentappin_modinagarNo ratings yet
- SecurityOfCriticalInfrastructure V2assignmentDocument4 pagesSecurityOfCriticalInfrastructure V2assignmentAyushNo ratings yet
- Unit 1 Booklet QuestionsDocument36 pagesUnit 1 Booklet QuestionsRini SandeepNo ratings yet
- Hacking Exposed Cisco Networks - Cisco Security Secrets & Solutions by Andrew Vladimirov, Konstantin Gavrilenko and Andrei MikhailovskyDocument1,096 pagesHacking Exposed Cisco Networks - Cisco Security Secrets & Solutions by Andrew Vladimirov, Konstantin Gavrilenko and Andrei MikhailovskyUli UliNo ratings yet
- ZigBeeZigBee PRO Security Assessment Based On Compromised Cryptographic KeysDocument6 pagesZigBeeZigBee PRO Security Assessment Based On Compromised Cryptographic KeysMohammad MohammadNo ratings yet
- CS QB EndDocument6 pagesCS QB EndKUSHANK PATILNo ratings yet
- Lesson Plan-Ns2Document4 pagesLesson Plan-Ns2priyeshNo ratings yet
- Monitoring and Diagnosing Networks: Dr. Jasim SaeedDocument11 pagesMonitoring and Diagnosing Networks: Dr. Jasim SaeedSameer SohailNo ratings yet
- Network SecurityDocument3 pagesNetwork SecuritySubash .SNo ratings yet
- ISEHV7 Course ContentDocument12 pagesISEHV7 Course ContentAppin NitinNo ratings yet
- EC8702 Adhoc SyllabusDocument3 pagesEC8702 Adhoc SyllabusThahsin ThahirNo ratings yet
- EC8702 Adhoc Syllabus PDFDocument3 pagesEC8702 Adhoc Syllabus PDFThahsin Thahir100% (1)
- Chapter 12 Security Monitoring Operational ChallengesDocument12 pagesChapter 12 Security Monitoring Operational ChallengesAkshata ChawhanNo ratings yet
- MTech Cyber I and II Sem SyllabusDocument24 pagesMTech Cyber I and II Sem SyllabusDarmoni LaishramNo ratings yet
- Practical FirewallsDocument295 pagesPractical Firewallsvivekpatle100% (1)
- Chapter 2 Network Security Devices and Cloud ServicesDocument36 pagesChapter 2 Network Security Devices and Cloud ServicesAkshata ChawhanNo ratings yet
- The Fifth International Conference On Ad Hoc, Sensor & Ubiquitous Computing (ASUC-2014)Document2 pagesThe Fifth International Conference On Ad Hoc, Sensor & Ubiquitous Computing (ASUC-2014)CS & ITNo ratings yet
- What Makes a Successful MarriageDocument3 pagesWhat Makes a Successful MarriageockiyacliffcNo ratings yet
- Ledger CorrectDocument1 pageLedger CorrectockiyacliffcNo ratings yet
- Omons SlideDocument20 pagesOmons SlideockiyacliffcNo ratings yet
- Ayama PresentationDocument8 pagesAyama PresentationockiyacliffcNo ratings yet
- Elder Tami's Project PresentationDocument19 pagesElder Tami's Project PresentationockiyacliffcNo ratings yet
- 227052-Article Text-553060-1-10-20220617Document14 pages227052-Article Text-553060-1-10-20220617ockiyacliffcNo ratings yet
- Production and Characterization of Bio-Based (Bambusa Vulgaris) Porous Activated Carbon For Use As Electrode Material in SupercapacitorDocument15 pagesProduction and Characterization of Bio-Based (Bambusa Vulgaris) Porous Activated Carbon For Use As Electrode Material in SupercapacitorockiyacliffcNo ratings yet
- Modeling and Simulation of LPG Plant From Flare Gas For Community Utilization in The Niger Delta, Nigeria.Document14 pagesModeling and Simulation of LPG Plant From Flare Gas For Community Utilization in The Niger Delta, Nigeria.ockiyacliffcNo ratings yet