Professional Documents
Culture Documents
Key Logger in Cyber Security: Conclusion Block Diagram
Key Logger in Cyber Security: Conclusion Block Diagram
Uploaded by
ASAD BAIG0 ratings0% found this document useful (0 votes)
92 views1 pageThe document summarizes key loggers, which are software or hardware that records keyboard inputs to steal sensitive information like passwords or credit card numbers. It discusses that key loggers can be either hardware devices attached to computers or software secretly installed. The document concludes that key loggers are one of the oldest cyber threats and allow attackers to intercept every keystroke typed by users.
Original Description:
Original Title
Asad Poster
Copyright
© © All Rights Reserved
Available Formats
PPTX, PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentThe document summarizes key loggers, which are software or hardware that records keyboard inputs to steal sensitive information like passwords or credit card numbers. It discusses that key loggers can be either hardware devices attached to computers or software secretly installed. The document concludes that key loggers are one of the oldest cyber threats and allow attackers to intercept every keystroke typed by users.
Copyright:
© All Rights Reserved
Available Formats
Download as PPTX, PDF, TXT or read online from Scribd
Download as pptx, pdf, or txt
0 ratings0% found this document useful (0 votes)
92 views1 pageKey Logger in Cyber Security: Conclusion Block Diagram
Key Logger in Cyber Security: Conclusion Block Diagram
Uploaded by
ASAD BAIGThe document summarizes key loggers, which are software or hardware that records keyboard inputs to steal sensitive information like passwords or credit card numbers. It discusses that key loggers can be either hardware devices attached to computers or software secretly installed. The document concludes that key loggers are one of the oldest cyber threats and allow attackers to intercept every keystroke typed by users.
Copyright:
© All Rights Reserved
Available Formats
Download as PPTX, PDF, TXT or read online from Scribd
Download as pptx, pdf, or txt
You are on page 1of 1
Bajaj Institute of Technology, Wardha
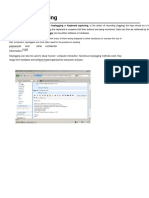
Key Logger in Cyber Security
Asad Shahakar Baig
Introduction Block diagram Conclusion
• Key loggers are a type of • A key logger is a type of
monitoring software designed surveillance software or
to record keystrokes made by a hardware device that has
user. One of the oldest forms capability to record every
of cyber threat, these keystroke.
keystroke loggers record the • There are two types of key
information you type into a logger namely hardware key
website or application and logger and software key
send to back to a third party. loggers.
Objectives References
• The main objective of key • Shetty, S. (2005, April).
loggers is to interfere in the Introduction to spyware key
chain of events that happen loggers. Security Focus.
when a key is pressed and Retrieved 27 March 2008
when the data is displayed on from
the monitor as a result of a http://www.securityfocus.co
keystroke. m/infocus/1829
• Either it can be hardware key • https://
logger or software key logger. www.researchgate.net/
publication/
www.bingimages.com 228797653_Keystroke_loggi
Department of Computer Engineering ng_keylogging
3rd semester/roll no.207.
You might also like
- Research Paper On KeyloggersDocument3 pagesResearch Paper On KeyloggersRish100% (1)
- Synopsis of Minor Project Keylogger': Dr. Brahampal Singh Tarun Chauhan 00820602019 1 ShiftDocument7 pagesSynopsis of Minor Project Keylogger': Dr. Brahampal Singh Tarun Chauhan 00820602019 1 ShiftTarun ChauhanNo ratings yet
- Synopsis of Major Project Keylogger': Submitted To - Submitted byDocument10 pagesSynopsis of Major Project Keylogger': Submitted To - Submitted byKushagra SinghNo ratings yet
- (IJCT-V2I2P14) Authors: Ms.C.Sathya, Mr.R.B.Saroo RajDocument9 pages(IJCT-V2I2P14) Authors: Ms.C.Sathya, Mr.R.B.Saroo RajIjctJournalsNo ratings yet
- System Surveillance Using KeyloggerDocument22 pagesSystem Surveillance Using Keyloggergarapati kavyasri0% (1)
- Internship ReportDocument14 pagesInternship ReportPrashantNo ratings yet
- Study On Key Logger: Challenges and SolutionsDocument10 pagesStudy On Key Logger: Challenges and SolutionsJeffrey walkerNo ratings yet
- Project ProposalDocument2 pagesProject ProposalRishNo ratings yet
- System Surveillance Using KeyloggerDocument22 pagesSystem Surveillance Using KeyloggerAsh KetchumNo ratings yet
- Keystroke Logging KeyloggingDocument14 pagesKeystroke Logging Keyloggingomkar ejjagiriNo ratings yet
- Synopsis of KeyloggerDocument17 pagesSynopsis of KeyloggerParvaiz RainaNo ratings yet
- Keystroke Logging KeyloggingDocument14 pagesKeystroke Logging KeyloggingAnjali100% (1)
- Seminar-I PPT Template-3rd Sem-21-22Document20 pagesSeminar-I PPT Template-3rd Sem-21-22ASAD BAIGNo ratings yet
- Keee SRSDocument10 pagesKeee SRSmaheshreddynaru0No ratings yet
- Keylogger Deployment and DetectionDocument6 pagesKeylogger Deployment and DetectionIJRASETPublicationsNo ratings yet
- Keylogger For Windows Using PythonDocument3 pagesKeylogger For Windows Using PythonEditor IJTSRDNo ratings yet
- NSM Theory NewDocument4 pagesNSM Theory Newguru shashankNo ratings yet
- Survey On Keyloggers A Monitoring ToolDocument3 pagesSurvey On Keyloggers A Monitoring ToolEditor IJTSRDNo ratings yet
- "Implementation of Keylogger Using HOOKUP Algorithm": Project SynopsisDocument7 pages"Implementation of Keylogger Using HOOKUP Algorithm": Project Synopsisraman dwivediNo ratings yet
- A Survey of Keylogger in Cybersecurity EducationDocument5 pagesA Survey of Keylogger in Cybersecurity EducationEditor IJTSRDNo ratings yet
- Keylogger WPS OfficeDocument10 pagesKeylogger WPS Officeroyceangelo.buayaNo ratings yet
- An Introduction To Undetectable Keyloggers With Experimental TestingDocument6 pagesAn Introduction To Undetectable Keyloggers With Experimental TestingibnuramadhanNo ratings yet
- Secure Software Project Report On: Key LoggerDocument10 pagesSecure Software Project Report On: Key LoggerAkash PruthiNo ratings yet
- Windows Post Exploitation (MSF) Keylogger For SecurityDocument7 pagesWindows Post Exploitation (MSF) Keylogger For SecurityIJRASETPublicationsNo ratings yet
- Keystroke LoggersDocument3 pagesKeystroke LoggersCherry MarieNo ratings yet
- B-157 PosterDocument1 pageB-157 PosterT SREEHARSHA REDDY,CSE(19-23) Vel Tech, ChennaiNo ratings yet
- Unprivileged Black-Box Detection of User-Space Key Loggers: AbstractDocument8 pagesUnprivileged Black-Box Detection of User-Space Key Loggers: AbstractInternational Journal of Engineering and TechniquesNo ratings yet
- Survey of Keylogger Technologies: February 2014Document9 pagesSurvey of Keylogger Technologies: February 2014Zoltán CserneiNo ratings yet
- Rino KeyloggerDocument11 pagesRino KeyloggerSrikrishnarajan NatarajanNo ratings yet
- 09 KeyloggersDocument13 pages09 Keyloggersdhruv goswami50% (2)
- Advanced Keylogger For Ethical HackingDocument5 pagesAdvanced Keylogger For Ethical HackingZoltán CserneiNo ratings yet
- Signum Soft KeyloggerDocument12 pagesSignum Soft KeyloggerLukaRaterNo ratings yet
- Advanced Keylogger For Ethical HackingDocument6 pagesAdvanced Keylogger For Ethical HackingAnagha MNo ratings yet
- A Hybrid Approach Based Advanced KeyloggerDocument5 pagesA Hybrid Approach Based Advanced KeyloggerEditor IJTSRDNo ratings yet
- Minor Project Presentation Topic: Keylogger and PC Monitoring SystemDocument19 pagesMinor Project Presentation Topic: Keylogger and PC Monitoring SystemDivyansh Singh Sengar0% (1)
- Security: Logmein An In-Depth LookDocument14 pagesSecurity: Logmein An In-Depth LookMrJavitoGMNo ratings yet
- A Review On Key Logger Malware Detection Concerning Password OpacityDocument8 pagesA Review On Key Logger Malware Detection Concerning Password OpacitySmarty HackNo ratings yet
- KeyloggerDocument33 pagesKeyloggerRaone gNo ratings yet
- BitLockerBypass (En)Document5 pagesBitLockerBypass (En)Overkill SecurityNo ratings yet
- Keystroke LoggingDocument9 pagesKeystroke LoggingDarshan Singh ThakurNo ratings yet
- INTERNSHIP Finalreport - RemovedDocument13 pagesINTERNSHIP Finalreport - RemovedPrashantNo ratings yet
- KeyloggerDocument6 pagesKeyloggerAnagha MNo ratings yet
- Keyloger TemplateDocument20 pagesKeyloger Templatepragathi RoopaSriNo ratings yet
- Lab Da-4Document25 pagesLab Da-4xyzNo ratings yet
- Record The Keystrokes Made by User Using Keyloggers To Monitor The SystemsDocument4 pagesRecord The Keystrokes Made by User Using Keyloggers To Monitor The SystemsdevilNo ratings yet
- Subject: Network Security Topic: Keyloggers Working and TypesDocument15 pagesSubject: Network Security Topic: Keyloggers Working and TypesskjdfkjsdNo ratings yet
- Ahmed 2019 Ijca 919483Document6 pagesAhmed 2019 Ijca 919483Naruto UzamakiNo ratings yet
- Simple Password Security System Using Logic Gates in MultisimDocument8 pagesSimple Password Security System Using Logic Gates in Multisimantoreep ghatak0% (2)
- Keylogger & SecuritYDocument12 pagesKeylogger & SecuritYjitbhav97No ratings yet
- Cyber Unit 2Document18 pagesCyber Unit 2Naseem AhamadNo ratings yet
- RGP IBM FR grp6Document24 pagesRGP IBM FR grp6Krish GajeraNo ratings yet
- Abuse Public PEFDocument159 pagesAbuse Public PEFMac JoyNo ratings yet
- Gid WP5Document10 pagesGid WP5fariborz33samNo ratings yet
- CyberDocument9 pagesCyberbabulkiidNo ratings yet
- Password AttacksDocument13 pagesPassword Attackstala.rateb.learnNo ratings yet
- SrsDocument13 pagesSrsSantoshkumar ShaliNo ratings yet
- Remove Keyloggers Removal InstructionsDocument3 pagesRemove Keyloggers Removal InstructionsRihlesh ParlNo ratings yet
- KeyloggerDocument13 pagesKeyloggerStar BoyNo ratings yet
- Supporting A Dynamic Program Signature: An Intrusion Detection Framework For MicroprocessorsDocument4 pagesSupporting A Dynamic Program Signature: An Intrusion Detection Framework For MicroprocessorsmosanabaniNo ratings yet
- Securing Application Deployment with Obfuscation and Code Signing: How to Create 3 Layers of Protection for .NET Release BuildFrom EverandSecuring Application Deployment with Obfuscation and Code Signing: How to Create 3 Layers of Protection for .NET Release BuildNo ratings yet
- 1st LectureDocument5 pages1st LectureDMJ ardunioNo ratings yet
- Declaration by Stacey PerinoDocument22 pagesDeclaration by Stacey PerinoSarah BatchaNo ratings yet
- Model of Conventional EncryptionDocument10 pagesModel of Conventional EncryptionekalveNo ratings yet
- Odern Password Cracking: A Hands-On Approach To Creating An Optimised and Versatile Attack.Document65 pagesOdern Password Cracking: A Hands-On Approach To Creating An Optimised and Versatile Attack.eraser296No ratings yet
- Letter To All OFIs Issuance of Risk-Based Cybersecurity Framework and Guidelines For Other Financial InstitutionsDocument43 pagesLetter To All OFIs Issuance of Risk-Based Cybersecurity Framework and Guidelines For Other Financial InstitutionsjideNo ratings yet
- CN 416-Week #1&2 - Introduction To Network ForensicsDocument32 pagesCN 416-Week #1&2 - Introduction To Network ForensicsITtickeiNo ratings yet
- Network Security Essentials: Fifth Edition by William StallingsDocument31 pagesNetwork Security Essentials: Fifth Edition by William StallingsMuhammad Imran ButtNo ratings yet
- TroublesCisco IOS Firewallhooting Cisco IOS Firewall-Based and Cisco Secure PIX Firewall-Based IPSec VPNsDocument54 pagesTroublesCisco IOS Firewallhooting Cisco IOS Firewall-Based and Cisco Secure PIX Firewall-Based IPSec VPNsJamesNo ratings yet
- Dns Using Blockchain-1 PDFDocument27 pagesDns Using Blockchain-1 PDFSidheeque FasalNo ratings yet
- Bhs Inggris 12 IpsDocument30 pagesBhs Inggris 12 IpsDhea Aulia PutriNo ratings yet
- Final Seminar ReportDocument20 pagesFinal Seminar Reportbalaji xeroxNo ratings yet
- Block Chain Hash FunctionsDocument35 pagesBlock Chain Hash FunctionsAkshay HariNo ratings yet
- Network Access Control: What Is NAC?: Joel M Snyder Senior Partner Opus OneDocument33 pagesNetwork Access Control: What Is NAC?: Joel M Snyder Senior Partner Opus Onesimardeepsingh3No ratings yet
- Cybercrime & Network Security: Presented by Jyoti SharmaDocument22 pagesCybercrime & Network Security: Presented by Jyoti SharmaNitin GuptaNo ratings yet
- Cyber Security Engineer Resume SampleDocument1 pageCyber Security Engineer Resume SampleAmit TiwariNo ratings yet
- FortiGate Cookbook Part2Document159 pagesFortiGate Cookbook Part2m dickyNo ratings yet
- BGP PresentationDocument15 pagesBGP Presentationapi-317825370No ratings yet
- Dell EMC VxRail - Troubleshooting Guide For VxRail Plugin Certificate Issue - Dell USDocument5 pagesDell EMC VxRail - Troubleshooting Guide For VxRail Plugin Certificate Issue - Dell US604597No ratings yet
- Steganography Powerpoint Presentation by Papan SarkarDocument11 pagesSteganography Powerpoint Presentation by Papan SarkarPapan SarkarNo ratings yet
- SummaryDocument2 pagesSummaryLucian MogosNo ratings yet
- Cyber-Security-Infographic - FCADocument1 pageCyber-Security-Infographic - FCAMousumi Utkarsh RayNo ratings yet
- Smt. Radhikatai Pandav College of Engineering NagpurDocument34 pagesSmt. Radhikatai Pandav College of Engineering NagpurMadhuri RahangdaleNo ratings yet
- CompTIA Security - (SY0-601) Practice Exam #6 - ResultadosDocument56 pagesCompTIA Security - (SY0-601) Practice Exam #6 - Resultadosjosue.monge.mongeNo ratings yet
- Output CertificateDocument1 pageOutput CertificateNIRNAY CHAKRABORTYNo ratings yet
- INFO8500 Instructional Plan W21Document11 pagesINFO8500 Instructional Plan W21Jonkers LeeNo ratings yet
- Unit 5 - Class - Lecture - SlidesDocument55 pagesUnit 5 - Class - Lecture - Slidescsbs249050No ratings yet
- Cybersecurity For SMEDocument35 pagesCybersecurity For SMEElijah100% (1)
- How Do I Setup Cisco VPN ClientDocument2 pagesHow Do I Setup Cisco VPN ClientsergiorsantosNo ratings yet
- Encryption and Decryption of Data Images AppDocument13 pagesEncryption and Decryption of Data Images AppPlayIt AllNo ratings yet
- CP R81.10 SitetoSiteVPN AdminGuideDocument241 pagesCP R81.10 SitetoSiteVPN AdminGuideClaudio LuizNo ratings yet