Professional Documents
Culture Documents
0 ratings0% found this document useful (0 votes)
57 viewsUDP Principles (Chapter 24) (User Datagram Protocol) : FALL 2005 Csi 4118 - University of Ottawa 1
UDP Principles (Chapter 24) (User Datagram Protocol) : FALL 2005 Csi 4118 - University of Ottawa 1
Uploaded by
Murtaza VasanwalaUDP is a connectionless transport layer protocol that provides fast, unreliable datagram delivery. It uses port numbers to identify applications and delivers individual messages without establishing connections. Well-known ports are used for common applications like DNS, SNMP, and DHCP, while dynamic ports above 49151 can be used for any purpose. Checksums are optional for error detection.
Copyright:
© All Rights Reserved
Available Formats
Download as PPT, PDF, TXT or read online from Scribd
You might also like
- Report On UdpDocument14 pagesReport On UdpSagar GaddamNo ratings yet
- TCP-IP Model in Data Communication and NetworkingDocument6 pagesTCP-IP Model in Data Communication and NetworkingAJER JOURNALNo ratings yet
- 15MA305-Statistics For Information Technology: Dr. S. AthithanDocument18 pages15MA305-Statistics For Information Technology: Dr. S. AthithanMurtaza VasanwalaNo ratings yet
- Ass. 1Document3 pagesAss. 1danilo sugot100% (1)
- MC - Press Iseries - And.as.400.java - At.work - CHMDocument656 pagesMC - Press Iseries - And.as.400.java - At.work - CHMcomputer_ebookNo ratings yet
- Bot Service DocumentatioDocument271 pagesBot Service DocumentatioLaurentiuStanciuNo ratings yet
- Liftmaster MYQPCK ManualDocument8 pagesLiftmaster MYQPCK Manualsharklaser69No ratings yet
- CS8581-Networks Lab Manual (2020-2024)Document50 pagesCS8581-Networks Lab Manual (2020-2024)john wickNo ratings yet
- CHAPTER 04 (Network)Document40 pagesCHAPTER 04 (Network)Mihirete BantegegnNo ratings yet
- Unit-5 NotesDocument45 pagesUnit-5 NotesMOGILIPURI KEERTHINo ratings yet
- Network Programming NotesDocument138 pagesNetwork Programming NotesLaxman YadavNo ratings yet
- UDPDocument7 pagesUDPMit Thakore100% (1)
- Lesson 3Document35 pagesLesson 3Bhon-Bhon AgcaoiliNo ratings yet
- AssgB9 - UDP SocketDocument5 pagesAssgB9 - UDP Socketvaibhav patilNo ratings yet
- MC0087Article On UDP PDFDocument1 pageMC0087Article On UDP PDFPramod ChakravarthyNo ratings yet
- 2 6-UdpDocument27 pages2 6-Udpedemo6870No ratings yet
- Chapter OneDocument13 pagesChapter OnemenbereNo ratings yet
- Research Work It301Document9 pagesResearch Work It301Jr Gadiano GallardoNo ratings yet
- Hct6000 Tcpip OptionDocument14 pagesHct6000 Tcpip OptionGerman DfrNo ratings yet
- Computer Networks I: Dr:-Rania Abul SeoudDocument37 pagesComputer Networks I: Dr:-Rania Abul SeoudMony JosephNo ratings yet
- Npms Unit-1Document36 pagesNpms Unit-1Karthik RaviNo ratings yet
- Unit 1 NotesDocument24 pagesUnit 1 Notessonal rajNo ratings yet
- User Datagram Protocol (UDP)Document9 pagesUser Datagram Protocol (UDP)frtessNo ratings yet
- L2 SocketsDocument31 pagesL2 SocketsCedric TangNo ratings yet
- 7TCPIPDocument40 pages7TCPIPgokul adethyaNo ratings yet
- Comptia-Network Study GuideDocument36 pagesComptia-Network Study GuideJonathan Velez Velazquez100% (3)
- DCN Unit-4 SaqDocument5 pagesDCN Unit-4 Saqsravan kumarNo ratings yet
- Well Known Ports (Numbers 0 To 1023) - These Numbers Are ReservedDocument1 pageWell Known Ports (Numbers 0 To 1023) - These Numbers Are ReservedNicoleta NovacNo ratings yet
- ChapterDocument57 pagesChapterYomif NiguseNo ratings yet
- Internet and Protocol-3Document16 pagesInternet and Protocol-3Par VeenNo ratings yet
- Computer Network - TCP - IP ModelDocument5 pagesComputer Network - TCP - IP ModelAMARJEET KUMARNo ratings yet
- PR Lab5 Vlas MihaiDocument17 pagesPR Lab5 Vlas MihaiAlexey DarievNo ratings yet
- Lecture 2 Introduction To Client Server ComputingDocument19 pagesLecture 2 Introduction To Client Server ComputingericNo ratings yet
- TCPIP ModelDocument9 pagesTCPIP Modelroysayanccp05No ratings yet
- Network Programming & ManagementDocument27 pagesNetwork Programming & ManagementmeerasasiNo ratings yet
- TCP IP ModelDocument8 pagesTCP IP Modelguptariya0111No ratings yet
- Ôn Tập GKDocument4 pagesÔn Tập GKHoàng DươngNo ratings yet
- Prog Linux Sockets 456Document19 pagesProg Linux Sockets 456mushtaq khan niaziNo ratings yet
- Introduction To TCPDocument1 pageIntroduction To TCPtinajose1211No ratings yet
- CS SreyashDocument10 pagesCS Sreyashtacac87741No ratings yet
- Network Programming and Java SocketsDocument27 pagesNetwork Programming and Java SocketsIsmail Adha KesumaNo ratings yet
- Network PROTOCOLSDocument11 pagesNetwork PROTOCOLSRose of sharonNo ratings yet
- Unit 4 Lec1Document18 pagesUnit 4 Lec1SangetaNo ratings yet
- Unit 4Document10 pagesUnit 4Nandkumar KhachaneNo ratings yet
- Network ProtocolsDocument16 pagesNetwork Protocolshassanabid15No ratings yet
- 3.2 TCPIP ModelDocument5 pages3.2 TCPIP ModelSuyasha JainNo ratings yet
- Chapter 7Document41 pagesChapter 7Muqeemuddin SyedNo ratings yet
- TCP IP Protocol Explanation 1 (03.01.2024)Document5 pagesTCP IP Protocol Explanation 1 (03.01.2024)aloishp36No ratings yet
- Client-Server ComputingDocument19 pagesClient-Server ComputingHISNONYMOUSNo ratings yet
- Ex No: 9 Study of UDP PerformanceDocument33 pagesEx No: 9 Study of UDP Performancenganeshv1988No ratings yet
- Programming With TCP/IP - Best PracticesDocument31 pagesProgramming With TCP/IP - Best PracticesmrwanzNo ratings yet
- NPM Unit 1 NotesDocument23 pagesNPM Unit 1 NotesVinoth ShankarNo ratings yet
- Chapter Two Literature ReviewDocument26 pagesChapter Two Literature Reviewaddulahi100% (1)
- TCP/IP ModelDocument12 pagesTCP/IP Modelulnoor315No ratings yet
- Unit 1 NotesDocument44 pagesUnit 1 Noteschetanwarke11No ratings yet
- Chapter 2Document14 pagesChapter 2Eyosias BelachewNo ratings yet
- SsssssDocument1 pageSsssssDautuso4.0No ratings yet
- What Is TCP/IP?: Transmission Control Protocol, or TCPDocument17 pagesWhat Is TCP/IP?: Transmission Control Protocol, or TCPShubham GuptaNo ratings yet
- Next Generation Networks Unit 2Document30 pagesNext Generation Networks Unit 2parveenntl0% (1)
- Port (Computer Networking)Document5 pagesPort (Computer Networking)Andres R. BucheliNo ratings yet
- Tcp&Udp ExplainingDocument17 pagesTcp&Udp ExplainingG TugstuguldurNo ratings yet
- Notes e CommerceDocument83 pagesNotes e CommerceSawmya ShanmuganathanNo ratings yet
- DCN TCP AssignmentDocument11 pagesDCN TCP Assignmenttalwandi bhindranNo ratings yet
- Designing and Implementing Linux Firewalls and QoS using netfilter, iproute2, NAT and l7-filterFrom EverandDesigning and Implementing Linux Firewalls and QoS using netfilter, iproute2, NAT and l7-filterNo ratings yet
- Unit 3 DNS (Domain Name System)Document184 pagesUnit 3 DNS (Domain Name System)Murtaza VasanwalaNo ratings yet
- 15MA305-Statistics For Information Technology: Dr. S. AthithanDocument17 pages15MA305-Statistics For Information Technology: Dr. S. AthithanMurtaza VasanwalaNo ratings yet
- 15ma305 - Statistics For Information Technology: Dr. N. Balaji Asst. Professor (SG)Document126 pages15ma305 - Statistics For Information Technology: Dr. N. Balaji Asst. Professor (SG)Murtaza Vasanwala0% (1)
- Name of The Applicant: Course AppliedDocument3 pagesName of The Applicant: Course AppliedMurtaza VasanwalaNo ratings yet
- Sample Statement of Purpose For Ms CourseDocument2 pagesSample Statement of Purpose For Ms CourseMurtaza VasanwalaNo ratings yet
- 117 Sop PDFDocument3 pages117 Sop PDFMurtaza VasanwalaNo ratings yet
- IP - The Internet Protocol: Unit - I IP HeaderDocument20 pagesIP - The Internet Protocol: Unit - I IP HeaderMurtaza VasanwalaNo ratings yet
- 117 Sop PDFDocument3 pages117 Sop PDFMurtaza VasanwalaNo ratings yet
- Internet Control Message Protocol (ICMP) : CSC465 - Computer NetworksDocument8 pagesInternet Control Message Protocol (ICMP) : CSC465 - Computer NetworksMurtaza VasanwalaNo ratings yet
- Unit I ARP and RARPDocument37 pagesUnit I ARP and RARPMurtaza VasanwalaNo ratings yet
- Enterprise Resource Planning UNIT-1Document59 pagesEnterprise Resource Planning UNIT-1Murtaza VasanwalaNo ratings yet
- Unit 1 Big Data Analytics - An Introduction (Final)Document65 pagesUnit 1 Big Data Analytics - An Introduction (Final)Murtaza VasanwalaNo ratings yet
- ERP and Business Process Reengineering: UNIT-3Document43 pagesERP and Business Process Reengineering: UNIT-3Murtaza VasanwalaNo ratings yet
- Abstract PDFDocument1 pageAbstract PDFMurtaza VasanwalaNo ratings yet
- ZM4000+Mxp 010+BMS+InterfaceDocument5 pagesZM4000+Mxp 010+BMS+InterfaceabdurasheediNo ratings yet
- 10 Linux and UNIX Interview Questions and Answers Asked in Wipro TCS CapegeminiDocument2 pages10 Linux and UNIX Interview Questions and Answers Asked in Wipro TCS CapegeminiDeepika GargNo ratings yet
- Grammarly 3Document5 pagesGrammarly 3michealNo ratings yet
- Development of An Effective Online Bus Pass Generation System For Transportation Service in Karnataka StateDocument4 pagesDevelopment of An Effective Online Bus Pass Generation System For Transportation Service in Karnataka Statesahil JzzNo ratings yet
- 1MRK505228-BEN E en Product Guide RED670 1.2 Pre-ConfiguredDocument92 pages1MRK505228-BEN E en Product Guide RED670 1.2 Pre-ConfiguredChen ChongNo ratings yet
- 06 ZXCTN 9008 (V2.08.31) Packet Transport Product Hardware Introduction 46P - DiminuidoDocument46 pages06 ZXCTN 9008 (V2.08.31) Packet Transport Product Hardware Introduction 46P - DiminuidoDaniel Dantas100% (1)
- Network Security and Cryptography Dr.P.rizwan AhmedDocument6 pagesNetwork Security and Cryptography Dr.P.rizwan AhmedRizwan AhmedNo ratings yet
- Sixth Sense Technology Shows That We Stepped To A New GenerationDocument10 pagesSixth Sense Technology Shows That We Stepped To A New GenerationVijila PoojaNo ratings yet
- The System For Simulation and Off-Line, Remote Programming of The Mitsubishi Movemaster RV-M1 RobotDocument8 pagesThe System For Simulation and Off-Line, Remote Programming of The Mitsubishi Movemaster RV-M1 RobotSebastian GuaquetaNo ratings yet
- BTU Meter - Manas Microsystems Pvt. Ltd.Document2 pagesBTU Meter - Manas Microsystems Pvt. Ltd.manasNo ratings yet
- Computer Science Engineering Sample PapersDocument4 pagesComputer Science Engineering Sample PapersSwapnil KoliNo ratings yet
- Standards For Multimedia CommunicationsDocument50 pagesStandards For Multimedia Communicationsoureducation.inNo ratings yet
- Software Test PlanDocument18 pagesSoftware Test PlanRheza Satria100% (1)
- Official Invitation Letter Malaysia Open Source Conference 2012 (MOSC2012)Document1 pageOfficial Invitation Letter Malaysia Open Source Conference 2012 (MOSC2012)LinuxMalaysia MalaysiaNo ratings yet
- High VSWR On 3GDocument11 pagesHigh VSWR On 3GRye MarasiganNo ratings yet
- N2 Micro Gateway Installation ManualDocument48 pagesN2 Micro Gateway Installation Manualcs9673100% (4)
- Dahua Ipc Hdbw1230e AwDocument3 pagesDahua Ipc Hdbw1230e AwguillermoNo ratings yet
- New Dual Sonet/Sdh and DS1/DS3 Capability: HP Communications Performance AnalyzerDocument80 pagesNew Dual Sonet/Sdh and DS1/DS3 Capability: HP Communications Performance AnalyzerSanjay YadavNo ratings yet
- Lecture Two Introduction To WAN: by Dr. Alaa I. Al-Muttairi 2020/2021Document32 pagesLecture Two Introduction To WAN: by Dr. Alaa I. Al-Muttairi 2020/2021Bashir Emad kadimNo ratings yet
- 8th SemDocument2 pages8th SemVasu Mkv100% (1)
- B4RN Business Plan v4.1Document26 pagesB4RN Business Plan v4.1b4rnNo ratings yet
- Motion Coordinator: Quick Connection GuideDocument8 pagesMotion Coordinator: Quick Connection GuidethehanhctmNo ratings yet
- Answer CCNA Discovery 3 Ver 4 0 Chapter 8 U Can Get 90 2%Document9 pagesAnswer CCNA Discovery 3 Ver 4 0 Chapter 8 U Can Get 90 2%poentren100% (10)
- 06-Communications and Computer NetworkingDocument28 pages06-Communications and Computer NetworkingM. RazaNo ratings yet
- Draka Kabl Uc300 24 U Utp C5e InstallDocument3 pagesDraka Kabl Uc300 24 U Utp C5e Installlejlas77No ratings yet
- Huawei AR Series Routers Application Comparison and OverviewDocument4 pagesHuawei AR Series Routers Application Comparison and OverviewElizabeth RichNo ratings yet
UDP Principles (Chapter 24) (User Datagram Protocol) : FALL 2005 Csi 4118 - University of Ottawa 1
UDP Principles (Chapter 24) (User Datagram Protocol) : FALL 2005 Csi 4118 - University of Ottawa 1
Uploaded by
Murtaza Vasanwala0 ratings0% found this document useful (0 votes)
57 views12 pagesUDP is a connectionless transport layer protocol that provides fast, unreliable datagram delivery. It uses port numbers to identify applications and delivers individual messages without establishing connections. Well-known ports are used for common applications like DNS, SNMP, and DHCP, while dynamic ports above 49151 can be used for any purpose. Checksums are optional for error detection.
Original Description:
Original Title
2.6-UDP
Copyright
© © All Rights Reserved
Available Formats
PPT, PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentUDP is a connectionless transport layer protocol that provides fast, unreliable datagram delivery. It uses port numbers to identify applications and delivers individual messages without establishing connections. Well-known ports are used for common applications like DNS, SNMP, and DHCP, while dynamic ports above 49151 can be used for any purpose. Checksums are optional for error detection.
Copyright:
© All Rights Reserved
Available Formats
Download as PPT, PDF, TXT or read online from Scribd
Download as ppt, pdf, or txt
0 ratings0% found this document useful (0 votes)
57 views12 pagesUDP Principles (Chapter 24) (User Datagram Protocol) : FALL 2005 Csi 4118 - University of Ottawa 1
UDP Principles (Chapter 24) (User Datagram Protocol) : FALL 2005 Csi 4118 - University of Ottawa 1
Uploaded by
Murtaza VasanwalaUDP is a connectionless transport layer protocol that provides fast, unreliable datagram delivery. It uses port numbers to identify applications and delivers individual messages without establishing connections. Well-known ports are used for common applications like DNS, SNMP, and DHCP, while dynamic ports above 49151 can be used for any purpose. Checksums are optional for error detection.
Copyright:
© All Rights Reserved
Available Formats
Download as PPT, PDF, TXT or read online from Scribd
Download as ppt, pdf, or txt
You are on page 1of 12
Part 2.
UDP Principles (Chapter 24)
(User Datagram Protocol)
FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 1
UDP: User Datagram Protocol
In TCP/IP protocol suite, using IP to transport
datagram (similar to IP datagram).
Allows a application to send datagram to
other application on the remote machine.
Delivery and duplicate detection are not
guaranteed.
Low overhead: faster than TCP
FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA
UDP Characteristics
End-to-End: an application sends/receives data to/from
another application.
Connectionless: Application does not need to preestablish
communication before sending data; application does not
need to terminate communication when finished.
Message-oriented: application sends/receives individual
messages (UDP datagram), not packets.
Best-effort: same best-effort delivery semantics as IP. I.e.
message can be lost, duplicated, and corrupted.
Arbitrary interaction: application communicates with many
or one other applications.
Operating system independent: identifying application
does not depend on O/S.
FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA
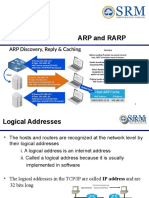
Identifying An Application
UDP cannot extend IP address
No unused bits
Cannot use OS-dependent quantity
Process ID, Task number, Job name
Must work on all computer systems
Technique
Each application assigned unique integer
Called protocol port number
FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA
Protocol Port Number
UDP uses Port Number to identify an application
as an endpoint.
UDP messages are delivered to the port specified
in the message by the sending application
In general, a port can be used for any datagram,
as long as the sender and the receiver agrees
In practice, a collection of well-known ports are
used for special purposes such as telnet, ftp, and
email. E.g. port 7 for Echo application.
Local operating system provides an interface for
processes to specify and access a port.
FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA
Well-known Port Numbers
list of UDP ports copied from /etc/services on Solaris
2.5:
FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA
UDP Multiplexing & Demultiplexing
Sender: multiplexing of UDP datagrams.
UDP datagrams are received from multiple application programs.
A single sequence of UDP datagrams is passed to IP layer.
Receiver: demultiplexing of UDP datagrams.
Single sequence of UDP datagrams received from IP layer.
UDP datagram received is passed to appropriate application.
FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA
UDP Datagram Format
Source Port - 16 bit port number
Destination Port - 16 bit port number
Length (of UDP header + data) - 16 bit count of octets
UDP checksum - 16 bit field. if 0, then there is no checksum, else it is a
checksum over a pseudo header + UDP data area
FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA
Checksum and Pseudo Header
UDP uses a pseudo-header to verify that the UDP
message has arrived at both the correct machine
and the correct port.
• Proto : IP protocol type code.
• Length : Length of the UDP datagram.
FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA
Encapsulation and Layering
UDP message is encapsulated into an IP datagram.
IP datagram in turn is encapsulated into a physical
frame for actually delivery.
FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA
Applications
Numerous key Internet applications use UDP, including: the
where queries must be fast and only consist of a single request
followed by a single reply packet
Domain Name System (DNS),
Simple Network Management Protocol (SNMP)
Routing Information Protocol (RIP)[1] and the
Dynamic Host Configuration Protocol (DHCP).
FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA
Port Ranges
The Internet Assigned Numbers Authority (IANA) has divided port
numbers into three ranges.[4]
Port numbers 0 through 1023 are used for common, well-known
services. On Unix-like operating systems, using one of these ports
requires superuser operating permission.
Port numbers 1024 through 49151 are the registered ports used for
IANA-registered services.
Ports 49152 through 65535 are dynamic ports that are not officially
designated for any specific service, and may be used for any
purpose. They also are used as ephemeral ports, from which
software running on the host may randomly choose a port in order
to define itself.[4] In effect, they are used as temporary ports primarily
by clients when communicating with servers.
FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA
You might also like
- Report On UdpDocument14 pagesReport On UdpSagar GaddamNo ratings yet
- TCP-IP Model in Data Communication and NetworkingDocument6 pagesTCP-IP Model in Data Communication and NetworkingAJER JOURNALNo ratings yet
- 15MA305-Statistics For Information Technology: Dr. S. AthithanDocument18 pages15MA305-Statistics For Information Technology: Dr. S. AthithanMurtaza VasanwalaNo ratings yet
- Ass. 1Document3 pagesAss. 1danilo sugot100% (1)
- MC - Press Iseries - And.as.400.java - At.work - CHMDocument656 pagesMC - Press Iseries - And.as.400.java - At.work - CHMcomputer_ebookNo ratings yet
- Bot Service DocumentatioDocument271 pagesBot Service DocumentatioLaurentiuStanciuNo ratings yet
- Liftmaster MYQPCK ManualDocument8 pagesLiftmaster MYQPCK Manualsharklaser69No ratings yet
- CS8581-Networks Lab Manual (2020-2024)Document50 pagesCS8581-Networks Lab Manual (2020-2024)john wickNo ratings yet
- CHAPTER 04 (Network)Document40 pagesCHAPTER 04 (Network)Mihirete BantegegnNo ratings yet
- Unit-5 NotesDocument45 pagesUnit-5 NotesMOGILIPURI KEERTHINo ratings yet
- Network Programming NotesDocument138 pagesNetwork Programming NotesLaxman YadavNo ratings yet
- UDPDocument7 pagesUDPMit Thakore100% (1)
- Lesson 3Document35 pagesLesson 3Bhon-Bhon AgcaoiliNo ratings yet
- AssgB9 - UDP SocketDocument5 pagesAssgB9 - UDP Socketvaibhav patilNo ratings yet
- MC0087Article On UDP PDFDocument1 pageMC0087Article On UDP PDFPramod ChakravarthyNo ratings yet
- 2 6-UdpDocument27 pages2 6-Udpedemo6870No ratings yet
- Chapter OneDocument13 pagesChapter OnemenbereNo ratings yet
- Research Work It301Document9 pagesResearch Work It301Jr Gadiano GallardoNo ratings yet
- Hct6000 Tcpip OptionDocument14 pagesHct6000 Tcpip OptionGerman DfrNo ratings yet
- Computer Networks I: Dr:-Rania Abul SeoudDocument37 pagesComputer Networks I: Dr:-Rania Abul SeoudMony JosephNo ratings yet
- Npms Unit-1Document36 pagesNpms Unit-1Karthik RaviNo ratings yet
- Unit 1 NotesDocument24 pagesUnit 1 Notessonal rajNo ratings yet
- User Datagram Protocol (UDP)Document9 pagesUser Datagram Protocol (UDP)frtessNo ratings yet
- L2 SocketsDocument31 pagesL2 SocketsCedric TangNo ratings yet
- 7TCPIPDocument40 pages7TCPIPgokul adethyaNo ratings yet
- Comptia-Network Study GuideDocument36 pagesComptia-Network Study GuideJonathan Velez Velazquez100% (3)
- DCN Unit-4 SaqDocument5 pagesDCN Unit-4 Saqsravan kumarNo ratings yet
- Well Known Ports (Numbers 0 To 1023) - These Numbers Are ReservedDocument1 pageWell Known Ports (Numbers 0 To 1023) - These Numbers Are ReservedNicoleta NovacNo ratings yet
- ChapterDocument57 pagesChapterYomif NiguseNo ratings yet
- Internet and Protocol-3Document16 pagesInternet and Protocol-3Par VeenNo ratings yet
- Computer Network - TCP - IP ModelDocument5 pagesComputer Network - TCP - IP ModelAMARJEET KUMARNo ratings yet
- PR Lab5 Vlas MihaiDocument17 pagesPR Lab5 Vlas MihaiAlexey DarievNo ratings yet
- Lecture 2 Introduction To Client Server ComputingDocument19 pagesLecture 2 Introduction To Client Server ComputingericNo ratings yet
- TCPIP ModelDocument9 pagesTCPIP Modelroysayanccp05No ratings yet
- Network Programming & ManagementDocument27 pagesNetwork Programming & ManagementmeerasasiNo ratings yet
- TCP IP ModelDocument8 pagesTCP IP Modelguptariya0111No ratings yet
- Ôn Tập GKDocument4 pagesÔn Tập GKHoàng DươngNo ratings yet
- Prog Linux Sockets 456Document19 pagesProg Linux Sockets 456mushtaq khan niaziNo ratings yet
- Introduction To TCPDocument1 pageIntroduction To TCPtinajose1211No ratings yet
- CS SreyashDocument10 pagesCS Sreyashtacac87741No ratings yet
- Network Programming and Java SocketsDocument27 pagesNetwork Programming and Java SocketsIsmail Adha KesumaNo ratings yet
- Network PROTOCOLSDocument11 pagesNetwork PROTOCOLSRose of sharonNo ratings yet
- Unit 4 Lec1Document18 pagesUnit 4 Lec1SangetaNo ratings yet
- Unit 4Document10 pagesUnit 4Nandkumar KhachaneNo ratings yet
- Network ProtocolsDocument16 pagesNetwork Protocolshassanabid15No ratings yet
- 3.2 TCPIP ModelDocument5 pages3.2 TCPIP ModelSuyasha JainNo ratings yet
- Chapter 7Document41 pagesChapter 7Muqeemuddin SyedNo ratings yet
- TCP IP Protocol Explanation 1 (03.01.2024)Document5 pagesTCP IP Protocol Explanation 1 (03.01.2024)aloishp36No ratings yet
- Client-Server ComputingDocument19 pagesClient-Server ComputingHISNONYMOUSNo ratings yet
- Ex No: 9 Study of UDP PerformanceDocument33 pagesEx No: 9 Study of UDP Performancenganeshv1988No ratings yet
- Programming With TCP/IP - Best PracticesDocument31 pagesProgramming With TCP/IP - Best PracticesmrwanzNo ratings yet
- NPM Unit 1 NotesDocument23 pagesNPM Unit 1 NotesVinoth ShankarNo ratings yet
- Chapter Two Literature ReviewDocument26 pagesChapter Two Literature Reviewaddulahi100% (1)
- TCP/IP ModelDocument12 pagesTCP/IP Modelulnoor315No ratings yet
- Unit 1 NotesDocument44 pagesUnit 1 Noteschetanwarke11No ratings yet
- Chapter 2Document14 pagesChapter 2Eyosias BelachewNo ratings yet
- SsssssDocument1 pageSsssssDautuso4.0No ratings yet
- What Is TCP/IP?: Transmission Control Protocol, or TCPDocument17 pagesWhat Is TCP/IP?: Transmission Control Protocol, or TCPShubham GuptaNo ratings yet
- Next Generation Networks Unit 2Document30 pagesNext Generation Networks Unit 2parveenntl0% (1)
- Port (Computer Networking)Document5 pagesPort (Computer Networking)Andres R. BucheliNo ratings yet
- Tcp&Udp ExplainingDocument17 pagesTcp&Udp ExplainingG TugstuguldurNo ratings yet
- Notes e CommerceDocument83 pagesNotes e CommerceSawmya ShanmuganathanNo ratings yet
- DCN TCP AssignmentDocument11 pagesDCN TCP Assignmenttalwandi bhindranNo ratings yet
- Designing and Implementing Linux Firewalls and QoS using netfilter, iproute2, NAT and l7-filterFrom EverandDesigning and Implementing Linux Firewalls and QoS using netfilter, iproute2, NAT and l7-filterNo ratings yet
- Unit 3 DNS (Domain Name System)Document184 pagesUnit 3 DNS (Domain Name System)Murtaza VasanwalaNo ratings yet
- 15MA305-Statistics For Information Technology: Dr. S. AthithanDocument17 pages15MA305-Statistics For Information Technology: Dr. S. AthithanMurtaza VasanwalaNo ratings yet
- 15ma305 - Statistics For Information Technology: Dr. N. Balaji Asst. Professor (SG)Document126 pages15ma305 - Statistics For Information Technology: Dr. N. Balaji Asst. Professor (SG)Murtaza Vasanwala0% (1)
- Name of The Applicant: Course AppliedDocument3 pagesName of The Applicant: Course AppliedMurtaza VasanwalaNo ratings yet
- Sample Statement of Purpose For Ms CourseDocument2 pagesSample Statement of Purpose For Ms CourseMurtaza VasanwalaNo ratings yet
- 117 Sop PDFDocument3 pages117 Sop PDFMurtaza VasanwalaNo ratings yet
- IP - The Internet Protocol: Unit - I IP HeaderDocument20 pagesIP - The Internet Protocol: Unit - I IP HeaderMurtaza VasanwalaNo ratings yet
- 117 Sop PDFDocument3 pages117 Sop PDFMurtaza VasanwalaNo ratings yet
- Internet Control Message Protocol (ICMP) : CSC465 - Computer NetworksDocument8 pagesInternet Control Message Protocol (ICMP) : CSC465 - Computer NetworksMurtaza VasanwalaNo ratings yet
- Unit I ARP and RARPDocument37 pagesUnit I ARP and RARPMurtaza VasanwalaNo ratings yet
- Enterprise Resource Planning UNIT-1Document59 pagesEnterprise Resource Planning UNIT-1Murtaza VasanwalaNo ratings yet
- Unit 1 Big Data Analytics - An Introduction (Final)Document65 pagesUnit 1 Big Data Analytics - An Introduction (Final)Murtaza VasanwalaNo ratings yet
- ERP and Business Process Reengineering: UNIT-3Document43 pagesERP and Business Process Reengineering: UNIT-3Murtaza VasanwalaNo ratings yet
- Abstract PDFDocument1 pageAbstract PDFMurtaza VasanwalaNo ratings yet
- ZM4000+Mxp 010+BMS+InterfaceDocument5 pagesZM4000+Mxp 010+BMS+InterfaceabdurasheediNo ratings yet
- 10 Linux and UNIX Interview Questions and Answers Asked in Wipro TCS CapegeminiDocument2 pages10 Linux and UNIX Interview Questions and Answers Asked in Wipro TCS CapegeminiDeepika GargNo ratings yet
- Grammarly 3Document5 pagesGrammarly 3michealNo ratings yet
- Development of An Effective Online Bus Pass Generation System For Transportation Service in Karnataka StateDocument4 pagesDevelopment of An Effective Online Bus Pass Generation System For Transportation Service in Karnataka Statesahil JzzNo ratings yet
- 1MRK505228-BEN E en Product Guide RED670 1.2 Pre-ConfiguredDocument92 pages1MRK505228-BEN E en Product Guide RED670 1.2 Pre-ConfiguredChen ChongNo ratings yet
- 06 ZXCTN 9008 (V2.08.31) Packet Transport Product Hardware Introduction 46P - DiminuidoDocument46 pages06 ZXCTN 9008 (V2.08.31) Packet Transport Product Hardware Introduction 46P - DiminuidoDaniel Dantas100% (1)
- Network Security and Cryptography Dr.P.rizwan AhmedDocument6 pagesNetwork Security and Cryptography Dr.P.rizwan AhmedRizwan AhmedNo ratings yet
- Sixth Sense Technology Shows That We Stepped To A New GenerationDocument10 pagesSixth Sense Technology Shows That We Stepped To A New GenerationVijila PoojaNo ratings yet
- The System For Simulation and Off-Line, Remote Programming of The Mitsubishi Movemaster RV-M1 RobotDocument8 pagesThe System For Simulation and Off-Line, Remote Programming of The Mitsubishi Movemaster RV-M1 RobotSebastian GuaquetaNo ratings yet
- BTU Meter - Manas Microsystems Pvt. Ltd.Document2 pagesBTU Meter - Manas Microsystems Pvt. Ltd.manasNo ratings yet
- Computer Science Engineering Sample PapersDocument4 pagesComputer Science Engineering Sample PapersSwapnil KoliNo ratings yet
- Standards For Multimedia CommunicationsDocument50 pagesStandards For Multimedia Communicationsoureducation.inNo ratings yet
- Software Test PlanDocument18 pagesSoftware Test PlanRheza Satria100% (1)
- Official Invitation Letter Malaysia Open Source Conference 2012 (MOSC2012)Document1 pageOfficial Invitation Letter Malaysia Open Source Conference 2012 (MOSC2012)LinuxMalaysia MalaysiaNo ratings yet
- High VSWR On 3GDocument11 pagesHigh VSWR On 3GRye MarasiganNo ratings yet
- N2 Micro Gateway Installation ManualDocument48 pagesN2 Micro Gateway Installation Manualcs9673100% (4)
- Dahua Ipc Hdbw1230e AwDocument3 pagesDahua Ipc Hdbw1230e AwguillermoNo ratings yet
- New Dual Sonet/Sdh and DS1/DS3 Capability: HP Communications Performance AnalyzerDocument80 pagesNew Dual Sonet/Sdh and DS1/DS3 Capability: HP Communications Performance AnalyzerSanjay YadavNo ratings yet
- Lecture Two Introduction To WAN: by Dr. Alaa I. Al-Muttairi 2020/2021Document32 pagesLecture Two Introduction To WAN: by Dr. Alaa I. Al-Muttairi 2020/2021Bashir Emad kadimNo ratings yet
- 8th SemDocument2 pages8th SemVasu Mkv100% (1)
- B4RN Business Plan v4.1Document26 pagesB4RN Business Plan v4.1b4rnNo ratings yet
- Motion Coordinator: Quick Connection GuideDocument8 pagesMotion Coordinator: Quick Connection GuidethehanhctmNo ratings yet
- Answer CCNA Discovery 3 Ver 4 0 Chapter 8 U Can Get 90 2%Document9 pagesAnswer CCNA Discovery 3 Ver 4 0 Chapter 8 U Can Get 90 2%poentren100% (10)
- 06-Communications and Computer NetworkingDocument28 pages06-Communications and Computer NetworkingM. RazaNo ratings yet
- Draka Kabl Uc300 24 U Utp C5e InstallDocument3 pagesDraka Kabl Uc300 24 U Utp C5e Installlejlas77No ratings yet
- Huawei AR Series Routers Application Comparison and OverviewDocument4 pagesHuawei AR Series Routers Application Comparison and OverviewElizabeth RichNo ratings yet