Professional Documents
Culture Documents
Network Security Protocols
Network Security Protocols
Uploaded by
sandeepgupta0 ratings0% found this document useful (0 votes)
15 views4 pagesNetwork security protocols secure data transmission over networks through various authentication, encryption, and integrity techniques. Popular protocols include IPSec, SSH, HTTPS, and Kerberos. IPSec uses the Internet Key Exchange protocol to dynamically associate cryptographic keys for authentication and encryption between two entities. SSH allows secure remote command line login and task execution, incorporating FTP functionality. HTTPS establishes an encrypted link using TLS to securely transfer data from a browser to a web server. Kerberos provides strong authentication for client-server applications using secret-key cryptography across an insecure network.
Original Description:
ppt ecmc
Original Title
ECMC_PPT
Copyright
© © All Rights Reserved
Available Formats
PPTX, PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentNetwork security protocols secure data transmission over networks through various authentication, encryption, and integrity techniques. Popular protocols include IPSec, SSH, HTTPS, and Kerberos. IPSec uses the Internet Key Exchange protocol to dynamically associate cryptographic keys for authentication and encryption between two entities. SSH allows secure remote command line login and task execution, incorporating FTP functionality. HTTPS establishes an encrypted link using TLS to securely transfer data from a browser to a web server. Kerberos provides strong authentication for client-server applications using secret-key cryptography across an insecure network.
Copyright:
© All Rights Reserved
Available Formats
Download as PPTX, PDF, TXT or read online from Scribd
Download as pptx, pdf, or txt
0 ratings0% found this document useful (0 votes)
15 views4 pagesNetwork Security Protocols
Network Security Protocols
Uploaded by
sandeepguptaNetwork security protocols secure data transmission over networks through various authentication, encryption, and integrity techniques. Popular protocols include IPSec, SSH, HTTPS, and Kerberos. IPSec uses the Internet Key Exchange protocol to dynamically associate cryptographic keys for authentication and encryption between two entities. SSH allows secure remote command line login and task execution, incorporating FTP functionality. HTTPS establishes an encrypted link using TLS to securely transfer data from a browser to a web server. Kerberos provides strong authentication for client-server applications using secret-key cryptography across an insecure network.
Copyright:
© All Rights Reserved
Available Formats
Download as PPTX, PDF, TXT or read online from Scribd
Download as pptx, pdf, or txt
You are on page 1of 4
Network Security Protocols
There are various categories of protocols like routing protocols,
mail transferring protocols, remote communication protocols,
and many more. Network security protocols are one such
category that makes sure that the security and integrity of the
data are preserved over a network. Various methodologies,
techniques, and processes are involved in these protocols to
secure the network data from any illegitimate attempt in
reviewing or extracting the actual content of data.
Internet Security Threats
Internet security threats impact the network, data security and other
internet connected systems. Cyber criminals have evolved several
techniques to threat privacy and integrity of bank accounts, businesses,
and organizations.
Following are some of the internet security threats:
• Mobile worms
• Malware
• PC and Mobile ransomware
• Large scale attacks like Stuxnet that attempts to destroy infrastructure.
• Hacking as a Service
• Spam
• Phishing
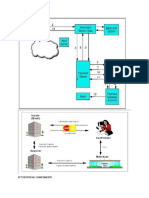
Some Network Security Protocols
Here are the lists of some popular network security protocols:
• IPSec protocol is classified by the IETF IPSec Work Group,
which offers authentication of data, integrity, as well as
privacy between 2 entities. Manual or dynamic association of
management in cryptographic keys is done with the help of an
IETF-specific key managing protocol named Internet Key
Exchange (IKE).
• Secure Shell (SSH) was invented in the year 1995, which is a
cryptographic network security protocol used for securing
data communication over a network. It permits the
command-line to login remotely as well as the execution of
specific tasks remotely. Various functionalities of FTP are
incorporated in SSH. SSH-1 and SSH-2 are the latest of its kind.
• HyperText Transfer Protocol Secure (HTTPS) is a secured
protocol used to secure data communication among two or
more systems. It set up an encrypted link with the help of
Secure Socket Layer (SSL), now known as Transport Layer
Security (TLS). Since data transferred using HTTPS is in the
encrypted format, so, it stops cybercriminals from
interpretation as well as alteration of data throughout the
transfer from browser to the webserver.
• Kerberos is another network validation protocol that was
intended for providing a strong authentication between
client-server applications with the help of secret-key
cryptography. According to the Kerberos network validation
protocol, all of its services and workplaces correspond to
an insecure network, which makes it more secure and
responsible.
You might also like
- 0Document110 pages0Index Peninsula100% (1)
- IntroductionDocument3 pagesIntroductionELDER LAGGAHNo ratings yet
- InternetsecurityprotocolsDocument30 pagesInternetsecurityprotocolsAvi SirikondaNo ratings yet
- Networks and Computer SecurityDocument4 pagesNetworks and Computer SecurityAsfund AusafNo ratings yet
- VPN Security ProtocolsDocument7 pagesVPN Security Protocolsmhds0hail0705No ratings yet
- Week 10Document30 pagesWeek 10aliya ajmalNo ratings yet
- SecurityDocument1 pageSecurityVetha moorthiNo ratings yet
- Secure Networking 101 MACsec, IPsec, and SSL BasicsDocument10 pagesSecure Networking 101 MACsec, IPsec, and SSL BasicsazertyNo ratings yet
- Safety and Security - SummaryDocument7 pagesSafety and Security - SummaryReda Zuhair AlQasimNo ratings yet
- Unit 6Document37 pagesUnit 6Remadan MohammedNo ratings yet
- Unit-6 Network Security and Public Key InfrastructureDocument36 pagesUnit-6 Network Security and Public Key Infrastructureshrestharojesh34No ratings yet
- Module - 1 Notes: Transport Level Security: Web Security Considerations, Secure Sockets Layer, TransportDocument45 pagesModule - 1 Notes: Transport Level Security: Web Security Considerations, Secure Sockets Layer, Transportrushil prasadNo ratings yet
- Computer Networks - Chapter 8Document9 pagesComputer Networks - Chapter 8ninebo5075No ratings yet
- Cryptography MaterialDocument46 pagesCryptography Materialmrsuhailv3No ratings yet
- SSL TlsDocument22 pagesSSL Tlsvice pyNo ratings yet
- Submitted By: Guidence ofDocument16 pagesSubmitted By: Guidence ofAnkit PandeyNo ratings yet
- Security in e - CommerceDocument4 pagesSecurity in e - CommerceAlex T BinoyNo ratings yet
- Cs707 Current Past Viva Solved Questions1Document4 pagesCs707 Current Past Viva Solved Questions1Zahid Gulzar100% (1)
- Vulnerabilities of The SSL Tls ProtocolDocument12 pagesVulnerabilities of The SSL Tls ProtocolManish AgarwalNo ratings yet
- Information Security LectureDocument5 pagesInformation Security LectureIsrafil TagulaoNo ratings yet
- Information Security Unit3Document6 pagesInformation Security Unit3anushk jainNo ratings yet
- FINAL TERM Topic Understanding Cybersecurity. BSA - BSMADocument7 pagesFINAL TERM Topic Understanding Cybersecurity. BSA - BSMAynoxtaikoNo ratings yet
- Network Security and EcommerceDocument49 pagesNetwork Security and EcommerceElisha NdhlovuNo ratings yet
- Ias 1 Midterm 2 ReyesDocument1 pageIas 1 Midterm 2 Reyescodclips0503No ratings yet
- Web Security Unit 6 Notes PDFDocument24 pagesWeb Security Unit 6 Notes PDFMohd FareeduddinNo ratings yet
- Transport Layer Security: Presented by Abhiram SahuDocument19 pagesTransport Layer Security: Presented by Abhiram SahuAbhiram SahuNo ratings yet
- Data Protection TechniquesDocument4 pagesData Protection Techniquesgayathri777No ratings yet
- Unit 5 Transport Level SecurityDocument81 pagesUnit 5 Transport Level SecurityBharath Kumar T VNo ratings yet
- ShibdasChakrabortyDocument10 pagesShibdasChakrabortyshibdasc339No ratings yet
- NSC Unit - 3 - 221210 - 134942Document29 pagesNSC Unit - 3 - 221210 - 134942SurenderNo ratings yet
- Security in E-CommerceDocument29 pagesSecurity in E-CommerceAlex T BinoyNo ratings yet
- Internet Security Is A Branch ofDocument7 pagesInternet Security Is A Branch ofsweety0410No ratings yet
- Itlbul2010 02Document7 pagesItlbul2010 02jldtecnoNo ratings yet
- Real-World Security Protocols: Department of Information TechnologyDocument33 pagesReal-World Security Protocols: Department of Information TechnologyAytenew DagneNo ratings yet
- Chapter 17Document32 pagesChapter 17pravin_renold7435No ratings yet
- Sockets Layer (SSL) and The Follow-On (Subsequent) Internet Standard ofDocument8 pagesSockets Layer (SSL) and The Follow-On (Subsequent) Internet Standard ofFazeelur RahmanNo ratings yet
- Computer Security (Chapter-4)Document28 pagesComputer Security (Chapter-4)Salih AkadarNo ratings yet
- Internet & Network Protocols & TypesDocument5 pagesInternet & Network Protocols & Typesbiswajitmohanty8260No ratings yet
- 4 Communication ProtocolDocument14 pages4 Communication ProtocolMay MyatNo ratings yet
- Introduction To WWWDocument76 pagesIntroduction To WWWArman KoriNo ratings yet
- VTU Network and Cyber Security Module-1 (15ec835, 17ec835)Document51 pagesVTU Network and Cyber Security Module-1 (15ec835, 17ec835)jayanthdwijesh h p100% (2)
- CSC 411 - Computing Systems Security Lesson 8 (2022)Document48 pagesCSC 411 - Computing Systems Security Lesson 8 (2022)freddymickdad413No ratings yet
- Ns 6Document35 pagesNs 6Harsha GangwaniNo ratings yet
- DCOM 258 Lab 14 PKI & Encryption ProtocolsDocument4 pagesDCOM 258 Lab 14 PKI & Encryption ProtocolsShaamim U AhmedNo ratings yet
- Unit-1 WASDocument3 pagesUnit-1 WASMohamed ShaaheenNo ratings yet
- UntitledDocument13 pagesUntitledBhumika MhatreNo ratings yet
- DSheet XOS 15.3Document25 pagesDSheet XOS 15.3fedde7882No ratings yet
- Chapter Two Fundamental of IS Web Services Security (WS Security)Document7 pagesChapter Two Fundamental of IS Web Services Security (WS Security)Getnete degemuNo ratings yet
- Presented By: Anurag Roll No:-1703233 Topic: Network SecurityDocument28 pagesPresented By: Anurag Roll No:-1703233 Topic: Network SecurityAnurag GuptaNo ratings yet
- Module 4 - Reading9 - InternetSecurityDocument11 pagesModule 4 - Reading9 - InternetSecurityChristopher AdvinculaNo ratings yet
- Internet SecurityDocument18 pagesInternet SecurityJatin JainNo ratings yet
- SSL and TlsDocument16 pagesSSL and Tlsveeravan2001No ratings yet
- TITLE - 2020-ODVA-Conference - CIP - Security - and - IEC - 62443 - Visoky - Wiberg - FinalDocument20 pagesTITLE - 2020-ODVA-Conference - CIP - Security - and - IEC - 62443 - Visoky - Wiberg - FinalShan ChokshiNo ratings yet
- Application Layer: Network SecurityDocument16 pagesApplication Layer: Network SecuritySunanda BansalNo ratings yet
- Secure Communication Channels: Secure Sockets Layer (SSL)Document5 pagesSecure Communication Channels: Secure Sockets Layer (SSL)Mani ShankarNo ratings yet
- Student Activity 1.3 Key: Internet Security: Ecurity UndamentalsDocument2 pagesStudent Activity 1.3 Key: Internet Security: Ecurity UndamentalsFmunoz MunozNo ratings yet
- Security: Abenoja, Michael Joseph B Campos, Jennylyn T Dugenia, Marrieda CDocument19 pagesSecurity: Abenoja, Michael Joseph B Campos, Jennylyn T Dugenia, Marrieda CJenny AndresNo ratings yet
- IPSECDocument23 pagesIPSECAkhilendraNo ratings yet
- Edexcel IAL IT Network NoteDocument4 pagesEdexcel IAL IT Network NoteDix BrosNo ratings yet
- Hacking Network Protocols: Unlocking the Secrets of Network Protocol AnalysisFrom EverandHacking Network Protocols: Unlocking the Secrets of Network Protocol AnalysisNo ratings yet
- Vineet MoocDocument20 pagesVineet MoocRobin HoodNo ratings yet
- Let'S Discuss Security !!: Louma Makkouk, Cybersecurity. Omar Rajab, CybersecurityDocument24 pagesLet'S Discuss Security !!: Louma Makkouk, Cybersecurity. Omar Rajab, Cybersecurityomar rajabNo ratings yet
- GDPR Top Tips - Dos and Don'ts: Today's TrainerDocument20 pagesGDPR Top Tips - Dos and Don'ts: Today's TrainerTom Nall100% (1)
- SSH Key Pair Generation v2Document7 pagesSSH Key Pair Generation v2IsaiSin20No ratings yet
- Cryptography & Information SecurityDocument7 pagesCryptography & Information SecurityragunathrevNo ratings yet
- wPKI Specification: 1 ScopeDocument5 pageswPKI Specification: 1 ScopeRadoslav PetkovićNo ratings yet
- Abstract On Network Security and CryptographyDocument13 pagesAbstract On Network Security and Cryptographytharun89% (9)
- Find Us On Tor Onionspace: Onion V3:: Because Ignorance Is BlissDocument6 pagesFind Us On Tor Onionspace: Onion V3:: Because Ignorance Is BlissMarlonNo ratings yet
- Vikram Andem RSA ConferenceDocument4 pagesVikram Andem RSA ConferenceJim GaricaNo ratings yet
- Sandblast Battle CardDocument3 pagesSandblast Battle CardLeonardo PereiraNo ratings yet
- Results For "Ramesh and Gargi": DocumentsDocument12 pagesResults For "Ramesh and Gargi": Documentscikeron503No ratings yet
- Domain Blacklist AntispamDocument53 pagesDomain Blacklist AntispamDiana DeseneazaFrumosNo ratings yet
- Security in Sprin-WsDocument20 pagesSecurity in Sprin-Wsmanu1212No ratings yet
- Middlesea Assist Ltd. - Contact, Malta's Provider of Roadside Breakdown, Home Assistance and Travel ServicesDocument1 pageMiddlesea Assist Ltd. - Contact, Malta's Provider of Roadside Breakdown, Home Assistance and Travel ServicesCarm VassalloNo ratings yet
- Hybrid CryptographDocument8 pagesHybrid CryptographCao ThủNo ratings yet
- HTTPS Setup GuideDocument9 pagesHTTPS Setup GuideZhang DanyangNo ratings yet
- Session 1 2 Blockchain v2.16Document204 pagesSession 1 2 Blockchain v2.16face2faceNo ratings yet
- Documents and E-Books PDFDocument4 pagesDocuments and E-Books PDFCarlos NavarroNo ratings yet
- Data Security PowerpointDocument25 pagesData Security Powerpointleanna hoyteNo ratings yet
- Authorization TechniquesDocument20 pagesAuthorization TechniquesRemial BusaNo ratings yet
- Top 10 Cyber Threats To Small Businesses.Document8 pagesTop 10 Cyber Threats To Small Businesses.infosectrain04No ratings yet
- TLS HandshakeDocument7 pagesTLS Handshakeinception.me5No ratings yet
- NIS - Class - Test - II - QB ANSWERS PDFDocument6 pagesNIS - Class - Test - II - QB ANSWERS PDFViveka NaikNo ratings yet
- Adobe Scan Nov 03, 2023Document1 pageAdobe Scan Nov 03, 20231729rmsanandapNo ratings yet
- IS3220 Lab 8Document6 pagesIS3220 Lab 8Damon MrFixit BakerNo ratings yet
- CybersecurityDocument28 pagesCybersecurityJoey Joseph Villota100% (2)
- Chapter Seven: Key ManagementDocument33 pagesChapter Seven: Key ManagementSumit Kumar DamNo ratings yet
- Testmayor Exam 210-260 Dumps PDFDocument13 pagesTestmayor Exam 210-260 Dumps PDFAmmyNo ratings yet
- Digital SignatureDocument17 pagesDigital SignatureSanmita NepalNo ratings yet