Professional Documents
Culture Documents
The Security Implication of Multiple Observers in A Distributed System
The Security Implication of Multiple Observers in A Distributed System
Uploaded by
d_codeCopyright:
Available Formats
You might also like
- Mazda 626 ECU DiagaramaDocument6 pagesMazda 626 ECU DiagaramaAndres100% (2)
- Observability of Power Systems Based On Fast Pseudorank Calculation of Sparse Sensitivity MatricesDocument6 pagesObservability of Power Systems Based On Fast Pseudorank Calculation of Sparse Sensitivity Matricesjaved shaikh chaandNo ratings yet
- Equivalente REI DinamicoDocument10 pagesEquivalente REI DinamicoqbjohnnydpNo ratings yet
- Centers Use Supervisory Control and Data Acquisition' (SCADA), Where The Data IsDocument7 pagesCenters Use Supervisory Control and Data Acquisition' (SCADA), Where The Data Isswathi_grenNo ratings yet
- A Coordinated Multi-Switch Attack For Cascading Failures in Smart GridDocument12 pagesA Coordinated Multi-Switch Attack For Cascading Failures in Smart GridBo ChenNo ratings yet
- Critical Infrastructure Interdependency Modeling: Using Graph Models To Assess The Vulnerability of Smart Power Grid and SCADA NetworksDocument6 pagesCritical Infrastructure Interdependency Modeling: Using Graph Models To Assess The Vulnerability of Smart Power Grid and SCADA NetworksNouman AshrafNo ratings yet
- Wide Area ProtectionDocument27 pagesWide Area ProtectionRamesh KannanNo ratings yet
- Transient Stability Assessment of Smart Power System Using Complex Networks FrameworkDocument7 pagesTransient Stability Assessment of Smart Power System Using Complex Networks FrameworkfpttmmNo ratings yet
- Menaa 2107274 ReportDocument13 pagesMenaa 2107274 Reportabir menaaNo ratings yet
- Towards A Framework For Cyber Attack Impact Analysis of Electric Cyber Physical SystemsDocument6 pagesTowards A Framework For Cyber Attack Impact Analysis of Electric Cyber Physical SystemsLakshani AkalankaNo ratings yet
- 1 s2.0 S014206150700097X Main - 2Document7 pages1 s2.0 S014206150700097X Main - 2Arash AbbasiNo ratings yet
- Fault Detection On Radial Power Distribution Systems Using Fuzzy LogicDocument8 pagesFault Detection On Radial Power Distribution Systems Using Fuzzy LogicDa DebebeNo ratings yet
- A Study of Communication and Power System Infrastructure Interdependence On PMU-based Wide Area Monitoring and ProtectionDocument7 pagesA Study of Communication and Power System Infrastructure Interdependence On PMU-based Wide Area Monitoring and ProtectionsupriyasenapatiNo ratings yet
- MA5630 Term Project ReportDocument22 pagesMA5630 Term Project ReportvamshiNo ratings yet
- Measurement Placement For Power System State Estimation by Decomposition TechniqueDocument5 pagesMeasurement Placement For Power System State Estimation by Decomposition TechniquePappo TotoNo ratings yet
- TeiDSBBV ACC2014 VVC PDFDocument7 pagesTeiDSBBV ACC2014 VVC PDFMárcio Venício Pilar AlcântaraNo ratings yet
- Determination of Emergency Power System Voltage Control ActionsDocument6 pagesDetermination of Emergency Power System Voltage Control ActionsLinda Carolina VasconezNo ratings yet
- towards a graph signal processing framework for modeling power system dynamicsDocument5 pagestowards a graph signal processing framework for modeling power system dynamicsPetterson PedroNo ratings yet
- Wide-Area Detection of Voltage Instability From Synchronized Phasor Measurements - Part I - PrincipleDocument9 pagesWide-Area Detection of Voltage Instability From Synchronized Phasor Measurements - Part I - Principlemosh08No ratings yet
- Dynamic Equivalents in Power System Studies A ReviDocument15 pagesDynamic Equivalents in Power System Studies A ReviRong GuoNo ratings yet
- Complex Science Application To The Analysis of Power Systems VulnerabilitiesDocument13 pagesComplex Science Application To The Analysis of Power Systems VulnerabilitiespremNo ratings yet
- General and Simplified Computation of Fault Flow and Contribution of Distributed Sources in Unbalanced Distribution NetworksDocument8 pagesGeneral and Simplified Computation of Fault Flow and Contribution of Distributed Sources in Unbalanced Distribution NetworkshassanNo ratings yet
- Effects of Limits in Small Signal Stability Analysis of Power SystemsDocument6 pagesEffects of Limits in Small Signal Stability Analysis of Power SystemsAshish DuttaNo ratings yet
- 5.ensemble Models For Circuit Topology Estimation, Fault Detection and ClassificaDocument14 pages5.ensemble Models For Circuit Topology Estimation, Fault Detection and ClassificaVEDER MIGUEL TORRES BENITESNo ratings yet
- A Network Reduction Method With Synchronized Phasor MeasurementsDocument6 pagesA Network Reduction Method With Synchronized Phasor MeasurementsicovinyNo ratings yet
- Project Report - Compressive Sensing - FinalDocument5 pagesProject Report - Compressive Sensing - FinalRubén Darío Viñán VelascoNo ratings yet
- Power System Structural Vulnerability Assessment Based On An Improved Maximum Flow ApproachDocument9 pagesPower System Structural Vulnerability Assessment Based On An Improved Maximum Flow Approachazangeneh19No ratings yet
- Power FactoryDocument9 pagesPower Factorypmahesh268No ratings yet
- Cyber-Physical Attacks in Power Networks: Models, Fundamental Limitations and Monitor DesignDocument8 pagesCyber-Physical Attacks in Power Networks: Models, Fundamental Limitations and Monitor DesignDaniel De Matos SilvestreNo ratings yet
- Structured Model Reduction of Power Systems: Christopher Sturk, Luigi Vanfretti, Federico Milano, and Henrik SandbergDocument8 pagesStructured Model Reduction of Power Systems: Christopher Sturk, Luigi Vanfretti, Federico Milano, and Henrik SandbergVerruumm AmineNo ratings yet
- 9bus System, Power FlowDocument17 pages9bus System, Power FlowZeeshan AhmedNo ratings yet
- Establishing Contingency Analysis With FACTS Devices Using Power World SimulatorDocument18 pagesEstablishing Contingency Analysis With FACTS Devices Using Power World SimulatorNasr GhanmiNo ratings yet
- PSA Lecture Notes1Document185 pagesPSA Lecture Notes1Hyma GelliNo ratings yet
- Thesis On Power System Stability PDFDocument5 pagesThesis On Power System Stability PDFWhitney Anderson100% (1)
- Smart Grid Cyber Health Assessment in A Big Bad Data WorldDocument16 pagesSmart Grid Cyber Health Assessment in A Big Bad Data WorldbifNo ratings yet
- Efficient Power System State EstimationDocument5 pagesEfficient Power System State Estimationc_u_r_s_e_dNo ratings yet
- Introduction To Electromagnetic Transient Analysis of Power SystemsDocument8 pagesIntroduction To Electromagnetic Transient Analysis of Power Systemsअंकित अरोड़ाNo ratings yet
- A Cyber Security Study of A SCADA Energy ManagementDocument11 pagesA Cyber Security Study of A SCADA Energy ManagementAsma FarooqNo ratings yet
- Manifold DataminingDocument5 pagesManifold Dataminingnelson_herreraNo ratings yet
- 10 1109@pmaps 2018 8440361Document6 pages10 1109@pmaps 2018 8440361samundra24No ratings yet
- OCPS Unit 5Document15 pagesOCPS Unit 520EPS0701No ratings yet
- Load Modeling For Fault Location in Distribution Systems With Distributed GenerationDocument8 pagesLoad Modeling For Fault Location in Distribution Systems With Distributed Generationcastilho22No ratings yet
- Application of The Fault Tree Analysis For Assessment of Power System ReliabilityDocument12 pagesApplication of The Fault Tree Analysis For Assessment of Power System ReliabilityReki Febrian100% (1)
- Applied Co-Simulation of Intelligent Power SystemsDocument28 pagesApplied Co-Simulation of Intelligent Power Systemsfredy52No ratings yet
- Power System Transient Stability ThesisDocument8 pagesPower System Transient Stability ThesisCollegeApplicationEssayHelpManchester100% (1)
- 10.1.1.139.6493 Co-SimulationDocument14 pages10.1.1.139.6493 Co-SimulationОлександр ДорошенкоNo ratings yet
- PHD Thesis Power System StabilityDocument4 pagesPHD Thesis Power System Stabilityafbtfcstf100% (2)
- Foreword For The Special Section On Analysis and Simulation of Very Large Power SystemsDocument3 pagesForeword For The Special Section On Analysis and Simulation of Very Large Power Systemsmirko.tNo ratings yet
- AnalysisComplexFaults 20090424 Web PDFDocument16 pagesAnalysisComplexFaults 20090424 Web PDFicovinyNo ratings yet
- TPEC 2023 Paper 126Document6 pagesTPEC 2023 Paper 126Sahil MehtaNo ratings yet
- Power System Static-State EstimationDocument6 pagesPower System Static-State EstimationPedro De Leon GuerraNo ratings yet
- Power System StabilityDocument9 pagesPower System StabilityMyScribdddNo ratings yet
- Risk Based TTC Evaluation by Probabilistic Method: K. Audomvongseree, and A. Yokoyama, Member, IEEEDocument6 pagesRisk Based TTC Evaluation by Probabilistic Method: K. Audomvongseree, and A. Yokoyama, Member, IEEEItalo ChiarellaNo ratings yet
- System Modeling and Its Effect On State Estimation in Unbalanced Low Voltage Networks in The Presence of Measurement ErrorsDocument6 pagesSystem Modeling and Its Effect On State Estimation in Unbalanced Low Voltage Networks in The Presence of Measurement ErrorstyaskartikaNo ratings yet
- b9 Research PaperDocument5 pagesb9 Research PaperKushagra BindraNo ratings yet
- General Description of Distribution SystemDocument3 pagesGeneral Description of Distribution SystemMadhumitha SelvarajNo ratings yet
- Distributed Algorithms For Transmission Power Control in Wireless Sensor NetworksDocument5 pagesDistributed Algorithms For Transmission Power Control in Wireless Sensor NetworksCHARALAMPOS CHRISTOFORIDISNo ratings yet
- Abstract: Complex Network Systems Have Been Extensively Used To Analyze NetworkDocument12 pagesAbstract: Complex Network Systems Have Been Extensively Used To Analyze NetworkRavindra JoshiNo ratings yet
- Distributed State Estimation of Multi-Region Power System Based On Consensus TheoryDocument16 pagesDistributed State Estimation of Multi-Region Power System Based On Consensus Theorysami_aldalahmehNo ratings yet
- ISO 14001:2015 Transition Presentation: Presented by Fredric LeungDocument26 pagesISO 14001:2015 Transition Presentation: Presented by Fredric LeungBiswadip BanerjeeNo ratings yet
- ITIL - Introducing Service Design PDFDocument17 pagesITIL - Introducing Service Design PDFKumar Soubhagya DuttaNo ratings yet
- HTML Basic LessonDocument8 pagesHTML Basic LessonR TECHNo ratings yet
- Creating NC FilesDocument8 pagesCreating NC FilesStelian ConstantinescuNo ratings yet
- C++ Vs Java - ComparativaDocument2 pagesC++ Vs Java - ComparativaJoaquín Schaffer0% (1)
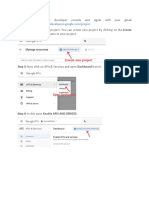
- Step 1: Open Google: Developer Console and Signin With Your Gmail AccountDocument11 pagesStep 1: Open Google: Developer Console and Signin With Your Gmail Accountjohn mark laquipNo ratings yet
- GTD Basics PDFDocument60 pagesGTD Basics PDFRahul_Ravindra_2899100% (4)
- 01 OverviewDocument65 pages01 OverviewdqltakedaNo ratings yet
- How To Find The Overdue Jobs?Document12 pagesHow To Find The Overdue Jobs?Denizio CaldasNo ratings yet
- RWD Uperform 4.10.0 Managing Content PDFDocument373 pagesRWD Uperform 4.10.0 Managing Content PDFotracuentaaux9No ratings yet
- Excel QuizDocument24 pagesExcel QuizSoumitra ChakrabortyNo ratings yet
- Webgoat DeveloperWorkbookDocument279 pagesWebgoat DeveloperWorkbookEdison AcostaNo ratings yet
- NCERT Solutions For Class 12th Maths Chapter 3 - MatricesDocument72 pagesNCERT Solutions For Class 12th Maths Chapter 3 - Matricesdilip saxena0% (1)
- Optimal Product ProcessDocument51 pagesOptimal Product ProcessVan Gunxsword100% (5)
- Exemple Concours Master Finace d'Entreprise 2013-2014, Fsjes RABAT - منتدى كلية الحقوق أكادير - FSJES AGADIR FORUMDocument3 pagesExemple Concours Master Finace d'Entreprise 2013-2014, Fsjes RABAT - منتدى كلية الحقوق أكادير - FSJES AGADIR FORUMSoukaina MoumenNo ratings yet
- KUMARAPERUMAL CHIDAMBARAM Auditor CVDocument4 pagesKUMARAPERUMAL CHIDAMBARAM Auditor CVKumaraperumal ChidambaramNo ratings yet
- XPSWMM: Tutorial 9: DTM Example inDocument12 pagesXPSWMM: Tutorial 9: DTM Example inrimana2144No ratings yet
- Concepts of Nuclear Physics by B L Cohen 0070115567 PDFDocument5 pagesConcepts of Nuclear Physics by B L Cohen 0070115567 PDFVeerendra Viru100% (1)
- A. Multiple Choice Questions (80%)Document4 pagesA. Multiple Choice Questions (80%)George ChalhoubNo ratings yet
- CNN-based and DTW Features For Human Activity Recognition On Depth MapsDocument14 pagesCNN-based and DTW Features For Human Activity Recognition On Depth Mapsjacekt89No ratings yet
- Number SystemDocument6 pagesNumber SystemJoerel NicolasNo ratings yet
- CHEM 1100 HessLaw F11Document3 pagesCHEM 1100 HessLaw F11SeverianzNo ratings yet
- Crack Windows 2Document2 pagesCrack Windows 2studyuntildieNo ratings yet
- Colon Classification 6Document2 pagesColon Classification 6Monica FloresNo ratings yet
- SNMP Reference Guide For Idrac and Chassis Management ControllerDocument116 pagesSNMP Reference Guide For Idrac and Chassis Management ControllerandreoaNo ratings yet
- Introduction of CADDocument6 pagesIntroduction of CADKhengling Lim100% (1)
- Shower Spares & Parts ShoweringDocument1 pageShower Spares & Parts Showeringf9zvxkvw5mNo ratings yet
- AVEVA Mechanical Equipment InterfaceDocument2 pagesAVEVA Mechanical Equipment InterfaceaminNo ratings yet
- Programming in C For BCA BIT BEDocument0 pagesProgramming in C For BCA BIT BEwww.bhawesh.com.npNo ratings yet
The Security Implication of Multiple Observers in A Distributed System
The Security Implication of Multiple Observers in A Distributed System
Uploaded by
d_codeOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
The Security Implication of Multiple Observers in A Distributed System
The Security Implication of Multiple Observers in A Distributed System
Uploaded by
d_codeCopyright:
Available Formats
The Security Implication of Multiple Observers in a Distributed System
Derek P. Ditch and Bruce M. McMillin
Department of Computer Science
Missouri University of Science and Technology
Rolla, Missouri, USA
derek.ditch,ff@mst.edu
AbstractCondentiality is an often overlooked, yet crucial
point in the security analysis of a system. infrastructures take
for granted that condentiality is maintained through obfusca-
tion by dissemination of information. This dissemination does
indeed maintain the condentiality of the system when only a
small portion of the information can be obtained by an outside
observer. However, when multiple observers collaboratively
make observations, the condential information can be revealed
or even just partially revealed. If a team of attackers on a
system can deduce enough information to successfully perform
a crippling attack, the system could not be considered secure.
This paper will bring together facets of graph theory, electrical
physics, and statistics to illustrate how a team of attackers could
compromise a partially deducible system. The infrastructure
considered in this paper is a power transmission system, but
these techniques could be applied to any system which could
be modeled as a resistance network; including trafc system,
oil and gas pipelines, or even a large scale computer network.
I. INTRODUCTION
Many nations modern critical infrastructures, include
systems with signicant cyber and physical components. The
concept of cyber-physical security consists of a combination
of the security considerations for the physical protection of
system and the protection of the control system against com-
puter network vulnerabilities. This combination of computer
system interaction and physical constraints of the system
add an additional layer of complexity in these cyber-physical
systems [1][2]. Since these systems now have this additional
complexity, it is necessary to perform analysis of these
systems using cross-subsystem techniques, which can be
used to show the additional relationships that exist between
the physical phenomena and the reactions of the control
system.
The nationwide electric power system infrastructure is
arguably the most important to be resilient against attack
and other failures. In the event of a widespread power
failure, many other critical systems are disabled as well.
Consider for a moment the blackout in the Northeastern
United States and Canada in the summer of 2003. While
the cause of this large-scale failure was a conglomeration
of failures, the overall cause was accidental. It was purely a
failure of proper fault tolerance planning and maintenance.
However, this exact same scenario could have been caused
by an attacker that could prot by such a large power outage.
Perhaps this attacker may even want to merely spread fear
in pursuit of his or her own political agenda. This failure
of fault tolerance could have just as easily been a failure of
cyber-physical security.
In this paper, we use the electric power grid as a moti-
vating example and present an approach to model a power
system using graphical networks. This approach is currently
used by a few researchers [3], but is not very widespread.
Graphs are often used in the security analysis of computer
systems. By tting this analysis technique, we instill a
uniform semantic basis, allowing us to use the same analysis
techniques across a multiple domains. Specically, we will
address the issue of condentiality of the power system with
respect to outside observers. The question we address then
is: Given an arbitrary graph, what is the minimum number
of observers that is needed to calculate the current state of
the graph, such that an attack is feasible? The nature of
the attack can be physical, or cyber, or both. Divulging the
condentiality of the cyber system through these external
observations, in particular, forms a type of information
leakage [4] from the condential domain of the control
system to an external observer. Note, that this question does
not necessarily require that the full system state be known.
A partially deducible system could be sufcient for such a
compromise. While we address this question by applying it
to a power system, the techniques presented in this paper
will work for any system that is modeled as a resistance
network depicted by a graph.
II. LITERATURE AND BACKGROUND
The techniques used in this paper are a combination of
graph theory, statistics, and physics. Modeling circuits and
solving them using graphs has been used for quite a while.
In fact, Kirchoffs current Loop Law is quite similar to the
graph theoretic algorithm for nding cycles through the use
of spanning trees.
Previous work on state estimation of power systems most
commonly uses a weighted least squares technique for the
purpose of solving an entire power system. This method
works using redundant information in a subset of system
measurements. This redundant data improves the accuracy
of the solution to the steady state of the system. The
limitation to this approach from an adversarys point of
view, is that it cannot be performed in real time. This is
because the weighted least squares technique is an iterative
technique that depends on prior measurements in order to
obtain the current system state [5]. However, the amount
of precision and granularity produced by the weighted least
squares approach is not necessarily required for an attacker
to successfully execute an attack on a vulnerable power
system. Using the techniques detailed in this paper, an
attacker or team of attackers could utilize signicantly less
information in order to locate a vulnerable power line in the
power system.
III. MODELING THE POWER SYSTEM AS A GRAPH
As stated in the introduction, we model the power system
as a graph, which gives us a uniform semantic basis on
which to perform the analysis. Modeling the power system
as a graph is rather straight forward. A graph is dened by a
set of vertices, V, and edges, E, and is denoted by G = {V,E}.
To t the power system into this, we dene the vertices to
represent buses and the edges to represent lines[6]. For the
purpose of illustration of the methods in this paper, we make
the following assumptions in our model:
we consider only real power and therefore use DC
formulas for simplicity (methods for AC work as well
[7], but further complicate the explanation)
we consider only single, directed edges between ver-
tices. In cases where multiple lines exist between
buses, simply combine them and add the conductances,
yielding the effective resistances.
We make these assumptions without loss of generality.
They give us a more exible model with reduced complexity.
A simple, directed graph allows us a wide variety of existing
graph algorithms at our disposal.
To begin, we will model the example 5-bus system given
in Figure 1 as a graph. The directions of power ow in
the graph model are arbitrarily chosen, just as they are in
circuit calculations. They simply change the sign of the
resulting power ow, but do not affect the relationship. We
are concerned primarily with the topological structure of the
power system, with a bit of numerical analysis.
The numbers shown in Figure 1 denote the conductance
of the edges. This could as well be considered power ow
in a power system. This is due to the denition of power:
P = IV =
V
2
R
= V
2
, where is the conductance. When
the voltage is one, they are equivalent. Since in a power
system voltage is constant, they are still equivalent.
Spectral graph theory is a branch of graph theory that is
mainly concerned with the topological features of a graph. It
uses matrix representations of the graph in order to describe
the relationships between the vertices and edges [8]. The rst
matrix we are concerned with is the incidence matrix. This
matrix maps the edges of a graph to its vertices, including
the direction of the edge. The entries of the incidence matrix
are as follows:
A(i, j) =
_
_
_
1 if i is the tail vertex of the edge (i, j)
1 if i is the head vertex of the edge (i, j)
0 otherwise
(1)
Next, we dene the resistance matrix, R, an nn diagonal
matrix with the entries equal to the i-th edge. Note, that these
edges are in the same order as the edges in A. Finally, we can
dene the Laplacian matrix, L. This matrix can summarize
the data of the A and R matrices and can be dened as:
L = A
T
R
1
A (2)
Equipped with these tools, it is possible to quickly solve
the steady state values of voltage potentials at each bus,
current on any line, and even the effective resistance between
any two points. These calculations can be performed by
knowing the generation and the loads of the power system.
However, an attacker will not necessarily know this infor-
mation at all times, particularly when a load exists at every
or even most buses. Instead what an attacker may attempt
would be to back solve using a subset of the line readings
in order to get a rough estimation of the power system state.
IV. COMPUTATIONS
Before getting into the steps an attacker could use against
a power system, we must rst understand the types of attacks
that could be performed on such as system. This will allow
us to identify the goals that such an adversary might pursue.
A. Avenues of Attack
Within the realm of information security, there are three
fundamental classications: condentiality, integrity, and
availability. Availability is the property in information se-
curity dened as the system being available when needed.
Availability is often ensured through fault tolerance and
physical security. Availability is also protected by the under-
lying integrity of the system. Integrity is the property that the
system state is not modied in an unauthorized manner. This
means that the system is operating within the boundaries set
within the specication. The integrity is further protected by
the condentiality. This property prevents the disclosure of
the high-level, or protected, information. Condentiality is
arguably the most difcult and most important of the three
properties to analyze and protect. This is due to the inherent
difculty in understanding all factors that could compromise
the systems secrecy. In the event that the condentiality is
compromised, so too can the integrity and the availability of
the system [9].
Attacks on the availability of a power system can range
from attacks on the control system, the sensor data, or more
physical attacks. An adversary could cause a power line to
overload by causing a fault to ground, or discretely causing
an increase in loads at key locations. A distributed load
increase could cause power to be routed in such a way that a
target line could be overloaded, causing a circuit breaker to
blow or even physical damage to a power line or substation.
B. Single Generation, Single Load
We will begin the model with a very simple graph for ease
of explanation. The graph pictured in Figure 1 illustrates a 5-
bus system with a one generator, one load, and a network of
lines between. In this simplied graph, we have removed all
loads except the load at bus C and all generation except the
generation at bus A . S
C
denotes the source of the graph at
A . In the power system, this is a generation. T
C
denotes the
sink of the graph at C . This is a load in a power system.
The numbers along each edge denote the conductance of
that edge. This conductance value is the reciprocal of the
resistance of the edge.
Our goal is to establish a relationship between the currents
along each edge of the network. We assume the attacker
has learned the resistance and physical structure of the
power system. This assumption is not outrageous, since this
information could be physically measured over a long period
of time. Also, since this information is generally static, the
attacker can assume that his time consuming reconnaissance
is still valid.
To begin, we build the incidence and resistance matrices,
which we use for further calculations.
A =
_
_
A B C D E
1 1 0 0 0 1
2 1 0 0 1 0
3 1 0 1 0 0
4 0 1 0 0 1
5 0 1 0 1 0
6 0 1 1 0 0
7 0 0 1 1 0
_
_
(3)
R =
_
_
.036
.067
0.059
.045
.125
.100
.667
_
_
(4)
Then, as previously dened, the Laplacian is calculated:
L = A
T
R
1
A
=
_
_
60 0 17 15 28
0 40 10 8 22
17 10 30 3 0
15 8 3 26 0
28 22 0 0 50
_
_
(5)
The Laplacian provides a relationship between the potentials
and currents. This can be seen, since the Laplacian contains
entries of the conductances, or inverse resistance. Then the
relationship v = i r becomes v
1
r
= v c = i, where c
is the conductance, or inverse resistance. It can be seen,
then, that using the Laplacian with vector multiplication
would result in a vector of currents that build-up at each
vertex. According to Kirchoffs law, this must be zero for
each vertex not at a generation or a load. This gives us the
following equation:
L
V =
I (6)
where
V contains the voltage potentials at each vertex and
I contains the net current at each vertex.
We can now use the Laplacian to solve for more inter-
esting static aspects of the power system. By performing
a random walk on an electrical power network, we can
nd the potentials located at each vertex. We can do this
by applying a 1-volt battery between the source and sink,
which is equivalent to applying a probability of one to the
source and a probability of zero to the sink. We now want
to solve for the rest of
V and we can even nd the effective
resistance between the source and sink along the way. We
use the relationship found in equation 6 substituting in the
probabilities at the source and sink. Since we know that
current only builds up at the source and sink, we also set
the rest of the currents to zero. We will also rearrange the
rows and columns to put vertices A and C rst, allowing an
easier visual for solving the system of equations. Using our
network, the system of equations are now:
_
_
60 17 0 15 28
17 30 10 3 0
0 10 40 8 22
15 3 8 26 0
28 0 22 0 50
_
_
_
_
1
0
v
B
v
D
v
E
_
_
=
_
_
i
A
i
C
0
0
0
_
_
(7)
Now, we solve the system using block matrices to derive
the following:
_
A B
T
B C
_ _
b
v
_
=
_
i
0
_
A
b + B
T
v =
i
B
b + Cv =
0
v = C
1
B
b
=
_
_
.036 .011 .016
.011 .042 .005
.016 .005 .027
_
_
_
_
0 10
15 3
28 0
_
_
_
1
0
_
=
_
_
.608
.764
.827
_
_
(8)
Finally, the result of the system potentials when applying
a 1-volt battery is represented by the vector v, hereafter
referred to as the unit-voltage potentials vector. We can also
calculate the unit-voltage currents vector, represented by
I,
which is the same as the found in equation 6. They are both
listed here:
V =
_
_
1
0.6079
0
0.7640
0.8275
_
I =
_
_
25.3710
0
25.3710
0
0
_
_
(9)
As a by-product of the previous calculations, we can
calculate the relationship between voltage and current be-
tween the source and the sink. This relationship is the
effective resistance between the source and sink. Following
the derivation in equation 8, we can solve for
i.
i = A
b B
T
C
1
B
b
= (AB
T
C
1
B)
b
=
_
_
1 1
1 1
__
b
(10)
As seen above, the equation (AB
T
C
1
B) yields a scalar,
, which is the inverse of the effective resistance between
the two vertices A and C . We can also use this effective
resistance as a scalar map to get the fraction of current from
the source that ows across each edge.
Theorem 1: For a system a single source and single sink,
only one measurement is required in order to calculate the
full system state.
Proof:
Using v, we can calculate the currents on each edge in
the graph where i
xy
= (v
x
v
y
)R
xy
. With
i, the unit-
voltage ow vector we can solve for the proportion of current
from the source that ows over each edge within the graph.
We do this by transforming
i to
i, called the unit-current
ow vector. This can be done using the observation that
the effective resistance between the any two vertices of the
graph demonstrates the ratio between the currents per edge
by applying a unit voltage and a unit current [10] (as seen
in equation 11).
v = R
eff
i
v = R
eff
i
v =
i =
1
i = R
eff
i
(11)
For our graph, the calculated unit-current ow vector is:
i =
_
_
.1904
.1395
.6701
.1904
.0492
.2396
.0903
_
_
These represent the proportion of current originating at
A that ows across each edge. Going back to our original
question asking how many observers are required to solve
the system, we now only need one measurement of the
current to determine the amount of power generated. Once
we have found this value, we can nd all of the current ows
across any edge.
C. Multiple Generations, Single Load
Following the discussion found in Section IV-B, it be-
comes almost trivial to solve a system with multiple gener-
ators, or sources. As is found in the original power system
diagram (Figure 1), we add a generator at vertex B.
Solving this system begins with the observation that the
current owing across each edge is the sum of the compo-
nent currents owing across the edge [11]. The components
in this case are the currents from each source in the system.
It is important to take into account the direction of the ow
when doing this.
i
xy
=
i
A
i
A,xy
+
i
B
i
B,xy
, where i
xy
= i
yx
(12)
A single observer is now presented with a single equation
containing two unknown values. The obvious solution to this
problem is to add an additional line measurement, which
is equivalent to adding another observer. This leads to the
following:
Corollary 1: For any electrical network modeled by a
graph with N sources and one sink, the network can be
solved given N or more observers.
Proof: Directly from the discussion above.
A second observer taking measurements on the independent
edge, (u,v), yields the system of equations:
i
A
=
i
xy
i
A,xy
i
B
i
B,xy
i
A,xy
i
B
=
i
uv
i
B,uv
i
A
i
A,uv
i
B,uv
(13)
D. Multiple Generations, Multiple Loads
In real power systems, there are several generators and
loads at most buses. Modeling this into a graph puts a sink
at each vertex, which adds a large amount of obfuscation,
with respect to our observers. Since every load between
the observer an any given generator can be arbitrarily large
(subject to limits of the transmission lines), an observer or
team of observers can no longer fully deduce the entire
power system using the one observer to one generator rule
presented above. In fact, in order to fully deduce the power
system, N-1 observers are required, where there are N edges
in the graph [12].
Even with this limitation, however, an attacker could
partially deduce the system. This partial deduction can
still provide enough information in order to successfully
complete an attack upon the system. Going back to the
types of attacks on a power system, the primary avenue of
attack is to overload a transmission line. Each transmission
line has a safe operating range and a physical limit to the
amount of current that it can transmit. In addition to that,
power substations have circuit breakers which will trip given
too large of a current. The attacker could gain a set of
inequalities using the above techniques.
Theorem 2: When a load is placed between an attackers
observation and the source of the current, the uncertainty
in the measurement is increased. The amount by which it
increased is dependent upon the structure of the graph and
the placement of the load in relation to the observer.
Proof: Specically, equation 13 changes to produce the
following inequality:
i
A
i
xy
i
A,xy
i
B
i
B,xy
i
A,xy
i
B
i
uv
i
B,uv
i
A
i
A,uv
i
B,uv
(14)
Uncertainty is dened here, as the difference between the
estimates of equation 14 and the exact state provided by
equation 13
Using this system of inequalities, if an attacker can
calculate the maximum current that a line can transmit, he
can calculate the maximum amount of current that needs
to drawn to a specic load, in order to trip any given line
in the graph. Another attack that could be performed is to
locate the lines which would cause the largest disruption in
the event that the power needed to be rerouted due to a fault
to ground.
For our example system, the graph in Figure 3 depicts the
relationship between the number of observers in the system
and the uncertainty of the solutions. In this sense, uncertainty
refers to the margin error between the calculated power ow,
and the actual power ow. At this time, there is not a formal
generic way to determine this relationship. It is dependent on
the placement of the observers and the topologica structure
of graph. The optimal placement of observers, and therefore
the techniques to thwart this are outside the scope of this
article.
V. RESULTS
This paper has demonstrated simple techniques that are
already used in calculation of power systems, but presents
them in a new light. Using these techniques, an attacker can
solve or partially solve a system. If an attacker can arrange
tight enough bounds upon a power system, then he could use
the demonstrated bounds to locate and exploit vulnerabilities
within the system. This is due to the fact that the real-time
condentiality of the state of the power system is revealed.
Even with these simple tools available to would-be at-
tackers, it is possible to thwart these types of attacks. For
example, one could limit the effectiveness of the bounds, or
even make the information gathering stage more difcult.
One way this can occur, is by increasing the connectivity
within the power system. This will make discovery of the
topology more difcult.
Further research in this area can determine exactly how
much information about a systems state can be deduced
using this partial deducibility technique. Little work has been
done to ascertain the implications of a partially deducible
system with respect to the system security. By combining
graph theory and probability analysis, it may be possible to
shed some light in this research void.
REFERENCES
[1] H. Tang and B. McMillin, Security property violation in CPS
through timing, Distributed Computing Systems Workshops,
International Conference on, vol. 0, pp. 519524, 2008.
[2] E. A. Lee, Cyber physical systems: Design challenges,
EECS Department, University of California, Berkeley, Tech.
Rep. UCB/EECS-2008-8, Jan 2008. [Online]. Available:
http://www.eecs.berkeley.edu/Pubs/TechRpts/2008/EECS-
2008-8.html
[3] A. Armbruster, M. Gosnell, B. McMillin, and M. Crow,
Power transmission control using distributed max-ow,
Computer Software and Applications Conference, 2005.
COMPSAC 2005. 29th Annual International, vol. 1, pp. 256
263 Vol. 2, July 2005.
[4] H. Tang and B. McMillin, Security of information ow in
the electric power grid, in Critical Infrastructure Protection,
Post-Proceedings of the First Annual IFIP Working Group
11.10 International Conference on Critical Infrastructure
Protection, Dartmouth College, Hanover, New Hampshire,
USA, March 19-21, 2007, ser. IFIP, E. Goetz and S. Shenoi,
Eds., vol. 253. Springer, 2007, pp. 4356.
[5] A. Monticelli, Electric power system state estimation, Pro-
ceedings of the IEEE, vol. 88, no. 2, pp. 262282, 2000.
[6] B. Bollob as, Graph Theory: An Introductory Course.
Springer, 1979.
[7] A. Abur and A. G. Exp osito, Power System State Estimation:
Theory and Implementation. New York: Marcel Dekker,
2004.
[8] F. R. K. Chung, Spectral graph theory, Regional Confer-
ence Series in Mathematics, American Mathematical Society,
vol. 92, pp. 1212, 1997.
[9] D. Brewer and M. Nash, The Chinese Wall security policy,
in Security and Privacy, 1989. Proceedings., 1989 IEEE
Symposium on, 1989, pp. 206214.
[10] P. G. Doyle and J. L. Snell, Random walks
and electric networks, 2000. [Online]. Available:
http://www.citebase.org/abstract?id=oai:arXiv.org:math/0001057
[11] G. L. Miller, Flow in planar graphs with multiple sources
and sinks, SIAM J. Comput., vol. 24, no. 5, pp. 10021017,
1995.
[12] T. Gamage and B. McMillin, Observering for changes:
Nondeducibility based analysis of cyber-physical systems,
in Critical Infrastructure Protection III, Post-Proceedings of
the Third Annual IFIP Working Group 11.10 International
Conference on Critical Infrastructure Protection, Dartmouth
College, Hanover, New Hampshire, USA, March 22-25, 2009,
ser. IFIP. Springer, 2009.
(a) 5 Node Power System Diagram
(b) 5 Node Power System Graph
Figure 1. Example Power System
Figure 2. 5 Node Power System Graph with 2 Sources
Figure 3. Example relationship between number of observers and amount
of uncertainty.
You might also like
- Mazda 626 ECU DiagaramaDocument6 pagesMazda 626 ECU DiagaramaAndres100% (2)
- Observability of Power Systems Based On Fast Pseudorank Calculation of Sparse Sensitivity MatricesDocument6 pagesObservability of Power Systems Based On Fast Pseudorank Calculation of Sparse Sensitivity Matricesjaved shaikh chaandNo ratings yet
- Equivalente REI DinamicoDocument10 pagesEquivalente REI DinamicoqbjohnnydpNo ratings yet
- Centers Use Supervisory Control and Data Acquisition' (SCADA), Where The Data IsDocument7 pagesCenters Use Supervisory Control and Data Acquisition' (SCADA), Where The Data Isswathi_grenNo ratings yet
- A Coordinated Multi-Switch Attack For Cascading Failures in Smart GridDocument12 pagesA Coordinated Multi-Switch Attack For Cascading Failures in Smart GridBo ChenNo ratings yet
- Critical Infrastructure Interdependency Modeling: Using Graph Models To Assess The Vulnerability of Smart Power Grid and SCADA NetworksDocument6 pagesCritical Infrastructure Interdependency Modeling: Using Graph Models To Assess The Vulnerability of Smart Power Grid and SCADA NetworksNouman AshrafNo ratings yet
- Wide Area ProtectionDocument27 pagesWide Area ProtectionRamesh KannanNo ratings yet
- Transient Stability Assessment of Smart Power System Using Complex Networks FrameworkDocument7 pagesTransient Stability Assessment of Smart Power System Using Complex Networks FrameworkfpttmmNo ratings yet
- Menaa 2107274 ReportDocument13 pagesMenaa 2107274 Reportabir menaaNo ratings yet
- Towards A Framework For Cyber Attack Impact Analysis of Electric Cyber Physical SystemsDocument6 pagesTowards A Framework For Cyber Attack Impact Analysis of Electric Cyber Physical SystemsLakshani AkalankaNo ratings yet
- 1 s2.0 S014206150700097X Main - 2Document7 pages1 s2.0 S014206150700097X Main - 2Arash AbbasiNo ratings yet
- Fault Detection On Radial Power Distribution Systems Using Fuzzy LogicDocument8 pagesFault Detection On Radial Power Distribution Systems Using Fuzzy LogicDa DebebeNo ratings yet
- A Study of Communication and Power System Infrastructure Interdependence On PMU-based Wide Area Monitoring and ProtectionDocument7 pagesA Study of Communication and Power System Infrastructure Interdependence On PMU-based Wide Area Monitoring and ProtectionsupriyasenapatiNo ratings yet
- MA5630 Term Project ReportDocument22 pagesMA5630 Term Project ReportvamshiNo ratings yet
- Measurement Placement For Power System State Estimation by Decomposition TechniqueDocument5 pagesMeasurement Placement For Power System State Estimation by Decomposition TechniquePappo TotoNo ratings yet
- TeiDSBBV ACC2014 VVC PDFDocument7 pagesTeiDSBBV ACC2014 VVC PDFMárcio Venício Pilar AlcântaraNo ratings yet
- Determination of Emergency Power System Voltage Control ActionsDocument6 pagesDetermination of Emergency Power System Voltage Control ActionsLinda Carolina VasconezNo ratings yet
- towards a graph signal processing framework for modeling power system dynamicsDocument5 pagestowards a graph signal processing framework for modeling power system dynamicsPetterson PedroNo ratings yet
- Wide-Area Detection of Voltage Instability From Synchronized Phasor Measurements - Part I - PrincipleDocument9 pagesWide-Area Detection of Voltage Instability From Synchronized Phasor Measurements - Part I - Principlemosh08No ratings yet
- Dynamic Equivalents in Power System Studies A ReviDocument15 pagesDynamic Equivalents in Power System Studies A ReviRong GuoNo ratings yet
- Complex Science Application To The Analysis of Power Systems VulnerabilitiesDocument13 pagesComplex Science Application To The Analysis of Power Systems VulnerabilitiespremNo ratings yet
- General and Simplified Computation of Fault Flow and Contribution of Distributed Sources in Unbalanced Distribution NetworksDocument8 pagesGeneral and Simplified Computation of Fault Flow and Contribution of Distributed Sources in Unbalanced Distribution NetworkshassanNo ratings yet
- Effects of Limits in Small Signal Stability Analysis of Power SystemsDocument6 pagesEffects of Limits in Small Signal Stability Analysis of Power SystemsAshish DuttaNo ratings yet
- 5.ensemble Models For Circuit Topology Estimation, Fault Detection and ClassificaDocument14 pages5.ensemble Models For Circuit Topology Estimation, Fault Detection and ClassificaVEDER MIGUEL TORRES BENITESNo ratings yet
- A Network Reduction Method With Synchronized Phasor MeasurementsDocument6 pagesA Network Reduction Method With Synchronized Phasor MeasurementsicovinyNo ratings yet
- Project Report - Compressive Sensing - FinalDocument5 pagesProject Report - Compressive Sensing - FinalRubén Darío Viñán VelascoNo ratings yet
- Power System Structural Vulnerability Assessment Based On An Improved Maximum Flow ApproachDocument9 pagesPower System Structural Vulnerability Assessment Based On An Improved Maximum Flow Approachazangeneh19No ratings yet
- Power FactoryDocument9 pagesPower Factorypmahesh268No ratings yet
- Cyber-Physical Attacks in Power Networks: Models, Fundamental Limitations and Monitor DesignDocument8 pagesCyber-Physical Attacks in Power Networks: Models, Fundamental Limitations and Monitor DesignDaniel De Matos SilvestreNo ratings yet
- Structured Model Reduction of Power Systems: Christopher Sturk, Luigi Vanfretti, Federico Milano, and Henrik SandbergDocument8 pagesStructured Model Reduction of Power Systems: Christopher Sturk, Luigi Vanfretti, Federico Milano, and Henrik SandbergVerruumm AmineNo ratings yet
- 9bus System, Power FlowDocument17 pages9bus System, Power FlowZeeshan AhmedNo ratings yet
- Establishing Contingency Analysis With FACTS Devices Using Power World SimulatorDocument18 pagesEstablishing Contingency Analysis With FACTS Devices Using Power World SimulatorNasr GhanmiNo ratings yet
- PSA Lecture Notes1Document185 pagesPSA Lecture Notes1Hyma GelliNo ratings yet
- Thesis On Power System Stability PDFDocument5 pagesThesis On Power System Stability PDFWhitney Anderson100% (1)
- Smart Grid Cyber Health Assessment in A Big Bad Data WorldDocument16 pagesSmart Grid Cyber Health Assessment in A Big Bad Data WorldbifNo ratings yet
- Efficient Power System State EstimationDocument5 pagesEfficient Power System State Estimationc_u_r_s_e_dNo ratings yet
- Introduction To Electromagnetic Transient Analysis of Power SystemsDocument8 pagesIntroduction To Electromagnetic Transient Analysis of Power Systemsअंकित अरोड़ाNo ratings yet
- A Cyber Security Study of A SCADA Energy ManagementDocument11 pagesA Cyber Security Study of A SCADA Energy ManagementAsma FarooqNo ratings yet
- Manifold DataminingDocument5 pagesManifold Dataminingnelson_herreraNo ratings yet
- 10 1109@pmaps 2018 8440361Document6 pages10 1109@pmaps 2018 8440361samundra24No ratings yet
- OCPS Unit 5Document15 pagesOCPS Unit 520EPS0701No ratings yet
- Load Modeling For Fault Location in Distribution Systems With Distributed GenerationDocument8 pagesLoad Modeling For Fault Location in Distribution Systems With Distributed Generationcastilho22No ratings yet
- Application of The Fault Tree Analysis For Assessment of Power System ReliabilityDocument12 pagesApplication of The Fault Tree Analysis For Assessment of Power System ReliabilityReki Febrian100% (1)
- Applied Co-Simulation of Intelligent Power SystemsDocument28 pagesApplied Co-Simulation of Intelligent Power Systemsfredy52No ratings yet
- Power System Transient Stability ThesisDocument8 pagesPower System Transient Stability ThesisCollegeApplicationEssayHelpManchester100% (1)
- 10.1.1.139.6493 Co-SimulationDocument14 pages10.1.1.139.6493 Co-SimulationОлександр ДорошенкоNo ratings yet
- PHD Thesis Power System StabilityDocument4 pagesPHD Thesis Power System Stabilityafbtfcstf100% (2)
- Foreword For The Special Section On Analysis and Simulation of Very Large Power SystemsDocument3 pagesForeword For The Special Section On Analysis and Simulation of Very Large Power Systemsmirko.tNo ratings yet
- AnalysisComplexFaults 20090424 Web PDFDocument16 pagesAnalysisComplexFaults 20090424 Web PDFicovinyNo ratings yet
- TPEC 2023 Paper 126Document6 pagesTPEC 2023 Paper 126Sahil MehtaNo ratings yet
- Power System Static-State EstimationDocument6 pagesPower System Static-State EstimationPedro De Leon GuerraNo ratings yet
- Power System StabilityDocument9 pagesPower System StabilityMyScribdddNo ratings yet
- Risk Based TTC Evaluation by Probabilistic Method: K. Audomvongseree, and A. Yokoyama, Member, IEEEDocument6 pagesRisk Based TTC Evaluation by Probabilistic Method: K. Audomvongseree, and A. Yokoyama, Member, IEEEItalo ChiarellaNo ratings yet
- System Modeling and Its Effect On State Estimation in Unbalanced Low Voltage Networks in The Presence of Measurement ErrorsDocument6 pagesSystem Modeling and Its Effect On State Estimation in Unbalanced Low Voltage Networks in The Presence of Measurement ErrorstyaskartikaNo ratings yet
- b9 Research PaperDocument5 pagesb9 Research PaperKushagra BindraNo ratings yet
- General Description of Distribution SystemDocument3 pagesGeneral Description of Distribution SystemMadhumitha SelvarajNo ratings yet
- Distributed Algorithms For Transmission Power Control in Wireless Sensor NetworksDocument5 pagesDistributed Algorithms For Transmission Power Control in Wireless Sensor NetworksCHARALAMPOS CHRISTOFORIDISNo ratings yet
- Abstract: Complex Network Systems Have Been Extensively Used To Analyze NetworkDocument12 pagesAbstract: Complex Network Systems Have Been Extensively Used To Analyze NetworkRavindra JoshiNo ratings yet
- Distributed State Estimation of Multi-Region Power System Based On Consensus TheoryDocument16 pagesDistributed State Estimation of Multi-Region Power System Based On Consensus Theorysami_aldalahmehNo ratings yet
- ISO 14001:2015 Transition Presentation: Presented by Fredric LeungDocument26 pagesISO 14001:2015 Transition Presentation: Presented by Fredric LeungBiswadip BanerjeeNo ratings yet
- ITIL - Introducing Service Design PDFDocument17 pagesITIL - Introducing Service Design PDFKumar Soubhagya DuttaNo ratings yet
- HTML Basic LessonDocument8 pagesHTML Basic LessonR TECHNo ratings yet
- Creating NC FilesDocument8 pagesCreating NC FilesStelian ConstantinescuNo ratings yet
- C++ Vs Java - ComparativaDocument2 pagesC++ Vs Java - ComparativaJoaquín Schaffer0% (1)
- Step 1: Open Google: Developer Console and Signin With Your Gmail AccountDocument11 pagesStep 1: Open Google: Developer Console and Signin With Your Gmail Accountjohn mark laquipNo ratings yet
- GTD Basics PDFDocument60 pagesGTD Basics PDFRahul_Ravindra_2899100% (4)
- 01 OverviewDocument65 pages01 OverviewdqltakedaNo ratings yet
- How To Find The Overdue Jobs?Document12 pagesHow To Find The Overdue Jobs?Denizio CaldasNo ratings yet
- RWD Uperform 4.10.0 Managing Content PDFDocument373 pagesRWD Uperform 4.10.0 Managing Content PDFotracuentaaux9No ratings yet
- Excel QuizDocument24 pagesExcel QuizSoumitra ChakrabortyNo ratings yet
- Webgoat DeveloperWorkbookDocument279 pagesWebgoat DeveloperWorkbookEdison AcostaNo ratings yet
- NCERT Solutions For Class 12th Maths Chapter 3 - MatricesDocument72 pagesNCERT Solutions For Class 12th Maths Chapter 3 - Matricesdilip saxena0% (1)
- Optimal Product ProcessDocument51 pagesOptimal Product ProcessVan Gunxsword100% (5)
- Exemple Concours Master Finace d'Entreprise 2013-2014, Fsjes RABAT - منتدى كلية الحقوق أكادير - FSJES AGADIR FORUMDocument3 pagesExemple Concours Master Finace d'Entreprise 2013-2014, Fsjes RABAT - منتدى كلية الحقوق أكادير - FSJES AGADIR FORUMSoukaina MoumenNo ratings yet
- KUMARAPERUMAL CHIDAMBARAM Auditor CVDocument4 pagesKUMARAPERUMAL CHIDAMBARAM Auditor CVKumaraperumal ChidambaramNo ratings yet
- XPSWMM: Tutorial 9: DTM Example inDocument12 pagesXPSWMM: Tutorial 9: DTM Example inrimana2144No ratings yet
- Concepts of Nuclear Physics by B L Cohen 0070115567 PDFDocument5 pagesConcepts of Nuclear Physics by B L Cohen 0070115567 PDFVeerendra Viru100% (1)
- A. Multiple Choice Questions (80%)Document4 pagesA. Multiple Choice Questions (80%)George ChalhoubNo ratings yet
- CNN-based and DTW Features For Human Activity Recognition On Depth MapsDocument14 pagesCNN-based and DTW Features For Human Activity Recognition On Depth Mapsjacekt89No ratings yet
- Number SystemDocument6 pagesNumber SystemJoerel NicolasNo ratings yet
- CHEM 1100 HessLaw F11Document3 pagesCHEM 1100 HessLaw F11SeverianzNo ratings yet
- Crack Windows 2Document2 pagesCrack Windows 2studyuntildieNo ratings yet
- Colon Classification 6Document2 pagesColon Classification 6Monica FloresNo ratings yet
- SNMP Reference Guide For Idrac and Chassis Management ControllerDocument116 pagesSNMP Reference Guide For Idrac and Chassis Management ControllerandreoaNo ratings yet
- Introduction of CADDocument6 pagesIntroduction of CADKhengling Lim100% (1)
- Shower Spares & Parts ShoweringDocument1 pageShower Spares & Parts Showeringf9zvxkvw5mNo ratings yet
- AVEVA Mechanical Equipment InterfaceDocument2 pagesAVEVA Mechanical Equipment InterfaceaminNo ratings yet
- Programming in C For BCA BIT BEDocument0 pagesProgramming in C For BCA BIT BEwww.bhawesh.com.npNo ratings yet