Professional Documents
Culture Documents
Befund USH EN
Befund USH EN
Uploaded by
renan silvaCopyright:
Available Formats
You might also like
- Paul de Man - Rhetoric of TemporalityDocument23 pagesPaul de Man - Rhetoric of TemporalityEgor Sofronov100% (3)
- Book Report of My Brother, My Executioner byDocument7 pagesBook Report of My Brother, My Executioner bycrimsonlover17% (6)
- Digital Cash (Anonymous Online Payment Scheme)Document11 pagesDigital Cash (Anonymous Online Payment Scheme)Arif Masood100% (5)
- CS5460 ChadMaughan Assignment4Document3 pagesCS5460 ChadMaughan Assignment4the_tigdraNo ratings yet
- Minimum Viable Block ChainDocument20 pagesMinimum Viable Block ChainAlbertoNo ratings yet
- 02 Key Management and Public Key Infrastructure ADocument51 pages02 Key Management and Public Key Infrastructure ADevil KenwayNo ratings yet
- GBGN17 FC Physical - EscrowDocument27 pagesGBGN17 FC Physical - EscrowChristos FloridisNo ratings yet
- Zerocoin - Anonymous Distributed E-Cash From Bitcoin PDFDocument15 pagesZerocoin - Anonymous Distributed E-Cash From Bitcoin PDFgeckxNo ratings yet
- PKI (Public Key Infrastructure) : P e P e e e PDocument2 pagesPKI (Public Key Infrastructure) : P e P e e e Psimon sylvesterNo ratings yet
- How Does The Blockchain Work - OneZeroDocument15 pagesHow Does The Blockchain Work - OneZeroSanchit AggarwalNo ratings yet
- Coinparty: Secure Multi-Party Mixing of BitcoinsDocument12 pagesCoinparty: Secure Multi-Party Mixing of BitcoinsAdolf CohAlcarazNo ratings yet
- Paper 3. Zerocoin Anonymous Distributed E-Cash From BitcoinDocument15 pagesPaper 3. Zerocoin Anonymous Distributed E-Cash From BitcoinQubits 01No ratings yet
- Zerocash: Decentralized Anonymous Payments From Bitcoin: 2014 IEEE Symposium On Security and PrivacyDocument16 pagesZerocash: Decentralized Anonymous Payments From Bitcoin: 2014 IEEE Symposium On Security and PrivacyjasonwNo ratings yet
- Chapters 1.key Management 2.Authentication-I 3.Authentication-Ii 4.Ipsec-Security at The Network Layer 5.security at Transport LayerDocument56 pagesChapters 1.key Management 2.Authentication-I 3.Authentication-Ii 4.Ipsec-Security at The Network Layer 5.security at Transport LayerRavish ShankarNo ratings yet
- DCAP Anonymous Payment SystemDocument13 pagesDCAP Anonymous Payment Systemholar45575No ratings yet
- Key Management and Public Key InfrastructureDocument61 pagesKey Management and Public Key InfrastructureAkash MahapatraNo ratings yet
- Gematmw Y10 Individual Project 1Document12 pagesGematmw Y10 Individual Project 1Nevan NovaNo ratings yet
- WhitepaperDocument45 pagesWhitepapersiddevice162No ratings yet
- Secure Hierarchical Bitcoin Wallet Scheme Against Privilege Escalation AttacksDocument11 pagesSecure Hierarchical Bitcoin Wallet Scheme Against Privilege Escalation AttacksKing's MonarchNo ratings yet
- How Does The Blockchain Work?: Blockchain Technology Explained in Simple WordsDocument27 pagesHow Does The Blockchain Work?: Blockchain Technology Explained in Simple WordsrainsolinNo ratings yet
- Trust Is Risk: A Decentralized Financial Trust PlatformDocument18 pagesTrust Is Risk: A Decentralized Financial Trust PlatformorfeasNo ratings yet
- CH Security ProtocolsDocument27 pagesCH Security ProtocolsMuhammad asafNo ratings yet
- Network Security UNIT 2Document30 pagesNetwork Security UNIT 2smitcse2021No ratings yet
- Block - Chain SolutionDocument30 pagesBlock - Chain SolutionPk Bijoy100% (1)
- Chapters 1.key Management 2.Authentication-I 3.Authentication-Ii 4.Ipsec-Security at The Network Layer 5.security at Transport LayerDocument56 pagesChapters 1.key Management 2.Authentication-I 3.Authentication-Ii 4.Ipsec-Security at The Network Layer 5.security at Transport LayerSudha SreedeviNo ratings yet
- Prsentation On IdentityBased-PREDocument29 pagesPrsentation On IdentityBased-PREosama ahmedNo ratings yet
- Block ChainDocument9 pagesBlock ChainChinmayi HSNo ratings yet
- Grid Computing 7700: Fall 2005 Lecture 16: Grid SecurityDocument32 pagesGrid Computing 7700: Fall 2005 Lecture 16: Grid SecurityJaswanth RoyalNo ratings yet
- Blockchain TutorialDocument16 pagesBlockchain TutorialDr. Ramu Kuchipudi Associate Professor (Contract)No ratings yet
- Zero KnowledgeDocument5 pagesZero KnowledgeMarcos CorrêaNo ratings yet
- Jerad Bates - Public Key InfrastructureDocument30 pagesJerad Bates - Public Key Infrastructurevenkatesh VRNo ratings yet
- A Protocol For Preventing Transaction Commitment Without Recipients Authorization On Blockchain and Its ImplementationDocument16 pagesA Protocol For Preventing Transaction Commitment Without Recipients Authorization On Blockchain and Its ImplementationAnitha TNo ratings yet
- Information Systems Security LAB: Key ManagementDocument10 pagesInformation Systems Security LAB: Key ManagementAbdullah Al-HallakNo ratings yet
- cns4 1Document12 pagescns4 1gadidheerajreddy.20.itNo ratings yet
- Security and CryptographyDocument6 pagesSecurity and Cryptographykelciefay8No ratings yet
- CH 10 ExtractDocument22 pagesCH 10 ExtractMuhammad asafNo ratings yet
- Blockchain Guide Starter Cryptocurrency ExplainationDocument12 pagesBlockchain Guide Starter Cryptocurrency ExplainationViktor OmsNo ratings yet
- Structure and Anonymity of The Bitcoin Transaction GraphDocument14 pagesStructure and Anonymity of The Bitcoin Transaction GraphshamanjrNo ratings yet
- Key ManagementDocument28 pagesKey Managementanon_212627844No ratings yet
- CryptoNote v1Document16 pagesCryptoNote v1ze355rNo ratings yet
- UnicryptoDocument5 pagesUnicryptoNikhil AnandNo ratings yet
- InfSec 7 PKIDocument24 pagesInfSec 7 PKINhư NguyễnNo ratings yet
- Public Key Infrastructure: Jim HurstDocument5 pagesPublic Key Infrastructure: Jim HurstBARNALI GUPTANo ratings yet
- Know Your Customer: Opening A New Bank Account Online Using UAAFDocument2 pagesKnow Your Customer: Opening A New Bank Account Online Using UAAFaldykurniawanNo ratings yet
- What Is Blockchain Technology?Document31 pagesWhat Is Blockchain Technology?alenNo ratings yet
- Web 3 GlosaryDocument51 pagesWeb 3 GlosaryFranzNo ratings yet
- CryptoNote v1 (Archive - Org)Document16 pagesCryptoNote v1 (Archive - Org)ze355rNo ratings yet
- How Perfect Offline Wallets Can Still Leak Bitcoin Private KeysDocument11 pagesHow Perfect Offline Wallets Can Still Leak Bitcoin Private Keysmorten44No ratings yet
- Deanonymisation of Clients in Bitcoin P2P NetworkDocument15 pagesDeanonymisation of Clients in Bitcoin P2P NetworkGary ShenNo ratings yet
- Lecture 5Document10 pagesLecture 5AHMED DARAJNo ratings yet
- Chapter 18: Fundamentals of The Public Key InfrastructureDocument21 pagesChapter 18: Fundamentals of The Public Key Infrastructureflorinn81No ratings yet
- Secure Multiparty Computations On BitcoinDocument18 pagesSecure Multiparty Computations On Bitcoinmoferi9083No ratings yet
- Deanonymisation of Clients in Bitcoin P2P Network: Alex Biryukov Dmitry Khovratovich Ivan PustogarovDocument14 pagesDeanonymisation of Clients in Bitcoin P2P Network: Alex Biryukov Dmitry Khovratovich Ivan PustogarovDelraja Washington BrownNo ratings yet
- Authentication Protocols and Key EstablishmentDocument34 pagesAuthentication Protocols and Key EstablishmentReza EsnaashariNo ratings yet
- Proposal On SSIDocument10 pagesProposal On SSIShubham DhakalNo ratings yet
- Zakaria Hamdino m2Document5 pagesZakaria Hamdino m2Zakaria HamdinoNo ratings yet
- Alternative Uses of The Blockchain I (2019!12!17 19-12-19 UTC)Document42 pagesAlternative Uses of The Blockchain I (2019!12!17 19-12-19 UTC)nerviosus locusNo ratings yet
- J Future 2018 08 029Document15 pagesJ Future 2018 08 029aliNo ratings yet
- PKI SecurityDocument64 pagesPKI SecurityVivien Di100% (1)
- Cassiopeia: Practical On-Chain Witness Encryption: Abstract. Witness Encryption Is A Holy Grail of Cryptography That ReDocument19 pagesCassiopeia: Practical On-Chain Witness Encryption: Abstract. Witness Encryption Is A Holy Grail of Cryptography That Reazucarado75No ratings yet
- Certificateless Public Key Cryptography: Public Key Cryptography (CL-PKC), A Model For The Use of Public Key CrypDocument22 pagesCertificateless Public Key Cryptography: Public Key Cryptography (CL-PKC), A Model For The Use of Public Key CrypDä PänNo ratings yet
- Cryptocurrencies: The Hidden Secrets to Master Cryptocurrencies in Just 3 DaysFrom EverandCryptocurrencies: The Hidden Secrets to Master Cryptocurrencies in Just 3 DaysNo ratings yet
- Department of Education: Republic of The PhilippinesDocument48 pagesDepartment of Education: Republic of The PhilippinesSophy SophyNo ratings yet
- Irb Protocol SBHFDocument7 pagesIrb Protocol SBHFbogus mailNo ratings yet
- CFA Exam Level 1: 2018 Cram NotesDocument48 pagesCFA Exam Level 1: 2018 Cram NotesMani ManandharNo ratings yet
- Partition Agreement: o The Portion of Two Thousand Seven Hundred Ninety (2,790) Square Meters DescribedDocument3 pagesPartition Agreement: o The Portion of Two Thousand Seven Hundred Ninety (2,790) Square Meters DescribedAidalyn MendozaNo ratings yet
- The Persuasive SpeechDocument2 pagesThe Persuasive Speechapi-629326078No ratings yet
- Product Management Report PDFDocument67 pagesProduct Management Report PDFEmma McQuillanNo ratings yet
- Topographic Map of Oak Hills NorthDocument1 pageTopographic Map of Oak Hills NorthHistoricalMapsNo ratings yet
- ENSC 1113 The Science of Global Challenges NotesDocument21 pagesENSC 1113 The Science of Global Challenges Notestalhahassanalvi786100% (2)
- Certificate of Good StandingsDocument5 pagesCertificate of Good StandingsRrichard Prieto MmallariNo ratings yet
- Alternative Risk Premia October 2019 1575682443 PDFDocument12 pagesAlternative Risk Premia October 2019 1575682443 PDFCaden LeeNo ratings yet
- Learning Express Proofreading Revising Editing Skills Success 205pDocument205 pagesLearning Express Proofreading Revising Editing Skills Success 205pphilipyap100% (1)
- Gmail - .Net Interview Confirmation - Cognizant Technology Solutions (Interview Date - 20th July 2019, Saturday - ICC Trade 4th Floor (B Wing), S B Road, Pune (Above Star Bazaar) Pune - 4119016 PDFDocument4 pagesGmail - .Net Interview Confirmation - Cognizant Technology Solutions (Interview Date - 20th July 2019, Saturday - ICC Trade 4th Floor (B Wing), S B Road, Pune (Above Star Bazaar) Pune - 4119016 PDFmahesh pawarNo ratings yet
- Reading. Forbes. 9 Differences Between Being A Leader and A ManagerDocument5 pagesReading. Forbes. 9 Differences Between Being A Leader and A ManagerHiNo ratings yet
- Patent Cooperation TreatyDocument11 pagesPatent Cooperation Treatyanubha0608_169697711No ratings yet
- RULE 110 Prosecution of Offenses I. Provisions and Notes: Vox Emissa Volat Litera Scripta Manet (The Spoken WordDocument5 pagesRULE 110 Prosecution of Offenses I. Provisions and Notes: Vox Emissa Volat Litera Scripta Manet (The Spoken WordEdward G-Boi DangilanNo ratings yet
- Interview Skill (Job & Negotiation)Document3 pagesInterview Skill (Job & Negotiation)annisaNo ratings yet
- Data Processing Agreement - MillionVerifierDocument7 pagesData Processing Agreement - MillionVerifierDorian Joel ZúñigaNo ratings yet
- 148895-1956-Florentino v. Philippine National BankDocument4 pages148895-1956-Florentino v. Philippine National BankJian CerreroNo ratings yet
- Ethical and Social Environment of ManagementDocument14 pagesEthical and Social Environment of ManagementmikkomartinezNo ratings yet
- Creating Oracle BI Publisher Report Using Template Builder: ExploreDocument8 pagesCreating Oracle BI Publisher Report Using Template Builder: ExploreAbebeNo ratings yet
- Jadwal Kuliah Ganjil 2019-2020 (Reg) BaruDocument5 pagesJadwal Kuliah Ganjil 2019-2020 (Reg) BarufikryNo ratings yet
- Small Wonder, SummariesDocument3 pagesSmall Wonder, SummariessagarchesterNo ratings yet
- References: 38 (s1), S25-S49, DoiDocument34 pagesReferences: 38 (s1), S25-S49, DoiMaxNo ratings yet
- HSE Incentive ProgramDocument7 pagesHSE Incentive ProgramDaniel GeneralNo ratings yet
- SAMPLE: User Experience: Buyer's Guide 2011Document36 pagesSAMPLE: User Experience: Buyer's Guide 2011Ricardo AraújoNo ratings yet
- Group 4 - The Rizal Law OutlineDocument3 pagesGroup 4 - The Rizal Law OutlineBaculio Janine G.No ratings yet
- Uet ThesisDocument34 pagesUet ThesisSADIA SAMINo ratings yet
- Debat Bahasa InggrisDocument4 pagesDebat Bahasa Inggrisnadela981No ratings yet
Befund USH EN
Befund USH EN
Uploaded by
renan silvaOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Befund USH EN
Befund USH EN
Uploaded by
renan silvaCopyright:
Available Formats
USH for Anonymous and Unlinkable Coin Spending for
BFDChain
Pu, Duan
Befund Foundation Ltd.
Abstract— In this paper, we propose Unlinkable potential risks: (1) Bob links Alice’s real-world
Secret Handshake (USH), which is based on Tate identity to her cryptocurrency identity/address (2) if
Paring cryptography, as a new protocol to provide Alice wants to purchase alcohol in the future, she will
anonymous and privacy-preserving coin spending need to disclose the same identity again to others
for BFDChain. which increase the risk to link up all her previous
transactions.
I. INTRODUCTION To solve this issue, we propose USH to achieve
anonymity and unlinkability for user’s credential like
A s one of the most important security aspects, how
to achieve unlinkability and anonymity is critical
the identity mentioned in the above example. We
assume that before the coin spending, both payer and
to the success of any blockchain systems because of
payee have already obtained credentials from a
its decentralized nature. We designed an unlinkable
central authority that cooperates with BFDChain (for
secret handshake (USH) protocol for BFDChain,
exmaple, DMV already built a sidechain on
which provides more anonymous and privacy-
BFDChain). Credential assignment can be built as a
preserving coin spending.
service or sub-chain attached to BFDchain. The
credential is to prove that the owner of the credential
The rest of this paper is organized as follows: In
is a member of a group, i.e., eligible for certain
Section II, we present the motivation to design and
purchase. USH protocol guarantees that (1) Bob
use USH for BFDChain. Then we provide a summary
cannot link Alice’s real-world identity to her
of threats to privacy and anonymity to on-chain
BFDchain ID/address after proving that she is
currencies. We then provide detailed technical
member of the group (2) Alice’s credential is
discussion of USH on BFDChain and its security
unlinkable, i.e., future same kind of transactions
analysis in Section IV and Section V, respectively.
won’t disclose her previous transaction. Furthermore,
Section VI concludes this paper.
even the central authority cannot know that it was
Alice who made the purchase from the public ledger
II. MOTIVATION of BFDchain.
One significant advantage to use on-chain currency is It is also well known that on-chain cryptocurrency
that user’s real-world identity is not disclosed when like BFDchain is built on elliptic curve cryptograph
sending or receiving payment, i.e. cryptocurrency (ECC), i.e., payer/payee’s addresses in coin wallet are
payment is sent to or received by user’s blockchain hashed values of elliptic curve point for signing and
address that is a hashed value of a single-time used verifying by elliptic curve digital signature algorithm
elliptic curve point. However, as payment is usually (ECDSA). USH is also designed on the same ECC
for real-world offline transaction, payer may need to based cryptosystem, so the new unlinkability and
disclose his email address or shipping address to anonymity for coin spending can be easily
complete the offline transaction or prove his implemented on BFDchain.
eligibility for the transaction. For example, Alice
wants to purchase alcohol from Bob. She needs to
disclose her real-world identity document to prove III. PRIVACY ISSUES IN CRYPTOCURRENCY
that she is over 21 years old before getting legally
There are many security concern and attacks for on-
qualified for the alcohol purchase. This causes two
chain currencies, e.g., doubling spending [1] and on elliptic curve so that our protocol can be
mining pool attacks [2] for Bitcoin. This paper implemented on BFDChain easily.
focuses on the privacy and anonymity issues for
cryptocurrencies. They achieve anonymity by 4.1 Mathematical Background
keeping public keys anonymous, i.e., the public can Definition 1: Bilinear Pairing
see payment is sent from payer to payee, but cannot A pairing is a bilinear map e: G1 × G1 → G2 if, for
link the transaction to anyone’s real identity. The any P, Q Î G1 and any a, b Î Z*q we have e(a×P,
reason is that both payer and payee use their hashed b×Q) = e(a×P, Q)b = e(P, b×Q)a = e(P, Q)a×b and
elliptic curve point as the address to send and receive e(P,Q) = e(Q, P)
payment. To further achieve the unlinkability, it is To provide an efficient computation of the bilinear
advised to use a new key pair for each transaction so map, we choose G1, G2 and e as a set of points on an
that no multiple transactions can be linked to the same elliptic curve, a multiplicative cyclic group over
user. However, the anonymity and unlinkability integers and Tate pairing, respectively. ECC has a
provided by the current on-chain currency are special discrete logarithm problem, Elliptic Curve
vulnerable through different attacks like address reuse, Discrete Logarithm Problem (ECDLP), defined as the
blockchain and public address analysis [3][4], etc. basis of elliptic curve cryptography (ECC). Based on
Also, adversary can make use of public web crawlers the parameters chosen above, another assumption we
the correlates social networks with cryptocurrency need is the BDH Assumption described as follows:
address like Bitcoin [5]. In [6] the authors mention Definition 2: Bilinear Diffie-Hellman (BDH) Assumption
that an adversary can associate the offline data like Given P, a×P, b×P, c×P for random a, b, c Î Z*q and
emails and shipping addresses with the online P Î G1, it is not possible to compute e(P, P)a×b×c with
information, then eventually get the private a non-negligible probability, i.e., it is hard to
information about the user. In [7] the authors show compute e(P, P)a×b×c
that cryptocurrency transactions can be linked to the In the follows we present the detail of the use of the
user cookies and then to the user’s real identity and homomorphic randomization in USH.
the user’s purchase history is revealed. Research [8][9]
also shows that the IP address in cryptocurrency P2P Definition 3: Homomorphic Randomization Function in
network might be the vulnerability that compromises SH
unlinkability. Suppose user U joins a group gi by obtaining a
credential gi×H1(IDU), where gi Î G2 represents the
To defend again these attacks, in [10] the authors group secret and H1(IDU) Î G1 represents U’s
propose ZeroCoin, which applies zero-knowledge assigned pseudonym. U selects a large random
authentication protocol to Bitcoin to provide integer sU Î G2, and uses the addition operation
anonymity. An extension of ZeroCoin is proposed by defined in G1 to compute sU× gi×H1(IDU) (sU times of
[11] as ZeroCash, which uses an improved version of addition of gi×H1(IDU)).
zero-knowledge proof. Also, the second generation of
cryptocurrencies like Ethereum [12] are designed Formal Definition of Secret Handshake: Alice has a pair
with better consideration for security and privacy
consisting of a pseudonym and a credential, ID_A and
issues. C_A, assigned from a central authority. Bob has his
ID_B and C_B assigned from a central authority.
IV. USH FOR UNLINKABLE AND After the execution of an SH protocol, Alice and Bob
ANONYMOUS COIN SPENDING ON BFDCHAIN know that C_A and C_B indicate common same group
membership if SH succeeds; otherwise, Alice (Bob)
cannot know anything about C_B(C_A). In addition,
The motivation to design and use of USH for Alice (Bob) cannot know who she (he) interacted with.
BFDchain is to provide privacy-preserving and
anonymous coin spending for both online and offline 4.2 USH for BFDChain
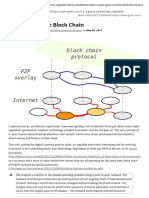
interactions for participants. We design USH based We will use the Fig.1 to illustrate how USH works on
on Tate Paring cryptography that is also built on top top of BFDChain.
Our proposed USH has three phases: Protocol
Initialization, Group Secret Mapping and
Authentication Computing. To be consistent with
other cryptographic protocol, we use Alice to
represent payer and Bob for payee. In the follows we
present the detail of the three phases.
Phase 1: Protocol Initialization
The CA determines the pairing parameters (q, G1, G2,
Fig.1 USH for BFDChain e, H1, H2) and group secrets [g1,…, gn], where gi Î G2.
In this section, we present the detail of USH on The CA publishes the pairing parameters while
BFDChain. We assume that payer and payee have keeping the group secrets in private. Alice requests
already registered in a central authority (CA) and
the CA to join the group with group secret gA Î [g1,…,
obtained credential that can be used to authenticate gn]. The CA verifies Alice’s qualification to decide
their membership to a secret group. CA collaborates
whether Alice can join the group. If yes, the CA
with BFDChain so that the credential assignment to
grants the group membership to Alice by issuing her
payer and payee is a service on the chain, a sub-chain
a credential gA×H1(IDA) Î G1, where gA Î G2. The
attached to the main chain. Then the payer and payee
credential is a secret of Alice to prove her
apply the unlinkable and anonymous secret
membership in group gA to another user in the same
handshake protocol, USH, to authenticate that the
payer is eligible for the transaction/purchase. The group. Alice cannot deduce gA from gA×H1(IDA) and
payer can also verify the payee’s eligibility if required. H1(IDA) by the assumption that DLP is hard in G1. It
If authentication succeeds, the payer and payee is important for preventing forgery of credentials.
continue for their transaction with BFDT. Otherwise, Users Alice and Bob use their credentials, KA =
either party can cancel the transaction. gA×H1(IDA) and KB = gB×H1(IDB), to generate
authentication messages to one another. Alice
Our main idea is to use the homomorphic randomly generates two large random numbers, nA1
randomization function in the Protocol and sA1. Alice computes WA1 = sA1×H1(IDA), as
Randomization phase to randomize user’s assigned described in the homomorphic randomization
pseudonyms to provide reusability of credentials. function above. That said, sA1 is used to minimize the
More specifically, we let a user generate a secret correlations of authentication messages produced by
random number in execution of the secret handshake. the same credential. Since using a credential multiple
The user multiplies the random number to an elliptic times will not create messages that can link to the user
curve point that represents the user’s pseudonym. The identity, our credential is reusable. nA1 prevents replay
random number minimizes the correlation among attacks. Bob also randomly generates two large
authentication messages even they are produced by numbers, nB1 and sB1, for the same purpose. Detailed
reuse of the same credential. First we present the interactions of group secret mapping phase and
parameters that are required in USH as (q, G1, G2, e, authentication computing phase are described as
H1, H2). Here q is a large prime number, G1 denotes follows:
an additive cyclic group of prime order q, G2 denotes Phase 2 and Phase 3: Group Secret Mapping and
a multiplicative cyclic group of the same order q, H1 Authentication Computing
is a collision-free hash function that maps a string
with arbitrary length to an element in G1, H2 is a
(a) Alice →Bob: nA1, WA1 = sA1×H1(IDA)
collision-free hash function that maps a string with
arbitrary length to a string with fixed length, and e (b) Bob: Compute VB,A = H2(U B,A || nA1 || nB1 || 0), U
denotes a bilinear map. G1 and G2 are selected in such B,A = e(WA1, sB1×KB). Here Bob implements the
a way that Discrete Logarithm Problem (DLP) is secret mapping function to map his own
assumed to be hard in both of them. credential KB = gB×H1(IDB) from an element in G1
to an element in G2 through bilinear map e.
(c) Bob →Alice: nB1, WB1 = sB1×H1(IDB), VB,A
(d) Alice: Compute V’B,A = H2(U’B,A || nA1 || nB1 || 0), Outside adversary: a malicious party that is an
U’B,A = e(WB1, sA1×KA). If VB,A = V’B,A, then Alice outsider of an authentication process. An outside
knows Bob belongs to the same group, i.e., gA = adversary does not participate in the authentication
gB. Otherwise, Bob belongs to a different group, process and knows nothing about the transmitted
i.e., gA ¹ gB or Bob belongs to no group. Here messages.
Alice implements the result computing function to Inside adversary: a malicious party that participates
find out whether H2(U’B,A || nA1 || nB1 || 0) = H2(U in an authentication process. The adversarial insider
B,A || nA1 || nB1 || 0). may have some matched group secrets with the
(e) Alice →Bob: VA,B = H2(U’B,A || nA1 || nB1 || 1) targeted victim and try to discover other unmatched
group secrets the victim has.
(f) Bob: Compute V’A,B = H2(U B,A || nA1 || nB1 || 1). If
VA,B = V’A,B, Bob knows that Alice belongs to the Based on the adversary model and attack model
same group. Otherwise, Alice belongs to a introduced above, we claim that our privacy-
different group, i.e., gA ¹ gB or Alice belongs to no preserving correlation technique provides the
group. following main security properties: unlinkability with
reusable credential and group membership
The protocol succeeds when VB,A = V’B,A and VA,B =
authenticity. In Theorem 1 we first prove that USH
V’A,B in steps (d) and (f). Based on the BDH
that uses homomorphic randomization function
assumption, it succeeds if, and only if, gA = gB.
provides unlinkability with reusable credential.
Otherwise, if it fails, Alice and Bob only know gA ¹
gB. Users other than Alice and Bob cannot know Theorem 1. USH holds Unlinkability on
whether gA = gB or not, because they cannot compute Homomorphic Randomization
V’B,A and V’A,B without KA and KB. A sketch of proof A privacy-preserving authentication protocol that
for VB,A = V’B,A is shown in (1). The rest of proof for uses homomorphic randomization function in
VA,B = V’A,B can be derived similarly. protocol initialization phase guarantees unlinkability
with reusable credential.
VB,A = H2(UB,A || nA1 || nB1 || 0) = H2(e(WA1, sB1×KB) || nA1 || nB1 || 0) Proof: Suppose user k requests to join a group with
= H2(e(sA1×H1(IDA), sB1×gB×H1(IDB)) || nA1 || nB1 || 0)
group secret gk Î G2. The CA grants the group
membership to k by issuing a credential gk×H1(IDK) Î
= H2(e(sA1×gB×H1(IDA), sB1×H1(IDB)) || nA1 || nB1 || 0)
G1, where IDk represents k’s assigned pseudonym
= H2(e(sB1×H1(IDB), sA1×gB×H1(IDA)) || nA1 || nB1 || 0) associated with gk. k cannot deduce gk from gk×H1(IDk).
= H2(e(WB1, sA1×KA) || nA1 || nB1 || 0) //iff, gA = gB There are two adversaries, t1 and t2, who want to know
= H2(U’B,A || nA1 || nB1 || 0) = V’B,A (1) whether they are interacting with same party and
which group this party belongs to. Assume that t1 is
The secret handshake protocol guarantees that 1) Bob not a member in group gk and t2 is. t2 may
cannot link Alice’s real-world identity to her communicate with other legitimate owners of group
BFDChain address after authenticating her credential. secret gk, corrupt some valid parties and obtain their
2) Alice’s credential is unlinkable. In future the same secrets. Here we use Uk to denote the set of users who
kind of transactions won’t be linked to her previous own the group secret gk. Now we define a Linkability
transaction. Furthermore, even the CA cannot know Detection Game as follows.
that it was Alice who made the purchase with Bob Step 1: The adversaries t1 and t2 communicate with k
given the public ledger of BFDChain. based on their own choices. From t1’s viewpoint, he
is interacting with party k1; from t2’s viewpoint, he is
V. SECURITY ANALYSIS interacting with party k2.
In the proposed USH protocol we consider any Step 2: T2 selects other parties Uc and corrupt them.
passive attack that aims at compromising Step 3: After the executions of USH protocol t1 and t2
confidentiality of sensitive information by analyzing want to find out whether k1 = k2. If yes, they know that
transmitted messages, e.g., dictionary attack to they are interacting with a same party and t2 knows
transmitted messages. We consider both outside that k2 has group secret gk.
adversaries and inside adversaries as follows.
We say that t1 and t2 win the Linkability Detection who own the targeted s. A picks a target user uTÎ UT,
Game if they find out that k1 = k2 and k2 has group and wants to convince uT that A is also an owner of
secret gk. the targeted s, i.e. A Î UT. We define the Group
Now we define the following probabilities: Membership Owner Impersonation Game for a
GL = Pr[t1 and t2 win Linkability Detection Game] – randomized, polynomial-time adversary A as follows.
0.5 Step 1: The adversary A communicates with owners
of the targeted s based on its own choice. A may
When t2 does not compromise any valid owner of Uk, compromise certain user UC Í U and obtain their
the above probability becomes: secrets, where UC denotes the set of compromised
GL|(UcÇUk)=Æ = Pr[t1 and t2 win Linkability Detection users and U denotes the whole user set in the network
Game | (UcÇ Uk)=Æ] – 0.5 G.
Step 2: A selects a target user uT Ï UC and uTÎ UT,
Here we say that our protocol holds unlinkability with where users in UT own the targeted s.
reusable credential if GA|(UcÇUk)=Æ is negligible for Step 3: A wants to convince uT that A owns the s, i.e.
any adversaries t1 and t2. In our protocol k generates A Î UT.
random numbers sk1 and sk2 to manipulate his assigned
pseudonym IDk and get elliptic curve points Wk1 = We say that A wins the Group Membership Owner
sk1×H1(IDk) and Wk2 = sk2×H1(IDk) as his randomized Impersonation Game if it convinces uT that it is an
identities for t1 and t2, respectively. Here Wk1 and Wk2 owner of s.
are generated to map k’s pseudonyms to random ECC Now we define the following probabilities:
points through the homomorphic randomization GA = Pr[ A wins Group Membership Owner
function as random oracles. By the assumptions that Impersonation Game]
DLP is hard in G1, no polynomial-time adversary
cannot deduce sk1 and sk2 from Wk1 = sk1×H1(IDk) and When A does not compromise any valid owner of s,
the above probability becomes:
Wk1 = sk1×H1(IDk) and thus cannot know Wk1 and Wk2
are generated based on the same pseudonym IDk. That G’A|(UCÇUT)=Æ = Pr[A wins Group Membership
said, their guess about whether k1 = k2 is no better Owner Impersonation Game | (UCÇ UT)=Æ]
than a random guess. Our protocol holds unlinkability
Here we say that our protocol holds Group
with reusable credential.
Membership Authenticity if G’ A|(UCÇUT)=Æ is
Theorem 2. USH holds Group Membership negligible for any adversary A. Similar to Theorem 1,
Authenticity we can further prove that USH holds group
In our protocol, the group membership authenticity membership authenticity. Detail of the proof is
means that an adversary cannot convince another omitted here since it is out of the scope of this paper.
party that it owns the group memberships as this party
has by interacting with him. In other words, the Theorem 1 proves that payer only needs to obtain the
adversary cannot impersonate owners of some credential from the central authority once, then he can
targeted group secrets. Because of the hardness of process this credential with homomorphic
ECDLP and BDH assumption, our protocol provides randomization and use it any times for authentication
group membership authenticity that any polynomial- without being linked to his real identity or his original
time adversary only has negligible probability of credential. Theorem 2 proves that no one can
cheating as a valid owner of some group membership impersonate the owner of the assigned credential.
without corrupting another valid owner of the
targeted group secret. Now we define the Group VI. CONCLUSION
Membership Owner Impersonation game. In this paper, we proposed USH to achieve privacy-
Proof: suppose there is an adversary A who aims at preserving and anonymous coin spending for
impersonating the owner of a group secret s. A may BFDChain. We discussed the motivation and
communicate with legitimate owners of the targeted s provided the formal security analysis of the proposed
in network G, corrupt some valid users and obtain protocol. It will be critical for the success of any on-
their secrets. Here we use UT to denote the set of users chain currency since it allows participants to bring
their real-world membership to the cryptocurrency for [11]E. B. Sasson, A. Chiesa, C. Garman, M. Green, I.
their coin spending with unlinkability and anonymity. Miers, E. Tromer, and M. Virza, “Zerocash:
Decentralized anonymous payments from bitcoin,”
REFERENCES in 2014 IEEE Symposium on Security and
[1] G. O. Karame, E. Androulaki, and S. Capkun, Privacy, May 2014, pp. 459–474.
“Double-spending fast payments in bitcoin,” in [12]Ethereum: A secure decentralized generaliaed
Proceedings of the 2012 ACM Conference on transaction ledger EIP-150 revision”, Gavin
Computer and Communications Security, ser. Wood
CCS ’12. New York, NY, USA: ACM, 2012, pp.
906–917.
[2] N. T. Courtois and L. Bahack, “On subversive
miner strategies and block withholding attack in
bitcoin digital currency,” CoRR, vol.
abs/1402.1718, 2014.
[3] D. Ron and A. Shamir, “Quantitative analysis of
the full bitcoin transaction graph,” in Financial
Cryptography and Data Security: 17th
International Conference, FC 2013. Springer
Berlin Heidelberg, 2013, pp. 6–24.
[4] E. Androulaki, G. O. Karame, M. Roeschlin, T.
Scherer, and S. Capkun,“Evaluating user privacy
in bitcoin,” in Financial Cryptography and Data
Security: 17th International Conference, FC 2013.
Springer Berlin Heidelberg, 2013, pp. 34–51.
[5] M. Fleder, M. S. Kester, and S. Pillai, “Bitcoin
transaction graph analysis,” CoRR, vol.
abs/1502.01657, 2015.
[6] P. Koshy, D. Koshy, and P. McDaniel, “An
analysis of anonymity in bitcoin using p2p
network traffic,” in Financial Cryptography and
Data Security: 18th International Conference, FC
2014,. Springer Berlin Heidelberg, 2014, pp. 469–
485.
[7] S. Goldfeder, H. A. Kalodner, D. Reisman, and A.
Narayanan, “When the cookie meets the
blockchain: Privacy risks of web payments via
cryptocurrencies,” CoRR, 2017.
[8] A. Biryukov, D. Khovratovich, and I. Pustogarov,
“Deanonymisation of clients in bitcoin p2p
network,” in Proceedings of the 2014 ACM
SIGSAC Conference on Computer and
Communications Security, ser.CCS ’14. ACM,
2014, pp. 15–29.
[9] A. Biryukov and I. Pustogarov, “Bitcoin over tor
isn’t a good idea,” in 2015 IEEE Symposium on
Security and Privacy, May 2015, pp. 122–134.
[10]I. Miers, C. Garman, M. Green, and A. D. Rubin,
“Zerocoin: Anonymous distributed e-cash from
bitcoin,” in 2013 IEEE Symposium on Security
and Privacy, May 2013, pp. 397–411.
You might also like
- Paul de Man - Rhetoric of TemporalityDocument23 pagesPaul de Man - Rhetoric of TemporalityEgor Sofronov100% (3)
- Book Report of My Brother, My Executioner byDocument7 pagesBook Report of My Brother, My Executioner bycrimsonlover17% (6)
- Digital Cash (Anonymous Online Payment Scheme)Document11 pagesDigital Cash (Anonymous Online Payment Scheme)Arif Masood100% (5)
- CS5460 ChadMaughan Assignment4Document3 pagesCS5460 ChadMaughan Assignment4the_tigdraNo ratings yet
- Minimum Viable Block ChainDocument20 pagesMinimum Viable Block ChainAlbertoNo ratings yet
- 02 Key Management and Public Key Infrastructure ADocument51 pages02 Key Management and Public Key Infrastructure ADevil KenwayNo ratings yet
- GBGN17 FC Physical - EscrowDocument27 pagesGBGN17 FC Physical - EscrowChristos FloridisNo ratings yet
- Zerocoin - Anonymous Distributed E-Cash From Bitcoin PDFDocument15 pagesZerocoin - Anonymous Distributed E-Cash From Bitcoin PDFgeckxNo ratings yet
- PKI (Public Key Infrastructure) : P e P e e e PDocument2 pagesPKI (Public Key Infrastructure) : P e P e e e Psimon sylvesterNo ratings yet
- How Does The Blockchain Work - OneZeroDocument15 pagesHow Does The Blockchain Work - OneZeroSanchit AggarwalNo ratings yet
- Coinparty: Secure Multi-Party Mixing of BitcoinsDocument12 pagesCoinparty: Secure Multi-Party Mixing of BitcoinsAdolf CohAlcarazNo ratings yet
- Paper 3. Zerocoin Anonymous Distributed E-Cash From BitcoinDocument15 pagesPaper 3. Zerocoin Anonymous Distributed E-Cash From BitcoinQubits 01No ratings yet
- Zerocash: Decentralized Anonymous Payments From Bitcoin: 2014 IEEE Symposium On Security and PrivacyDocument16 pagesZerocash: Decentralized Anonymous Payments From Bitcoin: 2014 IEEE Symposium On Security and PrivacyjasonwNo ratings yet
- Chapters 1.key Management 2.Authentication-I 3.Authentication-Ii 4.Ipsec-Security at The Network Layer 5.security at Transport LayerDocument56 pagesChapters 1.key Management 2.Authentication-I 3.Authentication-Ii 4.Ipsec-Security at The Network Layer 5.security at Transport LayerRavish ShankarNo ratings yet
- DCAP Anonymous Payment SystemDocument13 pagesDCAP Anonymous Payment Systemholar45575No ratings yet
- Key Management and Public Key InfrastructureDocument61 pagesKey Management and Public Key InfrastructureAkash MahapatraNo ratings yet
- Gematmw Y10 Individual Project 1Document12 pagesGematmw Y10 Individual Project 1Nevan NovaNo ratings yet
- WhitepaperDocument45 pagesWhitepapersiddevice162No ratings yet
- Secure Hierarchical Bitcoin Wallet Scheme Against Privilege Escalation AttacksDocument11 pagesSecure Hierarchical Bitcoin Wallet Scheme Against Privilege Escalation AttacksKing's MonarchNo ratings yet
- How Does The Blockchain Work?: Blockchain Technology Explained in Simple WordsDocument27 pagesHow Does The Blockchain Work?: Blockchain Technology Explained in Simple WordsrainsolinNo ratings yet
- Trust Is Risk: A Decentralized Financial Trust PlatformDocument18 pagesTrust Is Risk: A Decentralized Financial Trust PlatformorfeasNo ratings yet
- CH Security ProtocolsDocument27 pagesCH Security ProtocolsMuhammad asafNo ratings yet
- Network Security UNIT 2Document30 pagesNetwork Security UNIT 2smitcse2021No ratings yet
- Block - Chain SolutionDocument30 pagesBlock - Chain SolutionPk Bijoy100% (1)
- Chapters 1.key Management 2.Authentication-I 3.Authentication-Ii 4.Ipsec-Security at The Network Layer 5.security at Transport LayerDocument56 pagesChapters 1.key Management 2.Authentication-I 3.Authentication-Ii 4.Ipsec-Security at The Network Layer 5.security at Transport LayerSudha SreedeviNo ratings yet
- Prsentation On IdentityBased-PREDocument29 pagesPrsentation On IdentityBased-PREosama ahmedNo ratings yet
- Block ChainDocument9 pagesBlock ChainChinmayi HSNo ratings yet
- Grid Computing 7700: Fall 2005 Lecture 16: Grid SecurityDocument32 pagesGrid Computing 7700: Fall 2005 Lecture 16: Grid SecurityJaswanth RoyalNo ratings yet
- Blockchain TutorialDocument16 pagesBlockchain TutorialDr. Ramu Kuchipudi Associate Professor (Contract)No ratings yet
- Zero KnowledgeDocument5 pagesZero KnowledgeMarcos CorrêaNo ratings yet
- Jerad Bates - Public Key InfrastructureDocument30 pagesJerad Bates - Public Key Infrastructurevenkatesh VRNo ratings yet
- A Protocol For Preventing Transaction Commitment Without Recipients Authorization On Blockchain and Its ImplementationDocument16 pagesA Protocol For Preventing Transaction Commitment Without Recipients Authorization On Blockchain and Its ImplementationAnitha TNo ratings yet
- Information Systems Security LAB: Key ManagementDocument10 pagesInformation Systems Security LAB: Key ManagementAbdullah Al-HallakNo ratings yet
- cns4 1Document12 pagescns4 1gadidheerajreddy.20.itNo ratings yet
- Security and CryptographyDocument6 pagesSecurity and Cryptographykelciefay8No ratings yet
- CH 10 ExtractDocument22 pagesCH 10 ExtractMuhammad asafNo ratings yet
- Blockchain Guide Starter Cryptocurrency ExplainationDocument12 pagesBlockchain Guide Starter Cryptocurrency ExplainationViktor OmsNo ratings yet
- Structure and Anonymity of The Bitcoin Transaction GraphDocument14 pagesStructure and Anonymity of The Bitcoin Transaction GraphshamanjrNo ratings yet
- Key ManagementDocument28 pagesKey Managementanon_212627844No ratings yet
- CryptoNote v1Document16 pagesCryptoNote v1ze355rNo ratings yet
- UnicryptoDocument5 pagesUnicryptoNikhil AnandNo ratings yet
- InfSec 7 PKIDocument24 pagesInfSec 7 PKINhư NguyễnNo ratings yet
- Public Key Infrastructure: Jim HurstDocument5 pagesPublic Key Infrastructure: Jim HurstBARNALI GUPTANo ratings yet
- Know Your Customer: Opening A New Bank Account Online Using UAAFDocument2 pagesKnow Your Customer: Opening A New Bank Account Online Using UAAFaldykurniawanNo ratings yet
- What Is Blockchain Technology?Document31 pagesWhat Is Blockchain Technology?alenNo ratings yet
- Web 3 GlosaryDocument51 pagesWeb 3 GlosaryFranzNo ratings yet
- CryptoNote v1 (Archive - Org)Document16 pagesCryptoNote v1 (Archive - Org)ze355rNo ratings yet
- How Perfect Offline Wallets Can Still Leak Bitcoin Private KeysDocument11 pagesHow Perfect Offline Wallets Can Still Leak Bitcoin Private Keysmorten44No ratings yet
- Deanonymisation of Clients in Bitcoin P2P NetworkDocument15 pagesDeanonymisation of Clients in Bitcoin P2P NetworkGary ShenNo ratings yet
- Lecture 5Document10 pagesLecture 5AHMED DARAJNo ratings yet
- Chapter 18: Fundamentals of The Public Key InfrastructureDocument21 pagesChapter 18: Fundamentals of The Public Key Infrastructureflorinn81No ratings yet
- Secure Multiparty Computations On BitcoinDocument18 pagesSecure Multiparty Computations On Bitcoinmoferi9083No ratings yet
- Deanonymisation of Clients in Bitcoin P2P Network: Alex Biryukov Dmitry Khovratovich Ivan PustogarovDocument14 pagesDeanonymisation of Clients in Bitcoin P2P Network: Alex Biryukov Dmitry Khovratovich Ivan PustogarovDelraja Washington BrownNo ratings yet
- Authentication Protocols and Key EstablishmentDocument34 pagesAuthentication Protocols and Key EstablishmentReza EsnaashariNo ratings yet
- Proposal On SSIDocument10 pagesProposal On SSIShubham DhakalNo ratings yet
- Zakaria Hamdino m2Document5 pagesZakaria Hamdino m2Zakaria HamdinoNo ratings yet
- Alternative Uses of The Blockchain I (2019!12!17 19-12-19 UTC)Document42 pagesAlternative Uses of The Blockchain I (2019!12!17 19-12-19 UTC)nerviosus locusNo ratings yet
- J Future 2018 08 029Document15 pagesJ Future 2018 08 029aliNo ratings yet
- PKI SecurityDocument64 pagesPKI SecurityVivien Di100% (1)
- Cassiopeia: Practical On-Chain Witness Encryption: Abstract. Witness Encryption Is A Holy Grail of Cryptography That ReDocument19 pagesCassiopeia: Practical On-Chain Witness Encryption: Abstract. Witness Encryption Is A Holy Grail of Cryptography That Reazucarado75No ratings yet
- Certificateless Public Key Cryptography: Public Key Cryptography (CL-PKC), A Model For The Use of Public Key CrypDocument22 pagesCertificateless Public Key Cryptography: Public Key Cryptography (CL-PKC), A Model For The Use of Public Key CrypDä PänNo ratings yet
- Cryptocurrencies: The Hidden Secrets to Master Cryptocurrencies in Just 3 DaysFrom EverandCryptocurrencies: The Hidden Secrets to Master Cryptocurrencies in Just 3 DaysNo ratings yet
- Department of Education: Republic of The PhilippinesDocument48 pagesDepartment of Education: Republic of The PhilippinesSophy SophyNo ratings yet
- Irb Protocol SBHFDocument7 pagesIrb Protocol SBHFbogus mailNo ratings yet
- CFA Exam Level 1: 2018 Cram NotesDocument48 pagesCFA Exam Level 1: 2018 Cram NotesMani ManandharNo ratings yet
- Partition Agreement: o The Portion of Two Thousand Seven Hundred Ninety (2,790) Square Meters DescribedDocument3 pagesPartition Agreement: o The Portion of Two Thousand Seven Hundred Ninety (2,790) Square Meters DescribedAidalyn MendozaNo ratings yet
- The Persuasive SpeechDocument2 pagesThe Persuasive Speechapi-629326078No ratings yet
- Product Management Report PDFDocument67 pagesProduct Management Report PDFEmma McQuillanNo ratings yet
- Topographic Map of Oak Hills NorthDocument1 pageTopographic Map of Oak Hills NorthHistoricalMapsNo ratings yet
- ENSC 1113 The Science of Global Challenges NotesDocument21 pagesENSC 1113 The Science of Global Challenges Notestalhahassanalvi786100% (2)
- Certificate of Good StandingsDocument5 pagesCertificate of Good StandingsRrichard Prieto MmallariNo ratings yet
- Alternative Risk Premia October 2019 1575682443 PDFDocument12 pagesAlternative Risk Premia October 2019 1575682443 PDFCaden LeeNo ratings yet
- Learning Express Proofreading Revising Editing Skills Success 205pDocument205 pagesLearning Express Proofreading Revising Editing Skills Success 205pphilipyap100% (1)
- Gmail - .Net Interview Confirmation - Cognizant Technology Solutions (Interview Date - 20th July 2019, Saturday - ICC Trade 4th Floor (B Wing), S B Road, Pune (Above Star Bazaar) Pune - 4119016 PDFDocument4 pagesGmail - .Net Interview Confirmation - Cognizant Technology Solutions (Interview Date - 20th July 2019, Saturday - ICC Trade 4th Floor (B Wing), S B Road, Pune (Above Star Bazaar) Pune - 4119016 PDFmahesh pawarNo ratings yet
- Reading. Forbes. 9 Differences Between Being A Leader and A ManagerDocument5 pagesReading. Forbes. 9 Differences Between Being A Leader and A ManagerHiNo ratings yet
- Patent Cooperation TreatyDocument11 pagesPatent Cooperation Treatyanubha0608_169697711No ratings yet
- RULE 110 Prosecution of Offenses I. Provisions and Notes: Vox Emissa Volat Litera Scripta Manet (The Spoken WordDocument5 pagesRULE 110 Prosecution of Offenses I. Provisions and Notes: Vox Emissa Volat Litera Scripta Manet (The Spoken WordEdward G-Boi DangilanNo ratings yet
- Interview Skill (Job & Negotiation)Document3 pagesInterview Skill (Job & Negotiation)annisaNo ratings yet
- Data Processing Agreement - MillionVerifierDocument7 pagesData Processing Agreement - MillionVerifierDorian Joel ZúñigaNo ratings yet
- 148895-1956-Florentino v. Philippine National BankDocument4 pages148895-1956-Florentino v. Philippine National BankJian CerreroNo ratings yet
- Ethical and Social Environment of ManagementDocument14 pagesEthical and Social Environment of ManagementmikkomartinezNo ratings yet
- Creating Oracle BI Publisher Report Using Template Builder: ExploreDocument8 pagesCreating Oracle BI Publisher Report Using Template Builder: ExploreAbebeNo ratings yet
- Jadwal Kuliah Ganjil 2019-2020 (Reg) BaruDocument5 pagesJadwal Kuliah Ganjil 2019-2020 (Reg) BarufikryNo ratings yet
- Small Wonder, SummariesDocument3 pagesSmall Wonder, SummariessagarchesterNo ratings yet
- References: 38 (s1), S25-S49, DoiDocument34 pagesReferences: 38 (s1), S25-S49, DoiMaxNo ratings yet
- HSE Incentive ProgramDocument7 pagesHSE Incentive ProgramDaniel GeneralNo ratings yet
- SAMPLE: User Experience: Buyer's Guide 2011Document36 pagesSAMPLE: User Experience: Buyer's Guide 2011Ricardo AraújoNo ratings yet
- Group 4 - The Rizal Law OutlineDocument3 pagesGroup 4 - The Rizal Law OutlineBaculio Janine G.No ratings yet
- Uet ThesisDocument34 pagesUet ThesisSADIA SAMINo ratings yet
- Debat Bahasa InggrisDocument4 pagesDebat Bahasa Inggrisnadela981No ratings yet