Professional Documents
Culture Documents
'Y 'Y 'Y 'Y
'Y 'Y 'Y 'Y
Uploaded by
Eloiza PepitoOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
'Y 'Y 'Y 'Y
'Y 'Y 'Y 'Y
Uploaded by
Eloiza PepitoCopyright:
Available Formats
Threat control-Regulates network access, isolates infected systems, prevents intrusions, and protects assets by counteracting malicious traffic,
such as worms and viruses. Devices that provide threat control solutions are: Cisco ASA 5500 Series Adaptive Security Appliances
y y y y
Integrated Services Routers (ISR) Network Admission Control Cisco Security Agent for Desktops Cisco Intrusion Prevention Systems
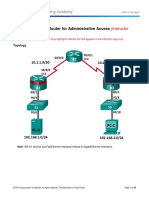
Most of the services listed in this section are usually not required. The table in the figure describes general vulnerable router services and lists best practices associated to those services. Turning off a network service on the router itself does not prevent it from supporting a network where that protocol is employed. For example, a network may require TFTP services to backup configuration files and IOS images. This service is typically provided by a dedicated TFTP server. In certain instances, a router could also be configured as a TFTP server. However, this is very unusual. Therefore, in most cases the TFTP service on the router should be disabled. In many cases, Cisco IOS software supports turning a service off entirely, or restricting access to particular network segments or sets of hosts. If a particular portion of a network needs a service but the rest does not, the restriction features should be employed to limit the scope of the service. Turning off an automatic network feature usually prevents a certain kind of network traffic from being processed by the router, or prevents it from traversing the router. For example, IP source routing is a little-used feature of IP that can be utilized in network attacks. Unless it is required for the network to operate, IP source routing should be disabled. Note: CDP is leveraged in some IP Phone implementations. This needs to be considered before broadly disabling the service. There are a variety of commands that are required to disable services. The show running-config output in the figure provides a sample configuration of various services which has been disabled. Services which should typically be disabled are listed below. These include: Small services such as echo, discard, and chargen - Use the no service tcp-small-servers or no service udp-small-servers command. y BOOTP - Use the no ip bootp server command.
y y y
Finger - Use the no service finger command. HTTP - Use the no ip http server command. SNMP - Use the no snmp-server command.
It is also important to disable services that allow certain packets to pass through the router, send special packets, or are used for remote router configuration. The corresponding commands to disable these services are:
y y y y
Cisco Discovery Protocol (CDP) - Use the no cdp run command. Remote configuration - Use the no service config command. Source routing - Use the no ip source-route command. Classless routing - Use the no ip classless command.
The interfaces on the router can be made more secure by using certain commands in interface configuration mode:
y y y
Unused interfaces - Use the shutdown command. No SMURF attacks - Use the no ip directed-broadcast command. Ad hoc routing - Use the no ip proxy-arp command.
SNMP, NTP, and DNS Vulnerabilities The methods for disabling or tuning the configurations for these services are beyond the scope of this course. These services are covered in the CCNP: ImplementingSecure Converged Wide-area Network course. The descriptions and guidelines to secure these services are listed below. SNMP SNMP is the standard Internet protocol for automated remote monitoring and administration. There are several different versions of SNMP with different security properties. Versions of SNMP prior to version 3 shuttle information in clear text. Normally, SNMP version 3 should be used. NTP Cisco routers and other hosts use NTP to keep their time-of-day clocks accurate. If possible, network administrators should configure all routers as part of an NTP hierarchy, which makes one router the master timer and provides its time to other routers on the network. If an NTP hierarchy is not available on the network, you should disable NTP. Disabling NTP on an interface does not prevent NTP messages from traversing the router. To reject
all
NTP
messages
at
particular
interface,
use
an
access
list.
DNS Cisco IOS software supports looking up hostnames with the Domain Name System(DNS). DNS provides the mapping between names, such as central.mydomain.com toIP addresses, such as 14.2.9.250. Unfortunately, the basic DNS protocol offers no authentication or integrity assurance. By default, name queries are sent to the broadcast address 255.255.255.255. If one or more name servers are available on the network, and it is desirable to use names in Cisco IOS commands, explicitly set the name server addresses using the global configuration command ip name-serveraddresses. Otherwise, turn off DNS name resolution with the command no ip domainlookup. It is also a good idea to give the router a name, using the command hostname. The name given to the router appears in the prompt.
You might also like
- 2.6.1.2 Lab - Securing The Router For Administrative Access (Filled)Document38 pages2.6.1.2 Lab - Securing The Router For Administrative Access (Filled)true0soul80% (5)
- Cisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3From EverandCisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3No ratings yet
- ISO27k Router Security Audit Checklist 1Document8 pagesISO27k Router Security Audit Checklist 1scribd_jrNo ratings yet
- 2.6.1.2 Lab - Securing The Router For Administrative AccessDocument54 pages2.6.1.2 Lab - Securing The Router For Administrative AccessDaniel Ergicho100% (1)
- ITsec Router Audit ChecklistDocument4 pagesITsec Router Audit ChecklistSuryakumar GubbalaNo ratings yet
- New Router Checklist PDFDocument15 pagesNew Router Checklist PDFJinto T.K.No ratings yet
- Router Technical Audit ChecklistDocument15 pagesRouter Technical Audit ChecklistJinto T.K.No ratings yet
- 1-Module 01 Basic & InterfaceDocument35 pages1-Module 01 Basic & InterfacevajragantaNo ratings yet
- Revision Notes CCNA 3 EasyDocument40 pagesRevision Notes CCNA 3 EasyNur Dinah YeeNo ratings yet
- Cisco Router Security: Principles and Practise: The Foundation of Network Security Is Router SecurityDocument28 pagesCisco Router Security: Principles and Practise: The Foundation of Network Security Is Router Securitykktamang09No ratings yet
- Cisco - Asegurando Router Old ServicesDocument5 pagesCisco - Asegurando Router Old ServicesFabian Molina AzocarNo ratings yet
- NXLD90 Router Security Configuration GuideDocument6 pagesNXLD90 Router Security Configuration GuideAbu FadilahNo ratings yet
- Module 1 - Basic Topology and Router Setup: The Following Will Be The Common Topology Used For The First Series of LabsDocument9 pagesModule 1 - Basic Topology and Router Setup: The Following Will Be The Common Topology Used For The First Series of LabskyawzinmonNo ratings yet
- CCNA 3 All ModulesDocument48 pagesCCNA 3 All ModulesFi3ta100% (1)
- It010 707 (Reference) Internetworking LabDocument109 pagesIt010 707 (Reference) Internetworking LabDivya K.SNo ratings yet
- Deny Any Packet From TheDocument8 pagesDeny Any Packet From Theiwc2008007No ratings yet
- M - BSM Basic Sys Manage XeDocument12 pagesM - BSM Basic Sys Manage XeGVNo ratings yet
- Ospf 3Document11 pagesOspf 3La PyaeNo ratings yet
- NXLD58 Securing Switch AccessDocument29 pagesNXLD58 Securing Switch AccessSai Kyaw HtikeNo ratings yet
- Cisco Routers and Switches: Phoenix Cisco User Group (PCUG)Document55 pagesCisco Routers and Switches: Phoenix Cisco User Group (PCUG)Denis ManicNo ratings yet
- Module 1 - Basic Topology and Router Setup: The Following Will Be The Common Topology Used For The First Series of LabsDocument9 pagesModule 1 - Basic Topology and Router Setup: The Following Will Be The Common Topology Used For The First Series of LabsHassan AwaisNo ratings yet
- Isp Workshop PDFDocument218 pagesIsp Workshop PDFSAPTARSHI GHOSHNo ratings yet
- Ccna Cheat Sheet New TopicsDocument3 pagesCcna Cheat Sheet New TopicsSteve Alain Onana Dang100% (1)
- Presentation ON Ccna: TRAINED BY - Kundan Singh (Aptron Solutions PVT LTD)Document36 pagesPresentation ON Ccna: TRAINED BY - Kundan Singh (Aptron Solutions PVT LTD)Akshay Mishra BhardwajNo ratings yet
- CNS Lab Manual 2019 Course - UpdatedDocument96 pagesCNS Lab Manual 2019 Course - Updatedswapnil khandareNo ratings yet
- ISIS QuestionDocument12 pagesISIS QuestionPrabin MaliNo ratings yet
- Cisco Basic SecurityDocument58 pagesCisco Basic SecurityPhuong PhamNo ratings yet
- Laporan Praktik Lab 2 - Securing The Router For Administrative Access - CompressedDocument57 pagesLaporan Praktik Lab 2 - Securing The Router For Administrative Access - CompressedRizky RismadhantiNo ratings yet
- TCP and UDP Small ServersDocument3 pagesTCP and UDP Small ServersLee KendrickNo ratings yet
- Ios Nat LBDocument7 pagesIos Nat LBJorge Mosquera RNo ratings yet
- Module 1 - Basic Topology, ISIS and iBGP: The Following Will Be The Common Topology Used For The First Series of LabsDocument14 pagesModule 1 - Basic Topology, ISIS and iBGP: The Following Will Be The Common Topology Used For The First Series of Labsmansour14No ratings yet
- 10.1.4-Packet-Tracer - Configure-Initial-Router-SettingsDocument5 pages10.1.4-Packet-Tracer - Configure-Initial-Router-SettingsPetru SpînuNo ratings yet
- 2.6.1.2 Lab - Securing The Router For Administrative Access PDFDocument38 pages2.6.1.2 Lab - Securing The Router For Administrative Access PDFAAANo ratings yet
- 10.2.3.6 Lab - Configuring Syslog and NTP PDFDocument9 pages10.2.3.6 Lab - Configuring Syslog and NTP PDFRubén San MartínNo ratings yet
- Lab - Securing The Router For Administrative Access: IntegrantesDocument59 pagesLab - Securing The Router For Administrative Access: IntegrantesAlex Fernando GarcesNo ratings yet
- Ipv6 Module 20 - Router SecurityDocument12 pagesIpv6 Module 20 - Router Securitycatalin ionNo ratings yet
- AutoSecure CiscoRouterDocument28 pagesAutoSecure CiscoRouterWaqas MoazzamNo ratings yet
- Redundant Backup ISP ASA 5500Document17 pagesRedundant Backup ISP ASA 5500Raj ShekarNo ratings yet
- Snort - Inline As A Solution: ProgrammingDocument11 pagesSnort - Inline As A Solution: Programming'Sami SneijderNo ratings yet
- ISO 27001 Router Security Audit Checklist: Yes No Router PolicyDocument14 pagesISO 27001 Router Security Audit Checklist: Yes No Router Policyrajesh35techieNo ratings yet
- Lab 5a - Configuring Syslog and NTP: TopologyDocument8 pagesLab 5a - Configuring Syslog and NTP: Topologydinooooo_No ratings yet
- ProjectDocument13 pagesProjectakhil krishnanNo ratings yet
- Cisco® Router Configuration & Troubleshooting - 3 - Initial Router SetupDocument10 pagesCisco® Router Configuration & Troubleshooting - 3 - Initial Router SetupDev VishwakarmaNo ratings yet
- 2.6.1.2 Lab - Securing The Router For Administrative Access - UnlockedDocument44 pages2.6.1.2 Lab - Securing The Router For Administrative Access - UnlockedAlonso Chi CitukNo ratings yet
- Como Habilitar Netbios en Routers CiscoDocument4 pagesComo Habilitar Netbios en Routers CiscocarlosNo ratings yet
- Top10 Cisco Ios CommandsDocument3 pagesTop10 Cisco Ios CommandsD Matthew KeltyNo ratings yet
- 2.5.1.1 Lab - Securing The Router For Administrative Access - InstructorDocument61 pages2.5.1.1 Lab - Securing The Router For Administrative Access - InstructorLupita VázquezNo ratings yet
- Cisco IOS Tips and TricksDocument16 pagesCisco IOS Tips and TricksChavara MatekweNo ratings yet
- Cisco ChecklistDocument6 pagesCisco ChecklistDema PermanaNo ratings yet
- Cisco IOS Security TemplateDocument10 pagesCisco IOS Security TemplateshankerunrNo ratings yet
- Cisco Router Configuration Tutorial PDFDocument8 pagesCisco Router Configuration Tutorial PDFHamami InkaZoNo ratings yet
- CCNA Cheat Sheet: Experts in NetworkingDocument8 pagesCCNA Cheat Sheet: Experts in NetworkingHeribertus BudhihartoNo ratings yet
- CCNA CommandsDocument12 pagesCCNA CommandsAnjanava KumarNo ratings yet
- Router Behind CM 19268Document5 pagesRouter Behind CM 19268Pablo Guerrero GuzmánNo ratings yet
- Basic ISDN Configuration: Document ID: 14221Document5 pagesBasic ISDN Configuration: Document ID: 14221Prem PankajNo ratings yet
- En NS2 ILM v20Document199 pagesEn NS2 ILM v20Elquia MadridNo ratings yet
- Sistema Operativo InternetworkDocument4 pagesSistema Operativo InternetworkRonny PeñaNo ratings yet
- Configure Admistrative RolesDocument20 pagesConfigure Admistrative RolesestebanNo ratings yet
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkFrom EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkNo ratings yet