Professional Documents
Culture Documents
0 ratings0% found this document useful (0 votes)
1 viewsIOT Micro by Sid
IOT Micro by Sid
Uploaded by
elonid786Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
You might also like
- MaxbountyapiDocument15 pagesMaxbountyapiUzzik JahatNo ratings yet
- Sketch The Architecture of Iot Toolkit and Explain Each Entity in BriefDocument9 pagesSketch The Architecture of Iot Toolkit and Explain Each Entity in BriefprabhaNo ratings yet
- Group Reporting Rubrics PDFDocument1 pageGroup Reporting Rubrics PDFhaniebalmNo ratings yet
- Choosing The Right Rtos For Iot Platform: March 2015Document7 pagesChoosing The Right Rtos For Iot Platform: March 2015okokoNo ratings yet
- Module 2 - Internet of Things - FinalDocument22 pagesModule 2 - Internet of Things - Finalelsa galgaoNo ratings yet
- Tinywow Iot Lab Manual 6768824Document33 pagesTinywow Iot Lab Manual 6768824Girish BabuNo ratings yet
- Iot and Applications SUBJECT CODE: 2180709: Laboratory ManualDocument38 pagesIot and Applications SUBJECT CODE: 2180709: Laboratory ManualSiva RamanNo ratings yet
- Tinywow Iot Lab Manual 6768835Document33 pagesTinywow Iot Lab Manual 6768835Girish BabuNo ratings yet
- Engineering An Iot-Edge-Cloud Computing System Architecture: Lessons Learnt From An Undergraduate Lab CourseDocument14 pagesEngineering An Iot-Edge-Cloud Computing System Architecture: Lessons Learnt From An Undergraduate Lab CourseAdama SOWNo ratings yet
- An Application Based Comparative Study of Lpwan Technologies For Iot EnvironmentDocument4 pagesAn Application Based Comparative Study of Lpwan Technologies For Iot EnvironmentTajbia HossainNo ratings yet
- Iot Uni-1Document53 pagesIot Uni-1sameer khanNo ratings yet
- Implementing Nb-Iot in Software - Experiences Using The Srslte LibraryDocument5 pagesImplementing Nb-Iot in Software - Experiences Using The Srslte LibraryKabamba Franck MUTEBANo ratings yet
- Demo - OpenAirInterface An Open LTE Network in A PCDocument3 pagesDemo - OpenAirInterface An Open LTE Network in A PCAmir EsparhamNo ratings yet
- Internet of Things - Architecture and Protocols - Unit 1Document56 pagesInternet of Things - Architecture and Protocols - Unit 1PrudhviNo ratings yet
- Ravel Riliskis Iotapp15Document6 pagesRavel Riliskis Iotapp15yousefNo ratings yet
- Intent Harmonization FWK ChangesDocument23 pagesIntent Harmonization FWK Changesquan voNo ratings yet
- A Comparative Study of AODV, DSR, and DYMO Routing Protocols Using OMNeT++Document5 pagesA Comparative Study of AODV, DSR, and DYMO Routing Protocols Using OMNeT++hhakim32No ratings yet
- Iot Ut - 2Document20 pagesIot Ut - 2Name SurnameNo ratings yet
- Abhinav RastogiDocument4 pagesAbhinav RastogiabhihackzNo ratings yet
- IoT Chapter 5Document36 pagesIoT Chapter 5piyalmajumderNo ratings yet
- Iot Architecture, Onem2M Model, Reference Model: L-T-P - (C) 4-0-0Document25 pagesIot Architecture, Onem2M Model, Reference Model: L-T-P - (C) 4-0-0deva dattaNo ratings yet
- Experiment 9Document29 pagesExperiment 9Aman SharmaNo ratings yet
- Chapter 4Document6 pagesChapter 4sarthak kothariNo ratings yet
- 2010 Aims 6lowpanDocument6 pages2010 Aims 6lowpanJeya Shree Arunjunai RajNo ratings yet
- Internet of Things - Architecture and Protocols - Unit 3Document51 pagesInternet of Things - Architecture and Protocols - Unit 3PrudhviNo ratings yet
- IoT Chapter 5Document36 pagesIoT Chapter 5piyalmajumderNo ratings yet
- Unit 2 NotesDocument99 pagesUnit 2 NotesKaushalNo ratings yet
- Abhishek Kumar Iot Assgn1 and Asgn 2Document36 pagesAbhishek Kumar Iot Assgn1 and Asgn 2Abhishek KumarNo ratings yet
- Unit 2Document99 pagesUnit 2nagamalleswari2010No ratings yet
- Stmicro Mcu Pfe 2012xDocument15 pagesStmicro Mcu Pfe 2012xkbma2009No ratings yet
- Network Analyzer and Report Generation Tool For NS-2 Using TCL ScriptDocument6 pagesNetwork Analyzer and Report Generation Tool For NS-2 Using TCL Scriptأبو أيوب تافيلالتNo ratings yet
- 3-Modul - PTI412 - IoT-1-2020Document16 pages3-Modul - PTI412 - IoT-1-202020200801015 Joko SulistyoNo ratings yet
- Midterm Exam Review Questions 1 - NewDocument21 pagesMidterm Exam Review Questions 1 - NewSirus DanhNo ratings yet
- Lecture 4Document21 pagesLecture 4najmi ariffinNo ratings yet
- IoT Protocols Antion JaimeDocument65 pagesIoT Protocols Antion JaimeandyNo ratings yet
- Shen Open5g Wico July2017Document28 pagesShen Open5g Wico July2017prashant817No ratings yet
- AML2018 Rentschler Fieldbus Topologies PaperDocument11 pagesAML2018 Rentschler Fieldbus Topologies Paperrodrigo.rpg.scNo ratings yet
- 4 - Designing Embedded Networking ApplicationsDocument23 pages4 - Designing Embedded Networking ApplicationsBrian roshNo ratings yet
- DEVASC Module 8Document134 pagesDEVASC Module 8JUAN MAURICIO QUEZADA JAMASMIENo ratings yet
- Module 1 LTE INTRO NB-IOTDocument30 pagesModule 1 LTE INTRO NB-IOTahad siddiquiNo ratings yet
- Only Provide The Important Points Which Can Come...Document55 pagesOnly Provide The Important Points Which Can Come...darthrishav2No ratings yet
- U-5 HalfDocument218 pagesU-5 HalfK.P.Revathi Asst prof - IT DeptNo ratings yet
- Internal 2 - Answer - 16 MarksDocument3 pagesInternal 2 - Answer - 16 MarksVelmurugan T - ECENo ratings yet
- Pankaj ResumeDocument3 pagesPankaj ResumeHemlata GuptaNo ratings yet
- Narrow Band Internet of ThingsDocument20 pagesNarrow Band Internet of ThingsPhông NguyênNo ratings yet
- Matter: 1.why Is It Necessary?Document15 pagesMatter: 1.why Is It Necessary?Nghiep Nguyen100% (1)
- Unit - 3 Iot Architecture - CDocument25 pagesUnit - 3 Iot Architecture - CLenin. S.B50% (2)
- Wp493 Iiot Edge PlatformsDocument10 pagesWp493 Iiot Edge PlatformshiperboreoatlantecNo ratings yet
- Technology ArchitectureDocument5 pagesTechnology Architecturearun kNo ratings yet
- Narrowband IoT: A Survey On Downlink and Uplink PerspectivesDocument9 pagesNarrowband IoT: A Survey On Downlink and Uplink PerspectivesNivi PsNo ratings yet
- 3.system Specification and DesignDocument11 pages3.system Specification and DesignJovanni Ivan JabatNo ratings yet
- Emertxe Certified Iot Programmer (Ecip) : Course SyllabusDocument7 pagesEmertxe Certified Iot Programmer (Ecip) : Course SyllabusBl KrishnaNo ratings yet
- IOT Unit 2 PDFDocument27 pagesIOT Unit 2 PDFUjjwal AgarwalNo ratings yet
- Pdf&rendition 1 3Document44 pagesPdf&rendition 1 3akshathamc5No ratings yet
- IoT - Module 3 - 8th SemDocument20 pagesIoT - Module 3 - 8th Sem1mv20is036No ratings yet
- Figure 1:internet of Things (IOT) Basic ArchitectureDocument7 pagesFigure 1:internet of Things (IOT) Basic Architecturekavita thakranNo ratings yet
- Application of Object Oriented Programming Paradigm in Embedded Systems DevelopmentDocument5 pagesApplication of Object Oriented Programming Paradigm in Embedded Systems DevelopmentInternational Journal of Innovative Science and Research TechnologyNo ratings yet
- IP Network DesignDocument11 pagesIP Network DesignJose Fabian MaldonadoNo ratings yet
- Iot Iat1 QP 1 C SolutionDocument5 pagesIot Iat1 QP 1 C SolutionSOURAV CHATTERJEENo ratings yet
- Basics of Iot Networking Common Iot Terms: Iot Architecture and Protocols Unit IiDocument13 pagesBasics of Iot Networking Common Iot Terms: Iot Architecture and Protocols Unit IiMaitrayee SuleNo ratings yet
- Rust for Network Programming and Automation, Second Edition: Work around designing networks, TCP/IP protocol, packet analysis and performance monitoring using Rust 1.68From EverandRust for Network Programming and Automation, Second Edition: Work around designing networks, TCP/IP protocol, packet analysis and performance monitoring using Rust 1.68No ratings yet
- Fuzzy Logic Research PaperDocument15 pagesFuzzy Logic Research PaperBhartish AchutaraoNo ratings yet
- CP-UNR-4K4324-I: 32 Ch. 4K Network Video RecorderDocument5 pagesCP-UNR-4K4324-I: 32 Ch. 4K Network Video RecorderRAJENDRAN PLNo ratings yet
- Mohd Dzulfikry Bin Mohd ArisDocument77 pagesMohd Dzulfikry Bin Mohd ArisNhu TranNo ratings yet
- Today We Will Cover: For Loop Nested LoopDocument23 pagesToday We Will Cover: For Loop Nested Loopali hassanNo ratings yet
- Smart Form in DetailDocument3 pagesSmart Form in DetailJammer FerreiraNo ratings yet
- An Introduction To O-RAN: White PaperDocument8 pagesAn Introduction To O-RAN: White Papermxyzptlk0072001No ratings yet
- Information System BookDocument48 pagesInformation System BookRidvan PaşaNo ratings yet
- Using Technology To Address Barriers To Learning: Technical Assistance SamplerDocument66 pagesUsing Technology To Address Barriers To Learning: Technical Assistance SamplerKAINo ratings yet
- 2.6.2 - CO PO ATTAINMENT ManualDocument60 pages2.6.2 - CO PO ATTAINMENT ManualI.T.S Engg100% (2)
- Homework 1 Wireless NetworksDocument2 pagesHomework 1 Wireless NetworkssjognipaNo ratings yet
- Home Studio SeriesDocument8 pagesHome Studio Seriesandrew_ai3100% (3)
- Electronic Science 1Document41 pagesElectronic Science 1Vinit KhaiwalNo ratings yet
- 571188Document28 pages571188eka prasetiaNo ratings yet
- HSBC Case StudyDocument3 pagesHSBC Case StudythunderNo ratings yet
- Core Mathematics C2: GCE Examinations Advanced SubsidiaryDocument4 pagesCore Mathematics C2: GCE Examinations Advanced Subsidiarynishit0157623637No ratings yet
- Curriculum Vitae (Dr. Rupen Chatterjee)Document7 pagesCurriculum Vitae (Dr. Rupen Chatterjee)avirup deNo ratings yet
- Adient Global Supplier Standards Manual - Main (GSS)Document13 pagesAdient Global Supplier Standards Manual - Main (GSS)Claudia PEÑANo ratings yet
- 8051 Microcontroller FeaturesDocument42 pages8051 Microcontroller FeaturesTech_MX67% (3)
- SPSS 15 ManualDocument779 pagesSPSS 15 ManualAyari PMNo ratings yet
- MCA (Revised) / BCA (Revised) Term-End Examination June, 2016Document4 pagesMCA (Revised) / BCA (Revised) Term-End Examination June, 2016Prerak Kumar SharmaNo ratings yet
- CSF 5 INP 18 PH Cybercrime Prevention ActDocument22 pagesCSF 5 INP 18 PH Cybercrime Prevention ActEstela BenegildoNo ratings yet
- Short-Term Load Forecasting Method Based On ARIMA and LSTMDocument5 pagesShort-Term Load Forecasting Method Based On ARIMA and LSTMandrew manuelNo ratings yet
- Powerschool Parent Portal Use Agreement 2010Document1 pagePowerschool Parent Portal Use Agreement 2010api-199941113No ratings yet
- Sagnik Chakraborty: Professional ExperienceDocument1 pageSagnik Chakraborty: Professional ExperiencePranit KumarNo ratings yet
- Acronis Backup & Recovery 11.5: Quick Start GuideDocument12 pagesAcronis Backup & Recovery 11.5: Quick Start GuideDhirender DagarNo ratings yet
- LETTERBACTIVITYPACKFREEBEEDocument68 pagesLETTERBACTIVITYPACKFREEBEEsheenaNo ratings yet
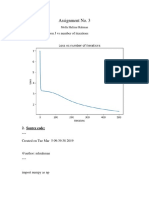
- Assignment No. 3: 1. Plot of Loss Function J Vs Number of IterationsDocument6 pagesAssignment No. 3: 1. Plot of Loss Function J Vs Number of Iterationssun_917443954No ratings yet
- ProductsDocument685 pagesProductsPrince Bin ArafatNo ratings yet
IOT Micro by Sid
IOT Micro by Sid
Uploaded by
elonid7860 ratings0% found this document useful (0 votes)
1 views3 pagesCopyright
© © All Rights Reserved
Available Formats
PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
Download as pdf or txt
0 ratings0% found this document useful (0 votes)
1 views3 pagesIOT Micro by Sid
IOT Micro by Sid
Uploaded by
elonid786Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
Download as pdf or txt
You are on page 1of 3
### Object-Oriented Programming (OOP) in Python: Write some stages of app development.
Narrowband Internet of Things (NB-IoT) is a low-power wide-
**OOP** is a programming paradigm that organizes area network (LPWAN) technology developed to connect a
software design around objects and classes. Here's a brief large number of devices with low data rates and low power
explanation of key OOP concepts: consumption. It is part of the LTE family and was standardized
by 3GPP (Third Generation Partnership Project) in Release 13.
1. **Classes**: ### Key Characteristics of NB-IoT
- Classes are blueprints for creating objects. They define
attributes (data) and methods (functions) that operate on 1. **Low Power Consumption**:
those attributes. - Designed to enable devices to operate for years on a single
- Example: A `Car` class may have attributes like `color` battery charge, making it ideal for applications where long
and `speed`, and methods like `accelerate()` and `brake()`. battery life is essential.
Developing, implementing, and deploying an IoT app involves several 2. **Objects**:
stages, including planning, development, testing, deployment, and - Objects are instances of classes. They represent 2. **Wide Coverage**:
maintenance. Here’s a detailed guide on how to go through these individual entities with unique characteristics. - Provides enhanced indoor and outdoor coverage compared
stages: - Example: An object `my_car` created from the `Car` class to traditional cellular networks, reaching deep inside buildings
would have its own color and speed attributes. and remote rural areas.
### 1. Planning
3. **Encapsulation**: 3. **Low Data Rates**:
**Define Objectives**: Clearly define what you want to achieve with - Encapsulation is the bundling of data and methods that - Supports low-bandwidth data transmissions, typically up to
your IoT app. Identify the problems you aim to solve and the value it operate on that data within a single unit (i.e., class). 250 kbps, which is sufficient for many IoT applications that do
will bring to users. - It promotes information hiding and protects the internal not require high-speed connectivity.
**Market Research**: Conduct market research to understand the state of an object from external interference. 4. **Massive Connectivity**:
needs of your target audience, competitors, and potential market 4. **Inheritance**: - Capable of supporting a large number of devices per cell,
opportunities. - Inheritance allows a class (subclass) to inherit attributes making it suitable for applications that involve connecting
and methods from another class (superclass). thousands of devices within a small area.
**Requirements Gathering**: Collect detailed requirements including - It promotes code reusability and enables the creation of
hardware (sensors, devices), software, communication protocols, and specialized classes that extend the functionality of existing 5. **Cost-Effective**:
data storage needs. ones. - Uses a narrow bandwidth (180 kHz) and leverages existing
LTE infrastructure, reducing the cost of deployment and
**Feasibility Study**: Evaluate the technical, economic, and 5. **Polymorphism**: operation.
operational feasibility of your IoT project. - Polymorphism allows objects of different classes to be
treated as objects of a common superclass. 6. **Robust Security**:
**Technology Stack**: Choose the appropriate technology stack for - It enables methods to behave differently based on the - Incorporates the same security features as LTE networks,
your IoT app, including programming languages, frameworks, IoT object they operate on, promoting flexibility and code including strong encryption and authentication mechanisms.
platforms (e.g., AWS IoT, Azure IoT, Google Cloud IoT), and abstraction.
communication protocols (e.g., MQTT, HTTP, CoAP). 7. **Low Latency**:
**Short Note on Python Strings**: - While designed for low data rates, NB-IoT offers relatively
### 2. Development low latency (usually in the range of 1.6 to 10 seconds), suitable
Python strings are sequences of characters enclosed for many IoT use cases.
#### Hardware Setup within single quotes (' '), double quotes (" "), or triple
quotes (""" """ or ''' '''). Here are some key points about 8. **Easy Integration**:
**Select IoT Devices**: Choose appropriate sensors, actuators, and Python strings: - Can be integrated into existing cellular networks, allowing
devices based on your application needs. mobile operators to deploy NB-IoT without significant
1. **Immutable**: additional investment.
**Device Configuration**: Configure the devices and ensure they are - Strings in Python are immutable, meaning they cannot
capable of connecting to the internet and transmitting data. be changed once created. Operations that appear to ### Applications of NB-IoT
#### Software Development modify strings actually create new strings. 1. **Smart Metering**:
2. **Indexing and Slicing**: - Enables real-time monitoring and management of utility
**Backend Development**: - Characters within a string can be accessed using meters (water, gas, electricity), improving efficiency and
- **Server Setup**: Set up your server infrastructure, which could be indexing and slicing. Indexing starts from 0, and negative reducing operational costs.
cloud-based or on-premises. indices count from the end of the string.
- **API Development**: Develop APIs for communication between 2. **Smart Cities**:
devices and the server. 3. **String Methods**: - Supports applications like smart street lighting, waste
- **Database**: Set up a database to store the collected data. - Python provides a variety of built-in methods for management, and environmental monitoring, enhancing urban
Consider using time-series databases like InfluxDB for IoT data. working with strings, including `split()`, `join()`, `upper()`, infrastructure and services.
**Frontend Development**: `lower()`, `strip()`, `replace()`, and more. 3. **Agriculture**:
- **User Interface**: Design and develop the user interface for web or 4. **String Formatting**: - Facilitates precision farming through soil moisture
mobile platforms where users can interact with the IoT app. - Python supports multiple ways of formatting strings, monitoring, weather stations, and livestock tracking, increasing
- **User Experience**: Ensure the UI is intuitive and user-friendly. including the `%` operator, the `str.format()` method, and f- agricultural productivity and sustainability.
**Firmware Development**: strings (formatted string literals). 4. **Healthcare**:
- **Device Code**: Develop and upload firmware to the IoT devices, 5. **Unicode Support**: - Powers remote health monitoring devices, enabling
ensuring they can collect data and send it to the server. - Python strings are Unicode by default, allowing for continuous tracking of patient health metrics and early
- **Communication Protocols**: Implement communication protocols representation of characters from different languages and detection of potential issues.
(e.g., MQTT, CoAP) in the device firmware. scripts. 5. **Industrial IoT**:
### 3. Implementation 6. **Raw Strings**: - Used in asset tracking, predictive maintenance, and remote
- Raw strings are prefixed with `r` or `R` and treat monitoring of industrial equipment, improving operational
**Connectivity**: backslashes (`\`) as literal characters rather than escape efficiency and reducing downtime.
- **Network Configuration**: Configure the network to ensure reliable characters.
connectivity between IoT devices and the backend system. 6. **Logistics and Asset Tracking**:
- **Edge Computing**: Implement edge computing if necessary to Python strings are versatile and widely used in various - Provides real-time tracking of goods and assets, ensuring
process data closer to the source and reduce latency. applications, including text processing, file handling, web better inventory management and reducing losses.
**Data Management**: development, and data manipulation. Their immutability ### Conclusion
- **Data Collection**: Ensure reliable data collection from IoT devices. and rich set of methods make them powerful tools for
- **Data Processing**: Implement data processing mechanisms, working with textual data in Python programs. NB-IoT is a crucial technology for the IoT ecosystem, offering a
including real-time analytics if required. cost-effective, energy-efficient, and scalable solution for
- **Data Storage**: Store data securely in databases and ensure connecting a vast number of devices. Its ability to provide
efficient retrieval. wide coverage, long battery life, and reliable connectivity
makes it ideal for a wide range of applications, from smart
**Security**: cities and agriculture to healthcare and industrial IoT. By
- **Device Security**: Implement security measures such as leveraging existing LTE infrastructure, NB-IoT allows for quick
encryption, authentication, and secure boot on IoT devices. and efficient deployment, driving the growth and adoption of
- **Network Security**: Secure the communication channels between IoT solutions worldwide.
devices and the backend.
- **Data Security**: Ensure data is encrypted both in transit and at
rest.
### 4. Testing
**Unit Testing**: Test individual components of the IoT system,
including device firmware, backend services, and the frontend
interface.
**Integration Testing**: Test the integration between IoT devices,
backend services, and the frontend to ensure they work together
seamlessly.
**Performance Testing**: Evaluate the performance of the IoT app
under different conditions to ensure it can handle expected loads. Explain OOPS statement also writes
**Security Testing**: Conduct security testing to identify and fix short note on Python Strings. What is two dimensional arrays and write
vulnerabilities. three conditional statements.
**User Acceptance . Testing (UAT)**: Get feedback from end users to ### Object-Oriented Programming (OOP) in Python: A two-dimensional array, also known
validate the functionality and usability of the IoT app. as a matrix, is an array with two levels
**OOP** is a programming paradigm that organizes software design
### 5. Deployment around objects and classes. Here's a brief explanation of key OOP of indexing. It consists of rows and
concepts: columns, forming a grid-like structure.
**Staging Environment**: Deploy the IoT app to a staging environment Each element in a two-dimensional
that mirrors the production environment. This helps in identifying any 1. **Classes**: array is identified by its row and
potential issues before the actual deployment. - Classes are blueprints for creating objects. They define attributes column indices.
(data) and methods (functions) that operate on those attributes.
**Production Deployment**: - Example: A `Car` class may have attributes like `color` and `speed`, Here's an example of a 3x3 two-
- **Device Deployment**: Install and configure IoT devices in the real- and methods like `accelerate()` and `brake()`. dimensional array in Python:
world environment.
- **Backend Deployment**: Deploy backend services to production 2. **Objects**:
servers. - Objects are instances of classes. They represent individual entities ```python
- **Frontend Deployment**: Deploy the frontend interface to with unique characteristics. matrix = [
production, ensuring it is accessible to users. - Example: An object `my_car` created from the `Car` class would [1, 2, 3],
have its own color and speed attributes. [4, 5, 6],
**Monitoring**: Implement monitoring tools to track the performance, [7, 8, 9]
connectivity, and health of IoT devices and backend services. 3. **Encapsulation**: ]
- Encapsulation is the bundling of data and methods that operate on ```
### 6. Maintenance that data within a single unit (i.e., class).
- It promotes information hiding and protects the internal state of an In this example, `matrix[0][0]` refers
**Regular Updates**: Regularly update device firmware, backend object from external interference.
services, and the frontend interface to add new features, fix bugs, and to the element at the first row and
enhance security. 4. **Inheritance**: first column, which is `1`, and
- Inheritance allows a class (subclass) to inherit attributes and `matrix[1][2]` refers to the element at
**Continuous Monitoring**: Continuously monitor the system to methods from another class (superclass). the second row and third column,
detect and resolve issues promptly. - It promotes code reusability and enables the creation of which is `6`.
specialized classes that extend the functionality of existing ones.
**Scalability**: Ensure the IoT app can scale to accommodate more Three conditional statements in
devices and users as needed. 5. **Polymorphism**: Python:
- Polymorphism allows objects of different classes to be treated as
**User Support**: Provide support to users for any issues they objects of a common superclass.
encounter with the IoT app. - It enables methods to behave differently based on the object they 1. **if statement**:
operate on, promoting flexibility and code abstraction. - Used to execute a block of code if a
### Conclusion condition is true.
**Short Note on Python Strings**: ```python
Developing, implementing, and deploying an IoT app is a complex x = 10
process that requires careful planning and execution across multiple Python strings are sequences of characters enclosed within single if x > 5:
stages. By following these steps, you can build a robust and scalable quotes (' '), double quotes (" "), or triple quotes (""" """ or ''' '''). Here print("x is greater than 5")
IoT solution that meets your objectives and delivers value to users. are some key points about Python strings: ```
1. **Immutable**:
- Strings in Python are immutable, meaning they cannot be changed 2. **elif statement**:
once created. Operations that appear to modify strings actually - Short for "else if", used to check
create new strings. additional conditions after the initial if
statement.
2. **Indexing and Slicing**: ```python
- Characters within a string can be accessed using indexing and x = 10
slicing. Indexing starts from 0, and negative indices count from the if x > 5:
end of the string. print("x is greater than 5")
3. **String Methods**: elif x < 5:
- Python provides a variety of built-in methods for working with print("x is less than 5")
strings, including `split()`, `join()`, `upper()`, `lower()`, `strip()`, `replace()`, ```
and more.
3. **else statement**:
4. **String Formatting**: - Used to execute a block of code if
- Python supports multiple ways of formatting strings, including the none of the preceding conditions are
`%` operator, the `str.format()` method, and f-strings (formatted string true.
literals). ```python
5. **Unicode Support**: x = 10
- Python strings are Unicode by default, allowing for representation if x > 5:
of characters from different languages and scripts. print("x is greater than 5")
else:
6. **Raw Strings**: print("x is not greater than 5")
- Raw strings are prefixed with `r` or `R` and treat backslashes (`\`) as ```
literal characters rather than escape characters.
Python strings are versatile and widely used in various applications, These conditional statements allow
including text processing, file handling, web development, and data you to control the flow of your Python
manipulation. Their immutability and rich set of methods make them code based on various conditions.
powerful tools for working with textual data in Python programs.
Write some stages of app development.
Machine-to-Machine (M2M) services refer to the direct communication between devices without human intervention. This
technology underpins the Internet of Things (IoT) by enabling devices to exchange information and perform actions
automatically. The evolution of mobile network generations (2G, 3G, 4G, and 5G) has significantly influenced the development Q. Define Sigfox and LoR Wan What are python arrays?
and capabilities of M2M services. ### Sigfox In Python, arrays are sequences of
### 2G (Second Generation) elements that can hold items of
**Sigfox** is a global Low Power Wide Area Network the same data type. Unlike lists,
**Characteristics:** (LPWAN) technology specifically designed for the which can contain elements of
- **Digital Technology**: Transitioned from analog to digital communications, providing better quality and security. Internet of Things (IoT). It offers: different data types, arrays in
- **Data Services**: Introduced basic data services like SMS (Short Message Service) and MMS (Multimedia Messaging Service).
- **Low Data Rates**: Data rates typically up to 64 kbps using technologies like GPRS (General Packet Radio Service) and EDGE
Python are homogeneous. They
(Enhanced Data Rates for GSM Evolution). - **Low Power Consumption**: Enables devices to provide efficient storage and
operate for years on a single battery. manipulation of large sets of
**M2M Applications**: - **Long Range**: Provides coverage up to 10 km in numeric data.
- **Remote Monitoring**: Basic M2M applications such as remote meter reading and simple telemetry. urban areas and 50 km in rural areas.
- **SMS-Based Services**: Use of SMS for sending alerts and notifications in applications like security systems and early M2M
applications.
- **Low Data Rates**: Supports small, infrequent data Python arrays are implemented
transmissions. using the `array` module, and they
### 3G (Third Generation) - **Subscription-Based**: Operates on a subscription offer features like indexing, slicing,
model for network access. and iteration similar to lists.
**Characteristics:** However, arrays are optimized for
- **Higher Data Rates**: Provided significantly higher data rates, typically up to 2 Mbps, with technologies like UMTS (Universal
Mobile Telecommunications System) and HSPA (High Speed Packet Access).
**Applications**: Asset tracking, smart metering, numerical computations and
- **Enhanced Data Services**: Improved mobile internet access, video calls, and more advanced data services. environmental monitoring, and security systems. consume less memory compared
to lists when dealing with large
**M2M Applications**: ### LoRaWAN datasets of numeric values.
- **Telematics**: Enabled more advanced telematics in vehicles, including GPS tracking, navigation, and fleet management.
- **Healthcare**: Remote health monitoring and telemedicine applications became more viable with better data speeds.
- **Industrial Automation**: Enhanced capabilities for remote control and monitoring of industrial equipment and processes.
**LoRaWAN** (Long Range Wide Area Network) is a Here's a brief summary of Python
communication protocol using LoRa technology for IoT arrays:
### 4G (Fourth Generation) networks. It features:
- Arrays are homogeneous
**Characteristics:** - **Long Range**: Covers up to 5 km in urban areas and sequences of elements with the
- **High-Speed Broadband**: Provided broadband internet speeds, typically up to 100 Mbps for mobile and even higher for
stationary users, using technologies like LTE (Long Term Evolution).
15 km in rural areas. same data type.
- **Low Latency**: Reduced latency, improving the responsiveness of applications. - **Low Power Consumption**: Devices can run up to 10 - They provide efficient storage
- **IP-Based Network**: Fully IP-based network architecture, supporting a wide range of applications and services. years on a single battery. and manipulation of numeric data.
- **Scalability**: Supports millions of devices in a single - Arrays are implemented using the
**M2M Applications**: network. `array` module in Python.
- **Smart Cities**: Enabled applications like smart street lighting, waste management, and intelligent transportation systems.
- **Advanced Telematics**: More sophisticated telematics applications in vehicles, including real-time traffic information and
- **Open Standard**: Maintained by the LoRa Alliance, - They support features like
vehicle diagnostics. ensuring interoperability. indexing, slicing, and iteration.
- **IoT Devices**: Proliferation of IoT devices in homes and industries, supporting applications like smart home automation, - Arrays are commonly used in
advanced industrial automation, and connected consumer electronics. **Applications**: Smart agriculture, smart cities, numerical computing and data
industrial IoT, home automation, and environmental processing applications.
### 5G (Fifth Generation) monitoring.
**Characteristics:**
- **Ultra-High Data Rates**: Offers data rates up to 10 Gbps, enabling very high-speed internet access.
- **Ultra-Low Latency**: Latency as low as 1 millisecond, essential for real-time applications.
- **Massive Connectivity**: Supports up to 1 million devices per square kilometer, ideal for massive IoT deployments. Q. Write some characteristics of RFID and explain how RFID is better than
- **Enhanced Reliability**: Provides highly reliable connections for mission-critical applications. barcodes.
**M2M Applications**:
### Characteristics of RFID
- **Autonomous Vehicles**: Supports vehicle-to-everything (V2X) communications, enabling autonomous driving and 1. **Wireless Communication**:
advanced traffic management.
- **Smart Factories**: Real-time control and monitoring of manufacturing processes, predictive maintenance, and robotics. - RFID (Radio Frequency Identification) uses radio waves to transmit data from an
- **Healthcare**: Advanced telemedicine, remote surgery, and continuous health monitoring with real-time data. RFID tag to a reader, enabling wireless communication and identification.
- **Smart Grids**: Enhanced energy management and distribution systems, integrating renewable energy sources and
optimizing consumption. 2. **Tags**:
- **Augmented Reality (AR) and Virtual Reality (VR)**: Supports immersive AR and VR applications in various fields, including - **Passive Tags**: Do not have their own power source and are powered by the
education, entertainment, and training.
reader's electromagnetic field. They have a shorter read range.
### Conclusion - **Active Tags**: Contain a battery and can transmit signals autonomously. They
The evolution from 2G to 5G has significantly enhanced the capabilities and applications of M2M services. Each generation has
have a longer read range.
brought improvements in data rates, latency, and connectivity, enabling more complex and sophisticated M2M applications. 3. **Readers**:
With 5G, the potential for M2M and IoT is vastly expanded, supporting a wide range of advanced use cases across various
industries, driving innovation, and improving efficiency and connectivity. - RFID readers emit radio waves and capture the data transmitted by the RFID
tags. They can be handheld, fixed, or integrated into other devices.
4. **Data Storage**:
What is raspberry pi architecture? - RFID tags can store more data compared to barcodes, with capacities ranging
The architecture of the Raspberry Pi is based on a System on a Chip (SoC) from a few bytes to several kilobytes, enabling detailed information storage.
design, which integrates various components into a single chip. Here's an 5. **Read Range**:
overview of the architecture of Raspberry Pi: - Passive tags can be read from a few centimeters to several meters, while active
### 1. **Broadcom SoC:** tags can be read from tens of meters away.
- The heart of the Raspberry Pi is a Broadcom SoC, which includes: 6. **Durability**:
- **CPU (Central Processing Unit)**: ARM processor (varies depending on - RFID tags are robust and can withstand harsh environmental conditions such as
the model), typically ARM Cortex-A53 or Cortex-A72. extreme temperatures, moisture, and physical stress.
- **GPU (Graphics Processing Unit)**: Broadcom VideoCore GPU,
responsible for graphics rendering and multimedia processing. 7. **Simultaneous Reading**:
- **RAM (Random Access Memory)**: Onboard RAM (varies by model), - RFID systems can read multiple tags at the same time, facilitating faster and
typically ranging from 256MB to 8GB, providing memory for running more efficient data collection.
applications and storing data.
### 2. **Input/Output (I/O) Ports:** 8. **Anti-Collision Mechanisms**:
- The Raspberry Pi includes various I/O ports for connectivity and - RFID systems incorporate anti-collision protocols to ensure that multiple tags
expansion, including: can be read simultaneously without interference.
- **USB Ports**: For connecting peripherals such as keyboards, mice, and ### Advantages of RFID Over Barcodes
external storage devices.
- **HDMI Port**: For connecting displays or TVs for video output. 1. **Line of Sight**:
- **Ethernet Port**: For wired network connectivity. - **RFID**: Does not require a direct line of sight to read tags, allowing tags to be
- **GPIO (General Purpose Input/Output)** Pins: For interfacing with read even when they are hidden or embedded within objects.
external devices and sensors, allowing for hardware projects and - **Barcodes**: Require a direct line of sight for the scanner to read the barcode,
experimentation. which can be cumbersome in certain situations.
- **Camera and Display Ports**: For connecting camera modules and
displays for video input and output. 2. **Read Range**:
- **Audio Jack**: For connecting speakers or headphones for audio - **RFID**: Can read tags from a greater distance, ranging from a few centimeters
output. for passive tags to several meters for active tags.
### 3. **Storage:** - **Barcodes**: Have a very short read range, typically a few centimeters.
- The Raspberry Pi typically uses a microSD card for primary storage, 3. **Data Capacity**:
where the operating system and user data are stored. Some models may - **RFID**: Tags can store significantly more data, including detailed information
also support booting from USB storage devices. about the tagged item, which can be updated as needed.
### 4. **Power Management:** - **Barcodes**: Can only store a limited amount of data, usually just an identifier
- Power is supplied to the Raspberry Pi via a micro USB or USB-C power or a series of numbers.
connector, depending on the model. The power management circuitry 4. **Durability and Longevity**:
regulates and distributes power to the various components on the board. - **RFID**: Tags are more durable and can withstand adverse environmental
### 5. **Operating System:** conditions such as moisture, heat, and physical damage.
- The Raspberry Pi supports various operating systems, including Raspbian - **Barcodes**: Can be easily damaged by dirt, moisture, or wear, making them
(based on Debian Linux), Ubuntu, and Windows 10 IoT Core. These operating unreadable.
systems run on the ARM architecture and are optimized for the Raspberry Pi 5. **Simultaneous Reading**:
hardware. - **RFID**: Can read multiple tags simultaneously, which is highly beneficial for
### 6. **Peripherals and Accessories:** inventory management and rapid data collection.
- The Raspberry Pi can be expanded and customized with various - **Barcodes**: Must be scanned one at a time, which can be time-consuming and
peripherals and accessories, including: inefficient in large-scale operations.
- **Wireless Connectivity**: Wi-Fi and Bluetooth modules for wireless 6. **Security**:
networking and communication. - **RFID**: Tags can be encrypted and have read/write capabilities, enhancing
- **HATs (Hardware Attached on Top)**: Expansion boards that stack on data security and allowing dynamic data updates.
top of the Raspberry Pi to add additional features or functionality. - **Barcodes**: Lack security features and are more susceptible to replication and
- **Sensors and Modules**: Various sensors, actuators, and modules can tampering.
be connected to the GPIO pins for building IoT projects, robotics, and more.
### Conclusion: 7. **Automation**:
The architecture of the Raspberry Pi is designed to provide a flexible and - **RFID**: Supports automation in processes such as inventory tracking, asset
affordable platform for learning, prototyping, and building a wide range of management, and access control, providing real-time data and reducing manual
projects, from simple hobbyist creations to more complex industrial effort.
applications. Its modular design, extensive connectivity options, and broad - **Barcodes**: While useful, require manual scanning, limiting the extent of
community support make it a popular choice for enthusiasts, educators, and automation possible.
professionals alike. ### Conclusion
RFID technology offers significant advantages over traditional barcodes,
particularly in terms of range, data capacity, durability, and simultaneous reading
Distinguished between Built in function and user capabilities. These features make RFID ideal for applications requiring efficient,
defined function. automated, and secure data collection in various industries such as logistics, retail,
Here's a brief distinction between built-in functions healthcare, and manufacturing. While barcodes remain useful for simple and cost-
and user-defined functions: effective identification tasks, RFID provides greater flexibility and efficiency,
especially in complex and large-scale operations.
1. **Built-in Functions**:
- Predefined functions provided by the programming
language or its standard libraries.
- Included in the language's core functionality and
readily available for use without the need for distinction between SaaS, PaaS, and IaaS:
additional coding.
- Examples: `print()`, `len()`, `sum()`, `range()` in 1. **SaaS (Software as a Service)**:
Python. - Provides software applications over the internet on a
subscription basis. Define cloud and its types.
2. **User-Defined Functions**: - Users access the software via a web browser or API
- Functions created by users to perform specific without needing to install or maintain it locally. **Cloud Computing** refers to the delivery of computing services
tasks or operations within their programs. - Examples: Google Workspace, Microsoft Office 365, over the internet, providing access to a shared pool of resources
- Defined by the user using the `def` keyword Salesforce. such as servers, storage, databases, networking, software, and
followed by a function name, parameters, and a block analytics. Users can leverage these services on-demand, without the
of code. 2. **PaaS (Platform as a Service)**: need for extensive infrastructure investments or management.
- Can be customized to suit specific requirements - Offers a platform allowing developers to build,
and reusable across the program. deploy, and manage applications without dealing with ### Types of Cloud Computing:
- Examples: Functions created by the programmer to infrastructure complexities.
perform custom calculations, data processing, or any - Provides tools and services for application 1. **Public Cloud**:
other desired functionality within their code. development, testing, and deployment. - Public cloud services are provided by third-party cloud service
- Examples: Heroku, AWS Elastic Beanstalk, Microsoft providers over the internet.
In essence, built-in functions are provided by the Azure App Service. - Resources are shared among multiple users and organizations.
programming language, while user-defined functions - Examples: Amazon Web Services (AWS), Microsoft Azure, Google
are created by users to extend the language's 3. **IaaS (Infrastructure as a Service)**: Cloud Platform (GCP).
capabilities and perform custom tasks tailored to their - Delivers virtualized computing resources over the
needs. internet, including servers, storage, and networking. 2. **Private Cloud**:
- Users have control over the infrastructure and can - Private cloud services are dedicated to a single organization and
manage it remotely. may be hosted on-premises or by a third-party provider.
- Examples: AWS EC2, Google Compute Engine, - Offers greater control, security, and customization compared to
Microsoft Azure Virtual Machines. public cloud.
- Examples: VMware Cloud Foundation, OpenStack, Microsoft Azure
In essence, SaaS delivers software applications, PaaS Stack.
provides a platform for application development, and
IaaS offers virtualized infrastructure resources. Each 3. **Hybrid Cloud**:
service model offers different levels of abstraction and - Hybrid cloud combines public and private cloud environments,
flexibility, catering to various needs and use cases. allowing data and applications to be shared between them.
- Offers flexibility, scalability, and cost-efficiency by leveraging
both on-premises and cloud resources.
- Examples: AWS Outposts, Azure Hybrid Cloud, Google Anthos.
4. **Multi-Cloud**:
- Multi-cloud involves using services from multiple cloud providers
to meet different business needs.
- Helps avoid vendor lock-in, increases redundancy, and enables
optimization of costs and performance.
- Examples: Using AWS for compute, Azure for AI services, and
Google Cloud for big data analytics.
Each type of cloud computing offers distinct advantages and use
cases, allowing organizations to choose the deployment model that
best suits their requirements, budget, and security considerations.
Wite some stages of app development Explain variables in python and define escape character sequence also.
App development is a structured process that involves multiple stages to ensure the final ### Variables in Python:
product is functional,
user-friendly, and meets the intended objectives. Here are the main stages of app In Python, a variable is a named reference to a value stored in memory. Variables are
development: used to store data that can be manipulated and accessed throughout the program.
Here are some key points about variables in Python:
### 1. **Idea and Conceptualization**
1. **Variable Naming**:
- **Brainstorming**: Generate and evaluate ideas for the app. - Variable names can contain letters, numbers, and underscores, but must start with
- **Market Research**: Analyze the market to understand the demand, competition, and a letter or underscore.
target audience. - They are case-sensitive (`my_variable` is different from `My_Variable`).
- **Feasibility Study**: Assess the technical, economic, and operational feasibility of the - It's good practice to use descriptive names that convey the purpose of the variable.
app idea.
2. **Variable Assignment**:
### 2. **Requirements Analysis and Planning** - Variables are assigned values using the assignment operator (`=`).
- Python is dynamically typed, so variables do not need to be explicitly declared with
- **Requirements Gathering**: Collect detailed requirements from stakeholders, a data type.
including features, functionalities, and user expectations.
- **Project Planning**: Define the project scope, create a timeline, allocate resources, and 3. **Variable Types**:
set milestones. - Variables in Python can hold various types of data, including integers, floats, strings,
- **Technical Specification**: Determine the technology stack, platforms (iOS, Android, lists, tuples, dictionaries, and custom objects.
web), and tools to be used.
4. **Variable Scope**:
### 3. **UI/UX Design** - The scope of a variable determines where it can be accessed within the program.
- Variables can have global scope (accessible throughout the program) or local scope
- **Wireframing**: Create basic sketches of the app layout to visualize the user flow. (accessible only within a specific function or block of code).
- **Prototyping**: Develop interactive prototypes to test and refine the app’s user
interface and experience. 5. **Variable Reassignment**:
- **Design**: Create high-fidelity designs, including graphics, icons, and animations, - Variables can be reassigned to different values throughout the program.
ensuring consistency with branding guidelines.
Here's an example of variable usage in Python:
### 4. **Development**
```python
- **Front-end Development**: Build the user interface, ensuring responsiveness and # Variable assignment
interactivity. x = 10
- **Back-end Development**: Develop the server-side logic, database structure, and APIs
for data exchange. # Variable reassignment
- **Integration**: Integrate third-party services, SDKs, and APIs as required. x=x+5
### 5. **Testing** # Printing variable value
print(x) # Output: 15
- **Unit Testing**: Test individual components for functionality and performance. ```
- **Integration Testing**: Ensure that different components of the app work together
seamlessly. ### Escape Character Sequence:
- **System Testing**: Conduct end-to-end testing of the entire app.
- **User Acceptance Testing (UAT)**: Get feedback from real users to validate the app’s Escape character sequences in Python are special sequences of characters used to
functionality and usability. represent characters that cannot be easily typed or printed directly. They begin with a
- **Performance Testing**: Assess the app’s speed, scalability, and stability under load. backslash (`\`) followed by a character or sequence of characters. Some commonly
- **Security Testing**: Identify and fix vulnerabilities to protect against threats. used escape character sequences in Python include:
### 6. **Deployment** - `\n`: Newline character (moves the cursor to the beginning of the next line).
- `\t`: Tab character (inserts a horizontal tab).
- **Preparation**: Prepare the app for release, including finalizing app store listings, - `\\`: Backslash character.
creating promotional materials, - `\'`: Single quote character.
and ensuring compliance with platform guidelines. - `\"`: Double quote character.
- **Submission**: Submit the app to app stores (Google Play, Apple App Store) for review
and approval. Here's an example demonstrating the usage of escape character sequences:
- **Launch**: Once approved, launch the app to the public and begin monitoring its
performance. ```python
print("Hello\nWorld!") # Output: Hello
### 7. **Maintenance and Updates** # World!
- **Monitoring**: Continuously monitor the app for bugs, crashes, and performance issues print("Python\tProgramming") # Output: Python Programming
using analytics and user feedback.
- **Bug Fixes**: Address any issues that arise post-launch to maintain app stability and print("This is a backslash: \\") # Output: This is a backslash: \
performance. ```
- **Updates**: Regularly update the app with new features, improvements, and security
patches to keep users engaged and Escape character sequences are useful for formatting output, including special
ensure compatibility with new OS versions. characters, and improving the readability of strings in Python.
### 8. **Marketing and User Acquisition**
- **Marketing Strategy**: Develop and execute marketing campaigns to promote the app
and attract users.
- **User Acquisition**: Use various channels like social media, paid advertising, and
content marketing to acquire new users.
- **User Engagement**: Implement strategies to retain users, such as push notifications,
in-app messages, and loyalty programs.
### 9. **Feedback and Improvement**
- **User Feedback**: Collect feedback from users through reviews, surveys, and direct
interactions.
- **Data Analysis**: Analyze user behavior and usage data to identify areas for
improvement.
- **Continuous Improvement**: Use the insights gained to enhance the app, adding new
features and refining existing ones.
### Conclusion Testing and integration are both crucial aspects of the software
development lifecycle, but they focus on different goals and
processes. Here’s a detailed comparison between the two:
App development is an iterative process that requires careful planning, execution, and
continuous improvement. ### Testing
By following these stages, **Definition**: Testing is the process of evaluating a software
developers can create high-quality apps that meet user needs and achieve business goals. application to ensure it meets the specified requirements and is
free of defects. It involves executing the software to identify any
bugs, errors, or missing functionalities.
#### Types of Testing:
1. **Unit Testing**:
- **Focus**: Individual components or functions.
- **Goal**: Ensure that each component works correctly in
isolation.
- **Tools**: JUnit, NUnit, pytest.
2. **Functional Testing**:
- **Focus**: Specific functionalities of the software.
- **Goal**: Verify that the software performs its intended
functions.
- **Tools**: Selenium, QTP.
3. **Regression Testing**:
- **Focus**: Previously tested functionalities.
- **Goal**: Ensure that new changes have not adversely affected
existing functionalities.
- **Tools**: TestComplete, Ranorex.
4. **Performance Testing**:
- **Focus**: Speed, responsiveness, and stability under load.
- **Goal**: Ensure the software performs well under expected
workload.
- **Tools**: JMeter, LoadRunner.
5. **Security Testing**:
- **Focus**: Software security.
- **Goal**: Identify vulnerabilities and ensure the software is
secure against attacks.
- **Tools**: OWASP ZAP, Burp Suite.
6. **User Acceptance Testing (UAT)**:
- **Focus**: End-to-end system functionality.
- **Goal**: Ensure the software meets business requirements and
is ready for deployment.
- **Tools**: Manual testing, custom scripts.
#### Key Characteristics:
- **Scope**: Specific features or components.
- **Granularity**: Can be very detailed and fine-grained (e.g., unit
tests).
- **Timing**: Typically performed throughout the development
process, especially before releases.
- **Responsibility**: Generally handled by QA testers and
developers.
### Integration
**Definition**: Integration is the process of combining individual
software components or subsystems into a single, unified system.
It ensures that different modules work together as intended.
#### Types of Integration:
1. **Continuous Integration (CI)**:
- **Focus**: Frequent integration of code changes.
- **Goal**: Detect integration issues early by frequently
integrating code and running automated tests.
- **Tools**: Jenkins, Travis CI, CircleCI.
2. **System Integration**:
Write note on break statement continue statement and pass - **Focus**: Integration of different systems or subsystems.
statement - **Goal**: Ensure that disparate systems interact correctly.
Certainly! Here's a short note on each of the statements: - **Tools**: Middleware, APIs, custom scripts.
1. **Break Statement**: 3. **Interface Integration**:
- **Focus**: Connecting different software interfaces.
- The `break` statement is used to exit a loop prematurely. - **Goal**: Ensure seamless communication between different
- When encountered within a loop (e.g., for loop, while loop), software applications.
it immediately terminates the loop's execution and transfers - **Tools**: RESTful APIs, SOAP, GraphQL.
control to the statement immediately following the loop. 4. **Data Integration**:
- Useful for stopping the execution of a loop based on a - **Focus**: Combining data from different sources.
certain condition without waiting for the loop to complete all - **Goal**: Ensure data consistency and accuracy across systems.
iterations. - **Tools**: ETL tools like Talend, Informatica, Apache Nifi.
2. **Continue Statement**: #### Key Characteristics:
- The `continue` statement is used to skip the remaining code - **Scope**: Entire systems or subsystems.
- **Granularity**: Higher level, focusing on how components
inside a loop for the current iteration and proceed to the next interact with each other.
iteration. - **Timing**: Performed after individual components are developed
- When encountered within a loop, it skips the execution of and tested.
the remaining code in the loop's body and jumps to the next - **Responsibility**: Generally handled by developers, system
iteration. integrators, and sometimes dedicated integration teams.
- Useful for skipping certain iterations of a loop based on a ### Comparison Summary
specific condition without exiting the loop entirely.
| Aspect | Testing | Integration
3. **Pass Statement**: |
- The `pass` statement is a null operation in Python. |------------------------|--------------------------------------------------|---------
-----------------------------------------|
- It serves as a placeholder for syntactically required | **Focus** | Verifying functionality, identifying bugs |
statements that do nothing. Combining components into a unified system |
- When encountered, it does nothing and allows the program | **Scope** | Individual features, functions, or components
to continue execution without raising any errors. | Entire systems, subsystems, or interfaces |
- Useful as a placeholder when writing code structure that | **Granularity** | Detailed and fine-grained | Higher
level, focusing on interaction |
requires no action at the moment but may be filled in later. | **Timing** | Throughout the development process |
After components are developed and unit tested |
In summary, `break` is used to exit a loop prematurely, | **Responsibility** | QA testers, developers |
`continue` is used to skip the current iteration of a loop, and Developers, system integrators, integration teams |
`pass` is used as a placeholder for empty code blocks. Each | **Tools** | JUnit, Selenium, JMeter, etc. | Jenkins,
middleware, APIs, ETL tools |
statement serves a specific purpose in controlling the flow of | **Goal** | Ensure software works correctly |
execution within loops in Python. Ensure different parts of the system work together|
You might also like
- MaxbountyapiDocument15 pagesMaxbountyapiUzzik JahatNo ratings yet
- Sketch The Architecture of Iot Toolkit and Explain Each Entity in BriefDocument9 pagesSketch The Architecture of Iot Toolkit and Explain Each Entity in BriefprabhaNo ratings yet
- Group Reporting Rubrics PDFDocument1 pageGroup Reporting Rubrics PDFhaniebalmNo ratings yet
- Choosing The Right Rtos For Iot Platform: March 2015Document7 pagesChoosing The Right Rtos For Iot Platform: March 2015okokoNo ratings yet
- Module 2 - Internet of Things - FinalDocument22 pagesModule 2 - Internet of Things - Finalelsa galgaoNo ratings yet
- Tinywow Iot Lab Manual 6768824Document33 pagesTinywow Iot Lab Manual 6768824Girish BabuNo ratings yet
- Iot and Applications SUBJECT CODE: 2180709: Laboratory ManualDocument38 pagesIot and Applications SUBJECT CODE: 2180709: Laboratory ManualSiva RamanNo ratings yet
- Tinywow Iot Lab Manual 6768835Document33 pagesTinywow Iot Lab Manual 6768835Girish BabuNo ratings yet
- Engineering An Iot-Edge-Cloud Computing System Architecture: Lessons Learnt From An Undergraduate Lab CourseDocument14 pagesEngineering An Iot-Edge-Cloud Computing System Architecture: Lessons Learnt From An Undergraduate Lab CourseAdama SOWNo ratings yet
- An Application Based Comparative Study of Lpwan Technologies For Iot EnvironmentDocument4 pagesAn Application Based Comparative Study of Lpwan Technologies For Iot EnvironmentTajbia HossainNo ratings yet
- Iot Uni-1Document53 pagesIot Uni-1sameer khanNo ratings yet
- Implementing Nb-Iot in Software - Experiences Using The Srslte LibraryDocument5 pagesImplementing Nb-Iot in Software - Experiences Using The Srslte LibraryKabamba Franck MUTEBANo ratings yet
- Demo - OpenAirInterface An Open LTE Network in A PCDocument3 pagesDemo - OpenAirInterface An Open LTE Network in A PCAmir EsparhamNo ratings yet
- Internet of Things - Architecture and Protocols - Unit 1Document56 pagesInternet of Things - Architecture and Protocols - Unit 1PrudhviNo ratings yet
- Ravel Riliskis Iotapp15Document6 pagesRavel Riliskis Iotapp15yousefNo ratings yet
- Intent Harmonization FWK ChangesDocument23 pagesIntent Harmonization FWK Changesquan voNo ratings yet
- A Comparative Study of AODV, DSR, and DYMO Routing Protocols Using OMNeT++Document5 pagesA Comparative Study of AODV, DSR, and DYMO Routing Protocols Using OMNeT++hhakim32No ratings yet
- Iot Ut - 2Document20 pagesIot Ut - 2Name SurnameNo ratings yet
- Abhinav RastogiDocument4 pagesAbhinav RastogiabhihackzNo ratings yet
- IoT Chapter 5Document36 pagesIoT Chapter 5piyalmajumderNo ratings yet
- Iot Architecture, Onem2M Model, Reference Model: L-T-P - (C) 4-0-0Document25 pagesIot Architecture, Onem2M Model, Reference Model: L-T-P - (C) 4-0-0deva dattaNo ratings yet
- Experiment 9Document29 pagesExperiment 9Aman SharmaNo ratings yet
- Chapter 4Document6 pagesChapter 4sarthak kothariNo ratings yet
- 2010 Aims 6lowpanDocument6 pages2010 Aims 6lowpanJeya Shree Arunjunai RajNo ratings yet
- Internet of Things - Architecture and Protocols - Unit 3Document51 pagesInternet of Things - Architecture and Protocols - Unit 3PrudhviNo ratings yet
- IoT Chapter 5Document36 pagesIoT Chapter 5piyalmajumderNo ratings yet
- Unit 2 NotesDocument99 pagesUnit 2 NotesKaushalNo ratings yet
- Abhishek Kumar Iot Assgn1 and Asgn 2Document36 pagesAbhishek Kumar Iot Assgn1 and Asgn 2Abhishek KumarNo ratings yet
- Unit 2Document99 pagesUnit 2nagamalleswari2010No ratings yet
- Stmicro Mcu Pfe 2012xDocument15 pagesStmicro Mcu Pfe 2012xkbma2009No ratings yet
- Network Analyzer and Report Generation Tool For NS-2 Using TCL ScriptDocument6 pagesNetwork Analyzer and Report Generation Tool For NS-2 Using TCL Scriptأبو أيوب تافيلالتNo ratings yet
- 3-Modul - PTI412 - IoT-1-2020Document16 pages3-Modul - PTI412 - IoT-1-202020200801015 Joko SulistyoNo ratings yet
- Midterm Exam Review Questions 1 - NewDocument21 pagesMidterm Exam Review Questions 1 - NewSirus DanhNo ratings yet
- Lecture 4Document21 pagesLecture 4najmi ariffinNo ratings yet
- IoT Protocols Antion JaimeDocument65 pagesIoT Protocols Antion JaimeandyNo ratings yet
- Shen Open5g Wico July2017Document28 pagesShen Open5g Wico July2017prashant817No ratings yet
- AML2018 Rentschler Fieldbus Topologies PaperDocument11 pagesAML2018 Rentschler Fieldbus Topologies Paperrodrigo.rpg.scNo ratings yet
- 4 - Designing Embedded Networking ApplicationsDocument23 pages4 - Designing Embedded Networking ApplicationsBrian roshNo ratings yet
- DEVASC Module 8Document134 pagesDEVASC Module 8JUAN MAURICIO QUEZADA JAMASMIENo ratings yet
- Module 1 LTE INTRO NB-IOTDocument30 pagesModule 1 LTE INTRO NB-IOTahad siddiquiNo ratings yet
- Only Provide The Important Points Which Can Come...Document55 pagesOnly Provide The Important Points Which Can Come...darthrishav2No ratings yet
- U-5 HalfDocument218 pagesU-5 HalfK.P.Revathi Asst prof - IT DeptNo ratings yet
- Internal 2 - Answer - 16 MarksDocument3 pagesInternal 2 - Answer - 16 MarksVelmurugan T - ECENo ratings yet
- Pankaj ResumeDocument3 pagesPankaj ResumeHemlata GuptaNo ratings yet
- Narrow Band Internet of ThingsDocument20 pagesNarrow Band Internet of ThingsPhông NguyênNo ratings yet
- Matter: 1.why Is It Necessary?Document15 pagesMatter: 1.why Is It Necessary?Nghiep Nguyen100% (1)
- Unit - 3 Iot Architecture - CDocument25 pagesUnit - 3 Iot Architecture - CLenin. S.B50% (2)
- Wp493 Iiot Edge PlatformsDocument10 pagesWp493 Iiot Edge PlatformshiperboreoatlantecNo ratings yet
- Technology ArchitectureDocument5 pagesTechnology Architecturearun kNo ratings yet
- Narrowband IoT: A Survey On Downlink and Uplink PerspectivesDocument9 pagesNarrowband IoT: A Survey On Downlink and Uplink PerspectivesNivi PsNo ratings yet
- 3.system Specification and DesignDocument11 pages3.system Specification and DesignJovanni Ivan JabatNo ratings yet
- Emertxe Certified Iot Programmer (Ecip) : Course SyllabusDocument7 pagesEmertxe Certified Iot Programmer (Ecip) : Course SyllabusBl KrishnaNo ratings yet
- IOT Unit 2 PDFDocument27 pagesIOT Unit 2 PDFUjjwal AgarwalNo ratings yet
- Pdf&rendition 1 3Document44 pagesPdf&rendition 1 3akshathamc5No ratings yet
- IoT - Module 3 - 8th SemDocument20 pagesIoT - Module 3 - 8th Sem1mv20is036No ratings yet
- Figure 1:internet of Things (IOT) Basic ArchitectureDocument7 pagesFigure 1:internet of Things (IOT) Basic Architecturekavita thakranNo ratings yet
- Application of Object Oriented Programming Paradigm in Embedded Systems DevelopmentDocument5 pagesApplication of Object Oriented Programming Paradigm in Embedded Systems DevelopmentInternational Journal of Innovative Science and Research TechnologyNo ratings yet
- IP Network DesignDocument11 pagesIP Network DesignJose Fabian MaldonadoNo ratings yet
- Iot Iat1 QP 1 C SolutionDocument5 pagesIot Iat1 QP 1 C SolutionSOURAV CHATTERJEENo ratings yet
- Basics of Iot Networking Common Iot Terms: Iot Architecture and Protocols Unit IiDocument13 pagesBasics of Iot Networking Common Iot Terms: Iot Architecture and Protocols Unit IiMaitrayee SuleNo ratings yet
- Rust for Network Programming and Automation, Second Edition: Work around designing networks, TCP/IP protocol, packet analysis and performance monitoring using Rust 1.68From EverandRust for Network Programming and Automation, Second Edition: Work around designing networks, TCP/IP protocol, packet analysis and performance monitoring using Rust 1.68No ratings yet
- Fuzzy Logic Research PaperDocument15 pagesFuzzy Logic Research PaperBhartish AchutaraoNo ratings yet
- CP-UNR-4K4324-I: 32 Ch. 4K Network Video RecorderDocument5 pagesCP-UNR-4K4324-I: 32 Ch. 4K Network Video RecorderRAJENDRAN PLNo ratings yet
- Mohd Dzulfikry Bin Mohd ArisDocument77 pagesMohd Dzulfikry Bin Mohd ArisNhu TranNo ratings yet
- Today We Will Cover: For Loop Nested LoopDocument23 pagesToday We Will Cover: For Loop Nested Loopali hassanNo ratings yet
- Smart Form in DetailDocument3 pagesSmart Form in DetailJammer FerreiraNo ratings yet
- An Introduction To O-RAN: White PaperDocument8 pagesAn Introduction To O-RAN: White Papermxyzptlk0072001No ratings yet
- Information System BookDocument48 pagesInformation System BookRidvan PaşaNo ratings yet
- Using Technology To Address Barriers To Learning: Technical Assistance SamplerDocument66 pagesUsing Technology To Address Barriers To Learning: Technical Assistance SamplerKAINo ratings yet
- 2.6.2 - CO PO ATTAINMENT ManualDocument60 pages2.6.2 - CO PO ATTAINMENT ManualI.T.S Engg100% (2)
- Homework 1 Wireless NetworksDocument2 pagesHomework 1 Wireless NetworkssjognipaNo ratings yet
- Home Studio SeriesDocument8 pagesHome Studio Seriesandrew_ai3100% (3)
- Electronic Science 1Document41 pagesElectronic Science 1Vinit KhaiwalNo ratings yet
- 571188Document28 pages571188eka prasetiaNo ratings yet
- HSBC Case StudyDocument3 pagesHSBC Case StudythunderNo ratings yet
- Core Mathematics C2: GCE Examinations Advanced SubsidiaryDocument4 pagesCore Mathematics C2: GCE Examinations Advanced Subsidiarynishit0157623637No ratings yet
- Curriculum Vitae (Dr. Rupen Chatterjee)Document7 pagesCurriculum Vitae (Dr. Rupen Chatterjee)avirup deNo ratings yet
- Adient Global Supplier Standards Manual - Main (GSS)Document13 pagesAdient Global Supplier Standards Manual - Main (GSS)Claudia PEÑANo ratings yet
- 8051 Microcontroller FeaturesDocument42 pages8051 Microcontroller FeaturesTech_MX67% (3)
- SPSS 15 ManualDocument779 pagesSPSS 15 ManualAyari PMNo ratings yet
- MCA (Revised) / BCA (Revised) Term-End Examination June, 2016Document4 pagesMCA (Revised) / BCA (Revised) Term-End Examination June, 2016Prerak Kumar SharmaNo ratings yet
- CSF 5 INP 18 PH Cybercrime Prevention ActDocument22 pagesCSF 5 INP 18 PH Cybercrime Prevention ActEstela BenegildoNo ratings yet
- Short-Term Load Forecasting Method Based On ARIMA and LSTMDocument5 pagesShort-Term Load Forecasting Method Based On ARIMA and LSTMandrew manuelNo ratings yet
- Powerschool Parent Portal Use Agreement 2010Document1 pagePowerschool Parent Portal Use Agreement 2010api-199941113No ratings yet
- Sagnik Chakraborty: Professional ExperienceDocument1 pageSagnik Chakraborty: Professional ExperiencePranit KumarNo ratings yet
- Acronis Backup & Recovery 11.5: Quick Start GuideDocument12 pagesAcronis Backup & Recovery 11.5: Quick Start GuideDhirender DagarNo ratings yet
- LETTERBACTIVITYPACKFREEBEEDocument68 pagesLETTERBACTIVITYPACKFREEBEEsheenaNo ratings yet
- Assignment No. 3: 1. Plot of Loss Function J Vs Number of IterationsDocument6 pagesAssignment No. 3: 1. Plot of Loss Function J Vs Number of Iterationssun_917443954No ratings yet
- ProductsDocument685 pagesProductsPrince Bin ArafatNo ratings yet