Professional Documents
Culture Documents
Memory Forensics
Memory Forensics
Uploaded by
raisulb0 ratings0% found this document useful (0 votes)
1 views2 pagesCopyright
© © All Rights Reserved
Available Formats
DOCX, PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
© All Rights Reserved
Available Formats
Download as DOCX, PDF, TXT or read online from Scribd
Download as docx, pdf, or txt
0 ratings0% found this document useful (0 votes)
1 views2 pagesMemory Forensics
Memory Forensics
Uploaded by
raisulbCopyright:
© All Rights Reserved
Available Formats
Download as DOCX, PDF, TXT or read online from Scribd
Download as docx, pdf, or txt
You are on page 1of 2
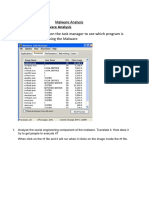
Memory Forensics
Memory forensics is the practice of analyzing a computer's memory dump to investigate and extract
information related to cyber incidents, such as malware, unauthorized access, or data breaches. It
involves capturing volatile data from a system's RAM to uncover evidence that may not be present
on the disk.
Volatility is an open-source memory forensics framework used to analyze and extract digital artifacts
from memory dumps of various operating systems. It provides tools to investigate malicious activity,
system state, and other relevant information by examining the volatile memory of a computer.
Step-by-step process for performing memory forensics using Volatility:
Step 1: Prepare Your Environment
1. Install Volatility
2. Acquire a Memory Dump using tools like 'procdump', 'DumpIt', 'FTK Imager', or 'WinPMEM'.
Step 2: Identify the Profile
1. Run ImageInfo: vol.py -f memory.dmp imageinfo
Step 3: Analyze the Memory Dump
1. List Processes: vol.py -f memory.dmp --profile=Win7SP1x64 pslist
2. Analyze Process Tree: vol.py -f memory.dmp --profile=Win7SP1x64 pstree
3. Check DLLs Loaded by a Process: vol.py -f memory.dmp --profile=Win7SP1x64 dlllist -p <PID>
4. List Open Handles: vol.py -f memory.dmp --profile=Win7SP1x64 handles -p <PID>
5. Check Network Connections: vol.py -f memory.dmp --profile=Win7SP1x64 netscan
6. Scan for Malicious Code: vol.py -f memory.dmp --profile=Win7SP1x64 malfind
7. Find File Objects in Physical Memory: vol.py -f memory.dmp --profile=Win7SP1x64 filescan
8. CreCreate a CSV Timeline of Events: vol.py -f memory.dmp --profile=Win7SP1x64 timeliner --
output-file=timeline.csv
Step 4: Extract and Analyze Specific Artifacts
1. Dump Process Memory: vol.py -f memory.dmp --profile=Win7SP1x64 procdump -p <PID> -D
/output/
2. List Registry Hives: vol.py -f memory.dmp --profile=Win7SP1x64 hivelist
3. Extract Registry Keys: vol.py -f memory.dmp --profile=Win7SP1x64 printkey -K "Software\
Microsoft\Windows\CurrentVersion\Run"
4. Command History: vol.py -f memory.dmp --profile=Win7SP1x64 cmdscan
Step 5: Report Findings
1. Document Analysis
2. Create a Timeline
3. Generate a Report
BlackPerl DFIR
Comparing commands from Vol2 > Vol3
https://lnkd.in/eu23YBMV
Command Reference
https://lnkd.in/eCrXWbqB
You might also like
- 5 6087116402542512855Document6 pages5 6087116402542512855Student Hulu100% (1)
- CF Lecture 07-Memory ForensicsDocument54 pagesCF Lecture 07-Memory ForensicsFaisal Shahzad100% (1)
- Static Malware Analysis TechniquesDocument15 pagesStatic Malware Analysis TechniquesvibhiNo ratings yet
- Experiment-2 Digital Forensics AIM-Capture The Memory of Any OS System and Try To Analyse .Mem File On Kali Using Volatility Tool DATE: 06-02-2021Document21 pagesExperiment-2 Digital Forensics AIM-Capture The Memory of Any OS System and Try To Analyse .Mem File On Kali Using Volatility Tool DATE: 06-02-2021TANISHA PATHAKNo ratings yet
- Study On Forensic Analysis of Physical Memory: Liming Cai, Jing Sha, Wei QianDocument4 pagesStudy On Forensic Analysis of Physical Memory: Liming Cai, Jing Sha, Wei QiankamelancienNo ratings yet
- Yash Darole DF 5Document7 pagesYash Darole DF 505. Yash DaroleNo ratings yet
- Unit-Ii CFDocument13 pagesUnit-Ii CFmanognaharikishanNo ratings yet
- ThickClient MethdologyDocument1 pageThickClient MethdologyadityaNo ratings yet
- Memory Forensics Cheat Sheet v1Document2 pagesMemory Forensics Cheat Sheet v1adam593No ratings yet
- Memory Fornesics NotesDocument28 pagesMemory Fornesics NotesShafeeque Olassery KunnikkalNo ratings yet
- FOR508HANDOUT - MemForensCheat Sheetv2 - E02 - 03Document2 pagesFOR508HANDOUT - MemForensCheat Sheetv2 - E02 - 03JonasNo ratings yet
- CertainlyDocument9 pagesCertainlysyedadeen18No ratings yet
- Incident Response Methodology - Windows Intrusion DetectionDocument4 pagesIncident Response Methodology - Windows Intrusion DetectionNome SobrenomeNo ratings yet
- Incident Response Methodology - Linux - Unix Intrusion DetectionDocument4 pagesIncident Response Methodology - Linux - Unix Intrusion DetectionNome SobrenomeNo ratings yet
- SANSDocument2 pagesSANSSandro MeloNo ratings yet
- Digital ForensicsDocument4 pagesDigital ForensicsAashirwad VermaNo ratings yet
- Eroraha Memory ForensicsDocument24 pagesEroraha Memory ForensicsAdriana HernandezNo ratings yet
- Computer Forensics Process For BeginnersDocument8 pagesComputer Forensics Process For BeginnersSachin Jung KarkiNo ratings yet
- File Carving Artifacts Extraction and Deleted Data RecoveryDocument2 pagesFile Carving Artifacts Extraction and Deleted Data RecoverySiddhesh KarekarNo ratings yet
- Solving Computer Forensic Case Using Autopsy: ScenarioDocument26 pagesSolving Computer Forensic Case Using Autopsy: ScenarioGaby CortezNo ratings yet
- IRM 7 Windows Malware DetectionDocument2 pagesIRM 7 Windows Malware DetectionbogneNo ratings yet
- Memory Dump ICS Lab.Document21 pagesMemory Dump ICS Lab.ricksant2003No ratings yet
- CF Practicals PDFDocument117 pagesCF Practicals PDFNikhil AmodkarNo ratings yet
- Windows - Forensics Building Lab and Essential InvestigationDocument238 pagesWindows - Forensics Building Lab and Essential InvestigationnicolasvNo ratings yet
- Lab 18-19: Memory Dump Tool (Moonsols Windows Memory Toolkit) Memory Analysis Tool (Volatility Framework)Document14 pagesLab 18-19: Memory Dump Tool (Moonsols Windows Memory Toolkit) Memory Analysis Tool (Volatility Framework)THUẬN NGUYỄN MINHNo ratings yet
- MEGO WriteupDocument5 pagesMEGO WriteupToby MacNo ratings yet
- Detect Malware W Memory ForensicsDocument27 pagesDetect Malware W Memory Forensicsمحيي البازNo ratings yet
- Windows ForensicsDocument68 pagesWindows ForensicsAmiraNo ratings yet
- More Windows ArtifactsDocument6 pagesMore Windows ArtifactsNicasio Aquino100% (1)
- CS Lab 2Document10 pagesCS Lab 2Vicky VickneshwariNo ratings yet
- Event Logs Management: Anthony Lai Founder & Editor Infosec Hong KongDocument33 pagesEvent Logs Management: Anthony Lai Founder & Editor Infosec Hong Kongapi-27294532No ratings yet
- Home Task 1Document3 pagesHome Task 1f21bscs008No ratings yet
- Samim-DFMA Lab WorkbookDocument48 pagesSamim-DFMA Lab WorkbookGarvit HoodaNo ratings yet
- Active Directory Exploitation Cheat Sheet: ShareDocument14 pagesActive Directory Exploitation Cheat Sheet: ShareSokoine Hamad DenisNo ratings yet
- Ethical Hacking Project WorkDocument16 pagesEthical Hacking Project Workravi tejaNo ratings yet
- Malware AnalysisDocument21 pagesMalware AnalysisAyush rawal100% (1)
- Project - InstructionsDocument2 pagesProject - Instructionschunkymonkey323No ratings yet
- Hunting For Credentials Dumping in Windows EnvironmentDocument61 pagesHunting For Credentials Dumping in Windows EnvironmentzdravkoNo ratings yet
- Sysmon DocumentationDocument7 pagesSysmon Documentationbenoit.ponjeeNo ratings yet
- 04-OS and Multimedia ForensicsDocument189 pages04-OS and Multimedia ForensicsMohammed Lajam100% (1)
- Malware AnalysisDocument15 pagesMalware AnalysisJosue OuattaraNo ratings yet
- Netcat by Knight CrawlerDocument9 pagesNetcat by Knight Crawlerqwerty9020No ratings yet
- Lec 3 Digial ForensicDocument19 pagesLec 3 Digial Forensicprincess.mirna2003No ratings yet
- CHFI Crash Study GuideDocument9 pagesCHFI Crash Study Guidecyber forensicNo ratings yet
- Sec535 PR PDFDocument23 pagesSec535 PR PDFFREDDY ALLAN PALACIOS GONZÁLEZNo ratings yet
- Computer Forensics ProjectsDocument4 pagesComputer Forensics Projectszaid khattakNo ratings yet
- LIVEdataWIN UNIXDocument51 pagesLIVEdataWIN UNIXChirayu AggarwalNo ratings yet
- 27.2.10 Lab - Extract An Executable From A PCAP-1 - TecsonDocument6 pages27.2.10 Lab - Extract An Executable From A PCAP-1 - TecsonelijahjoshtecsonNo ratings yet
- Helix Version 3Document14 pagesHelix Version 3Divik ShrivastavaNo ratings yet
- Digital Forensic Analysis Lab ExerciseDocument3 pagesDigital Forensic Analysis Lab Exercisealshdadyfhmy398100% (1)
- Chmod666 NIM Cheat SheetDocument2 pagesChmod666 NIM Cheat SheetHemantNo ratings yet
- Helix Tool Use CaseDocument32 pagesHelix Tool Use CaseSantosh kumar beheraNo ratings yet
- List of Window ArtifactsDocument19 pagesList of Window Artifactsanasonadi234No ratings yet
- Trace Log 20220301091122Document10 pagesTrace Log 20220301091122FRANSISKUS JIMMYNo ratings yet
- Forensics - Lab 6Document4 pagesForensics - Lab 6ManuelGonzalezAnidoNo ratings yet
- Sys Mon InternalsDocument46 pagesSys Mon Internalsשוקולד וסוכר ומלח שוקולד סוכרNo ratings yet
- HTB Sherlock LogjammerDocument22 pagesHTB Sherlock Logjammerlolkek0001No ratings yet
- Footprinting, Reconnaissance, Scanning and Enumeration Techniques of Computer NetworksFrom EverandFootprinting, Reconnaissance, Scanning and Enumeration Techniques of Computer NetworksNo ratings yet