Professional Documents
Culture Documents
DES and AES
DES and AES
Uploaded by
Ayesha's wayCopyright:
Available Formats
You might also like
- Encryption and Decryption Algorithms 1Document5 pagesEncryption and Decryption Algorithms 1Jolina Joy B. BayacaNo ratings yet
- Anderson AESDocument7 pagesAnderson AESMiraculous MiracleNo ratings yet
- Cryptography - Encryption/DecryptionDocument11 pagesCryptography - Encryption/Decryptionpalak2407No ratings yet
- (Delfs and Knebl 2015) : Individual Assignment - Im41103 Network SecurityDocument6 pages(Delfs and Knebl 2015) : Individual Assignment - Im41103 Network SecurityNaue J.No ratings yet
- Anderson DESDocument16 pagesAnderson DESMiraculous MiracleNo ratings yet
- Net Security Chap 2Document20 pagesNet Security Chap 2Asif KoujaganurNo ratings yet
- Encryption Algorithms and Digital SignaturesDocument11 pagesEncryption Algorithms and Digital SignaturesPrateek MahajanNo ratings yet
- Expansion of Round Key Generations in AESDocument20 pagesExpansion of Round Key Generations in AESAno_NimskaNo ratings yet
- Encryption MethodsDocument1 pageEncryption MethodsAli EsamNo ratings yet
- Individual Compu AssigDocument4 pagesIndividual Compu AssigSufiyan MohammedNo ratings yet
- Cryptographypptslideshare 130224053459 Phpapp01 PDFDocument11 pagesCryptographypptslideshare 130224053459 Phpapp01 PDFbalbirNo ratings yet
- Encryption Is Described As The Way of Turning Normal Data Into What Is Known As Cipher TextDocument3 pagesEncryption Is Described As The Way of Turning Normal Data Into What Is Known As Cipher TextTed RogersNo ratings yet
- Ric or Secret Key Cryptography and Asymmetric or Public Key Cryptography. SymmetDocument12 pagesRic or Secret Key Cryptography and Asymmetric or Public Key Cryptography. Symmetvikas310No ratings yet
- Des PDFDocument12 pagesDes PDFmjk4321No ratings yet
- Des PDFDocument12 pagesDes PDFAvinash AvuthuNo ratings yet
- File Encryption, Decryption Using AES Algorithm in Android PhoneDocument6 pagesFile Encryption, Decryption Using AES Algorithm in Android PhoneAnonymous MSmf7l33HYNo ratings yet
- UntitledDocument5 pagesUntitledDanirose RionalNo ratings yet
- 1 Aes Algorithm Using 512 Bit Key Implemented For Secure CommunicationDocument4 pages1 Aes Algorithm Using 512 Bit Key Implemented For Secure CommunicationnatsufrozNo ratings yet
- I Jist 020601Document16 pagesI Jist 020601ijfcstjournalNo ratings yet
- 4 Common Encryption Methods and Use CasesDocument3 pages4 Common Encryption Methods and Use CasesPrabir Kumar MandalNo ratings yet
- Image Security by 3 DesDocument14 pagesImage Security by 3 DesnaveenNo ratings yet
- Asko One GuyDocument7 pagesAsko One GuyHussaini ZubairuNo ratings yet
- AesDocument83 pagesAesGeetha KoteswaraNo ratings yet
- CNS Unit-3Document21 pagesCNS Unit-3Sanika BhaydeNo ratings yet
- WP Encryption En-Lesson 6Document7 pagesWP Encryption En-Lesson 6LDB2No ratings yet
- Confidential Data Storage and DeletionDocument22 pagesConfidential Data Storage and DeletionpoojaNo ratings yet
- Final DocumentDocument60 pagesFinal DocumentRitul RaiNo ratings yet
- EncryptionDocument14 pagesEncryptionSubhrajyoti MallNo ratings yet
- Advanced Encryption Standard (AES) Algorithm To Encrypt and Decrypt DataDocument12 pagesAdvanced Encryption Standard (AES) Algorithm To Encrypt and Decrypt Datatatigutla thulasammaNo ratings yet
- Design and Implementation of Pipelined AES Encryption System Using FPGADocument7 pagesDesign and Implementation of Pipelined AES Encryption System Using FPGAC BNo ratings yet
- Survey Paper Comparing ECC With RSA, AES and Blowfish AlgorithmsDocument4 pagesSurvey Paper Comparing ECC With RSA, AES and Blowfish AlgorithmsEditor IJRITCCNo ratings yet
- Cis Unit2 NotesDocument35 pagesCis Unit2 NotesAAMENA SUZZANNENo ratings yet
- What Is CryptographyDocument9 pagesWhat Is CryptographySagar DixitNo ratings yet
- 2'nd PaperDocument2 pages2'nd PaperRajeshNo ratings yet
- Assignment 1Document10 pagesAssignment 1Barney StinsonNo ratings yet
- White Paper: AES EncryptionDocument5 pagesWhite Paper: AES EncryptionelyiasaNo ratings yet
- AES EncryptionDocument5 pagesAES EncryptionBenvin BaijuNo ratings yet
- Lecture #3Document6 pagesLecture #3Zahid AbbasNo ratings yet
- Comparative Study of Different Cryptographic Algorithms For Data Security in Cloud ComputingDocument7 pagesComparative Study of Different Cryptographic Algorithms For Data Security in Cloud ComputingPathan MehemudNo ratings yet
- The Data Encryption Standard (DES)Document12 pagesThe Data Encryption Standard (DES)RajwecNo ratings yet
- CryptographyDocument9 pagesCryptographyTom LunaNo ratings yet
- No Network Is 100Document7 pagesNo Network Is 100AngelDayanaNo ratings yet
- Topic 7 - CryptographyDocument22 pagesTopic 7 - Cryptographyrojaluteshi28No ratings yet
- Ly Thuyet Mat Ma Do Trong Tuan Aes Details (Cuuduongthancong - Com)Document20 pagesLy Thuyet Mat Ma Do Trong Tuan Aes Details (Cuuduongthancong - Com)mạnh nguyễnNo ratings yet
- Comparative Study of Different Cryptographic Algorithms For Data Security in Cloud ComputingDocument5 pagesComparative Study of Different Cryptographic Algorithms For Data Security in Cloud ComputingAsaba BrianNo ratings yet
- NSC Module II PptsDocument32 pagesNSC Module II PptssamNo ratings yet
- Instructor Materials Chapter 4: The Art of Protecting SecretsDocument29 pagesInstructor Materials Chapter 4: The Art of Protecting SecretsDewi Ayu LestariNo ratings yet
- Ccna 7Document7 pagesCcna 7Paulo RijoNo ratings yet
- AES Seminar ReportDocument17 pagesAES Seminar ReportAbinash AgrawalNo ratings yet
- SecurityDocument78 pagesSecuritypriyeshb13No ratings yet
- Aes Presentation-Group 1Document10 pagesAes Presentation-Group 1DerrickNo ratings yet
- Network SecurityDocument11 pagesNetwork SecurityAshu ChauhanNo ratings yet
- Secure File Storage On Cloud Using Hybrid CryptographyDocument8 pagesSecure File Storage On Cloud Using Hybrid CryptographyVicky VigneshNo ratings yet
- Digital Forensics Question BankDocument18 pagesDigital Forensics Question BankSwaroop DeshpandeNo ratings yet
- A Review Paper On AES and DES Cryptographic AlgorithmsDocument6 pagesA Review Paper On AES and DES Cryptographic AlgorithmsFadhil SahibNo ratings yet
- Doubble EncriptionDocument60 pagesDoubble Encriptiondeepak kumarNo ratings yet
- Aes & RsaDocument3 pagesAes & Rsaelm elmNo ratings yet
- School of Computer Science and Engineering Fall Semester 2020-21Document9 pagesSchool of Computer Science and Engineering Fall Semester 2020-21Jaanaavi WasadeNo ratings yet
- eu-LISA Single Programming Document 2017-2019 PDFDocument249 pageseu-LISA Single Programming Document 2017-2019 PDFRiikka PellinenNo ratings yet
- Statement For A/c XXXXXXXXX2500 For The Period 23-Apr-2022 To 22-Apr-2023Document3 pagesStatement For A/c XXXXXXXXX2500 For The Period 23-Apr-2022 To 22-Apr-2023DANGI TVSNo ratings yet
- FY17 Stockpile Stewardship and Management PlanDocument134 pagesFY17 Stockpile Stewardship and Management PlanNational Nuclear Security Administration100% (1)
- Capstone Final Report-1Document53 pagesCapstone Final Report-1AbhijeetNo ratings yet
- Premarket-Cybersecurity-Guidance 2018 (5663)Document24 pagesPremarket-Cybersecurity-Guidance 2018 (5663)Santosh DixitNo ratings yet
- GVHD: TS. Phạm Văn Tính SVTH: Đoàn Bảo Trung Phạm Văn Nam Tô Thị Thùy Trang Nguyễn Thị Bích ThủyDocument33 pagesGVHD: TS. Phạm Văn Tính SVTH: Đoàn Bảo Trung Phạm Văn Nam Tô Thị Thùy Trang Nguyễn Thị Bích ThủyTrang TôNo ratings yet
- CEHEXAMDocument8 pagesCEHEXAMMbang Abdoul KaderNo ratings yet
- Unit 3 - E-Commerce NotesDocument8 pagesUnit 3 - E-Commerce NotesUtpal KantNo ratings yet
- Alcatel-Lucent 1830 PSS FIPS 140-2 Security Policy PDFDocument63 pagesAlcatel-Lucent 1830 PSS FIPS 140-2 Security Policy PDFAlexNo ratings yet
- PscsDocument3 pagesPscsRobert RobinsonNo ratings yet
- Information Assurance and Security 1 Prelim ExamDocument20 pagesInformation Assurance and Security 1 Prelim ExamAlec BrentNo ratings yet
- Sat - 52.Pdf - Credit Card Fraud Detection With Formula Based AuthenticationDocument11 pagesSat - 52.Pdf - Credit Card Fraud Detection With Formula Based AuthenticationVj KumarNo ratings yet
- Username Enumeration: Real-World Example of A Username Enumeration AttackDocument2 pagesUsername Enumeration: Real-World Example of A Username Enumeration AttackAgrebi noorNo ratings yet
- Modern Cryptography Primer BOOKDocument246 pagesModern Cryptography Primer BOOKFahad IftkharNo ratings yet
- ReadmeDocument16 pagesReadmehygfgNo ratings yet
- The Convergence of Operational Risk and Cyber SecurityDocument16 pagesThe Convergence of Operational Risk and Cyber Securityshirley liliana peña carlosNo ratings yet
- Remote Access Policy Template v1.0Document7 pagesRemote Access Policy Template v1.0rsgrthyjhNo ratings yet
- Fortigate 3700f SeriesDocument12 pagesFortigate 3700f SeriesAmanuelNo ratings yet
- Related-Key AttacksDocument42 pagesRelated-Key Attacksedmund2008No ratings yet
- Network - Diagnostics - 2023 01 09.14 09 29Document23 pagesNetwork - Diagnostics - 2023 01 09.14 09 29jaewm123No ratings yet
- Intel (R) Token Provider For Rsa SecuridDocument10 pagesIntel (R) Token Provider For Rsa SecuridkevinNo ratings yet
- Electronic Transaction Act 2063: NITC/Ministry of Environment, Science and Technology)Document29 pagesElectronic Transaction Act 2063: NITC/Ministry of Environment, Science and Technology)setup vpnNo ratings yet
- Comptia Cloud Cv0 003 Exam ObjectivesDocument18 pagesComptia Cloud Cv0 003 Exam ObjectivesSafari MatabishNo ratings yet
- When Intrusion Detection Meets Blockchain Technology: A ReviewDocument10 pagesWhen Intrusion Detection Meets Blockchain Technology: A ReviewpauloNo ratings yet
- Fortigate 400f SeriesDocument10 pagesFortigate 400f SeriesDaniel MontanoNo ratings yet
- Government of Kerala: Minority CertificateDocument1 pageGovernment of Kerala: Minority CertificateBI185824125 Personal AccountingNo ratings yet
- By Palo Alto Networks - PA-3200 Series - DatasheetDocument3 pagesBy Palo Alto Networks - PA-3200 Series - DatasheetFebzNo ratings yet
- BCA Program Outcomes Program Specific Outcomes and Course OutcomesDocument10 pagesBCA Program Outcomes Program Specific Outcomes and Course Outcomesyuvrajverma8305No ratings yet
- E-Safety and Health and SafetyDocument10 pagesE-Safety and Health and SafetyiGNATIOUSNo ratings yet
- Login VPDDocument2 pagesLogin VPDJukeNo ratings yet
DES and AES
DES and AES
Uploaded by
Ayesha's wayCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
DES and AES
DES and AES
Uploaded by
Ayesha's wayCopyright:
Available Formats
Z DES & AES
Data encryption standard and advance encryption standard are also called block
cypher.
Encryption algorithms are divided into two categories based on the input type, as
a block cipher and stream cipher. Block cipher is an encryption algorithm that
takes a fixed size of input say b bits and produces a ciphertext of b bits again. If
the input is larger than b bits it can be divided further.
DES:
in cryptography”. The Data Encryption Standard, or DES, is an algorithm
for data encryption. It uses symmetric keys of 56-bit size.
The DES algorithm is an archetypal block cipher. It converts a plaintext
bit of fixed length into a ciphertext bit string, keeping its length
unchanged. The block size for DES is 64-bit.
From the very beginning, DES also received criticism due to 56-bit
encryption being too short and a little insecure for modern applications.
However, it played an integral role in the advancement of cryptography.
Various countries worldwide quickly adopted DES after IBM developed it
in the early 1970s.
In 1972, the National Bureau of Standards (US) felt the need for an
encryption standard to protect classified information. Around 1973, the
Atalla Corporation invented a hardware security module, the first of its
kind. It also boosted the need for an international encryption standard.
In 1974, IBM, a competitor to Atalla Corporation, proposed a cipher
named DES. The IBM developed DES on an earlier algorithm called Horst
Feistel’s Lucifer cipher. Horst Feistel, an IBM cryptographer, developed
the Lucifer cipher in 1971.
In 1976, DES became an encryption standard approved by the US
government, followed by its authorisation in 1977 to be used on all
unclassified data. DES received a reaffirmation as a standard in 1983,
1988, 1993 and 1999.
2002 AES or Advanced Encryption Standard ousted DES as the accepted
standard. In 2005, the NIST withdrew the DES algorithm and only
approved Triple DES until 2030 for sensitive government information.
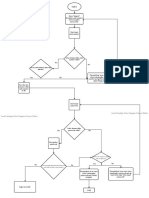
Steps for Encryption
The encryption process consists of the steps discussed below:
Step 1: Starts when the Initial Permutation function acquires the 64-bit
plain text.
Step 2: The plain text block goes through the Initial Permutation or IP.
Step 3: A successful IP produces two permuted half blocks. These two are
called LPT and RPT.
Step 4: This step takes 16 rounds of the encryption process. Both the LPT
and RPT go through this procedure. The encryption procedure consists of
five stages. These are-
S-box Permutation
Key Transformation
P-box Permutation
Expansion Permutation
XOR and Swapping
Step 5: The two half blocks (RPT and LPT) are combined again. The
newly merged block goes through a Final Permutation (FP) procedure.
Step 6: As a result, a 64-bit ciphertext is produced.
What Are the Practical Applications of the DES Algorithm?
The uses of the DES algorithm include:
When a comparatively less secure encryption can do the job, DES is a perfect
choice.
DES can generate random numbers.
Also, DES produces a Triple DES algorithm and uses three DES keys in the
procedure.
https://www.tutorialspoint.com/cryptography/data_encryption_standard.htm
AES:
Aes and des both are symmetric encryption techniques.The
Advanced Encryption Standard (AES) is a symmetric block
cipher chosen by the U.S. government to protect classified
information. AES is implemented in software and hardware
throughout the world to encrypt sensitive data. It is essential
for government computer security, cybersecurity and
electronic data protection.
Advanced Encryption Standard (AES) is a specification for the encryption
of electronic data established by the U.S National Institute of Standards
and Technology (NIST) in 2001. AES is widely used today as it is a much
stronger than DES and triple DES despite being harder to implement.
Points to remember
AES is a block cipher.
The key size can be 128/192/256 bits.
Encrypts data in blocks of 128 bits each.
That means it takes 128 bits as input and outputs 128 bits of encrypted
cipher text as output. AES relies on substitution-permutation network
principle which means it is performed using a series of linked operations
which involves replacing and shuffling of the input data.
Working of the cipher :
AES performs operations on bytes of data rather than in bits. Since the
block size is 128 bits, the cipher processes 128 bits (or 16 bytes) of the
input data at a time.
The number of rounds depends on the key length as follows :
128 bit key – 10 rounds
192 bit key – 12 rounds
256 bit key – 14 rounds
Applications:
AES is widely used in many applications which require secure data
storage and transmission. Some common use cases include:
Wireless security: AES is used in securing wireless networks, such
as Wi-Fi networks, to ensure data confidentiality and prevent
unauthorized access.
Database Encryption: AES can be applied to encrypt sensitive data
stored in databases. This helps protect personal information, financial
records, and other confidential data from unauthorized access in case
of a data breach.
Secure communications: AES is widely used in protocols like such
as internet communications, email, instant messaging, and voice/video
calls.It ensures that the data remains confidential.
Data storage: AES is used to encrypt sensitive data stored on hard
drives, USB drives, and other storage media, protecting it from
unauthorized access in case of loss or theft.
Virtual Private Networks (VPNs): AES is commonly used in VPN
protocols to secure the communication between a user’s device and a
remote server. It ensures that data sent and received through the VPN
remains private and cannot be deciphered by eavesdroppers.
Secure Storage of Passwords: AES encryption is commonly
employed to store passwords securely. Instead of storing plaintext
passwords, the encrypted version is stored. This adds an extra layer
of security and protects user credentials in case of unauthorized
access to the storage.
File and Disk Encryption: AES is used to encrypt files and folders on
computers, external storage devices, and cloud storage. It protects
sensitive data stored on devices or during data transfer to prevent
unauthorized access.
You might also like
- Encryption and Decryption Algorithms 1Document5 pagesEncryption and Decryption Algorithms 1Jolina Joy B. BayacaNo ratings yet
- Anderson AESDocument7 pagesAnderson AESMiraculous MiracleNo ratings yet
- Cryptography - Encryption/DecryptionDocument11 pagesCryptography - Encryption/Decryptionpalak2407No ratings yet
- (Delfs and Knebl 2015) : Individual Assignment - Im41103 Network SecurityDocument6 pages(Delfs and Knebl 2015) : Individual Assignment - Im41103 Network SecurityNaue J.No ratings yet
- Anderson DESDocument16 pagesAnderson DESMiraculous MiracleNo ratings yet
- Net Security Chap 2Document20 pagesNet Security Chap 2Asif KoujaganurNo ratings yet
- Encryption Algorithms and Digital SignaturesDocument11 pagesEncryption Algorithms and Digital SignaturesPrateek MahajanNo ratings yet
- Expansion of Round Key Generations in AESDocument20 pagesExpansion of Round Key Generations in AESAno_NimskaNo ratings yet
- Encryption MethodsDocument1 pageEncryption MethodsAli EsamNo ratings yet
- Individual Compu AssigDocument4 pagesIndividual Compu AssigSufiyan MohammedNo ratings yet
- Cryptographypptslideshare 130224053459 Phpapp01 PDFDocument11 pagesCryptographypptslideshare 130224053459 Phpapp01 PDFbalbirNo ratings yet
- Encryption Is Described As The Way of Turning Normal Data Into What Is Known As Cipher TextDocument3 pagesEncryption Is Described As The Way of Turning Normal Data Into What Is Known As Cipher TextTed RogersNo ratings yet
- Ric or Secret Key Cryptography and Asymmetric or Public Key Cryptography. SymmetDocument12 pagesRic or Secret Key Cryptography and Asymmetric or Public Key Cryptography. Symmetvikas310No ratings yet
- Des PDFDocument12 pagesDes PDFmjk4321No ratings yet
- Des PDFDocument12 pagesDes PDFAvinash AvuthuNo ratings yet
- File Encryption, Decryption Using AES Algorithm in Android PhoneDocument6 pagesFile Encryption, Decryption Using AES Algorithm in Android PhoneAnonymous MSmf7l33HYNo ratings yet
- UntitledDocument5 pagesUntitledDanirose RionalNo ratings yet
- 1 Aes Algorithm Using 512 Bit Key Implemented For Secure CommunicationDocument4 pages1 Aes Algorithm Using 512 Bit Key Implemented For Secure CommunicationnatsufrozNo ratings yet
- I Jist 020601Document16 pagesI Jist 020601ijfcstjournalNo ratings yet
- 4 Common Encryption Methods and Use CasesDocument3 pages4 Common Encryption Methods and Use CasesPrabir Kumar MandalNo ratings yet
- Image Security by 3 DesDocument14 pagesImage Security by 3 DesnaveenNo ratings yet
- Asko One GuyDocument7 pagesAsko One GuyHussaini ZubairuNo ratings yet
- AesDocument83 pagesAesGeetha KoteswaraNo ratings yet
- CNS Unit-3Document21 pagesCNS Unit-3Sanika BhaydeNo ratings yet
- WP Encryption En-Lesson 6Document7 pagesWP Encryption En-Lesson 6LDB2No ratings yet
- Confidential Data Storage and DeletionDocument22 pagesConfidential Data Storage and DeletionpoojaNo ratings yet
- Final DocumentDocument60 pagesFinal DocumentRitul RaiNo ratings yet
- EncryptionDocument14 pagesEncryptionSubhrajyoti MallNo ratings yet
- Advanced Encryption Standard (AES) Algorithm To Encrypt and Decrypt DataDocument12 pagesAdvanced Encryption Standard (AES) Algorithm To Encrypt and Decrypt Datatatigutla thulasammaNo ratings yet
- Design and Implementation of Pipelined AES Encryption System Using FPGADocument7 pagesDesign and Implementation of Pipelined AES Encryption System Using FPGAC BNo ratings yet
- Survey Paper Comparing ECC With RSA, AES and Blowfish AlgorithmsDocument4 pagesSurvey Paper Comparing ECC With RSA, AES and Blowfish AlgorithmsEditor IJRITCCNo ratings yet
- Cis Unit2 NotesDocument35 pagesCis Unit2 NotesAAMENA SUZZANNENo ratings yet
- What Is CryptographyDocument9 pagesWhat Is CryptographySagar DixitNo ratings yet
- 2'nd PaperDocument2 pages2'nd PaperRajeshNo ratings yet
- Assignment 1Document10 pagesAssignment 1Barney StinsonNo ratings yet
- White Paper: AES EncryptionDocument5 pagesWhite Paper: AES EncryptionelyiasaNo ratings yet
- AES EncryptionDocument5 pagesAES EncryptionBenvin BaijuNo ratings yet
- Lecture #3Document6 pagesLecture #3Zahid AbbasNo ratings yet
- Comparative Study of Different Cryptographic Algorithms For Data Security in Cloud ComputingDocument7 pagesComparative Study of Different Cryptographic Algorithms For Data Security in Cloud ComputingPathan MehemudNo ratings yet
- The Data Encryption Standard (DES)Document12 pagesThe Data Encryption Standard (DES)RajwecNo ratings yet
- CryptographyDocument9 pagesCryptographyTom LunaNo ratings yet
- No Network Is 100Document7 pagesNo Network Is 100AngelDayanaNo ratings yet
- Topic 7 - CryptographyDocument22 pagesTopic 7 - Cryptographyrojaluteshi28No ratings yet
- Ly Thuyet Mat Ma Do Trong Tuan Aes Details (Cuuduongthancong - Com)Document20 pagesLy Thuyet Mat Ma Do Trong Tuan Aes Details (Cuuduongthancong - Com)mạnh nguyễnNo ratings yet
- Comparative Study of Different Cryptographic Algorithms For Data Security in Cloud ComputingDocument5 pagesComparative Study of Different Cryptographic Algorithms For Data Security in Cloud ComputingAsaba BrianNo ratings yet
- NSC Module II PptsDocument32 pagesNSC Module II PptssamNo ratings yet
- Instructor Materials Chapter 4: The Art of Protecting SecretsDocument29 pagesInstructor Materials Chapter 4: The Art of Protecting SecretsDewi Ayu LestariNo ratings yet
- Ccna 7Document7 pagesCcna 7Paulo RijoNo ratings yet
- AES Seminar ReportDocument17 pagesAES Seminar ReportAbinash AgrawalNo ratings yet
- SecurityDocument78 pagesSecuritypriyeshb13No ratings yet
- Aes Presentation-Group 1Document10 pagesAes Presentation-Group 1DerrickNo ratings yet
- Network SecurityDocument11 pagesNetwork SecurityAshu ChauhanNo ratings yet
- Secure File Storage On Cloud Using Hybrid CryptographyDocument8 pagesSecure File Storage On Cloud Using Hybrid CryptographyVicky VigneshNo ratings yet
- Digital Forensics Question BankDocument18 pagesDigital Forensics Question BankSwaroop DeshpandeNo ratings yet
- A Review Paper On AES and DES Cryptographic AlgorithmsDocument6 pagesA Review Paper On AES and DES Cryptographic AlgorithmsFadhil SahibNo ratings yet
- Doubble EncriptionDocument60 pagesDoubble Encriptiondeepak kumarNo ratings yet
- Aes & RsaDocument3 pagesAes & Rsaelm elmNo ratings yet
- School of Computer Science and Engineering Fall Semester 2020-21Document9 pagesSchool of Computer Science and Engineering Fall Semester 2020-21Jaanaavi WasadeNo ratings yet
- eu-LISA Single Programming Document 2017-2019 PDFDocument249 pageseu-LISA Single Programming Document 2017-2019 PDFRiikka PellinenNo ratings yet
- Statement For A/c XXXXXXXXX2500 For The Period 23-Apr-2022 To 22-Apr-2023Document3 pagesStatement For A/c XXXXXXXXX2500 For The Period 23-Apr-2022 To 22-Apr-2023DANGI TVSNo ratings yet
- FY17 Stockpile Stewardship and Management PlanDocument134 pagesFY17 Stockpile Stewardship and Management PlanNational Nuclear Security Administration100% (1)
- Capstone Final Report-1Document53 pagesCapstone Final Report-1AbhijeetNo ratings yet
- Premarket-Cybersecurity-Guidance 2018 (5663)Document24 pagesPremarket-Cybersecurity-Guidance 2018 (5663)Santosh DixitNo ratings yet
- GVHD: TS. Phạm Văn Tính SVTH: Đoàn Bảo Trung Phạm Văn Nam Tô Thị Thùy Trang Nguyễn Thị Bích ThủyDocument33 pagesGVHD: TS. Phạm Văn Tính SVTH: Đoàn Bảo Trung Phạm Văn Nam Tô Thị Thùy Trang Nguyễn Thị Bích ThủyTrang TôNo ratings yet
- CEHEXAMDocument8 pagesCEHEXAMMbang Abdoul KaderNo ratings yet
- Unit 3 - E-Commerce NotesDocument8 pagesUnit 3 - E-Commerce NotesUtpal KantNo ratings yet
- Alcatel-Lucent 1830 PSS FIPS 140-2 Security Policy PDFDocument63 pagesAlcatel-Lucent 1830 PSS FIPS 140-2 Security Policy PDFAlexNo ratings yet
- PscsDocument3 pagesPscsRobert RobinsonNo ratings yet
- Information Assurance and Security 1 Prelim ExamDocument20 pagesInformation Assurance and Security 1 Prelim ExamAlec BrentNo ratings yet
- Sat - 52.Pdf - Credit Card Fraud Detection With Formula Based AuthenticationDocument11 pagesSat - 52.Pdf - Credit Card Fraud Detection With Formula Based AuthenticationVj KumarNo ratings yet
- Username Enumeration: Real-World Example of A Username Enumeration AttackDocument2 pagesUsername Enumeration: Real-World Example of A Username Enumeration AttackAgrebi noorNo ratings yet
- Modern Cryptography Primer BOOKDocument246 pagesModern Cryptography Primer BOOKFahad IftkharNo ratings yet
- ReadmeDocument16 pagesReadmehygfgNo ratings yet
- The Convergence of Operational Risk and Cyber SecurityDocument16 pagesThe Convergence of Operational Risk and Cyber Securityshirley liliana peña carlosNo ratings yet
- Remote Access Policy Template v1.0Document7 pagesRemote Access Policy Template v1.0rsgrthyjhNo ratings yet
- Fortigate 3700f SeriesDocument12 pagesFortigate 3700f SeriesAmanuelNo ratings yet
- Related-Key AttacksDocument42 pagesRelated-Key Attacksedmund2008No ratings yet
- Network - Diagnostics - 2023 01 09.14 09 29Document23 pagesNetwork - Diagnostics - 2023 01 09.14 09 29jaewm123No ratings yet
- Intel (R) Token Provider For Rsa SecuridDocument10 pagesIntel (R) Token Provider For Rsa SecuridkevinNo ratings yet
- Electronic Transaction Act 2063: NITC/Ministry of Environment, Science and Technology)Document29 pagesElectronic Transaction Act 2063: NITC/Ministry of Environment, Science and Technology)setup vpnNo ratings yet
- Comptia Cloud Cv0 003 Exam ObjectivesDocument18 pagesComptia Cloud Cv0 003 Exam ObjectivesSafari MatabishNo ratings yet
- When Intrusion Detection Meets Blockchain Technology: A ReviewDocument10 pagesWhen Intrusion Detection Meets Blockchain Technology: A ReviewpauloNo ratings yet
- Fortigate 400f SeriesDocument10 pagesFortigate 400f SeriesDaniel MontanoNo ratings yet
- Government of Kerala: Minority CertificateDocument1 pageGovernment of Kerala: Minority CertificateBI185824125 Personal AccountingNo ratings yet
- By Palo Alto Networks - PA-3200 Series - DatasheetDocument3 pagesBy Palo Alto Networks - PA-3200 Series - DatasheetFebzNo ratings yet
- BCA Program Outcomes Program Specific Outcomes and Course OutcomesDocument10 pagesBCA Program Outcomes Program Specific Outcomes and Course Outcomesyuvrajverma8305No ratings yet
- E-Safety and Health and SafetyDocument10 pagesE-Safety and Health and SafetyiGNATIOUSNo ratings yet
- Login VPDDocument2 pagesLogin VPDJukeNo ratings yet