Professional Documents
Culture Documents
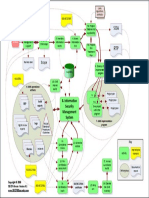
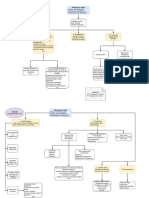
Iso 27001
Iso 27001
Uploaded by
nebojsamiOriginal Description:
Copyright
Available Formats
Share this document
Read this document in other languages
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Iso 27001
Iso 27001
Uploaded by
nebojsamiCopyright:
Available Formats
Implementing Information Security Based on ISO 27001 and ISO 27002
This interactive 2 day course provides an introduction to the ISO/IEC 27001:2005 and ISO/IEC 27002:2007 (formerly ISO/IEC 17799 / BS 7799) international standards for information security. The course presents a straightforward and logical approach to developing, implementing and maintaining your Information Security Management Process and Systems. The course guides its participants through the Information Security Process and provides detailed guidance on how to effectively design, plan and implement this process and the related Information Security Management Systems (ISMS). Additionally it provides practical direction to prepare for a security audit and to enforcing compliance. Who should attend? This course will be beneficial for anyone who is looking for the details of the ISO/IEC 27001:2005 and 27002:2007 standards, including: Staff responsible for Information Security Management or implementation of ISO/IEC 27001 and/or ISO 27002 Information Security Managers IT managers responsible for delivering or running critical business information systems IT consultants advising clients on security matters Information Service Provider (ISP) staff responsible for security issues. Security Managers, Auditors, Project Managers, Operations Managers and Business managers What You Will Learn This course will enable delegates to: Understand the requirements of the ISO/IEC 27001:2005 and ISO/IEC 27002 standards Practical techniques for designing and implementing an ISMS Detail explanations of the ISO/IEC 27001:2005 ISMS components and the improvement cycle Understand the necessary skills to design, implement, maintain and audit an effective ISMS Assess an organisations information security needs against ISO/IEC 27002:2007 and ISO/IEC 27001:2005 In addition the course will have hands-on activities in which delegates will have the opportunity to undertake practical exercises with the intention of formulating practical documents that can be used in their business, including: Information Security policy Identification of information assets and their value Determination of risk and impacts Identification of control objective and controls Risk Analysis and Risk Treatment Plan Statement of Applicability (SOA) Completion of ISMS documentation requirements Production of a ISMS Project Implementation Plan Learning Method This course is conducted as an instructor-led workshop and includes a combination of lectures and exercises. Each delegate will receive the book Implementing Information Security based on ISO 27001 & ISO 17799 (ISBN: 9789077212783), the course notes, and a certificate of attendance.
www.alctraining.com.au 1300 767 592 www.lucidit.com.au
Implementing Information Security Based on ISO 27001 and ISO 27002
Prerequisite A basic knowledge of information systems, security and management processes Course Fee $1,250 + gst In-House Training This course is available for private presentation, either on your own premises or 'off-site'. There are many advantages to in-house training. Please contact ALC for a quotation and to discuss your requirements. Telephone 1300 767 592 or email learn@alctraining.com.au
Course Structure The course will cover the following topics: 1. Information Security Introduction Introduction to Information Security Management (ISM) Information Security Focus ISM Benefits 2. Security Standards and Best Practices Introduction to Security Standards and Best Practices and their purpose: o ASCII 33 Ensures minimum standard for government ICT security o ISO 27001:2005 - Defines the ISMS requirements o ISO 27002 (ISO 17799:2005) - Defines a code of best practices for the management of information security o AS 8001:2003 - Control of fraud and corruption o AS/NZS 4360:2004 - Risk Management o SABSA "best practice" method for delivering information security solutions to enterprises o CobiT - Control Objectives for Information and related Technology o ITIL - The IT Infrastructure Library o SOX - Sarbanes-Oxley o Prince2 - PRojects IN Controlled Environments, v2 3. The ISO 27001 and 27002 Standards ISO 27000 series Overview ISO/IEC 27001 Overview ISO/IEC 27002 (ISO 17799:2005) Control Objectives and Controls Technology 4. Information Security Process Process approach Implementation of an ISMS The Plan Do Check Act Model 5. The 6 Steps of the Plan Phase: Scope Policy Assess Risk Treat Risk Control Objectives Statement of Applicability 6. Audit Readiness & Preparation The Security Audit Process Strategic, Tactical and Operational documents
www.alctraining.com.au 1300 767 592 www.lucidit.com.au
Implementing Information Security Based on ISO 27001 and ISO 27002
Reasons for Non-Implementation Audit Process 7. Enforcing Compliance Reasons for Enforcing Compliance Policy Compliance Reviews Policy Compliance Vs Vulnerability Assessments Survival Tactics 8. Organisational Change Challenge Service Culture Barriers Management Effort 9. Realising the Benefits IT Security Management Benefits Advantages of implementing ISO 27001 and 27002 Critical Success Factors
www.alctraining.com.au 1300 767 592
www.lucidit.com.au
You might also like
- Nine Steps to Success: An ISO27001:2013 Implementation OverviewFrom EverandNine Steps to Success: An ISO27001:2013 Implementation OverviewRating: 3 out of 5 stars3/5 (2)
- Amazon's Distribution StrategyDocument3 pagesAmazon's Distribution StrategyJaya Krishna Singu0% (1)
- Re Clarke Peter JDocument8 pagesRe Clarke Peter JParesh HiraniNo ratings yet
- QSA Main Student Study Guide 4.12Document21 pagesQSA Main Student Study Guide 4.12Jon GordonNo ratings yet
- ITSC Seminar - 27001 27002 Update Philip SyDocument30 pagesITSC Seminar - 27001 27002 Update Philip SySyed ZiaNo ratings yet
- ISO IEC 27001 Lead Auditor A Complete Guide - 2021 EditionFrom EverandISO IEC 27001 Lead Auditor A Complete Guide - 2021 EditionNo ratings yet
- Job Analysis, Job Design and Quality of Work LifeDocument14 pagesJob Analysis, Job Design and Quality of Work Lifes1103294475% (8)
- MF0002 Mergers Acquisition Model PaperDocument8 pagesMF0002 Mergers Acquisition Model PaperJhorapaata67% (3)
- Cobit and Iso 27001Document64 pagesCobit and Iso 27001Antonio ClimaNo ratings yet
- ISO IEC 27001 Lead AuditorDocument7 pagesISO IEC 27001 Lead AuditorDaniel Stuart0% (1)
- STAR Certification SecureCloud2014Document27 pagesSTAR Certification SecureCloud2014abcd100% (1)
- SGS KN ISOIEC 42001 Artificial Intelligence AI Management System Product Sheet ENDocument1 pageSGS KN ISOIEC 42001 Artificial Intelligence AI Management System Product Sheet ENJosue FamaNo ratings yet
- 915 Trust in AI Systems Oct 25 2022Document27 pages915 Trust in AI Systems Oct 25 2022multi mediaNo ratings yet
- Iso15408 2Document354 pagesIso15408 2Rowatinex RosNo ratings yet
- Part 3 Cybersecurity - Competency - Guide - Cyber Security Control PolicyDocument56 pagesPart 3 Cybersecurity - Competency - Guide - Cyber Security Control PolicyJason KingNo ratings yet
- Network Security, Report 01Document5 pagesNetwork Security, Report 01dara100% (1)
- Computer Security ActivitiesDocument29 pagesComputer Security ActivitiesPANKAJ MANJHINo ratings yet
- SGS KN AI Clearing FDIS ISOIEC 42001 Case Study FD ENDocument5 pagesSGS KN AI Clearing FDIS ISOIEC 42001 Case Study FD ENJosue FamaNo ratings yet
- ISO 20000 A Complete Guide - 2020 EditionFrom EverandISO 20000 A Complete Guide - 2020 EditionRating: 4 out of 5 stars4/5 (1)
- ISO 27001:2013 Gap AnalysisDocument8 pagesISO 27001:2013 Gap AnalysisTSANIA MAULIDIANo ratings yet
- Isca CH 4 BCP PMDocument18 pagesIsca CH 4 BCP PMPabitra Kumar PrustyNo ratings yet
- ISFDocument22 pagesISFLuis RoblesNo ratings yet
- Beta - OCEG.integrated Data Privacy Capability ModelDocument151 pagesBeta - OCEG.integrated Data Privacy Capability ModelAtifNo ratings yet
- VI-404576-TM-1 Cyber Essentials Why Your Organisation Should Get Badged PDFDocument20 pagesVI-404576-TM-1 Cyber Essentials Why Your Organisation Should Get Badged PDFRubab IqbalNo ratings yet
- Firewall Audit Check ListDocument7 pagesFirewall Audit Check ListIsaiahNo ratings yet
- CIS Controls SANS Poster 2022 4Document2 pagesCIS Controls SANS Poster 2022 4Pablo Umaña CamposNo ratings yet
- CISA Study Notes - 27th August 2022Document3 pagesCISA Study Notes - 27th August 2022Chitij ChauhanNo ratings yet
- Chapter 7Document26 pagesChapter 7Fazal KarimNo ratings yet
- SS IEC 62443-3-3-2018 PreviewDocument19 pagesSS IEC 62443-3-3-2018 PreviewTrường NguyễnNo ratings yet
- CSA Framework Policies Control Proc + Chpt11Document44 pagesCSA Framework Policies Control Proc + Chpt11RammyBrad100% (1)
- PCI QSA Training Course DescriptionDocument2 pagesPCI QSA Training Course Descriptionr4mbo78No ratings yet
- Classification of Security Operations CenterDocument7 pagesClassification of Security Operations CenterTulasidharan MudaliarNo ratings yet
- Cloud Security Guide For SMEsDocument50 pagesCloud Security Guide For SMEsaleraniNo ratings yet
- ISO27k ISMS Implementation and Certification Process 4v1 PDFDocument1 pageISO27k ISMS Implementation and Certification Process 4v1 PDFJMNAYAGAMNo ratings yet
- CCM and STAR ProgramDocument40 pagesCCM and STAR ProgramjeNo ratings yet
- ISO 20000 Version 2018 Vs 2011Document9 pagesISO 20000 Version 2018 Vs 2011dibiemNo ratings yet
- ISC - Actualtests.cissp ISSAP.v2015!03!13.by - Adella.237qDocument68 pagesISC - Actualtests.cissp ISSAP.v2015!03!13.by - Adella.237qdeewanandNo ratings yet
- KnowYourBroadband AIRTELDocument15 pagesKnowYourBroadband AIRTELRohit AgarwalNo ratings yet
- CRISC BrochureDocument2 pagesCRISC BrochureSpipparisNo ratings yet
- Certified ISO 27005 Risk Manager With OctaveDocument2 pagesCertified ISO 27005 Risk Manager With OctavetestNo ratings yet
- WP 62443 Compliance 051120 1Document7 pagesWP 62443 Compliance 051120 1이창선No ratings yet
- Sox Octave FinalDocument11 pagesSox Octave FinalErick MorenoNo ratings yet
- 82 Guidelines To Cyber Security With Iso 27032Document4 pages82 Guidelines To Cyber Security With Iso 27032Valamunis DomingoNo ratings yet
- CSMS Solutions Brief v4Document2 pagesCSMS Solutions Brief v4Ehsan ArbabtaftiNo ratings yet
- Sample Technical Document (Brochure)Document4 pagesSample Technical Document (Brochure)Saleem UddinNo ratings yet
- Iso - Iec 20000Document22 pagesIso - Iec 20000Vincenzo OstoniNo ratings yet
- Raghavender - SR Security - GRC ConsultantDocument8 pagesRaghavender - SR Security - GRC ConsultantraghuNo ratings yet
- Assignment No 5 Vulnerability ManagementDocument19 pagesAssignment No 5 Vulnerability ManagementJusil T. GaiteNo ratings yet
- IT Security Management - IsMSDocument53 pagesIT Security Management - IsMSRavi Raman100% (1)
- Emcs Csa CCMDocument23 pagesEmcs Csa CCMNoki ChannelNo ratings yet
- Certified ISO 20000 Lead Auditor-Two PageDocument2 pagesCertified ISO 20000 Lead Auditor-Two PagePECBCERTIFICATIONNo ratings yet
- CMMI CP Model Development ApproachDocument15 pagesCMMI CP Model Development ApproachMarco Antonio AgneseNo ratings yet
- IRCA Technical Review Briefing Note ISO 27001 PDFDocument16 pagesIRCA Technical Review Briefing Note ISO 27001 PDFtstehNo ratings yet
- Production Control Group Copy The Source Program To Production LibrariesDocument7 pagesProduction Control Group Copy The Source Program To Production LibrariesrushicNo ratings yet
- Qualifications ISO27001Document11 pagesQualifications ISO27001ricardo2020No ratings yet
- Applying ISO 27000Document16 pagesApplying ISO 27000blackbeast8100% (1)
- Secure Coding StandardDocument4 pagesSecure Coding StandardLayer8 IOTNo ratings yet
- SSPA Program Guide v8 - en-US PDFDocument19 pagesSSPA Program Guide v8 - en-US PDFBrunoNo ratings yet
- ISOIEC 27018 Compliance BackgrounderDocument2 pagesISOIEC 27018 Compliance BackgrounderSiderevs_NvncivsNo ratings yet
- CISM BrochureDocument2 pagesCISM BrochurevihitvasaniNo ratings yet
- ISO27k Standards ListingDocument6 pagesISO27k Standards ListingTikCGNo ratings yet
- Large Scale RetailingDocument3 pagesLarge Scale Retailingscb_bankersNo ratings yet
- Quiz AkbiDocument2 pagesQuiz AkbiDHEASITANo ratings yet
- (HBR - 201007-08) The Execution Trap. (Cover Story)Document2 pages(HBR - 201007-08) The Execution Trap. (Cover Story)ChangKwon ChungNo ratings yet
- CompareContrast - TPS Vs MIS Vs DSSDocument2 pagesCompareContrast - TPS Vs MIS Vs DSSethan71% (7)
- Essential Guide To The: How To Build, Implement, and Demonstrate CCPA ComplianceDocument25 pagesEssential Guide To The: How To Build, Implement, and Demonstrate CCPA ComplianceLinda BrinsfieldNo ratings yet
- Certification OrganismsDocument2 pagesCertification Organismsfrabe90No ratings yet
- Guimaras State College Graduate SchoolDocument4 pagesGuimaras State College Graduate SchoolRhoda Mae DelaCruz YpulongNo ratings yet
- Human Resource Management Review: David G. Collings, Hugh Scullion, Vlad VaimanDocument3 pagesHuman Resource Management Review: David G. Collings, Hugh Scullion, Vlad VaimansujitsekharmoharanaigitNo ratings yet
- Smart Accounting Chap 8Document8 pagesSmart Accounting Chap 8Pereyanka RajeswaranNo ratings yet
- Relevant Cost For Decission MakingDocument17 pagesRelevant Cost For Decission MakingMichelle Pratiwi TjioeNo ratings yet
- Incident Response NotesDocument36 pagesIncident Response NotesChristopher C. ChengNo ratings yet
- Submitted To: Raihan Sharif (Rsh3) : Operations Management Mgt314 Section: 14 Summer-2019Document16 pagesSubmitted To: Raihan Sharif (Rsh3) : Operations Management Mgt314 Section: 14 Summer-2019Jarin Tasnim LiraNo ratings yet
- Human Resource Development Review-2013-Alagaraja-117-43 PDFDocument28 pagesHuman Resource Development Review-2013-Alagaraja-117-43 PDFJoe HungNo ratings yet
- Modern Auditing: Modern AuditingDocument30 pagesModern Auditing: Modern AuditingLarasma Mutiara PutriNo ratings yet
- MMFIDocument3 pagesMMFImayoorNo ratings yet
- Original Management Accounting Information For Creating and Managing Value 8Th Edition Full ChapterDocument41 pagesOriginal Management Accounting Information For Creating and Managing Value 8Th Edition Full Chapterantonio.cummins133100% (27)
- Strategic Foresight PlatformDocument575 pagesStrategic Foresight Platformtestato123No ratings yet
- QM-001 QMS-Quality ManualDocument13 pagesQM-001 QMS-Quality ManualFERNANDO MORANTESNo ratings yet
- AssignmentDocument7 pagesAssignmentmian577938No ratings yet
- Planning An Audit ISA 300: EP: Engagement Partner ET: Engagement TeamDocument2 pagesPlanning An Audit ISA 300: EP: Engagement Partner ET: Engagement TeamMuhammad AslamNo ratings yet
- P6F 1 2 SGDocument17 pagesP6F 1 2 SGLuis Mario CarvajalNo ratings yet
- VP Director Communications PR in Dallas FT Worth TX Resume Cynthia Northrop-WhiteDocument4 pagesVP Director Communications PR in Dallas FT Worth TX Resume Cynthia Northrop-WhiteCynthiaNorthropWhiteNo ratings yet
- Assignment On SWOT Analysis, BCG Matrix, and Porter's Five Forces Model Analysis: A Case Study On Agora LTDDocument10 pagesAssignment On SWOT Analysis, BCG Matrix, and Porter's Five Forces Model Analysis: A Case Study On Agora LTDHaidar Jun ChowdhuryNo ratings yet
- Management of Human Resources The Essentials Canadian 5Th Edition Dessler Solutions Manual Full Chapter PDFDocument38 pagesManagement of Human Resources The Essentials Canadian 5Th Edition Dessler Solutions Manual Full Chapter PDFJoshuaAndersonwpdr100% (13)
- Ideas Are Free Alan G Robinson Dean M Schroeder Business SummaryDocument10 pagesIdeas Are Free Alan G Robinson Dean M Schroeder Business SummarybhailogNo ratings yet
- Assessing Employee Productivity (Master's) - HMK1000.1Document10 pagesAssessing Employee Productivity (Master's) - HMK1000.1kmp pssrNo ratings yet